Submitted:
29 August 2024
Posted:
30 August 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Related Works
1.2. Contribution
2. Preliminaries
- samples x uniformly random from a set S.
- For a randomized algorithm A, denotes the output of A with input x and randomness r, while denotes the random output (with unspecified randomness).
- Min-entropy .
- A concatenating with B is represented by and also by (if the context is clear).
- negl is negligible: for any polynomial
- denotes set
- is the Euclidean norm:
- denotes the set of vector . We use to denote
2.1. Ring and Module
- -
- R-1. A is a commutative group under addition operator + with identity element 0.
- -
- R-2. A is associative under multiplication operator: for , (ab)c=a(bc). Also, it has a unit element 1: 1a=a.
- -
- R-3. It satisfies the distributive law: for , and
- 1.
- ;
- 2.
- 3.
- 4.
- , where is the multiplicative identity of R.
2.2. Elements in Quantum Computing
2.3. Multi-Signature
2.3.1. Security Model
- Correctness.For generated by KeyGen, the signature generated by signing algorithm on a message M will pass the verification, except for a negligible probability.
- Existential Unforgeability.For any quantum polynomial time adversary in the above forgery game, is negligible.
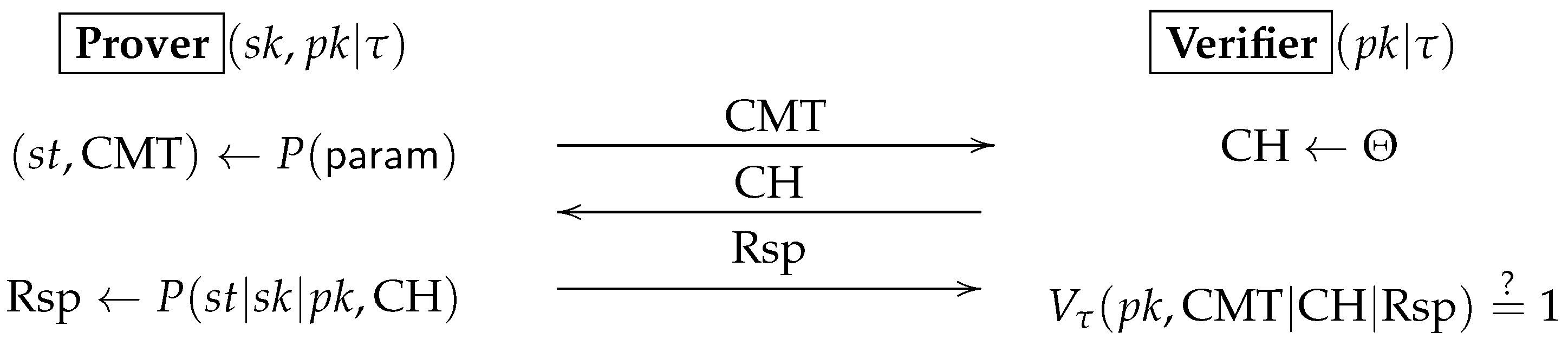
2.4. Canonical Linear Identification
- i.
- are -modules for some ring with (as a set);
- ii.
-
For any and public/private pairs (), we have that is a private key of .Note: Operator • between and (resp. ) might be different. But we will use the same symbol • as long as it is clear from the context.
- iii.
-
Let and for If is a faithfully generated transcript of the ID scheme w.r.t. , thenwhere and .Note: we require Equation (1) to hold only if the keys and transcripts are faithfully generated. If some are contributed by attacker, this equality might fail.
3. Basic Properties in Quantum Computing
- 1.
- ;
- 2.
- 3.
- 1.
- If , then
- 2.
- If and , then Especially, if , then
- 1.
- If A operates on while B operates on with D being a control register in the same basis for both A and B, then
- 2.
- If A is a projector on D in basis and B operates on with D being a control register in the same basis, then
4. Quantum Random Oracle
4.1. Standard Random Oracle
4.2. Compressed Random Oracle
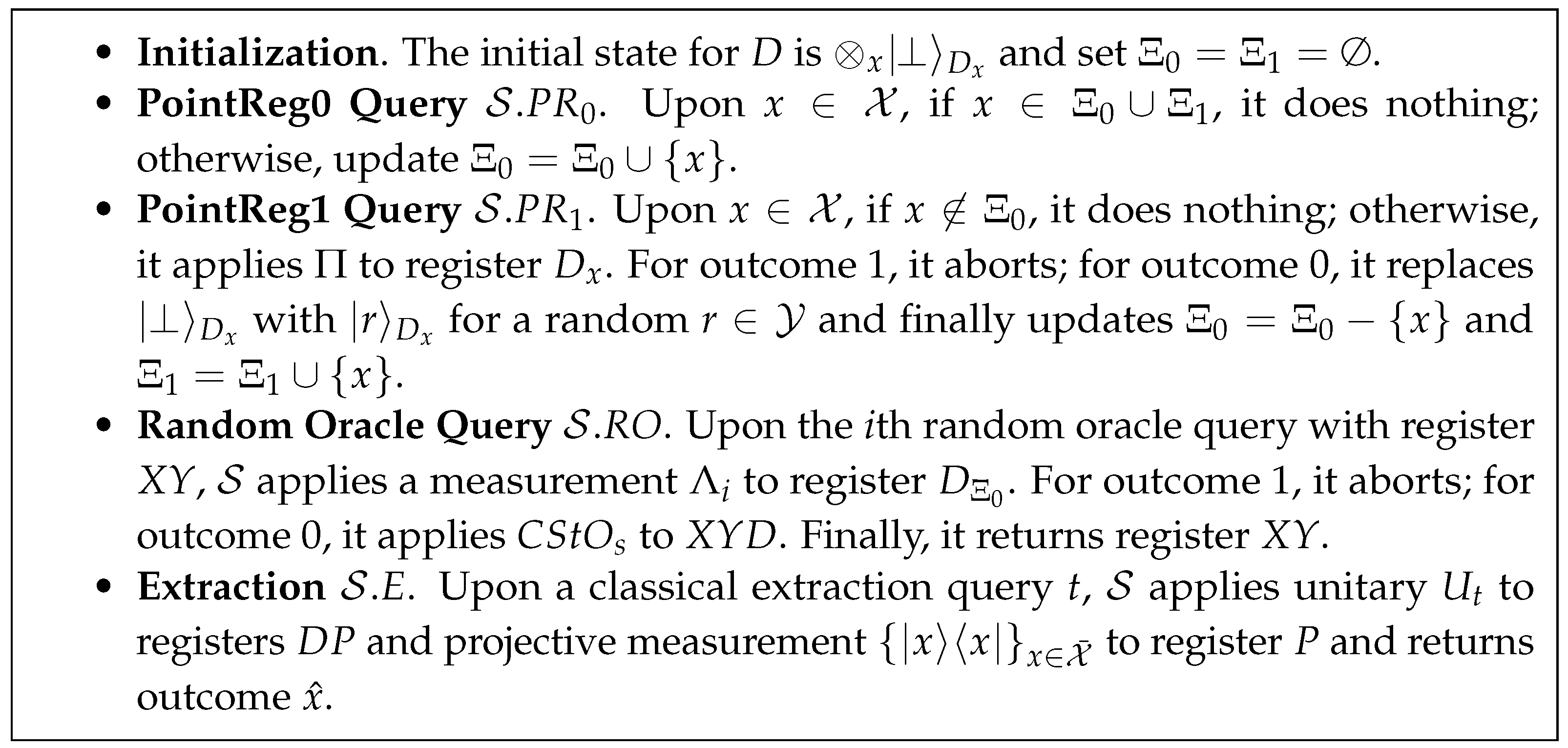
4.3. Compressed Random Oracle with Adaptive Special Points
- PointReg0 Query. One can send a new point to oracle. If , it does nothing; otherwise, the oracle updates
-
Random Oracle Query. One can issue a random oracle query by providing a query register X and a response register Y to oracle. If this is the ith random oracle query, the oracle applies a projective measurement in the computational basis to oracle register ( can be determined by i and some parameters that are determined before the oracle starts). If the outcome is 1, it aborts; otherwise, it applies to registers, whereFinally, it returns register .
- PointReg1 Query. One can send to oracle. If , it does nothing. Otherwise, it measures with , where . If the outcome is 1, it aborts; otherwise, it updates with for a random (this can be done as is now classic; or, we can apply unitary ). Finally, it updates and
- In the classic random oracle, a simulator can set the random oracle values of special queries to his own choices. In the , a special point will be first recorded in and later set to a planned value (when a PointReg1 query on this point is issued). We handle special points in two stages for technical reasons (See the remark after Theorem 5) only. Essentially, if we define the random oracle value of a special point early (e.g., at the time of adding into ), it could make the previously selected experiment change to a different one.
- is to formulate the selected experiment in Section 5 as a well-defined random oracle model. Especially, measurement in a random oracle query is to make sure the interaction with oracle follows the restriction of the selected experiment. If the measurement outcome is 1, it indicates that the game is not consistent with the selected experiment and hence it can stop now; otherwise, it continues. This randomly selected but consistent experiment can guarantee the adversary to have a good success probability, compared with the original game.
- In the classic random oracle, a simulator can pay attention to each query to make sure that each special point is not queried before it is set to the designated value. In the quantum setting, recording each query is difficult as one can query which indicates that every x is actually queried. To overcome this, we need to confirm that is not defined by measurement Π on . If measurement is successful, then will have now and non-⊥ components in the superposition are pruned and we can define the random oracle value for this x; if the measurement fails, we have no way to set the random oracle value for x and so abort.
4.4. Measurement
4.5. Bounding the Probability for Relation Search through Oracle Queries
4.6. Simulating with Extraction
4.6.1. Extraction at the End of Game
4.6.2. Extraction on the Fly
4.7. Efficient Encoding of and
5. Extracting Queries to that Witness the Future Adversarial Output
- right before the ith query, ; but after it, .
- after ith query and before the jth query, it remains that .
- after jth query and before the kth query,
- right after the kth query,
6. Quantum Security of the JAK Multi-Signature Framework
6.1. Review of JAK Mutli-Signature Framework
- R-1. Signer i takes and sends to all signers.
- R-2. Upon for all j (we don’t restrict for brevity), signer i sends to all signers.
- R-3. Upon , signer i checks if for all j. If no, it rejects; otherwise, it computes , and . Finally, it sends to all signers.
- Output. Upon , signer i computes , and outputs the aggregated public-key and multi-signature .
6.2. Security Theorem
- Whenever a random oracle query is issued, does as follows. Assume this is the ℓth random oracle query. If or , then (like challenger in ) will apply a projective measurement on X register in the computational basis and results in or and then it issues a PointReg0 query with each or to . If (for or 2), it issues a query with (which does measurement on like challenger in ). Then (no matter what is ℓ), recall that, in , the challenger will conduct a projective measurement (determined by ℓ and ) on D and another projective measurement (still determined by on D. These measurements are described in and can be seen that they are only applied on as desired by . These two measurements can be combined into one projective measurement in the computational basis on . Then, to be consistent with , in issues the random oracle query with its register to which will handle it first with measurement and then with (if it does not abort). Under this reformatting, the action on the joint state is the same as in .
- When issues a signing query so that contains , in computes , and normally as in , with possibly random oracle access to as in the previous item. Next, it issues query and then query both with x to , and finally a classic random oracle query with x (if it does not abort), where the random oracle queries are handled as the above reformatting. In turn, if does not abort, receives the reply and it continues normally as in to generate the signature. Note that together with acts the same as together with in . Thus, this does not change the view of and the joint quantum state.
7. Quantum Security of The JAK ID Scheme
- As a convention for lattice over ring, the security parameter is denoted by n (a power of 2);
- q is a prime with mod 8;
- ; ; is the set of invertible elements in ;
- A vector is implicitly a column vector and the ith component is or ;
- for a matrix or vector X, is its transpose;
- denotes the all-1 vector of dimension clear only in the specific context;
- for ,
- always uses the default representative with and similarly, for , each coefficient of u by default belongs to this range;
- is the Euler’s number;
- .
7.1. Ring-LWE and Ring-SIS
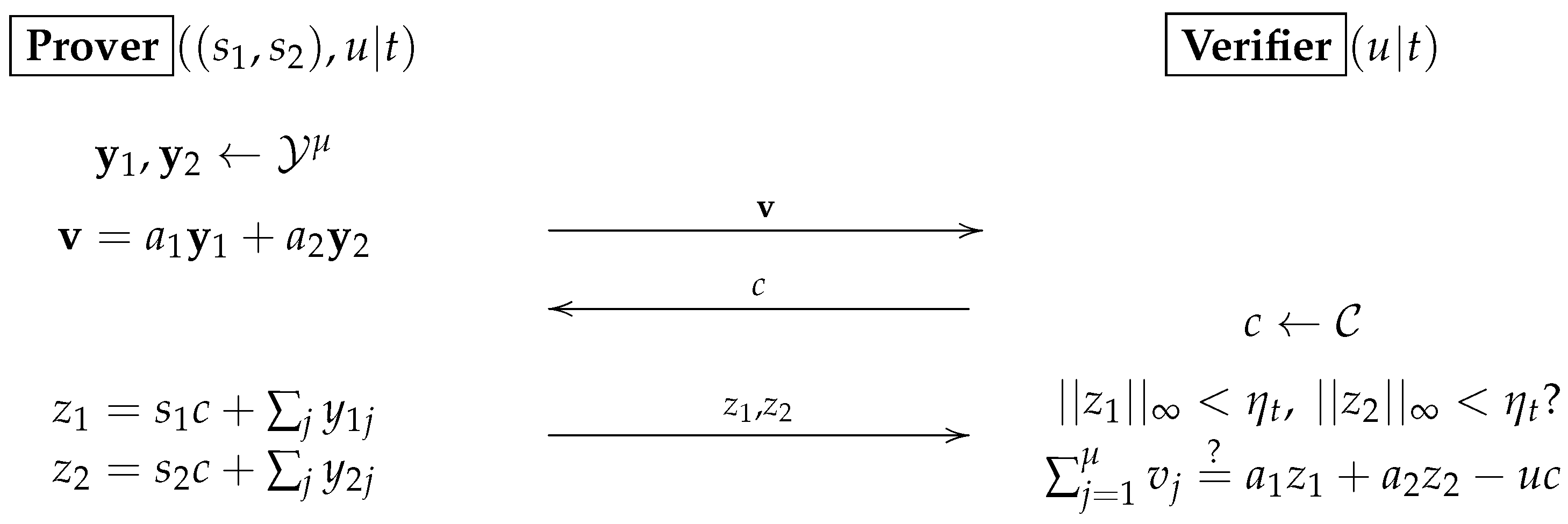
7.2. The JAK ID Scheme
- 1.
- Prover generates and computes and sends to Verifier, where
- 2.
- Receiver samples and sends it to Prover.
- 3.
- Upon c, Prover computes
- 4.
- Upon , Verifier checks if and for where and t is a positive integer (that represents the number of signers when converted to a signature scheme) and recall that (as a convention) is the ith component of . If all are valid, it accepts; otherwise, it rejects.
8. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Proof of Theorem 6
- Initially, is executed to generate a public-key for and and a private key for . has an initial state while has an initial state Let .
- The protocol proceeds in n rounds. In round , executes and sends it to . For , replies with a challenge . For , runs and outputs 0 (for reject) or 1 (for accept).
Appendix A.1. Collapsing Public-Coin Protocol
- Initially, Chal generates and gives it to .
- Then, (in the role of ) and Chal (in the role of ) executes the protocol except for round n. At round n, generates a quantum superposition (over the response ) which might be entangled with states in extra registers. He then provides to Chal.
- Upon , uses a measurement to check if in is a valid response for . If the verification fails, Chal aborts; otherwise, let be the superposition containing all the valid ’s. Then, flips a coin . If , it does nothing; otherwise, it measures in the computational basis. Finally, it sends the resulting superposition back to
- Finally, outputs a guess bit for b, which is also set as the output of the game.
Appendix A.2. Two Public-Coin Protocols from Our ID Scheme
Appendix A.2.1. Protocol Σ 1 .
- 1.
- A sends to challenger and holds a state , where .
- 2.
- Challenger sends to A.
- 3.
- A applies a unitary to and results in . It measures in the computational basis and sends it to challenger.
- 4.
- Challenger accepts if and for , where .
Appendix A.2.2. Protocol Σ 2 .
- 1.
- A sends to challenger, where .
- 2.
- Challenger sends to A.
- 3.
- A sends to challenger and prepares a state .
- 4.
- Challenger replies with .
- 5.
- A applies a unitary to its state and results in , where, although not stated, also depends on the previous messages. It measures in the computational basis and sends it to challenger.
- 6.
- Challenger accepts if and .
Appendix A.3. Security of the JAK ID Scheme when Σ 1 and Σ 2 are Weakly Collapsing
Appendix A.4. Σ 2 and Σ 1 are Weakly Collapsing
- constantmode: Let the domain of f be all r with being a valid transcript when . Then, the probability that f has an image of size at most p, is at least That is, , for .
- injectivemode: for , f is injective over all r s.t. is a valid transcript when , except for a negligible probability.
-
indistinguishability. We first define game for
- -
- is given and challenge has .
- -
- (in the role of ) andChal(in the role of ) execute Σ in the first rounds, resulting in the partial transcript .
- -
- If let ; otherwise,mode=injective. Then, challenger samplesand provides it to Then, outputs a guess bit for b, which is also defined as the output of the game.
The function generator is -compatible w.r.t. Σ if for any polynomial time quantum algorithm and for , we have
Appendix B. Encoding of CStO or CStO s and Efficient Operations on Oracle State
- -
- If , then .
- -
- If , then (this implies after the operation).
- -
- If (i.e., x is not in D) and , then
- -
- If and , then .
- 1.
- O does not operate on D. For example, attacker’s operator and projective measurements on P belong to this category. In this case, since and O operates on disjoint registers and . So instead of , it suffices to apply O.
- 2.
- . Recall that and for and for . We implement with . The validity of this implementation can be verified through the basis state The verification is tedious but straightforward and hence omitted here.
- 3.
- . Recall that for , there exists so that and for for any Then, is encoded as , where . Define where and for We remind that Define unitary so that Then, can be implemented by by directly operating on without decoding D.
- 4.
- Measurement on (in PointReg1 query). In this case, we implement as . For any , let . It suffices to verify This can be checked for cases for . Tedious details are omitted.
- 5.
- Measurement on D. In this paper, measurement property on D with only depends on the non-⊥ entries. That is, the property equals to for some , where Hence, measurement on uncompressed D for property f can be done on compressed D for property . For example, f is a collision property on for non-⊥ is equivalent to the collision property on encoded (i.e., ). Since on the encoded D can be implemented efficiently, measurement of property f can be done efficiently.
Appendix C. Proof of Lemma 14
- P: It consists of the basis states so that contains a collision.
- Q: It consists of the basis states satisfying: (1) has no collision; (2) ; (3) .
- R: It consists of the basis states satisfying: (1) has no collision; (2) ; (3) .
- S: It consists of the basis states satisfying: (1) has no collision; (2) .
Appendix D. Proof of Theorem 4
-
Case : It contains all in so that1. is not in (i.e., every index has coordinate ).2. and
-
Case : It contains all in so that1. is not in the database before the th query2. is in the database after the th query and befire th query3. is not in the database after the th query and befire th query4. is in the database after the th query.
References
- Michel Abdalla, Pierre Alain Fouque, Vadim Lyubashevsky, Mehdi Tibouchi, Tightly-Secure Signatures from Lossy Identification Schemes. EUROCRYPT 2012, 572-590.
- H. K. Alper and J. Burdges. Two-round trip schnorr multi-signatures via delinearized witnesses. In T. Malkin and C. Peikert, editors, CRYPTO 2021, Part I, volume 12825 of LNCS, pages 157-188, Virtual Event, Aug. 2021. Springer, Heidelberg.
- Ali Bagherzandi, Jung Hee Cheon and Stanislaw Jarecki, Multisignatures secure under the discrete logarithm assumption and a generalized forking lemma. CCS 2008, pp. 449-458, 2008.
- Mihir Bellare, Phillip Rogaway: Random Oracles are Practical: A Paradigm for Designing Efficient Protocols. CCS 1993: 62-73, 1993.
- Mihir Bellare, Gregory Neven: Multi-signatures in the plain public-Key model and a general forking lemma. CCS 2006: 390-399.
- Ian F. Blake, Shuhong Gao and Ronald C. Mullin, Explicit Factorization of x2k+1 over Fp with Prime p≡3 mod 4. Appl. Algebra Eng. Commun. Comput. 4:89-94 (1993).
- Alexandra Boldyreva, Threshold Signatures, Multisignatures and Blind Signatures Based on the Gap-Diffie-Hellman-Group Signature Scheme. Public Key Cryptography 2003: 31-46.
- D. Boneh, C. Gentry, B. Lynn, and H. Shacham. Aggregate and verifiably encrypted signatures from bilinear maps. In E. Biham, editor, EUROCRYPT 2003, volume 2656 of LNCS, pages 416-432. Springer-Verlag, 2003.
- Dan Boneh, Mark Zhandry, Secure Signatures and Chosen Ciphertext Security in a Quantum Computing World. CRYPTO (2) 2013: 361-379.
- Cecilia Boschini, Akira Takahashi, and Mehdi Tibouchi. Musig-L: Lattice-based multi-signature with single-round online phase, CRYPTO’22.
- Ran Canetti, Oded Goldreich, Shai Halevi: The Random Oracle Methodology, Revisited. STOC 1998: 209-218.
- Kai-Min Chung, Serge Fehr, Yu-Hsuan Huang, Tai-Ning Liao: On the Compressed-Oracle Technique, and Post-Quantum Security of Proofs of Sequential Work. EUROCRYPT (2) 2021: 598-629.
- Ronald Cramer, Léo Ducas, and Benjamin Wesolowski. Short stickelberger class relations and application to ideal-svp. Eurocrypt 2017.
- Ivan Damgård, Claudio Orlandi, Akira Takahashi, and Mehdi Tibouchi. Two-round n-out-of-n and multisignatures and trapdoor commitment from lattices. PKC 2021, LNCS 12710, pages 99-130, 2021.
- Jelle Don, Serge Fehr, Christian Majenz, Christian Schaffner: Online-Extractability in the Quantum Random-Oracle Model. EUROCRYPT’22.
- Léo Ducas and Alain Durmus. Ring-lwe in polynomial rings. In PKC 2012, LNCS 7293, pages 34-51. Springer, 2012.
- Rachid El Bansarkhani and Jan Sturm. An efficient lattice-based multisignature scheme with applications to bitcoins, CANS’16, pages 140-155.
- Nils Fleischhacker, Mark Simkin, Zhenfei Zhang: Squirrel: Efficient Synchronized Multi-Signatures from Lattices. CCS 2022, papges 1109-1123, 2022.
- Masayuki Fukumitsu and Shingo Hasegawa. A tightly-secure lattice-based multisignature. The 6th Asia Public-Key Cryptography Workshop 2019, page 3-11, 2019.
- Masayuki Fukumitsu and Shingo Hasegawa. A lattice-based provably secure multisignature scheme in quantum random oracle model, ProvSec 2020.
- Qianqian He, Xiangjun Xin and Qinglan Yang, Security analysis and improvement of a quantum multi-signature protocol, Quantum Information Processing, 20:26, 2021.
- K. Itakura and K. Nakamura, A public-key cryptosystem suitable for digital multisignatures. NEC Research & Development, 71:1-8, 1983.
- S. Jiang, D. Alhadidi and H. F. Khojir, Key-and-Signature Compact Multi-Signatures for Blockchain: A Compiler with Realizations, IEEE Transactions on Dependable and Secure Computing, accepted, 2024. [CrossRef]
- S. Jiang, G. Gong, J. He, K. Nguyen and H. Wang, PAKEs: New Framework, New Techniques and More Efficient Lattice-Based Constructions in the Standard Model, The International Conference on Practice and Theory in Public-Key Cryptography (PKC’20), A. Kiayias, M. Kohlweiss, P. Wallden, V. Zikas (Eds.), LNCS 12110, IACR, pp. 396-427, 2020.
- D. H. Jiang, Q. Z. Hu, X. Q. Liang, G. B. Xu, A novel quantum multi-signature protocol based on locally indistinguishable orthogonal product states. Quantum Inf. Process. 18(9), 268 (2019). [CrossRef]
- Meenakshi Kansal, Amit Kumar Singh, Ratna Dutta, Efficient Multi-Signature Scheme Using Lattice. Comput. J. 65(9): 2421-2429 (2022).
- Meenakshi Kansal and Ratna Dutta, Round Optimal Secure Multisignature Schemes from Lattice with Public Key Aggregation and Signature Compression. AFRICACRYPT 2020, pages 281-300, 2020.
- Eike Kiltz, Vadim Lyubashevsky, and Christian Schaffner. A concrete treatment of Fiat-Shamir signatures in the quantum random-oracle model, J. B. Nielsen and V. Rijmen (Eds.), EUROCRYPT 2018, Springer, pages 552-586, 2018.
- Serge Lang, Algebra, GTM 211, Springer-Verlag, 2002.
- Qipeng Liu and Mark Zhandry, Revisiting Post-quantum Fiat-Shamir. CRYPTO (2) 2019: 326-355.
- Zi-Yuan Liu, Yi-Fan Tseng, and Raylin Tso. Cryptanalysis of a round optimal lattice-based multisignature scheme. Cryptology ePrint Archive, Report 2020/1172, 2020.
- Steve Lu, Rafail Ostrovsky, Amit Sahai, Hovav Shacham, Brent Waters: Sequential Aggregate Signatures and Multisignatures Without Random Oracles. EUROCRYPT 2006: 465-485.
- Vadim Lyubashevsky and Daniele Micciancio, Generalized Compact Knapsacks Are Collision Resistant. ICALP 2006, part 2, pages 144-155, 2006.
- Vadim Lyubashevsky, Chris Peikert, and Oded Regev. On ideal lattices and learning with errors over rings. J. ACM, 60(6):43:1-43:35, 2013.
- Vadim Lyubashevsky, Chris Peikert, and Oded Regev. A toolkit for Ring-LWE cryptography. In EUROCRYPT 2013, volume 7881 of LNCS, pages 35–54. Springer, 2013.
- Changshe Ma, Jian Weng, Yingjiu Li, Robert H. Deng: Efficient discrete logarithm based multi-signature scheme in the plain public key model. Des. Codes Cryptogr. 54(2): 121-133 (2010).
- Changshe Ma, Mei Jiang, Practical Lattice-Based Multisignature Schemes for Blockchains. IEEE Access 7: 179765-179778 (2019).
- Maxwell, G., Poelstra, A., Seurin, Y., Wuille, P.: Simple schnorr multi-signatures with applications to bitcoin. Cryptology ePrint Archive, Report 2018/068 (2018).
- Silvio Micali, Kazuo Ohta, Leonid Reyzin: Accountable-subgroup multisignatures: extended abstract. CCS 2001: 245-254.
- D. Micciancio and O. Regev. Worst-case to average-case reductions based on gaussian measures. SIAM J. Comput., 37(1): 267-302, 2007.
- Satoshi Nakamoto. Bitcoin: A Peer-to-Peer Electronic Cash System, 2008. Available at http://bitcoin.org/bitcoin.pdf.
- J. Nick, T. Ruffing, and Y. Seurin. MuSig2: Simple two-round Schnorr multi-signatures. CRYPTO 2021, Part I, LNCS 12825, pp. 189-221, Springer, 2021.
- Michael A. Nielsen and Isaac L. Chuang, Quantum Computation and Quantum Information, Cambridge University Press, New York, 2010.
- Chris Peikert, Alon Rosen, Efficient Collision-Resistant Hashing from Worst-Case Assumptions on Cyclic Lattices. TCC 2006, pages 145-166, 2006.
- Peter W. Shor, Algorithms for Quantum Computation: Discrete Logarithms and Factoring. FOCS 1994, pp. 124-134.
- Ewa Syta, Iulia Tamas, Dylan Visher, David Isaac Wolinsky, Philipp Jovanovic, Linus Gasser, Nicolas Gailly, Ismail Khoffi, and Bryan Ford. Keeping authorities “honest or bust” with decentralized witness cosigning. IEEE Symposium on Security and Privacy 2016, pp. 526-545. IEEE Computer Society Press, May 2016.
- Dominique Unruh, Quantum Proofs of Knowledge. EUROCRYPT 2012: 135-152.
- John Watrous, Quantum Computing, Lecture notes, 2006. Available at https://cs.uwaterloo.ca/ watrous/QC-notes/.
- Mark Zhandry, How to Record Quantum Queries, and Applications to Quantum Indifferentiability, CRYPTO 2019, part II, pages 239-268.
| 1 | Let be the representative of and assume that it can be efficiently computed from any . Let be a unitary with ; measuring register C in the computational basis gives . |
| 2 |
can be tested by a projective measurement with , which can be implemented by writing bit onto a new register and measuring it. |
| 3 | If before the oracle query, then it remains after the oracle query (i.e., after applying ) if and only if Y register is currently . Thus, to test if after the oracle query, we can simply apply the unitary and measure if Q register has 0. That is, we can make the test without applying the operation. |
| 4 | Recall that in -, PointReg1 query for occurs when issues the th random oracle query, where the test measurement has outcome (since it does not abort) and hence . |
| 5 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).



