Submitted:
15 February 2024
Posted:
16 February 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- Development of a Comprehensive IoMT Security Dataset: This paper introduces the CICIoMT2024 dataset, an advanced effort to construct a realistic and multi-protocol benchmark for the security of the Internet of Medical Things. By executing 18 different cyberattacks against a diverse set of 40 IoMT devices, we contribute to the Healthcare field by providing a comprehensive dataset containing most of the protocols in the devices in this field, namely Wi-Fi, MQTT, and Bluetooth protocols.
- Innovative Methodology in IoMT Attack Simulation and Data Collection: A unique aspect of this paper is the systematic approach to simulating and capturing IoMT network traffic under various cyberattack scenarios. Considering the complex network of healthcare organizations, it is essential to consider several attributes, such as understanding the effects of different types of attacks, including DDoS, DoS, Recon, MQTT, and spoofing, using a combination of real and simulated devices. Advanced network monitoring techniques and specialized hardware, such as network taps, ensure the high fidelity of data collection.
- Profiling IoMT Device Lifecycle for Enhanced Security Understanding: This research goes beyond merely conducting attacks on IoMT devices. We also attempt to capture the lifecycle of these devices in different vital phases of a device from the moment they join the network until they leave. Mobility in healthcare organizations is considered to be a regular aspect. Thus, profiling the lifecycle of these devices, encompassing various operational phases such as power interaction, idle, active, and interaction states, becomes very important. This study offers an in-depth understanding of the devices’ behavioral patterns by meticulously capturing and analyzing the behavior of IoMT devices from the moment they join the network. This profiling is critical in identifying and mitigating potential security vulnerabilities.
- Multi-dimensional Evaluation: This research extends beyond dataset creation to evaluate the efficacy of multiple machine learning algorithms in detecting and classifying IoMT cyberattacks. By assessing techniques like Logistic Regression, Adaboost, Random Forest, and Deep Neural Networks, the study not only benchmarks the current state of ML in IoMT security but also opens avenues for future exploration in algorithm optimization and feature engineering.
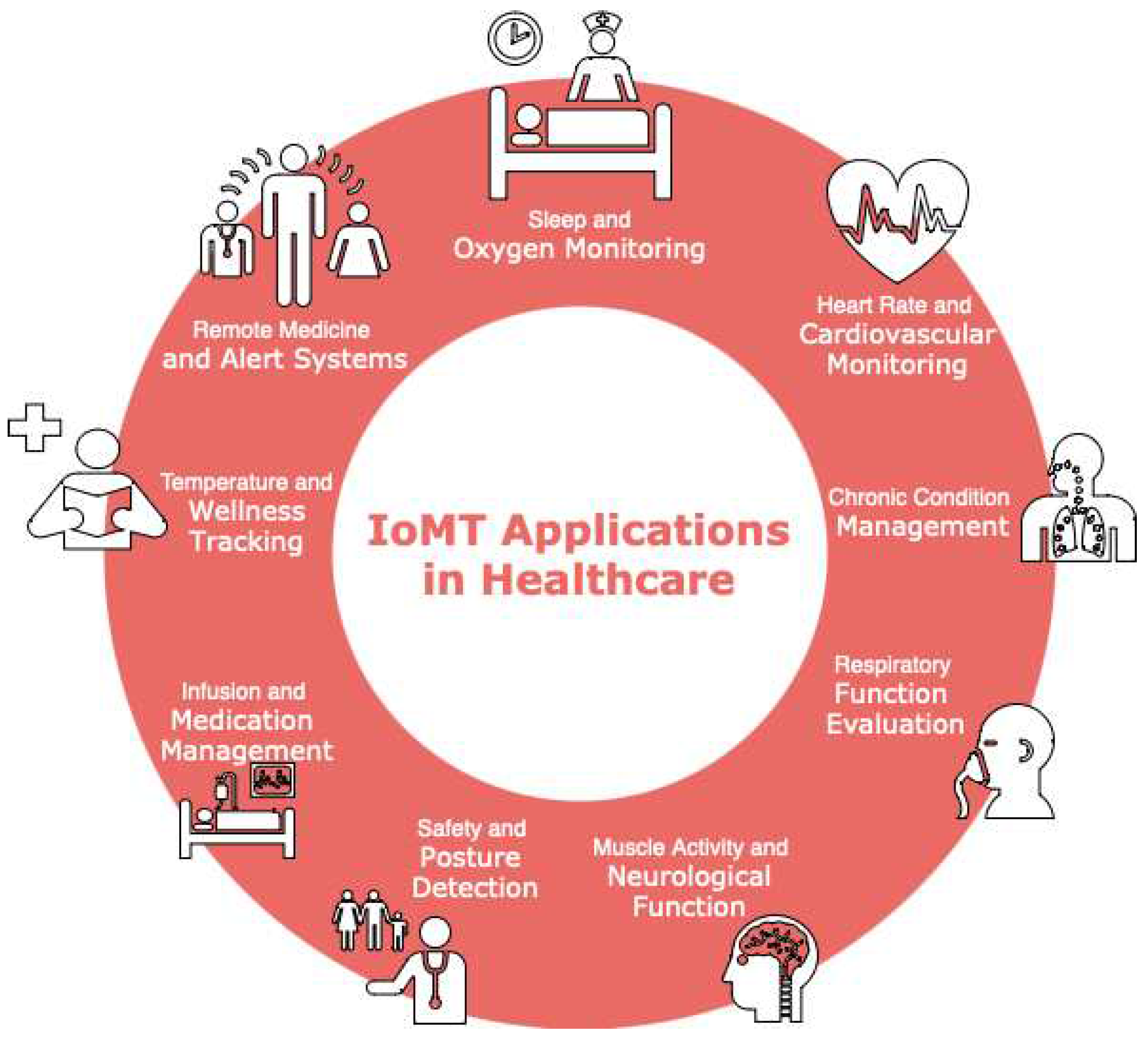
2. Internet of Medical Things (IoMT) in Healthcare
3. Healthcare dataset in IoT domain
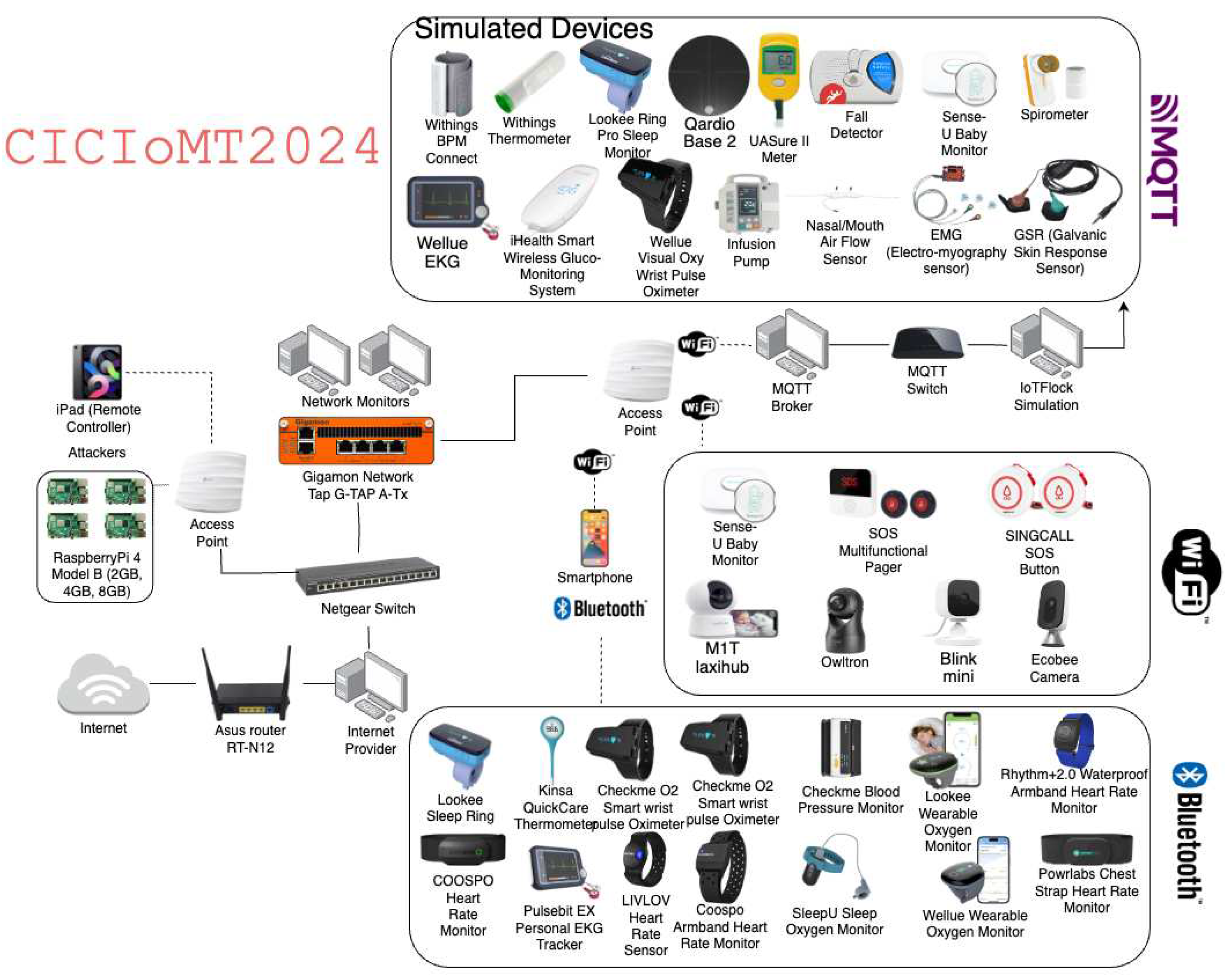
4. The Proposed CICIoMT2024
4.1. CIC IoT lab
4.2. IoMT Topology
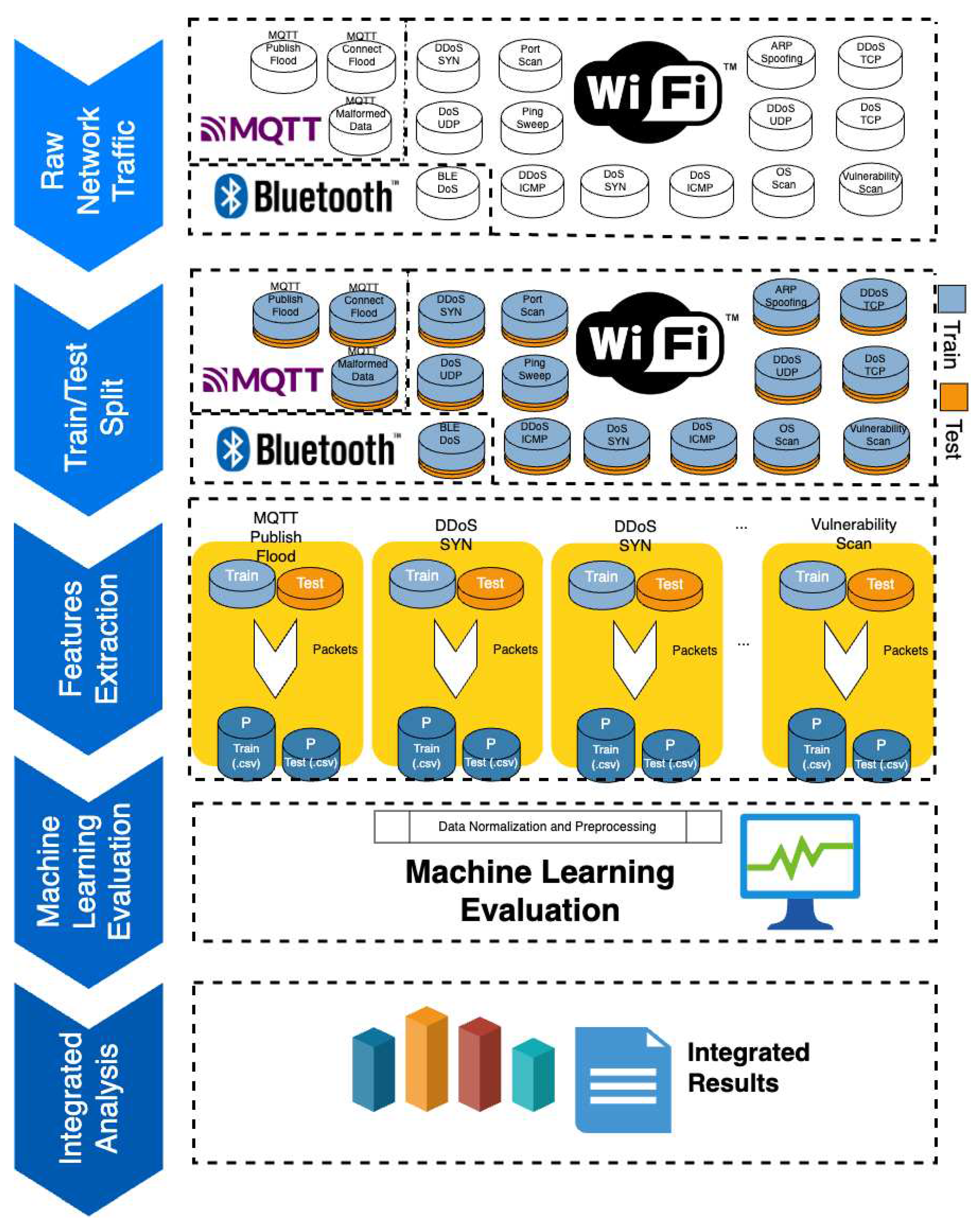
4.3. Generation of Malicious Traffic
4.3.1. Wi-Fi
4.3.2. MQTT
4.3.3. Bluetooth Low Energy (BLE)
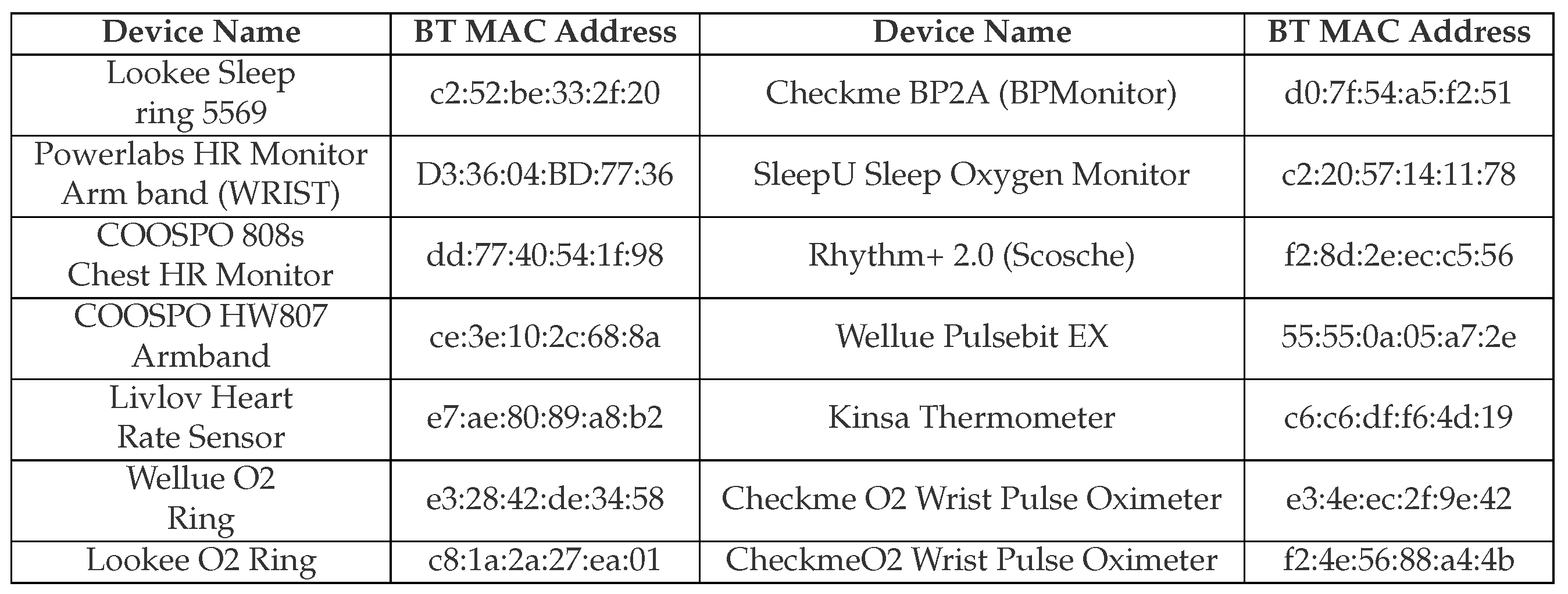
- Lookee Sleep Ring: showcased resilience against the attack, operating without any noticeable disruptions.
- Powerlabs HR Monitor Arm Band: Similarly, this armband maintained its standard functionality during the attack.
- COOSPO HW807 Armband: In stark contrast, our attack had a significant impact on this device. It became overwhelmed and subsequently turned off.
- Livlov Heart Rate Sensor: This heart rate sensor managed to resist our attack, operating without any observed disruptions.
- Wellue O2 Ring: This device remained unaffected and continued to operate normally.
- Lookee O2 Ring: This device was vulnerable to our attack. Upon execution, the device became overwhelmed and turned off.
- Checkme BP2A: This device displayed a unique behavior. While it stored data during the attack, it only transmitted this data once a Bluetooth connection was re-established.
- SleepU Sleep Oxygen Monitor: This monitor resisted our attack, showcasing its resilience by maintaining standard functionality.
- Rhythm+ 2.0 (Scosche): significantly affected by our attack, this device became overwhelmed and subsequently shut down.
- Wellue Pulsebit EX: This device withstood the attack and continued to operate without disruptions.
- Checkme O2 Smart Wrist Pulse Oximeter: It resisted our attack, continuing its standard operations.
- Kinsa Thermometer: Our attack impacted this device uniquely. While under attack, it was not possible to reset the connection by turning off the thermometer. The only methods to terminate the connection were to either let the battery deplete or to halt the attack. The device behaved as it remained connected throughout the attack.
4.4. IoMT Profiling
4.4.1. Power Experiments
- Singcall Sensor: This device does not explicitly have a power button instead it has a reset button. The device is disconnected from the network when reset and connects back to it when we reconnect the device to the app.
- SOS Multifunctional Pager: This device includes the button and its base station. In these experiments, since the button depended on the base station, the base station was powered on and off.
- Sense U Baby: This device includes an MQTT base station (publisher) and a sensor that collects data and sends it to the base station. The data collected during this experiment is that of the base station. The sensor was excluded since it does not take part in communicating with the cloud service and only repeatedly collects data and transmits it to the base station for publishing. This behavior is later analyzed in idle/active experiments.
4.4.2. Idle Experiments
4.4.3. Active Experiments
4.4.4. Interaction Experiments
- Physical: carried out where devices could be interacted with using physical buttons. These experiments were combined with LAN and WAN experiments where applicable, i.e., the apps were either connected to the same network as the IoMT devices or connected to another network.
- LAN: These experiments were carried out by making use of the device’s companion apps, and interacting with them while being on the same network as the IoMT devices.
- WAN: These experiments were carried out by making use of the device’s companion apps, and interacting with them while being on another network as the IoMT devices.
5. Methodology
- Accuracy: evaluates the classification models by calculating the proportion of correct predictions in a dataset using the following expression:
- Recall: ratio classes identified to the total number of occurrences of this particular class:
- Precision: ratio of correctly classified labels to the total number of positive classifications:
- F1-Score: geometric average of precision and recall:
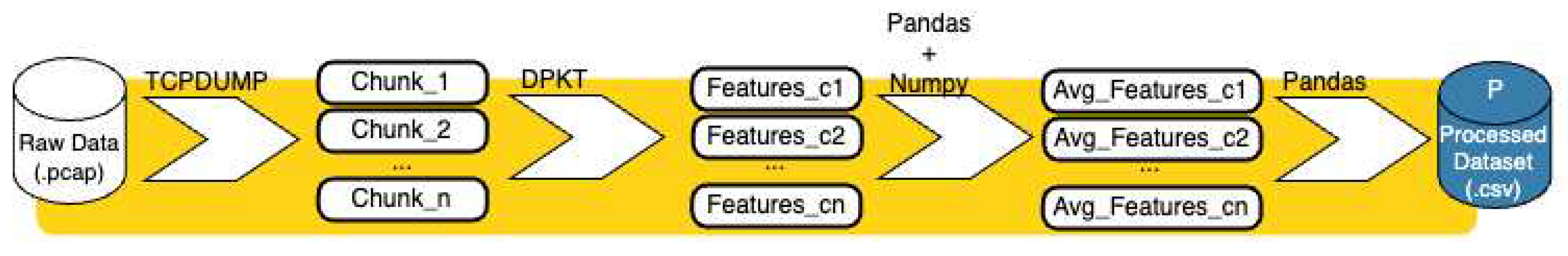
6. Feature Extraction and Data Description
7. Machine Learning (ML) Evaluation
8. Conclusion
Acknowledgments
References
- Madakam, S.; Lake, V.; Lake, V.; Lake, V.; et al. Internet of Things (IoT): A literature review. Journal of Computer and Communications 2015, 3, 164. [Google Scholar] [CrossRef]
- Farooq, M.U.; Waseem, M.; Mazhar, S.; Khairi, A.; Kamal, T. A review on internet of things (IoT). International journal of computer applications 2015, 113, 1–7. [Google Scholar] [CrossRef]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of things for smart cities. IEEE Internet of Things journal 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Mukherjee, A.; Pal, A.; Misra, P. Data analytics in ubiquitous sensor-based health information systems. In Proceedings of the 2012 Sixth International Conference on Next Generation Mobile Applications, Services and Technologies. IEEE; 2012; pp. 193–198. [Google Scholar] [CrossRef]
- Yuan, B.; Herbert, J. A cloud-based mobile data analytics framework: case study of activity recognition using smartphone. In Proceedings of the 2014 2nd IEEE International Conference on Mobile Cloud Computing, Services, and Engineering. IEEE; 2014; pp. 220–227. [Google Scholar] [CrossRef]
- Loke, S.W. Supporting ubiquitous sensor-cloudlets and context-cloudlets: Programming compositions of context-aware systems for mobile users. Future Generation Computer Systems 2012, 28, 619–632. [Google Scholar] [CrossRef]
- Hsu, C.W.; Yeh, C.C. Understanding the factors affecting the adoption of the Internet of Things. Technology Analysis & Strategic Management 2017, 29, 1089–1102. [Google Scholar]
- Riggins, F.J.; Wamba, S.F. Research directions on the adoption, usage, and impact of the internet of things through the use of big data analytics. In Proceedings of the 2015 48th Hawaii international conference on system sciences. IEEE; 2015; pp. 1531–1540. [Google Scholar] [CrossRef]
- Bojan, T.M.; Kumar, U.R.; Bojan, V.M. An internet of things based intelligent transportation system. In Proceedings of the 2014 IEEE international conference on vehicular electronics and safety. IEEE; 2014; pp. 174–179. [Google Scholar] [CrossRef]
- Kassab, M.; DeFranco, J.; Laplante, P. A systematic literature review on internet of things in education: Benefits and challenges. Journal of computer Assisted learning 2020, 36, 115–127. [Google Scholar] [CrossRef]
- Hossein Motlagh, N.; Mohammadrezaei, M.; Hunt, J.; Zakeri, B. Internet of Things (IoT) and the energy sector. Energies 2020, 13, 494. [Google Scholar] [CrossRef]
- Vishnu, S.; Ramson, S.J.; Jegan, R. Internet of medical things (IoMT)-An overview. In Proceedings of the 2020 5th international conference on devices, circuits and systems (ICDCS). IEEE; 2020; pp. 101–104. [Google Scholar] [CrossRef]
- Ghubaish, A.; Salman, T.; Zolanvari, M.; Unal, D.; Al-Ali, A.; Jain, R. Recent advances in the internet-of-medical-things (IoMT) systems security. IEEE Internet of Things Journal 2020, 8, 8707–8718. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Nawaz, M.H.; Ulusar, U.D. Intelligence in the Internet of Medical Things era: A systematic review of current and future trends. Computer Communications 2020, 150, 644–660. [Google Scholar] [CrossRef]
- Wei, K.; Zhang, L.; Guo, Y.; Jiang, X. Health monitoring based on internet of medical things: architecture, enabling technologies, and applications. IEEE Access 2020, 8, 27468–27478. [Google Scholar] [CrossRef]
- Wu, Q.; Tang, P.; Yang, M. Data processing platform design and algorithm research of wearable sports physiological parameters detection based on medical internet of things. Measurement 2020, 165, 108172. [Google Scholar] [CrossRef]
- Yadav, N.; Keshtkar, F.; Schweikert, C.; Crocetti, G. Cradle: An IOMT psychophysiological analytics platform. In Proceedings of the Proceedings of the Workshop on Human-Habitat for Health (H3): Human-Habitat Multimodal Interaction for Promoting Health and Well-Being in the Internet of Things Era, 2018, pp.; pp. 1–7. [CrossRef]
- Kumar, N.; Kaushal, R.K.; Panda, S.N. IoT based smart and portable system for remote patient monitoring and drug delivery. In Proceedings of the Journal of Physics: Conference Series. IOP Publishing, Vol. 1950; 2021; p. 012017. [Google Scholar] [CrossRef]
- Yew, H.T.; Ng, M.F.; Ping, S.Z.; Chung, S.K.; Chekima, A.; Dargham, J.A. Iot based real-time remote patient monitoring system. In Proceedings of the 2020 16th IEEE international colloquium on signal processing &, 2020, its applications (CSPA). IEEE; pp. 176–179. [CrossRef]
- Lu, Y.; Da Xu, L. Internet of Things (IoT) cybersecurity research: A review of current research topics. IEEE Internet of Things Journal 2018, 6, 2103–2115. [Google Scholar] [CrossRef]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A survey of iot-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Communications Surveys & Tutorials 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Kaur, B.; Dadkhah, S.; Shoeleh, F.; Neto, E.C.P.; Xiong, P.; Iqbal, S.; Lamontagne, P.; Ray, S.; Ghorbani, A.A. Internet of Things (IoT) security dataset evolution: Challenges and future directions. Internet of Things, 1007. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT security: An exhaustive survey on IoT vulnerabilities and a first empirical look on Internet-scale IoT exploitations. IEEE Communications Surveys & Tutorials 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Butun, I.; Österberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, attacks, and countermeasures. IEEE Communications Surveys & Tutorials 2019, 22, 616–644. [Google Scholar] [CrossRef]
- Booth, H.; Rike, D.; Witte, G.A. The national vulnerability database (nvd): Overview 2013.
- Danso, P.K.; Dadkhah, S.; Neto, E.C.P.; Zohourian, A.; Molyneaux, H.; Lu, R.; Ghorbani, A.A. Transferability of Machine Learning Algorithm for IoT Device Profiling and Identification. IEEE Internet of Things Journal 2023. [Google Scholar] [CrossRef]
- Hassan, W.H.; et al. Current research on Internet of Things (IoT) security: A survey. Computer networks 2019, 148, 283–294. [Google Scholar] [CrossRef]
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A real-time dataset and benchmark for large-scale attacks in IoT environment 2023. [CrossRef]
- Koutras, D.; Stergiopoulos, G.; Dasaklis, T.; Kotzanikolaou, P.; Glynos, D.; Douligeris, C. Security in IoMT communications: A survey. Sensors 2020, 20, 4828. [Google Scholar] [CrossRef] [PubMed]
- Sivanathan, A.; Gharakheili, H.H.; Sivaraman, V. Managing IoT cyber-security using programmable telemetry and machine learning. IEEE Transactions on Network and Service Management 2020, 17, 60–74. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Communications Surveys & Tutorials 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Suresh, M.; Anitha, R. Evaluating machine learning algorithms for detecting DDoS attacks. In Proceedings of the Advances in Network Security and Applications: 4th International Conference, CNSA 2011, Chennai, India, 2011 4. Springer, 2011, July 15-17; pp. 441–452. [CrossRef]
- Zekri, M.; El Kafhali, S.; Aboutabit, N.; Saadi, Y. DDoS attack detection using machine learning techniques in cloud computing environments. In Proceedings of the 2017 3rd international conference of cloud computing technologies and applications (CloudTech). IEEE; 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Tavana, M.; Ozger, M.; Baltaci, A.; Schleicher, B.; Schupke, D.; Cavdar, C. Wireless power transfer for aircraft IoT applications: System design and measurements. IEEE Internet of Things Journal 2021, 8, 11834–11846. [Google Scholar] [CrossRef]
- Neto, E.C.P.; Dadkhah, S.; Sadeghi, S.; Molyneaux, H.; Ghorbani, A.A. A review of Machine Learning (ML)-based IoT security in healthcare: A dataset perspective. Computer Communications 2023. [Google Scholar] [CrossRef]
- Dwivedi, R.; Mehrotra, D.; Chandra, S. Potential of Internet of Medical Things (IoMT) applications in building a smart healthcare system: A systematic review. Journal of oral biology and craniofacial research 2022, 12, 302–318. [Google Scholar] [CrossRef] [PubMed]
- Mbengue, S.M.; Diallo, O.; El Hadji, M.N.; Rodrigues, J.J.; Neto, A.; Al-Muhtadi, J. Internet of medical things: Remote diagnosis and monitoring application for diabetics. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC). IEEE; 2020; pp. 583–588. [Google Scholar] [CrossRef]
- Subramaniam, E.V.D.; Srinivasan, K.; Qaisar, S.M.; Pławiak, P. Interoperable IoMT Approach for Remote Diagnosis with Privacy-Preservation Perspective in Edge Systems. Sensors 2023, 23, 7474. [Google Scholar] [CrossRef] [PubMed]
- Joshi, S.; Joshi, S. A sensor based secured health monitoring and alert technique using iomt. In Proceedings of the 2019 2nd International Conference on Intelligent Communication and Computational Techniques (ICCT). IEEE; 2019; pp. 152–156. [Google Scholar] [CrossRef]
- Khan, M.A.; Algarni, F. A healthcare monitoring system for the diagnosis of heart disease in the IoMT cloud environment using MSSO-ANFIS. IEEE Access 2020, 8, 122259–122269. [Google Scholar] [CrossRef]
- Rachakonda, L.; Mohanty, S.P.; Kougianos, E. cStick: a calm stick for fall prediction, detection and control in the IoMT framework. In Proceedings of the IFIP International Internet of Things Conference. Springer; 2021; pp. 129–145. [Google Scholar]
- Gupta, A.; Srivastava, R.; Gupta, H.; Kumar, B. IoT based fall detection monitoring and alarm system for elderly. In Proceedings of the 2020 IEEE 7th Uttar Pradesh Section International Conference on Electrical, Electronics and Computer Engineering (UPCON). IEEE; 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Arora, S. IoMT (Internet of Medical Things): Reducing cost while improving patient care. IEEE pulse 2020, 11, 24–27. [Google Scholar] [CrossRef] [PubMed]
- Karagiannis, D.; Mitsis, K.; Nikita, K.S. Development of a Low-Power IoMT Portable Pillbox for Medication Adherence Improvement and Remote Treatment Adjustment. Sensors 2022, 22, 5818. [Google Scholar] [CrossRef] [PubMed]
- Villanueva-Miranda, I.; Nazeran, H.; Martinek, R. A semantic interoperability approach to heterogeneous internet of medical things (IoMT) platforms. In Proceedings of the 2018 IEEE 20th international conference on e-Health networking, applications and services (HealthCom). IEEE; 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Kavitha, D.; Subramaniam, C. Security threat management by software obfuscation for privacy in internet of medical thing (IoMT) application. Journal of Computational and Theoretical Nanoscience 2017, 14, 3100–3114. [Google Scholar] [CrossRef]
- Piché, M.E.; Tchernof, A.; Després, J.P. Obesity phenotypes, diabetes, and cardiovascular diseases. Circulation research 2020, 126, 1477–1500. [Google Scholar] [CrossRef]
- Halson, S.L. Sleep monitoring in athletes: motivation, methods, miscalculations and why it matters. Sports medicine 2019, 49, 1487–1497. [Google Scholar] [CrossRef]
- Wang, J.; Chen, M.; Chen, Q.; Wang, H. Medical Oxygen Sensor Based on Acoustic Resonance Frequency Tracking Using FPGA. IEEE Sensors Journal 2022, 22, 21281–21286. [Google Scholar] [CrossRef]
- Kotronis, C.; Routis, I.; Politi, E.; Nikolaidou, M.; Dimitrakopoulos, G.; Anagnostopoulos, D.; Amira, A.; Bensaali, F.; Djelouat, H. Evaluating Internet of Medical Things (IoMT)-based systems from a human-centric perspective. Internet of Things 2019, 8, 100125. [Google Scholar] [CrossRef]
- Razdan, S.; Sharma, S. Internet of medical things (IoMT): Overview, emerging technologies, and case studies. IETE technical review 2022, 39, 775–788. [Google Scholar] [CrossRef]
- Zhong, W.; Ji, Z.; Sun, C. A review of monitoring methods for cerebral blood oxygen saturation. In Proceedings of the Healthcare. MDPI, Vol. 9; 2021; p. 1104. [Google Scholar] [CrossRef]
- Wilson, F.P.; Martin, M.; Yamamoto, Y.; Partridge, C.; Moreira, E.; Arora, T.; Biswas, A.; Feldman, H.; Garg, A.X.; Greenberg, J.H.; et al. Electronic health record alerts for acute kidney injury: multicenter, randomized clinical trial. Bmj 2021, 372. [Google Scholar] [CrossRef] [PubMed]
- Hu, R.; Michel, B.; Russo, D.; Mora, N.; Matrella, G.; Ciampolini, P.; Cocchi, F.; Montanari, E.; Nunziata, S.; Brunschwiler, T. An unsupervised behavioral modeling and alerting system based on passive sensing for elderly care. Future Internet 2021, 13, 6. [Google Scholar] [CrossRef]
- Khan, M.M.; Mehnaz, S.; Shaha, A.; Nayem, M.; Bourouis, S.; et al. IoT-based smart health monitoring system for COVID-19 patients. Computational and Mathematical Methods in Medicine 2021, 2021. [Google Scholar] [CrossRef]
- Hashim, N.; Norddin, N.; Idris, F.; Yusoff, S.; Zahari, M. IoT blood pressure monitoring system. Indonesian Journal of Electrical Engineering and Computer Science 2020, 19, 1384–1390. [Google Scholar] [CrossRef]
- Chalmers, T.; Hickey, B.A.; Newton, P.; Lin, C.T.; Sibbritt, D.; McLachlan, C.S.; Clifton-Bligh, R.; Morley, J.; Lal, S. Stress watch: The use of heart rate and heart rate variability to detect stress: A pilot study using smart watch wearables. Sensors 2021, 22, 151. [Google Scholar] [CrossRef]
- Romano, C.; Schena, E.; Formica, D.; Massaroni, C. Comparison between chest-worn accelerometer and gyroscope performance for heart rate and respiratory rate monitoring. Biosensors 2022, 12, 834. [Google Scholar] [CrossRef]
- Dian, F.J.; Vahidnia, R.; Rahmati, A. Wearables and the Internet of Things (IoT), applications, opportunities, and challenges: A Survey. IEEE access 2020, 8, 69200–69211. [Google Scholar] [CrossRef]
- Arquilla, K.; Webb, A.K.; Anderson, A.P. Textile electrocardiogram (ECG) electrodes for wearable health monitoring. Sensors 2020, 20, 1013. [Google Scholar] [CrossRef] [PubMed]
- Serhani, M.A.; T. El Kassabi, H.; Ismail, H.; Nujum Navaz, A. ECG monitoring systems: Review, architecture, processes, and key challenges. Sensors 2020, 20, 1796. [Google Scholar] [CrossRef] [PubMed]
- Brice, J.H.; Cyr, J.M.; Hnat, A.T.; Wei, T.L.; Principe, S.; Thead, S.E.; Delbridge, T.R.; Winslow, J.E.; Studnek, J.R.; Fernandez, A.R.; et al. Assessment of key health and wellness indicators among North Carolina emergency medical service providers. Prehospital Emergency Care 2019, 23, 179–186. [Google Scholar] [CrossRef] [PubMed]
- Khan, M.F.; Ghazal, T.M.; Said, R.A.; Fatima, A.; Abbas, S.; Khan, M.; Issa, G.F.; Ahmad, M.; Khan, M.A.; et al. An iomt-enabled smart healthcare model to monitor elderly people using machine learning technique. Computational Intelligence and Neuroscience 2021, 2021. [Google Scholar] [CrossRef] [PubMed]
- Chamberlain, S.D.; Singh, I.; Ariza, C.; Daitch, A.; Philips, P.; Dalziel, B.D. Real-time detection of COVID-19 epicenters within the United States using a network of smart thermometers. MedRxiv, 2020. [Google Scholar] [CrossRef]
- Chandrasekaran, R.; Katthula, V.; Moustakas, E. Patterns of use and key predictors for the use of wearable health care devices by US adults: insights from a national survey. Journal of medical Internet research 2020, 22, e22443. [Google Scholar] [CrossRef] [PubMed]
- Wu, M.; Luo, J. Wearable technology applications in healthcare: a literature review. Online J. Nurs. Inform 2019, 23. [Google Scholar]
- Walker, R.C.; Tong, A.; Howard, K.; Palmer, S.C. Patient expectations and experiences of remote monitoring for chronic diseases: systematic review and thematic synthesis of qualitative studies. International journal of medical informatics 2019, 124, 78–85. [Google Scholar] [CrossRef] [PubMed]
- Fang, M.; Wang, D.; Coresh, J.; Selvin, E. Trends in diabetes treatment and control in US adults, 1999–2018. New England Journal of Medicine 2021, 384, 2219–2228. [Google Scholar] [CrossRef] [PubMed]
- Lamonaca, F.; Carnì, D.L.; Spagnuolo, V.; Grimaldi, G.; Bonavolontà, F.; Liccardo, A.; Moriello, R.S.L.; Colaprico, A. A new measurement system to boost the IoMT for the blood pressure monitoring. In Proceedings of the 2019 IEEE International Symposium on Measurements &, 2019, Networking (M&N). IEEE; pp. 1–6. [CrossRef]
- Alarcón-Paredes, A.; Francisco-García, V.; Guzmán-Guzmán, I.P.; Cantillo-Negrete, J.; Cuevas-Valencia, R.E.; Alonso-Silverio, G.A. An IoT-based non-invasive glucose level monitoring system using raspberry pi. Applied Sciences 2019, 9, 3046. [Google Scholar] [CrossRef]
- Yang, Y.; Yang, M.; Shen, C.; Wang, F.; Yuan, J.; Li, J.; Zhang, M.; Wang, Z.; Xing, L.; Wei, J.; et al. Evaluating the accuracy of different respiratory specimens in the laboratory diagnosis and monitoring the viral shedding of 2019-nCoV infections. MedRxiv, 2020. [Google Scholar] [CrossRef]
- Nicolò, A.; Massaroni, C.; Schena, E.; Sacchetti, M. The importance of respiratory rate monitoring: From healthcare to sport and exercise. Sensors 2020, 20, 6396. [Google Scholar] [CrossRef]
- Reshiwaran, A.; Jegatheswaran, L.; Sakira, I.J.; Abd Rahman, N.A. A Review on IoMT device Vulnerabilities and Countermeasures. In Proceedings of the Journal of Physics: Conference Series. IOP Publishing, Vol. 1712; 2020; p. 012020. [Google Scholar] [CrossRef]
- Sui, S.X.; Williams, L.J.; Holloway-Kew, K.L.; Hyde, N.K.; Pasco, J.A. Skeletal muscle health and cognitive function: a narrative review. International journal of molecular sciences 2020, 22, 255. [Google Scholar] [CrossRef] [PubMed]
- Alam, M.G.R.; Abedin, S.F.; Moon, S.I.; Talukder, A.; Hong, C.S. Healthcare IoT-based affective state mining using a deep convolutional neural network. IEEE Access 2019, 7, 75189–75202. [Google Scholar] [CrossRef]
- Warmerdam, E.; Hausdorff, J.M.; Atrsaei, A.; Zhou, Y.; Mirelman, A.; Aminian, K.; Espay, A.J.; Hansen, C.; Evers, L.J.; Keller, A.; et al. Long-term unsupervised mobility assessment in movement disorders. The Lancet Neurology 2020, 19, 462–470. [Google Scholar] [CrossRef]
- Hong, Z.; Hong, M.; Wang, N.; Ma, Y.; Zhou, X.; Wang, W. A wearable-based posture recognition system with AI-assisted approach for healthcare IoT. Future Generation Computer Systems 2022, 127, 286–296. [Google Scholar] [CrossRef]
- Mozaffari, N.; Rezazadeh, J.; Farahbakhsh, R.; Yazdani, S.; Sandrasegaran, K. Practical fall detection based on IoT technologies: A survey. Internet of things 2019, 8, 100124. [Google Scholar] [CrossRef]
- Anwary, A.R.; Cetinkaya, D.; Vassallo, M.; Bouchachia, H.; et al. Smart-Cover: A real time sitting posture monitoring system. Sensors and Actuators A: Physical 2021, 317, 112451. [Google Scholar] [CrossRef]
- Talal, M.; Zaidan, A.; Zaidan, B.; Albahri, A.S.; Alamoodi, A.H.; Albahri, O.S.; Alsalem, M.; Lim, C.K.; Tan, K.L.; Shir, W.; et al. Smart home-based IoT for real-time and secure remote health monitoring of triage and priority system using body sensors: Multi-driven systematic review. Journal of medical systems 2019, 43, 1–34. [Google Scholar] [CrossRef] [PubMed]
- Kretchy, I.A.; Asiedu-Danso, M.; Kretchy, J.P. Medication management and adherence during the COVID-19 pandemic: perspectives and experiences from low-and middle-income countries. Research in social and administrative pharmacy 2021, 17, 2023–2026. [Google Scholar] [CrossRef] [PubMed]
- Taylor, M.A.; Jones, R. Risk of medication errors with infusion pumps: a study of 1,004 events from 132 hospitals across pennsylvania. Patient Safety 2019, 1, 60–69. [Google Scholar] [CrossRef]
- Sharma, R.; Singh, D.; Gaur, P.; Joshi, D. Intelligent automated drug administration and therapy: Future of healthcare. Drug Delivery and Translational Research. [CrossRef]
- Bhuiyan, M.N.; Rahman, M.M.; Billah, M.M.; Saha, D. Internet of things (IoT): A review of its enabling technologies in healthcare applications, standards protocols, security, and market opportunities. IEEE Internet of Things Journal 2021, 8, 10474–10498. [Google Scholar] [CrossRef]
- Singh, D.; Sandhu, A.; Thakur, A.; Priyank, N. An overview of IoT hardware development platforms. Int. J. Emerg. Technol 2020, 11, 155–163. [Google Scholar]
- Capra, M.; Peloso, R.; Masera, G.; Ruo Roch, M.; Martina, M. Edge computing: A survey on the hardware requirements in the internet of things world. Future Internet 2019, 11, 100. [Google Scholar] [CrossRef]
- Hady, A.A.; Ghubaish, A.; Salman, T.; Unal, D.; Jain, R. Intrusion detection system for healthcare systems using medical and network data: A comparison study. IEEE Access 2020, 8, 106576–106584. [Google Scholar] [CrossRef]
- Ahmed, M.; Byreddy, S.; Nutakki, A.; Sikos, L.F.; Haskell-Dowland, P. ECU-IoHT: A dataset for analyzing cyberattacks in Internet of Health Things. Ad Hoc Networks 2021, 122, 102621. [Google Scholar] [CrossRef]
- Zubair, M.; Ghubaish, A.; Unal, D.; Al-Ali, A.; Reimann, T.; Alinier, G.; Hammoudeh, M.; Qadir, J. Secure Bluetooth Communication in Smart Healthcare Systems: A Novel Community Dataset and Intrusion Detection System. Sensors 2022, 22, 8280. [Google Scholar] [CrossRef] [PubMed]
- Hussain, F.; Abbas, S.G.; Shah, G.A.; Pires, I.M.; Fayyaz, U.U.; Shahzad, F.; Garcia, N.M.; Zdravevski, E. A framework for malicious traffic detection in IoT healthcare environment. Sensors 2021, 21, 3025. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.; Rompolos, K.; Sarigiannidis, P.; Argyriou, V.; Lagkas, T.; Sarigiannidis, A.; Goudos, S.; Wan, S. Modeling, detecting, and mitigating threats against industrial healthcare systems: a combined software defined networking and reinforcement learning approach. IEEE Transactions on Industrial Informatics 2021, 18, 2041–2052. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Słowińska, M.; Theodorakopoulos, G.; Burnap, P. A supervised intrusion detection system for smart home IoT devices. IEEE Internet of Things Journal 2019, 6, 9042–9053. [Google Scholar] [CrossRef]
- Mirsky, Y.; Doitshman, T.; Elovici, Y.; Shabtai, A. Kitsune: an ensemble of autoencoders for online network intrusion detection. arXiv preprint arXiv:1802.09089, arXiv:1802.09089 2018. [CrossRef]
- Guerra-Manzanares, A.; Medina-Galindo, J.; Bahsi, H.; Nõmm, S. MedBIoT: Generation of an IoT Botnet Dataset in a Medium-sized IoT Network. In Proceedings of the ICISSP; 2020; pp. 207–218. [Google Scholar] [CrossRef]
- Parmisano, A.; Garcia, S.; Erquiaga, M. A Labeled Dataset with Malicious and Benign IoT Network Traffic. Stratosphere Laboratory: Praha, Czech Republic.
- Ullah, I.; Mahmoud, Q.H. A Scheme for Generating a Dataset for Anomalous Activity Detection in IoT Networks. In Proceedings of the Canadian Conference on Artificial Intelligence; 2020; pp. 508–520. [Google Scholar] [CrossRef]
- Vaccari, I.; Chiola, G.; Aiello, M.; Mongelli, M.; Cambiaso, E. MQTTset, a New Dataset for Machine Learning Techniques on MQTT. Sensors 2020, 20, 6578. [Google Scholar] [CrossRef]
- Hindy, H.; Bayne, E.; Bures, M.; Atkinson, R.; Tachtatzis, C.; Bellekens, X. Machine Learning Based IoT Intrusion Detection System: An MQTT Case Study. arXiv preprint arXiv:2006.15340, arXiv:2006.15340 2020.
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT telemetry dataset: a new generation dataset of IoT and IIoT for data-driven Intrusion Detection Systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Dadkhah, S.; Mahdikhani, H.; Danso, P.K.; Zohourian, A.; Truong, K.A.; Ghorbani, A.A. Towards the development of a realistic multidimensional IoT profiling dataset. In Proceedings of the 2022 19th Annual International Conference on Privacy, Security & Trust (PST). IEEE; 2022; pp. 1–11. [Google Scholar]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE communications surveys & tutorials 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Alhijawi, B.; Almajali, S.; Elgala, H.; Salameh, H.B.; Ayyash, M. A survey on DoS/DDoS mitigation techniques in SDNs: Classification, comparison, solutions, testing tools and datasets. Computers and Electrical Engineering 2022, 99, 107706. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defence mechanisms in the IoT network. Telecommunication systems 2020, 73, 3–25. [Google Scholar] [CrossRef]
- Uma, M.; Padmavathi, G. A survey on various cyber attacks and their classification. Int. J. Netw. Secur. 2013, 15, 390–396. [Google Scholar] [CrossRef]
- Mazurczyk, W.; Caviglione, L. Cyber reconnaissance techniques. Communications of the ACM 2021, 64, 86–95. [Google Scholar] [CrossRef]
- Alatram, A.; Sikos, L.F.; Johnstone, M.; Szewczyk, P.; Kang, J.J. DoS/DDoS-MQTT-IoT: A dataset for evaluating intrusions in IoT networks using the MQTT protocol. Computer Networks 2023, 231, 109809. [Google Scholar] [CrossRef]
- Vaccari, I.; Aiello, M.; Cambiaso, E. SlowITe, a novel denial of service attack affecting MQTT. Sensors 2020, 20, 2932. [Google Scholar] [CrossRef] [PubMed]
- TCPDUMP. Tcpdump(1) man page. https://www.tcpdump.org/manpages/tcpdump.1.html.
- DPKT. Dpkt documentation. https://dpkt.readthedocs.io/en/latest/.
- PANDAS. pandas-dev/pandas: Pandas 2020. [CrossRef]
- Bapat, R.; Mandya, A.; Liu, X.; Abraham, B.; Brown, D.E.; Kang, H.; Veeraraghavan, M. Identifying malicious botnet traffic using logistic regression. In Proceedings of the 2018 systems and information engineering design symposium (SIEDS). IEEE; 2018; pp. 266–271. [Google Scholar] [CrossRef]
- AlShahrani, B.M.M.; et al. Classification of cyber-attack using Adaboost regression classifier and securing the network. Turkish Journal of Computer and Mathematics Education (TURCOMAT) 2021, 12, 1215–1223. [Google Scholar]
- Rehman Javed, A.; Jalil, Z.; Atif Moqurrab, S.; Abbas, S.; Liu, X. Ensemble adaboost classifier for accurate and fast detection of botnet attacks in connected vehicles. Transactions on Emerging Telecommunications Technologies 2022, 33, e4088. [Google Scholar] [CrossRef]
- Khan, F.; Ahamed, J.; Kadry, S.; Ramasamy, L.K. Detecting malicious URLs using binary classification through ada boost algorithm. International Journal of Electrical & Computer Engineering (2088-8708) 2020, 10. [Google Scholar] [CrossRef]
- Choubisa, M.; Doshi, R.; Khatri, N.; Hiran, K.K. A simple and robust approach of random forest for intrusion detection system in cyber security. In Proceedings of the 2022 International Conference on IoT and Blockchain Technology (ICIBT). IEEE; 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Liu, Z.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine learning and deep learning methods for cybersecurity. Ieee access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Danso, P.K.; Neto, E.C.P.; Dadkhah, S.; Zohourian, A.; Molyneaux, H.; Ghorbani, A.A. Ensemble-based Intrusion Detection for Internet of Things Devices. In Proceedings of the 2022 IEEE 19th International Conference on Smart Communities: Improving Quality of Life Using ICT, IoT and AI (HONET). IEEE; 2022; pp. 034–039. [Google Scholar] [CrossRef]


| Year | Devices | Attacks | Heathcare | IoT | Extensive Profiling | |
| WUSTL EHMS [87] | 2020 | Windows Laptop, Blood Oxygen Saturation (SpO2), PM4100 Six Pe Board, EKG or ECG |
Spoofing and Data alteration | ✓ | ✓ | X |
| ECU-IoHT [88] | 2021 | Bluetooth Adapter, wireless network adapter, Windows 10 laptop, Heart rate sensor, Blood pressure sensor, Temperature sensor, Kali laptop, Libelium MySignals |
Network scan, Script Injection, ARP spoofing Smurf,DoS, |
✓ | ✓ | X |
| BlueTack [89] | 2022 | SpO2, heart rate, and ECG | DDoS, Bluesmack, MITM, and DoS |
✓ | ✓ | X |
| ICU [90] | 2021 | response (GSR) Sensor, Galvanic skin, Nasal/Mouth, Barometer, Remote Electrocardiogram, Fire Sensor, (ECG) monitoring, Smoke Sensor Solar Radiation Sensor, Pulsoximeter (SPO2), CO Sensor, Infusion Pump Glucometer, monitor Sensor Blood pressure, AirFlow Sensor, Electromyography (EMG), Body Temperature Sensor Sensor, Air Temperature Sensor Air Humidity Sensor |
SlowITE, and brute force, DDoS MQTT, MQTT publish flood |
✓ | ✓ | X |
| IEC [91] | 2021 | Industrial Healthcare equipment, SDN Switch |
MITM, Traffic Sniffing, DoS, Unauthorized Access |
✓ | ✓ | X |
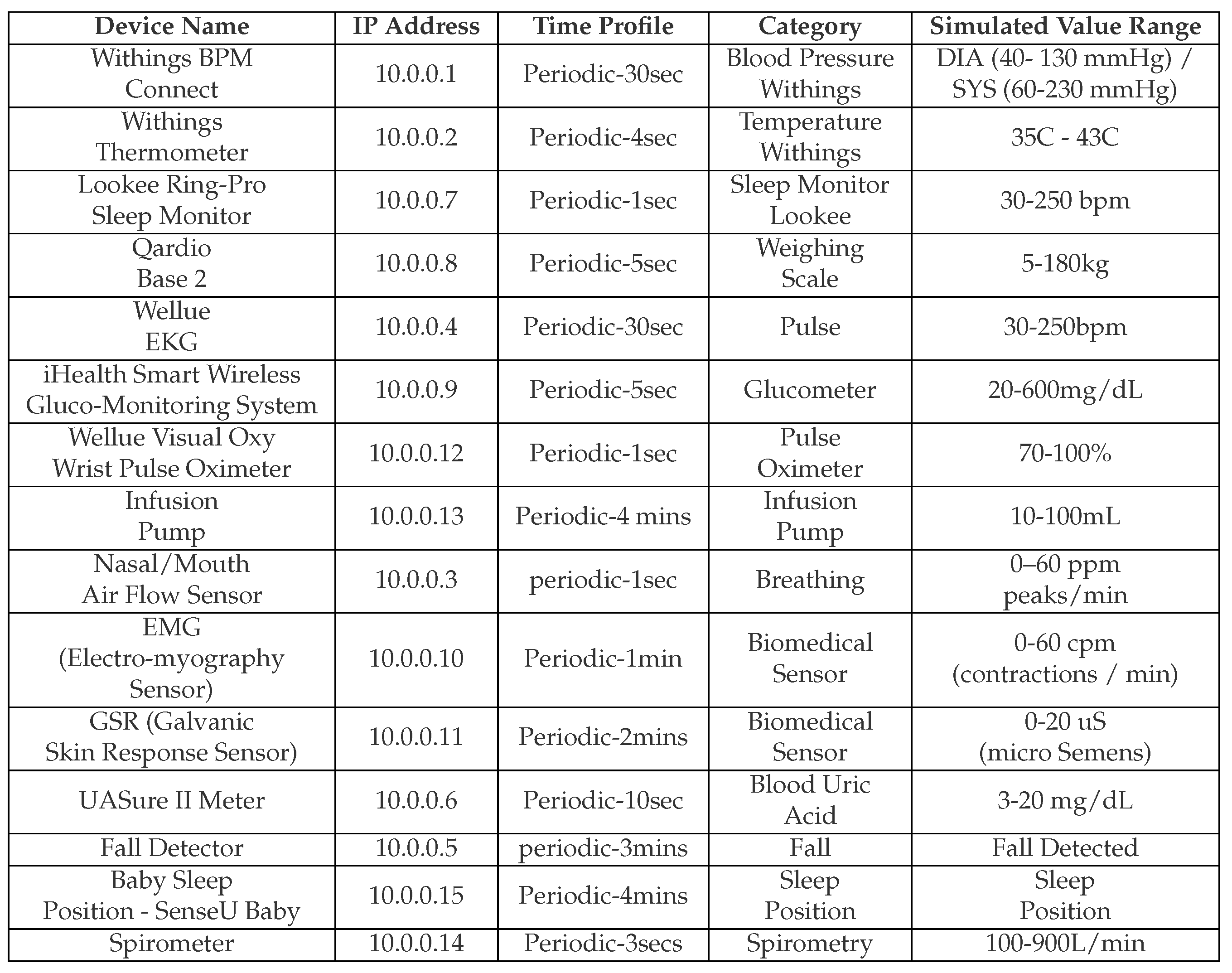
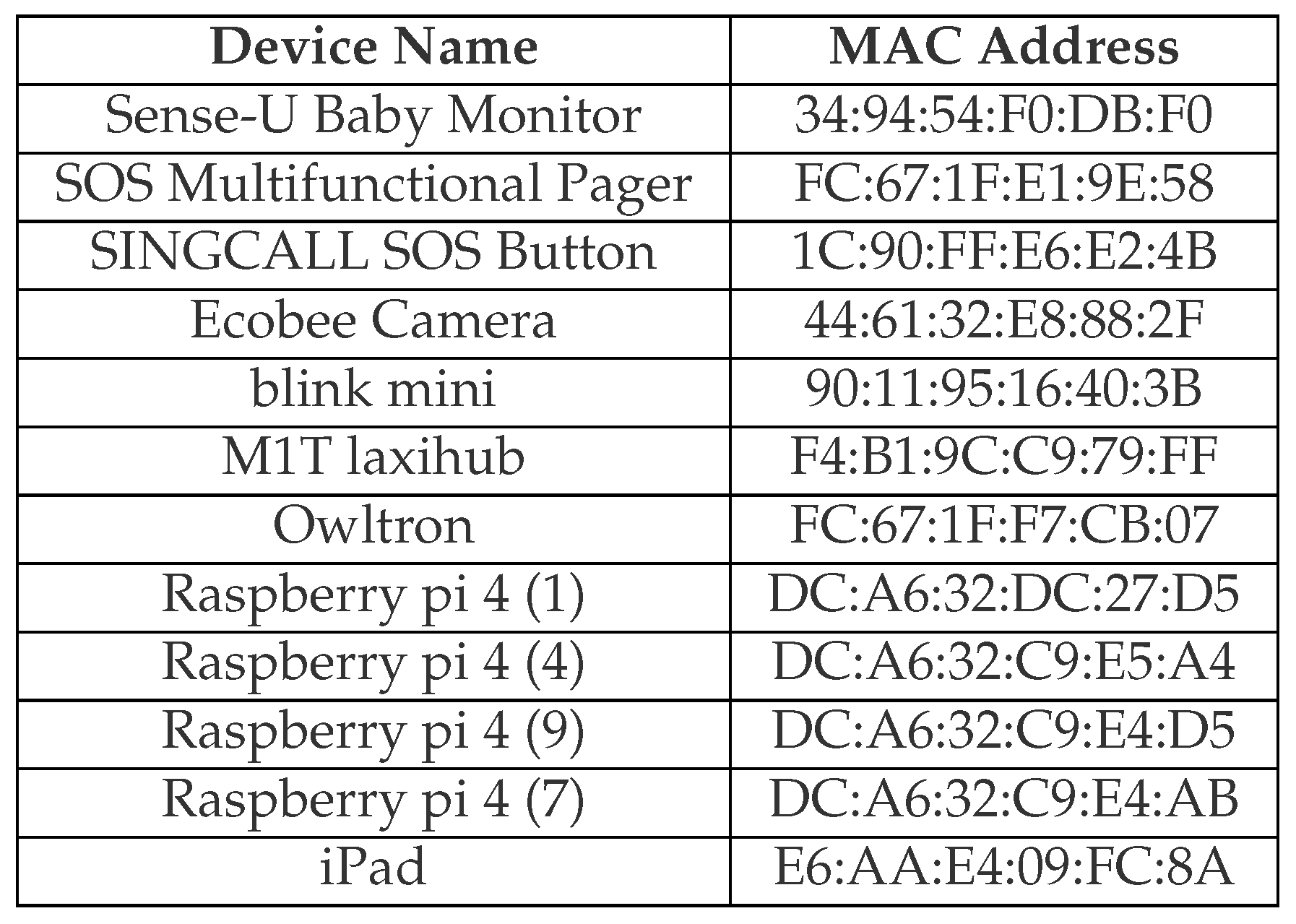
| CICIoMT2024 | 2024 | Sense-U Baby Monitor, SOS Multifunctional Pager, SINGCALL SOS Button, Ecobee Camera, blink mini, M1T laxihub, owltron, TP-Link_CIC (AP2), Raspberry pi 4 (4), iPad, TP-Link_CICIoT_Doctor (AP1), Lookee Sleep ring, Powerlabs HR Monitor Arm band, COOSPO 808s Chest HR Monitor, COOSPO HW807 Armband, Livlov Heart Rate Sensor, Wellue O2 Ring - 3438, Lookee O2 Ring, Checkme BP2A, SleepU Sleep Oxygen Monitor, Rhythm+ 2.0, Wellue Pulsebit EX, Kinsa Thermometer, Checkme O2 Wrist Pulse Oximeter (2), Dell CICM99, Samsung A11. Simulated devices: Withings BPM Connect, Withings Thermometer, Lookee Ring-Pro Sleep Monitor, Qardio Base 2, Wellue EKG, iHealth Smart Wireless Gluco-Monitoring System, Wellue Visual Oxy Wrist Pulse Oximeter, Nasal/Mouth Air Flow Sensor, EMG (Electro-myography Sensor), GSR (Galvanic Skin Response Sensor), Industrial devices, UASure II Meter, Fall Detector, Baby Sleep Position - SenseU Baby, Spirometer |
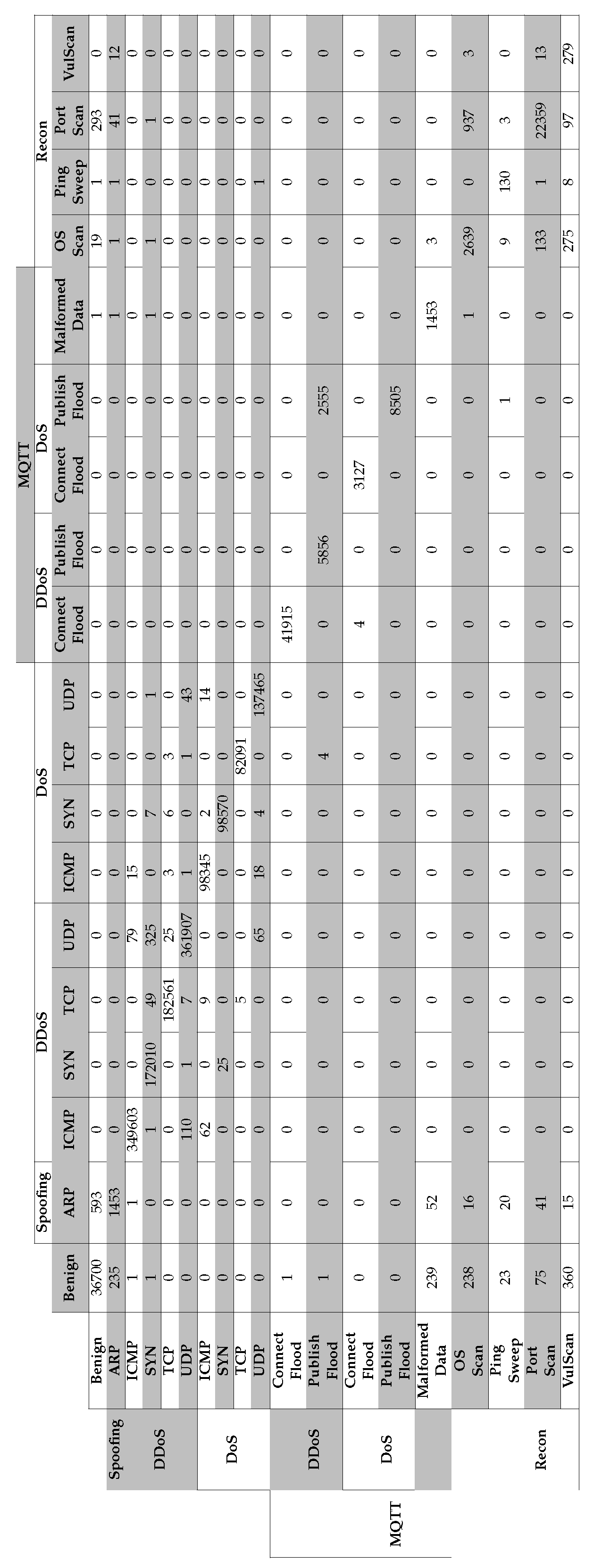
ARP spoofing, Ping Sweep, Recon VulScan, OS Scan, Port Scan, MQTT Malformed Data, MQTT DoS Connect flood, MQTT DoS Publish flood, MQTT DDoS Connect flood, MQTT DDoS Publish flood, DoS TCP, DoS ICMP, DoS SYN, DoS UDP, DDoS TC, DDoS ICMP, DDoS SYN, DDoS UDP |
✓ | ✓ | ✓ |
 |
 |
 |
| # | Feature | Description |
|---|---|---|
| 1 | Header Length | Length of the packet header |
| 2 | Duration | Lifetime of the packet in transit |
| 3 | Rate | Speed of packet transmission within a flow |
| 4 | Srate | Transmission speed of outgoing packets in a flow |
| 5 | fin flag number | Value of the Fin flag in TCP/IP |
| 6 | syn flag number | Value of the Syn flag in TCP/IP |
| 7 | rst flag number | Value of the Rst flag in TCP/IP |
| 8 | psh flag numbe | Value of the Psh flag in TCP/IP |
| 9 | ack flag number | Value of the Ack flag in TCP/IP |
| 10 | ece flag numbe | Value of the Ece flag in TCP/IP |
| 11 | cwr flag number | Value of the Cwr flag in TCP/IP |
| 12 | syn count | Tally of Syn flag occurrences in a flow |
| 13 | ack count | Tally of Ack flag occurrences in a flow |
| 14 | fin count | Tally of Fin flag occurrences in a flow |
| 15 | rst count | Tally of Rst flag occurrences in a flow |
| 16 | IGMP | Denotes the use of IGMP in application layer protocols |
| 17 | HTTPS | Denotes the use of HTTPS in application layer protocols |
| 18 | HTTP | Denotes the use of HTTP in application layer protocols |
| 19 | Telnet | Denotes the use of Telnet in application layer protocols |
| 20 | DNS | Denotes the use of DNS in application layer protocols |
| 21 | SMTP | Denotes the use of SMTP in application layer protocols |
| 22 | SSH | Denotes the use of SSH in application layer protocols |
| 23 | IRC | Denotes the use of IRC in application layer protocols |
| 24 | TCP | Usage of TCP in the transport layer protocol |
| 25 | UDP | Usage of UDP in the transport layer protocol |
| 26 | DHCP | Presence of DHCP in the application layer protocol |
| 27 | ARP | Usage of ARP in the link layer protocol |
| 28 | ICMP | Usage of ICMP in the network layer protocol |
| 29 | IPv | Usage of IP in the network layer protocol |
| 30 | LLC | Usage of LLC in the link layer protocol |
| 31 | Tot sum | Total packet length within a flow |
| 32 | Min | Shortest packet length in a flow |
| 33 | Max | Longest packet length in a flow |
| 34 | AVG | Mean packet length in a flow |
| 35 | Std | Variability in packet length within a flow |
| 36 | Tot size | Length of the packet |
| 37 | IAT | Interval between the current and previous packet |
| 38 | Number | Total number of packets in the flow |
| 39 | Radius | Root mean square of the variances of incoming and outgoing packet lengths in the flow |
| 40 | Magnitude | Root mean square of the averages of incoming and outgoing packet lengths in the flow |
| 41 | Variance | Ratio of the variances of incoming to outgoing packet lengths in the flow |
| 42 | Covariance | Covariance between the lengths of incoming and outgoing packets |
| 43 | Weight | Product of the number of incoming and outgoing packets |
| 44 | Protocol Type | Type of protocol used (IP, UDP, TCP, etc.) expressed in integer values |
| mean | std | min | 25% | 50% | 75% | max | |
|---|---|---|---|---|---|---|---|
| Header_Length | 29962.4717 | 282363.394 | 0 | 2.17 | 108 | 19421 | 9896704 |
| Protocol Type | 8.04720327 | 6.30483218 | 0 | 1.05 | 6 | 17 | 17 |
| Duration | 64.6369088 | 7.85306556 | 0 | 64 | 64 | 64 | 255 |
| Rate | 15744.4895 | 40008.5463 | 0 | 6.42273084 | 133.141869 | 19759.2022 | 2097152 |
| Srate | 15744.4895 | 40008.5463 | 0 | 6.42273084 | 133.141869 | 19759.2022 | 2097152 |
| fin_flag_number | 0.0051233 | 0.03415862 | 0 | 0 | 0 | 0 | 1 |
| syn_flag_number | 0.15721153 | 0.33687886 | 0 | 0 | 0 | 0 | 1 |
| rst_flag_number | 0.03951838 | 0.13929947 | 0 | 0 | 0 | 0 | 1 |
| psh_flag_number | 0.02217887 | 0.0965354 | 0 | 0 | 0 | 0 | 1 |
| ack_flag_number | 0.09566387 | 0.25214153 | 0 | 0 | 0 | 0 | 1 |
| ece_flag_number | 2.91E-06 | 0.0005036 | 0 | 0 | 0 | 0 | 0.2 |
| cwr_flag_number | 1.92E-06 | 0.00037966 | 0 | 0 | 0 | 0 | 0.2 |
| ack_count | 0.02797713 | 0.17825565 | 0 | 0 | 0 | 0 | 11.2 |
| syn_count | 0.2938792 | 0.60364144 | 0 | 0 | 0 | 0 | 10.7 |
| fin_count | 0.08557531 | 0.56123908 | 0 | 0 | 0 | 0 | 151.74 |
| rst_count | 65.8712672 | 498.281211 | 0 | 0 | 0 | 0 | 9576.5 |
| HTTP | 0.00086767 | 0.0284215 | 0 | 0 | 0 | 0 | 1 |
| HTTPS | 0.00559028 | 0.06034021 | 0 | 0 | 0 | 0 | 1 |
| DNS | 0.00015156 | 0.0052478 | 0 | 0 | 0 | 0 | 1 |
| Telnet | 1.25E-05 | 0.00089169 | 0 | 0 | 0 | 0 | 0.1 |
| SMTP | 1.25E-05 | 0.00089171 | 0 | 0 | 0 | 0 | 0.1 |
| SSH | 2.61E-05 | 0.00271903 | 0 | 0 | 0 | 0 | 1 |
| IRC | 1.25E-05 | 0.00089234 | 0 | 0 | 0 | 0 | 0.11111111 |
| TCP | 0.41487102 | 0.48990278 | 0 | 0 | 0 | 1 | 1 |
| UDP | 0.31084898 | 0.45956644 | 0 | 0 | 0 | 1 | 1 |
| DHCP | 3.26E-06 | 0.00098659 | 0 | 0 | 0 | 0 | 0.6 |
| ARP | 0.00076075 | 0.01928389 | 0 | 0 | 0 | 0 | 1 |
| ICMP | 0.27351348 | 0.44404871 | 0 | 0 | 0 | 0.99 | 1 |
| IGMP | 4.47E-06 | 0.0012065 | 0 | 0 | 0 | 0 | 0.7 |
| IPv | 0.99923925 | 0.01928389 | 0 | 1 | 1 | 1 | 1 |
| LLC | 0.99923925 | 0.01928389 | 0 | 1 | 1 | 1 | 1 |
| Tot sum | 636.01138 | 991.6091 | 42 | 441 | 525 | 567 | 23467 |
| Min | 55.1201614 | 69.0993765 | 42 | 42 | 50 | 54 | 1514 |
| Max | 72.3325073 | 133.609047 | 42 | 43.77 | 50 | 54 | 1514 |
| AVG | 60.5865132 | 88.0720219 | 42 | 42.0933304 | 50 | 54 | 1514 |
| Std | 6.06053694 | 38.0578569 | 0 | 0 | 0 | 0 | 721.15087 |
| Tot size | 60.5890934 | 87.8768798 | 42 | 42.24 | 50 | 54 | 1514 |
| IAT | 84683677.9 | 17819169.6 | -1.2820613 | 84679174 | 84696417 | 84696902.6 | 169470846 |
| Number | 9.49908609 | 0.84157738 | 1 | 9.5 | 9.5 | 9.5 | 15 |
| Magnitue | 10.4382451 | 3.15807323 | 9.16515139 | 9.17497736 | 10 | 10.3923048 | 55.027266 |
| Radius | 8.56000977 | 53.8045034 | 0 | 0 | 0 | 0 | 1020.23203 |
| Covariance | 2370.54475 | 19758.8155 | 0 | 0 | 0 | 0 | 520437.887 |
| Variance | 0.09074362 | 0.2329791 | 0 | 0 | 0 | 0 | 1 |
| Weight | 141.527342 | 21.6618865 | 1 | 141.55 | 141.55 | 141.55 | 244.6 |
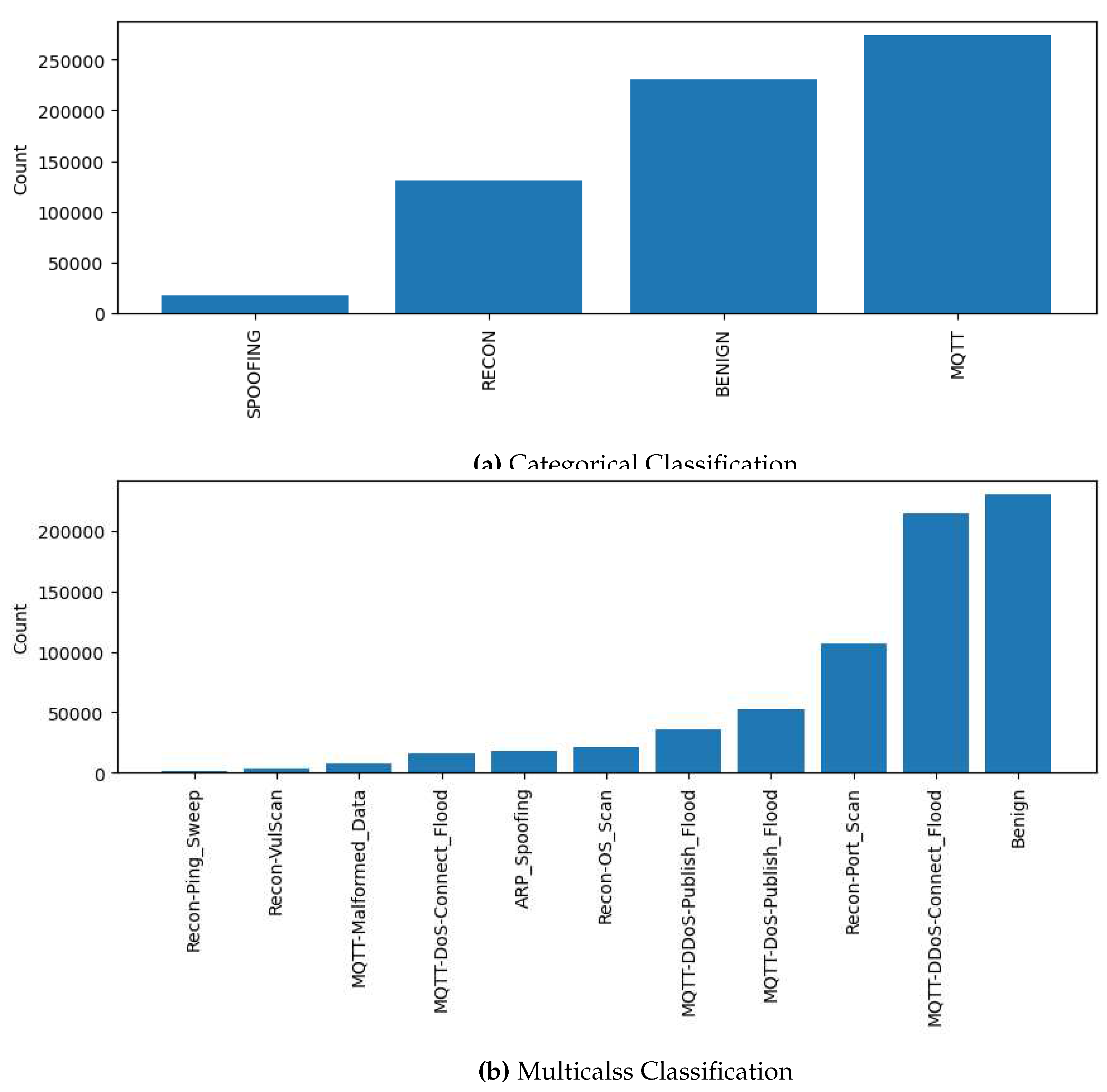
| Class | Category | Attack | Count |
|---|---|---|---|
| BENIGN | - | - | 230339 |
| ATTACK | SPOOFING | ARP Spoofing | 17791 |
| RECON | Ping Sweep | 926 | |
| Recon VulScan | 3207 | ||
| OS Scan | 20666 | ||
| Port Scan | 106603 | ||
| MQTT | Malformed Data | 6877 | |
| DoS Connect Flood | 15904 | ||
| DDoS Publish Flood | 36039 | ||
| DoS Publish Flood | 52881 | ||
| DDoS Connect Flood | 214952 | ||
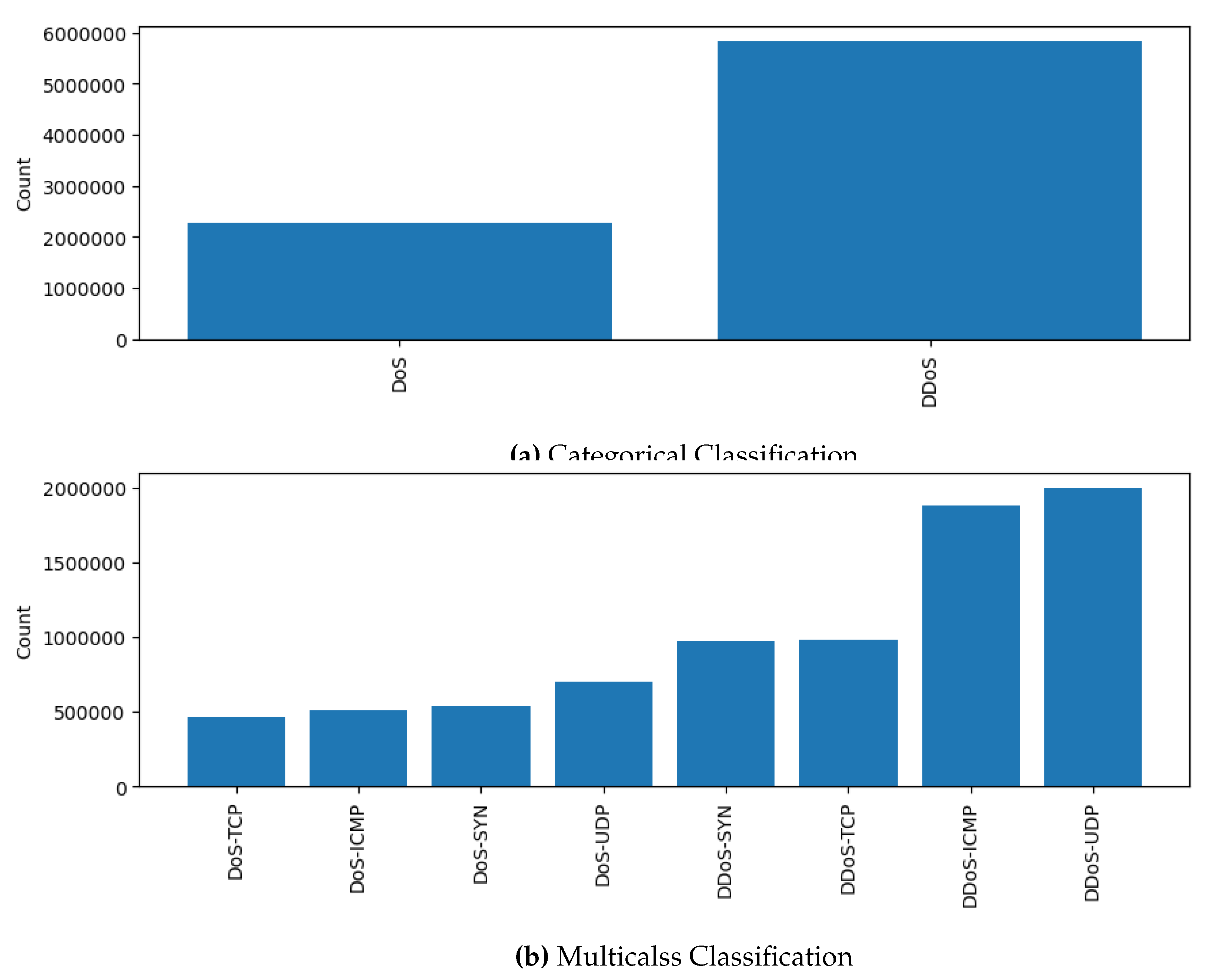
| DoS | DoS TCP | 462480 | |
| DoS ICMP | 514724 | ||
| DoS SYN | 540498 | ||
| DoS UDP | 704503 | ||
| DDoS | DDoS SYN | 974359 | |
| DDoS TCP | 987063 | ||
| DDoS ICMP | 1887175 | ||
| DDoS UDP | 1998026 |
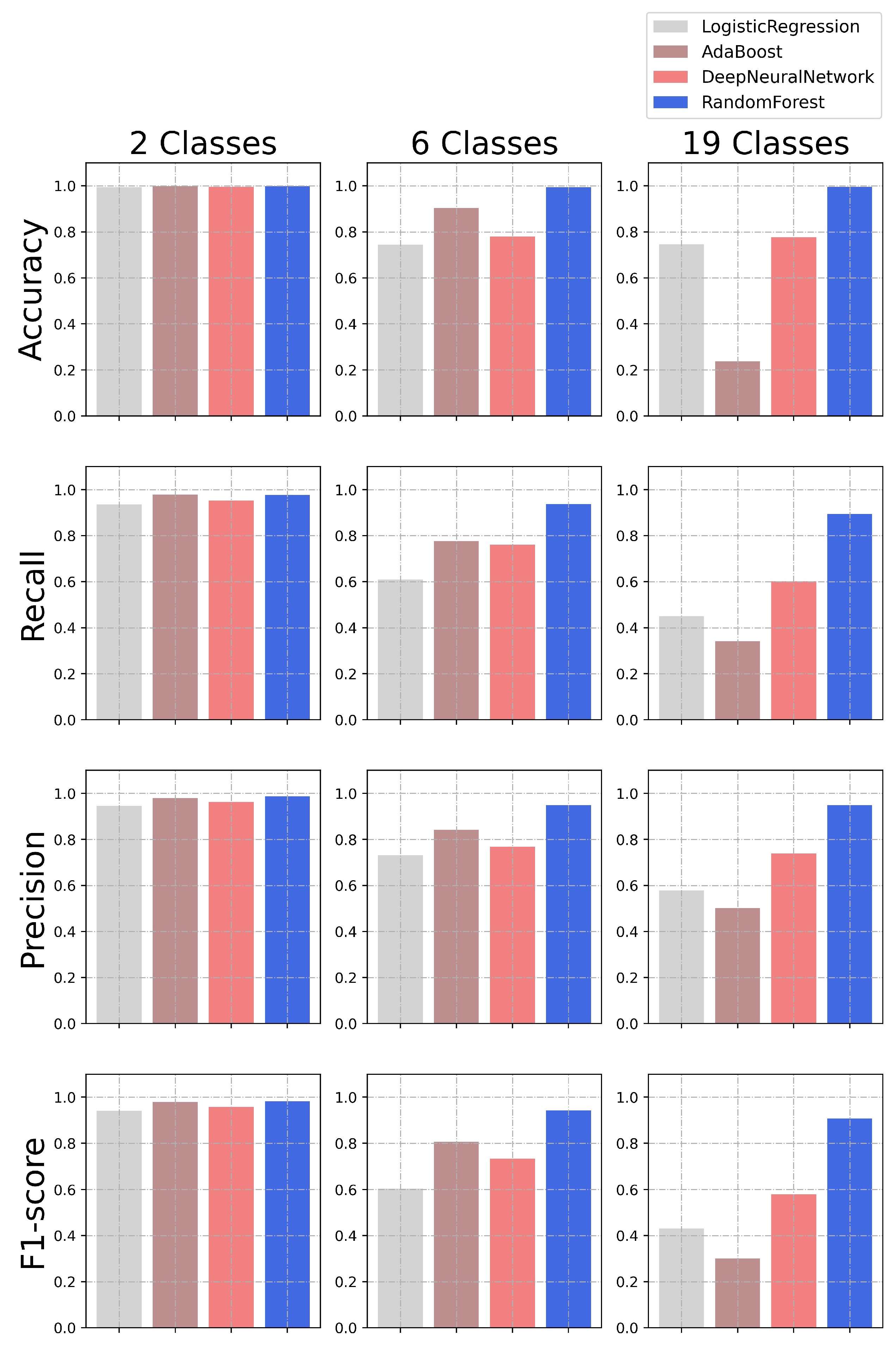
| LR | AB | DNN | RF | ||
| Binary (2 classes) |
Accuracy | 0.99464682 | 0.99807704 | 0.99617391 | 0.99837193 |
| Recall | 0.93505479 | 0.97788699 | 0.95233191 | 0.97640269 | |
| Precision | 0.94600144 | 0.9797801 | 0.96276398 | 0.98754544 | |
| F1-Score | 0.94045653 | 0.97883158 | 0.95748541 | 0.98190642 | |
| Categorical (6 classes) |
Accuracy | 0.74399479 | 0.90303572 | 0.78052413 | 0.99388111 |
| Recall | 0.60901055 | 0.77537141 | 0.76020495 | 0.9379039 | |
| Precision | 0.73229673 | 0.8417807 | 0.76809269 | 0.94855819 | |
| F1-Score | 0.60443814 | 0.80562143 | 0.73354862 | 0.94221191 | |
| Multiclass (19 classes) |
Accuracy | 0.74562534 | 0.23653652 | 0.77656609 | 0.99553086 |
| Recall | 0.4495978 | 0.34171028 | 0.60194873 | 0.89345693 | |
| Precision | 0.57814073 | 0.50168939 | 0.73835033 | 0.94831885 | |
| F1-Score | 0.43098172 | 0.30109723 | 0.57906237 | 0.90736136 |
| BENIGN | ATTACK | |
| BENIGN | 35853 | 1754 |
| ATTACK | 874 | 1575701 |
| BENIGN | DDoS | DoS | MQTT | RECON | SPOOFING | |
| BENIGN | 36620 | 0 | 1 | 0 | 666 | 320 |
| DDoS | 2 | 1066695 | 67 | 0 | 0 | 0 |
| DoS | 0 | 170 | 425010 | 0 | 1 | 0 |
| MQTT | 234 | 0 | 7372 | 47548 | 4 | 52 |
| RECON | 597 | 0 | 0 | 5 | 27007 | 67 |
| SPOOFING | 219 | 0 | 0 | 1 | 99 | 1425 |
 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





