Submitted:
26 December 2023
Posted:
27 December 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Mathematical elements used in DSA
2.1. ElGamal model and Diffie-Hellman Protocol
2.2. Hash Sha-512 Algorithm
2.3. Digital Signature Algorithm (DSA)
- An integer is chosen at random.
2.4. Number
2.5. Entropy
2.6. Correlation Coefficient
2.7. Discrete Fourier Transform
2.8. Goodness-of-Fit test
3. Presentation of new Elements
3.1. The Permutaions Algorithm
- An increasing array is constructed as follows: , ⋯.
- The constant is taken, and according to Eq. (26), this constant satisfies . Therefore, is an element of the array generated in I. Hence, in this research it is proposed to eliminate from the array, and replace it with the last element of the array generated in I; that is, by . As can be seen, only two operations were carried out. In the first, an element is removed from the array, and in the second, its place is replaced by the last element of the array from step 1. It is mentioned that when is the last element of the array from the previous step, in this case 1; then, its place is occupied by the immediately preceding one; that is, in this case it would be .
- In this step we take , and in the same way as before, is an element of the array that resulted in 2, because . From here, is removed from the array in step 2, and its position is replaced by the last element of the array. In case is the last element of the array, then its position is taken by the immediately preceding element.
- If its continue removing elements from the array, it reach the following scenario; and , where with . In this sense, because it is the only element left to eliminate, in other words, it has position zero.
3.2. Digital Signature procedure proposed
3.3. Diffie-Hellman protocol and number for the Digital Signature Algorithm
- Randomly generate an integer k that satisfies .
- Using your private key you obtain the variable according to Eq.(28).Additionally, perform the calculation indicated in Eq.(29).Taking the integer associated with the string h of 512 bits, the operations of Eq. (30).In this case, C represents a 2048-bit string, which is obtained in the following way: from the product 2048 bits are taken after the decimal point. Using the algorithm described at the beginning of this section and taking the Bytes to the right of the decimal point and after bit 2048, it is possible to obtain a permutation on an array of 256 elements, which defines an with the agreed attributes . This box is named S.
- Once the string C and the box S are generated, the parameter is obtained according to Eq. (31).The operation is a substitution procedure, in this sense, The C string of 2048 bits is divided into blocks of one byte, and to perform the substitution it proceed in the same way as the Advanced Encryption Standard AES [44].
- Also, perform the calculation . With the above measurements, B can obtain C by performing the operation of Eq. (30), and subsequently generate S. Then, it can be calculated at . It is written differently, because it is not necessarily equal to .
- To conclude this part, B verifies if , if so, it confirms that the message was sent by A; Furthermore, it was not altered. Otherwise, the signature is rejected.
4. Particular values for model of signature proposed
-
The model used is p, where the module p and the primitive , which intervene in the signing process and are written in hexadecimal base; furthermore, , with being prime and n being even. The particular values of these variables are written below:= c90ecc40f41b8e2a0858037f4de90d2e15a6121ce9b151fb4e0d51c0de8a9666ea882eba 9d233fa3abadf70a098be5e5a00eb1005bd8c3519301ffb272988665148d3d7239670cd33d60 599b41160608ab5497a5d17c149d3e35f8e7f15aef0696e8c48a37e8e2ba73bcf0a267886ff257f7f75b2603455a2418d69c4651d00f= ee5b8b66666ff516440a0501edb330ca85b09bd8e231e588a65050a93aeb664c6334cd057 362004f76619adc2bc3dfa5d25bc76f8e5a5eb999431e6b1720512b9e78a2b47d9694c0b403a146d24541011ca6a4840acbe26ecda9a6ff8ac674ab6df1127c77221e9f32654e31d30a4cf70442b6bfb0d4dedb99126be6ffc6eab1n = 62p = 47a9c62c3021e4dbd0e8ee548d5e1b2dc6a1c4f5bb0345f720ba54f2256a9befb394d7b15 5fa27bfe1701aa3f61732f852c51deebd0b20bfc098266348d5cdff871e3d4a6b623a3a40c3a4495d13b699771c4c9d036ef1cce70c746d618ad2000520ffe9db5764e74e2344befe45688d4a4ff 14219e346de9911f398aa6c86438e38ab0ffcfe56160fb060f361e0c06335c458a516a6bd6a0e4 2677593be5b0d663905152c4ffb9d0cbc7552904a7c13453008950343bd204d41ed3d47cd4b f4fa03956208dfe0c5f1d9fa8275073ca63f20df1de1bbedec281f890956a2355 e8517a334e9c1 e8c8aea862d3b5965e1c6c22ef7efe212154c979e9fbdfc7e7445f= 1bc36c7fd8704a7d008f320070dc9c2a2cd51047d7d48401816693f6d f3c83f6a99d7 2bf3d8555f192dcbe33aaabad164070b905b92a8d2bbc8f2c72eab5bb61fa1e549 3c21c7fd1dd8c2e50f06072b4c31bf0e3ca3e07574c361d6b9eec474229ae024fb3fcf3f040f937eef2e6383e644189be811aaf8e7175111ce364a24c960e7273514b7772fffaa39d7074465e53a76ec78ac3270a938295fcf51b5dc962240658513aaab0c383005dbf7ae530c5fcd4c7420e0301bb4d89b0e3de8f61f6c844155c81aed618c6dd7e4be4d2277376e6b93c4001a717b2376911f14a017ca f3d6f8da8adabeeed578d0fa3a4bd1b7b74adbe82b2327936f352b60248ceThe particular values of private and public keys, both for the sender and for the recipient, as well as the common key, , are presented below:= c3ef3be7248d72be5de8d531ff2b5aaa1c5c6caf2d7fade94302fd3eb923f53e0e9fa67a1 5fa19a842af51ddb4a6d897fe633c9c5c908cfeca68df86fe58cdcc08300cc05ea38c0020cb8d6d19a465a7688d97122cca67a978fcd71d1cc709c96a0213d389753cfa8a99d212a648e1a3aa1 8bf86036ebbe10eeed469a950163c74572d00e1fdb9fbbc08531b3486ec9d0c46f25c9543cf5eb4d31d2071adaf339a6ee586e938c0e3762a4492029ffbd536a98d77a3f63b740f7aea002b 0f6844818863da1f7f14ae896ed735502fb18b2f77818ceba6e6d4be952dc9bb37e6b6fce38ea1f7f174ee8004590ea1a22600a0e2a8a584d9f40273c2e73d82e5284a= 4067213f39fd257d30ac2a17470628c0beb1dc53c806ce4632e026e4350299cc7f484072 af98a7f88e67cbee75ea7721c09a728508dd7626438ad5d49c7716f6f6d5d397cec0c7b98f229 48cec6b251e198ea11c48690320d8faa22cc20ee21fc76eb50ed84f226d13536fecb7d85520d4 e78eb36ded395ca07d3ef85c906e8a592042e948fcfdc3c7d78d79e8bccb577c9c00796c47421 215bd9c0fb8b03a41e4901e652642b2d63e0885c2c161e9da36c10d363f848ec2d973a5dc155 e9129c73adb1411920a72f3653c23845558805a9d404e7116a8be0bbbad58c2837520a5b4220 e16d27aa628a1ec3f191363db1db54380d87480b2ee48bc1580c06a26a2= c4b942d9c75e950495fa22f46b196ecc45fb5332fa4b4b23ffff999144af53c80f08ea89c639 1677d8da4258938cb48dbf085ca2bbbb9899725c4ee9dc4e47ce7c1e80b0e1f2825cd97540eb 8bac8a907fe02eb404a93c44b065bc47489fb10ede073e0e838d910f4375ea95fd462f14bd8e 7872a3acf19da600f26c9a62ac0aa6371c633234648814db059be90be459c991d526aa044766 51352ee84059f8983acfcc92936dcacfe2264d1c0763e7a05397292c22e1025df53a4ef69542ab68bc4aec1073cf47a6e42cad7aeff27ad81fa94c5afabcd543068f43fd25de8248237a335784d829354d541ac289cb23cf9166b78a6c648d29bd09703d50edbf4a= 25df467d93e9ad760aadaeabf23be2bb6fd579707964433ed719bac3878cab157ee2b05 f5209475ce133ceab202f8cbae552f62852bda4031f1603cc082134a111fcf3a8867e2c5ab884b 9da0b6a9fe1bc9ece7410467421e03cde66d5a2de2840c8896c1eb63d0230c17ac46af284e1d1 5de080004fa87b7cd816c5c09d44295e385eca13f00659a1532de359a7d7716032db3998b5ad b0b529f36a6d5c65f8c831e555f17de40f841203574598652568a399f159327fc1da17a75b2dfa087c9ec69bcd09efe897f4acf41c8c6fc93ecbfd7ad60c7344e8451c8dbdad5b51544ed769 d525a678383dc27706ee2cd788a34d8955d18cfd640b5af8c4091093f99= 154b4820e5d1480d15f78ae71061a2699c9bce5883f22b70083ccadcc15b03592ab89461 740860487fb8c8b49c785f1b68a2884b007283921a0531dc79f5e212bc27fd0500855c32942f d759bb491f024133ee6928fca8116a686900004177fa04b4ae2ddc7b50449abcf17c421b8ea3 0f671736771d25794bdfde42f2cedd0d2378942150023a2d1cc949793ec7ee2172277bedc4a2 7cf50c9352bc3b1a5120dfd55a3778604cac6f1b52350909d62d9e2e263c81b5b3a96f7cf52e fbaf738776138b454fd32d3fe6fa501ad84ae2f70a2b6c97caee23446feede85dd58a5f3a62b 7c965cc78e6e551d34d50eddfc9f756e9704345edf4bf15c6e9b03f320b1f2
-
In relation to the variables k and h that were used in this development, they are shown below, as well as the box that was generated with these values is presented in the Table 2.k = 0053f7811cbc41ddd8ee8d01888a31508b6f5b07b0838ca4c4b347856c3705ce351a6b90 e9f9be27240a96e22660d1e9e96cca5b75c6cbb6732dbf7c00cc2b12c4be5fea42d4e8e47095 48f18a86e8f922aa4dfe7c4c8a8118fbf5248fd51d90a208fb988f95669ea757cc351c441f081f f10cf92a5b728d9ae31186809a82d1b7bf66a23985e2ddae184ab745e21b9dc7092f54e93c2b 60e1af3baa3b63015cecaaca0fa7ea02286fa0ea7f6da8874003bbdd1620385d85d5269b9728 7843ba28934de8410e6f08d1b8d394fade0a7bb9cd3f473795af825f105856b022f073534118 357037d104bc262efe56cc4bd3d3087df1979dcae066349bee3aa7b00e56h = 0c91b4b65321c770d0e892391636893f757bcf982364ae934991c546ec1d920b387d61f52 d087ca87205ecbb980cae454bcf223191ce506b542e680d5483d2f6
-
Finally, the values of the parameters are described, and , which represent the signing of the sender, that is, . In addition, the information of the number was obtained from some important works [45,46].= 1d95637beae8d5e86c5c9d16b1cc6087cfd7ed7a9addda50f2cd7cea7dcddbbc1d6e8f1 747584383177ddfd8aa87e8ea4d2ae6047e5b7f5f7cfe344a87a47d21550e4d99f8697237f2d 1e14d432b2cf50252048ffaad2c9d634b8bed1ff369a25122edff9d099095e4c3600004b3be9 5fdc728f878b0b62ed46ab4d595109ea2a465c67aefb42a2d885f17e82af6460e59f28c61efb 362ea32e7e6c821a5dd5d15816953cf22ca0084d30147969faa28a1c483c29026e7a269f7054 e845c3ad70cc087ca61827c06088be618fb82775659b177108986f91e9753521d50f205d1f93 de1a222f11398d693ebd6dcf71741ec6a2b84bdbc185d69918a5ab89219a2d4= 21c7b8510dac23a98bfcedccc90102e20983e26dc8d713da2e4f1266403df05a31e4ac3 bee8e6ee7244945f3c0fc74907b3a15ac5ee40feeec7ac3cbbb033ddd123fd6b896c34638b70 f050700adc7cc10639a314f118d598e071d68753ac1766a7f34cf5505eb6712346648d95018a b2978602f1ec7dccea7e52c6f791895892e41b18d8efb32b3dae46ac2f2b8258aa222be42359 c803fe929b0d388ad741dfdf79034b36f17cb31298f2b8ce87f955220bda00f536cdd9e3407c 8bf61fd4cad3c0c8a220b4a6fd1649dae2a5d80ce87ee095724549ef86bf689d52a2e085d961 913ff056f5f7bb69dd490508c954c3148765c9272870de1e4c8e7d31830b3
5. Experiments and Results
5.1. number
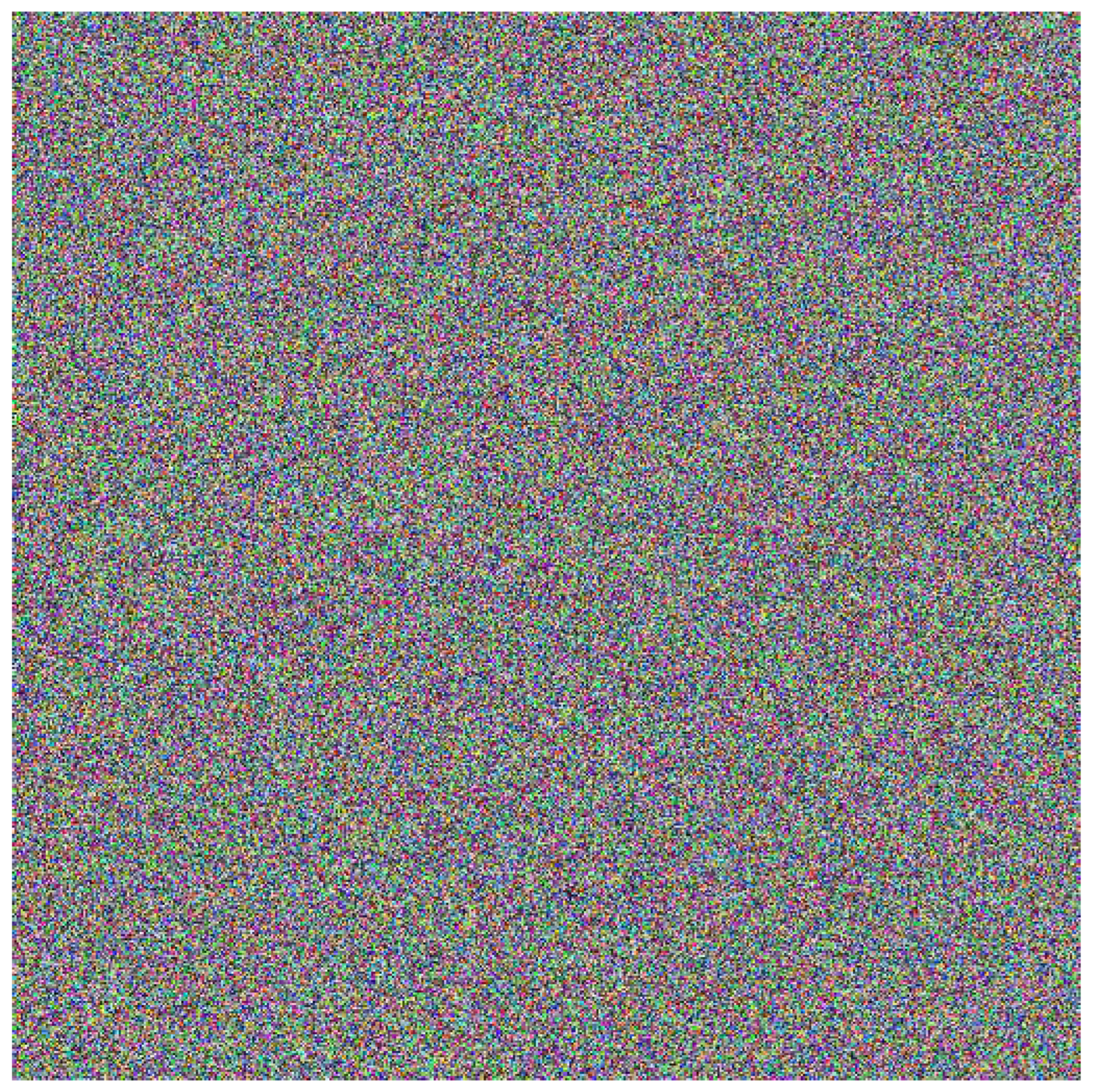
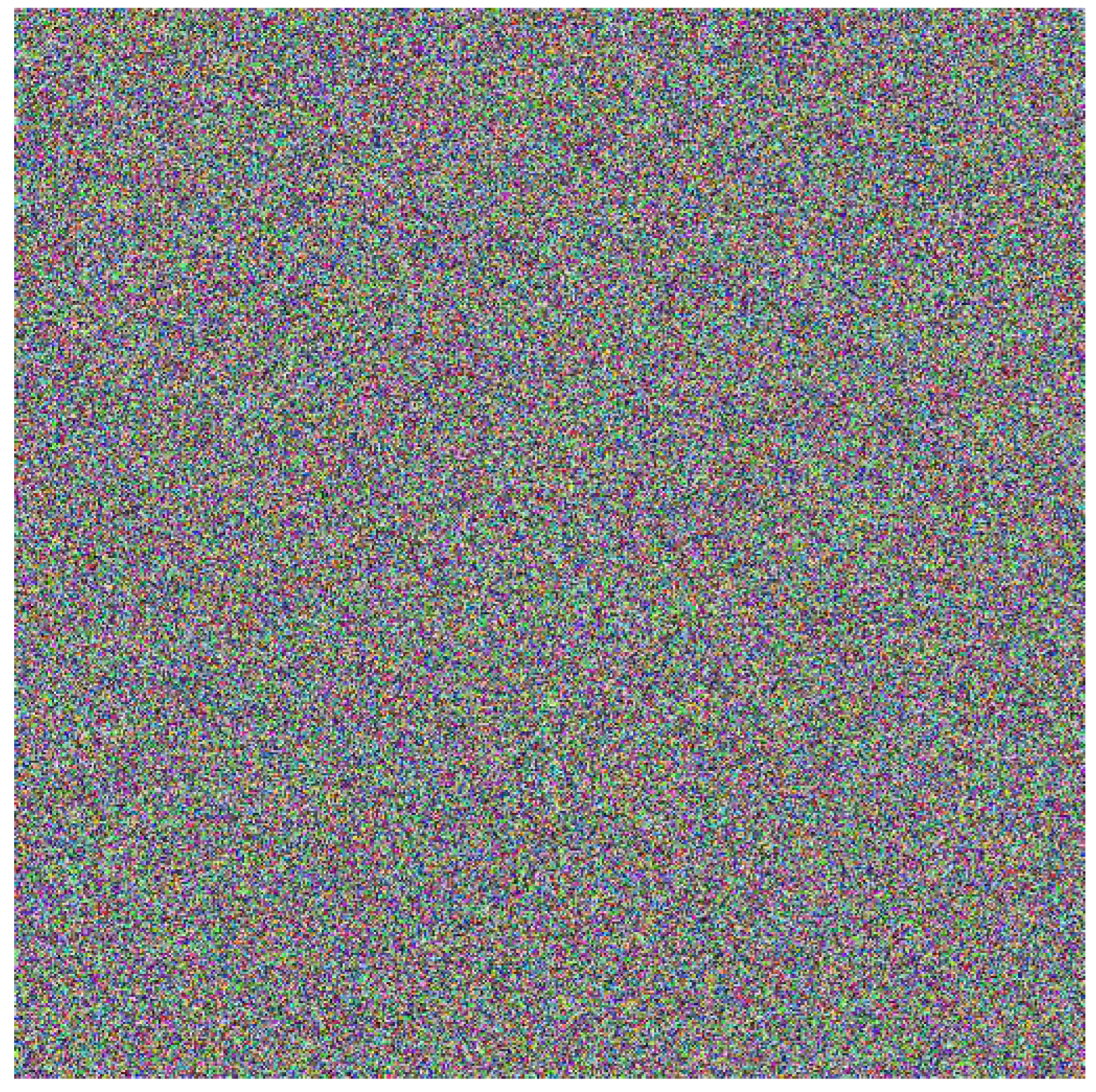
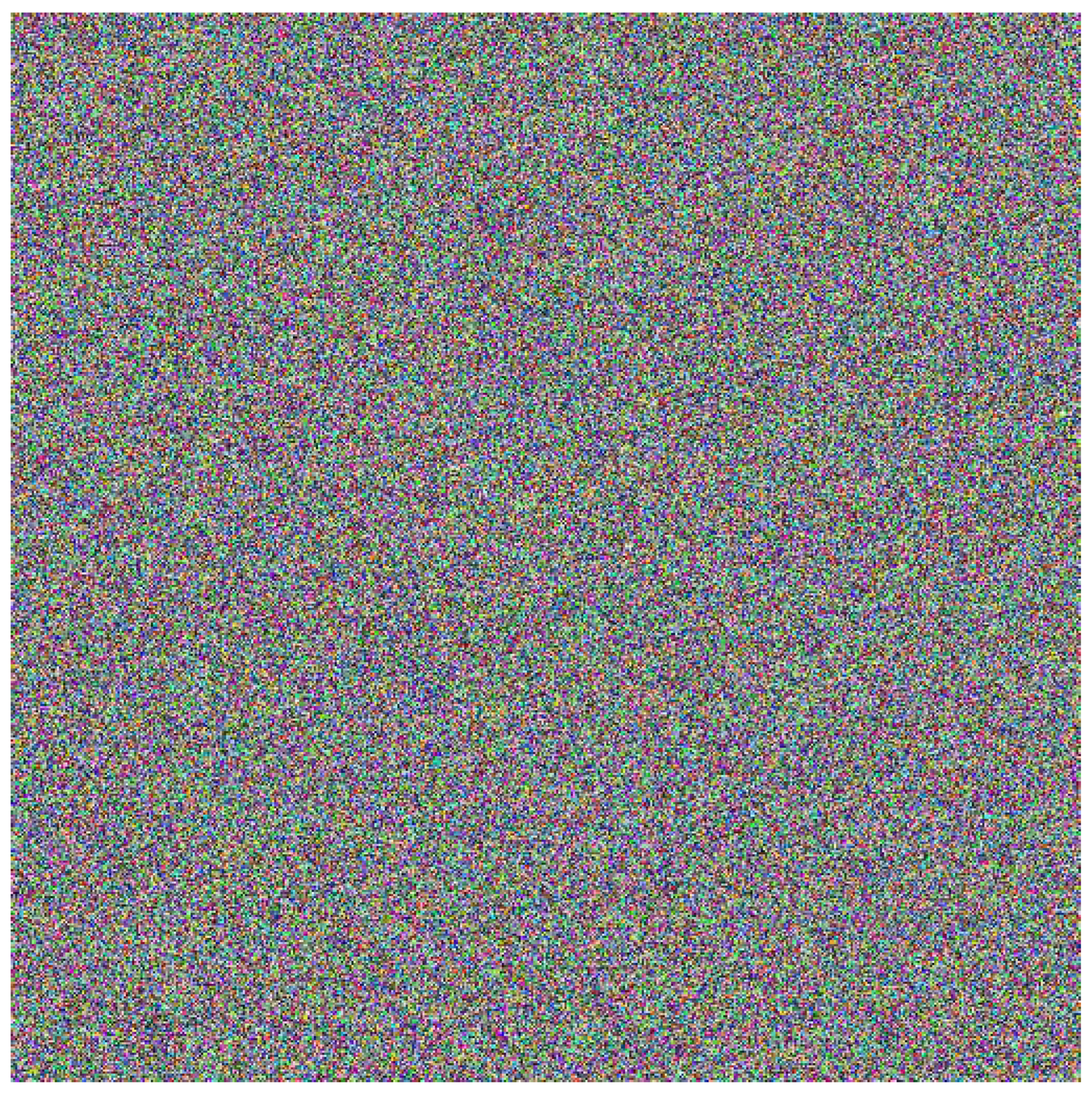
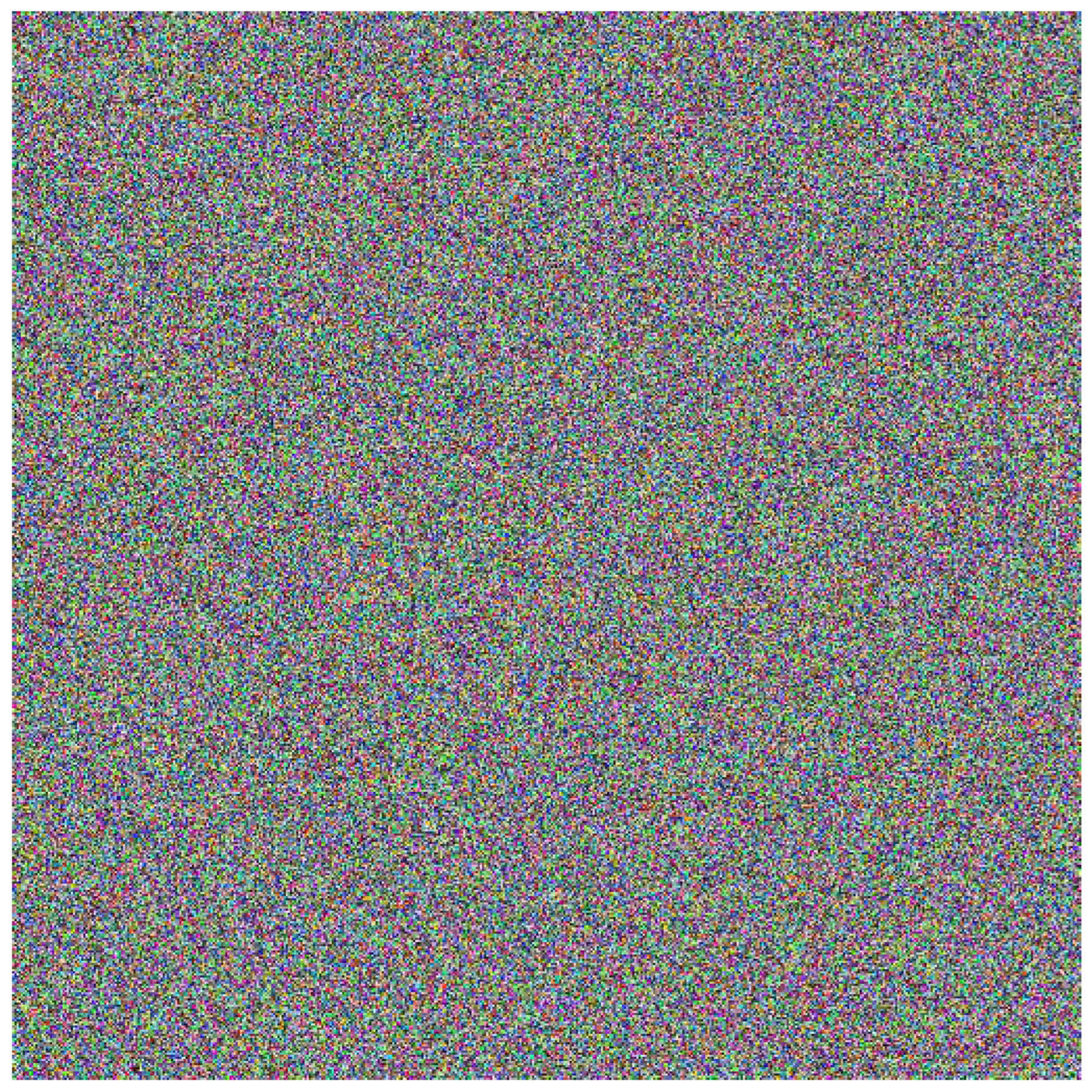
5.2. An Image Construccion Using Signatures Blocks
5.3. Sensitivity to changing plain text
5.4. Sensitivity to changes in the sender’s private key
6. Analysis of Results
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| DSA | Digital Signature Algorithm based on ElGamal, Diffie-Hellman protocol and the number |
| DSA | Digital Signature Algorithm |
| S-box | Substitution box |
| DFT | Discrete Fourier Transform |
References
- KUMAR, Vivek. a. Enhanced pairing-free identity-based broadcast authentication protocol in WSN using ElGamal ECC. Security and Privacy 2023, 6, e278. [Google Scholar] [CrossRef]
- Dawson, J.K.; Ayawli, B.B.K.; Agyemang, S.; Baah, P.; Akyeramfo-Sam, S. Ensuring Cloud Data Security Using the Soldier Ant Algorithm. Journal of Advances in Information Technology 2023, 14. [Google Scholar] [CrossRef]
- Abusukhon, A.; Anwar, M.N.; Mohammad, Z.; Alghannam, B. A hybrid network security algorithm based on Diffie Hellman and Text-to-Image Encryption algorithm. Journal of Discrete Mathematical Sciences and Cryptography 2019, 22, 65–81. [Google Scholar] [CrossRef]
- Wang, L.; Yuan, Y.; Ding, Y.e.a. Analysis and Design of Identity Authentication for IoT Devices in the Blockchain Using Hashing and Digital Signature Algorithms. International Journal of Distributed Sensor Networks 2023, 2023. [Google Scholar] [CrossRef]
- Schoenmakers, B.; Segers, T. Secure Groups for Threshold Cryptography and Number-Theoretic Multiparty Computation. Cryptography 2023, 7, 56. [Google Scholar] [CrossRef]
- Parida, P.; Pradhan, C.; Gao, X.Z.; Roy, D.S.; Barik, R.K. Image encryption and authentication with elliptic curve cryptography and multidimensional chaotic maps. IEEE Access 2021, 9, 76191–76204. [Google Scholar] [CrossRef]
- Qin, Y.; Zhang, B. Privacy-Preserving Biometrics Image Encryption and Digital Signature Technique Using Arnold and ElGamal. Applied Sciences 2023, 13, 8117. [Google Scholar] [CrossRef]
- Badawy, M. Security Evaluation of Different Hashing Functions with RSA for Digital Signature. IJCI. International Journal of Computers and Information 2023, 10, 99–116. [Google Scholar] [CrossRef]
- Shafique, Arslan. Chaos and Cellular Automata-Based Substitution Box and Its Application in Cryptography. Mathematics 2023, 11, 2322. [Google Scholar] [CrossRef]
- Akhmetzyanova, L.; Alekseev, E.K.; Babueva, A.A.; Smyshlyaev, S.V. On the (im) possibility of secure ElGamal blind signatures. Mathematical issues of cryptography 2023, 14, 25–42. [Google Scholar] [CrossRef]
- Singh, A.K.; Roy, M.K.; Karforma, S.; Mukhopadhyay, S. IMPLEMENTATION OF E-BANKING TRANSACTION SYSTEM USING ELGAMAL DS. Journal of Data Acquisition and Processing 2023, 38, 1883. [Google Scholar] [CrossRef]
- Mehibel, N.; HAMADOUCHE, M. Efficient and secure digital signature algorithm (DSA). Emirates Journal for Engineering Research 2023, 28, 3. [Google Scholar]
- Adeniyi, E.A.; Falola, P.B.; Maashi, M.S.; Aljebreen, M.; Bharany, S. Secure sensitive data sharing using RSA and ElGamal cryptographic algorithms with hash functions. Information 2022, 13, 442. [Google Scholar] [CrossRef]
- Abdallah, H.A.; ElKamchouchi, D.H. Signing and verifying encrypted medical images using double random phase encryption. Entropy 2022, 24, 538. [Google Scholar] [CrossRef] [PubMed]
- Jasra, B.; Moon, A.H. Color image encryption and authentication using dynamic DNA encoding and hyper chaotic system. Expert Systems with Applications 2022, 206, 117861. [Google Scholar] [CrossRef]
- Qin, Y.; Zhang, B. Privacy-Preserving Biometrics Image Encryption and Digital Signature Technique Using Arnold and ElGamal. Applied Sciences 2023, 13, 8117. [Google Scholar] [CrossRef]
- Yousif, S.F. Performance comparison between RSA and El-Gamal algorithms for Speech Data Encryption and decryption. Diyala Journal of Engineering Sciences 2023, 123–137. [Google Scholar] [CrossRef]
- Lubis, R.K.; Pardede, A.; Khair, H. Digital Signature Security Analysis By Applying The Elgamal Algorithm And The Idea Method. Journal of Artificial Intelligence and Engineering Applications (JAIEA) 2023, 3, 373–382. [Google Scholar] [CrossRef]
- Saeed, H.; Elsisi, M.; Diab, T.O.; El Sobky, W.I.; Abdel-Wahed, M.; Mahmoud, A.K. Famous Digital Signatures Used In Smart Contracts. In Proceedings of the 2023 International Telecommunications Conference (ITC-Egypt). IEEE; 2023; pp. 649–656. [Google Scholar]
- Ngendahimana, M.; Shen, W.; et al. RSA Cryptosystem Speed Security Enhancement (Hybrid and Parallel Domain Approach). Crypto and Information Security 2023, 2, 1–20. [Google Scholar] [CrossRef]
- Kokaras, M.; Foti, M. The cost of privacy on blockchain: A study on sealed-bid auctions. Blockchain: Research and Applications 2023, 100133. [Google Scholar] [CrossRef]
- Panario, D.; Perin, L.P.; Stevens, B. Comparing balanced sequences obtained from ElGamal function to random balanced sequences. Cryptography and Communications 2023, 15, 675–707. [Google Scholar] [CrossRef]
- Liu, J. Digital signature and hash algorithms used in Bitcoin and Ethereum. In Proceedings of the Third International Conference on Machine Learning and Computer Application (ICMLCA 2022). SPIE, 2023, Vol. 12636, pp. 1302–1321.
- Stinson D., P.M. Cryptography: theory and practice; Taylor & Francis group, 2019.
- Gallian, J. Contemporary abstract algebra; Chapman and HallCRC, 2021.
- FIPS, P. 180-4 Secure Hash Standard (SHS). FIPS, PUB 2015.
- Baccouri, S.; Farhat, H.; Azzabi, T.; Attia, R. Lightweight authentication scheme based on Elliptic Curve El Gamal. Journal of Information and Telecommunication 2023, 1–31. [Google Scholar] [CrossRef]
- Shawky, M.A.; Jabbar, A.; Usman, M.; Imran, M.; Abbasi, Q.H.; Ansari, S.; Taha, A. Efficient Blockchain-Based Group Key Distribution for Secure Authentication in VANETs. IEEE Networking Letters 2023, 5, 64–68. [Google Scholar] [CrossRef]
- Lei Wang, Y.Y.; Ding, Y. Analysis and Design of Identity Authentication for IoT Devices in the Blockchain Using Hashing and Digital Signature Algorithms. International Journal of Distributed Sensor Networks 2023, 2023. [Google Scholar] [CrossRef]
- Balasubramanian, K.; Davidson, E.R. Rational approximations to pie: transcendental π and Euler’s Constant e. Journal of Mathematical Chemistry 2023, 1–6. [Google Scholar] [CrossRef]
- Garipcan, A.M.; Erdem, E. FPGA modeling of a novel fully-synthesizable and secure TRNG based on key-dependent s-box. Digital Signal Processing 2023, 136, 103969. [Google Scholar] [CrossRef]
- Shannon, C.E. A mathematical theory of communication. The Bell System Technical Journal 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Rana, S.; Mondal, M.R.H.; Kamruzzaman, J. RBFK cipher: a randomized butterfly architecture-based lightweight block cipher for IoT devices in the edge computing environment. Cybersecurity 2023, 6, 3. [Google Scholar] [CrossRef]
- Wen, H.; Kang, S.; Wu, Z.; Lin, Y.; Huang, Y. Dynamic RNA Coding Color Image Cipher Based on Chain Feedback Structure. Mathematics 2023, 11, 3133. [Google Scholar] [CrossRef]
- Al-Mhadawi, M.M.; Albahrani, E.A.b.; Lafta, S.H. Efficient and secure chaotic PRNG for color image encryption. Microprocessors and Microsystems 2023, 101, 104911. [Google Scholar] [CrossRef]
- Heumann, C.; Schomaker, M.; Shalabh. Hypothesis testing. In Introduction to Statistics and Data Analysis: With Exercises, Solutions and Applications in R; Springer, 2023; pp. 219–265.
- Ahakonye, L.A.C.; Nwakanma, C.I.; Lee, J.M.; Kim, D.S. SCADA intrusion detection scheme exploiting the fusion of modified decision tree and Chi-square feature selection. Internet of Things 2023, 21, 100676. [Google Scholar] [CrossRef]
- Luengo, E.A.; Olivares, B.A.; Villalba, L.J.G.; Hernandez-Castro, J. Further analysis of the statistical independence of the NIST SP 800-22 randomness tests. Applied Mathematics and Computation 2023, 459, 128222. [Google Scholar] [CrossRef]
- Lorenzo-Seva, U.; Ferrando, P.J. A simulation-based scaled test statistic for assessing model-data fit in least-squares unrestricted factor-analysis solutions. Methodology 2023, 19, 96–115. [Google Scholar] [CrossRef]
- Silva-García, V.M.; Flores-Carapia, R.; Cardona-López, M.A.; Villarreal-Cervantes, M.G. Generation of Boxes and Permutations Using a Bijective Function and the Lorenz Equations: An Application to Color Image Encryption. Mathematics 2023, 11, 599. [Google Scholar] [CrossRef]
- Ventre, A.G. Algorithms. In Calculus and Linear Algebra: Fundamentals and Applications; Springer, 2023; pp. 257–267.
- Mahboob, A.; Siddique, I.; Asif, M.; Nadeem, M.; Saleem, A. Construction of highly non linear component of block cipher based on mclaurin series and mellin transformation with application in image encryption. Multimedia Tools and Applications 2023, 1–9. [Google Scholar] [CrossRef]
- Panario, D.; Perin, L.P.; Stevens, B. Comparing balanced sequences obtained from ElGamal function to random balanced sequences. Cryptography and Communications 2023, 15, 675–707. [Google Scholar] [CrossRef]
- Pujiono, I.P.; Rachmawanto, E.H.; Nugroho, D.A. The Implementation of Improved Advanced Encryption Standard and Least Significant Bit for Securing Messages in Images. Journal of Applied Intelligent System 2023, 8, 69–80. [Google Scholar] [CrossRef]
- Müller, H. The Physics of Transcendental Numbers. Progress in Physics 2019, 15, 148–155. [Google Scholar]
- Balasubramanian, K.; Davidson, E.R. Rational approximations to pie: transcendental π and Euler’s Constant e. Journal of Mathematical Chemistry 2023, 1–6. [Google Scholar] [CrossRef]
- Lai, Q.; Hu, G.; Erkan, U.; Toktas, A. A novel pixel-split image encryption scheme based on 2D Salomon map. Expert Systems with Applications 2023, 213, 118845. [Google Scholar] [CrossRef]
- Blazy, O.; Kakvi, S.A. Identity-Based Encryption in DDH Hard Groups. In Proceedings of the International Conference on Cryptology in Africa. Springer, 2022, pp. 81–102.
- De Feo, L.; Delpech de Saint Guilhem, C.; Fouotsa, T.B.; Kutas, P.; Leroux, A.; Petit, C.; Silva, J.; Wesolowski, B. Séta: Supersingular encryption from torsion attacks. In Proceedings of the Advances in Cryptology–ASIACRYPT 2021: 27th International Conference on the Theory and Application of Cryptology and Information Security, Singapore, December 6–10, 2021, Proceedings, Part IV 27. Springer, 2021, pp. 249–278.
- Lalem, F.; Laouid, A.; Kara, M.; Al-Khalidi, M.; Eleyan, A. A Novel Digital Signature Scheme for Advanced Asymmetric Encryption Techniques. Applied Sciences 2023, 13, 5172. [Google Scholar] [CrossRef]
- Li, L.; Abd El-Latif, A.A.; Niu, X. Elliptic curve ElGamal based homomorphic image encryption scheme for sharing secret images. Signal Processing 2012, 92, 1069–1078. [Google Scholar] [CrossRef]
- Khader, A.S.; Lai, D. Preventing man-in-the-middle attack in Diffie-Hellman key exchange protocol. In Proceedings of the 2015 22nd international conference on telecommunications (ICT). IEEE, 2015, pp. 204–208.
- Ranasinghe, R.; Athukorala, P. A generalization of the ElGamal public-key cryptosystem. Journal of Discrete Mathematical Sciences and Cryptography 2022, 25, 2395–2403. [Google Scholar] [CrossRef]
- Yang, N.; Tian, Y.; Zhou, Z.; Zhang, Q. A provably secure collusion-resistant identity-based proxy re-encryption scheme based on NTRU. Journal of Information Security and Applications 2023, 78, 103604. [Google Scholar] [CrossRef]


| 0 | 0 | 0✓ | 5 | 5 | 5 | 5✓ |
| 1 | 1 | 1 | 1✓ | 3 | 3✓ | |
| 2 | 2 | 2 | 2 | 2✓ | ||
| 3 | 3 | 3 | 3 | |||
| 4 | 4✓ | 5 | ||||
| 5 | 5 |
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 80 | 00 | 21 | 6e | 89 | c2 | 4a | 5d | f4 | 0a | 1f | 01 | f6 | 9a | 1e | 0b | |
| ad | 09 | f8 | 69 | 42 | 9c | e0 | 20 | 48 | 2c | 25 | de | cf | fc | 19 | 7e | |
| e5 | ef | 4c | 1b | 44 | 77 | d2 | 46 | 82 | 73 | 93 | 24 | f1 | 8a | 02 | 03 | |
| 84 | d4 | fa | 64 | 60 | 95 | 79 | 08 | 27 | c1 | 51 | 0e | e7 | ac | 6c | 07 | |
| 86 | 5c | 54 | 2d | f0 | 6f | 16 | 7d | 39 | dd | 04 | ec | 52 | 45 | b5 | bd | |
| df | fd | b2 | 49 | 30 | e4 | 17 | 3b | 62 | 29 | 9d | cd | cb | ae | 56 | b7 | |
| 14 | ab | 26 | d1 | 6d | a4 | 5a | db | 36 | 0f | 94 | f7 | 53 | e9 | d3 | 05 | |
| eb | c9 | 61 | c7 | 34 | b9 | 63 | cc | 8d | 9b | a1 | f3 | 18 | 67 | 0c | e1 | |
| 75 | 22 | 74 | 81 | 3e | aa | dc | c5 | 06 | d0 | e6 | b8 | 58 | 31 | 4d | 90 | |
| 97 | 4f | 6a | b0 | ea | 68 | 72 | fe | c6 | c4 | 1d | 55 | a6 | 10 | a5 | ff | |
| 28 | fb | ca | 96 | 47 | 7f | 4e | 43 | b6 | f2 | 33 | d5 | 23 | 7b | 41 | c0 | |
| e3 | 1c | 85 | 76 | be | 83 | a7 | b1 | 92 | 59 | f5 | ee | 66 | ed | 8b | b3 | |
| 0d | e2 | 3f | e8 | 40 | 87 | 99 | 37 | bb | 8f | 2f | 5f | 70 | d7 | 5b | 88 | |
| 15 | 13 | c3 | c8 | da | a9 | a8 | 2a | 65 | 8c | af | f9 | 32 | d8 | 12 | 1a | |
| 4b | 6b | a2 | 11 | 57 | bc | 2e | 78 | 2b | ba | d6 | a3 | 98 | bf | 7a | 9e | |
| 50 | 7c | a0 | d9 | 35 | 9f | 3d | 3c | 3a | ce | 38 | 71 | b4 | 8e | 91 | 5e |
| Chain length | Percentage of zeros | Percentage of ones |
|---|---|---|
| 75.000000 % | 25.000000 % | |
| 57.812500 % | 42.187500 % | |
| 54.687500 % | 45.312500 % | |
| 51.318359 % | 48.681640 % | |
| 49.935913 % | 50.064086 % | |
| 50.069427 % | 49.930572 % | |
| 49.978303 % | 50.021696 % | |
| 49.978560 % | 50.021439 % | |
| 50.003378 % | 49.996621 % | |
| 49.999330 % | 50.000669 % | |
| 50.000011 % | 49.999988 % | |
| 49.999981 % | 50.000018 % |
| Color | Red | Green | Blue |
|---|---|---|---|
| Entropy |
| Color | Red | Green | Blue |
|---|---|---|---|
| Entropy |
| Correlation | Red | Green | Blue |
|---|---|---|---|
| Horizontal | |||
| Vertical | |||
| Diagonal |
| Color | Red | Green | Blue |
|---|---|---|---|
| DFT | ✓ | ✓ | ✓ |
| Color | Red | Green | Blue |
|---|---|---|---|
| test | ✓ | ✓ | ✓ |
| Color | Red | Green | Blue |
|---|---|---|---|
| Entropy |
| Correlation | Red | Green | Blue |
|---|---|---|---|
| Horizontal | |||
| Vertical | |||
| Diagonal |
| Color | Red | Green | Blue |
|---|---|---|---|
| DFT | ✓ | ✓ | ✓ |
| Color | Red | Green | Blue |
|---|---|---|---|
| test | ✓ | ✓ | ✓ |
| Color | Red | Green | Blue |
|---|---|---|---|
| Entropy |
| Correlation | Red | Green | Blue |
|---|---|---|---|
| Horizontal | |||
| Vertical | |||
| Diagonal |
| Color | Red | Green | Blue |
|---|---|---|---|
| DFT | ✓ | ✓ | ✓ |
| Color | Red | Green | Blue |
|---|---|---|---|
| test | ✓ | ✓ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





