Submitted:
15 December 2024
Posted:
17 December 2024
You are already at the latest version
Abstract
Keywords:
I. Introduction
II. Methodology
A. Type of Study
B. Techniques and Instruments
C. Bibliographic Search Procedure
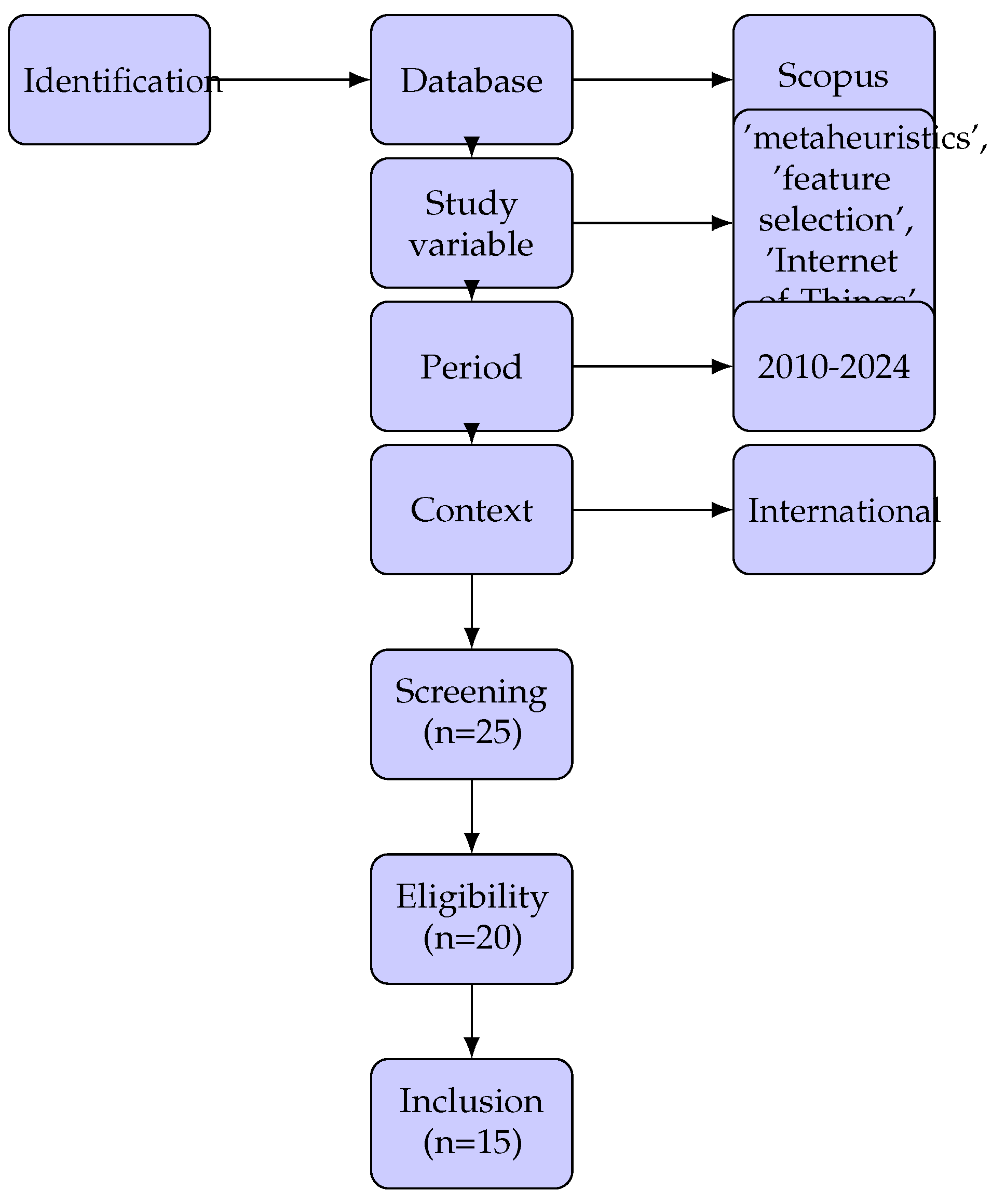
D. Study Analysis
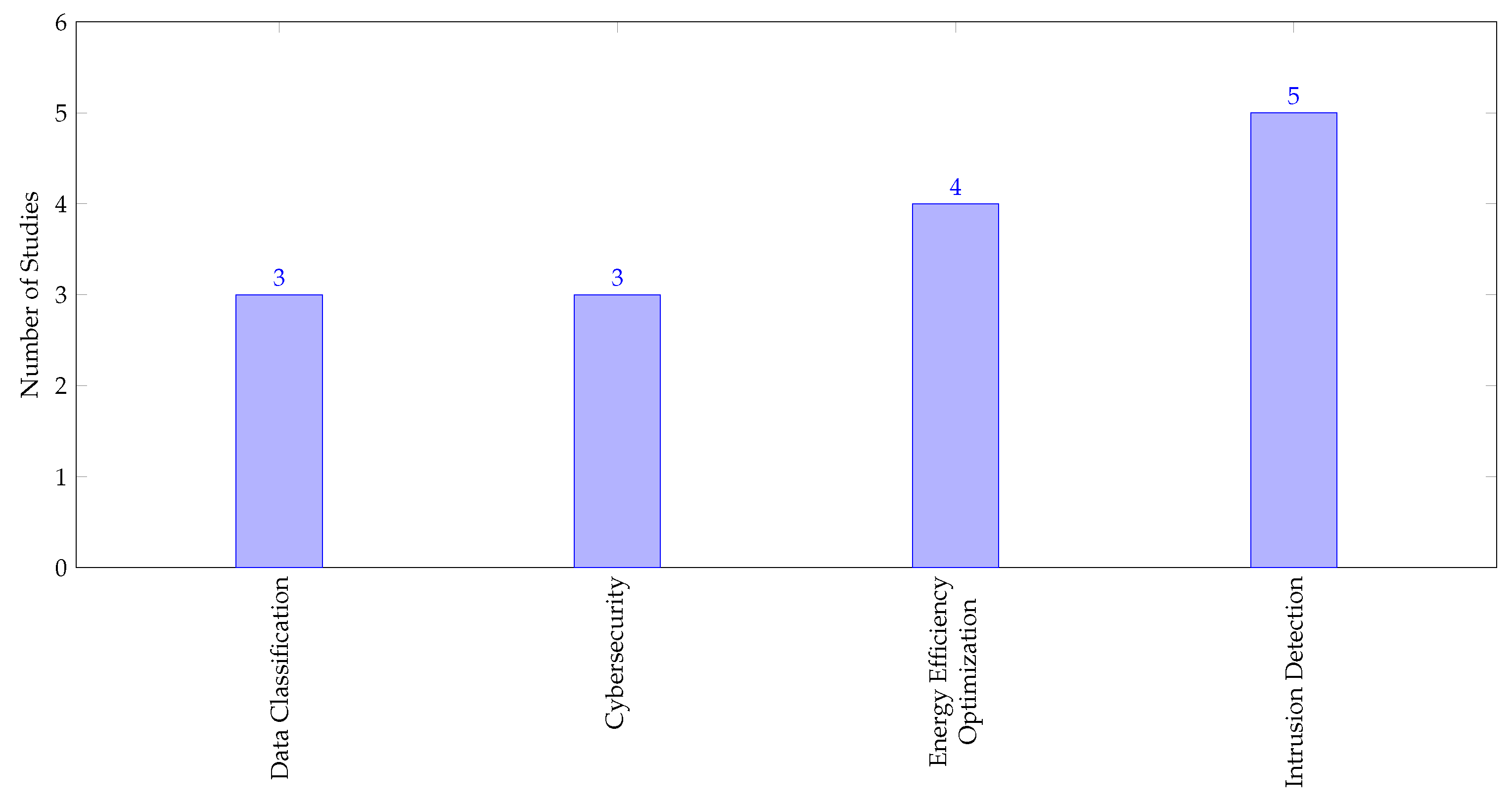
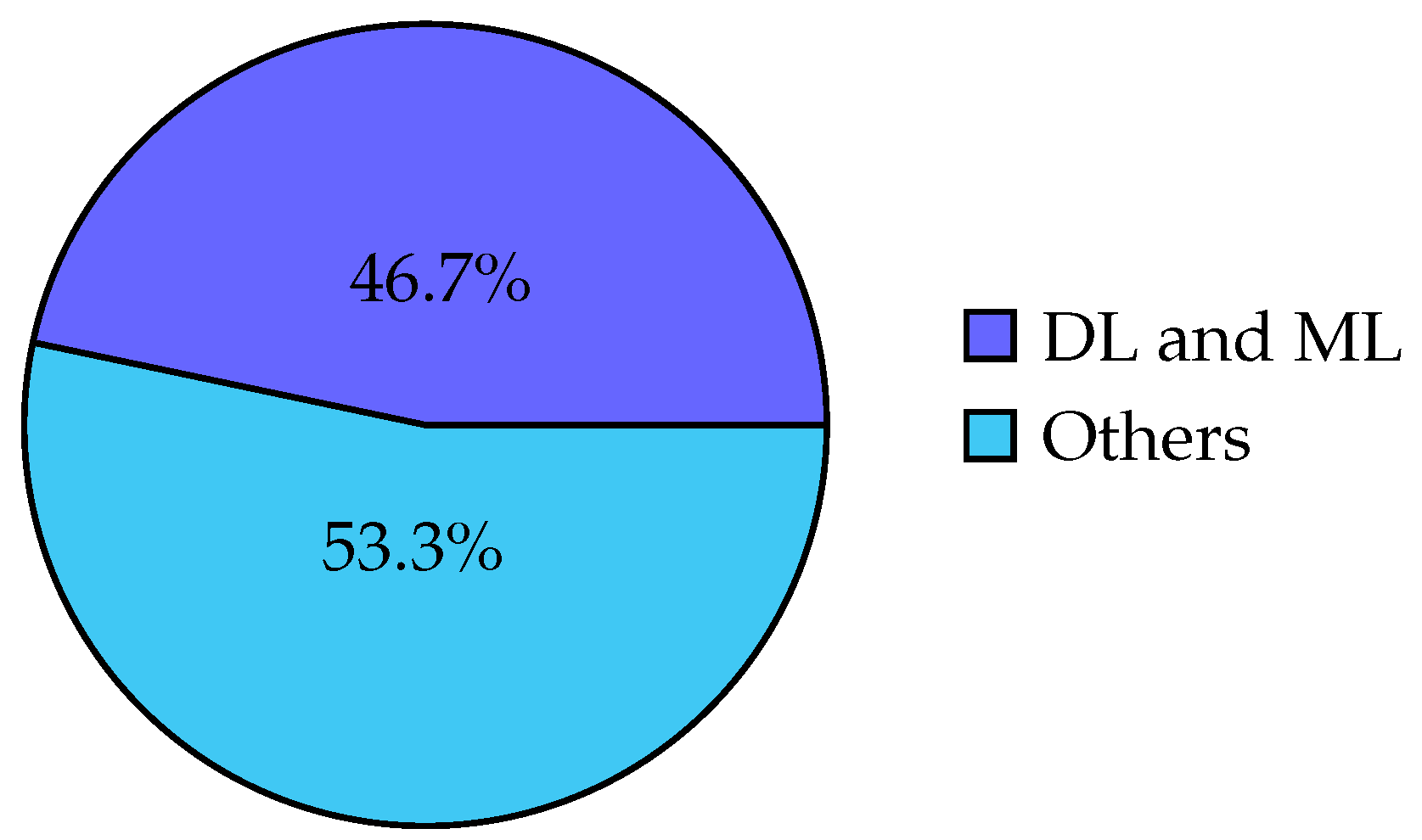
III. Results
IV. Discussion
V. Conclusion
References
- K. Lin, Y. Huang, J. C. Hung, and Y. Lin, “Feature Selection and Parameter Optimization of Support Vector Machines Based on Modified Cat Swarm Optimization,” International Journal of Distributed Sensor Networks, vol. 2015, pp. 1–12, 2015. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-84937795869&doi=10.1155%2f2015%2f365869&partnerID=40&md5=abdc025be22b2b260560caa788f162b7. [CrossRef]
- V. K. Kalimuthu and T. Muthu, “Oppositional Coyote Optimization based Feature Selection with Deep Learning Model for Intrusion Detection in Fog-Assisted Wireless Sensor Network,” Acta Montanistica Slovaca, vol. 28, no. 2, pp. 18, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85172330570&doi=10.46544%2fAMS.v28i2.18&partnerID=40&md5=7096ffeff5a8701c96ee79ba0a614a38. [CrossRef]
- M. M. Asiri, H. G. Mohamed, M. K. Nour, M. Al Duhayyim, A. S. A. Aziz, A. Motwakel, A. S. Zamani, and M. I. Eldesouki, “Hybrid Metaheuristics Feature Selection with Stacked Deep Learning-Enabled Cyber-Attack Detection Model,” Computer Systems Science and Engineering, vol. 2023, pp. 1063, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85143821389&doi=10.32604%2fcsse.2023.031063&partnerID=40&md5=fb53ed5466a33e587e44b071e938de4c. [CrossRef]
- F. S. Alrayes, N. Alshuqayran, M. K. Nour, M. Al Duhayyim, A. Mohamed, A. A. Abdelmageed, G. P. Mohammed, and I. Yaseen, “Optimal Fuzzy Logic Enabled Intrusion Detection for Secure IoT-Cloud Environment,” Computers, Materials and Continua, vol. 2023, pp. 32591, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85145355981&doi=10.32604%2fcmc.2023.032591&partnerID=40&md5=5c902b58ca674a756f39a84093031493.
- L. A. Maghrabi, I. R. Alzahrani, D. Alsalman, Z. M. AlKubaisy, D. Hamed, and M. Ragab, “Golden Jackal Optimization with a Deep Learning-Based Cybersecurity Solution in Industrial Internet of Things Systems,” Electronics (Switzerland), vol. 12, no. 19, pp. 4091, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85175031076&doi=10.3390%2felectronics12194091&partnerID=40&md5=5523d8b7df5431ffd977effe27e8e853. [CrossRef]
- I. Katib and M. Ragab, “Blockchain-Assisted Hybrid Harris Hawks Optimization Based Deep DDoS Attack Detection in the IoT Environment,” Mathematics, vol. 11, no. 8, pp. 1887, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85153970460&doi=10.3390%2fmath11081887&partnerID=40&md5=17b0419e37e9c355cd810487b90dafba. [CrossRef]
- M. A. Elaziz, A. Dahou, A. Mabrouk, R. A. Ibrahim, and A. O. Aseeri, “Medical Image Classifications for 6G IoT-Enabled Smart Health Systems,” Diagnostics, vol. 13, no. 5, pp. 834, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85149724139&doi=10.3390%2fdiagnostics13050834&partnerID=40&md5=946b4811b98e437ef033eaa2e6915c28.
- M. Ragab, S. M. Alshammari, A. S. Al-Malaise Al-Ghamdi, A. S. Althaqafi, and A. S. AL-Ghamdi, “Modified Metaheuristics with Weighted Majority Voting Ensemble Deep Learning Model for Intrusion Detection System,” Computer Systems Science and Engineering, vol. 2023, pp. 1446, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85169697448&doi=10.32604%2fcsse.2023.041446&partnerID=40&md5=2dd55e57b65d3a1ee392a328b2b52f6e. [CrossRef]
- F. Alrowais, M. M. Eltahir, S. S. Aljameel, R. Marzouk, G. P. Mohammed, and A. S. Salama, “Modeling of Botnet Detection Using Chaotic Binary Pelican Optimization Algorithm With Deep Learning on Internet of Things Environment,” IEEE Access, vol. 2023, pp. 332690, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85177087408&doi=10.1109%2fACCESS.2023.3332690&partnerID=40&md5=32280eacafcc3323592f40368572d61b. [CrossRef]
- F. Y. Assiri and M. Ragab, “Optimal Deep-Learning-Based Cyberattack Detection in a Blockchain-Assisted IoT Environment,” Mathematics, vol. 11, no. 19, pp. 4080, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85176427308&doi=10.3390%2fmath11194080&partnerID=40&md5=84c30467750400a36d49a05ccf606ad4. [CrossRef]
- A. Fatani, M. Abd Elaziz, A. Dahou, M. A. A. Al-Qaness, S. Ali Lu, S. A. Alfadhli, and S. S. Alresheedi, “IoT Intrusion Detection System Using Deep Learning and Enhanced Transient Search Optimization,” IEEE Access, vol. 9, pp. 3109081, 2021. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85115210347&doi=10.1109%2fACCESS.2021.3109081&partnerID=40&md5=730b07e02f079f93617caacc76c9c596. [CrossRef]
- T. Muthu and V. K. Kalimuthu, “Seagull Optimization-based Feature Selection with Optimal Extreme Learning Machine for Intrusion Detection in Fog Assisted WSN,” Tehnicki Vjesnik, vol. 28, pp. 95, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85171470095&doi=10.17559%2fTV-20230130000295&partnerID=40&md5=e3a0e83031794e5e9a77fbb74260fd88. [CrossRef]
- M. A. Alohali, M. Eltahir, F. N. Al-Wesabi, M. Al Duhayyim, A. M. Mustafa Hilal, and A. Motwakel, “Optimal Deep Learning Based Ransomware Detection and Classification in the Internet of Things Environment,” Computer Systems Science and Engineering, vol. 2023, pp. 6802, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85158821150&doi=10.32604%2fcsse.2023.036802&partnerID=40&md5=e6d4492e1375adb99a17c0637bd8cda6. [CrossRef]
- L. Almuqren, H. Alqahtani, S. S. Aljameel, A. S. Salama, I. Yaseen, and A. A. Alneil, “Hybrid Metaheuristics With Machine Learning Based Botnet Detection in Cloud Assisted Internet of Things Environment,” IEEE Access, vol. 11, pp. 32369, 2023. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85174800426&doi=10.1109%2fACCESS.2023.3322369&partnerID=40&md5=6b8455b493bd4b722bcc7875f009ce64. [CrossRef]
- S. A. Althubiti, J. Escorcia-Gutierrez, M. Gamarra, R. Soto-Diaz, R. F. Mansour, F. Alenezi, “Improved Metaheuristics with Machine Learning Enabled Medical Decision Support System,” Computers, Materials and Continua, vol. 2022, pp. 28878, 2022. [Online]. Available: https://www.scopus.com/inward/record.uri?eid=2-s2.0-85132345851&doi=10.32604%2fcmc.2022.028878&partnerID=40&md5=f64133bdbb5bebd57e6fffc95df96844. [CrossRef]
| Study | Metaheuristics | Application in IoT | Key Results or Contributions |
|---|---|---|---|
| Lin et al. (2015) | Cat Swarm Optimization (CSO) | SVM Optimization in Sensor Networks | Improving SVM Accuracy |
| Kalimuthu et al. (2023) | Coyote Optimization | Intrusion Detection in Sensor Networks | Improving Detection Rate |
| Asiri et al. (2023) | Hybrid + Deep Learning | Cyber Attack Detection | High Detection Accuracy |
| Alrayes et al. (2023) | Fuzzy Logic + Metaheuristics | Intrusion Detection in IoT-Cloud | Improved Performance in IoT Environments |
| Maghrabi et al. (2023) | Golden Jackal Optimization | Security in IoT Industrial Systems | High Effectiveness in Threat Detection |
| Katib et al. (2023) | Harris Hawks Optimization | DDoS Attack Detection | Reducing DDoS Attacks |
| Elaziz et al. (2023) | Deep Learning + Optimization | IoT Medical Image Classification | Improved Diagnostic Accuracy |
| Ragab et al. (2023) | Metaheuristics + Voting | Intrusion Detection | Increased Efficiency and Accuracy |
| Alrowais et al. (2023) | Pelican Optimization + Deep Learning | Botnet Detection in IoT | High Botnet Detection Rate |
| Assiri & Ragab (2023) | Deep Learning + Blockchain | Cyberattack Detection in IoT | Efficiency in IoT Security |
| Fatani et al. (2021) | Transient Search Optimization | IoT Intrusion Detection | Improved Accuracy Performance |
| Muthu et al. (2023) | Seagull Optimization | Intrusion Detection in WSN | Increased Accuracy |
| Alohali et al. (2023) | Deep Learning + Optimization | Ransomware Detection in IoT | Increased Ransomware Effectiveness |
| Almuqren et al. (2023) | Metaheuristics + Machine Learning | Botnet Detection in IoT | Improved Real-Time Detection |
| Althubiti et al. (2022) | Metaheuristics + Machine Learning | IoT Medical Support System | High Accuracy in Diagnosis |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





