Submitted:
08 July 2024
Posted:
08 July 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Related Work
2.1. Intrusion Detection System (IDS)
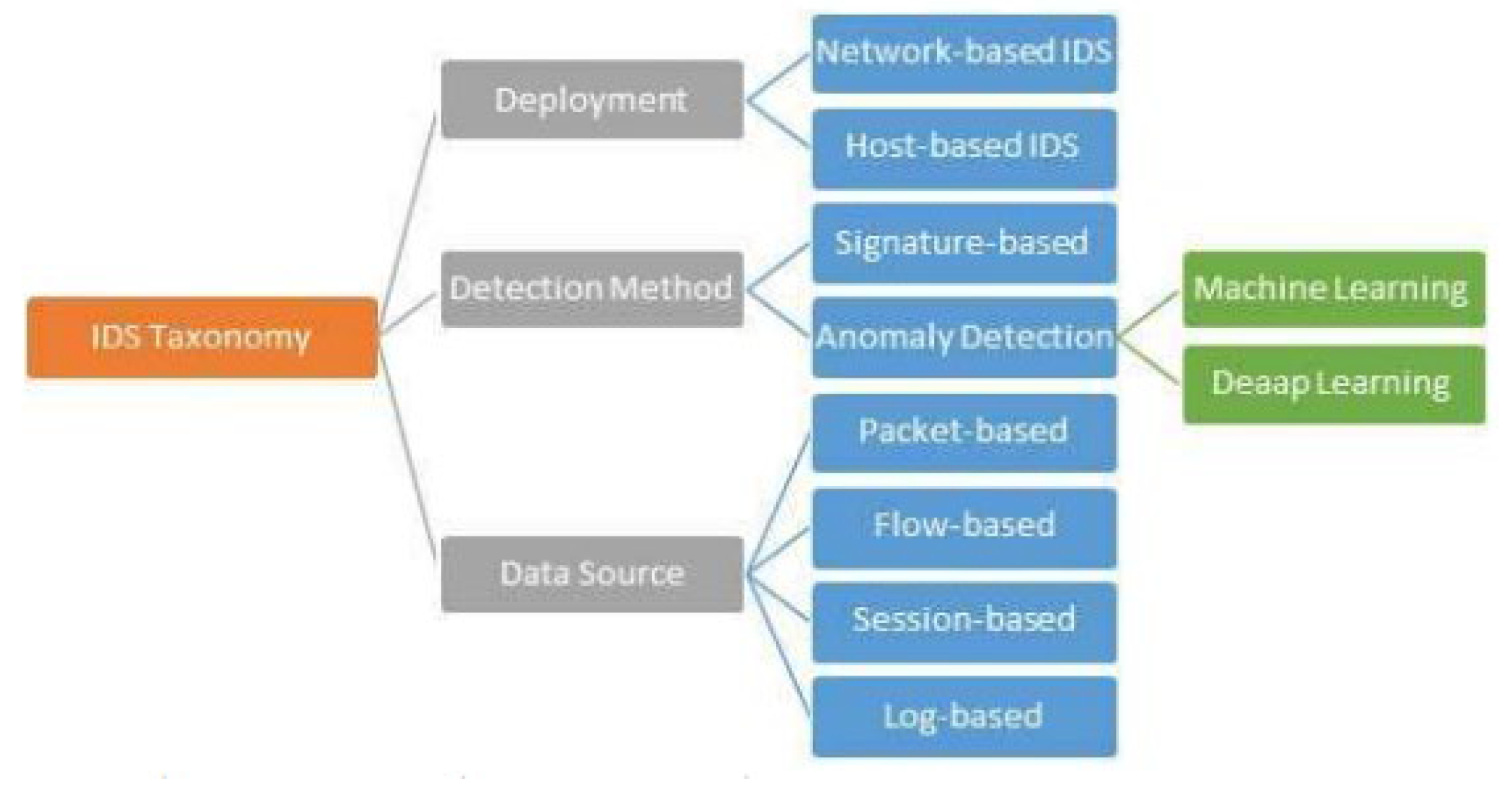
2.2. Classification of Intrusion Detection Systems
2.3. Intrusion Detection Technology of Traditional Machine Learning
2.4. Application of Deep Learning in Intrusion Detection Systems (IDS)
3. Methodology
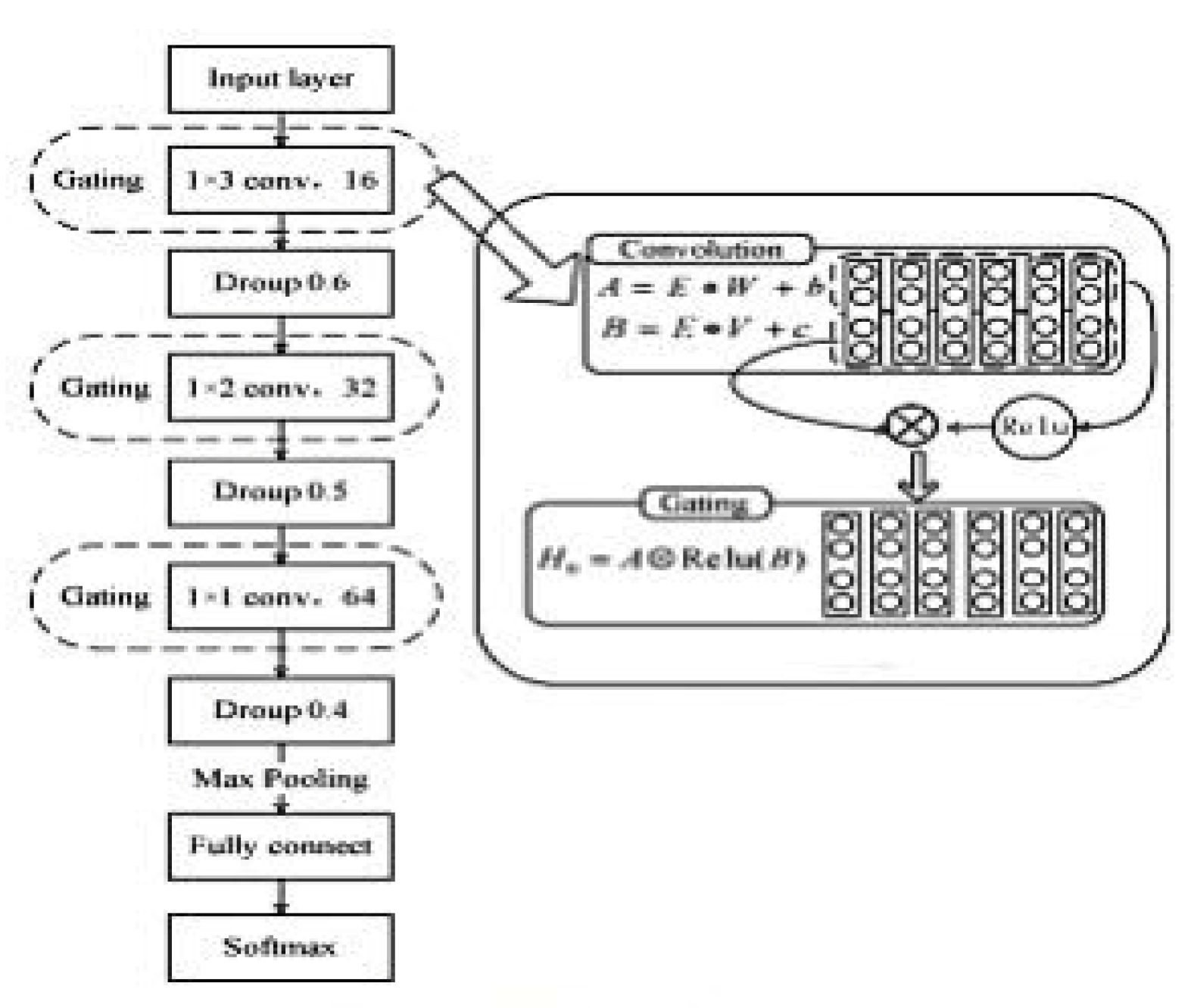
3.1. CNN-Focal Intrusion Detection Model
3.2. Experimental Design
| Dataset Name | Training Set Size | Test Set Size | Number of Features | Label Categories |
|---|---|---|---|---|
| NSL-KDD | 125973 | 22543 | 41 | Normal, Probe, Dos, U2L, R2L |
| NSL-KDD | 125973 instances | 22543 instances | 41 | Normal, Probe, R2L, U2R, DoS |
| NSL-KDD | Large | Small | 41 | Normal, Probe, Dos, R2L, U2R |
| NSL-KDD | 125973 records | 22543 records | 41 | Normal, Probe, DoS, U2R, R2L |
| NSL-KDD | Comprehensive | Limited | 41 | Normal, Probe, Dos, U2L, R2L |
3.3. Data Preprocessing
3.4. Experimental Resul
| Model | Dataset Used | Training Method | Evaluation Metrics | Results Summary |
| CNN-Focal | NSL-KDD | Train-test split (70%-30%) | Accuracy, Precision, Recall, F1-score | Achieved high accuracy and balanced performance across all metrics. The model effectively addressed class imbalance using Focal Loss. |
| CNN-Cross | NSL-KDD | Train-test split (70%-30%) | Accuracy, Precision, Recall, F1-score | Compared performance with CNN-Focal using Cross Entropy Loss, showing differences in effectiveness in handling class imbalance. |
| SVM | NSL-KDD | Train-test split (70%-30%) | Accuracy, Precision, Recall, F1-score | Provided benchmark for traditional machine learning approach in intrusion detection, showing competitive results. |
| RandomForest | NSL-KDD | Train-test split (70%-30%) | Accuracy, Precision, Recall, F1-score | Demonstrated ensemble learning’s effectiveness in handling complex feature relationships. |
| DecisionTree | NSL-KDD | Train-test split (70%-30%) | Accuracy, Precision, Recall, F1-score | Showed basic decision-making capability with moderate performance metrics. |
4. Conclusion
References
- Sagduyu, Yalin E., Yi Shi, and Tugba Erpek. “IoT network security from the perspective of adversarial deep learning.” 2019 16th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON). IEEE, 2019.
- Alom, M.Z.; Taha, T.M. (2017, June). Network intrusion detection for cyber security using unsupervised deep learning approaches. In 2017 IEEE National Aerospace and Electronics Conference (NAECON) (pp. 63-69). IEEE.
- Kumar, C.; Bharati, T.S.; Prakash, S. Online social network security: a comparative review using machine learning and deep learning. Neural Processing Letters 2021, 53, 843–861. [Google Scholar] [CrossRef]
- Gong, Y.; Zhu, M.; Huo, S.; et al. Utilizing Deep Learning for Enhancing Network Resilience in Finance[C]//2024 7th International Conference on Advanced Algorithms and Control Engineering (ICAACE). IEEE 2024, 987–991. [Google Scholar]
- Uppal HA, M.; Javed, M.; Arshad, M. An overview of the intrusion detection system (IDS) along with its commonly used techniques and classifications. International Journal of Computer Science and Telecommunications 2014, 5, 20–24. [Google Scholar]
- Abbas, S.H.; Naser WA, K.; Kadhim, A.A. Subject review: Intrusion Detection System (IDS) and Intrusion Prevention System (IPS). Global Journal of Engineering and Technology Advances 2023, 14, 155–158. [Google Scholar] [CrossRef]
- Pradhan, M.; Nayak, C.K.; Pradhan, S.K. (2020). Intrusion detection systems (IDS) and their types. In Securing the Internet of things: Concepts, methodologies, tools, and applications (pp. 481-497). IGI Global.
- Tian, J.; Li, H.; Qi, Y.; Wang, X.; Feng, Y. Intelligent medical detection and diagnosis assisted by deep learning. Applied and Computational Engineering 2024, 64, 121–126. [Google Scholar] [CrossRef]
- Borkar, A.; Donode, A.; Kumari, A. (2017, November). A survey on the Intrusion Detection System (IDS) and Internal Intrusion Detection and Protection System (IIDPS). In 2017 International Conference on Inventive Computing and Informatics (ICICI) (pp. 949-953). IEEE.
- Liu, B.; Cai, G.; Ling, Z.; Qian, J.; Zhang, Q. Precise positioning and prediction system for autonomous driving based on generative artificial intelligence. Applied and Computational Engineering 2024, 64, 42–49. [Google Scholar] [CrossRef]
- Wang, B.; He, Y.; Shui, Z.; Xin, Q.; Lei, H. Predictive optimization of DDoS attack mitigation in distributed systems using machine learning. Applied and Computational Engineering 2024, 64, 95–100. [Google Scholar] [CrossRef]
- Ashoor, A.S.; Gore, S. Importance of intrusion detection system (IDS). International Journal of Scientific and Engineering Research 2011, 2, 1–4. [Google Scholar]
- Cui, Z.; Lin, L.; Zong, Y.; Chen, Y.; Wang, S. Precision gene editing using deep learning: A case study of the CRISPR-Cas9 editor. Applied and Computational Engineering 2024, 64, 134–1. [Google Scholar] [CrossRef]
- Xiao, J.; Wang, J.; Bao, W.; Deng, T.; Bi, S. Application progress of natural language processing technology in financial research.
- Choudhury, M.; Li, G.; Li, J.; Zhao, K.; Dong, M.; Harfoush, K. (2021, September). Power Efficiency in Communication Networks with Power-Proportional Devices. In 2021 IEEE Symposium on Computers and Communications (ISCC) (pp. 1-6). IEEE.
- Yuan, J.; Lin, Y.; Shi, Y.; Yang, T.; Li, A. Applications of Artificial Intelligence Generative Adversarial Techniques in the Financial Sector. Academic Journal of Sociology and Management 2024, 2, 59–66. [Google Scholar]
- Haowei, Ma, et al. CRISPR/Cas-based nanobiosensors: A reinforced approach for specific and sensitive recognition of mycotoxins. Food Bioscience 2023, 56, 103110. [Google Scholar]
- Yu, D.; Xie, Y.; An, W.; Li, Z.; Yao, Y. (2023, December). Joint Coordinate Regression and Association For Multi-Person Pose Estimation, A Pure Neural Network Approach. In Proceedings of the 5th ACM International Conference on Multimedia in Asia (pp. 1-8).
- Kumar, S.; Gupta, S.; Arora, S. Research trends in network-based intrusion detection systems: A review. Ieee Access 2021, 9, 157761–157779. [Google Scholar] [CrossRef]
- Lin, Y.; Li, A.; Li, H.; Shi, Y.; Zhan, X. GPU-Optimized Image Processing and Generation Based on Deep Learning and Computer Vision. Journal of Artificial Intelligence General Science (JAIGS) 2024, 5, 39–49. [Google Scholar] [CrossRef]
- Liao, H.J.; Lin CH, R.; Lin, Y.C.; Tung, K.Y. Intrusion detection system: A comprehensive review. Journal of Network and Computer Applications 2013, 36, 16–24. [Google Scholar] [CrossRef]
- Shone, N.; Ngoc, T.N.; Phai, V.D.; Shi, Q. A deep learning approach to network intrusion detection. IEEE transactions on emerging topics in computational intelligence 2018, 2, 41–50. [Google Scholar] [CrossRef]
- Sekar, R.; Guang, Y.; Verma, S.; Shanbhag, T. (1999, November). A high-performance network intrusion detection system. In Proceedings of the 6th ACM Conference on Computer and Communications Security (pp. 8-17).
- Huang, C.; Bandyopadhyay, A.; Fan, W.; Miller, A.; Gilbertson-White, S. Mental toll on working women during the COVID-19 pandemic: An exploratory study using Reddit data. PloS one 2023, 18, e0280049. [Google Scholar] [CrossRef] [PubMed]
- Ma, Haowei. “Research on promotion of lower limb movement function recovery after stroke by using lower limb rehabilitation robot in combination with constant velocity muscle strength training.” 2021 7th international symposium on mechatronics and industrial informatics (ISMII). IEEE, 2021.
- Bi, Shuochen, Wenqing Bao, Jue Xiao, Jiangshan Wang, and Tingting Deng. “Application and practice of AI technology in quantitative investment. arXiv preprint arXiv:2404.18184, arXiv:2404.18184(2024).
- Liang, P.; Song, B.; Zhan, X.; Chen, Z.; Yuan, J. Automating the training and deployment of models in MLOps by integrating systems with machine learning. Appl. Comput. Eng. 2024, 67, 1–7. [Google Scholar] [CrossRef]
- Haowei, M. A. , et al. Employing Sisko non-Newtonian model to investigate the thermal behavior of blood flow in a stenosis artery: Effects of heat flux, different severities of stenosis, and different radii of the artery. Alexandria Engineering Journal 2023, 68, 291–300. [Google Scholar] [CrossRef]
- Li, A.; Yang, T.; Zhan, X.; Shi, Y.; Li, H. Utilizing Data Science and AI for Customer Churn Prediction in Marketing. Journal of Theory and Practice of Engineering Science 2024, 4, 72–79. [Google Scholar]
- Farnaaz, N.; Jabbar, M.A. Random forest modeling for network intrusion detection system. Procedia Computer Science 2016, 89, 213–217. [Google Scholar] [CrossRef]
- Liao, H.J.; Lin CH, R.; Lin, Y.C.; Tung, K.Y. Intrusion detection system: A comprehensive review. Journal of Network and Computer Applications 2013, 36, 16–24. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, B.; Gong, Y.; Huang, J.; Xu, J.; Wan, W. Application of machine learning optimization in cloud computing resource scheduling and management. Appl. Comput. Eng. 2024, 64, 17–22. [Google Scholar] [CrossRef]
- Huang, J.; Zhang, Y.; Xu, J.; Wu, B.; Liu, B.; Gong, Y. Implementation of seamless assistance with Google Assistant leveraging cloud computing. Appl. Comput. Eng. 2024, 64, 170–176. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




