Introduction:
Information and communication technologies, Communication, and networking
Knowledge exchange, social interaction, Digital landscape, Information security, Cybercrime, Cybersecurity strategies, Artificial Intelligence (AI), Machine Learning (ML)
Anomaly detection, Threat prediction, Automated response, Cybersecurity tactics
AI applications in cybersecurity, Cybersecurity education, Massive Open Online Courses (MOOCs), Global cost of data breach, AI-driven threat intelligence, Machine learning in cybersecurity, Cybersecurity data analysis, Tool development, Security incidents, Cybersecurity models, Data analytic models, Threat identification, Risk assessment, Intruder detection, Network forensics, Industry 4.0, Internet of Things (IoT)
Cyber Physical Systems (CPS), Cyber threat detection, SoftGrid, Cyber deception strategies, User and entity behavior analytics (UEBA), Anomaly reporting, Brute-force attacks, Data access, Data loss
1.0. Introduction
The swift advancement of information and communication technologies, notably the Internet, has ushered in favorable outcomes for both organizations and individuals. The Internet serves as a vital platform for fostering communication and networking, facilitating knowledge exchange [
1], and enabling social interaction [
2], all of which play crucial roles in human progress. However, alongside these advantages, there exists a shadowy facet. The growing dependence on third-party, backend users and cloud-based data storage and applications within the digital landscape has rendered it exceedingly challenging and vulnerable for organizations to ensure comprehensive security for their information systems.
In recent years, there has been a dramatic surge in information security incidents, encompassing unauthorized access [
3], denial of service (DoS) attacks [
4], malware intrusions [
5], zero-day exploits [
6] , data breaches [
7], and social engineering tactics like phishing [
8]. This surge can be attributed to the ever-increasing significance of information technology in our lives. To illustrate, consider that in 2010, the security industry was aware of fewer than 50 million unique malware executables. By 2012, this number had doubled to surpass 100 million. More recently, in 2019, the security sector identified a staggering 900 million malicious executables, and this figure continues to grow, as indicated by AV-TEST statistics [
9].
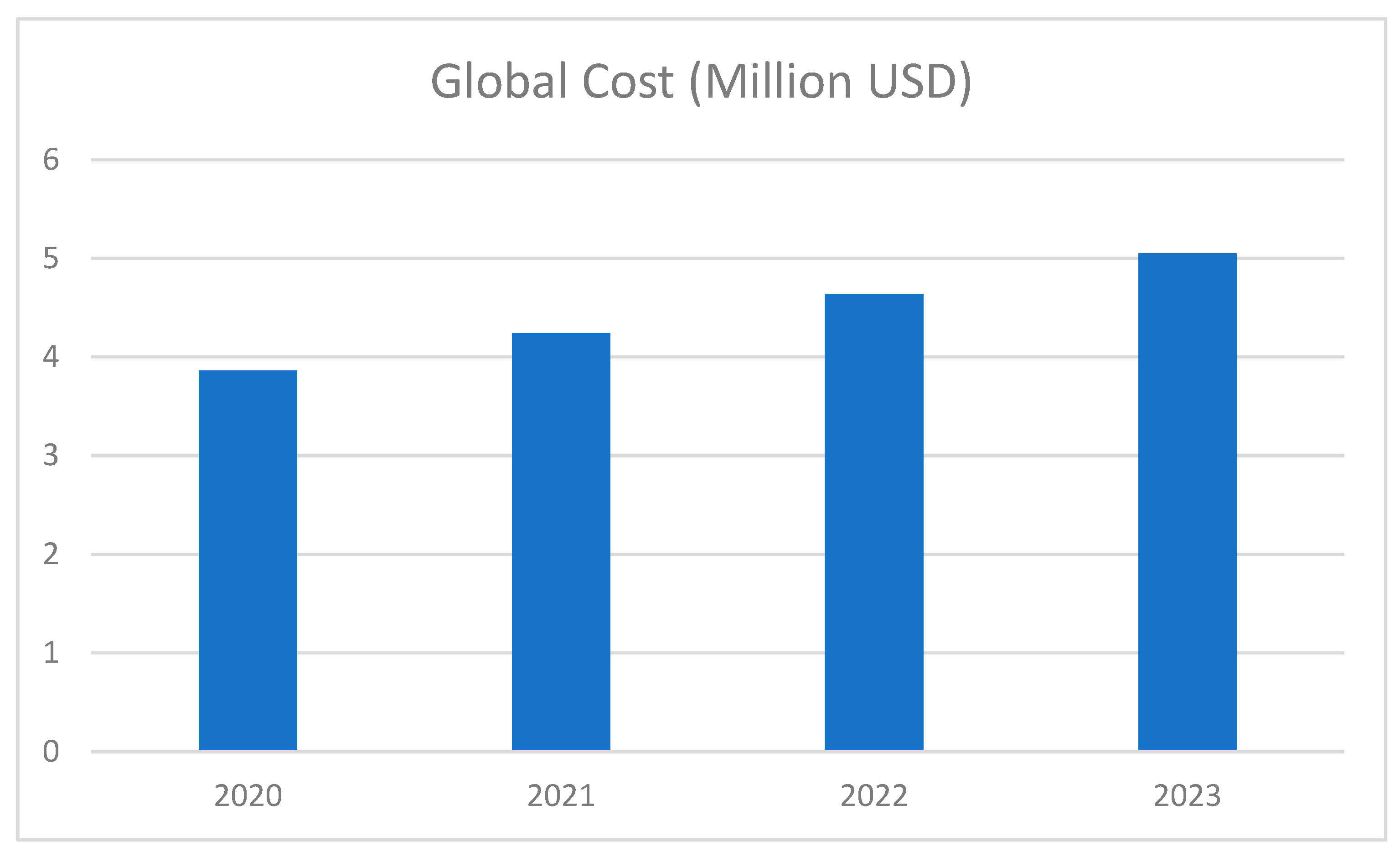
The repercussions of cybercrime and network attacks can be financially devastating for both businesses and individuals. For instance, research reveals that the average global cost of a data breach is USD 8.19 million, with a cost of USD 3.9 million in the United States [
10]. Moreover, cybercrime exacts a hefty toll on the global economy, amounting to USD 400 billion annually [
11]. Security experts project that the number of breached records is poised to triple in the next five years [
12]. Consequently, organizations must develop and implement comprehensive cybersecurity strategies to mitigate potential future losses.
It is quite important that the security of countries, nations, depends vigorously on people, government substances, and those with admittance to information, applications, and high-exceptional status apparatuses, as demonstrated by late financial exploration discoveries [
13].
Besides, endeavors are being constrained to look for creative arrangements that go past customary safety efforts because of the sharp expansion in computerized dangers and weaknesses in the always changing online protection scene. Irregularity identification, danger expectation, and robotized response have become fundamental components in the fight against digital assailants. In this unique situation, there has been a great deal of interest in the capability of artificial intelligence and ML innovations to reinforce the security stance of associations and organizations. [
14].
ML offers a pragmatic method for propelling online protection endeavors in view of their expedient examination of huge datasets and capacity to recognize patterns. This study examines the viability of network protection by consolidating artificial intelligence/ML into the spaces of mechanized reaction, danger forecast, and peculiarity discovery. Utilizing computer-based intelligence/ML calculations' capacities, associations might have the option to expect and defeat hurtful action, answer immediately to arising dangers, and invigorate their protections [
15].
This article investigates the province of simulated intelligence/ML applications in online protection, displaying striking turns of events and their results. It likewise analyzes the strategies, calculations, and models that have been effective in distinguishing irregularities and anticipating risks, illustrating both their benefits and burdens.
This examination intently looks at robotized reaction frameworks and the Normal Shortcoming Specification (CWE) Classification of Weaknesses, with an emphasis on how computer-based intelligence/ML can be utilized to rapidly and precisely foster countermeasures against cyberthreats. through an exhaustive investigation of the corpus of past examination, contextual investigations, and genuine executions. The motivation behind this study is to introduce astute perspectives on the changing field of network safety empowered by man-made intelligence and ML. Eventually, it adds to a superior comprehension of how simulated intelligence/ML can be utilized in contemporary online protection methodologies for danger expectation, automated reaction, and irregularity recognition.
3.0. AI-Driven Data Collection and Analysis
Threat intelligence is the process of gathering and analyzing information about actual or possible attacks that might jeopardize an organization. Threat intelligence is centered on the analysis and interpretation of data to detect threats, pinpoint early warning signs, and put defensive measures in place. Artificial intelligence (AI) is a major factor in threat intelligence since it helps to automate data storage, analysis, and collection. Handling the enormous volumes of data produced in today's digital environment is made possible by this.
Machine learning (ML) and other AI techniques are used in AI-powered threat intelligence to find patterns and anomalies that may be signs of approaching danger. It excels at spotting patterns and trends in sizable datasets, foreseeing impending attacks, and offering practical suggestions for lowering risk. AI-driven threat intelligence has several advantages, such as enhanced predictive power, speedier threat identification, and effective handling of massive data volumes.
comprehensive case study on cybersecurity risks that centers on vulnerabilities found in 2022 after a sizable dataset from the Cybersecurity and Infrastructure Security Agency (CISA) was analyzed.
Comprehending the current weaknesses is essential for formulating efficient defensive tactics and eliminating possible hazards. The Common Vulnerabilities and Exposures (CVE), vendor and product details, vulnerability names, dates of discovery, severity ratings, and suggested actions are just a few of the many details about multiple vulnerabilities that can be found in the dataset that was retrieved from
www.kaggle.com. examining this data to look for important trends, patterns, and insights. Throughout this study, a variety of methods and approaches was employed to capitalize on the potent data analysis and visualization features of the R programming language, including clustering, network analysis, and Bayesian analysis.
3.1. AL Libraries
The R programming language loads a set of R packages that are a part of the Tidyverse database using the library(tidyverse) statement. Popular tools for data analysis, visualization, and manipulation like ggplot2, tidyr, and dplyr are included in these packages.
3.2. Dataset Preparation and Correlation
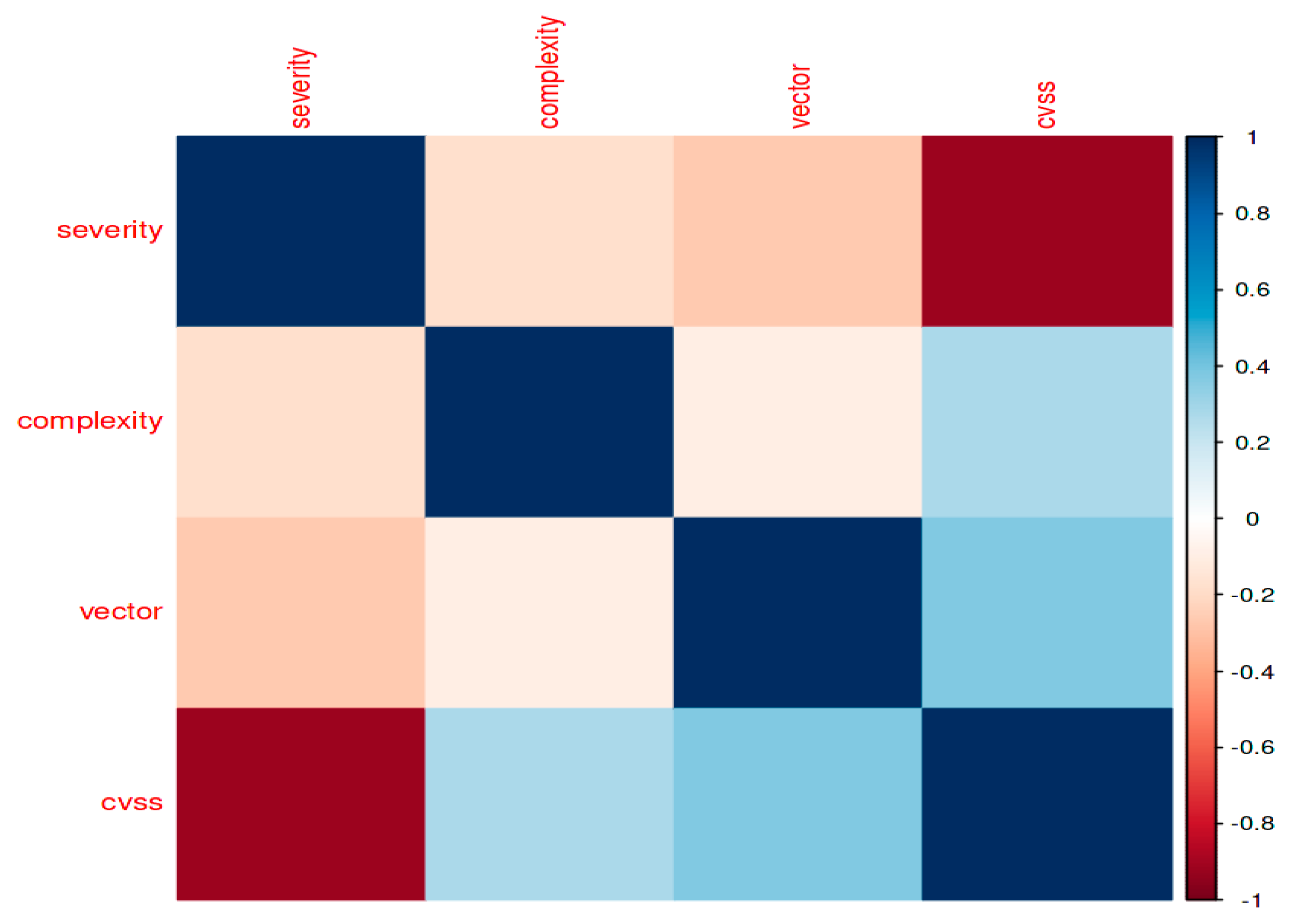
A correlation plot is a graphical representation in R that shows the connections or relationships between multiple variables. It is commonly employed in exploratory data analysis to determine the relationships between various variables within a dataset. When dealing with numerical data, correlation graphs are especially helpful for spotting patterns, connections, and interdependencies between variables. In R-Programming, correlation plots are useful tools that help with feature selection, data analysis, and model building decisions. They can be used to comprehend correlations within a dataset. As seen in figure 3, they support modeling and data exploration activities and offer a succinct synopsis of the relationships between the variables. The correlation coefficients between two variables, like severity, can be seen visually with correlation plots. The strength and direction of the linear relationship between the variables are thus shown by the correlation coefficients. A high positive correlation (near 1) means that the variables represented by the combination of severity and sevrity move in the same direction, whereas a high negative correlation (near -1) means that the variables move in opposite directions, as can be seen in the legend in figure 3 below. A helpful tool for identifying which variables have a strong association and which do not is a correlation plot. For instance, there is a clear correlation between the severity and the variables. This is important when selecting features for machine learning, as you may want to choose the variables that are most relevant to a prediction model. Correlation charts are often represented by heatmaps, where the intensity of each color represents the strength of the correlation; dark blue, for example, is typically associated with high positive correlations; dark red, for example, is associated with large negative correlations; and neutral colors, like white or light gray, are associated with weak correlations. The distribution of vulnerability severity levels is shown in
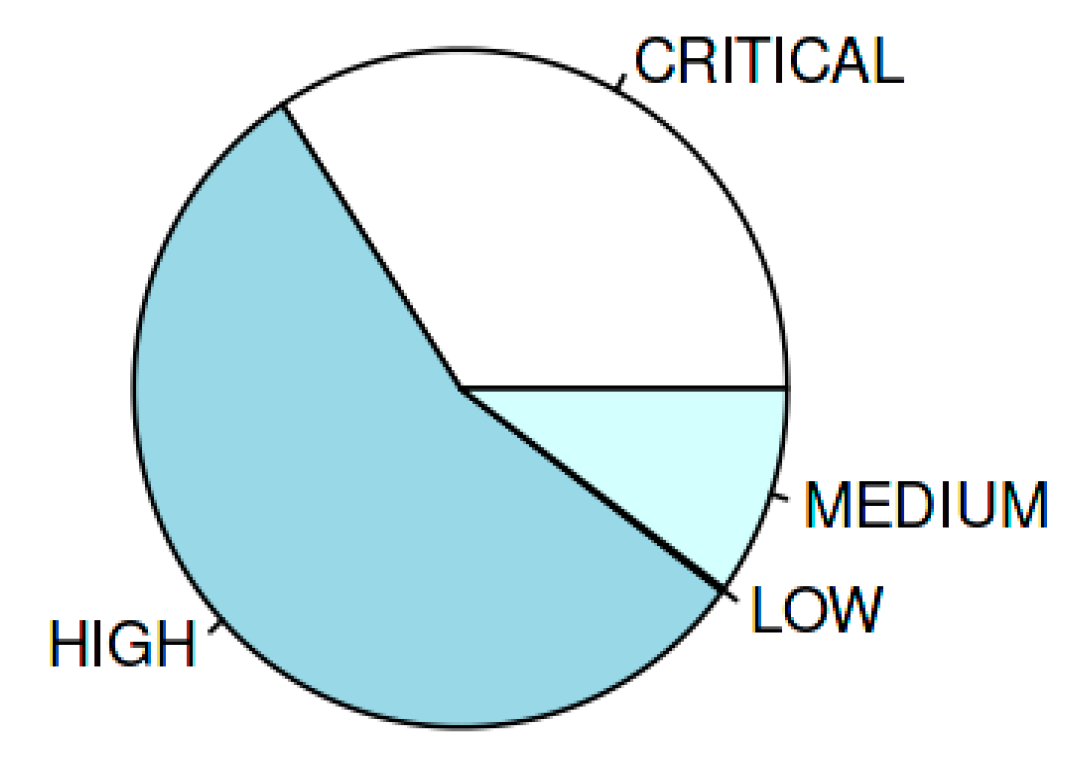
Figure 4, which can help reduce dimensionality and facilitate the interpretation of complex datasets.
Figure 3.
Convolution Matrix.
Figure 3.
Convolution Matrix.
Figure 4.
Distribution of Vulnerability Severity Levels.
Figure 4.
Distribution of Vulnerability Severity Levels.
3.3. Examination of Image Trend and Number of Vulnerabilities
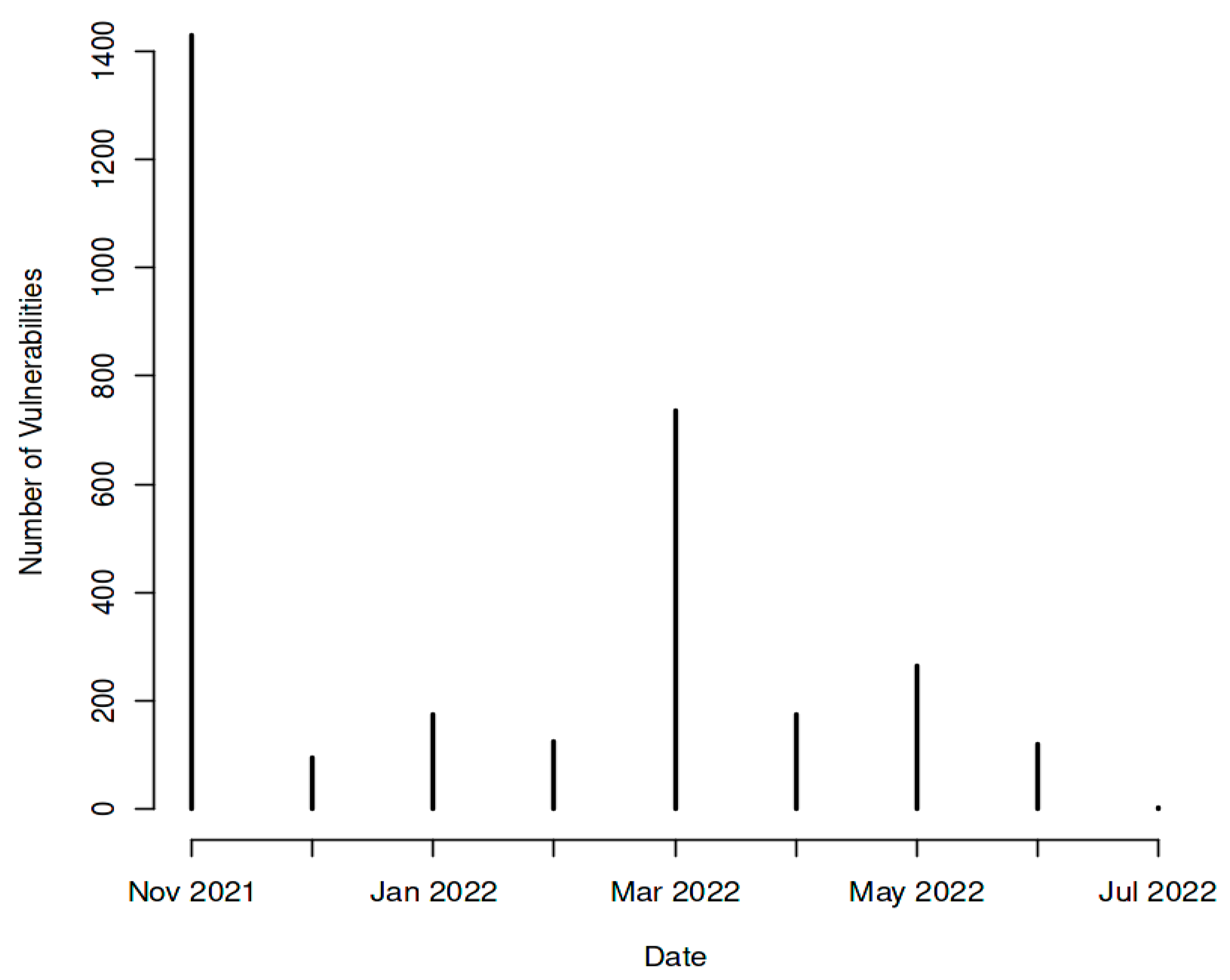
Figure 5 illustrates the vulnerability risk over time, offering a concise summary of the escalating number of disclosed vulnerabilities in the past two years. This upward trend is likely influenced by the growing usage of technology, the intricate nature of software and systems, and the increasing sophistication of attackers. Such a pattern holds significant implications for organizations, as attackers can leverage vulnerabilities for launching attacks, accessing systems and data, or pilfering information. As a result, businesses may experience a range of issues, such as monetary losses, harm to their brand, and operational pauses.
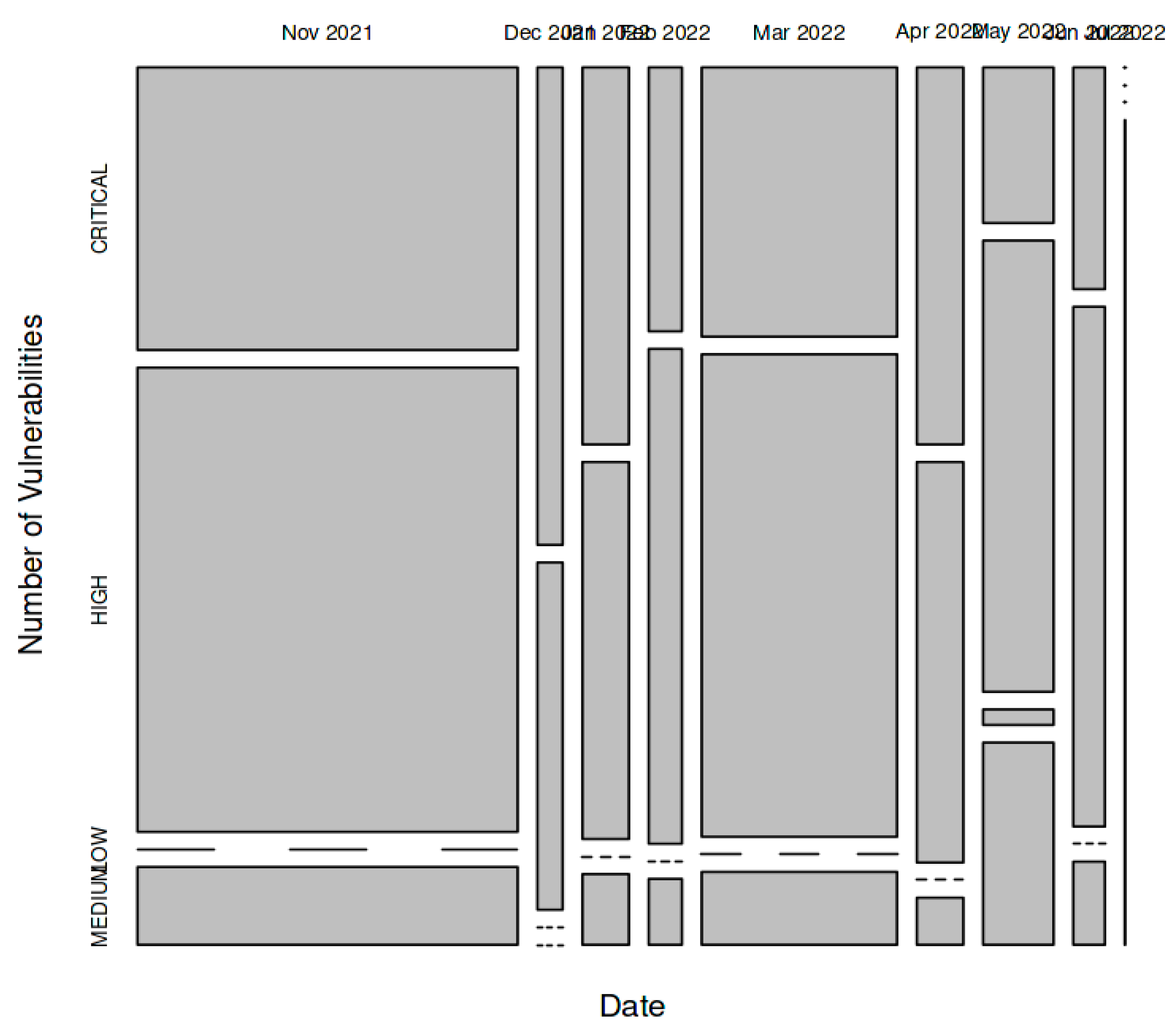
Figure 6 below, which displays the Trend Vulnerability Counts by Severity, illustrates that over the past year, there have been more vulnerabilities across all severity categories. The greatest increase in vulnerabilities has been seen in those with high and critical severity, with medium and low severity coming in close second.
The growing complexity of software and systems, the rise in the number of people utilizing technology, and the growing expertise of attackers are all likely contributing factors to this trend. Organizations are significantly impacted by this trend. Attackers can launch attacks, obtain access to systems and data, or steal information by using vulnerabilities of any severity. As a result, businesses may experience a range of issues, such as monetary losses, harm to their brand, and operational pauses. Companies need to be proactive in protecting themselves from vulnerabilities that range in severity. This entails spotting vulnerabilities and fixing them as soon as it's practical, putting security measures in place to lessen the chance that vulnerabilities will be exploited, and training staff members on security best practices.
3.4. Effect on organizations
For companies of all kinds, the growing number of vulnerabilities is a serious concern. In order to safeguard themselves against vulnerabilities, companies must implement these measures:
• Identifying weaknesses and fixing them: As soon as system and software vulnerabilities are discovered, businesses must find them and fix them. Numerous tools and methods, including vulnerability scanning, penetration testing, and code review, can be used to achieve this.
• Putting security controls in place: In order to lessen the chance that vulnerabilities will be exploited, organizations must put security controls in place. Firewalls, access control systems, and intrusion detection systems are a few of these controls.
• Employee education: Organizations must provide training to staff members on security best practices and how to fend off attacks that take advantage of weaknesses.
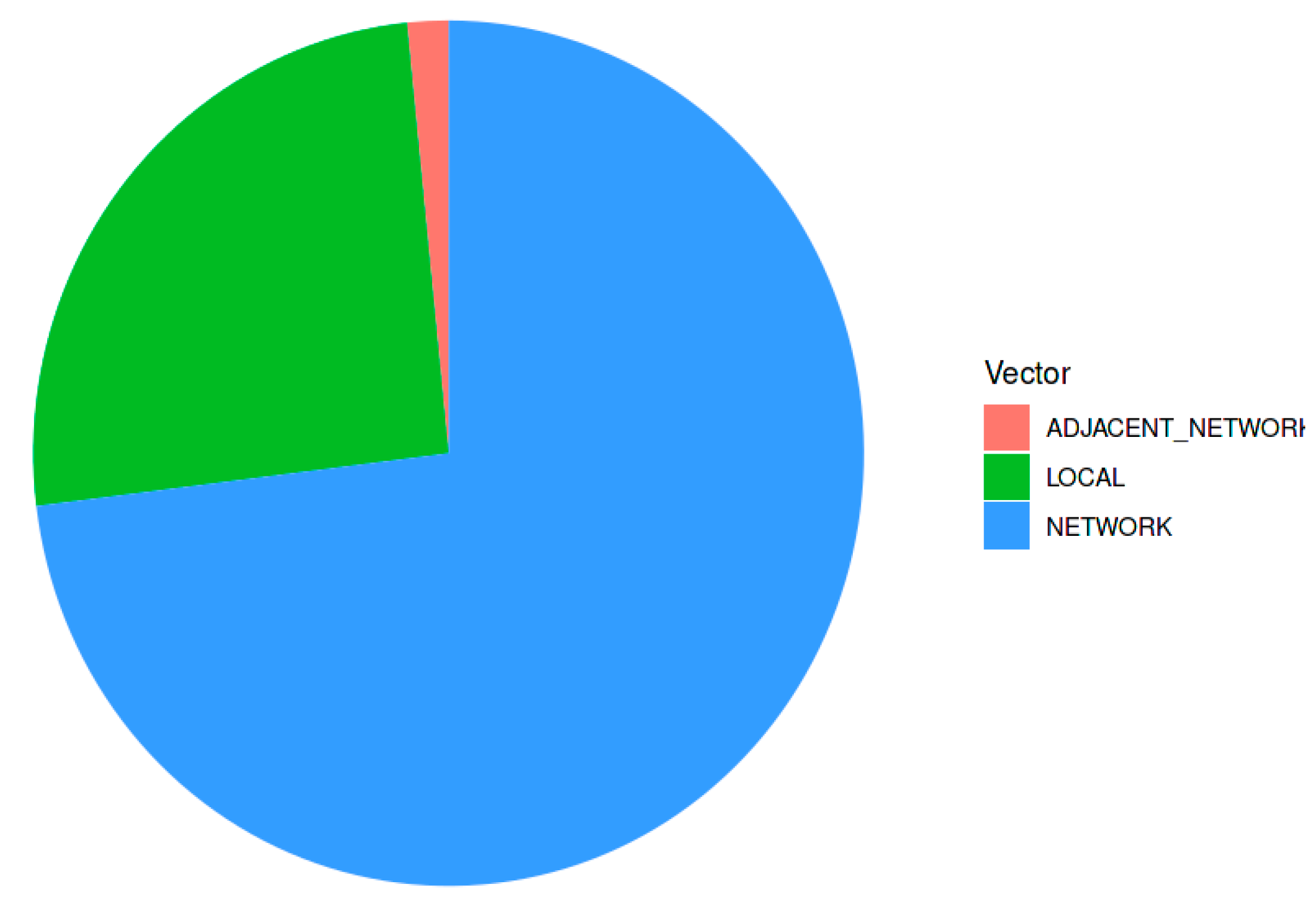
Figure 7 below displays a pie chart that illustrates the distribution of vulnerabilities by vector. The pie chart indicates that remote attack vectors account for 65 percent of vulnerabilities. This implies that physical access to the target computer is not necessary for an attacker to take advantage of these vulnerabilities.
Adjacent network attack vectors rank second in terms of vulnerability severity, accounting for 20% of all vulnerabilities. This implies that attackers with access to the same network as the target system may be able to take advantage of these vulnerabilities. 15% of vulnerabilities are caused by local attack vectors. This implies that attackers with physical access to the target computer are the only ones who can take advantage of these vulnerabilities. It is important to keep in mind that the majority of vulnerabilities originate from remote attack vectors. As a result, companies should concentrate their security efforts on eliminating distant threats. Security measures like firewalls, intrusion detection systems, and access control systems can be put into place to achieve this. Companies also need to be mindful of the weaknesses that hackers, gaining entry to the same network as the target computer, may exploit against them. Businesses that operate in high-risk sectors like finance and healthcare should pay particular attention to this.
Lastly, businesses must take precautions against deliberate assaults. This entails setting up both technological and physical security measures, such as entry control and CCTV cameras.
Based on information from the National Institute of Standards and Technology (NIST),
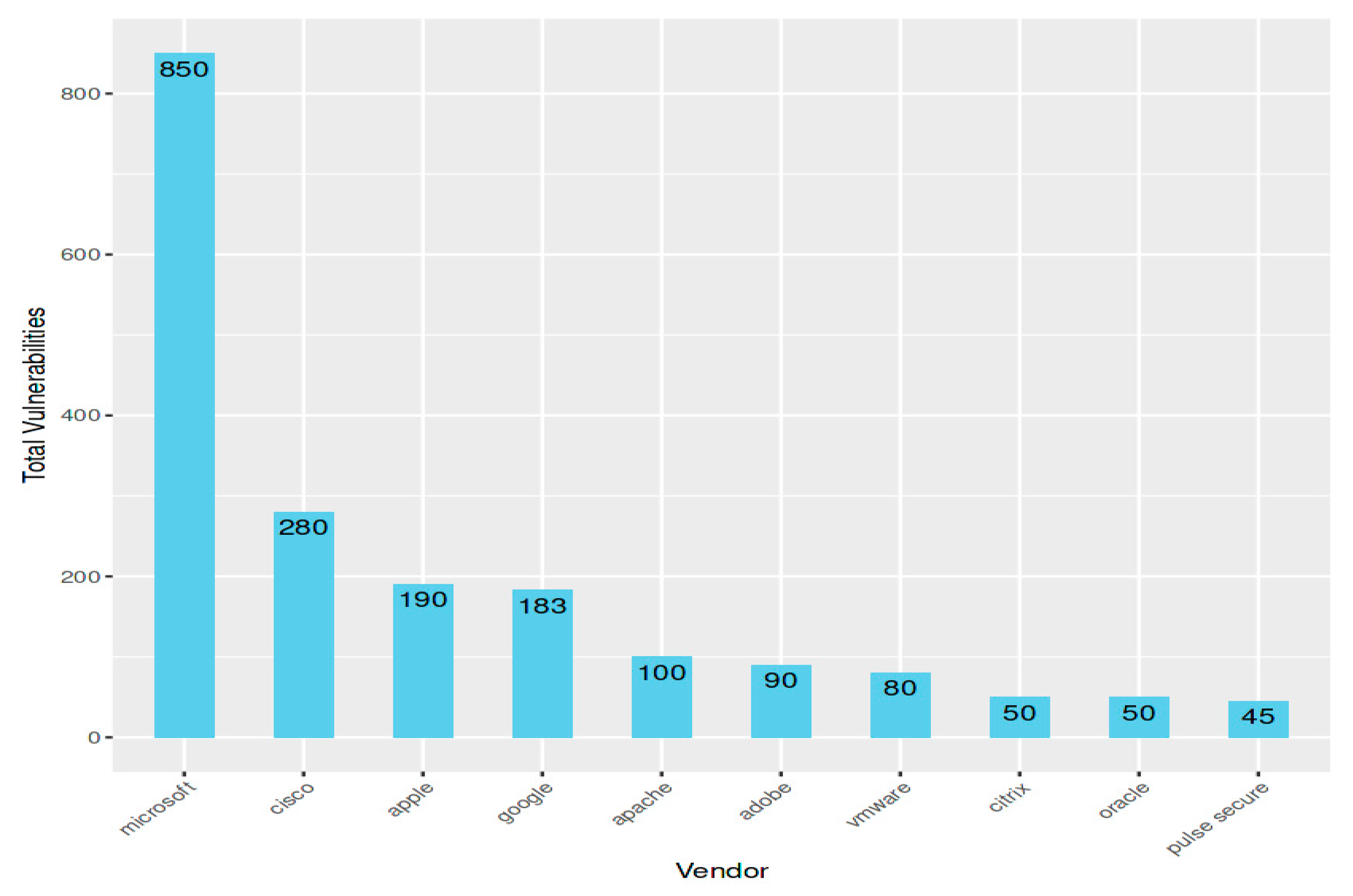
Figure 9 enumerates the top 10 vendors with the greatest number of vulnerabilities. Citrix, Oracle, Apple, Google, Cisco, Microsoft, VMware, Adobe, and Pulse Secure are the top ten vendors.
Figure 8.
Top Ten Vendor with highest number of vulnerabilities.
Figure 8.
Top Ten Vendor with highest number of vulnerabilities.
This information is important because it demonstrates that vulnerabilities exist even in the biggest and most reputable technology companies. Businesses that utilize the software from these providers are required to be aware of the vulnerabilities and take the appropriate action to address them.
Vulnerabilities might make a big difference. Attackers can use vulnerabilities to initiate attacks, obtain access to systems and data, or steal data. Organizations may face numerous issues as a result of this, such as financial losses, damage to their brand, and interruptions to business operations. Organizations can take a number of steps to reduce the possibility that their vulnerabilities will be exploited, including:
• Determining and addressing vulnerabilities: Companies need to identify and address system and software vulnerabilities as soon as they are found. To achieve this, a variety of instruments and techniques can be applied, such as code review, vulnerability scanning, and penetration testing.
• Implementing security controls: Organizations need to implement security controls to reduce the likelihood that vulnerabilities will be exploited. Among these controls are intrusion detection systems, firewalls, and access control systems.
• Employee education: Companies need to train employees on security best practices and how to defend against exploitative attacks.
Companies using software from the top ten vendors listed above should be particularly mindful of the software's vulnerabilities. To do this, businesses can visit the NIST website and search for software vulnerabilities that affect their software. Companies can also register to receive security alerts from the vendors they collaborate with.
By taking these precautions, organizations can reduce the risk that their vulnerabilities will be exploited and protect themselves from the negative consequences of security breaches.
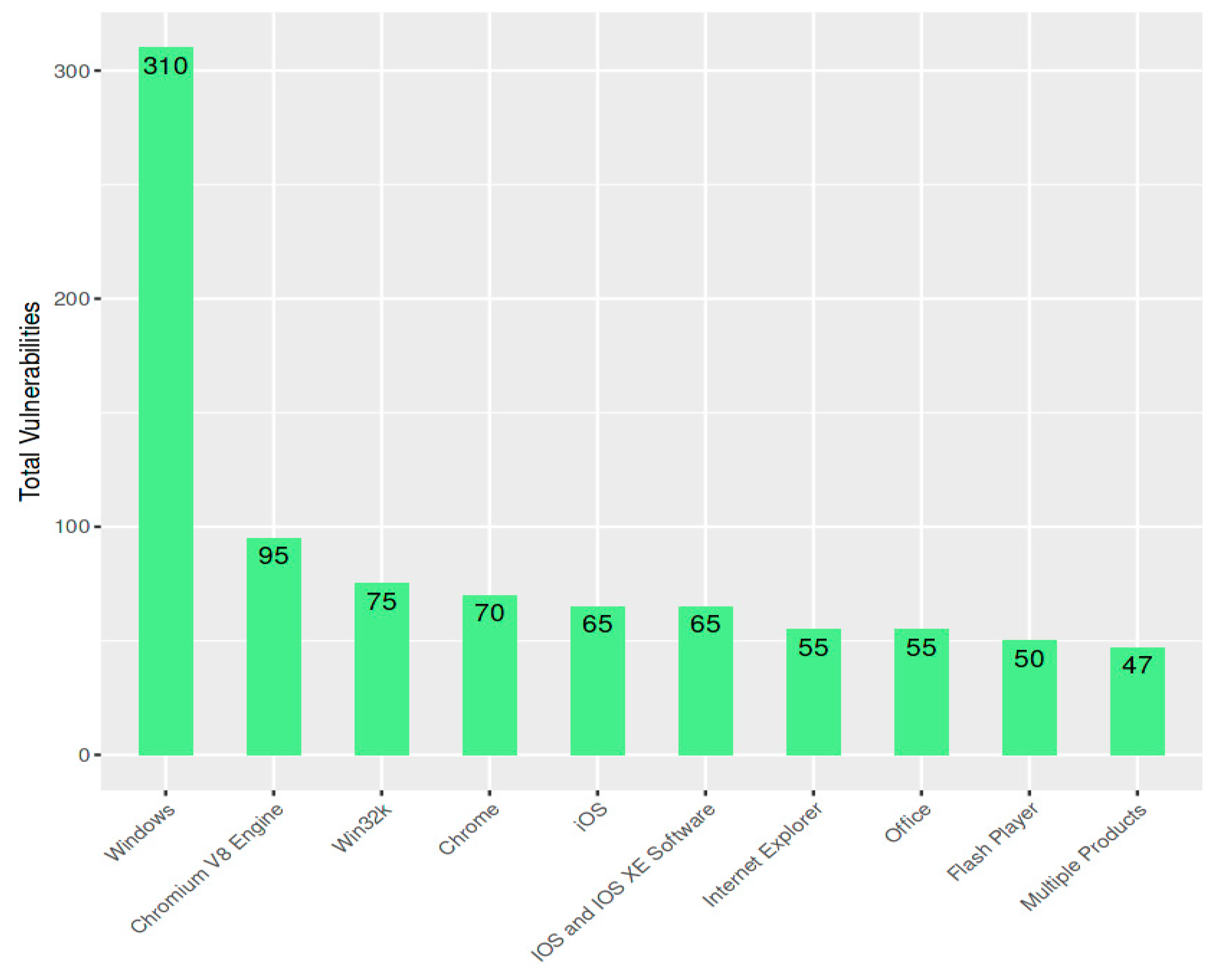
The figure 8 above shows the top 10 vendors with the highest number of vulnerabilities in 2022, according to CVE Details shown in figure 8 above.
With 850 vulnerabilities, Microsoft has the most, according to the graph. With 800 vulnerabilities, Cisco comes in second, followed by Apple with 600 vulnerabilities. Both Google and Apache have 400 vulnerabilities, which ties them for fourth place. There are 380 vulnerabilities with Adobe, 280 with VMware, 200 with Citrix, 190 with Oracle, and 183 with Pulse Secure.
There are various cybersecurity concerns for this graph. Firstly, it demonstrates that the most vulnerable software suppliers are also the biggest and most recognizable ones. This is because there are several ways for attackers to discover and take advantage of software vulnerabilities due to these companies' extensive attack surface. Second, the graph indicates that there are more vulnerabilities every year. This can be attributed to various variables, such as the expanding quantity of software applications, the complexity of software, and the intelligence of attackers.
Cybersecurity is negatively impacted by the growing number of software vulnerabilities. It first makes maintaining the security of an organization's systems more challenging. Companies must promptly fix vulnerabilities, but it can be challenging to stay on top of the ever-increasing number of vulnerabilities.
Second, attackers find it simpler to exploit systems as a result of the growing number of vulnerabilities. Vulnerabilities can be used by attackers to break into systems, steal information, or initiate attacks. Third, maintaining a secure posture costs more for enterprises due to the growing number of vulnerabilities. For their systems to remain secure, organizations must spend in security staff and equipment.
To lower their risk exposure, organizations should also think about utilizing software from a range of providers. A software vulnerability in a single vendor's product is more likely to impact an organization that uses only that vendor's software. Utilizing software from many manufacturers can help organizations lower their vulnerability to a single flaw.
3.5. Top Ten Applications with highest number of vulnerabilities
The top 10 apps with the most vulnerabilities in 2022 are depicted in figure 9 above, which has many ramifications for cybersecurity. Initially, it demonstrates that the most extensively used and well-liked programs are also the most susceptible. This is a result of the enormous attack surface these apps possess, which gives hackers a wide range of options for locating and taking advantage of software flaws.
Secondly, the graph indicates that there are more vulnerabilities in applications every year. This can be attributed to various variables, such as the expanding quantity of software applications, the complexity of software, and the intelligence of attackers. Numerous detrimental implications on cybersecurity result from the growing number of vulnerabilities in applications. It first increases the difficulty of keeping an organization's systems secure. Businesses need to address vulnerabilities as soon as possible, but it can be challenging to keep up with the increasing number of vulnerabilities.
Second, attackers find it simpler to exploit systems as a result of the growing number of vulnerabilities. Vulnerabilities can be used by attackers to break into systems, steal data, or initiate attacks.
Third, it costs more for businesses to maintain a secure posture because there are an increasing number of vulnerabilities. For their systems to continue to be secure, organizations must invest in security personnel and equipment.
In addition to the aforementioned, companies ought to think about the following:
• To prevent intrusions into their web applications, use a web application firewall (WAF). Web application vulnerability-exploiting attacks can be detected and prevented with the aid of a WAF.
• To safeguard their cloud-based apps, use a cloud security platform. The use of a cloud security platform can help detect and prevent attackers trying to take advantage of holes in cloud-based applications.
• Set up a security information and event management (SIEM) system to keep an eye out for any odd activity on their systems.
The identification of attacks that take advantage of application vulnerabilities can be aided by a SIEM system. Organizations can lower the risks associated with the rising number of application vulnerabilities by implementing these measures.
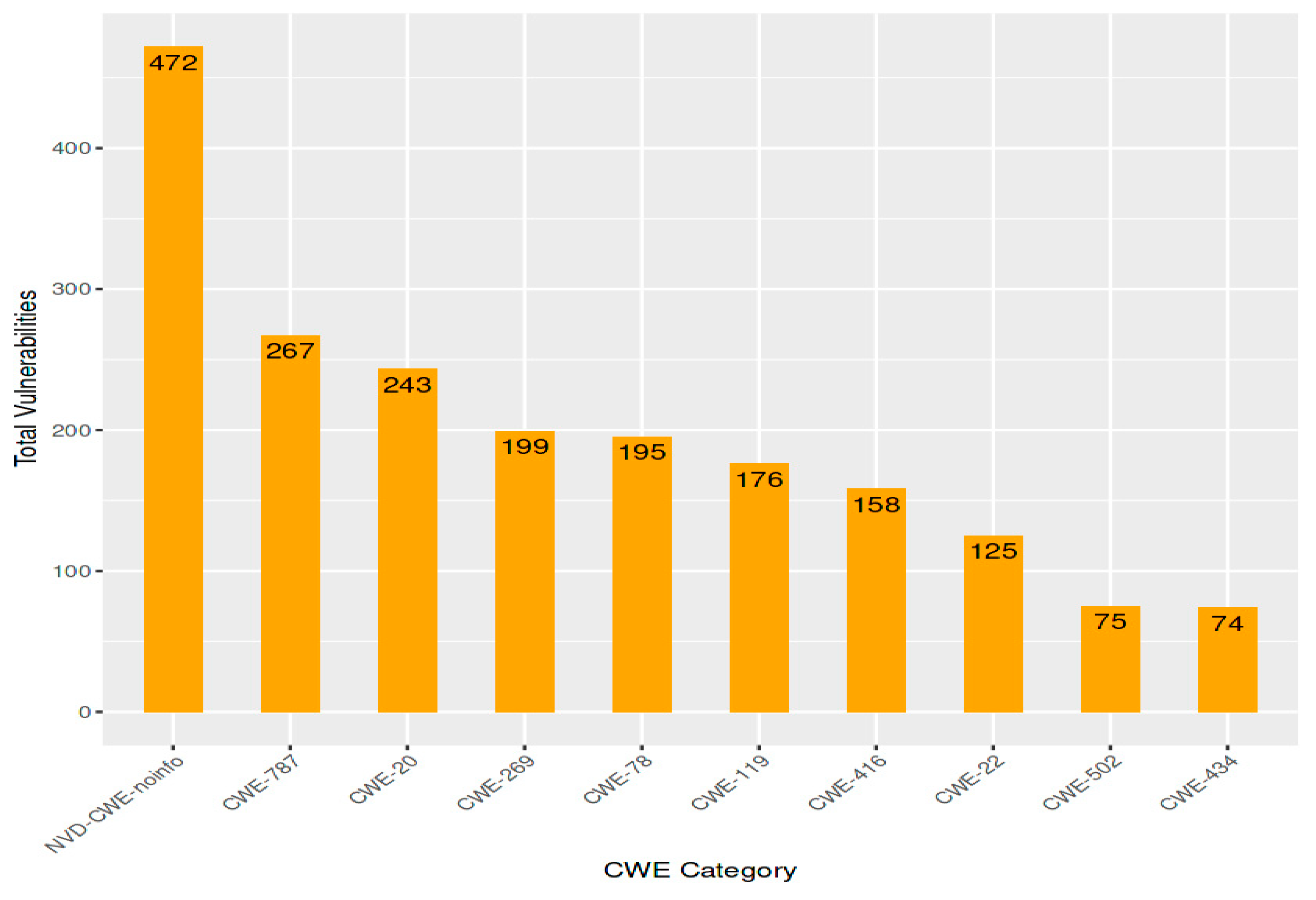
Figure 10.
Most Common CWE categories among Vulnerabilities.
Figure 10.
Most Common CWE categories among Vulnerabilities.
The most prevalent CWE (Common Weakness Enumeration) categories for vulnerabilities are displayed in figure 10. CWE is a list of software and hardware vulnerability types that the community has developed. The following are the top ten categories:
CWE-119: Improper Input Validation
CWE-78: Improper Neutralization of Special Elements used in Output
CWE-20: Improper Authentication
CWE-269: Improper Privilege Management
CWE-787: Out-of-bounds Read
CWE-416: Use of Hard-coded Credentials
CWE-22: Path Traversal
CWE-502: Deserialization of Untrusted Data
CWE-200: Information Exposure
CWE-400: Unrestricted Uploading of File with harmful File Type
These categories are all related to common programming errors that could lead to software vulnerabilities. For example, CWE-119 explains how insufficient user input validation exposes a system to the risk of malicious code injection by attackers. Attackers may use cross-site scripting attacks (CWE-78) if special characters in output are not properly neutralized.
Because these vulnerabilities are common, cybersecurity is negatively impacted in a number of ways. It first makes it easier for attackers to exploit systems. Attackers may use these vulnerabilities to gain access to systems, steal data, or launch attacks. Second, it increases the difficulty of keeping an organization's systems secure. Companies must quickly fix these vulnerabilities, but it can be challenging to stay on top of the constantly expanding list of flaws.
The following recommendations address how businesses can lessen the risks associated with the most prevalent CWE categories of vulnerabilities:
• Implement the Security Development Lifecycle (SDL) program. An SDL program is the process of incorporating security into the software development life cycle.
• Make use of the static application security testing (SAST) technology. An SAST tool can be used to identify software vulnerabilities before they are deployed.
• Make use of DAST (dynamic application security testing) software. It is possible to identify software vulnerabilities while it is operating by using a DAST tool.
• Provide secure coding techniques training to developers.
The most prevalent CWE categories for vulnerabilities should be known to developers, as well as how to prevent them. By taking these steps, businesses can help lower the risks connected to the most common CWE categories of vulnerabilities. The following frequently occurring CWE categories contain exploitable vulnerabilities:
Table 1.
CWE Categories among other vulnerabilities.
Table 1.
CWE Categories among other vulnerabilities.
| CWE Category |
vulnerabilities |
| CWE-119 |
Inadequate input validation can allow an attacker to insert SQL code into a database and steal data or perform other malicious tasks. |
| CWE-78 |
Cross-site scripting attacks can be leveraged by improper neutralization of special elements used in output, giving an attacker the ability to steal session cookies. |
| CWE-20 |
Unauthorized access to a system or application can be obtained by abusing improper authentication. |
| CWE-269 |
An attacker may be able to carry out harmful activities on a system by elevating privileges through the use of improper privilege management. |
| CWE-787 |
By using read to read data outside of the allocated memory buffer and breaking the limits, an attacker might be able to obtain private data. |
| CWE-416 |
Passwords and other sensitive data can be stolen through the use of hard-coded credentials. |
| CWE-22 |
An attacker may be able to obtain files outside of the intended directory by using path traversal, which gives them access to sensitive information. |
| CWE-502 |
It is possible to use the deserialization of untrusted data to run arbitrary code on a computer. |
| CWE-200 |
Information Exposure can be used to steal private information, including financial or consumer data. |
| CWE-400 |
Malicious files could be uploaded to a system by an attacker, who could then use them to steal data or run arbitrary code. Due to this vulnerability, files containing risky file types can be uploaded without restriction. |