Submitted:
18 December 2023
Posted:
19 December 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
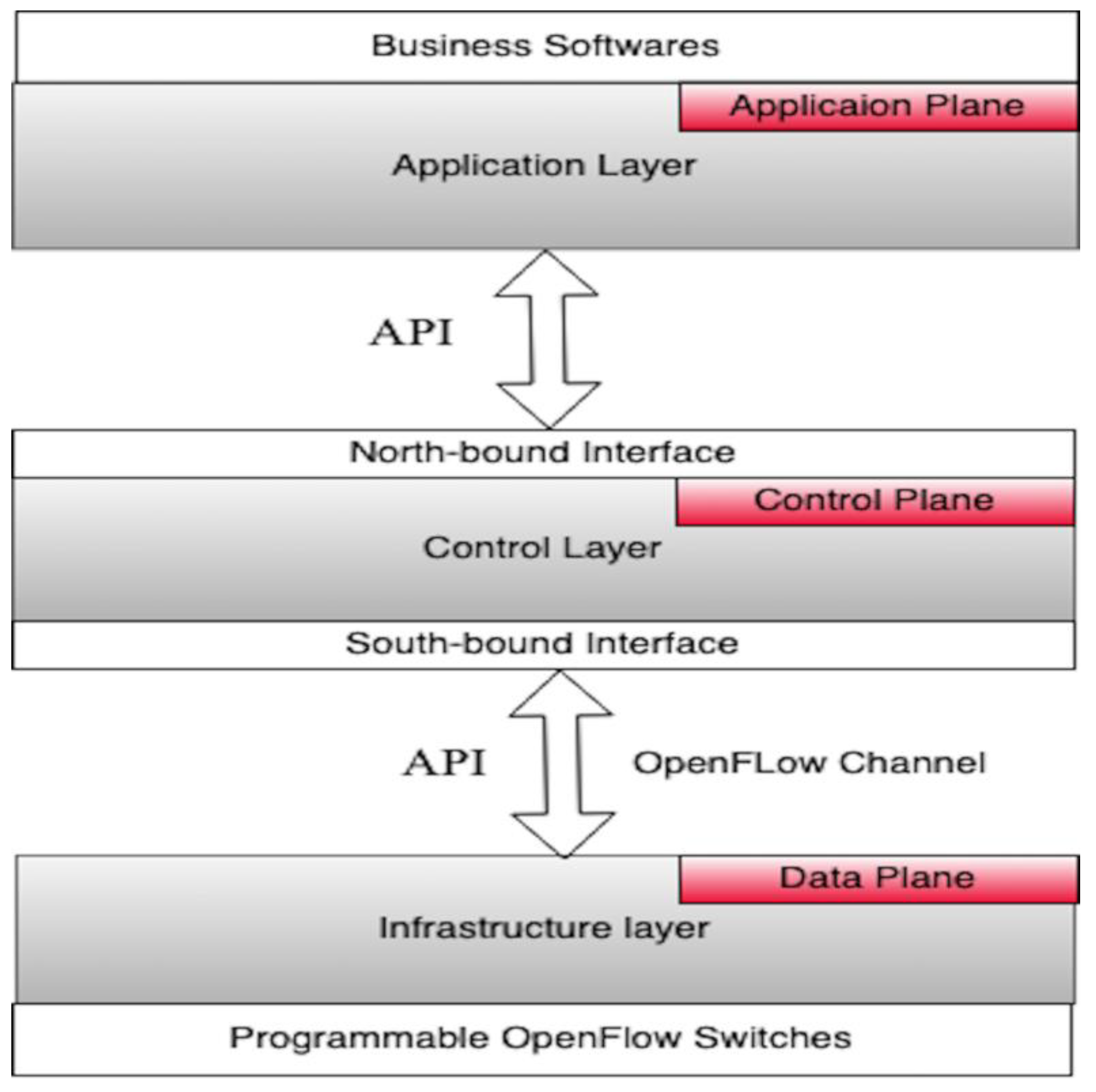
2. Software-Defined Networks (SDN)
2.1. OpenFlow Protocol
2.1.1. Data Plane
2.1.2. Control Plane
2.2. SDN Security Features
2.2.1. To achieve resilience of the SDN infrastructure to several attacks
- (1)
- Centralising the monitoring of malformed flow: The controller manages the network's data. Hence, the controller is able to observe all the suspicious activity throughout the network [12].
- (2)
- Programmable configuration: An essential advantage covered by SDN is the programmable features. When any malicious behaviour in the network is detected, the new configuration of a program acts instantaneously to deal with the identified anomalies [11].
2.2.2. Features that make the SDN environment vulnerable to various attacks
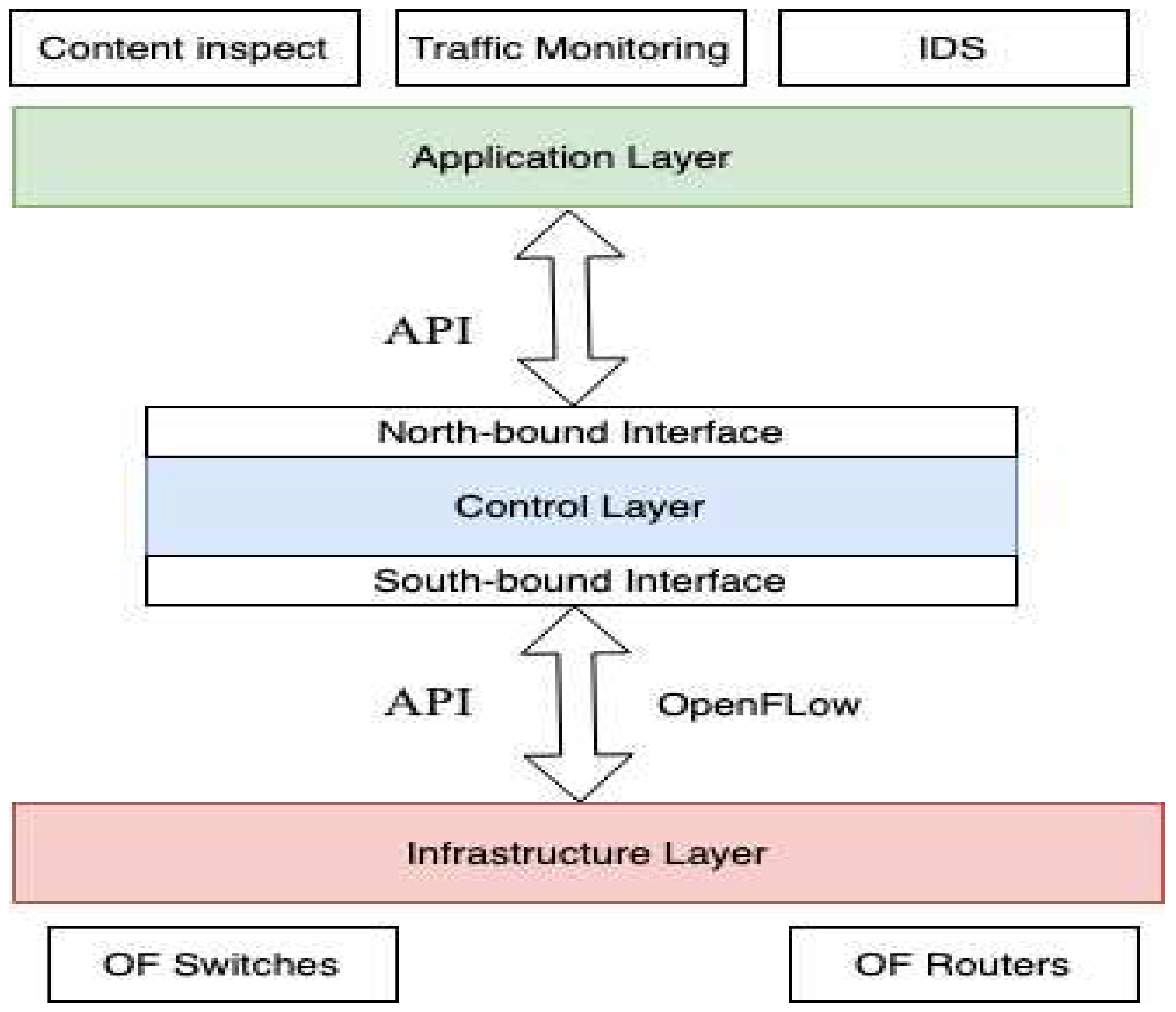
3. Intrusion Detection Systems (IDS) in SDN
3.1. IDS Overview
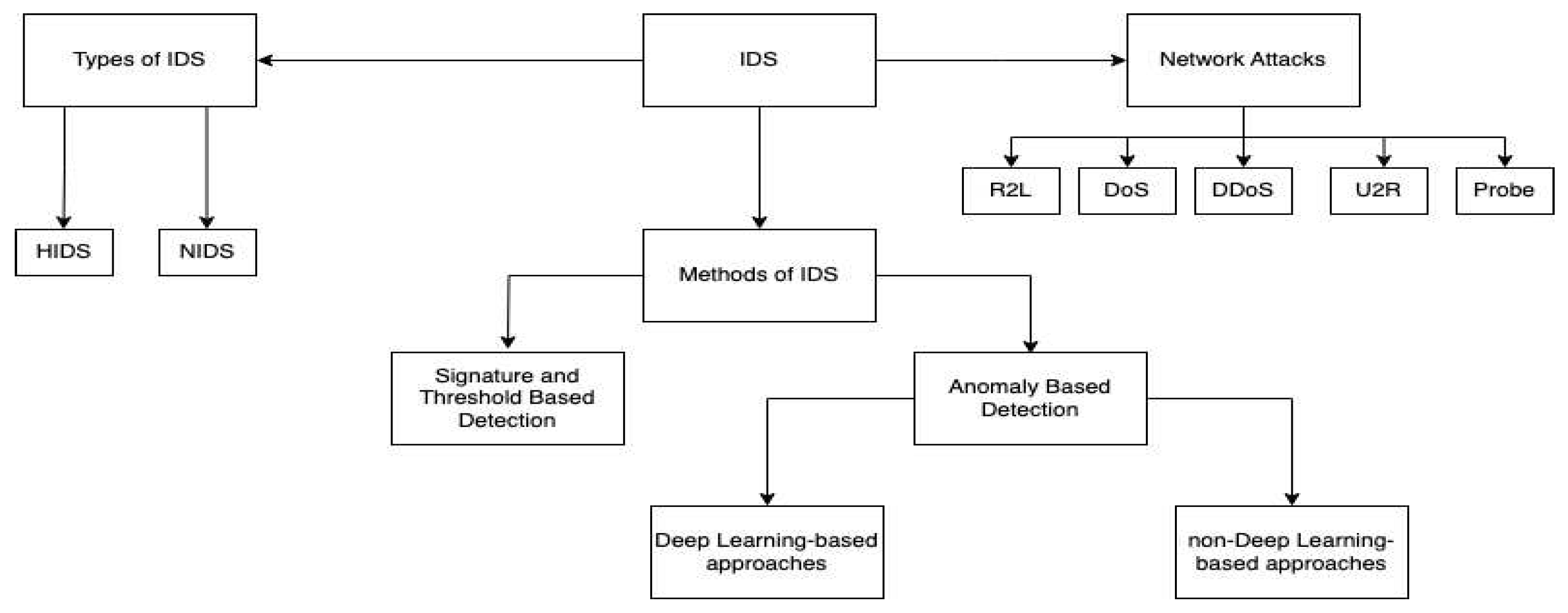
3.2. Type of IDS
- Host-based Intrusion Detection System: The IDS must be installed on a computer or personal device like a mobile or tablet. It is an important application that examines all the activities on the device. It detects and prevents attacks if there are intruders [15].
- Network-based Intrusion Detection System: This system observes the traffic to detect malignant activities by checking the traffic behaviour at various stages throughout the entire network and raises the alarm when an anomaly is identified [15].
4. Attacks in SDN
4.1. Network Attacks Overview
4.2. Specific Attacks:
4.3. Effects of Attacks on the SDN Environment
4.4. Vulnerable Points in the SDN Environment
5. Methods of Intrusion Detection System in SDN
5.1. Signature and Threshold Detection Method
5.2. Anomaly - Based Detection
| Aspect | non-DL Approaches within IDS in SDNs | Deep Learning (DL) Approaches within IDS in SDNs |
|---|---|---|
| Pros | - Interpretability and Explainability: Non-DL models offer explicit rules, aiding in understanding decision-making [24]. - Efficiency with Moderate-Sized Datasets: Techniques like SVMs perform well without excessive computational demands [22]. - Adaptive Learning: non-DL models can adapt to changing behaviours effectively [17]. - Availability of Off-the-Shelf Algorithms: A wide range of established non-DL algorithms are available. |
- Complex Feature Extraction: DL architectures excel in extracting intricate features from raw data [24]. - Superior Accuracy in Complex Scenarios: DL models often achieve higher accuracy [23].- Adaptability to Diverse Data Structures: DL methods can process diverse data formats without explicit feature engineering [19]. - Potential for Real-Time Decision-Making: Optimised DL architectures enable rapid decisions [11]. |
| Cons | - Struggles with Complex Data Patterns: Traditional non-DL methods might struggle to discern intricate attack patterns. - Limited Scalability: Some non-DL models face challenges in handling large-scale SDNs effectively [9]. - Dependency on Feature Engineering: Some non-DL techniques require manual feature engineering [11]. |
- High Computational Demands: DL models require substantial computational resources [4]. - Black-Box Nature and Interpretability: DL architectures often result in opaque models [8]. - Data Dependency and Overfitting Risks: DL models are highly data-dependent and prone to overfitting [11]. |
- The KDD'99 is a widely used data set for the evaluation of anomaly detection methods. Some pitfalls and problems of KDD'99 led to the creation of the NSL-KDD, which is a refined version of the KDD'99 dataset.
- CICIDS2017: Another dataset from the Canadian Institute for Cybersecurity, this dataset is much newer and includes modern attack behaviours. It is highly regarded for having a balance of multiple types of network intrusions and normal behaviours which allows for a comprehensive evaluation of IDS.
- ISCX2012: Created by the Information Security Centre of Excellence (ISCX), this dataset is recognized for its extensive coverage of both normal and attack traffic.
- Kyoto: The Kyoto University’s Honeypot datasets are some of the most comprehensive ones for IDS as well. These datasets include a wide variety of attacks, including fewer common ones, making them quite useful for intrusion detection research.
- CSE-CIC-IDS2018: This dataset is another product of the Canadian Institute for Cybersecurity, and it is one of the most recent and comprehensive datasets for developing and training IDS. It contains a wide array of updated attacks which provide researchers with a current 'snapshot' of internet traffic to assist in IDS development and training.
| Dataset | Year | No. of Features | Notable Attack types | Method of Data Collection |
|---|---|---|---|---|
| KDD'99 | 1999 | 41 | U2R, R2L, DoS, Probe | Simulated network traffic |
| NSL-KDD | 2009 | 41 | U2R, R2L, DoS, Probe | Improved version of KDD'99 with unnecessary duplicates removed |
| CICIDS2017 | 2017 | 80 | Brute Force, DoS, Heartbleed, Web Attack, Infiltration, Botnet | Real network traffic |
| ISCX2012 | 2012 | 283 | HTTP, DoS, scanning, infiltration | Simulated network traffic |
| Kyoto | 2006 | Depends on varied releases | Wide array, including less common and recent attacks | Honeypots and real network traffic |
| CSE-CIC-IDS2018 | 2018 | 78-85 depending on the scenario | Brute Force, DoS, Heartbleed, Infiltration, Web Attacks | Real network traffic |
| Ref and authors | Approach | Number of Features | Detected Attack | Controller | Dataset | Accuracy/False Alarm |
|---|---|---|---|---|---|---|
| [39] | SVM | 6 | DDoS | SDN controller | Simulation datasets | Detection Rate of 95.24% and False Alarm of 1.26% |
| [40] | ASVM | 5 | DDoS | POX controller | Simulation datasets | Accuracy 97% |
| [43] | SVM | 29 | DoS | OpenDaylight | KDD99 dataset | Accuracy of 97.63% |
| [44] | SMO, Naive Bayes, and J48 | 41 | DDoS | SDN controller | NSL dataset | Accuracy of 99.4% for SMO |
| [36] | The analysed algorithms were SVM, Naïve Bayes, KNN, ASVM, HMM, K-means, Random Forest, Decision tables, K-medoids, and fuzzy | 5 | DDoS | POX controller | NSL-KDD dataset | The highest accuracy is 81.5% for the J48 algorithm |
| [45] | Graph Theory | Statistics Flow | DoS | POX controller | CAIDA dataset | The precision of 0.84, Recall of 0.78, and F-score of 0.81 |
| [46] | C4.5 | 52 | DoS and Prob attacks | SDN controller | 1999 Darpa dataset | The precision of 0.989 and recall of 0.964 |
| [47] | SOM | 4 | DDoS | NOX controller | 1999 Darpa dataset | Detection Rate of 98.61% and False Alarm of 0.59% |
| [48] | SVM algorithm with a kernel function | 8 | IPsweep, Probe, and DDoS | SDN controller | 1998 DARPA and 2000 DARPA | Accuracy Rate of 94.81% and False Alarm of 0.11% |
| [49] | J48-tree | 41 | known and unknown attacks | NetFPGA10G | KDD'99 | Detection Rate of 91.81% and False Alarm of 0.55% |
| [51] | Naive Bayes, KNN, K-means and K-mediods | 52 | DDoS | POX controller | privet dataset | Detection Rates of 94%, 90%, 86% and 88% |
| [24] | NN | 6 | DOS, U2R, R2L, and Probes | SDN controller | NSL-KDD | Detection Rate of 97.4% |
| [52] | KNN | 23 | DoS | SDN controller | NSL-KDD | Accuracy Rate of 91.27% and 0.99% of precision |
| [53] | Random Forest | 5 | DOS | NOX controller | Specific dataset | Detection Rate of 90% and False Alarm of 70% |
| [54] | TRW-CB and Rate Limiting | 4 | DoS, Probe, DDoS, U2R, and R2L | NOX controller | KDD Cup 1999 dataset | Accuracy Rate of 96.3% |
| [55] | K-means++, AdaBoost, and Random Forest (RF) | 6 | DDoS, DoS, U2R, and R2L | SDN controller | KDD Cup 1999 dataset | Accuracy Rate of 84% |
| [56] | J48 algorithm | 41 | DoS, Probe, U2R, and R2L | SDN controller | NSL-KDD | Detection Rate of 90.9% for DoS |
| [57] | Bernoulli random | 2 | DDoS | SDN controller | DARP 1999 dataset | None |
| [58] | Idle-timeout Adjustment (IA) & SVM | The six Basic features | DDoS | OpenFlow controller | CAIDA | None |
5.2.3. Deep Learning-based Approaches
| Ref & Author | Approach | Features | Attack Detected | Controller | Dataset | Limitations | Accuracy/False Alarm |
|---|---|---|---|---|---|---|---|
| [60] | Relu and Softmax function | 5 | DDoS and DoS | ONOS | CICIDS2017 | Must reduce the bottleneck controller and low number of used features | 99.6 |
| [62] | Deep NN | 6 | DoS | OpenFlow Controller | KDD | The accuracy must be increased. Must reduce the bottleneck controller | 75.75% |
| [61] | SAE | TCP, UDP features | DDoS | POX | Traffic Dataset | Must reduce the bottleneck controller | 95.65% |
| [63] | Recurrent Neural Network. | 6 | DoS | POX | NSL-KDD | Model optimisation is required in feature selection and extraction | 89% |
| [65] | GRU-LSTM DNN | 52 | Prop, U2R, R2L and DoS | POX | NSL-KDD | Model optimisation required | 87% |
| [64] | CNN | 48 and 9 | Prop, U2R, R2L, DoS, etc. | OpenFlow | InSDN | Model optimisation required | 98.92% |
6. Evaluation Metrics
- False Positive (K): This alarm occurs when regular traffic is wrongly classified as attack traffic.
- False Negative (S): This alarm occurs when attack traffic is wrongly classified as regular traffic.
- True Positive (N): This occurs when attack traffic is classified correctly as attack traffic.
- True Negative (P): This occurs when normal traffic is classified accurately as regular traffic.
7. Testing and Implementation Tools
- Wireshark: Wireshark is a software network protocol analyser commonly used in network analysis, troubleshooting, and collecting packets and flows from connected devices [75]. Wireshark is an open-source packet sniffer tool. It authorises administrators and researchers to catch and analyse network traffic in real-time. This software's advanced abilities and comprehensive characteristics make it a useful tool in academic and professional settings. It is available online on [76].
| Tool | Description | Link |
|---|---|---|
| Mininet Emulator | Mininet is an open-source network emulator that enables the design of virtual SDN networks. It's useful for assessing IDS performance under managed conditions. | [14] |
| Scapy | Scapy is a packet generation tool that helps develop customised packets to simulate network traffic, aiding in testing IDS in SDN networks. | [16] |
| Open vSwitch (OVS) | OvS is an open-source virtual switch that simulates components of SDN architectures. It's handy for designing custom IDS modules. | [18] |
| Snort | Snort is a popular open-source IDS that can be integrated with SDN networks to provide various detection policies and abilities. | [20] |
| Bro/Zeek | Zeek (formerly known as Bro) is a robust network security monitoring framework for SDN networks that offers real-time traffic analysis facilities. | [22] |
| Slowloris | Slowloris is an open-source tool developed using Python, known for its implementation in HTTP DoS/DDoS attacks, which can stress a server's thread pool. | [23] |
| Wireshark | Wireshark is an open-source network protocol analyser used for network analysis, troubleshooting, and collecting packets from connected devices. | [25] |
8. The Findings and Research Gaps
8.1. An effective way to process network traffic
8.2. Distribute the processing stages over OpenFlow devices
8.3. Detect Slow DDoS/DoS Attack
8.4. Employing outdated datasets for training and testing the proposed models
8.5. Getting high accuracy with limited raw features by using DL/non-DL approaches
8.6. Test the proposed models with the real network environments
8.7. The scalability of using more than one controller
9. Conclusion
Data Statement
References
- Palanikumar, R.; Ramasamy, K. Software defined network based self-diagnosing faulty node detection scheme for surveillance applications. Computer Communications 2020, 152, 333–337. [Google Scholar] [CrossRef]
- Yuki, G.; Bryan, N.; Seah, W.K.; Takahashi, Y. Queueing analysis of software defined network with realistic OpenFlow–based switch model. Computer Networks 2019, 164. [Google Scholar]
- Herrera, J.A.; Camargo, J.E. A survey on machine learning applications for software defined network security. in In International Conference on Applied Cryptography and Network Security, Cham, 2019.
- Arash, S.; Kaafar, M.A.; Buyya, R.; Jha, S. Software-defined network (SDN) data plane security: issues, solutions, and future directions. Handbook of Computer Networks and Cyber Security 2020, 341–387. [Google Scholar]
- Shaghaghi, A.; Kanhere, S.S.; Kaafar, M.A.; Jha, S. Gwardar: Towards protecting a software-defined network from malicious network operating systems. in In 2018 IEEE 17th International Symposium on Network Computing and Applications (NCA), 2018.
- Neghabi, A.A.; Navimipour, N.J.; Hosseinzadeh, M.; Rezaee, A. Nature-inspired meta-heuristic algorithms for solving the load balancing problem in the software-defined network. International Journal of Communication Systems 2019, 32, e3875. [Google Scholar] [CrossRef]
- Hauser, F.; Häberle, M.; Merling, D.; Lindner, S.; Gurevich, V.; Zeiger, F.; Frank, R.; Menth, M. A survey on data plane programming with p4: Fundamentals, advances, and applied research. Journal of Network and Computer Applications 2023, 212, 103561. [Google Scholar] [CrossRef]
- Bhowmik, C.D.; Gayen, T. Traffic aware dynamic load distribution in the Data Plane of SDN using Genetic Algorithm: A case study on NSF network. Pervasive and Mobile Computing 2022, 88, 101723. [Google Scholar] [CrossRef]
- Bhuiyan, Z.A.; Islam, S.; Islam, M.M.; Ullah, A.A.; Naz, F.; Rahman, M.S. On the (in) Security of the Control Plane of SDN Architecture: A Survey. IEEE Access 2023, 11. [Google Scholar] [CrossRef]
- Sarmiento, D.E.; Lebre, A.; Nussbaum, L.; Chari, A. Decentralized SDN control plane for a distributed cloud-edge infrastructure: A survey. IEEE Communications Surveys & Tutorials 2021, 23, 256–281. [Google Scholar]
- Pradhan, M.; Nayak, C.K.; Pradhan, S.K. Intrusion detection system (IDS) and their types. Securing the Internet of Things: Concepts, Methodologies, Tools, and Applications - IGI Global 2020, 481–497. [Google Scholar]
- Swami, R.; Dave, M.; Ranga, V. Software-defined networking-based ddos defense mechanisms. ACM Computing Surveys (CSUR) 2019, 52, 1–36. [Google Scholar] [CrossRef]
- Hanselmann, M.; Strauss, T.; Dormann, K.; Ulmer, H. CANet: An unsupervised intrusion detection system for high dimensional CAN bus data. IEEE Access 2020, 8, 58194–58205. [Google Scholar] [CrossRef]
- Santhana, K.R.; Golden, J.E.; Harold, R.Y.; Kumar, R.; Son, L.H.; Tuan, T.A.; Long, H.V. Modified zone based intrusion detection system for security enhancement in mobile ad hoc networks. Wireless Networks 2020, 26, 1275–1289. [Google Scholar]
- Weizhi, M.; Tischhauser, E.W.; Wang, Q.; Wang, Y.; Han, J. When intrusion detection meets blockchain technology: a review. IEEE Access 2018, 6, 10179–10188. [Google Scholar]
- Ali, T.E.; Chong, Y.-W.; Manickam, S. Machine Learning Techniques to Detect a DDoS Attack in SDN: A Systematic Review. Applied Sciences 2023, 13, 3183. [Google Scholar] [CrossRef]
- Karnani, S.; Agrawal, N.; Kumar, R. A comprehensive survey on low-rate and high-rate DDoS defense approaches in SDN: taxonomy, research challenges, and opportunities. Multimedia Tools and Applications 2023, 1–54. [Google Scholar] [CrossRef]
- Ahmad, I.; Namal, S.; Ylianttila, M.; Gurtov, A. Security in software defined networks: A survey. IEEE Communications Surveys & Tutorials 2015, 17, 2317–2346. [Google Scholar]
- Lent, D.M.B.; Novaes, M.P.; Carvalho, L.F.; Lloret, J.; Rodrigues, J.J.; Proença, M.L. A gated recurrent unit deep learning model to detect and mitigate distributed denial of service and portscan attacks. IEEE Access 2022, 10, 73229–73242. [Google Scholar] [CrossRef]
- Alotaibi, F.M.; Vassilakis, V.G. Toward an SDN-Based Web Application Firewall: Defending against SQL Injection Attacks. Future Internet 2023, 15, 170. [Google Scholar] [CrossRef]
- He, D.; Dai, J.; Liu, X.; Zhu, S.; Chan, S.; Guizani, M. Adversarial Attacks for Intrusion Detection Based on Bus Traffic. IEEE Network 2022, 36, 203–209. [Google Scholar] [CrossRef]
- Lin, H.T.; Wang, P.C. TCAM-based packet classification for many-field rules of SDNs. Computer Communications 2023, 203, 89–98. [Google Scholar] [CrossRef]
- Santos, R.; Souza, D.; Santo, W.; Ribeiro, A.; Moreno, E. Machine learning algorithms to detect DDoS attacks in SDN. Concurrency and Computation: Practice and Experience 2020, 32, 16. [Google Scholar] [CrossRef]
- Abubakar, A.; Pranggono, B. Machine learning based intrusion detection system for software defined networks. in In 2017 seventh international conference on emerging security technologies (EST), 2017.
- Awad, M.; Khanna, R. Support vector machines for classification- Efficient Learning Machines. Springer 2015, 39–66. [Google Scholar]
- Divya, T.; Agarwal, S. A survey on Data Mining approaches for Healthcare. International Journal of Bio-Science and Bio-Technology 2013, 5, 241–266. [Google Scholar]
- Xindong, W.; Kumar, V.; Quinlan, J.R.; Ghosh, J.; Yang, Q.; Motoda, H.; McLachlan, G.J. op 10 algorithms in data mining. Knowledge and information systems 2008, 14, 1–37. [Google Scholar]
- Javed, A.; Seemab, L. Handling intrusion and DDoS attacks in Software Defined Networks using machine learning techniques. in In 2014 National Software Engineering Conference, 2014.
- Irina, R. An empirical study of the naive Bayes classifier. in In IJCAI 2001 workshop on empirical methods in artificial intelligence, 2001.
- Jadhav, S.D.; Channe, H.P. Comparative study of K-NN, naive Bayes and decision tree classification techniques. International Journal of Science and Research (IJSR) 2016, 5, 1842–1845. [Google Scholar]
- Ting, S.L.; Ip, W.H.; Tsang, A.H. Is Naive Bayes a good classifier for document classification. nternational Journal of Software Engineering and Its Applications 2011, 5, 37–46. [Google Scholar]
- Pal, M. Random forest classifier for remote sensing classification. International journal of remote sensing 2005, 26, 217–222. [Google Scholar] [CrossRef]
- Kim, J.; Kim, J.; Kim, H.; Shim, M.; Choi, E. CNN-based network intrusion detection against denial-of-service attacks. Electronics 2020, 9, 916. [Google Scholar] [CrossRef]
- Hershey, S.; Chaudhuri, S.; Ellis, D.P.; Gemmeke, J.F.; Jansen, A.; Moore, R.C.; Plakal, M. CNN architectures for large-scale audio classification. in In 2017 ieee international conference on acoustics, speech and signal processing (icassp), 201.
- Jin, X.-B.; Yang, N.-X.; Wang, X.-Y.; Bai, Y.-T.; Su, T.-L.; Kong, J.-L. Hybrid deep learning predictor for smart agriculture sensing based on empirical mode decomposition and gated recurrent unit group model. Sensors 2020, 20, 1334. [Google Scholar] [CrossRef]
- Elsayed, M.S.; Le-Khac, N.-A.; Dev, S.; Jurcut, A.D. Machine-learning techniques for detecting attacks in SDN. in 2019 IEEE 7th International Conference on Computer Science and Network Technology (ICCSNT), Dalian, China, 2019.
- Elsayed, M.S.; Le-Khac, N.-A.; Jurcut, A.D. InSDN: A Novel SDN Intrusion Dataset. IEEE Access 2020, 8, 165263–165284. [Google Scholar] [CrossRef]
- Li, D.; Yu, C.; Zhou, Q.; Yu, J. Using SVM to Detect DDoS Attack in SDN Network. in In IOP Conference Series: Materials Science and Engineering, 2018.
- Jin, Y.; Cheng, X.; Jian, Z.; Feng, L.; Ling, S. A DDoS attack detection method based on SVM in software defined network. Security and Communication Networks 2018. [Google Scholar]
- Oo, M.M.; Kamolphiwong, S.; Kamolphiwong, T.; Vasupongayya, S. Advanced Support Vector Machine-(ASVM-) Based Detection for Distributed Denial of Service (DDoS) Attack on Software Defined Networking (SDN). Journal of Computer Networks and Communications, 2019. [Google Scholar]
- Silva, D.; Santos, A.; Wickboldt, J.A.; Granville, L.Z.; Schaeffer-Filho, A. ATLANTIC: A framework for anomaly traffic detection, classification, and mitigation in SDN. in In NOMS 2016-2016 IEEE/IFIP Network Operations and Management Symposium, 2016.
- Song, A.; Younghee, P.; Keyur, G.; Youngsoo, K.; Kalgi, B.; Kunal, G. Machine-learning based threat-aware system in software defined networks. in In 2017 26th international conference on computer communication and networks (ICCCN), 2017.
- Wang, P.; Chao, K.-M.; Lin, H.-C.; Lin, W.-H.; Lo, C.-C. An efficient flow control approach for SDN-based network threat detection and migration using support vector machine. in In 2016 IEEE 13th International Conference on e-Business Engineering (ICEBE), 2016.
- Alshamrani, A.; Chowdhary, A.; Pisharody, S.; Lu, D.; Huang, D. A defense system for defeating DDoS attacks in SDN based networks. in In Proceedings of the 15th ACM International Symposium on Mobility Management and Wireless Access, 2017. [Google Scholar]
- AlEroud, A.; Alsmadi, I. Identifying cyber-attacks on software defined networks: An inference-based intrusion detection approach. Journal of Network and Computer Applications, 2017; 80, 152–152. [Google Scholar]
- L., A; Dinh, P.; Le, H.; Cuong, T.N. Flexible network-based intrusion detection and prevention system on software-defined networks. in In 2015 International Conference on Advanced Computing and Applications (ACOMP), 2015.
- Braga, R.; Mota, E.; Passito, A. Lightweight DDoS flooding attack detection using NOX/OpenFlow. in In IEEE Local Computer Network Conference, 2010.
- K. RT, S. T. DDoS detection and analysis in SDN-based environment using support vector machine classifier. in In 2014 Sixth International Conference on Advanced Computing (ICoAC), 2014.
- Van, N.T.; Bao, H.; Thinh, T.N. An anomaly-based intrusion detection architecture integrated on openflow switch. in In Proceedings of the 6th International Conference on Communication and Network Security, 2016.
- Jankowski, A.; Amanowicz, M. On efficiency of selected machine learning algorithms for intrusion detection in software defined networks. International Journal of Electronics and Telecommunications 2016, 62, 247–252. [Google Scholar] [CrossRef]
- Barki, L.; Shidling, A.; Meti, N.; Narayan, D.G.; Mulla, M.M. Detection of distributed denial of service attacks in software defined networks. in In 2016 International Conference on Advances in Computing, Communications and Informatics (ICACCI), 2016.
- Majd, L.; Toker, L. Minimizing false positive rate for DoS attack detection: A hybrid SDN-based approach. CT Express 2020, 6, 125–127. [Google Scholar]
- Jiaqi, L.; Zhifeng, Z.; Li, R.; Zhang, H. Ai-based two-stage intrusion detection for software defined iot networks. IEEE Internet of Things Journal 2018, 6, 2093–2102. [Google Scholar]
- Akbar, M.S.; Khalid, J.; Khayam, S.A. Revisiting traffic anomaly detection using software defined networking.. in In International workshop on recent advances in intrusion detection, Berlin, Heidelberg, 2011.
- Jiaqi, L.; Zhao, Z.; Li, R. Machine learning-based IDS for software-defined 5G network. ET Networks 2017, 7, 53–60. [Google Scholar]
- Sathya, R.; Thangarajan, R. Efficient anomaly detection and mitigation in software defined networking environment. in In 2015 2nd international conference on electronics and communication systems (ICECS), 2015.
- Dong, P.; Du, X.; Zhang, H.; Xu, T. A detection method for a novel DDoS attack against SDN controllers by vast new low-traffic flows. in In 2016 IEEE International Conference on Communications (ICC), 2016.
- Phan, T.V.; Toan, T.V.; Tuyen, D.V.; Huong, T.T.; Thanh, N.H. Openflowsia: An optimized protection scheme for software-defined networks from flooding attacks. in In 2016 IEEE Sixth International Conference on Communications and Electronics (ICCE), 2016.
- Scott-Hayward, S.; Natarajan, S.; Sezer, S. A survey of security in software defined networks. IEEE Communications Surveys & Tutorials 2015, 18, 623–654. [Google Scholar]
- Boukria, S.; Guerroumi, M. Intrusion detection system for SDN network using deep learning approach. in In 2019 International Conference on Theoretical and Applicative Aspects of Computer Science (ICTAACS), 2019.
- Niyaz, Q.; Sun, W.; Javaid, A.Y. A Deep Learning Based DDoS Detection System in Software-Defined Networking (SDN). Cornell University, vol. arXiv 2016." arXiv preprint arXiv:1611.07400, 2016.
- Tang, T.A.; Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Ghogho, M. Deep learning approach for network intrusion detection in software defined networking. in In 2016 international conference on wireless networks and mobile communications (WINCOM), 2016.
- Tang, T.A.; Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Ghogho, M. Deep recurrent neural network for intrusion detection in sdn-based networks. in In 2018 4th IEEE Conference on Network Softwarization and Workshops (NetSoft), 2018.
- ElSayed, M.S.; Le-Khac, N.-A.; Albahar, M.A.; Jurcut, A. A novel hybrid model for intrusion detection systems in SDNs based on CNN and a new regularization technique. Journal of Network and Computer Applications 2021, 191. [Google Scholar] [CrossRef]
- Dey, S.K.; Rahman, M.M. Flow based anomaly detection in software defined networking: A deep learning approach with feature selection method. in In 2018 4th International Conference on Electrical Engineering and Information & Communication Technology (iCEEiCTP), 2018.
- Hande, Y.; Muddana, A. Intrusion Detection System Using Deep Learning for Software Defined Networks (SDN). in In 2019 International Conference on Smart Systems and Inventive Technology (ICSSIT), 2019.
- Scapy. Scapy. 2023. [Online]. Available: https://scapy.net/. [Accessed 21 07 2019].
- Ma, H.; Luo, X.; Xu, D. Intelligent queue management of open vSwitch in multi-tenant data center. Future Generation Computer Systems 2023, 144, 50–62. [Google Scholar] [CrossRef]
- vSwitch. Open vSwitch. 2023. [Online]. Available: https://www.openvswitch.org/download/. [Accessed 20 12 2021].
- Alsharabi, N.; Alqunun, M.; Murshed, B.A.H. Detecting Unusual Activities in Local Network Using Snort and Wireshark Tools. Journal of Advances in Information Technology 2023, 14. [Google Scholar] [CrossRef]
- Snort. Snort. 2023. [Online]. Available: https://www.snort.org/downloads. [Accessed 12 06 2021].
- Tiwari, A.; Saraswat, S.; Dixit, U.; Pandey, S. Refinements In Zeek Intrusion Detection System. in 8th International Conference on Advanced Computing and Communication Systems (ICACCS), 2022.
- Zeek. Zeek. 2023. [Online]. Available: https://docs.zeek.org/en/master/install.html. [Accessed 14 September 2023].
- Yaltirakli, G. Github. 2015. [Online]. Available: https://github.com/gkbrk/slowloris. [Accessed 12 08 2022].
- Jawaharan, R.; Mohan, P.M.; Das, T.; Gurusamy, M. Empirical evaluation of sdn controllers using mininet/wireshark and comparison with cbench. in 27th international conference on computer communication and networks (ICCCN), 201.
- Wireshark. Wireshark. 2022. [Online]. Available: https://www.wireshark.org/. [Accessed 12 July 2022].
- Kumar, G.; Alqahtani, H. Machine Learning Techniques for Intrusion Detection Systems in SDN-Recent Advances, Challenges and Future Directions. CMES-Computer Modeling in Engineering & Sciences 2023, 134. [Google Scholar]
| # | Methods Signature - Based | Methods Anomaly - Based |
|---|---|---|
| 1 | Implementation is easy | Difficult to implement |
| 2 | Reliable | Less Reliable |
| 3 | Speed is high | Speed is low. |
| 4 | Less Robust | More Robust |
| 5 | Low rate of Alarm | A high rate of Alarm |
| 6 | Low scalability | High Scalability |
| Algorithms | Type | Advantages | Disadvantages |
| SVM | non-DL |
|
|
| DT | non-DL | ||
| NB | non-DL |
|
|
| RF | non-DL |
|
|
| K-NN | non-DL | ||
| LR | non-DL |
|
|
| LogR | non-DL | ||
| ANN | DL | ||
| CNN | DL |
|
|
| GRU | DL |
| The Event | Abnormal | Normal |
| Abnormal | True Positive (N) | False Negative(S) |
| Normal | False Positive(K) | True Negative(P) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





