I. Introduction
The cybersecurity landscape is constantly evolving, with cyber threats becoming increasingly serious and frequent. According to recent statistics, the global cost of cybercrime is projected to exceed $20 trillion by 2026. This exponential rise in cybercrime has far-reaching consequences, not only in terms of financial losses but also in terms of the potential disruption to critical infrastructure and compromise of sensitive information. A report submitted highlights that more cyber-attacks are expected by the fall of 2020.
In addition, cybercriminals are constantly evolving their tactics, utilizing advanced techniques to bypass security measures and gain unauthorized access to valuable data. As a result, organizations in both the public and private sectors are faced with the daunting challenge of safeguarding their digital assets and maintaining cybersecurity in an increasingly connected and digitized world [
1]. The importance of cybersecurity cannot be underestimated, as cyber-attacks have the potential to cause significant institutional, financial, and reputational damage.
Moreover, the emergence of new technologies such as artificial intelligence, quantum computing, digital currencies, blockchain, big data, and the Internet of Things has further amplified the complexity of cybersecurity. These advancements bring numerous advantages to our lives and socio-political relations, but they also introduce new risks and vulnerabilities. There is an urgent need for organizations to adopt a proactive and holistic approach towards cybersecurity, taking into account not only the technical aspects but also the human and ethical dimensions. In this paper, we aim to provide insights and recommendations for adapting to the evolution of cyber threats in the coming years, specifically focusing on the year 2024 and beyond. To achieve this, we will analyze current trends and insights from reputable sources such as. The proliferation of cyber threats presents an ongoing challenge for CISOs around the world, especially as organizations continue to embrace digital transformation and remote work strategies.
II. AI and Machine Learning in Cybersecurity: A Dynamic Force for Defense
The relentless innovation of cybercriminals necessitates equally sophisticated security solutions. Artificial Intelligence (AI) and Machine Learning (ML) are rapidly transforming cybersecurity, offering a dynamic force to combat advanced attacks and safeguard sensitive data. This report delves into the expanding role of AI and ML in cybersecurity, highlighting three crucial subtopics that are shaping the future of this critical field.
Firstly, AI-driven threat detection systems are revolutionizing how organizations identify and respond to cyber threats in real-time. These systems can analyze vast amounts of data, detect anomalies, and predict potential security breaches with unprecedented accuracy, allowing for proactive defense strategies.
Secondly, ML algorithms are enhancing the efficacy of security measures by continuously learning from new data and adapting to evolving threats. By leveraging ML, cybersecurity solutions can autonomously detect and mitigate emerging risks, reducing the reliance on manual intervention and improving overall response times.
Thirdly, AI-powered behavioral analytics provide insights into user behaviors and network activities, enabling organizations to detect insider threats and unauthorized access more effectively. By analyzing patterns and anomalies in user behavior, AI algorithms can identify suspicious activities and prevent potential breaches before they occur.
Furthermore, the convergence of AI and ML with other cutting-edge technologies such as big data analytics and blockchain is amplifying their impact on cybersecurity, creating a multifaceted defense ecosystem capable of addressing the most sophisticated cyber threats.
In conclusion, the integration of AI and ML technologies into cybersecurity operations is essential for staying ahead in the ongoing battle against cybercrime. By harnessing the power of these advanced technologies, organizations can fortify their defenses, mitigate risks, and safeguard their digital assets in an increasingly hostile cyber landscape. Enhanced Threat Detection and Response
Traditional security methods often fall behind cyber threats. Here, AI and ML excel. These algorithms can analyze massive network data in real time to find anomalies and suspicious patterns that may indicate an attack. This lets security teams detect threats faster and respond better, reducing damage and downtime. Imagine a sophisticated malware attack on your system. Traditional methods may miss subtle network traffic changes. However, an AI-powered security system can detect these deviations and respond immediately, possibly stopping the attack. [
2]
A. Streamlined Security Operations
Traditional security systems generate a lot of alerts and events, overwhelming security teams. Alert fatigue and missed critical threats can result from information overload. Many mundane security tasks can be automated with AI and ML. These algorithms can analyze logs, prioritize incidents, and scan vulnerabilities through massive data sets. Security professionals can focus on strategic initiatives and complex investigations with more time. Imagine a security analyst spending hours reviewing unlimited alerts. They can delegate these tasks to AI-powered automation and focus on investigating breaches and developing long-term security strategies.
B. Proactive Threat Hunting
AI and ML go beyond just reacting to threats; they can actively hunt for them within a network. By analyzing network traffic and user behavior for deviations from established baselines, AI can identify potential threats before they escalate into major incidents. This proactive approach significantly enhances an organization's overall security posture. Imagine a scenario where a hacker attempts to gain unauthorized access to a system by exploiting a zero-day vulnerability (a previously unknown flaw). Traditional security measures might not detect this attack. However, an AI-powered system, constantly analyzing user behavior, can identify unusual activity and trigger an investigation, potentially thwarting the attack before any damage occurs. [
2]
III. Zero-Trust Architectures: Redefining Network Security
Zero-trust architectures (ZTAs) are designed to address the limitations of perimeter-based security by assuming that threats could exist both inside and outside the network. This approach advocates for continuous authentication and authorization processes, ensuring that access to resources is granted on a need-to-know and least-privilege basis. By implementing robust identity and access management (IAM) solutions, organizations can enforce strict controls over user permissions and prevent unauthorized access to sensitive data.
Furthermore, ZTAs leverage network segmentation and micro-segmentation to compartmentalize resources and limit the lateral movement of attackers within the network. This granular approach enhances visibility and control, allowing security teams to detect and respond to threats more effectively. Additionally, the adoption of encryption and cryptographic techniques ensures data confidentiality and integrity, even in the event of a breach.
Moreover, ZTAs promote the adoption of continuous monitoring and analytics tools to detect anomalous behavior and potential security incidents in real-time. By leveraging machine learning and artificial intelligence, organizations can proactively identify emerging threats and take timely remedial actions to mitigate risks.
In conclusion, zero-trust architectures represent a fundamental shift in the way organizations approach network security. By embracing the principles of least privilege, continuous authentication, and strict access controls, businesses can enhance their cybersecurity posture and mitigate the evolving threat landscape effectively. As technology continues to advance, the adoption of ZTAs will be crucial for safeguarding critical assets and ensuring the resilience of digital infrastructure.
A. Micro-Segmentation and Least Privilege Access
Traditional network architectures provide broad access to resources once inside the perimeter. ZTAs address this vulnerability by segmenting the network into smaller, more secure zones. This "micro-segmentation" restricts lateral movement, limiting the damage a potential attacker can inflict even if they breach a specific zone. Additionally, ZTAs enforce the principle of "least privilege access," granting users and devices only the minimum permissions required to perform their tasks. This minimizes the potential impact of compromised credentials. [
3]
B. Continuous Monitoring and Identity Verification
ZTAs move beyond static perimeter defenses. They continuously monitor user activity, device health, and network traffic for anomalies. Advanced analytics and identity verification tools are employed to constantly assess trust and access requests. Multi-factor authentication (MFA) is a cornerstone of this continuous verification, adding an extra layer of security beyond passwords. Imagine a scenario where a compromised laptop is used to access the network. In a traditional system, this might go unnoticed. However, a ZTA's continuous monitoring would detect the unusual activity and potentially block access before any damage is done.
C. Zero Trust Network Access (ZTNA) for the Cloud
The rise of cloud computing and remote workforces necessitates secure access to applications and data residing outside the traditional network perimeter. ZTNA, a core component of ZTAs, addresses this challenge. It acts as a secure gateway, authenticating users and devices before granting access to specific resources, regardless of their location. This ensures that only authorized users can access sensitive information, even when working from outside the office. Imagine a company with employees working remotely across the globe. ZTNA allows them to securely access cloud-based applications without compromising network security. [
4]
IV. Integration of Cybersecurity and Business Strategy: A Collaborative Approach
Cybersecurity is no longer an afterthought; it's a fundamental component of successful business strategy. In today's digital world, cyber threats pose significant risks to an organization's reputation, financial stability, and overall operations. This report explores the critical need for integrating cybersecurity with business strategy, highlighting three key aspects of this collaborative approach.
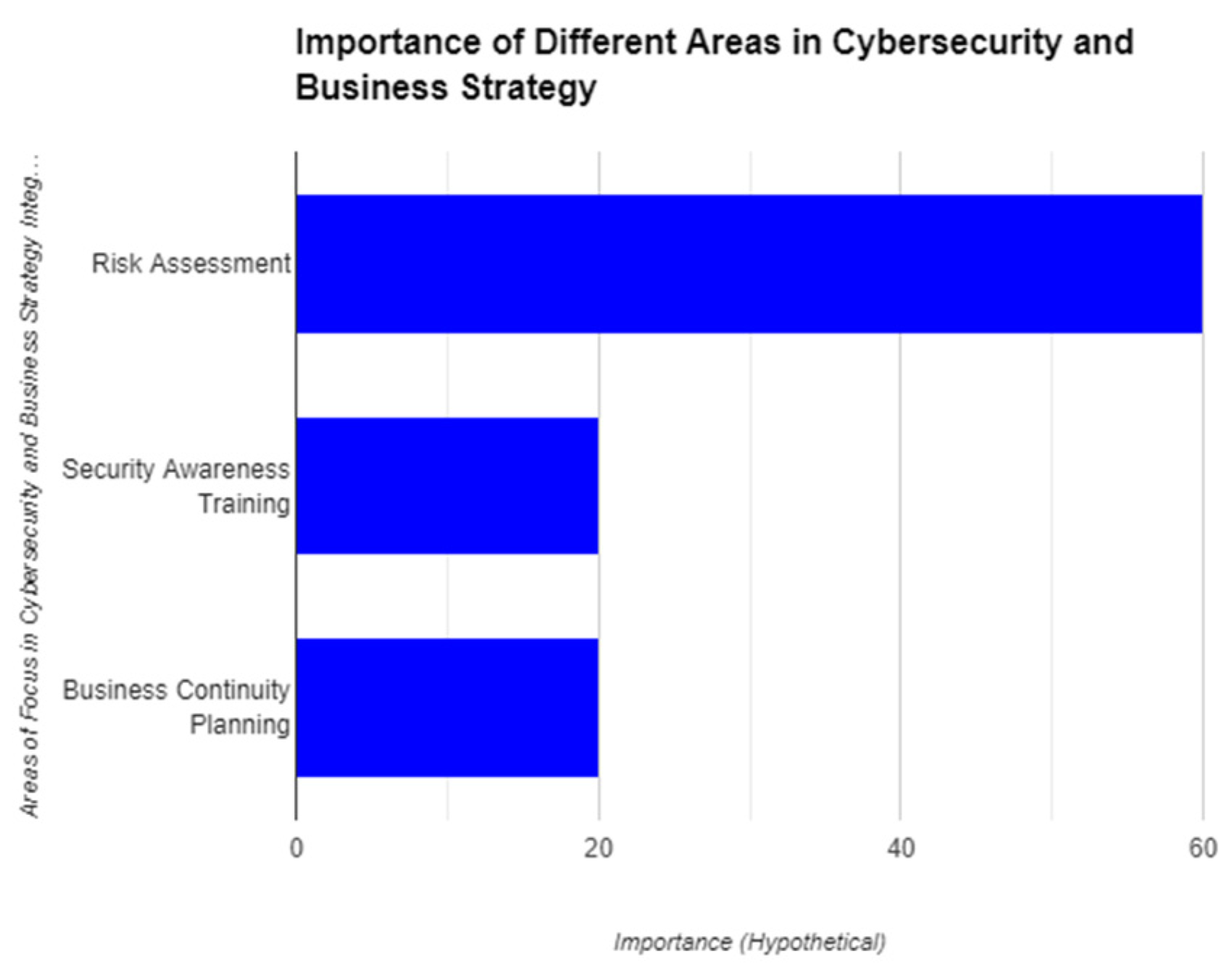
Figure 1.
Importance of Different Ares In Cybersecurity and Business Strategy.
Figure 1.
Importance of Different Ares In Cybersecurity and Business Strategy.
A. Risk Assessment and Alignment
The first step in integrating cybersecurity is understanding the organization's risk landscape. A comprehensive risk assessment identifies potential threats, vulnerabilities, and the impact they could have on critical assets and business goals. By aligning cybersecurity efforts with overall business objectives, organizations can prioritize investments and implement controls that address the most significant risks. Imagine a company focused on innovation, heavily reliant on intellectual property. Their risk assessment might reveal a vulnerability in their product development platform. By aligning cybersecurity with business strategy, the company can prioritize resources to address this vulnerability, protecting its competitive edge.
B. Security Culture and Awareness
Building a strong security culture is essential for effective integration. This involves fostering a shared responsibility for cybersecurity across all levels of the organization. By implementing regular security awareness training programs and promoting a culture of vigilance, employees become a vital line of defense against cyber threats. Imagine a scenario where an employee receives a phishing email. In a company with a strong security culture, the employee would be equipped to identify and report suspicious emails, preventing a potential cyberattack. [
5]
C. Business Continuity and Disaster Recovery Planning
Even with the best security measures in place, cyberattacks can happen. Integrating cybersecurity with business strategy requires robust continuity and disaster recovery plans. These plans outline the steps needed to recover from a cyberattack with minimal disruption to business operations. By having these plans in place, organizations can minimize downtime, financial losses, and reputational damage in the event of a security breach. Imagine a company experiencing a ransomware attack. A well-defined disaster recovery plan would allow them to quickly restore critical systems and data, minimizing the impact on business operations. [
6]
In addition to recovery plans, proactive measures such as regular backups of critical data, employee training on cybersecurity best practices, and implementing multi-factor authentication can help mitigate the risk of cyberattacks. Collaborative efforts between IT security teams and other departments within the organization are crucial for ensuring the effectiveness of these measures. Furthermore, conducting regular cybersecurity audits and assessments can help identify vulnerabilities and areas for improvement in the existing security infrastructure.
Moreover, establishing clear communication protocols and designated response teams can streamline incident response efforts during a cyber crisis. This ensures swift action and coordination across all levels of the organization, minimizing confusion and delays in implementing remediation strategies. Additionally, fostering a culture of cybersecurity awareness and accountability among employees can serve as a frontline defense against cyber threats, empowering individuals to recognize and report suspicious activities promptly.
V. Cyber Resilience: Building Bouncing Back Better
The digital age presents a double-edged sword for organizations. While technology fuels innovation and growth, it also exposes them to a constantly evolving landscape of cyber threats. Cyber resilience is no longer a luxury; it's a critical capability for thriving in today's environment. This report explores the concept of cyber resilience and highlights three key subtopics that build an organization's ability to withstand and recover from cyberattacks.
A. Proactive Threat Detection and Response
The foundation of cyber resilience lies in proactive threat detection and response. This involves implementing robust security measures that go beyond basic perimeter defense. Security teams leverage threat intelligence, vulnerability scanning tools, and advanced analytics to identify and address potential threats before they escalate into major incidents. Imagine a scenario where a sophisticated malware campaign attempts to infiltrate an organization's network. Proactive cyber resilience measures would detect malicious activity early on, allowing security teams to take swift action and prevent widespread damage. [
7]
B. Incident Response Planning and Recovery
Cyberattacks are a reality, so being prepared for them is crucial. A well-defined incident response plan outlines the steps to take in the event of a security breach. This includes procedures for containment, eradication, and recovery. By having a plan in place and regularly rehearsing it, organizations can minimize downtime, data loss, and reputational damage. Imagine a company experiencing a ransomware attack. An effective incident response plan would outline clear actions for isolating the affected systems, restoring data from backups, and communicating with stakeholders. This swift response would minimize disruption and expedite recovery. [
8]
C. Business Continuity and Operational Resilience
Cyber resilience goes beyond technical measures. It requires building operational resilience across the organization. This involves ensuring critical business functions can continue despite a cyberattack. This might involve implementing redundancy in critical systems, diversifying suppliers, and establishing alternative communication channels. Imagine a company with a geographically dispersed workforce. Operational resilience measures, like cloud-based backups and remote access solutions, ensure business continuity even if a cyberattack disrupts on-site operations at a specific location. [
9]
VII. The Increasing Importance of Data Privacy: A Growing Concern in the Digital Age
As our lives become increasingly intertwined with the digital world, the personal information we share online holds ever-greater value. This data can be used for a variety of purposes, from targeted advertising to identity theft. This report explores the growing importance of data privacy, highlighting three key factors driving this concern.
A. The Rise of the Data Economy
The digital age has ushered in a data economy where personal information is a valuable commodity. Companies collect vast amounts of data on our online behavior, preferences, and even physical movements. This data is used to personalize advertising, develop targeted marketing campaigns, and even influence our purchasing decisions. While some data collection offers convenience, the lack of transparency and control over how this information is used raises significant privacy concerns. Imagine a scenario where a seemingly innocuous fitness tracker app collects your location data and sells it to advertisers. This raises questions about user consent and the potential misuse of personal information. [
13]
B. Evolving Data Privacy Regulations
The worldwide nature of data flows is a significant issue that makes compliance activities more difficult since it requires businesses to make sure that various regulatory frameworks in various jurisdictions are followed. Furthermore, additional complexity is introduced by the quick speed of technological innovation, necessitating ongoing compliance strategy modification. Furthermore, the significance of giving data privacy efforts top priority within enterprises is highlighted by the possibility of severe fines and harm to one's reputation in the event of non-compliance. In an increasingly regulated environment, organizations need to invest in strong data governance policies to preserve compliance and trust, as data privacy remains a top concern for both customers and authorities [
14].
C. Heightened Awareness of Data Breaches
Massive data breaches have become common, exposing millions of people's data. These incidents can cause identity theft, financial fraud, and reputational harm. Public awareness of these risks has increased data privacy concerns and demand stronger protections. Data security and responsible data handling are more likely to build consumer trust in this changing landscape. Imagine a credit card data breach at a company. This can cost customers money and damage the company's reputation. [
15]
VIII. The Rise Zero-Trust Architectures: Redefining Network Security
Zero-trust architectures (ZTAs) are more than just a response to existing security issues; they recognize the changing nature of technology and the sophistication of cyberattacks. By understanding that attacks might come from both internal and external sources, ZTAs encourage a proactive and adaptive security posture, which is critical in today's interconnected world.
Furthermore, the use of ZTAs is not limited to major corporations or organizations with significant IT resources. Small and medium-sized enterprises can also benefit from adopting zero-trust principles to protect their digital assets from increasingly sophisticated cyber threats.
Overall, the transition to zero-trust systems marks a fundamental shift in how enterprises approach cybersecurity. Businesses that prioritize continuous authentication, strong access restrictions, and complete visibility can better fight against a wide range of cyber-attacks and protect their vital assets in an ever-changing threat landscape.
A. Micro-segmentation and Least Privilege Access
Traditional network architectures provide broad access to resources once inside the perimeter. ZTAs address this vulnerability by segmenting the network into smaller, more secure zones. This "micro-segmentation" restricts lateral movement, limiting the damage a potential attacker can inflict even if they breach a specific zone. Additionally, ZTAs enforce the principle of "least privilege access," granting users and devices only the minimum permissions required to perform their tasks. This minimizes the potential impact of compromised credentials. [
16]
B. Continuous Monitoring and Identity Verification
ZTAs move beyond static perimeter defenses. They continuously monitor user activity, device health, and network traffic for anomalies. Advanced analytics and identity verification tools are employed to constantly assess trust and access requests. Multi-factor authentication (MFA) is a cornerstone of this continuous verification, adding an extra layer of security beyond passwords. Imagine a scenario where a compromised laptop is used to access the network. In a traditional system, this might go unnoticed. However, a ZTA's continuous monitoring would detect the unusual activity and potentially block access before any damage is done. [
17]
C. Zero Trust Network Access (ZTNA) for the Cloud:
The rise of cloud computing and remote workforces necessitates secure access to applications and data residing outside the traditional network perimeter. ZTNA, a core component of ZTAs, addresses this challenge. It acts as a secure gateway, authenticating users and devices before granting access to specific resources, regardless of their location. This ensures that only authorized users can access sensitive information, even when working from outside the office. Imagine a company with employees working remotely across the globe. ZTNA allows them to securely access cloud-based applications without compromising network security.
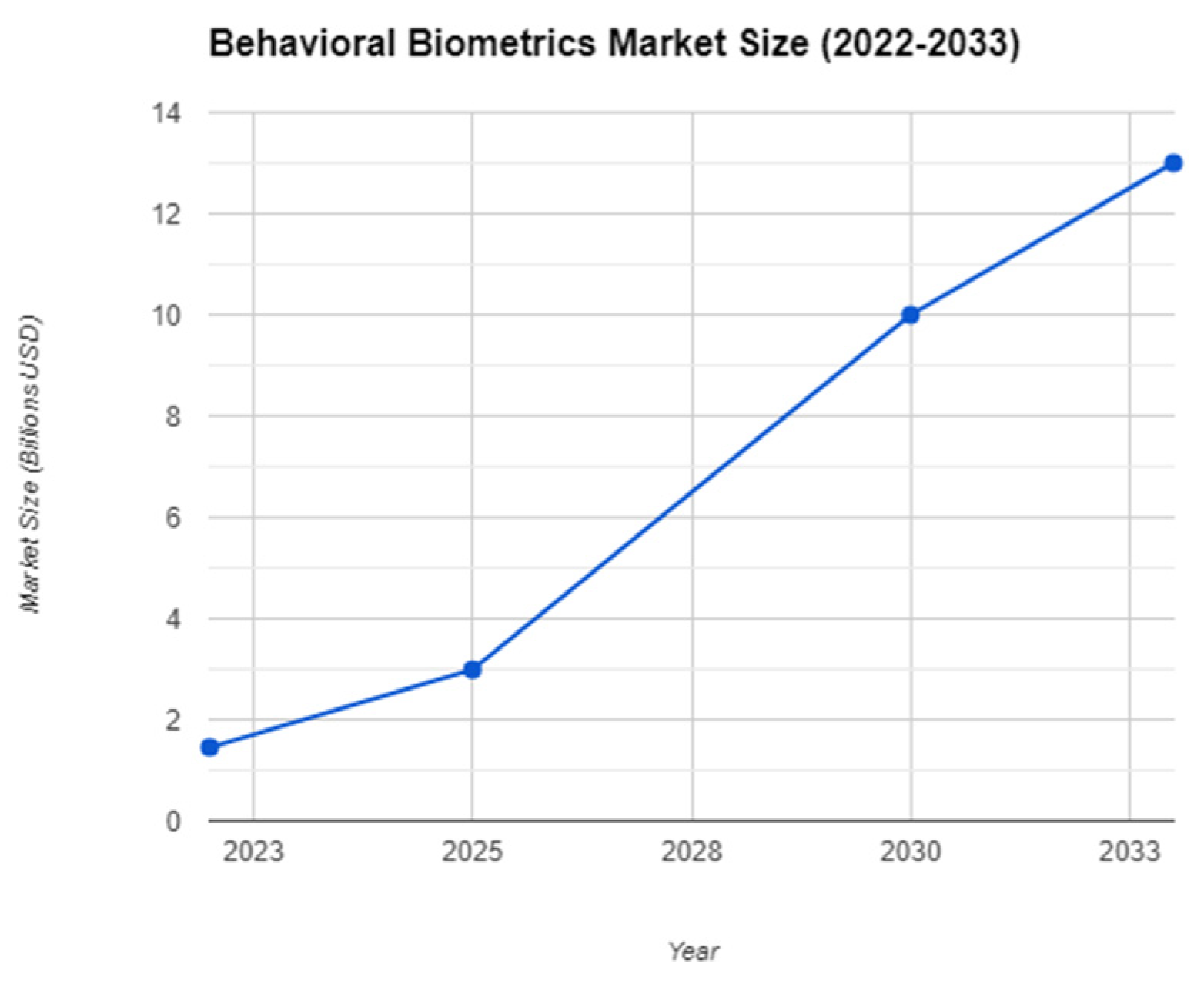
XI. Behavioral Biometrics
Behavioral biometrics offer an additional layer of security by analyzing unique patterns in typing rhythm, mouse movements, touchscreen gestures, and even speech characteristics. This dynamic approach enhances authentication accuracy and resilience against impersonation or fraud attempts. Furthermore, behavioral biometrics can adapt to changes in user behavior over time, providing a robust and frictionless authentication experience while maintaining security integrity. As organizations increasingly prioritize user experience without compromising security, behavioral biometrics are emerging as a valuable solution for authentication and fraud prevention across various industries.
Figure 3.
Behavioral Biometrics Market Size.
Figure 3.
Behavioral Biometrics Market Size.
Behavioral biometrics can be further broken down into several subcategories, each focusing on a specific aspect of user interaction.
Typing Dynamics: Analyzes how a user types, including typing speed, rhythm, pressure, and dwell time on keys.
Mouse Dynamics: Analyzes how a user interacts with a mouse, including movement patterns, click speed, and scrolling behavior.
Touch Dynamics: Analyzes how a user interacts with a touchscreen device, including swipe patterns, tap pressure, and dwell time on specific areas.
Gait Analysis: Analyzes a user's walking pattern, often used in conjunction with other forms of biometrics for high-security applications.
Cognitive Biometrics: Analyzes a user's cognitive responses during interaction, such as reaction time to stimuli or patterns in mouse movement during decision-making tasks.
Voice Recognition: Analyzes the unique characteristics of a user's voice, including pitch, tone, accent, and speech patterns, to authenticate their identity in voice-based interactions.
Signature Dynamics: Analyzes the individual nuances in a user's signature, including pen pressure, stroke order, and overall handwriting style, to verify their identity in digital signature applications.
Facial Dynamics: Analyzes subtle facial movements and expressions, such as micro-expressions and blinking patterns, to authenticate users in facial recognition systems and detect spoofing attempts.
X. Conclusion
In 2024, cybersecurity will face both opportunities and difficulties. The amalgamation of Artificial Intelligence (AI) and Machine Learning (ML) provides enterprises with unparalleled speed and precision in proactive threat identification and response capabilities. Protecting sensitive data and user privacy is crucial, as seen by laws like the CCPA and GDPR and growing data privacy concerns.
Supply chain security is becoming a top priority, necessitating extensive precautions against sophisticated threats. To fortify their defenses, businesses are putting supply chain audits, vendor risk management plans, and improved due diligence processes into place. To protect data integrity and secrecy, quantum-resistant cryptography must be developed in light of the advent of quantum computing.
Computing has also brought forth benefits as well as challenges, necessitating the creation of cryptographic solutions that are resistant to quantum attacks to protect data integrity and secrecy.
Optimizing resource allocation and security operations requires cybersecurity automation and orchestration. Automation of threat detection, incident response, and vulnerability management can help organizations defend against cyberattacks.
To survive the ever-changing threat landscape, organizations need proactive cybersecurity. This includes strong policies, processes, and cybersecurity awareness. Researchers, industry experts, policymakers, and regulators must collaborate to address cyber risks.
The 2024 cybersecurity trends essentially highlight the necessity of ongoing innovation, watchfulness, and cooperation to keep ahead of changing threats and guarantee a safe and stable digital future.
References
- “Cyber Security Defense Policies: A Proposed Guidelines for Organization’s Cyber Security Practices”, International Journal of Advanced Computer Science and Applications. https://thesai.org/Publications/ViewPaper?Volume=11&Issue=8&Code=IJACSA&SerialNo=17.
- A. S. Writer, “10 Ai ML in IT security trends to look out for in 2024,” AiThority, https://aithority.com/machine-learning/10-ai-ml-in-it-security-trends-to-look-out-for-in-2024 (accessed Apr. 22, 2024).
- “Using Darktrace for threat hunting: Darktrace Blog,” RSS, https://darktrace.com/blog/using-darktrace-for-threat-hunting (accessed Apr. 22, 2024).
- “Zero trust,” Palo Alto Networks, https://www.paloaltonetworks.com/zero-trust (accessed Apr. 22, 2024).
- “SSE & SASE | Converge Networking and Security”, Apr. 21, 2024. https://www.cloudflare.com/zero-trust/ (accessed Apr. 21, 2024).
- “Council Post: Why Cybersecurity Should Be Part Of Any Business Strategy”, Nov. 21, 2022. https://www.forbes.com/sites/forbestechcouncil/2022/11/21/why-cybersecurity-should-be-part-of-any-business-strategy/ (accessed Apr. 21, 2024).
- “The Competitive Edge: How Cybersecurity Integration Drives Business Success”. https://mackjacksonjr.medium.com/the-competitive-edge-how-cybersecurity-integration-drives-business-success-38d64d128484 (accessed Apr. 21, 2024).
- “cyber resiliency - Glossary | CSRC”, Apr. 21, 2024. https://csrc.nist.gov/glossary/term/cyber_resiliency (accessed Apr. 21, 2024).
- “What is Cyber Resilience?”, Apr. 21, 2024. https://blogs.opentext.com/cyber-resilience-definition/ (accessed Apr. 21, 2024).
- “What is Cyber Resilience?”. https://www.ibm.com/topics/cyber-resilience (accessed Apr. 21, 2024).
- “Deepfake”, Apr. 21, 2024. https://en.wikipedia.org/w/index.php?title=Deepfake&oldid=1219846632 (accessed Apr. 21, 2024).
- “Deep fakes | Synthesis AI | AI and machine learning”, Apr. 21, 2024. https://feedmagazine.tv/features/synthesia-ai/ (accessed Apr. 21, 2024).
- “EU turns to Big Tech to help deep fake-proof election”, Apr. 21, 2024. https://www.politico.eu/article/eu-big-tech-help-deepfake-proof-election-2024/ (accessed Apr. 21, 2024).
- “Markets & data”, Apr. 21, 2024. https://www.economist.com/markets-data (accessed Apr. 21, 2024).
- “General Data Protection Regulation (GDPR) Compliance Guidelines”, Apr. 21, 2024. https://gdpr.eu/ (accessed Apr. 21, 2024).
- “Help Center”. https://www.idtheftcenter.org/help-center/ (accessed Apr. 21, 2024).
- “Zero Trust”. https://www.paloaltonetworks.com/zero-trust (accessed Apr. 21, 2024).
- “Zero Trust Network Access (ZTNA)”. https://www.zscaler.com/capabilities/zero-trust-network-access (accessed Apr. 21, 2024).
- [PDF] A survey on machine learning techniques for cyber security in the last decade | semantic scholar, https://www.semanticscholar.org/paper/A-Survey-on-Machine-Learning-Techniques-for-Cyber-Shaukat-Luo/4c30d041c137948aa75e40912f14558234bf1ce2 (accessed Apr. 23, 2024).
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).