Submitted:
05 March 2024
Posted:
06 March 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Overview of IoMT and IoHT
2.1. Internet of Medical Things (IoMT) Networks
- A.
- Connectivity: IoMT networks connect various pieces of medical equipment by using a variety of wired and wireless networking technologies[51]. Cellular networks, Wi-Fi, Bluetooth, Zigbee, and low-power wide-area networks are some of the technologies that fall under this category (LPWAN)[52,53]. The kind of connection that is implemented is decided by a number of factors, the most important of which are the power and data requirements of the device, in addition to its portability.
- B.
- Data Collection: The networks that make up the IoMT collect data in real time from many different kinds of medical devices[54,55]. This category of devices may include imaging equipment, infusion pumps, imaging software, wearable health trackers, vital sign monitors, and other medical instruments[56]. Data may contain information on the patient's health, diagnostic data, data regarding medication adherence, and aspects connected to the environment, among other things. .
- C.
- Data Transmission: After being collected, the information on the medical histories of patients is then sent, in a secure way that is also encrypted, to centralised systems such as Electronic Health Record (EHR) systems, cloud-based platforms, or healthcare institutions[57,58,59,60]. The confidentiality of patient information must be protected at all costs, and compliance with relevant healthcare standards must be ensured by using data security measures of the highest priority.
- D.
- Data Management: IoMT networks make use of data management techniques so that medical data may be successfully organised, stored, and retrieved. The networks also make use of these strategies in various capacities[61,62,63]. It is standard practise to organise data in a methodical manner so that it is simple for medical professionals to get the information they want. This makes it possible for them to do their jobs more effectively.
- E.
- Interoperability: Interoperability between devices that were produced by a number of different manufacturers and data that was gathered from a number of different sources is one of the challenges that IoMT networks need to solve. With the assistance of standards such as Health Level Seven International (HL7) and Fast Healthcare Interoperability Resources, it should be possible to achieve this goal with a greater degree of convenience (FHIR)[64,65].
- F.
- Scalability: IoMT networks need to be scalable in order to serve the ever-increasing number of medical devices as well as the ever-increasing volume of data[66]. The capacity to scale ensures that the network can continue to function normally despite the ever-evolving demands that are put upon it by the healthcare sector.
- G.
- Reliability: In the field of healthcare, it is very vital to have networks that can be relied upon. Downtime or connection issues may have huge ramifications, which is why IoMT networks are designed to be very reliable[67]. To decrease the possibility of failures, many IoMT networks have redundancy as a built-in feature to help reduce the risk of failures.
- H.
- Security: The privacy of the patients' information and the safety of the network are two issues that must be prioritised above all others. The networks that comprise the IoMT are equipped with severe security measures such as encryption, authentication, access control, and intrusion detection systems[68].
- I.
- Real-time Monitoring: Networks that are connected to the IoMT make it possible to monitor the state of patients in real time[69]. When healthcare workers are connected to a variety of medical devices, they are able to get fast alerts and updates on the condition of patients, which helps them to react promptly in the event of an emergency.
- J.
- Machine Learning and Analytics: In order to extract valuable information from the vast amounts of healthcare data that are gathered, IoMT networks often make use of machine learning and data analytics[70]. The early detection of illnesses, the recommendation of treatments, and the management of resources are all areas in which predictive analytics might potentially be of service.
- K.
- Telemedicine Integration: The integration of telemedicine systems, which allows remote patient monitoring as well as consultations and follow-up visits, is made possible thanks to IoMT networks, which are a crucial component of the integration process[71]. This is especially important when it comes to providing medical care to those who reside in remote or rural areas since it reduces travel time.
- L.
- Regulatory Compliance: It is of the utmost importance to conduct oneself in a way that is in keeping with the requirements of the laws that control healthcare, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States[72,73]. IoMT networks have the obligation of ensuring that the information belonging to patients is handled in a manner that is in accordance with these requirements.
2.2. Internet of Medical Things (IoMT) Architecture
- A.
-
IoMT Devices and Sensors Layer:
- ▪
- Medical Devices: Specialized tools like electrocardiogram (ECG) machines and imaging gadgets sit above this layer with more generalised instruments like wearable health trackers, infusion pumps, and vital sign monitors. Sensors built inside these gadgets record vital patient health information[77].
- ▪
- IoMT Sensors: In the realm of data collecting, sensors are of invaluable service. They can keep tabs on your vitals, including your heart rate, blood pressure, oxygen levels, glucose levels, and temperature, in addition to a host of other metrics. In order to keep an eye on a variety of health issues and diagnose them as they emerge, these sensors capture continuous readings[78].
- B.
-
Connectivity Layer:
- ▪
- Wireless Technologies: Data from medical devices may be sent to the IoMT network with greater ease thanks to the usage of a wide range of wireless technologies such as Wi-Fi, Bluetooth, Zigbee, and cellular networks. All of the above technologies are applicable here[79]. These wireless connections guarantee that the data is transferred in a safe and efficient manner.
- ▪
- Wired Connections: Some healthcare facilities may require certain medical devices to only function via hardwired connections. Medical facilities and clinics fall within this category[80]. It's done like this to ensure reliable data transmission at high speeds and lessen the chance of interference from wireless signals.
- C.
-
IoMT Gateway Layer:
- ▪
- IoMT Gateways: IoT devices link to the main network using gateways that the IoMT supplies. Data collection begins with information being gathered from a variety of devices, followed by basic processing and aggregation of that data, and finally, delivery to the network of interest[81,82]. When gateways use local storage, users may be certain that their data will be preserved even if the underlying network goes down. Data persistence is the process by which this is achieved.
- D.
-
IoMT Network Layer:
- ▪
- Cloud-Based Platforms: The data collected by IoMT gadgets is sent to cloud-based systems that are safe, scalable, and in line with the rules that govern the healthcare industry. It's possible that both doctors and patients might benefit from using these kinds of platforms, since they allow for the storage, analysis, and remote access to patient data. The patients will benefit from them as well[83].
- ▪
- Local Hospital Networks: Local healthcare network infrastructures are responsible for managing and processing data generated by IoMT devices located inside an organisation. This is because IoMT equipment is often housed inside a building. These regional networks not only provide data redundancy but also ensure that information can be handled quickly and effectively[84].
- E.
-
Data Management and Processing Layer:
- ▪
- Data Storage: In order to keep track of past patient information, IoMT's design incorporates data storage systems that may reside either on-premises or in the cloud. These infrastructures may be located anywhere is most convenient. These systems must follow the rules governing the totality of data storage[85].
- ▪
- Data Processing and Analytics: The information obtained from IoT devices has to be processed and analysed before it can be of any value. In the field of healthcare, practitioners place a significant amount of reliance on advanced analytics and machine learning algorithms, which assist them in recognising trends, predicting the progression of illnesses, and making educated judgments[86].
- F.
-
Security Layer:
- ▪
- Data Security: There are stringent safety measures in place due to the delicate nature of healthcare data. Some of these measures include of encrypting data, limiting access, and authenticating users[87]. These safeguards prevent data breaches and ensure that sensitive patient information is not accessed by any other parties.
- ▪
- Compliance: In order to protect the privacy of patients and prevent any unauthorised parties from having access to their medical records, it is crucial to adhere to healthcare rules such as the Health Insurance Portability and Accountability Act (HIPAA). To preserve the privacy of their patients' medical records, healthcare providers must ensure that they are in compliance with all applicable laws and regulations[88].
- G.
-
Healthcare Applications Layer:
- ▪
- Electronic Health Records (EHR): Because of the interoperability between IoMT and EHRs, healthcare providers now have access to more in-depth patient data than ever before. This consolidation will allow for a more thorough understanding of the patient's medical background and records[89].
- ▪
- Telemedicine Platforms: IoMT is crucial in the field of telemedicine since it prepares the way for telehealth services such as teleconsultations and telemonitoring. A patient's IoMT-generated health data may be shared with their doctor during a telemedicine appointment[90].
- ▪
- Clinical Decision Support: Using information from the Internet of Medical Things, clinical decision support systems are developed to help doctors make more informed decisions. These systems provide recommendations in real time based on actual patient data[91].
- H.
-
Patient-Facing Applications Layer:
- ▪
- Mobile Apps: Patients may apply mobile apps to access their health data, get notifications, and contact with healthcare practitioners. These applications promote patient involvement and allow self-monitoring[92].
- ▪
- Patient Portals: Web-based patient portals enable safe access to health information, appointment scheduling, and engagement with healthcare professionals. Patients may actively engage in their treatment and acquire their medical information[93].
2.3. Internet of Healthcare Things (IoHT) Networks
- A.
- Wireless Sensor Networks (WSNs): The IoHT commonly makes use of WSNs, which are consisting of sensors and other pieces of equipment that are linked to one another and may monitor a variety of various elements of a person's health. Wearable devices, implantable sensors, and environmental sensors used in hospitals are just a few examples of the numerous types of sensors that might be utilized[95].
- B.
- IoHT Gateways: There are typically gateways or hubs in IoHT networks that mediate communication between IoHT devices and remote or local healthcare IT infrastructure. These nodes and intersections may also be thought of as mediators. These entryways or hubs of activity are also sometimes called "interfaces." When it comes to aggregating data, doing basic processing on it, and securely transporting it, gateways are invaluable tools. Also, gateways can do these things simultaneously[96].
- C.
- Cloud Integration: In order to store and handle the vast amounts of data generated by healthcare devices, IoHT networks often turn to cloud computing. There are a few reasons why this is done. Data analytics, real-time patient monitoring, and off-site access to patient records are all made possible by cloud-based systems for use by medical personnel[97].
- D.
- Edge Computing: As edge computing grows more widespread, IoHT networks are increasingly relying on edge devices to process data in a more decentralised fashion. This results in less waiting time and allows for quicker decisions to be made under time-sensitive healthcare conditions[98].
- E.
- 5G Technology: The widespread use of IoHT networks is directly attributable to the huge improvements in connection speeds and data transmission capacity brought about by the advent of 5G technology. Real-time patient monitoring and other telemedicine applications rely heavily on the availability of stable, low-latency connections[99].
- F.
- IoT Protocols: IoHT networks use a variety of communication protocols designed specifically for the IoTto ensure the timely and accurate transfer of data. When connecting to other devices in the IoHT, the most popular protocols used are HTTP, MQTT, and CoAP[100].
- G.
- Security: It is of the utmost importance that IoHT networks be maintained secure at all times since healthcare data is so sensitive. There are strict mechanisms in place for encryption, authentication, and access control to ensure that patient data remains private[101].
- H.
- Scalability: In order to support the ever-increasing number of sensors and other IoHT nodes, IoHT networks need to be scalable. In healthcare facilities, scalability is a must-have quality since the number of linked devices is likely to grow quickly[102].
- I.
- Interoperability: It is crucial to keep interoperability in mind when designing networks for the IoHT. Complete healthcare data transmission requires the flawless operation of several devices, each of which was manufactured by a different company and makes use of a distinct communication protocol[103].
- J.
- Energy Efficiency: Many IoHT devices run on batteries, thus they must be very efficient in using power so that they can keep monitoring in real time without always needing to be recharged. The creation of low-power communication protocols and energy-saving methods is crucial[104].
- K.
- Compliance: IoHT networks are required to comply with healthcare legislation, such as HIPAA in the United States, to protect the confidentiality of patient information and fulfil their obligations under the law. In the United States, this legislation is known as the Health Insurance Portability and Accountability Act (HIPAA)[105].
- L.
- Data Analytics: The IoHT generates enormous amounts of data via its network of connected devices. Because of this, they often include components for data analytics and machine learning in order to derive meaningful insights from the aforementioned data in order to improve the quality of treatment provided to patients[106].
- M.
- Telemedicine Integration: It is feasible to conduct healthcare consultations and services via the internet thanks to the IoHT networks, many of which are designed to interact smoothly and without hiccups with telemedicine systems[107].
- N.
- Patient Portals: Some IoHT networks include patient portals, which enable consumers to view their own health data and connect with healthcare practitioners in order to improve their capacity to self-manage their treatment. The goal of these patient portals is to improve consumers' ability to take charge of their own healthcare[108].
- O.
- Research and Clinical Trials: IoHT networks are able to contribute to the development of medical research in a number of ways. One of these methods is by ensuring that patients who take part in clinical trials are able to provide continuous data that is kept current[109].
- P.
- Healthcare Management: The management of healthcare, the enhancement of hospital operations, and the optimization of resource allocation are all areas that benefit from the use of IoHT networks[110].
2.4. IoHT Architecture
3. Challenges and Opportunities of IoMT and IoHT in the Synergy of WSNs and Machine Learning
3.1. Challenges of IoMT and IoHT
- A.
- Data Security and Privacy:
- B.
- Interoperability:
- C.
- Regulatory Compliance:
- D.
- Data Overload:
- E.
- Data Quality:
- F.
- Scalability:
- G.
- Energy Efficiency:
- H.
- Standardization:
- I.
- Device Reliability:
- J.
- Ethical Considerations:
- K.
- Medical Errors:
- L.
- Resource Constraints:
- M.
- Cost of Implementation:
- N.
- Resistance to Adoption:
- O.
- Network Latency:
- P.
- Data Ownership and Control:
- Q.
- Data Integration:
- R.
- Data Storage and Retention:
- S.
- S. Cybersecurity:
- T.
- Evolving Technology:
3.2. Opportunitiess of IoMT and IoHT
- A.
- Improved Patient Outcomes:
- B.
- Remote Patient Monitoring:
- C.
- Telemedicine:
- D.
- Preventive Healthcare:
- E.
- Health Data Analytics:
- F.
- Personalized Medicine:
- G.
- Cost Reduction:
- H.
- Enhanced Quality of Life:
- I.
- Chronic Disease Management:
- J.
- Efficient Resource Management:
- K.
- Public Health Initiatives:
- L.
- AI Integration:
- M.
- Wearable Devices:
- N.
- Patient Engagement:
- O.
- IoMT in Mental Health:
- P.
- IoMT in Rehabilitation:
- Q.
- Enhanced EHRs:
- R.
- IoMT in Smart Homes:
- S.
- Pharmacovigilance:
- T.
- Personalized Nutrition:
| Paper | Challenges | Machine Learning Technique | Key Findings | Implications |
|---|---|---|---|---|
| [194] | Data Security and Privacy | Encryption, Anomaly Detection | Data breaches are putting patients in serious peril. | Protect sensitive patient data by developing new encryption mechanisms and anomaly detection methods. |
| [195] | Interoperability | Data Integration, Standards | the impossibility of sharing data because of disparate standards and technology. | Promote standardisation and provide solid integration solutions to improve data exchange. |
| [196] | Regulatory Compliance | Compliance Monitoring | Maintaining medical compliance is a difficult task. | In order to avoid financial penalties, programmes of regular monitoring and conformity to rules are required. |
| [197] | Data Overload | Big Data Analytics | Large data sets may be a hardship in the healthcare industry. | Invest in analytics for huge data sets to acquire meaningful insights and better your decision-making processes. |
| [198] | Data Quality | Data Validation, Cleaning | Erroneous information might result in medical errors. | Use a data validation and cleaning process to ensure the integrity of your data. |
| [199] | Scalability | Scalable Infrastructure | Healthcare systems are under strain as IoMT use grows. | A scalable infrastructure can accommodate an ever-increasing population of interconnected gadgets. |
| [200] | Energy Efficiency | Low-Power Algorithms | It is crucial to extend the battery life of IoMT devices. | Optimizing your device's performance requires investigating low-power algorithms and energy-harvesting strategies. |
| [201] | Standardization | Standardization Frameworks | The lack of standards hinders the flow of data. | Propose and support standardised protocols and channels of communication to hasten the arrival of interoperability. |
| [202] | Device Reliability | Quality Control, Testing | Device malfunctions might cause harm to patients. | Create rigorous procedures for evaluating IoMT equipment as part of quality assurance. |
| [203] | Ethical Considerations | Data Governance, Consent | confusing issues with authorization and ownership. | Build transparent data governance processes and get approval to use patient information. |
| [204] | Medical Errors | Clinical Decision Support | Serious concerns are raised by inaccuracies in remote monitoring. | Medical professionals may use a little help from clinical decision support tools. |
| [205] | Resource Constraints | Low-Cost Solutions | Adoption is challenging in environments with few resources. | Use low-cost IoMT equipment and prioritise critical services to stay under your set financial limits. |
| [206] | Cost of Implementation | Cost-Benefit Analysis | The high barrier to entry may deter organisations. | Weigh the advantages against the disadvantages and investigate any potential financial incentives. |
| [207] | Resistance to Adoption | Education, Training | Many individuals are sceptical about disruption because it might be frightening. | Educating both medical professionals and patients on the potential benefits of IoMT is crucial. |
| [208] | Network Latency | Low-Latency Communication | A data delay might have catastrophic consequences. | Investing in a dependable communication infrastructure with low latency is essential for real-time tracking. |
| [209] | Data Ownership and Control | Legal Frameworks | It's challenging to identify which information belongs to whom. | Formalize patient data rights via regulatory frameworks. |
| [210] | Data Integration | Middleware, APIs | It's hard to integrate data seamlessly. | Use middleware and APIs to standardise data formats and facilitate integration. |
| [211] | Data Storage and Retention | Cloud Solutions, Archiving | Long-term data storage requires large storage capacity. | Use data archiving and cloud computing for efficient data lifecycle management. |
| [212] | Cybersecurity | Threat Detection, Encryption | Cybercriminals often target the healthcare sector with their attacks. | IoMT infrastructure needs intrusion detection, encryption, and regular security audits to keep it safe. |
| [213] | Evolving Technology | Continuous Learning | Keeping up with technology is an ongoing uphill struggle. | Stay current by making learning and innovative problem-solving part of your daily routine. |
| Paper | Opportunities | ML Technique | Key Findings | Implications |
|---|---|---|---|---|
| [214] | Improved Patient Outcomes | Predictive Analytics, AI | The health outcomes may be better with constant supervision. | Invest in AI and analytics that can forecast outcomes to better serve patients. |
| [215] | Remote Patient Monitoring | Data Analytics, AI | Personalized care reduces the need for hospital readmissions. | Allow for medical therapy to be tailored to each patient via remote monitoring. |
| [216] | Telemedicine | Telehealth Platforms, AI | improves availability and simplicity of access to medical treatment. | Invest in artificial intelligence and telemedicine to provide distant treatment. |
| [217] | Preventive Healthcare | Early Warning Systems, AI | Preventative healthcare techniques help people prevent health problems. | Put together early warning systems that are driven by AI. |
| [218] | Health Data Analytics | Big Data Analytics | The insights gleaned from large data sets provide better decision support. | Put money into big data analytics so you can make educated healthcare decisions. |
| [219] | Personalized Medicine | Precision Medicine, AI | personalised treatment based on each individual's history. | Make use of individualised care with the use of AI and precision medicine. |
| [220] | Cost Reduction | Process Optimization | Saving money may arise from remote monitoring. | Reduce healthcare costs by streamlining processes. |
| [221] | Enhanced Quality of Life | Gerontechnology, AI | IoMT helps older patients live better lives. | Care for both young and old requires financial investment in IoMT. |
| [222] | Chronic Disease Management | Disease Prediction Models, AI | With the aid of IoMT, chronic diseases can be better controlled. | Create AI-powered sickness prediction algorithms. |
| [223] | Efficient Resource Management | Resource Allocation Models | IoMT allows for more efficient use of healthcare resources. | Applying strategies for allocating resources is essential for good administration. |
| [224] | Public Health Initiatives | Disease Surveillance, Data Sharing | When it comes to public health, IoHT has your back. | Make use of IoHT for tracking diseases and controlling epidemics. |
| [225] | AI Integration | AI-Driven Diagnostics | The predictive and diagnostic abilities of AI are enhanced. | Intelligent medical diagnosis is possible when AI is combined with IoMT. |
| [226] | Wearable Devices | Smart Wearables | Promote lifelong introspection and health. | Make high-tech wearables that can monitor your health stats. |
| [227] | Patient Engagement | Patient-Centered Apps | IoMT promotes patient autonomy and active participation. | Create software with patient participation in mind. |
| [228] | IoMT in Mental Health | Mental Health Monitoring | The effects of IoMT on mental health are substantial. | The Internet of Mental Things can monitor and aid psychological health. |
| [229] | IoMT in Rehabilitation | Physical Therapy Models, AI | IoMT helps in therapy and rehabilitation. | Consider the uses of IoMT in the realms of medicine and rehabilitation. |
| [230] | Enhanced Electronic Health Records | EHR Integration, Data Normalization | Integrating IoMT information into existing patient files is beneficial. | By incorporating IoMT data into EHR systems, more complete patient profiles may be created. |
| [231] | IoMT in Smart Homes | Healthcare Support in Smart Homes | IoMT helps with medical treatment in smart homes. | Construct IoMT applications for connected dwellings. |
| [232] | Pharmacovigilance | Drug Safety Monitoring | IoMT helps with keeping an eye on the security of medications. | IoMT may be used to monitor drug quality and side effects. |
| [233] | Personalized Nutrition | Dietary Recommendations, AI | Plan your diet in accordance with medical advice. | Use information from IoMT to provide personalised dietary advice. |
4. Application of Internet of Medical Things (IoMT) & Internet of Healthcare Things (IoHT)
5. Security Issues of Internet of Medical Things (IoMT) & Internet of Healthcare Things (IoHT)
6. Open and Research Issue
7. Conclusion
Conflict of Interest:
References
- Castillejo, P.; Martinez, J.-F.; Rodriguez-Molina, J.; Cuerva, A. Integration of wearable devices in a wireless sensor network for an E-health application. IEEE Wireless Commun. 2013, 20, 38–49. [Google Scholar] [CrossRef]
- Shirehjini, A.A.N.; Yassine, A.; Shirmohammadi, S. Equipment location in hospitals using RFID-based positioning system. IEEE Trans. Inf. Technol. Biomed. 2012, 16, 1058–1069. [Google Scholar] [CrossRef]
- Choudhury, T.; Kumar, V.; Nigam, D. Intelligent classification and clustering of lung and oral cancer through decision tree & genetic algorithm. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2015, 5, 501–510. [Google Scholar]
- Choudhury, T.; Kumar, V.; Nigam, D. Intelligent classification and clustering of lung and oral cancer through decision tree & genetic algorithm. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2015, 5, 501–510. [Google Scholar]
- Afsana, F.; Asif-Ur-Rahman, M.; Ahmed, M.R.; Mahmud, M.; Kaiser, M.S. An energy conserving routing scheme for wireless body sensor nanonetwork communication. IEEE Access 2018, 6, 9186–9200. [Google Scholar] [CrossRef]
- Haque, I.T.; Abu-Ghazaleh, N. Wireless software defined networking: A survey and taxonomy. IEEE Commun. Surveys Tuts. 2016, 18, 2713–2737. [Google Scholar] [CrossRef]
- McFarlane, D. The Origin of the Internet of Things, June 2015. Available online: https://www.redbite.com/the-origin-of-the-internet-of-things/.
- Ganzha, M.; Paprzycki, M.; Pawłowski, W.; Szmeja, P.; Wasielewska, K. Semantic interoperability in the Internet of Things: An overview from the INTER-IoT perspective. J. Netw. Comput. Appl. 2017, 81, 111–124. [Google Scholar] [CrossRef]
- Columbus, L. Roundup of Internet of Things Forecasts and Market Estimates, Nov. 2016. Available online: https://www.forbes.com/sites/louiscolumbus/2016/11/27/roundup-of-internet-of-things-forecasts-and-market-estimates-2016/.
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision architectural elements and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Chehri, A.; Mouftah, H.; Jeon, G. A smart network architecture for e-health applications. In Intelligent Interactive Multimedia Systems and Services; Springer: Berlin, Germany, 2010; pp. 157–166. [Google Scholar]
- He, W.; Goodkind, D.; Kowal, P. An Aging World 2015, Dec. 2017. Available online: https://www.census.gov/library/publications/2016/demo/P95-16-1.html.
- Hamdi, O.; Chalouf, M.A.; Ouattara, D.; Krief, F. eHealth: Survey on research projects, comparative study of telemonitoring architectures and main issues. J. Netw. Comput. Appl. 2014, 46, 100–112. [Google Scholar] [CrossRef]
- Wamba, S.F.; Anand, A.; Carter, L. A literature review of RFID-enabled healthcare applications and issues. Int. J. Inf. Manag. 2013, 33, 875–891. [Google Scholar] [CrossRef]
- Verma, P.K.; et al. Machine-to-machine (M2M) communications: A survey. J. Netw. Comput. Appl. 2016, 66, 83–105. [Google Scholar] [CrossRef]
- Arkian, H.R.; Diyanat, A.; Pourkhalili, A. MIST: Fog-based data analytics scheme with cost-efficient resource provisioning for IoT crowdsensing applications. J. Netw. Comput. Appl. 2017, 82, 152–165. [Google Scholar] [CrossRef]
- Tokognon, C.A.; Gao, B.; Tian, G.Y.; Yan, Y. Structural health monitoring framework based on Internet of Things: A survey. IEEE Internet Things J. 2017, 4, 619–635. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K.-S. The Internet of Things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Xu, X.; Rao, X.; Lau, V.K.N. Active user detection and channel estimation in uplink CRAN systems. Proc. ICC 2015, 2727–2732. [Google Scholar]
- Sethi, P.; Sarangi, S.R. Internet of Things: Architectures, Protocols, and Applications. J. Electr. Comput. Eng. 2017, 2017, 1–25. [Google Scholar] [CrossRef]
- Acampora, G.; Cook, D.J.; Rashidi, P.; Vasilakos, A.V. A Survey on Ambient Intelligence in Healthcare. Proc. IEEE 2013, 101, 2470–2494. [Google Scholar] [CrossRef]
- Spanakis, E.; et al. Connection between biomedical telemetry and telemedicine. In Handbook of Biomedical Telemetry; Wiley: Hoboken, NJ, USA, 2014; pp. 419–444. [Google Scholar]
- James, A.; Cooper, J.; Jeffery, K.; Saake, G. Research directions in database architectures for the Internet of Things: A communication of the first international workshop on database architectures for the Internet of Things (DAIT 2009). In Dataspace: The Final Frontier; Springer: Heidelberg, Germany, 2009; pp. 225–233. [Google Scholar]
- Priyadarshi, R.; Bhardwaj, P.; Gupta, P.; Nath, V. Utilization of Smartphone-Based Wireless Sensors in Agricultural Science: A State of Art. In Microelectronics, Communication Systems, Machine Learning and Internet of Things: Select Proceedings of MCMI 2020; Springer: Singapore, 2022; pp. 681–688. [Google Scholar]
- Cooper, J.; James, A. Challenges for Database Management in the Internet of Things. IETE Tech. Rev. 2009, 26, 320–329. [Google Scholar] [CrossRef]
- Kaiser, M.; Ahmed, K.M. Neuro-fuzzy selection algorithm for optimal relaying in OFDM systems. Int. J. Auton. Adapt. Commun. Syst. 2017, 10, 213. [Google Scholar] [CrossRef]
- Mahmud, M.; Rahman, M.M.; Travalin, D.; Hussain, A. Service oriented architecture based Web application model for collaborative biomedical signal analysis. Biomed. Tech. (Berl) 2012, 57, 780–783. [Google Scholar] [CrossRef] [PubMed]
- Priyadarshi, R.; Gupta, B. 2-D coverage optimization in obstacle-based FOI in WSN using modified PSO. J. Supercomput. 2023, 79, 4847–4869. [Google Scholar] [CrossRef]
- Díaz, M.; Martín, C.; Rubio, B. State-of-the-art, challenges, and open issues in the integration of Internet of things and cloud computing. J. Netw. Comput. Appl. 2016, 67, 99–117. [Google Scholar] [CrossRef]
- Zhang, Y.; Qiu, M.; Tsai, C.-W.; Hassan, M.M.; Alamri, A. Health-CPS: Healthcare cyber-physical system assisted by cloud and big data. IEEE Syst. J. 2017, 11, 88–95. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar] [CrossRef]
- Verba, N.; Chao, K.-M.; James, A.; Goldsmith, D.; Fei, X.; Stan, S.-D. Platform as a service gateway for the Fog of Things. Adv. Eng. Informatics 2017, 33, 243–257. [Google Scholar] [CrossRef]
- Andriopoulou, F.; Dagiuklas, T.; Orphanoudakis, T. Integrating IoT and fog computing for healthcare service delivery. In Components and Services for IoT Platforms: Paving the Way for IoT Standards; Springer: Cham, Switzerland, 2017; pp. 213–232. [Google Scholar]
- Dubey, H.; et al. , Switzerland, 2017; pp. 281–321.applications. In Handbook of Large-Scale Distributed Computing in Smart Healthcare; Springer: Cham, Switzerland, 2017; pp. 281–321. [Google Scholar]
- Ahlgren, B.; Aranda, P.A.; Chemouil, P.; Oueslati, S.; Correia, L.M.; Karl, H.; Söllner, M.; Welin, A. Content, connectivity, and cloud: ingredients for the network of the future. IEEE Commun. Mag. 2011, 49, 62–70. [Google Scholar] [CrossRef]
- Qi, J.; Yang, P.; Min, G.; Amft, O.; Dong, F.; Xu, L. Advanced internet of things for personalised healthcare systems: A survey. Pervasive Mob. Comput. 2017, 41, 132–149. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Chang, V.; Badaroglu, M.; Constant, N.; Mankodiya, K. Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare. Futur. Gener. Comput. Syst. 2018, 78, 659–676. [Google Scholar] [CrossRef]
- Kraemer, F.A.; Braten, A.E.; Tamkittikhun, N.; Palma, D. Fog computing in healthcare—A review and discussion. IEEE Access 2017, 5, 9206–9222. [Google Scholar] [CrossRef]
- Mutlag, A.A.; Ghani, M.K.A.; Arunkumar, N.; Mohamed, M.A.; Mohd, O. Enabling technologies for fog computing in healthcare IoT systems. Future Gener. Comput. Syst. 2019, 90, 62–78. [Google Scholar] [CrossRef]
- MAhmad, M.; Amin, M.B.; Hussain, S.; Kang, B.H.; Cheong, T.; Lee, S. Health Fog: a novel framework for health and wellness applications. J. Supercomput. 2016, 72, 3677–3695. [Google Scholar] [CrossRef]
- Rahmani, A.M.; Gia, T.N.; Negash, B.; Anzanpour, A.; Azimi, I.; Jiang, M.; Liljeberg, P. Exploiting smart e-Health gateways at the edge of healthcare Internet-of-Things: A fog computing approach. Futur. Gener. Comput. Syst. 2018, 78, 641–658. [Google Scholar] [CrossRef]
- Xu, B.; et al. Ubiquitous data accessing method in IoT-based information system for emergency medical services. IEEE Trans. Ind. Informat. 2014, 10, 1578–1586. [Google Scholar]
- Fan, Y.J.; Yin, Y.H.; Xu, L.D.; Zeng, Y.; Wu, F. IoT-based smart rehabilitation system. IEEE Trans. Ind. Informat. 2014, 10, 1568–1577. [Google Scholar]
- Maksimovic, M.; Vujovic, V.; Perisic, B. A custom Internet of Things healthcare system. Proc. CISTI 2015, 1–6. [Google Scholar]
- Catarinucci, L; et al. An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Ukil, A.; Bandyoapdhyay, S.; Puri, C.; Pal, A. IoT healthcare analytics: The importance of anomaly detection. Proc. AINA 2016, 994–997. [Google Scholar]
- Gope, P.; Hwang, T. BSN-care: A secure IoT-based modern healthcare system using body sensor network. IEEE Sens. J. 2016, 16, 1368–1376. [Google Scholar] [CrossRef]
- Puri, C.; et al. iCarMa: Inexpensive cardiac arrhythmia management—An IoT healthcare analytics solution. Proc. IoT Health 2016, 3–8. [Google Scholar]
- Azimi, I.; Anzanpour, A.; Rahmani, A.M.; Liljeberg, P.; Tenhunen, H. Self-aware early warning score system for IoT-based personalized healthcare. In eHealth 360 o; Springer: Cham, Switzerland, 2017; pp. 49–55. [Google Scholar]
- Singh, M.P.; Priyadarshi, R.; Sharma, P.; Thakur, A. Small size rectangular microstrip patch antenna with a cross slot using SIW. In Proceedings of the 2017 Fourth International Conference on Image Information Processing (ICIIP), Shimla, India, 21–23 December 2017; IEEE; pp. 1–4. [Google Scholar]
- Laplante, P.A.; Laplante, N. The Internet of Things in Healthcare: Potential Applications and Challenges. It Prof. 2016, 18, 2–4. [Google Scholar] [CrossRef]
- Botta, A.; de Donato, W.; Persico, V.; Pescapé, A. On the integration of cloud computing and Internet of Things. Proc. FiCloud 2014, 23–30. [Google Scholar]
- Puliafito, A.; Celesti, A.; Villari, M.; Fazio, M. Towards the Integration between IoT and Cloud Computing: An Approach for the Secure Self-Configuration of Embedded Devices. Int. J. Distrib. Sens. Networks 2015, 11. [Google Scholar] [CrossRef]
- Botta, A.; de Donato, W.; Persico, V.; Pescapé, A. Integration of Cloud computing and Internet of Things: A survey. Futur. Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Hassanalieragh, M.; Page, A.; Soyata, T.; Sharma, G.; Aktas, M.; Mateos, G.; Kantarci, B.; Andreescu, S. Health monitoring and management using Internet-of-Things (IoT) sensing with cloud-based processing: Opportunities and challenges. In Proceedings of the 2015 IEEE International Conference on Services Computing, New York, NY, USA, 27 June–2 July 2015; pp. 285–292. [Google Scholar] [CrossRef]
- Singh, L.; Kumar, A.; Priyadarshi, R. Performance and comparison analysis of image processing based forest fire detection. In Nanoelectronics, Circuits and Communication Systems: Proceeding of NCCS 2018; Springer: Singapore, 2020; pp. 473–479. [Google Scholar]
- Biswas, S.; Anisuzzaman, *!!! REPLACE !!!*; Akhter, T.; Kaiser, M.S.; Mamun, S.A. Cloud based healthcare application architecture and electronic medical record mining: An integrated approach to improve healthcare system. Proc. ICCIT 2014, 286–291. [Google Scholar]
- Pathinarupothi, R.K.; Ramesh, M.V.; Rangan, E. Multi-layer architectures for remote health monitoring. Proc. HealthCom 2016, 1–6. [Google Scholar]
- Hossain, M.S.; Muhammad, G. Cloud-assisted Industrial Internet of Things (IIoT)—Enabled framework for health monitoring. Comput. Netw. 2016, 101, 192–202. [Google Scholar] [CrossRef]
- Suciu, G.; Suciu, V.; Martian, A.; Craciunescu, R.; Vulpe, A.; Marcu, I.; Halunga, S.; Fratu, O. Big data Internet of Things and cloud convergence—An architecture for secure e-health applications. J. Med. Syst. 2015, 39, 141. [Google Scholar] [CrossRef] [PubMed]
- Ma, Y.; Wang, Y.; Yang, J.; Miao, Y.; Li, W. Big Health Application System based on Health Internet of Things and Big Data. IEEE Access 2017, 5, 7885–7897. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Singh, M.P.; Tripathi, H.; Sharma, P. Design and performance analysis of vivaldi antenna at very high frequency. In Proceedings of the 2017 Fourth International Conference on Image Information Processing (ICIIP), Shimla, India, 21–23 December 2017; IEEE, 2017. [Google Scholar]
- Páez, D.G.; Aparicio, F.; de Buenaga, M.; Ascanio, J.R. Big data and IoT for chronic patients monitoring. In Computing and Ambient Intelligence. Personalisation and User Adapted Services; Springer: Cham, Switzerland, 2014; pp. 416–423. [Google Scholar]
- Ji, Z.; Ganchev, I.; O’droma, M.; Zhang, X.; Zhang, X. A Cloud-Based X73 Ubiquitous Mobile Healthcare System: Design and Implementation. Sci. World J. 2014, 2014, 1–14. [Google Scholar] [CrossRef] [PubMed]
- Ochian, A.; Suciu, G.; Fratu, O.; Voicu, C.; Suciu, V. An overview of cloud middleware services for interconnection of healthcare platforms. Proc. ICComm 2014, 1–4. [Google Scholar]
- Nepal, S.; Ranjan, R.; Choo, K.-K.R. Trustworthy Processing of Healthcare Big Data in Hybrid Clouds. IEEE Cloud Comput. 2015, 2, 78–84. [Google Scholar] [CrossRef]
- Vishnu Anugrahith, S.; et al. A novel deployment scheme to enhance the coverage in wireless sensor network. In Proceedings of the Fourth International Conference on Microelectronics, Computing and Communication Systems: MCCS 2019; Springer: Singapore, 2021. [Google Scholar]
- Aazam, M.; Khan, I.; Alsaffar, A.A.; Huh, E.-N. Cloud of Things: Integration of IoT with cloud computing. In Robots and Sensor Clouds; Springer: Cham, Switzerland, 2016; pp. 77–94. [Google Scholar]
- Abawajy, J.H.; Hassan, M.M. Federated Internet of Things and Cloud Computing Pervasive Patient Health Monitoring System. IEEE Commun. Mag. 2017, 55, 48–53. [Google Scholar] [CrossRef]
- Dehury, C.K.; Sahoo, P.K. Design and implementation of a novel service management framework for IoT devices in cloud. J. Syst. Softw. 2016, 119, 149–161. [Google Scholar] [CrossRef]
- Doukas, C.; Maglogiannis, I. Bringing IoT and Cloud Computing towards Pervasive Healthcare. In Proceedings of the 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Palermo, Italy, 4–6 July 2012; pp. 922–926. [Google Scholar] [CrossRef]
- Alamri, A.; Ansari, W.S.; Hassan, M.M.; Hossain, M.S.; Alelaiwi, A. A Survey on Sensor-Cloud: Architecture, Applications, and Approaches. Int. J. Distrib. Sens. Networks 2013, 9. [Google Scholar] [CrossRef]
- Rahul, P.; Kumar, R.R. An energy-efficient LEACH routing protocol for wireless sensor networks. In Proceedings of the Fourth International Conference on Microelectronics, Computing and Communication Systems: MCCS 2019; Springer: Singapore, 2021. [Google Scholar]
- Hassan, M.M.; Albakr, H.S.; Al-Dossari, H. A cloud-assisted Internet of Things framework for pervasive healthcare in smart city environment. Proc. EMASC 2014, 9–13. [Google Scholar]
- Muhammad, G.; Rahman, S.M.M.; Alelaiwi, A.; Alamri, A. Smart Health Solution Integrating IoT and Cloud: A Case Study of Voice Pathology Monitoring. IEEE Commun. Mag. 2017, 55, 69–73. [Google Scholar] [CrossRef]
- Bagula, A.; et al. Cloud based patient prioritization as service in public health care. Proc. ITU-WT 2016, 1–8. [Google Scholar]
- Sanjeev, K.; et al. Performance analysis of novel energy aware routing in wireless sensor network. In Nanoelectronics, Circuits and Communication Systems: Proceeding of NCCS 2018; Springer: Singapore, 2020. [Google Scholar]
- Hasan, R.; Hossain, M.M.; Khan, R. Aura: An IoT based cloud infrastructure for localized mobile computation outsourcing. Proc. MobileCloud 2015, 183–188. [Google Scholar]
- Tabish, R.; et al. A 3G/WiFi-enabled 6LoWPAN-based U-healthcare system for ubiquitous real-time monitoring and data logging. Proc. MECBME 2014, 277–280. [Google Scholar]
- Khoi, N.M.; Saguna, S.; Mitra, K.; Åhlund, C. IReHMo: An efficient IoT-based remote health monitoring system for smart regions. Proc. HealthCom 2015, 563–568. [Google Scholar]
- Gomes, B.; Muniz, L.; da Silva e Silva, F.J.; Rios, L.E.T.; Endler, M. A comprehensive cloud-based IoT software infrastructure for ambient assisted living. Proc. CloudTech 2015, 1–8. [Google Scholar]
- Mohammed, J.; et al. Internet of Things: Remote patient monitoring using Web services and cloud computing. Proc. iThings 2014, 256–263. [Google Scholar]
- Fazio, M.; Celesti, A.; Márquez, F.G.; Glikson, A.; Villari, M. Exploiting the FIWARE cloud platform to develop a remote patient monitoring system. Proc. ISCC 2015, 264–270. [Google Scholar]
- Wu, T.; Wu, F.; Redoute, J.M.; Yuce, M.R. An autonomous wireless body area network implementation towards IoT connected healthcare applications. IEEE Access 2017, 5, 11413–11422. [Google Scholar] [CrossRef]
- Randheer, S.K.; Kumar, S.; Priyadarshi, R. Energy-aware clustering in wireless sensor networks. In Nanoelectronics, Circuits and Communication Systems: Proceeding of NCCS 2018; Springer: Singapore, 2020. [Google Scholar]
- Gupta, P.K.; Maharaj, B.T.; Malekian, R. A novel and secure IoT based cloud centric architecture to perform predictive analysis of users activities in sustainable health centres. Multimedia Tools Appl. 2017, 76, 18489–18512. [Google Scholar] [CrossRef]
- Park, J.; Kwon, H.; Kang, N. IoT–Cloud collaboration to establish a secure connection for lightweight devices. Wirel. Netw. 2017, 23, 681–692. [Google Scholar] [CrossRef]
- Hassan, M.M.; Lin, K.; Yue, X.; Wan, J. A multimedia healthcare data sharing approach through cloud-based body area network. Futur. Gener. Comput. Syst. 2017, 66, 48–58. [Google Scholar] [CrossRef]
- Chen, M.; Zhang, Y.; Li, Y.; Hassan, M.M.; Alamri, A. AIWAC: affective interaction through wearable computing and cloud technology. IEEE Wirel. Commun. 2015, 22, 20–27. [Google Scholar] [CrossRef]
- Chen, M.; Ma, Y.; Li, Y.; Wu, D.; Zhang, Y.; Youn, C.-H. Wearable 2.0: Enabling Human-Cloud Integration in Next Generation Healthcare Systems. IEEE Commun. Mag. 2017, 55, 54–61. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Nath, V. A novel diamond–hexagon search algorithm for motion estimation. Microsyst. Technol. 2019, 25, 4587–4591. [Google Scholar] [CrossRef]
- Xu, B.; Xu, L.; Cai, H.; Jiang, L.; Luo, Y.; Gu, Y. The design of an m-Health monitoring system based on a cloud computing platform. Enterp. Inf. Syst. 2017, 11, 17–36. [Google Scholar] [CrossRef]
- La, H.J.; Jung, H.T.; Kim, S.D. Extensible disease diagnosis cloud platform with medical sensors and IoT devices. Proc. FiCloud 2015, 371–378. [Google Scholar]
- Mulfari, D.; Celesti, A.; Fazio, M.; Villari, M.; Puliafito, A. Achieving assistive technology systems based on IoT devices in cloud computing. EAI Endorsed Trans. Cloud Syst. 2015, 1, e4. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Buyya, R. Fog Computing: Helping the Internet of Things Realize Its Potential. Computer 2016, 49, 112–116. [Google Scholar] [CrossRef]
- Rahul, P.; Bhardwaj, A. Node non-uniformity for energy effectual coordination in wsn. Int. J. Inf. Technol. Secur. 2017, 9. [Google Scholar]
- Shi, Y.; Ding, G.; Wang, H.; Roman, H.E.; Lu, S. The fog computing service for healthcare. Proc. Ubi-HealthTech 2015, 1–5. [Google Scholar]
- Gia, T.N.; Jiang, M.; Sarker, V.K.; Rahmani, A.M.; Westerlund, T.; Liljeberg, P.; Tenhunen, H. Low-cost fog-assisted health-care IoT system with energy-efficient sensor nodes. Proc. IWCMC 2017, 1765–1770. [Google Scholar]
- Lake, D.; Milito, R.; Morrow, M.; Vargheese, R.; Systems, C. Internet of Things: Architectural Framework for eHealth Security. J. ICT Stand. 2014, 1, 301–328. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Singh, M.P.; Bhardwaj, A.; Sharma, P. Amount of fading analysis for composite fading channel using Holtzman approximation. In Proceedings of the 2017 fourth international conference on image information processing (ICIIP), IEEE. Shimla, India, 21-23 December 2017. [Google Scholar]
- Mahmud, M.; Kaiser, M.S.; Rahman, M.M.; Shabut, A.; Al-Mamun, S.; Hussain, A. A Brain-Inspired Trust Management Model to Assure Security in a Cloud Based IoT Framework for Neuroscience Applications. Cogn. Comput. 2018, 10, 864–873. [Google Scholar] [CrossRef]
- Dineshkumar, P.; SenthilKumar, R.; Sujatha, K.; Ponmagal, R.S.; Rajavarman, V.N. Big data analytics of IoT based health care monitoring system. Proc. UPCON 2016, 55–60. [Google Scholar]
- Mahmud, M.; Kaiser, M.S.; Hussain, A.; Vassanelli, S. Applications of Deep Learning and Reinforcement Learning to Biological Data. IEEE Trans. Neural Networks Learn. Syst. 2018, 29, 2063–2079. [Google Scholar] [CrossRef] [PubMed]
- Priyadarshi, R.; Soni, S.K.; Bhadu, R.; Nath, V. Performance analysis of diamond search algorithm over full search algorithm. Microsyst. Technol. 2017, 24, 2529–2537. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutorials 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Sutar, S.; Koul, R.; Suryavanshi, R. Integration of smart phone and IOT for development of smart public transportation system. In Proceedings of the 2016 International Conference on Internet of Things and Applications (IOTA), Pune, India, 22–24 January 2016; pp. 73–78. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K.-S. The Internet of Things for Health Care: A Comprehensive Survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Feng, S.; Setoodeh, P.; Haykin, S. Smart Home: Cognitive Interactive People-Centric Internet of Things. IEEE Commun. Mag. 2017, 55, 34–39. [Google Scholar] [CrossRef]
- Rahul, P.; Yadav, S.; Bilyan, D. Performance and comparison analysis of MIEEP routing protocol over adapted LEACH protocol. Smart Comput. Strateg. Theor. Pract. Asp. 2019, 237–245. [Google Scholar]
- Etim, I.E.; Lota, J. Power control in cognitive radios Internet-of Things (IoT) for factories and industrial automation. In Proceedings of the Annual Conference of the IEEE Industrial Electronics Society, Florence, Italy, 23–26 October 2016; pp. 4701–4705. [Google Scholar]
- Li, X.; Huang, Q.; Wu, D. Distributed large-scale co-simulation for IoT-aided smart grid control. IEEE Access 2017, 5, 19951–19960. [Google Scholar] [CrossRef]
- Rodrigues, J.J.P.C.; Sendra, S.; de la Torre, I. e-Health Systems—Theory Advances and Technical Applications; Elsevier: Amsterdam, The Netherlands, 2016; p. 296. [Google Scholar]
- Priyadarshi, R.; et al. A hexagonal network division approach for reducing energy hole issue in WSN. Eur. J. Pure Appl. Math. 2018, 118. [Google Scholar]
- Alberti, A.M.; Scarpioni, G.D.; Magalhaes, V.J.; Cerqueira, A.; Rodrigues, J.J.; Righi, R.d.R. Advancing NovaGenesis architecture towards future Internet of Things. IEEE Internet Things J. 2017. [Google Scholar] [CrossRef]
- Elmisery, A.M.; Rho, S.; Botvich, D. A fog based middleware for automated compliance with OECD privacy principles in Internet of healthcare things. IEEE Access 2016, 4, 8418–8441. [Google Scholar] [CrossRef]
- Khairuddin, A.; Azir, K.F.K.; Kan, P.E. Limitations and future of electrocardiography devices: A review and the perspective from the Internet of Things. In Proceedings of the 2017 International Conference on Research and Innovation in Information Systems (ICRIIS), Langkawi, Malaysia, 16–17 July 2017; pp. 1–7. [Google Scholar]
- Priyadarshi, R.; Tripathi, H.; Bhardwaj, A.; Thakur, A. Performance metric analysis of modified LEACH routing protocol in wireless sensor network. Int. J. Eng. Technol. 2017, 7, 196–201. [Google Scholar] [CrossRef]
- Li, C.; Hu, X.; Zhang, L. The IoT-based heart disease monitoring system for pervasive healthcare service. Procedia Comput. Sci. 2017, 112, 2328–2334. [Google Scholar] [CrossRef]
- Vergara, P.M.; de la Cal, E.; Villar, J.R.; González, V.M.; Sedano, J. An IoT platform for epilepsy monitoring and supervising. J. Sensors 2017, 2017. [Google Scholar] [CrossRef]
- Deshkar, S.; Thanseeh, R.A.; Menon, V.G. A review on IoT based m-Health systems for diabetes. Int. J. Comput. Sci. Telecommun. 2017, 8, 13–18. [Google Scholar]
- Catarinucci, L.; et al. , An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Rahul, P.; et al. Energy efficient leach routing in wireless sensor network. Int. J. Pure Appl. Math. 2018, 118, 135–142. [Google Scholar]
- Yin, Y.; Zeng, Y.; Chen, X.; Fan, Y. The Internet of Things in healthcare: An overview. J. Ind. Inf. Integr. 2016, 1, 3–13. [Google Scholar] [CrossRef]
- Woo, M.W.; Lee, J.; Park, K. A reliable IoT system for personal healthcare devices. Future Generat. Comput. Syst. 2018, 78, 326–640. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Chang, V.; Badaroglu, M.; Constant, N.; Mankodiya, K. Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare. Future Generat. Comput. Syst. 2018, 78, 659–676. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Gupta, B. Area Coverage Optimization in Three-Dimensional Wireless Sensor Network. Wirel. Pers. Commun. 2021, 117, 843–865. [Google Scholar] [CrossRef]
- Firouzi, F.; Rahmani, A.M.; Mankodiya, K.; Badaroglu, M.; Merrett, G.; Wong, P.; Farahani, B. Internet-of-Things and big data for smarter healthcare: From device to architecture, applications and analytics. Futur. Gener. Comput. Syst. 2018, 78, 583–586. [Google Scholar] [CrossRef]
- IEEE, 802.15.4-2015; IEEE Standard for Low-Rate Wireless Networks. 2015.
- Machado, F.M.; Koehler, I.M.; Ferreira, M.S.; Sovierzoski, M.A. An mHealth remote monitor system approach applied to MCC using ECG signal in an android application. In New Advances in Information Systems and Technologies; 2016; pp. 43–49. [Google Scholar]
- Maia, P.; et al. A Web platform for interconnecting body sensors and improving health care. Procedia Comput. Sci. 2014, 40, 135–142. [Google Scholar] [CrossRef]
- Rahul, P.; Soni, S.K.; Sharma, P. An enhanced GEAR protocol for wireless sensor networks. In Nanoelectronics, Circuits and Communication Systems: Proceeding of NCCS 2017; Springer: Singapore, 2019. [Google Scholar]
- Lima, R.C.; Feitosa, C.H.; Pereira CA, P.; Aranha, E.R. Wireless sensor networks application on remote healthcare monitoring. Rev. Interdiscipl. Tecnol. Edu. 2016, 2, 1–5. [Google Scholar]
- Matar, G.; Lina, J.-M.; Carrier, J.; Riley, A.; Kaddoum, G. Internet of Things in sleep monitoring: An application for posture recognition using supervised learning. In Proceedings of the International Conference on e-Health Networking, Applications and Services, Munich, Germany, 14–16 September 2016; pp. 1–6. [Google Scholar]
- Istepanian, R.S.H.; Hu, S.; Philip, N.Y.; Sungoor, A. The potential of Internet of m-health Things ‘m-IoT’ for non-invasive glucose level sensing. In Proceedings of the Annual International Conference of the IEEE Engineering in Medicine and Biology Society, Boston, MA, USA, 30 August—3 September 2011; pp. 5264–5266. [Google Scholar]
- Priyadarshi, R.; Gupta, B. Coverage area enhancement in wireless sensor network. Microsyst. Technol. 2020, 26, 1417–1426. [Google Scholar] [CrossRef]
- Senthilkumar, R.; Ponmagal, R.S.; Sujatha, K. Efficient health care monitoring and emergency management system using IoT. Int. J. Control Theory Appl. 2016, 9, 137–145. [Google Scholar]
- Msayib, Y.; Gaydecki, P.; Callaghan, M.; Dale, N.; Ismail, S. An intelligent remote monitoring system for total knee arthroplasty patients. J. Med. Syst. 2017, 41, 90. [Google Scholar] [CrossRef]
- Kitsiou, S.; Thomas, M.; Marai, G.E.; Maglaveras, N.; Kondos, G.; Arena, R.; Gerber, B. Development of an innovative mHealth platform for remote physical activity monitoring and health coaching of cardiac rehabilitation Patients. In Proceedings of the IEEE EMBS International Conference on Biomedical & Health Informatics (BHI), Orlando, FL, USA, 16–19 February 2017; pp. 133–136. [Google Scholar]
- Rawat, P.; Chauhan, S.; Priyadarshi, R. A Novel Heterogeneous Clustering Protocol for Lifetime Maximization of Wireless Sensor Network. Wirel. Pers. Commun. 2020, 117, 825–841. [Google Scholar] [CrossRef]
- Khan, S.F. Health care monitoring system in Internet of Things (IoT) by using RFID. In Proceedings of the International Conference on Industrial Technology and Management (ICITM), Cambridge, UK, 7–10 March 2017; pp. 198–204. [Google Scholar]
- Qi, J.; Yang, P.; Min, G.; Amft, O.; Dong, F.; Xu, L. Advanced internet of things for personalised healthcare systems: A survey. Pervasive Mob. Comput. 2017, 41, 132–149. [Google Scholar] [CrossRef]
- Alshurafa, N.; Sideris, C.; Pourhomayoun, M.; Kalantarian, H.; Sarrafzadeh, M.; Eastwood, J.-A. Remote Health Monitoring Outcome Success Prediction Using Baseline and First Month Intervention Data. IEEE J. Biomed. Heal. Informatics 2017, 21, 507–514. [Google Scholar] [CrossRef]
- Abawajy, J.H.; Hassan, M.M. Federated Internet of Things and Cloud Computing Pervasive Patient Health Monitoring System. IEEE Commun. Mag. 2017, 55, 48–53. [Google Scholar] [CrossRef]
- Ara, A.; Al-Rodhaan, M.; Tian, Y.; Al-Dhelaan, A. A Secure Privacy-Preserving Data Aggregation Scheme Based on Bilinear ElGamal Cryptosystem for Remote Health Monitoring Systems. IEEE Access 2017, 5, 12601–12617. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Singh, L.; Singh, A.; Thakur, A. SEEN: Stable Energy Efficient Network for Wireless Sensor Network. In Proceedings of the 2018 5th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 22–23 February 2018; pp. 338–342. [Google Scholar]
- Nkenyereye, L.; Jang, J.-W. Performance Evaluation of Server-side JavaScript for Healthcare Hub Server in Remote Healthcare Monitoring System. Procedia Comput. Sci. 2016, 98, 382–387. [Google Scholar] [CrossRef]
- Al Mamun, K.A.; Alhussein, M.; Sailunaz, K.; Islam, M.S. Cloud based framework for Parkinson’s disease diagnosis and monitoring system for remote healthcare applications. Futur. Gener. Comput. Syst. 2017, 66, 36–47. [Google Scholar] [CrossRef]
- Ganapathy, R.; Grewal, A.; Castleman, J. Remote monitoring of blood pressure to reduce the risk of preeclampsia related complications with an innovative use of mobile technology. Pregnancy Hypertens. 2016, 6, 263–265. [Google Scholar] [CrossRef]
- Silva, B.M.; Rodrigues, J.J.; Díez, I.d.l.T.; López-Coronado, M.; Saleem, K. Mobile-health: A review of current state in 2015. J. Biomed. Informatics 2015, 56, 265–272. [Google Scholar] [CrossRef]
- Murakami, A.; Kobayashi, L.O.M.A.; Tachinardi, U.; Gutierrez, M.A.; Furuie, S.S.; Pires, F.A. Acesso a informações médicas através do uso de sistemas de computação móvel. In Congresso Brasileiro de Informática na Saúde; Sociedade Brasileira de Informática em Saúde: Ribeirão Preto, Brazil, 2004. [Google Scholar]
- Amulya, A.; et al. 2-D coverage optimization in WSN using a novel variant of particle swarm optimisation. In Proceedings of the 2020 7th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 27-28 February 2020; IEEE, 2020. [Google Scholar]
- da Costa, T.M.; Salomão, P.L.; Martha, A.S.; Pisa, I.T.; Sigulem, D. The impact of short message service text messages sent as appointment reminders to patients’ cell phones at outpatient clinics in São Paulo, Brazil. Int. J. Med Informatics 2009, 79, 65–70. [Google Scholar] [CrossRef] [PubMed]
- Shellington, E.M.; Felfeli, T.; Shigematsu, R.; Gill, D.P.; Petrella, R.J. HealtheBrain: an innovative smartphone application to improve cognitive function in older adults. mHealth 2017, 3. [Google Scholar] [CrossRef] [PubMed]
- Crema, C.; Depari, A.; Flammini, A.; Sisinni, E.; Vezzoli, A.; Bellagente, P. Virtual Respiratory Rate Sensors: An Example of A Smartphone-Based Integrated and Multiparametric mHealth Gateway. IEEE Trans. Instrum. Meas. 2017, 66, 2456–2463. [Google Scholar] [CrossRef]
- Aranki, D.; Kurillo, G.; Yan, P.; Liebovitz, D.M.; Bajcsy, R. Real-Time Tele-Monitoring of Patients with Chronic Heart-Failure Using a Smartphone: Lessons Learned. IEEE Trans. Affect. Comput. 2016, 7, 206–219. [Google Scholar] [CrossRef]
- Rawat, P.; Chauhan, S.; Priyadarshi, R. Energy-Efficient Clusterhead Selection Scheme in Heterogeneous Wireless Sensor Network. J. Circuits, Syst. Comput. 2020, 29, 2050204. [Google Scholar] [CrossRef]
- Lorenzi, P.; Rao, R.; Romano, G.; Kita, A.; Irrera, F. Mobile Devices For The Real Time Detection Of Specific Human Motion Disorders. IEEE Sens. J. 2016, 16, 8220–8227. [Google Scholar] [CrossRef]
- Ren, Y.; Chen, Y.; Chuah, M.C.; Yang, J. User Verification Leveraging Gait Recognition for Smartphone Enabled Mobile Healthcare Systems. IEEE Trans. Mob. Comput. 2015, 14, 1961–1974. [Google Scholar] [CrossRef]
- Silsupadol, P.; Teja, K.; Lugade, V. Reliability and validity of a smartphone-based assessment of gait parameters across walking speed and smartphone locations: Body, bag, belt, hand, and pocket. Gait Posture 2017, 58, 516–522. [Google Scholar] [CrossRef] [PubMed]
- Pepa, L.; Verdini, F.; Spalazzi, L. Gait parameter and event estimation using smartphones. Gait Posture 2017, 57, 217–223. [Google Scholar] [CrossRef] [PubMed]
- Priyadarshi, R.; Gupta, B.; Anurag, A. Wireless Sensor Networks Deployment: A Result Oriented Analysis. Wirel. Pers. Commun. 2020, 113, 843–866. [Google Scholar] [CrossRef]
- Osmani, V. Smartphones in Mental Health: Detecting Depressive and Manic Episodes. IEEE Pervasive Comput. 2015, 14, 10–13. [Google Scholar] [CrossRef]
- Alshurafa, N.; Eastwood, J.-A.; Nyamathi, S.; Liu, J.J.; Xu, W.; Ghasemzadeh, H.; Pourhomayoun, M.; Sarrafzadeh, M. Improving Compliance in Remote Healthcare Systems Through Smartphone Battery Optimization. IEEE J. Biomed. Heal. Inform. 2015, 19, 57–63. [Google Scholar] [CrossRef]
- Seeger, C.; Van Laerhoven, K.; Buchmann, A. MyHealthAssistant: An Event-driven Middleware for Multiple Medical Applications on a Smartphone-Mediated Body Sensor Network. IEEE J. Biomed. Heal. Inform. 2015, 19, 752–760. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Rawat, P.; Nath, V.; Acharya, B.; Shylashree, N. Three level heterogeneous clustering protocol for wireless sensor network. Microsyst. Technol. 2020, 26, 3855–3864. [Google Scholar] [CrossRef]
- Poon, T.W.K.; Friesen, M.R. Algorithms for Size and Color Detection of Smartphone Images of Chronic Wounds for Healthcare Applications. IEEE Access 2015, 3, 1799–1808. [Google Scholar] [CrossRef]
- Wang, L.; Pedersen, P.C.; Strong, D.M.; Tulu, B.; Agu, E.; Ignotz, R. Smartphone-Based Wound Assessment System for Patients With Diabetes. IEEE Trans. Biomed. Eng. 2015, 62, 477–488. [Google Scholar] [CrossRef]
- Velikova, M.; Smeets, R.L.; van Scheltinga, J.T.; Lucas, P.J.; Spaanderman, M. Smartphone-based analysis of biochemical tests for health monitoring support at home. Heal. Technol. Lett. 2014, 1, 92–97. [Google Scholar] [CrossRef]
- Higgins, J.P. Smartphone Applications for Patients' Health and Fitness. Am. J. Med. 2016, 129, 11–19. [Google Scholar] [CrossRef] [PubMed]
- Matarazzo, T.; Vazifeh, M.; Pakzad, S.; Santi, P.; Ratti, C. Smartphone data streams for bridge health monitoring. Procedia Eng. 2017, 199, 966–971. [Google Scholar] [CrossRef]
- Firth, J.; Torous, J.; Nicholas, J.; Carney, R.; Rosenbaum, S.; Sarris, J. Can smartphone mental health interventions reduce symptoms of anxiety? A meta-analysis of randomized controlled trials. J. Affect. Disord. 2017, 218, 15–22. [Google Scholar] [CrossRef] [PubMed]
- Priyadarshi, R.; Soni, S.K.; Nath, V. Energy efficient cluster head formation in wireless sensor network. Microsyst. Technol. 2018, 24, 4775–4784. [Google Scholar] [CrossRef]
- Chao, E.; Meenan, C.K.; Ferris, L.K. Smartphone-Based Applications for Skin Monitoring and Melanoma Detection. Dermatol. Clin. 2017, 35, 551–557. [Google Scholar] [CrossRef] [PubMed]
- Brayboy, L.M.; Sepolen, A.; Mezoian, T.; Schultz, L.; Landgren-Mills, B.S.; Spencer, N.; Wheeler, C.; Clark, M.A. Girl Talk: A Smartphone Application to Teach Sexual Health Education to Adolescent Girls. J. Pediatr. Adolesc. Gynecol. 2017, 30, 23–28. [Google Scholar] [CrossRef] [PubMed]
- Costa, S.E.P.; Rodrigues, J.J.P.C.; Silva, B.M.C.; Isento, J.N.; Corchado, J.M. Integration of Wearable Solutions in AAL Environments with Mobility Support. J. Med Syst. 2015, 39. [Google Scholar] [CrossRef]
- Valera, A.J.J.; Zamora, M.A.; Skarmeta, A.F.G. An architecture based on Internet of Things to support mobility and security in medical environments. In Proceedings of the 7th IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 9–12 January 2010; pp. 1–5. [Google Scholar]
- Priyadarshi, R.; Singh, L.; Singh, A. A novel HEED protocol for wireless sensor networks. In Proceedings of the 2018 5th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 22-23 February 2018; IEEE, 2018. [Google Scholar]
- Ray, P.P. Home health hub Internet of Things (H3 IoT): An architectural framework for monitoring health of elderly people. In Proceedings of the International Conference on Science Engineering and Management Research, Chennai, India, 27–29 November 2014; pp. 1–3. [Google Scholar]
- Lopes, I.C.; Vaidya, B.; Rodrigues, J.J.P.C. Towards an autonomous fall detection and alerting system on a mobile and pervasive environment. Telecommun. Syst. 2013, 52, 2299–2310. [Google Scholar] [CrossRef]
- Horta, E.T.; Lopes, I.C.; Rodrigues, J.J.P.C. Ubiquitous mHealth approach for biofeedback monitoring with falls detection techniques and falls prevention methodologies. In Mobile Health—mHealth; Springer: New York, NY, USA, 2015; Volume 5, pp. 43–75. [Google Scholar]
- Mano, L.; Funes, M.; Volpato, T.; Neto, J. Explorando tecnologias de IoT no contexto de health smart home: Uma abordagem para detecção de quedas em pessoas idosas. J. Adv. Theor. Appl. Inform. 2016, 2, 46–57. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Rawat, P.; Nath, V. Energy dependent cluster formation in heterogeneous wireless sensor network. Microsyst. Technol. 2019, 25, 2313–2321. [Google Scholar] [CrossRef]
- Mainetti, L.; Patrono, L.; Secco, A.; Sergi, I. An IoT-aware AAL system for elderly people. In Proceedings of the International Multidisciplinary Conference on Computer and Energy Science (SpliTech), Split, Croatia, 13–15 July 2016; pp. 1–6. [Google Scholar]
- Silva, L.A.; Costa, K.A.P.; Ribeiro, P.B.; Fernandes, D.; Papa, J.P. On the Feasibility of Optimum-Path Forest in the Context of Internet-of-Things-Based Applications. Recent Patents Signal Process. 2016, 5, 52–60. [Google Scholar] [CrossRef]
- Pereira, C.R.; Nakamura, R.Y.; Costa, K.A.; Papa, J.P. An Optimum-Path Forest framework for intrusion detection in computer networks. Eng. Appl. Artif. Intell. 2012, 25, 1226–1234. [Google Scholar] [CrossRef]
- Costa, K.A.; Pereira, L.A.; Nakamura, R.Y.; Pereira, C.R.; Papa, J.P.; Falcão, A.X. A nature-inspired approach to speed up optimum-path forest clustering and its application to intrusion detection in computer networks. Inf. Sci. 2015, 294, 95–108. [Google Scholar] [CrossRef]
- Bleda, A.L.; Fernandez-Luque, F.J.; Rosa, A.; Zapata, J.; Maestre, R. Smart Sensory Furniture Based on WSN for Ambient Assisted Living. IEEE Sensors J. 2017, 17, 5626–5636. [Google Scholar] [CrossRef]
- Liu, W.; Shoji, Y.; Shinkuma, R. Logical Correlation-Based Sleep Scheduling for WSNs in Ambient-Assisted Homes. IEEE Sensors J. 2017, 17, 3207–3218. [Google Scholar] [CrossRef]
- Rafferty, J.; Nugent, C.D.; Liu, J.; Chen, L. From Activity Recognition to Intention Recognition for Assisted Living Within Smart Homes. IEEE Trans. Hum.-Mach. Syst. 2017, 47, 368–379. [Google Scholar] [CrossRef]
- Schwiegelshohn, F.; Hubner, M.; Wehner, P.; Gohringer, D. Tackling The New Health-Care Paradigm Through Service Robotics: Unobtrusive, efficient, reliable, and modular solutions for assisted-living environments. IEEE Consum. Electron. Mag. 2017, 6, 34–41. [Google Scholar] [CrossRef]
- Zdravevski, E.; Lameski, P.; Trajkovik, V.; Kulakov, A.; Chorbev, I.; Goleva, R.; Pombo, N.; Garcia, N. Improving Activity Recognition Accuracy in Ambient-Assisted Living Systems by Automated Feature Engineering. IEEE Access 2017, 5, 5262–5280. [Google Scholar] [CrossRef]
- Bi, J.; Yuan, H.; Tie, M.; Song, X. Heuristic virtual machine allocation for multi-tier Ambient Assisted Living applications in a cloud data center. China Commun. 2016, 13, 56–65. [Google Scholar] [CrossRef]
- Yao, B.; Hagras, H.; Alghazzawi, D.; Alhaddad, M.J. A Big Bang–Big Crunch Type-2 Fuzzy Logic System for Machine-Vision-Based Event Detection and Summarization in Real-World Ambient-Assisted Living. IEEE Trans. Fuzzy Syst. 2016, 24, 1307–1319. [Google Scholar] [CrossRef]
- Erden, F.; Velipasalar, S.; Alkar, A.Z.; Cetin, A.E. Sensors in Assisted Living: A survey of signal and image processing methods. IEEE Signal Process. Mag. 2016, 33, 36–44. [Google Scholar] [CrossRef]
- Hossain, M.A.; Parra, J.; Rahman, S.M.M.; Alamri, A.; Ullah, S.; Mouftah, H.T. From Sensing to Alerting: a Pathway of RESTful Messaging in Ambient Assisted Living. IEEE Wirel. Commun. 2016, 23, 102–110. [Google Scholar] [CrossRef]
- Parada, R.; Melia-Segui, J.; Morenza-Cinos, M.; Carreras, A.; Pous, R. Using RFID to Detect Interactions in Ambient Assisted Living Environments. IEEE Intell. Syst. 2015, 30, 16–22. [Google Scholar] [CrossRef]
- Machado, A.; Maran, V.; Augustin, I.; Wives, L.K.; de Oliveira, J.P.M. Reactive, proactive, and extensible situation-awareness in ambient assisted living. Expert Syst. Appl. 2017, 76, 21–35. [Google Scholar] [CrossRef]
- Garcés, L.; Ampatzoglou, A.; Avgeriou, P.; Nakagawa, E.Y. Quality attributes and quality models for ambient assisted living software systems: A systematic mapping. Inf. Softw. Technol. 2017, 82, 121–138. [Google Scholar] [CrossRef]
- Roy, P.C.; Abidi, S.R.; Abidi, S.S.R. Possibilistic activity recognition with uncertain observations to support medication adherence in an assisted ambient living setting. Knowl.-Based Syst. 2017, 133, 156–173. [Google Scholar] [CrossRef]
- Demir, E.; Köseoğlu, E.; Sokullu, R.; Şeker, B. Smart Home Assistant for Ambient Assisted Living of Elderly People with Dementia. Procedia Comput. Sci. 2017, 113, 609–614. [Google Scholar] [CrossRef]
- Dobbins, C.; Rawassizadeh, R.; Momeni, E. Detecting physical activity within lifelogs towards preventing obesity and aiding ambient assisted living. Neurocomputing 2017, 230, 110–132. [Google Scholar] [CrossRef]
- Portocarrero, J.M.T.; Souza, W.L.; Demarzo, M.; Prado, A.F. Biblioteca digital brasileira da computação. Proc. X Workshop Inform. Méd. 2010. [Google Scholar]
- de Souza Rios, T.; da Silva Bezerra, R.M. WHMS4: An integrated model for health remote monitoring: A case study in nursing homes for the elderly. In Proceedings of the Iberian Conference on Information Systems and Technologies (CISTI), Aveiro, Portugal, 17–20 June 2015; pp. 1–6. [Google Scholar]
- Raad, M.W.; Sheltami, T.; Shakshuki, E. Ubiquitous tele-health system for elderly patients with Alzheimer’s. Procedia Comput. Sci. 2015, 52, 685–689. [Google Scholar] [CrossRef]
- Chen, M.; Ma, Y.; Li, Y.; Wu, D.; Zhang, Y.; Youn, C.-H. Wearable 2.0: Enabling human-cloud integration in next generation healthcare systems. IEEE Commun. Mag. 2017, 55, 54–61. [Google Scholar] [CrossRef]
- Li, J.; Zhou, H.; Zuo, D.; Hou, K.-M.; De Vaulx, C. Ubiquitous health monitoring and real-time cardiac arrhythmias detection: a case study. Bio-Medical Mater. Eng. 2014, 24, 1027–1033. [Google Scholar] [CrossRef]
- Thapliyal, H.; Khalus, V.; Labrado, C. Stress Detection and Management: A Survey of Wearable Smart Health Devices. IEEE Consum. Electron. Mag. 2017, 6, 64–69. [Google Scholar] [CrossRef]
- Spano, E.; Di Pascoli, S.; Iannaccone, G. Low-Power Wearable ECG Monitoring System for Multiple-Patient Remote Monitoring. IEEE Sensors J. 2016, 16, 5452–5462. [Google Scholar] [CrossRef]
- Liu, J.; Sun, W. Smart Attacks against Intelligent Wearables in People-Centric Internet of Things. IEEE Commun. Mag. 2016, 54, 44–49. [Google Scholar] [CrossRef]
- Huang, H.; Zhou, J.; Li, W.; Zhang, J.; Zhang, X.; Hou, G. Wearable indoor localisation approach in Internet of Things. IET Networks 2016, 5, 122–126. [Google Scholar] [CrossRef]
- de la Guia, E.; Camacho, V.L.; Orozco-Barbosa, L.; Lujan, V.M.B.; Penichet, V.M.R.; Perez, M.L. Introducing IoT and Wearable Technologies into Task-Based Language Learning for Young Children. IEEE Trans. Learn. Technol. 2016, 9, 366–378. [Google Scholar] [CrossRef]
- Pasluosta, C.F.; Gassner, H.; Winkler, J.; Klucken, J.; Eskofier, B.M. An Emerging Era in the Management of Parkinson's Disease: Wearable Technologies and the Internet of Things. IEEE J. Biomed. Heal. Informatics 2015, 19, 1873–1881. [Google Scholar] [CrossRef] [PubMed]
- Arias, O.; Wurm, J.; Hoang, K.; Jin, Y. Privacy and Security in Internet of Things and Wearable Devices. IEEE Trans. Multi-Scale Comput. Syst. 2015, 1, 99–109. [Google Scholar] [CrossRef]
- Sood, S.K.; Mahajan, I. Wearable IoT sensor based healthcare system for identifying and controlling chikungunya virus. Comput. Ind. 2017, 91, 33–44. [Google Scholar] [CrossRef] [PubMed]
- Cui, K.; Zhou, K.; Qiu, T.; Li, M.; Yan, L. A hierarchical combinatorial testing method for smart phone software in wearable IoT systems. Comput. Electr. Eng. 2017, 61, 250–265. [Google Scholar] [CrossRef]
- Sheng, Z.; Yang, S.; Yu, Y.; Vasilakos, A.V.; Mccann, J.A.; Leung, K.K. A survey on the ietf protocol suite for the internet of things: standards, challenges, and opportunities. IEEE Wirel. Commun. 2013, 20, 91–98. [Google Scholar] [CrossRef]
- de Carvalho Silva, J.; Rodrigues, J.J.P.C.; Alberti, A.M.; Solic, P.; Aquino, A.L.L. LoRaWAN—A low power WAN protocol for Internet of Things: A review and opportunities. Proceedings of International Multidisciplinary Conference on Computer and Energy Science, Split, Croatia, 12–14 July 2017; pp. 143–148. [Google Scholar]
- Bao, Y.; Tang, Z.; Li, H.; Zhang, Y. Computer vision and deep learning–based data anomaly detection method for structural health monitoring. Struct. Heal. Monit. 2019, 18, 401–421. [Google Scholar] [CrossRef]
- Heitner, B.; Obrien, E.J.; Yalamas, T.; Schoefs, F.; Leahy, C.; Décatoire, R. Updating probabilities of bridge reinforcement corrosion using health monitoring data. Eng. Struct. 2019, 190, 41–51. [Google Scholar] [CrossRef]
- Hogan, D.R.; A Stevens, G.; Hosseinpoor, A.R.; Boerma, T. Monitoring universal health coverage within the Sustainable Development Goals: development and baseline data for an index of essential health services. Lancet Glob. Heal. 2018, 6, e152–e168. [Google Scholar] [CrossRef]
- Xie, Q.; Faust, K.; Van Ommeren, R.; Sheikh, A.; Djuric, U.; Diamandis, P. Deep learning for image analysis: Personalizing medicine closer to the point of care. Crit. Rev. Clin. Lab. Sci. 2019, 56, 61–73. [Google Scholar] [CrossRef]
- Yang, G.; Jiang, M.; Ouyang, W.; Ji, G.; Xie, H.; Rahmani, A.M.; et al. IoT-based remote pain monitoring system: From device to cloud platform. IEEE J. Biomed. Health Informat. 2018, 22, 1711–1719. [Google Scholar] [CrossRef] [PubMed]
- Bassoli, M.; Bianchi, V.; De Munari, I. A Plug and Play IoT Wi-Fi Smart Home System for Human Monitoring. Electronics 2018, 7, 200. [Google Scholar] [CrossRef]
- Fong, E.-M.; Chung, W.-Y. Mobile Cloud-Computing-Based Healthcare Service by Noncontact ECG Monitoring. Sensors 2013, 13, 16451–16473. [Google Scholar] [CrossRef]
- Augusto, V.; Xie, X. A Modeling and Simulation Framework for Health Care Systems. IEEE Trans. Syst. Man, Cybern. Syst. 2014, 44, 30–46. [Google Scholar] [CrossRef]
- Zhang, T.; Sodhro, A.H.; Luo, Z.; Zahid, N.; Nawaz, M.W.; Pirbhulal, S.; Muzammal, M. A Joint Deep Learning and Internet of Medical Things Driven Framework for Elderly Patients. IEEE Access 2020, 8, 75822–75832. [Google Scholar] [CrossRef]
- Zheng, Y.-J. Water wave optimization: A new nature-inspired metaheuristic. Comput. Oper. Res. 2015, 55, 1–11. [Google Scholar] [CrossRef]
- Kaushik, A.; Khan, R.; Solanki, P.; Gandhi, S.; Gohel, H.; Mishra, Y.K. From Nanosystems to a Biosensing Prototype for an Efficient Diagnostic: A Special Issue in Honor of Professor Bansi D. Malhotra. Biosens. 2021, 11, 359. [Google Scholar] [CrossRef]
- Sekar, M.; Sriramprabha, R.; Sekhar, P.K.; Bhansali, S.; Ponpandian, N.; Pandiaraj, M.; Viswanathan, C. Towards wearable sensor platforms for the electrochemical detection of cortisol. J. Electrochem. Soc. 2020, 167, 67508. [Google Scholar] [CrossRef]
- Kaur, D.; Uslu, S.; Rittichier, K.J.; Durresi, A. Trustworthy artificial intelligence: A review. ACM Comput. Surv. 2022, 55, 1–38. [Google Scholar] [CrossRef]
- McCulloch, W.S.; Pitts, W. A logical calculus of the ideas immanent in nervous activity. Bull. Math. Biophys. 1943, 5, 115–133. [Google Scholar] [CrossRef]
- Hebb, D.O. The Organization of Behavior: A Neuropsychological Theory; John Wiley and Sons, Inc.: New York, NY, USA, 1949; p. 335. [Google Scholar]
- Turing, A.M. I. —Computing Machinery and Intelligence. Mind 1950, LIX, 433–460. [Google Scholar] [CrossRef]
- Zhang, L.; Tan, J.; Han, D.; Zhu, H. From machine learning to deep learning: Progress in machine intelligence for rational drug discovery. Drug Discov. Today 2017, 22, 1680–1685. [Google Scholar] [CrossRef]
- Lysenko, A.; Sharma, A.; Boroevich, A.K.; Tsunoda, T. An integrative machine learning approach for prediction of toxicity-related drug safety. Life Sci. Alliance 2018, 1, e201800098. [Google Scholar] [CrossRef] [PubMed]
- Pahari, S.; Sun, L.; Alexov, E. PKAD: A database of experimentally measured pKa values of ionizable groups in proteins. Database 2019, 2019, baz024. [Google Scholar] [CrossRef] [PubMed]
- Senior, A.W.; Evans, R.; Jumper, J.; Kirkpatrick, J.; Sifre, L.; Green, T.; Qin, C.; Žídek, A.; Nelson, A.W.R.; Bridgland, A.; et al. Improved protein structure prediction using potentials from deep learning. Nature 2020, 577, 706–710. [Google Scholar] [CrossRef] [PubMed]
- Paul, D.; Sanap, G.; Shenoy, S.; Kalyane, D.; Kalia, K.; Tekade, R.K. Artificial intelligence in drug discovery and development. Drug Discov. Today 2021, 26, 80–93. [Google Scholar] [CrossRef]
- Odusami, M.; Maskeliūnas, R.; Damaševičius, R.; Krilavičius, T. Analysis of Features of Alzheimer’s Disease: Detection of Early Stage from Functional Brain Changes in Magnetic Resonance Images Using a Finetuned ResNet18 Network. Diagnostics 2021, 11, 1071. [Google Scholar] [CrossRef]
- Svoboda, E. Artificial intelligence is improving the detection of lung cancer. Nature 2020, 587, S20–S22. [Google Scholar] [CrossRef]
- Bellemo, V.; Lim, G.; Rim, T.H.; Tan, G.S.W.; Cheung, C.Y.; Sadda, S.; He, M.; Tufail, A.; Lee, M.L.; Hsu, W.; et al. Artificial Intelligence Screening for Diabetic Retinopathy: The Real-World Emerging Application. Curr. Diab. Rep. 2019, 19, 72. [Google Scholar] [CrossRef]
- Jiang, F.; Jiang, Y.; Zhi, H.; Dong, Y.; Li, H.; Ma, S.; Wang, Y.; Dong, Q.; Shen, H.; Wang, Y. Artificial intelligence in healthcare: Past, present and future. Stroke Vasc. Neurol. 2017, 2, 230–243. [Google Scholar] [CrossRef]
- Friedman, C.; Shagina, L.; Lussier, Y.; Hripcsak, G. Automated encoding of clinical documents based on natural language processing. J. Am. Med. Inform. Assoc. 2004, 11, 392–402. [Google Scholar] [CrossRef]
- Carriere, J.; Shafi, H.; Brehon, K.; Pohar Manhas, K.; Churchill, K.; Ho, C.; Tavakoli, M. Case report: Utilizing AI and NLP to assist with healthcare and rehabilitation during the COVID-19 pandemic. Front. Artif. Intell. 2021, 4, 613637. [Google Scholar] [CrossRef] [PubMed]
- Orru, G.; Pettersson-Yeo, W.; Marquand, A.F.; Sartori, G.; Mechelli, A. Using support vector machine to identify imaging biomarkers of neurological and psychiatric disease: A critical review. Neurosci. Biobehav. Rev. 2012, 36, 1140–1152. [Google Scholar] [CrossRef]
- Farina, D.; Vujaklija, I.; Sartori, M.; Kapelner, T.; Negro, F.; Jiang, N.; Bergmeister, K.; Andalib, A.; Principe, J.; Aszmann, O.C. Man/machine interface based on the discharge timings of spinal motor neurons after targeted muscle reinnervation. Nat. Biomed. Eng. 2017, 1, 0025. [Google Scholar] [CrossRef]
- Sweilam, N.H.; Tharwat, A.A.; Abdel Moniem, N.K. Support vector machine for diagnosis cancer disease: A comparative study. Egypt. Inform. J. 2010, 11, 81–92. [Google Scholar] [CrossRef]
- Khedher, L.; Ramírez, J.; Górriz, J.M.; Brahim, A.; Segovia, F. Early diagnosis of Alzheimer’s disease based on partial least squares, principal component analysis and support vector machine using segmented MRI images. Neurocomputing 2015, 151, 139–150. [Google Scholar] [CrossRef]
- Martin-Isla, C.; Campello, V.M.; Izquierdo, C.; Raisi-Estabragh, Z.; Baeßler, B.; Petersen, S.E.; Lekadir, K. Image-Based Cardiac Diagnosis with Machine Learning: A Review. Front. Cardiovasc. Med. 2020, 7, 1. [Google Scholar] [CrossRef]
- Soguero-Ruiz, C.; Fei, W.M.E.; Jenssen, R.; Augestad, K.M.; Álvarez, J.-L.R.; Jiménez, I.M.; Lindsetmo, R.-O.; Skrøvseth, S.O. Data-driven temporal prediction of surgical site infection. In Proceedings of the AMIA Annual Symposium Proceedings, American Medical Informatics Association, San Francisco, CA, USA, 14–18 November 2015; Volume 2015, p. 1164. [Google Scholar]
- Shokrekhodaei, M.; Cistola, D.P.; Roberts, R.C.; Quinones, S. Non-Invasive Glucose Monitoring Using Optical Sensor and Machine Learning Techniques for Diabetes Applications. IEEE Access 2021, 9, 73029–73045. [Google Scholar] [CrossRef] [PubMed]
- Hashimoto, D.A.; Rosman, G.; Rus, D.; Meireles, O.R. Artificial Intelligence in Surgery: Promises and Perils. Ann. Surg. 2018, 268, 70–76. [Google Scholar] [CrossRef] [PubMed]
- Galbusera, F.; Casaroli, G.; Bassani, T. Artificial intelligence and machine learning in spine research. JOR Spine 2019, 2, e1044. [Google Scholar] [CrossRef]
- Chang, M.; Canseco, J.A.; Nicholson, K.J.; Patel, N.; Vaccaro, A.R. The Role of Machine Learning in Spine Surgery: The Future Is Now. Front. Surg. 2020, 7, 54. [Google Scholar] [CrossRef]
- Goswami, M.; Sebastian, N.J. Performance Analysis of Logistic Regression, KNN, SVM, Naïve Bayes Classifier for Healthcare Application During COVID-19. In Innovative Data Communication Technologies and Application; Raj, J.S., Kamel, K., Lafata, P., Eds.; Springer Nature: Singapore, 2022; Volume 96, pp. 645–658. ISBN 9789811671661. [Google Scholar]
- Kaur, P.; Kumar, R.; Kumar, M. A healthcare monitoring system using random forest and internet of things (IoT). Multimed. Tools Appl. 2019, 78, 19905–19916. [Google Scholar] [CrossRef]
- Khosravan, N.; Bagci, U. S4ND: Single-shot single-scale lung nodule detection. In Proceedings of the International Conference on Medical Image Computing and Computer-Assisted Intervention, Granada, Spain, 16–20 September 2018; pp. 794–802. [Google Scholar]
- Ardila, D.; Kiraly, A.P.; Bharadwaj, S.; Choi, B.; Reicher, J.J.; Peng, L.; Tse, D.; Etemadi, M.; Ye, W.; Corrado, G. End-to-end lung cancer screening with three-dimensional deep learning on low-dose chest computed tomography. Nat. Med. 2019, 25, 954–961. [Google Scholar] [CrossRef] [PubMed]
- Muhammad, W.; Hart, G.R.; Nartowt, B.; Farrell, J.J.; Johung, K.; Liang, Y.; Deng, J. Pancreatic cancer prediction through an artificial neural network. Front. Artif. Intell. 2019, 2, 2. [Google Scholar] [CrossRef]
- Hirschauer, T.J.; Adeli, H.; Buford, J.A. Computer-Aided Diagnosis of Parkinson’s Disease Using Enhanced Probabilistic Neural Network. J. Med. Syst. 2015, 39, 179. [Google Scholar] [CrossRef] [PubMed]
- Sarraf, S.; DeSouza, D.D.; Anderson, J.; Tofighi, G. DeepAD: Alzheimer’s Disease Classification via Deep Convolutional Neural Networks using MRI and fMRI. BioRxiv 2017, 070441. [Google Scholar]
- Ramzan, F.; Khan, M.U.G.; Rehmat, A.; Iqbal, S.; Saba, T.; Rehman, A.; Mehmood, Z. A deep learning approach for automated diagnosis and multi-class classification of Alzheimer’s disease stages using resting-state fMRI and residual neural networks. J. Med. Syst. 2020, 44, 37. [Google Scholar] [CrossRef]
- Pang, K.; Song, X.; Xu, Z.; Liu, X.; Liu, Y.; Zhong, L.; Peng, Y.; Wang, J.; Zhou, J.; Meng, F. Hydroplastic foaming of graphene aerogels and artificially intelligent tactile sensors. Sci. Adv. 2020, 6, eabd4045. [Google Scholar] [CrossRef]
- Hayasaka, T.; Lin, A.; Copa, V.C.; Lopez, L.P.; Loberternos, R.A.; Ballesteros, L.I.M.; Kubota, Y.; Liu, Y.; Salvador, A.A.; Lin, L. An electronic nose using a single graphene FET and machine learning for water, methanol, and ethanol. Microsyst. Nanoeng. 2020, 6, 50. [Google Scholar] [CrossRef]
- Khanam, J.J.; Foo, S.Y. A comparison of machine learning algorithms for diabetes prediction. ICT Express 2021, 7, 432–439. [Google Scholar] [CrossRef]
- Kwon, Y.-T.; Kim, H.; Mahmood, M.; Kim, Y.-S.; Demolder, C.; Yeo, W.-H. Printed, wireless, soft bioelectronics and deep learning algorithm for smart human–machine interfaces. ACS Appl. Mater. Interfaces 2020, 12, 49398–49406. [Google Scholar] [CrossRef]
- Kaushik, A.K.; Dhau, J.S.; Gohel, H.; Mishra, Y.K.; Kateb, B.; Kim, N.-Y.; Goswami, D.Y. Electrochemical SARS-CoV-2 Sensing at Point-of-Care and Artificial Intelligence for Intelligent COVID-19 Management. ACS Appl. Bio Mater. 2020, 3, 7306–7325. [Google Scholar]
- Esteva, A.; Chou, K.; Yeung, S.; Naik, N.; Madani, A.; Mottaghi, A.; Liu, Y.; Topol, E.; Dean, J.; Socher, R. Deep learning-enabled medical computer vision. npj Digit. Med. 2021, 4, 5. [Google Scholar] [CrossRef]
- Langarizadeh, M.; Moghbeli, F. Applying Naive Bayesian Networks to Disease Prediction: A Systematic Review. Acta Inform. Medica 2016, 24, 364. [Google Scholar] [CrossRef]
- Shen, Y.; Li, Y.; Zheng, H.-T.; Tang, B.; Yang, M. Enhancing ontology-driven diagnostic reasoning with a symptom-dependency-aware Naïve Bayes classifier. BMC Bioinform. 2019, 20, 330. [Google Scholar] [CrossRef]
- Fauziyyah, N.A.; Abdullah, S.; Nurrohmah, S. Reviewing the Consistency of the Naïve Bayes Classifier’s Performance in Medical Diagnosis and Prognosis Problems. AIP Conf. Proc. 2020, 2242, 30019. [Google Scholar]
- Uddin, S.; Haque, I.; Lu, H.; Moni, M.A.; Gide, E. Comparative performance analysis of K-nearest neighbour (KNN) algorithm and its different variants for disease prediction. Sci. Rep. 2022, 12, 6256. [Google Scholar] [CrossRef]
- Li, C.; Zhang, S.; Zhang, H.; Pang, L.; Lam, K.; Hui, C.; Zhang, S. Using the K-Nearest Neighbor Algorithm for the Classification of Lymph Node Metastasis in Gastric Cancer. Comput. Math. Methods Med. 2012, 2012, 876545. [Google Scholar] [CrossRef]
- Rahmat, D.; Putra, A.A.; Setiawan, A.W. Heart Disease Prediction Using K-Nearest Neighbor. In Proceedings of the 2021 International Conference on Electrical Engineering and Informatics (ICEEI), Kuala Terengganu, Malaysia, 12–13 October 2021; IEEE: Kuala Terengganu, Malaysia, 2021; pp. 1–6. [Google Scholar]
- Khalilia, M.; Chakraborty, S.; Popescu, M. Predicting disease risks from highly imbalanced data using random forest. BMC Med. Inform. Decis. Mak. 2011, 11, 51. [Google Scholar] [CrossRef]
- Ooka, T.; Johno, H.; Nakamoto, K.; Yoda, Y.; Yokomichi, H.; Yamagata, Z. Random forest approach for determining risk prediction and predictive factors of type 2 diabetes: Large-scale health check-up data in Japan. BMJ Nutr. Prev. Health 2021, 4, 140–148. [Google Scholar] [CrossRef]
- Fawagreh, K.; Gaber, M.M. Resource-efficient fast prediction in healthcare data analytics: A pruned Random Forest regression approach. Computing 2020, 102, 1187–1198. [Google Scholar] [CrossRef]
- Amethiya, Y.; Pipariya, P.; Patel, S.; Shah, M. Comparative analysis of breast cancer detection using machine learning and biosensors. Intell. Med. 2022, 2, 69–81. [Google Scholar] [CrossRef]
- Wanders, A.J.T.; Mees, W.; Bun, P.A.M.; Janssen, N.; Rodríguez-Ruiz, A.; Dalmış, M.U.; Karssemeijer, N.; van Gils, C.H.; Sechopoulos, I.; Mann, R.M.; et al. Interval Cancer Detection Using a Neural Network and Breast Density in Women with Negative Screening Mammograms. Radiology 2022, 303, 269–275. [Google Scholar] [CrossRef] [PubMed]
- Qureshi, T.A.; Gaddam, S.; Wachsman, A.M.; Wang, L.; Azab, L.; Asadpour, V.; Chen, W.; Xie, Y.; Wu, B.; Pandol, S.J. Predicting pancreatic ductal adenocarcinoma using artificial intelligence analysis of pre-diagnostic computed tomography images. Cancer Biomark. 2022, 33, 211–217. [Google Scholar] [CrossRef] [PubMed]
- Akbilgic, O.; Butler, L.; Karabayir, I.; Chang, P.P.; Kitzman, D.W.; Alonso, A.; Chen, L.Y.; Soliman, E.Z. ECG-AI: Electrocardiographic artificial intelligence model for prediction of heart failure. Eur. Heart J. Digit. Health 2021, 2, 626–634. [Google Scholar] [CrossRef] [PubMed]
- Siontis, K.C.; Noseworthy, P.A.; Attia, Z.I.; Friedman, P.A. Artificial intelligence-enhanced electrocardiography in cardiovascular disease management. Nat. Rev. Cardiol. 2021, 18, 465–478. [Google Scholar] [CrossRef] [PubMed]
- Zhou, X.Y.; Guo, Y.; Shen, M.; Yang, G.Z. Application of artificial intelligence in surgery. Front. Med. 2020, 14, 417–430. [Google Scholar] [CrossRef] [PubMed]
- Farina, D.; Vujaklija, I.; Brånemark, R.; Bull, A.M.J.; Dietl, H.; Graimann, B.; Hargrove, L.J.; Hoffmann, K.-P.; Huang, H.; Ingvarsson, T.; et al. Toward higher-performance bionic limbs for wider clinical use. Nat. Biomed. Eng. 2021. [CrossRef]
- Wang, M.; Wang, T.; Luo, Y.; He, K.; Pan, L.; Li, Z.; Cui, Z.; Liu, Z.; Tu, J.; Chen, X. Fusing stretchable sensing technology with machine learning for human–machine interfaces. Adv. Funct. Mater. 2021, 31, 2008807. [Google Scholar] [CrossRef]
- Mujawar, M.A.; Gohel, H.; Bhardwaj, S.K.; Srinivasan, S.; Hickman, N.; Kaushik, A. Nano-enabled biosensing systems for intelligent healthcare: Towards COVID-19 management. Mater. Today Chem. 2020, 17, 100306. [Google Scholar] [CrossRef]
- Kujawska, M.; Kaushik, A. Exploring magneto-electric nanoparticles (MENPs): A platform for implanted deep brain stimulation. Neural Regen. Res. 2023, 18, 129–130. [Google Scholar] [CrossRef]
- Chaudhary, V.; Kaushik, A.; Furukawa, H.; Khosla, A. Review—Towards 5th Generation AI and IoT Driven Sustainable Intelligent Sensors Based on 2D MXenes and Borophene. ECS Sensors Plus 2022, 1, 13601. [Google Scholar] [CrossRef]
- Khunger, A.; Kaur, N.; Mishra, Y.K.; Ram Chaudhary, G.; Kaushik, A. Perspective and prospects of 2D MXenes for smart biosensing. Mater. Lett. 2021, 304, 130656. [Google Scholar] [CrossRef]
- Chao, M.; He, L.; Gong, M.; Li, N.; Li, X.; Peng, L.; Shi, F.; Zhang, L.; Wan, P. Breathable Ti3C2Tx MXene/Protein Nanocomposites for Ultrasensitive Medical Pressure Sensor with Degradability in Solvents. ACS Nano 2021, 15, 9746–9758. [Google Scholar] [CrossRef]
- Chia, H.L.; Mayorga-Martinez, C.C.; Antonatos, N.; Sofer, Z.; Gonzalez-Julian, J.J.; Webster, R.D.; Pumera, M. MXene Titanium Carbide-based Biosensor: Strong Dependence of Exfoliation Method on Performance. Anal. Chem. 2020, 92, 2452–2459. [Google Scholar] [CrossRef]
- Chaudhary, V.; Ashraf, N.; Khalid, M.; Walvekar, R.; Yang, Y.; Kaushik, A.; Mishra, Y.K. Emergence of MXene–Polymer Hybrid Nanocomposites as High-Performance Next-Generation Chemiresistors for Efficient Air Quality Monitoring. Adv. Funct. Mater. 2022, 2112913. [Google Scholar] [CrossRef]
- Lee, H.J.; Yang, J.C.; Choi, J.; Kim, J.; Lee, G.S.; Sasikala, S.P.; Lee, G.-H.; Park, S.-H.K.; Lee, H.M.; Sim, J.Y.; et al. Hetero-Dimensional 2D Ti3C2Tx MXene and 1D Graphene Nanoribbon Hybrids for Machine Learning-Assisted Pressure Sensors. ACS Nano 2021, 15, 10347–10356. [Google Scholar] [CrossRef]
- Kumar Sharma, P.; Ruotolo, A.; Khan, R.; Mishra, Y.K.; Kumar Kaushik, N.; Kim, N.-Y.; Kumar Kaushik, A. Perspectives on 2D-borophene flatland for smart bio-sensing. Mater. Lett. 2022, 308, 131089. [Google Scholar]
- Kujawska, M.; Bhardwaj, S.K.; Mishra, Y.K.; Kaushik, A. Using graphene-based biosensors to detect dopamine for efficient parkinson’s disease diagnostics. Biosensors 2021, 11, 433. [Google Scholar] [CrossRef] [PubMed]
- Huang, M.; Li, Z.; Zhu, H. Recent Advances of Graphene and Related Materials in Artificial Intelligence. Adv. Intell. Syst. 2022, 2200077. [Google Scholar] [CrossRef]
- Madhu, S.; Ramasamy, S.; Magudeeswaran, V.; Manickam, P.; Nagamony, P.; Chinnuswamy, V. SnO2 nanoflakes deposited carbon yarn-based electrochemical immunosensor towards cortisol measurement. J. Nanostruct. Chem. 2022, 1–13. [Google Scholar] [CrossRef]
- Fang, Y.; Zou, Y.; Xu, J.; Chen, G.; Zhou, Y.; Deng, W.; Zhao, X.; Roustaei, M.; Hsiai, T.K.; Chen, J. Ambulatory Cardiovascular Monitoring Via a Machine-Learning-Assisted Textile Triboelectric Sensor. Adv. Mater. 2021, 33, 2104178. [Google Scholar] [CrossRef]
- Nakhleh, M.K.; Baram, S.; Jeries, R.; Salim, R.; Haick, H.; Hakim, M. Artificially intelligent nanoarray for the detection of preeclampsia under real-world clinical conditions. Adv. Mater. Technol. 2016, 1, 1600132. [Google Scholar] [CrossRef]
- Olorunyomi, J.F.; Geh, S.T.; Caruso, R.A.; Doherty, C.M. Metal–organic frameworks for chemical sensing devices. Mater. Horizons 2021, 8, 2387–2419. [Google Scholar] [CrossRef]
- Wu, J.; Chen, J.; Wang, C.; Zhou, Y.; Ba, K.; Xu, H.; Bao, W.; Xu, X.; Carlsson, A.; Lazar, S. Metal–organic framework for transparent electronics. Adv. Sci. 2020, 7, 1903003. [Google Scholar] [CrossRef] [PubMed]
- Assen, A.H.; Yassine, O.; Shekhah, O.; Eddaoudi, M.; Salama, K.N. MOFs for the sensitive detection of ammonia: Deployment of fcu-MOF thin films as effective chemical capacitive sensors. ACS Sens. 2017, 2, 1294–1301. [Google Scholar] [CrossRef] [PubMed]
- Zhang, T.; Gao, C.; Huang, W.; Chen, Y.; Wang, Y.; Wang, J. Covalent organic framework as a novel electrochemical platform for highly sensitive and stable detection of lead. Talanta 2018, 188, 578–583. [Google Scholar] [CrossRef] [PubMed]
- Varahachalam, S.P.; Lahooti, B.; Chamaneh, M.; Bagchi, S.; Chhibber, T.; Morris, K.; Bolanos, J.F.; Kim, N.Y.; Kaushik, A. Nanomedicine for the SARS-CoV-2: State-of-theart and future prospects. Int. J. Nanomed. 2021, 16, 539–560. [Google Scholar] [CrossRef] [PubMed]
- Vashist, A.; Kaushik, A.; Ghosal, A.; Bala, J.; Nikkhah-Moshaie, R.; Wani, W.A.; Manickam, P.; Nair, M. Nanocomposite Hydrogels: Advances in Nanofillers Used for Nanomedicine. Gels 2018, 4, 75. [Google Scholar] [CrossRef]
- Dubey, A.K.; Kumar Gupta, V.; Kujawska, M.; Orive, G.; Kim, N.-Y.; Li, C.; Kumar Mishra, Y.; Kaushik, A. Exploring nano-enabled CRISPR-Cas-powered strategies for efficient diagnostics and treatment of infectious diseases. J. Nanostruct. Chem. 2022. [CrossRef]
- Bhushan, P.; Kamat, V.; Abrol, I.; Kaushik, A.; Bhansali, S. Bio-acceptability of wearable sensors: A mechanistic study towards evaluating ionic leaching induced cellular inflammation. Sci. Rep. 2022, 12, 1–9. [Google Scholar] [CrossRef]
- Granda, J.M.; Donina, L.; Dragone, V.; Long, D.-L.; Cronin, L. Controlling an organic synthesis robot with machine learning to search for new reactivity. Nature 2018, 559, 377–381. [Google Scholar] [CrossRef]
- Oh, E.; Liu, R.; Nel, A.; Gemill, K.B.; Bilal, M.; Cohen, Y.; Medintz, I.L. Meta-analysis of cellular toxicity for cadmium-containing quantum dots. Nat. Nanotechnol. 2016, 11, 479–486. [Google Scholar] [CrossRef]
- Chaudhary, V.; Mostafavi, E.; Kaushik, A. De-coding Ag as an efficient antimicrobial nano-system for controlling cellular/biological functions. Matter 2022, 5, 1995–1998. [Google Scholar] [CrossRef]
- Manickam, P.; Vashist, A.; Madhu, S.; Sadasivam, M.; Sakthivel, A.; Kaushik, A.; Nair, M. Gold nanocubes embedded biocompatible hybrid hydrogels for electrochemical detection of H2O2. Bioelectrochemistry 2020, 131, 107373. [Google Scholar] [CrossRef] [PubMed]
- Shinde, R.B.; Veerapandian, M.; Kaushik, A.; Manickam, P. State-of-Art Bio-Assay Systems and Electrochemical Approaches for Nanotoxicity Assessment. Front. Bioeng. Biotechnol. 2020, 8, 325. [Google Scholar] [CrossRef]
- Sundarapandi, M.; Shanmugam, S.; Ramaraj, R. Synthesis and catalytic activities of metal shells (monolayer, bilayer, and alloy layer)-coated gold octahedra toward catalytic reduction of nitroaromatics. J. Phys. Chem. C 2019, 123, 21066–21075. [Google Scholar] [CrossRef]
- Pashkov, D.M.; Guda, A.A.; Kirichkov, M.V.; Guda, S.A.; Martini, A.; Soldatov, S.A.; Soldatov, A.V. Quantitative analysis of the UV–vis spectra for gold nanoparticles powered by supervised machine learning. J. Phys. Chem. C 2021, 125, 8656–8666. [Google Scholar] [CrossRef]
- Srinivasan, B.; Vo, T.; Zhang, Y.; Gang, O.; Kumar, S.; Venkatasubramanian, V. Designing DNA-grafted particles that self-assemble into desired crystalline structures using the genetic algorithm. Proc. Natl. Acad. Sci. USA 2013, 110, 18431–18435. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Gupta, B.; Anurag, A. Deployment techniques in wireless sensor networks: a survey, classification, challenges, and future research issues. J. Supercomput. 2020, 76, 7333–7373. [Google Scholar] [CrossRef]
- Angenent-Mari, N.M.; Garruss, A.S.; Soenksen, L.R.; Church, G.; Collins, J.J. A deep learning approach to programmable RNA switches. Nat. Commun. 2020, 11, 1–12. [Google Scholar] [CrossRef]
- Ren, F.; Ward, L.; Williams, T.; Laws, K.J.; Wolverton, C.; Hattrick-Simpers, J.; Mehta, A. Accelerated discovery of metallic glasses through iteration of machine learning and high-throughput experiments. Sci. Adv. 2018, 4, eaaq1566. [Google Scholar] [CrossRef] [PubMed]
- Jackson, N.E.; Bowen, A.S.; Antony, L.W.; Webb, M.A.; Vishwanath, V.; de Pablo, J.J. Electronic structure at coarse-grained resolutions from supervised machine learning. Sci. Adv. 2019, 5, eaav1190. [Google Scholar] [CrossRef]
- Jin, X.; Liu, C.; Xu, T.; Su, L.; Zhang, X. Artificial intelligence biosensors: Challenges and prospects. Biosens. Bioelectron. 2020, 165, 112412. [Google Scholar] [CrossRef]
- Song, Y.; Jiang, J.; Wang, X.; Yang, D.; Bai, C. Prospect and application of Internet of Things technology for prevention of SARIs. Clin. eHealth 2020, 3, 1–4. [Google Scholar] [CrossRef]
- Ding, X.; Mauk, M.G.; Yin, K.; Kadimisetty, K.; Liu, C. Interfacing pathogen detection with smartphones for point-of-care applications. Anal. Chem. 2018, 91, 655–672. [Google Scholar] [CrossRef] [PubMed]
- Jain, S.; Nehra, M.; Kumar, R.; Dilbaghi, N.; Hu, T.; Kumar, S.; Kaushik, A.; Li, C. Internet of medical things (IoMT)-integrated biosensors for point-of-care testing of infectious diseases. Biosens. Bioelectron. 2021, 179, 113074. [Google Scholar] [CrossRef] [PubMed]
- Karuppaiah, G.; Velayutham, J.; Hansda, S.; Narayana, N.; Bhansali, S.; Manickam, P. Towards the development of reagent-free and reusable electrochemical aptamer-based cortisol sensor. Bioelectrochemistry 2022, 145, 108098. [Google Scholar] [CrossRef] [PubMed]
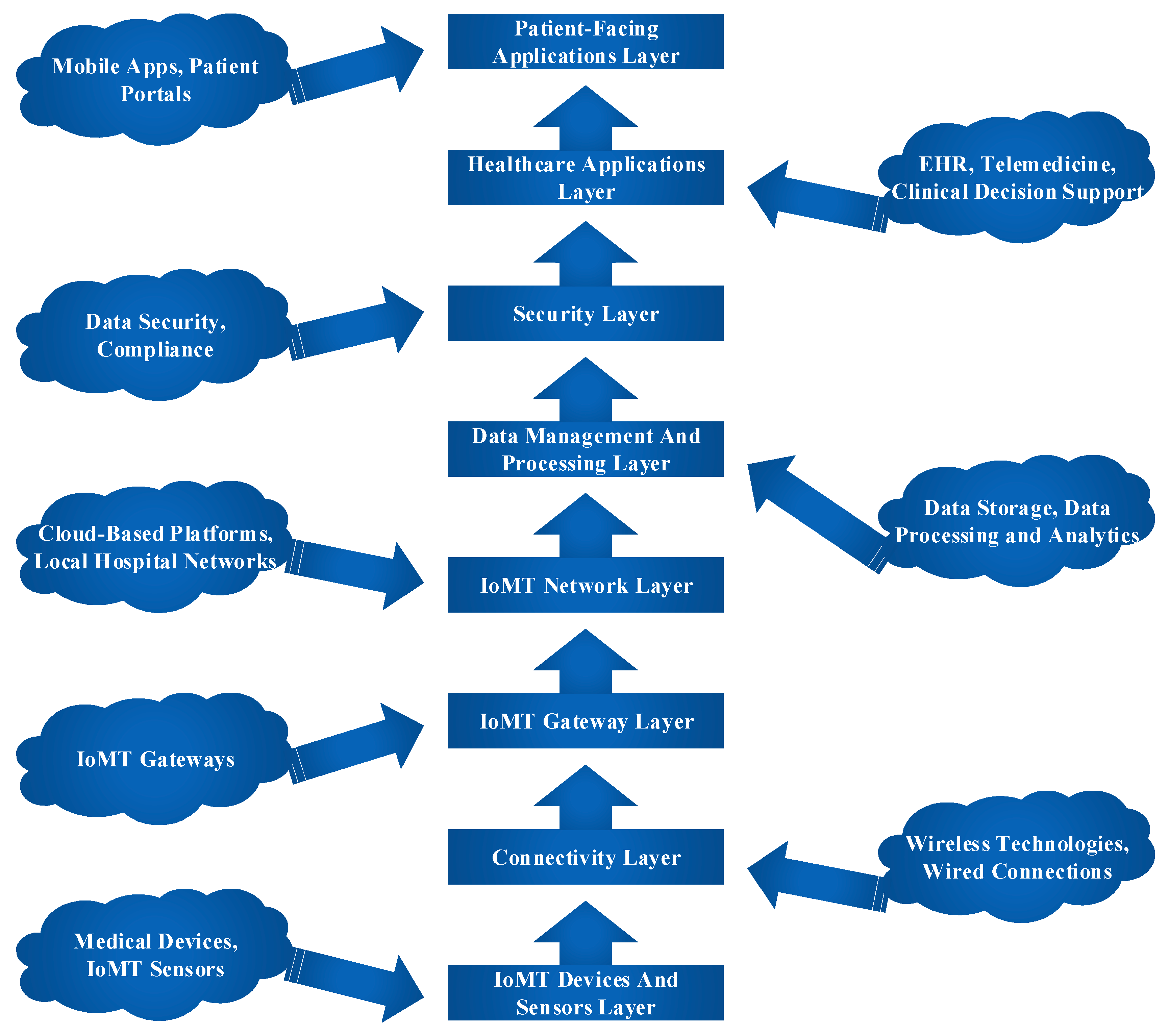
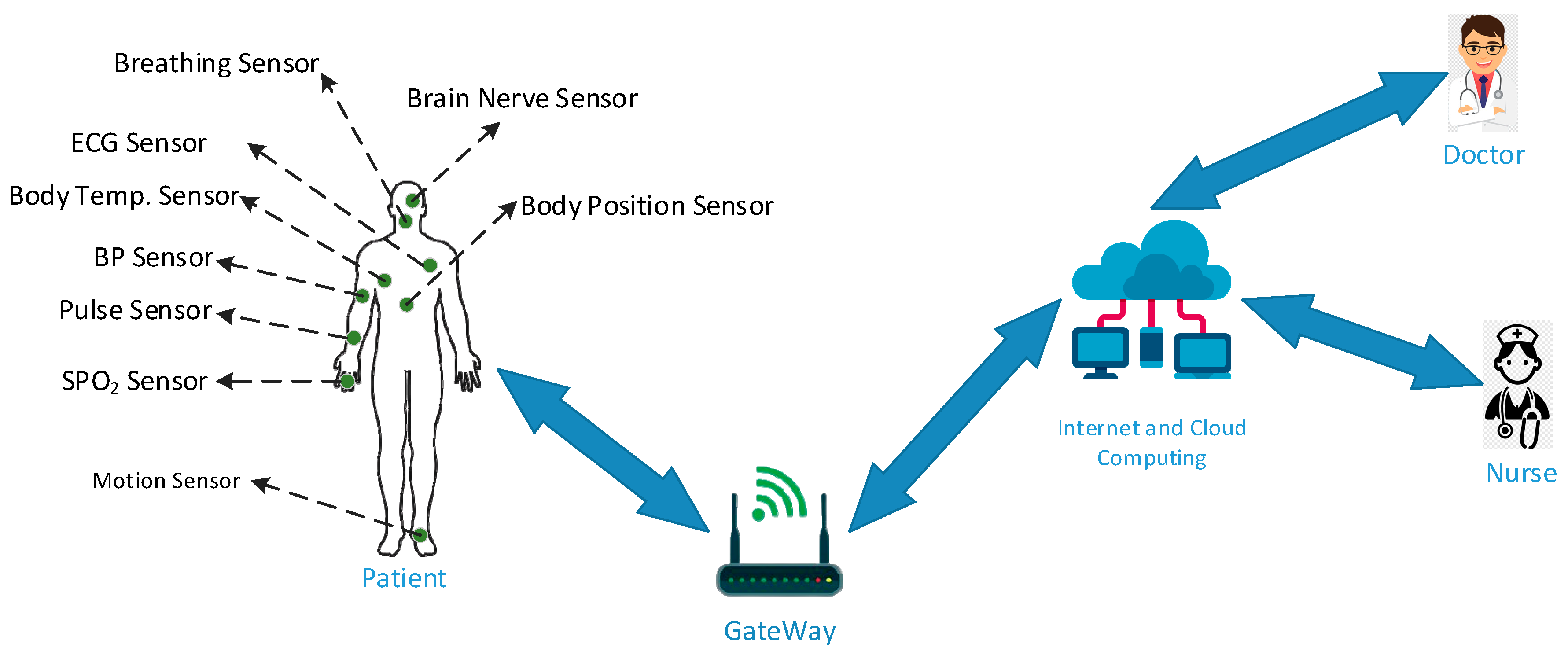
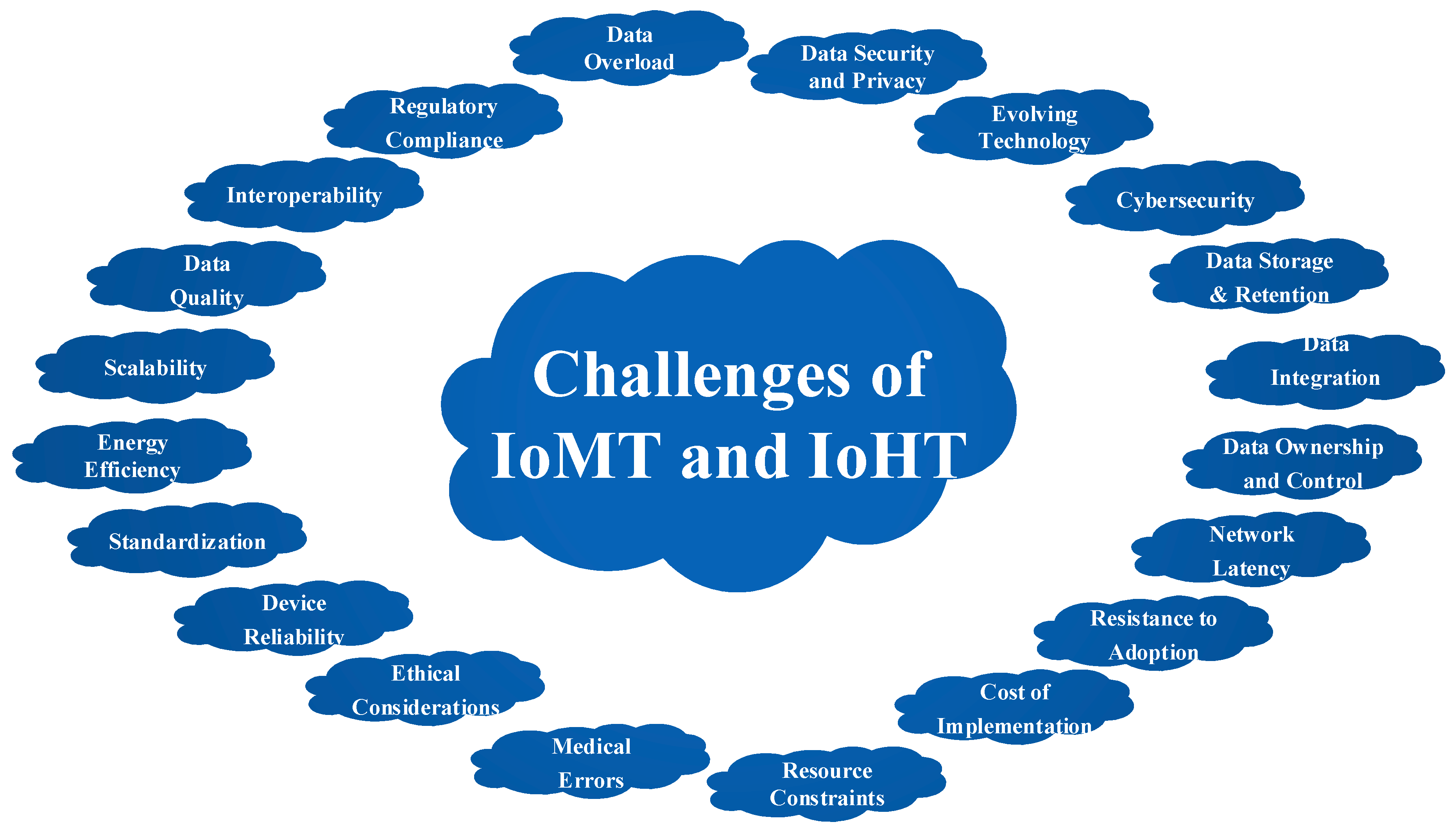
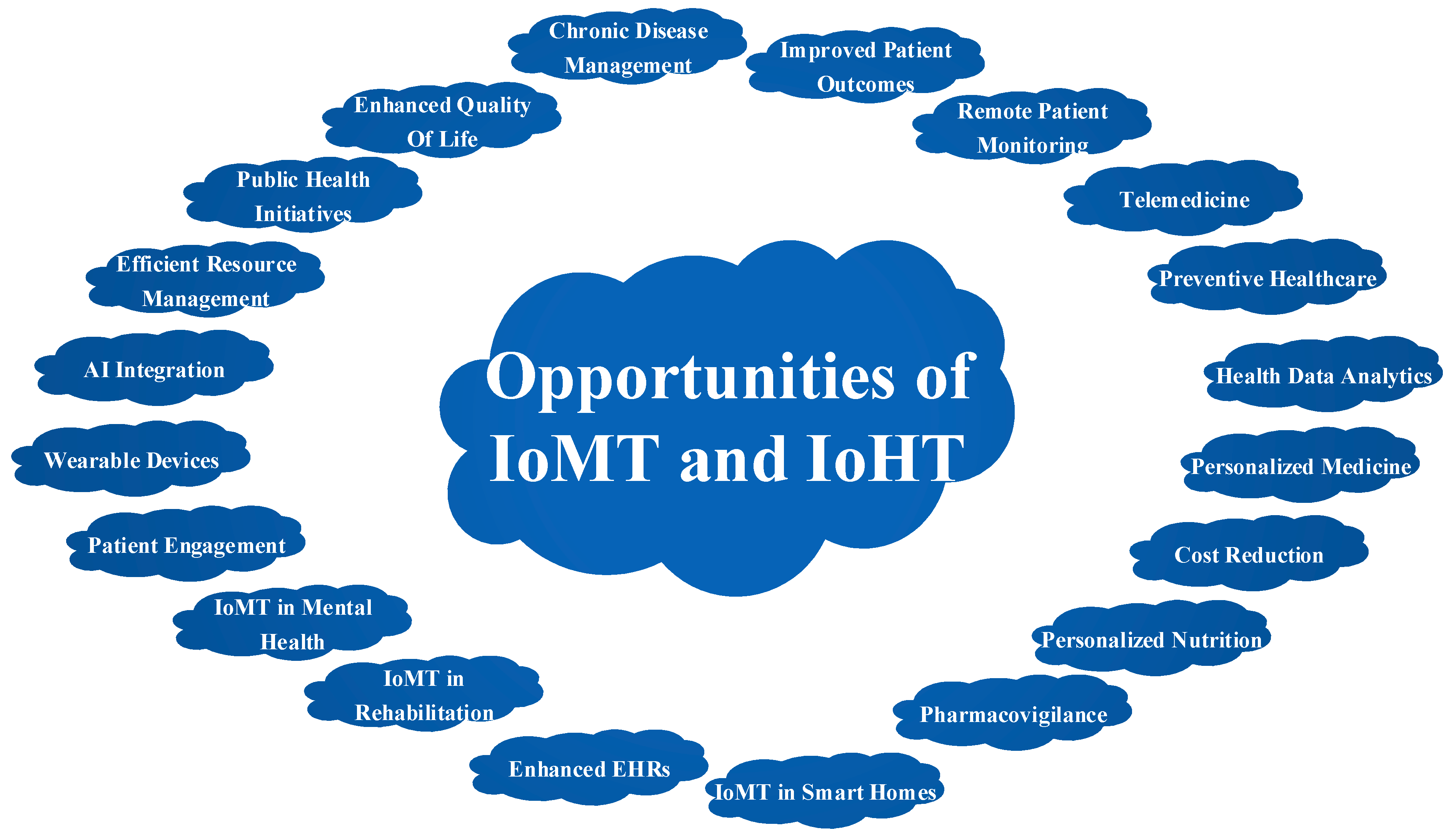
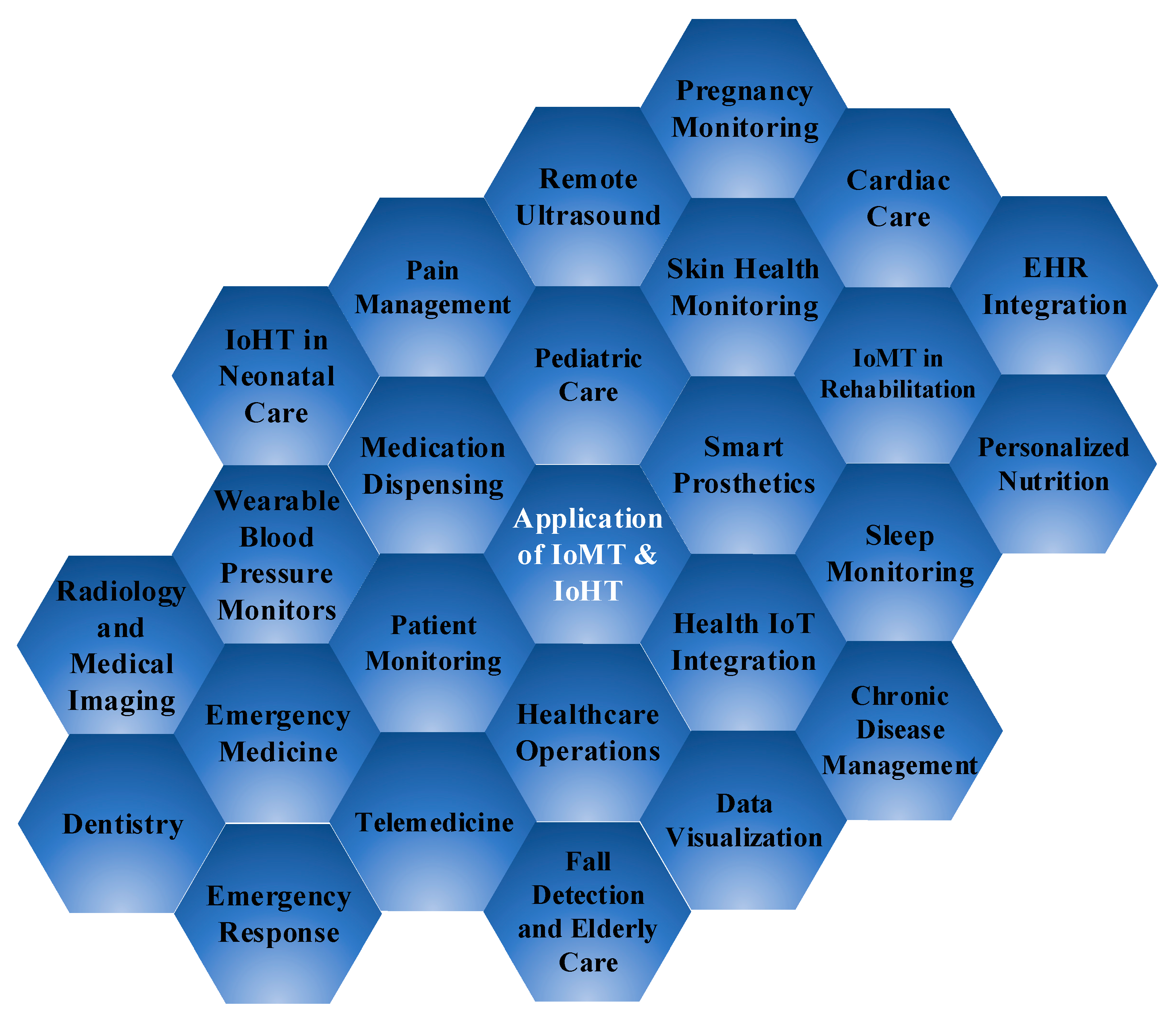
| Paper | Applications | Goals | Advantages | Future Directions |
|---|---|---|---|---|
| [235] | Patient Monitoring | Continuous health monitoring | Early detection, improved outcomes | Integration with AI for predictive analytics |
| [236] | Telemedicine | Remote doctor-patient consultations | Increased healthcare accessibility | Real-time data sharing with IoHT devices |
| [237] | Chronic Disease Management | Manage long-term health conditions | Improved quality of life, cost reduction | ML-based personalized care plans |
| [238] | Fall Detection and Elderly Care | Detect falls and monitor elderly | Enhanced safety for seniors | ML models to distinguish falls from activities |
| [239] | Pediatric Care | Monitor child health and development | Early detection of child health issues | ML-powered growth and development tracking |
| [240] | Mental Health Monitoring | Track mental health conditions | Early intervention for mental health | ML for sentiment analysis and prediction |
| [241] | Medication Adherence | Ensure patients take medications as prescribed | Improved treatment outcomes | ML algorithms for predicting non-adherence |
| [242] | Public Health and Epidemic Monitoring | Monitor disease outbreaks | Early detection of epidemics, effective response | ML integration for predictive modeling |
| [243] | Dentistry | Monitor oral health and dental care | Improved oral hygiene and reduced dental problems | ML for early dental issue detection |
| [244] | Radiology and Medical Imaging | Enhance radiological diagnostics | Improved accuracy in disease detection | ML-based image analysis for automated diagnosis |
| [246] | Cardiac Care | Continuous monitoring of heart health | Early detection of cardiac issues | Real-time ECG analysis using ML algorithms |
| [247] | EHR Integration | Integrating IoHT and IoMT data with EHRs | Comprehensive and up-to-date patient records | ML-driven insights and pattern recognition |
| [248] | Personalized Nutrition | Tailor dietary recommendations based on health data | Improved nutrition and health | ML for analyzing dietary habits and suggesting personalized meal plans |
| [249] | Emergency Response | Improve emergency response systems | Faster response times, enhanced care | ML for triage and resource allocation |
| [250] | IoHT in Smart Homes | Provide healthcare support in smart homes | Enhanced well-being and convenience | ML for home automation based on health data |
| [251] | Pregnancy Monitoring | Monitor maternal health and fetal development | Early detection of pregnancy complications | Integration with AI for comprehensive fetal monitoring |
| [252] | Healthcare Operations | Optimize hospital operations and patient flow | Efficient resource allocation and management | ML for predictive maintenance of medical equipment |
| [253] | Postoperative Care | Enhance postoperative care and recovery | Reduced complications and faster recovery | ML-powered post-op progress tracking and support |
| [254] | Data Visualization | Develop effective data visualization techniques | Enhanced data-driven decision-making | Advanced ML-driven data visualization tools |
| [255] | Emergency Medicine | Utilize IoMT in emergency medicine | Improved response and triage in emergencies | ML for faster patient assessments and treatment |
| [256] | Global Health | Address global health challenges with IoHT | Improved healthcare access and disease control | AI-driven predictive models for global health trends |
| [257] | Health IoT Integration | Integration of IoMT with other health IoT devices | Comprehensive health monitoring ecosystem | ML for advanced health data fusion and analysis |
| [258] | Patient Empowerment | Empower patients in healthcare decisions | Active involvement in healthcare management | AI-driven personalized health recommendations |
| [259] | Skin Health Monitoring | Monitor dermatological conditions | Early detection and improved skin health | AI for automated skin condition diagnosis and tracking |
| [260] | Sleep Monitoring | Track sleep patterns and quality | Improved sleep management and overall health | ML for personalized sleep improvement strategies |
| [261] | Wearable Blood Pressure Monitors | Monitor blood pressure | Better hypertension management | ML for predicting blood pressure trends and risks |
| [262] | IoMT in Asthma Management | Manage and control asthma | Better asthma control and reduced exacerbations | ML for personalized asthma action plans |
| [263] | Pain Management | Track and manage chronic pain | Enhanced pain control and quality of life | ML for personalized pain management plans |
| [264] | Smart Prosthetics | Enhance the functionality of prosthetic devices | Improved mobility and quality of life | Integration with brain-computer interfaces |
| [265] | IoMT in Rehabilitation | Assist in physical and occupational therapy | Enhanced rehabilitation and recovery | AI-driven personalized therapy plans |
| [266] | Remote Ultrasound | Perform remote ultrasound diagnostics | Expand access to medical imaging | Integration of AI for remote diagnostic accuracy |
| [267] | Wound Monitoring | Monitor wound healing and infection | Improved wound care and recovery | AI for wound condition tracking and analysis |
| [268] | IoHT in Neonatal Care | Enhance care for premature infants | Better neonatal care and developmental monitoring | ML for predictive models for neonatal health |
| [269] | Medication Dispensing | Automate medication dispensing and management | Improved medication accuracy and adherence | Integration of AI for prescription error prevention |
| Paper | Security Issues | Experiment | Proposed Framework/Model | Result |
|---|---|---|---|---|
| [274] | Data Privacy | Lab Testing | Blockchain-Based Security | Improved Data Secrecy |
| [275] | Authentication Vulnerabilities | Field Deployment | Multi-Factor Authentication | Superior Authentication of Users |
| [276] | Data Integrity | Simulation | Digital Signatures | Guaranteed Accuracy of Information |
| [277] | Device Vulnerabilities | Real-world Testing | Intrusion Detection System | Reduced Potential for Electronic Security Flaws |
| [278] | Unauthorized Data Access | Pilot Study | Role-Based Access Control | Intruders are being denied entry. |
| [279] | Data Transmission Security | Field Trials | Secure Communication Protocols | Secure Information Exchange |
| [280] | Remote Monitoring Security | Clinical Trials | End-to-End Encryption | Improvements in Remote Monitoring Security |
| [281] | Compliance with Regulations | Compliance Audit | IoHT Compliance Framework | Obtaining Desired Results |
| [282] | Vulnerabilities in Firmware | Device Monitoring | Regular Firmware Updates | fewer vulnerabilities in firmware |
| [283] | Network Vulnerabilities | Network Assessment | Segmentation & Firewalls | Increased Network Safety |
| [284] | Data Encryption | Data Transmission | AES-256 Encryption | Data Encryption for Safety |
| [285] | User Authentication | User Testing | Biometric Authentication | User Authentication That's Even Better |
| [286] | Healthcare Data Encryption | Data Storage | Homomorphic Encryption | Confidential Medical Records |
| [287] | Security of Wearable Devices | Device Analysis | Secure Boot & Firmware Signing | Advances in Portable Electronics Security |
| [288] | Scalability & Security | Scalability Testing | Edge Computing Security | Protected and Capable IoT |
| [289] | IoT Device Patching | Device Management | Automated Patch Management | Properly Applied Security Updates |
| [290] | Mobile App Security | App Testing | Mobile App Security Framework | More Secure Mobile applications |
| [291] | Trust Management | Real-world Healthcare | Trust Evaluation Model | Enhancing Trust Management |
| [292] | Compliance Auditing | Compliance Review | IoT Security Auditing | Towards a Standards-Based IoT |
| [293] | Cloud Security | Cloud Deployment | Cloud Security Protocols | Better Cloud Security |
| [294] | IoT Ecosystem Security | IoT Ecosystem Analysis | Comprehensive IoT Security | Ecosystems should have more protection. |
| [295] | Data Redundancy | Cloud Testing | Distributed Data Storage | Improved Data Quality Through Redundancy |
| [296] | Intrusion Prevention | Field Implementation | Behavior-Based Intrusion Detection | Security Upgraded to Prevent Break-ins |
| [297] | Real-time Monitoring | Live Healthcare Environment | AI-Driven Real-time Analysis | Real-time Threat Detection |
| [298] | Privacy-Preserving Analytics | Data Analytics Experiment | Differential Privacy Techniques | Security Analysis of Private Data |
| [299] | End-User Training | User Education | IoT Security Training Program | Users Now Pay More Attention to Security Issues |
| [300] | Access Control | System Testing | Role-Based Access Policies | Improvements to the Automated Entry System |
| [301] | Data Backup & Recovery | Disaster Recovery Simulation | Automated Data Backup | Improved Data Recovery |
| [302] | Vendor Security | Vendor Evaluation | Vendor Security Assessments | Safety Measures Enhanced at Supplier Locations |
| [303] | Zero Trust Architecture | Network Testing | Zero Trust Model Implementation | Network Security Improvements |
| [304] | Supply Chain Security | Supply Chain Analysis | Supply Chain Auditing | Increased Supply Chain Security |
| [305] | Threat Intelligence | Threat Analysis | Threat Intelligence Integration | Safety Measures to Avoid Threats |
| [306] | Mobile Device Security | Mobile Device Testing | Mobile Device Management | Mobile Device Security, Improved |
| [307] | Wireless Network Security | Wireless Network Testing | WPA3 Encryption | Wireless Network Security, Enhanced |
| [308] | Malware Protection | Malware Analysis | Advanced Malware Detection | Anti-Malware Protections Strengthened |
| [309] | Data Anonymization | Data Anonymization Experiment | Privacy-Preserving Data Techniques | Confidentiality of Medical Records |
| [310] | Device Lifecycle Management | Device Lifecycle Analysis | Device Lifecycle Tracking | Improvements in Mobile Device Management |
| [311] | Continuous Monitoring | Live System Monitoring | Real-time Security Monitoring | Improved Constant Monitoring |
| [312] | User Authorization | Authorization Testing | Authorization Protocols | More Secure Sign-In Methods |
| [313] | Biomedical Data Protection | Healthcare Data Analysis | Medical Data Encryption | Private Medical Records |
| [314] | Security Awareness Training | Workforce Education | Employee Security Training | Workers' Consciousness Raise |
| [315] | Compliance Enforcement | Compliance Validation | Automated Compliance Checks | Strengthened Enforcement and Supervised Monitoring of Compliance |
| [316] | Data Retention Policies | Policy Implementation | Data Retention Guidelines | Storage Capacity Limits |
| [317] | Third-Party Security | Vendor Assessment | Third-Party Audits | Protection Against Unauthorized Entities Improved |
| [318] | Geofencing | Geofencing Experiment | Location-Based Access Control | Enhanced Safety Measures in Various Locations |
| [319] | Data Access Logging | Log Analysis | Access Log Implementation | Better Recording of Data Access |
| Sl. No. | Open Research Issue | Description |
|---|---|---|
| 1 | IoMT Security Frameworks | Create thorough patient data protection measures for IoMT. |
| 2 | Interoperability in IoMT | Fix the disconnects between IoMT gadgets and infrastructure. |
| 3 | Privacy-Preserving IoMT | Determine what measures may be used to ensure patients' privacy while sharing health information via IoMT devices. |
| 4 | Edge Computing for IoMT | See whether the low-latency processing and analytics offered by edge computing can help IoMT. |
| 5 | Machine Learning for Disease Prediction | Build ML models for early disease detection using IoMT patient data. |
| 6 | IoMT Data Analytics | It's important to investigate how we can make sense of all the data generated by IoMT devices. |
| 7 | Secure IoMT Communication | Secure communication mechanisms for IoMT are needed to safeguard patient data as it travels from devices to healthcare professionals. |
| 8 | IoMT Device Management | Find methods to enhance IoMT gadget management and maintenance in hospitals and other healthcare facilities. |
| 9 | Telemedicine and IoMT | Examine how Internet of Medical Things (IoMT) might enhance telemedicine for the benefit of remote patients. |
| 10 | Regulatory Compliance in IoMT | Examine the compliance and regulatory requirements for implementing IoMT in healthcare settings. |
| 11 | IoMT-Based Chronic Disease Management | To better manage chronic diseases like diabetes and hypertension, you should develop a strategy for incorporating IoMT. |
| 12 | IoMT and Elderly Care | Find out how the Internet of Medical Things may assist in the care, monitoring, and improvement of the quality of life for the elderly. |
| 13 | IoMT and Pediatrics | Explore how IoMT may be used to monitoring a child's health and development in the field of pediatrics. |
| 14 | Security of IoHT Data | Investigate methods of securing sensitive patient data during IoHT transmission. |
| 15 | IoHT for Public Health | Research the potential of IoHT for application in public health initiatives, including disease surveillance and outbreak prevention. |
| 16 | IoMT Data Sharing Standards | Design protocols to ensure the privacy and integrity of data sent between IoMT devices and healthcare infrastructures. |
| 17 | AI and IoMT Integration | Investigate the potential of AI in IoMT for enhancing clinical analysis and decision making. |
| 18 | Smart IoMT Wearables | Read up on the development of high-tech wearables for continuous health monitoring and improvement. |
| 19 | Patient Engagement with IoMT | Explore options for encouraging more patients to try IoMT and continue with their treatments. |
| 20 | Data Ethics in IoMT | Find out more about the ethical challenges that the IoMT's data collection, processing, and storage methods present. |
| 21 | IoMT for Mental Health | Investigate the potential of IoMT for monitoring and improving people's emotional well-being. |
| 22 | IoMT for Postoperative Care | Consider how the IoMT might enhance postoperative care, monitoring, and healing. |
| 23 | AI-Driven IoMT Predictive Maintenance | Develop AI-based predictive maintenance solutions for IoMT devices to stop breakdowns before they happen. |
| 24 | IoMT in Remote Areas | Study the application of IoMT in remote and impoverished areas with poor healthcare access. |
| 25 | IoMT for Drug Adherence | Investigation of IoMT's potential to improve medication adherence may lead to better treatment outcomes. |
| 26 | IoHT and Global Health | Learn more about the potential of IoHT in improving healthcare delivery in low-resource settings and addressing global health challenges. |
| 27 | IoMT-Based Health Gamification | Make games for IoMT that encourage healthy habits and patient engagement. |
| 28 | IoMT Data Security Protocols | Research cutting-edge security methods to keep IoMT data secure from hackers and other cyber criminals. |
| 29 | IoMT in Emergency Medicine | Take a look at how topics like triage and life support are being handled using IoMT in the field of emergency care. |
| 30 | IoMT and Wearable ECG Devices | Examine how non-invasive, wearable ECG monitoring technologies have developed and what their future potential is. |
| 31 | IoMT and Wearable Blood Glucose Monitors | Study how well and how often continuous glucose monitoring work for those with diabetes. |
| 32 | IoMT in Oncology | Investigate the potential benefits of IoMT in cancer diagnosis, treatment, and follow-up. |
| 33 | IoMT in Rehabilitation | Find out whether IoMT can help the healing processes of PT and OT by looking into it. |
| 34 | IoMT Data Visualization | Develop effective data visualization techniques for displaying IoMT-generated data to medical professionals. |
| 35 | IoMT and Health Insurance | Examine the potential effects of IoMT on healthcare insurance, specifically the role of individual pricing models. |
| 36 | IoMT in Dentistry | Consider the potential of IoMT to enhance dental care and the monitoring of oral health. |
| 37 | IoMT in Radiology | Explore the potential of IoMT in radiology and medical imaging for improving diagnosis and treatment. |
| 38 | IoMT and Hospital Operations | Consider the ways in which IoMT might enhance processes like hospital administration and patient flow. |
| 39 | IoMT for Pregnancy Monitoring | Explore the possibilities of IoMT in pregnancy monitoring to keep mom and baby healthy. |
| 40 | IoMT for Cardiac Rehabilitation | Explore how IoMT may contribute to better heart health and rehabilitation programs. |
| 41 | IoMT and Electronic Health Records (EHR) | Research how IoMT data may be included into EHR systems for comprehensive patient records. |
| 42 | IoMT in Smart Homes | Study the potential for IoMT to enhance the health and happiness of linked home dwellers. |
| 43 | IoMT and Healthcare Analytics | Examine IoMT data-using healthcare analytics technology to make educated judgments. |
| 44 | IoMT and Pharmacovigilance | Find out how IoMT can improve the safety and side effect monitoring of medications in the real world. |
| 45 | IoMT and Emergency Response | Explore how improving current systems with IoMT might shorten response times in times of emergency. |
| 46 | IoMT in Personalized Nutrition | Investigate the potential of IoMT for making health-specific dietary recommendations to individuals. |
| 47 | IoMT and Health IoT Devices | Consider the potential of integrating IoMT with other IoT health devices to build a more complete health ecosystem. |
| 48 | IoMT and Patient Empowerment | Investigate how IoMT may improve patient participation in healthcare decision-making. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





