Submitted:
12 December 2023
Posted:
14 December 2023
You are already at the latest version
Abstract
Keywords:
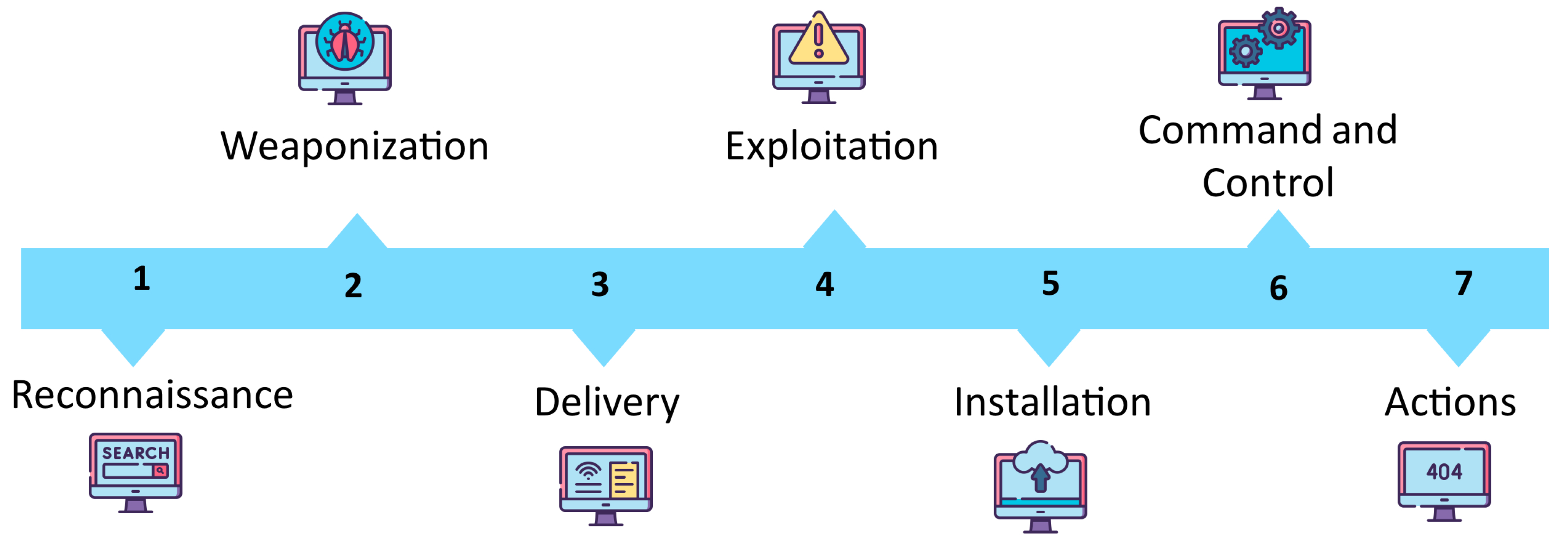
1. Introduction
- What are the different types of malware?
- What are the types of malware sandboxing techniques?
- What are the challenges and limitations in malware detection?
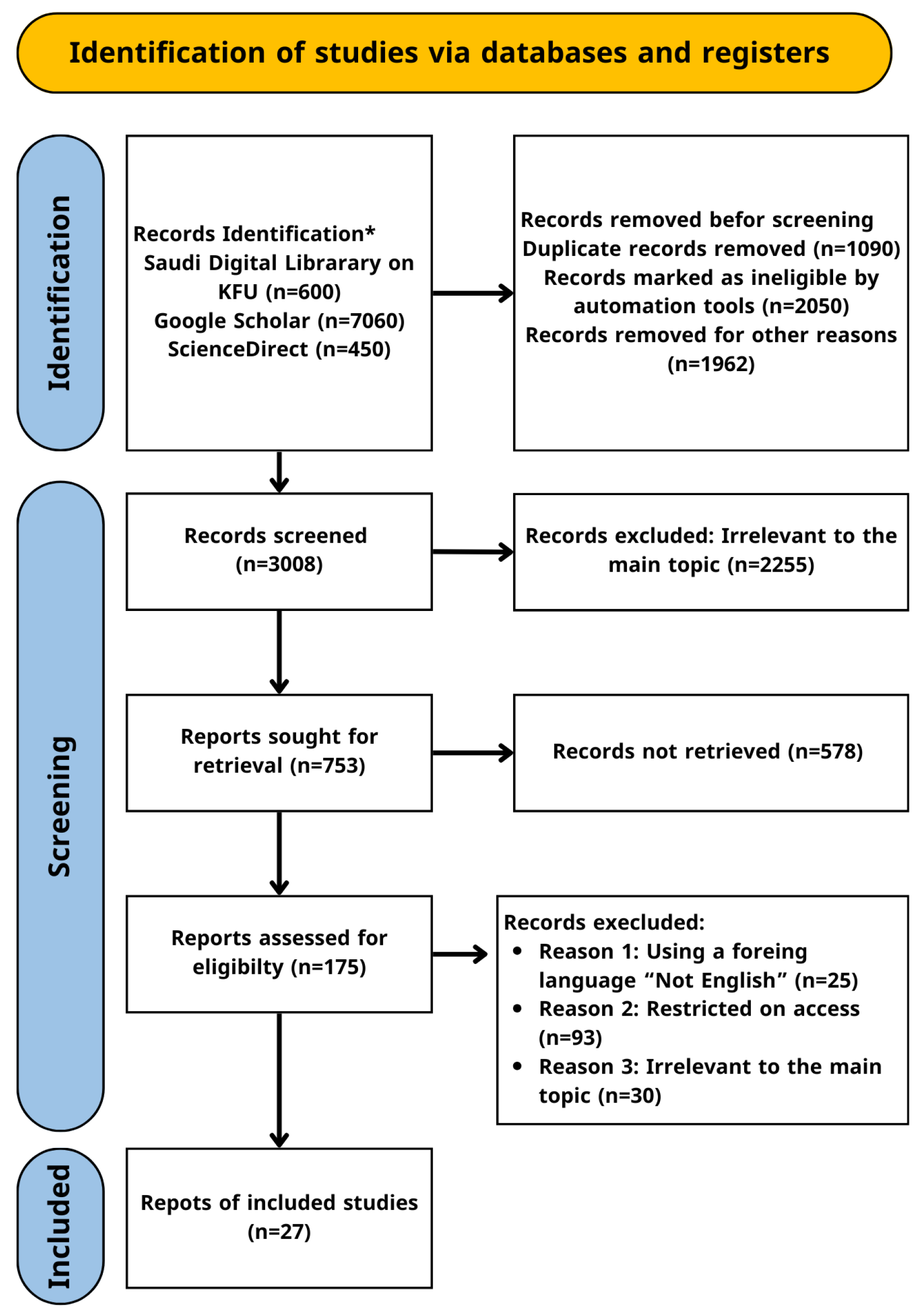
2. Research Methodology
3. Malware Sandbox Overview
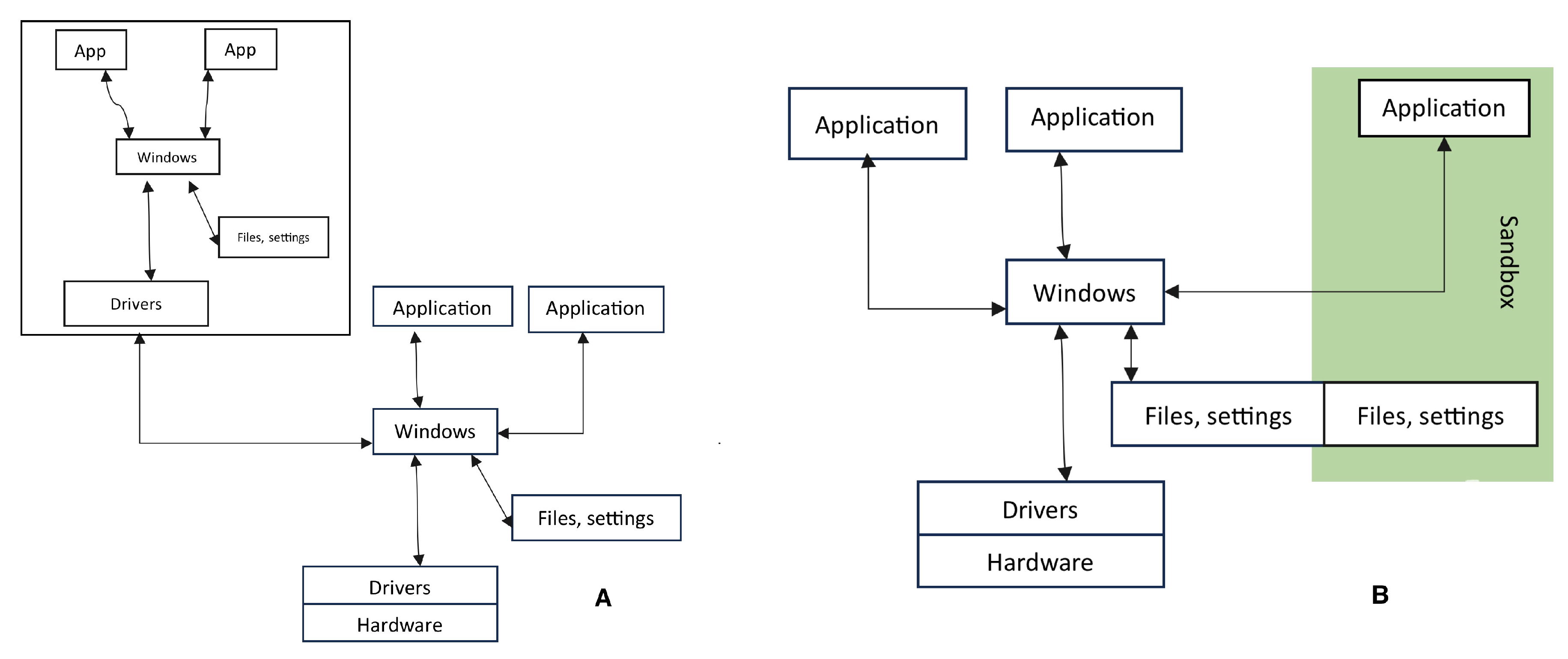
3.1. VirtualBox and Sandbox
3.2. Techniques for Analyzing Malware
- Static Analysis: Static analysis entails scrutinizing the structure and code of malware without executing it, providing vital insights into its potential impact. Standard static analysis methods include: Disassembling: Translation of malware’s binary code into assembly language for understanding its functionality. Decompiling: Reverse engineering compiled code into a high-level programming language to unveil the malware’s purpose. Debugging: Analysis of code in a debugging environment to pinpoint vulnerabilities and potential attack vectors.
- Dynamic Analysis: Dynamic malware analysis observes malware behavior in a controlled environment like a virtual machine. Executing the malware in isolation allows monitoring its activity, understanding its capabilities, and assessing potential impacts. This technique helps identify functions like spreading mechanisms.
- Hybrid Analysis: Hybrid analysis integrates the strengths of both static and dynamic approaches. It begins with static analysis, extracting information such as embedded files and code obfuscation. Subsequently, dynamic analysis in a controlled environment, like a sandbox, helps observe the malware’s behavior and uncover malicious activities not evident during static analysis. These comprehensive malware analysis techniques see Figure 3, whether static, dynamic, or hybrid, are indispensable for cybersecurity professionals in comprehending, mitigating, and responding to ever-evolving cyber threats [8].
4. Related Work
| Type of Tool | Tool Name | Description |
|---|---|---|
| BinText | A mechanism for extracting binary data to text that outputs resource strings, Unicode, and ASCII text in simple plain text. | |
| TrID | uses binary signatures to identify file types without the need for set rules. | |
| Static [16] | Ultimate Packer for Executables (UPX) | The UCL data compression algorithm is used in this freeware and open-source executable packer. |
| XORSearch | An open-source program that uses brute force to look for strings encoded with XOR, ROL, ROT, or SHIFT in a file. | |
| Exeinfo PE | Verifies .exe files by giving the precise size and malware entry point information. | |
| FakeNet | creates the illusion of a phony network for malware operating in a virtual machine. | |
| Process Monitor (Procmon) | Windows Sysinternals Freeware monitors and displays real-time file system activity. | |
| ProcDOT | uses the GraphViz suite to create a graph by processing the log files from Procmon and PCAP. | |
| Dynamic [16] | Wireshark | examines various network protocols’ structural analysis to show how encapsulation works. |
| Process Explorer | Freeware system monitors and task managers offer Windows Task Manager’s functionality for gathering data about active processes. | |
| RegShot | Open-source registry Using a quick snapshot of the system registry, the compare utility compares the registry after the malware has been executed. |
| Type of Malware | Description | Propagation | Delivery | Targets | Notable Characteristics |
|---|---|---|---|---|---|
| Virus | Self-replicating malware that spreads through infected files or scripts. | Email, downloads, websites. | Requires user interaction. | Files, applications, OS. | Destructive or data-stealing. |
| Worm | Self-propagating malware that spreads through network vulnerabilities. | Network transmissions, emails, websites. | Rapidly infects multiple systems. | Networked computers, servers. | No user interaction is required. |
| Trojan | Deceptive malware disguised as legitimate software. | Email, downloads, websites. | Deceives users for installation. | User systems, data. | Unauthorized access, data theft. |
| Ransomware | Encrypts files and demands payment for decryption. | Email, downloads, websites. | Monetarily motivated. | Individuals, businesses. | Highly disruptive. |
| Adware | Displays unwanted ads, collect user data. | Software bundles, downloads, websites. | Generates ad revenue. | User data for targeted ads. | Slows down systems. |
| Spyware | Spies on users, and captures sensitive data. | Downloads, websites, bundled with other malware. | Covert data ex-filtration. | Keystrokes, login credentials. | Data theft focus. |
| Rootkit | Hides presence, allows unauthorized access. | Often part of other malware. | Difficult to detect, maintains persistence. | Data theft, system control. | Backdoor access. |
5. Challenges and Limitations in Malware Detection
5.1. Evasive Malware Detection
5.2. Real-Time Malware Analysis of IoT Devices
5.3. Malware Detection and Analysis
5.4. Ransomware and IoT Malware Analysis
5.5. Machine Learning for Malware Detection
5.6. IoT Malware Evasion Techniques
5.7. Industrial Control Systems
5.8. Behavioral Analysis
| Challenges in Evasive Malware Detection | Limitations |
|---|---|
| Increasing Sophistication of Evasion Techniques | Difficulty in Distinguishing Legitimate vs. Malicious Evasion Techniques |
| Rapid Evolution of Malware | Detection and Recognition of Unknown Evasion Techniques |
| Adaptive and Dynamic Nature of Evasive Malware | Optimizing Execution Environments for Practical Implementation |
| Zero-Day Malware and Emerging Variants | Efficient Adaptability to Zero-Day Malware Through Learning Mechanisms, Including Resource and Time Constraints |
| Limited Availability of Comprehensive Datasets | Challenges in Prioritizing and Creating Comprehensive Evasive Behavior Datasets |
| High Resource and Time Complexity in Detection | Balancing Complexity in Multiple Execution Environments |
| Integration and Compatibility with Security Systems | Implementation Challenges in Adapting Detection Mechanisms to Existing Security Infrastructure |
6. Future Extension
- Evasive Behavior Dataset Creation: We suggest prioritising the creation of a comprehensive dataset representing evasive behaviours. This essential resource will significantly aid researchers in developing more robust solutions for evasive malware detection.
- Distinguishing Legitimate vs. Malicious Evasion Techniques: We suggest addressing the challenge of distinguishing between evasion techniques used in legitimate behaviour and those employed for malicious purposes. Developing methods for accurate classification is crucial for effective detection.
- Detection of Unknown Evasion Techniques: We suggest focusing on enhancing the capability of models to detect and recognize unknown evasion techniques. Overcoming this challenge is critical to staying ahead of evolving and sophisticated evasion tactics.
- Optimizing Execution Environments: We suggest tackling the challenge of using multiple execution environments in evasive malware detection without introducing high complexity regarding time and resources. Streamlining this process is essential for practical implementation.
- Zero-Day Malware Adaptability: We suggest developing and implementing efficient updating learning mechanisms to adaptively learn new behaviours, particularly in the context of zero-day malware and emerging variants. Deep learning and unsupervised machine learning can be crucial in this adaptation.
7. Conclusion
- Malware Sandbox: The name of the malware sandbox.
- Description: The description of the malware sandbox.
- Analysis Capabilities: If Assess the sandbox’s ability to analyze code without executing it or during execution.
- OS: The operating system the malware sandbox supports.
- Signature-Based: If the malware sandbox relies on signature-based detection.
- Detection Techniques: The techniques used to detect malware in the malware sandbox.
- Licensing Model: If the malware sandbox has an open-source or commercial license.
| Malware Sandbox | Description | Analysis Capabilities | OS | Signature Based | Detection Techniques | Licensing Model |
|---|---|---|---|---|---|---|
| Cuckoo Sandbox [1,18,25,30,34,46]. | A malicious code investigation tool that examines malware in detail and provides comprehensive results based on the series of tests made by it during the execution of the malicious code sample. | Dynamic and Static analysis. | Windows, Linux, and macOS. | NO | A combination of behavioural and static analysis techniques to detect malware. | Open-Source |
| Limon Sandbox [26]. | An open-source sandbox designed for dynamic malware analysis. It focuses on analyzing malware behaviour during runtime to understand its impact on a system. | Dynamic analysis | Linux | YES | A combination of heuristics and behavioural analysis techniques | Open-Source |
| Lisa Sandbox [26] | A powerful virtual environment that allows researchers, analysts, and security professionals to examine and analyze potentially harmful files safely. It provides a secure environment to execute and observe the behaviour of files without risking the host system’s integrity. | Dynamic and Static analysis. | Windows, Linux, and macOS | YES | A combination of behaviour-based analysis, signature-based detection, machine learning algorithms, heuristics, and anomaly detection. | Free versions with limited features and offer commercial licenses |
| Joe Sandbox [30,47]. | A fully automated malware analysis system that provides deep analysis and agile sandboxing capabilities. It supports all types of file formats, including Android apps, and generates reports in XML, JSON, HTML, PDF, etc. | Dynamic analysis. | Windows, Linux, and macOS | NO | A combination of behavioral and static analysis techniques | A commercial licenses |
| AnyRun Sandbox [30]. | A cloud-based sandboxing platform that allows users to analyze malware behaviour in real-time | Dynamic and Static analysis. | Windows, Linux, and macOS | YES | Behavioral analysis techniques | A commercial licenses |
| VMRay Analyzer [48,49]. | An agent-less dynamic behaviour analysis tool for malware. It is embedded in the hypervisor to monitor the behaviour of malware and overcome the problem in traditional sandboxes. | Static and Dynamic analysis techniques | Windows, Linux, and macOS | YES | A combination of signature-based detection and behavioral analysis | A commercial licenses |
| Malwr [47]. | An online platform and community-driven malware analysis service that allows users to submit and analyze suspicious files in a controlled environment and give a very detailed report in html/xml format. | Dynamic analysis | Windows, Linux, and macOS | NO | A combination of behavioral and static analysis techniques | Open-Source |
| Threat Expert [47]. | an online malware analysis system that provides a simple user interface for analyzing malware samples by submitting them. It generates a detailed report on the malware, including the time stamp of the malware, the type of packers used by the malware author, and the level of security. | Dynamic analysis | Windows | NO | A combination of behavioral and static analysis techniques | A commercial licenses |
| Drakvuf sandboxe [35]. | Controlled environments created for executing and observing potentially malicious code. These sandboxes aim to provide a secure and isolated space where malware samples can be executed, allowing analysts to study their behaviour without risking damage to the actual operating environment. | Dynamic analysis | Windows | NO | Behaviour analysis techniques | Open-source |
Abbreviations
| SLR | Systematic Literature Review |
| PRISMA | Preferred Reporting Items for Systematic |
| QCQP | Quadratically Constrained Quadratic Program |
| HCP | Honeypot-based Collaborative Protection |
| IoT | Internet of Things |
| CERTS | Computer Emergency Response Teams |
| UPX | Ultimate Packer for Executables |
| Process | Monitor Procmon |
| UBER | User Behavior Emulator |
| SCADA | Supervisory Sontrol And Data Acquisition |
| ICS | Industrial Control Systems |
| UI | User Interface |
| SVM | Support Vector Machines |
| DT | Decision Trees |
| CNN | Convolutional Neural Networks |
References
- Miwa, S., Miyachi, T., Eto, M., Yoshizumi, M., & Shinoda, Y. Design and Implementation of an Isolated Sandbox with Mimetic Internet Used to Analyze Malwares. In DETER, 2007.
- Yokoyama, A., Ishii, K., Tanabe, R., Papa, Y., Yoshioka, K., Matsumoto, T., ... & Rossow, C. Sandprint: Fingerprinting malware sandboxes to provide intelligence for sandbox evasion. In Research in Attacks, Intrusions, and Defenses: 19th International Symposium, RAID 2016, Paris, France, September 19-21, 2016, Proceedings 19 (pp. 165-187). Springer International Publishing, 2016. [CrossRef]
- Faruk, M. J. H., Shahriar, H., Valero, M., Barsha, F. L., Sobhan, S., Khan, M. A., ... & Wu, F. (2021, December). Malware detection and prevention using artificial intelligence techniques. In 2021 IEEE International Conference on Big Data (Big Data), 2021, (pp. 5369-5377). IEEE. [CrossRef]
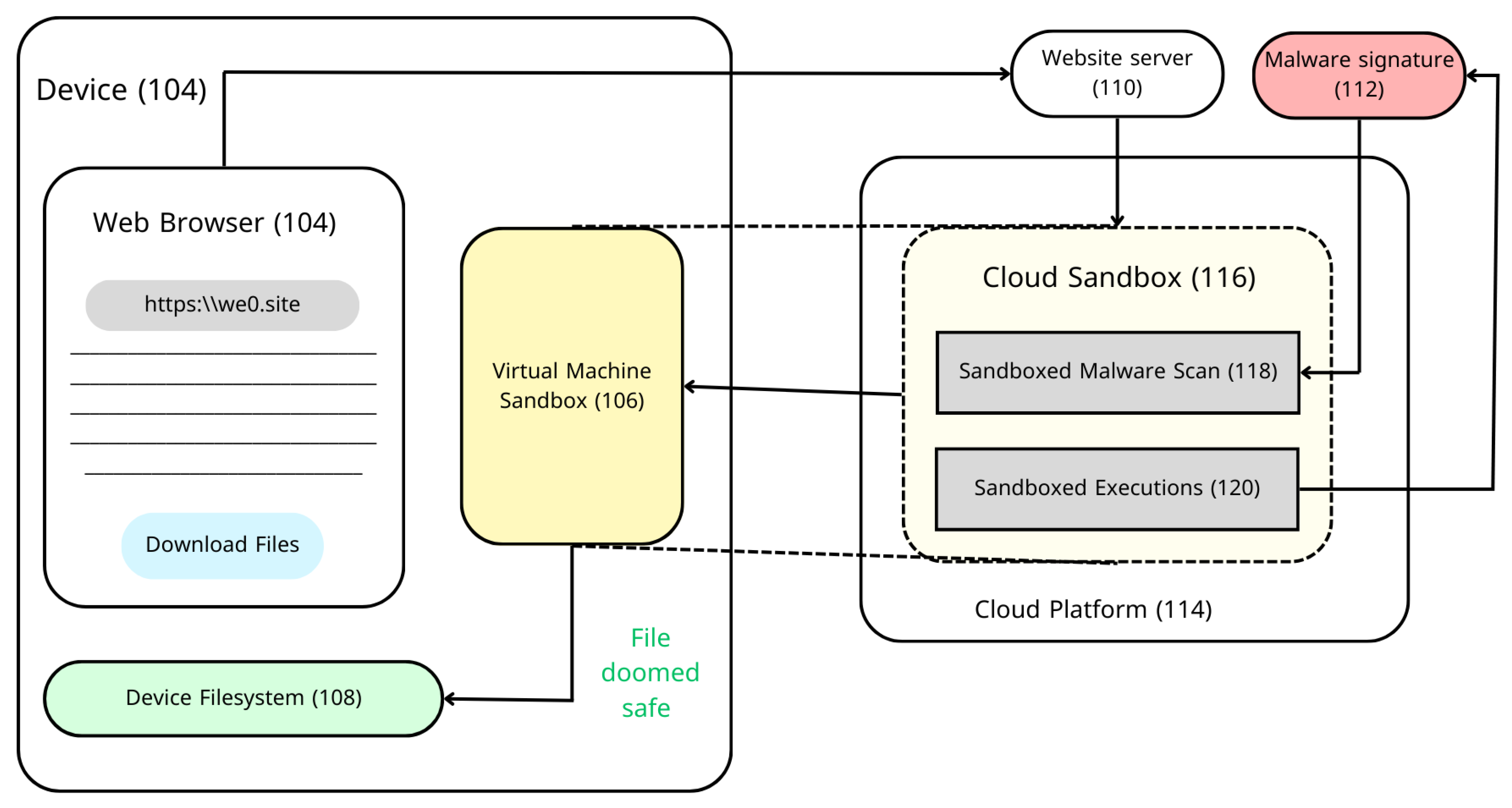
- Malware Sanboxes Available Online :https://www.vmray.com/glossary/malware-sandbox/ (accessed on 30 Nov 2023).
- Page MJ, McKenzie JE, Bossuyt PM, Boutron I, Hoffmann TC, Mulrow CD, et al, “The PRISMA 2020 Statement: An Updated Guideline for Reporting Systematic Reviews”, BMJ, 2021. [CrossRef]
- What’s the Difference Between a Sandbox and a Virtual Machine? Available online: https://askleo.com/whats-the-difference-between-a-sandbox-and-a-virtual-machine/ (accessed on 15 Nov 2023).
- Afianian, A., Niksefat, S., Sadeghiyan, B., & Baptiste, D. Malware dynamic analysis evasion techniques: A survey. ACM Computing Surveys (CSUR), 2019, 52(6), 1-28. [CrossRef]
- BELEA, A. R. Methods for Detecting Malware Using Static, Dynamic and Hybrid Analysis. In Proceedings of the International Conference on Cybersecurity and Cybercrime-2023 2023 (pp. 258-265). Asociatia Romana pentru Asigurarea Securitatii Informatiei. [CrossRef]
- Kamal, A., Derbali, M., Jan, S., Bangash, J. I., Khan, F. Q., Jerbi, H., ... & Ahmad, G. (2021). A User-friendly Model for Ransomware Analysis Using Sandboxing. Computers, Materials & Continua. 2021, 67(3). [CrossRef]
- Yong Wong, M., Landen, M., Antonakakis, M., Blough, D. M., Redmiles, E. M., & Ahamad, M. (2021, November). An inside look into the practice of malware analysis. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security 2021 (pp. 3053-3069). [CrossRef]
- Sikdar, S., Ruan, S., Han, Q., Pitimanaaree, P., Blackthorne, J., Yener, B., & Xia, L. (2022). Anti-Malware Sandbox Games. arXiv preprint arXiv:2202.13520 2022. arXiv:2202.13520 2022.
- Brodschelm, L., & Gelderie, M. Application Sandboxing for Linux Desktops: A User-friendly Approach 2022. [CrossRef]
- Chen, Q., & Bridges, R. A. Automated behavioral analysis of malware: A case study of wannacry ransomware. In 2017 16th IEEE International Conference on machine learning and applications (ICMLA) 2017(pp. 454-460). IEEE. [CrossRef]
- Tan, H., Chandramohan, M., Cifuentes, C., Bai, G., & Ko, R. K. Coldpress: An extensible malware analysis platform for threat intelligence. arXiv preprint arXiv:2103.07012 2021. arXiv:2103.07012 2021.
- Al-Marghilani, A. Comprehensive Analysis of IoT Malware Evasion Techniques. Engineering, Technology & Applied Science Research, 2021 11(4), 7495-7500. [CrossRef]
- UPPIN, C. Dynamic Analysis of a Window-Based Malware Using Automated sandboxing. UPPIN, C. Dynamic Analysis of a Window-Based Malware Using Automated sandboxing. 2019. [CrossRef]
- Liu, S., Feng, P., Wang, S., Sun, K., & Cao, J. Enhancing malware analysis sandboxes with emulated user behavior. Computers & Security, 2022 115, 102613. [CrossRef]
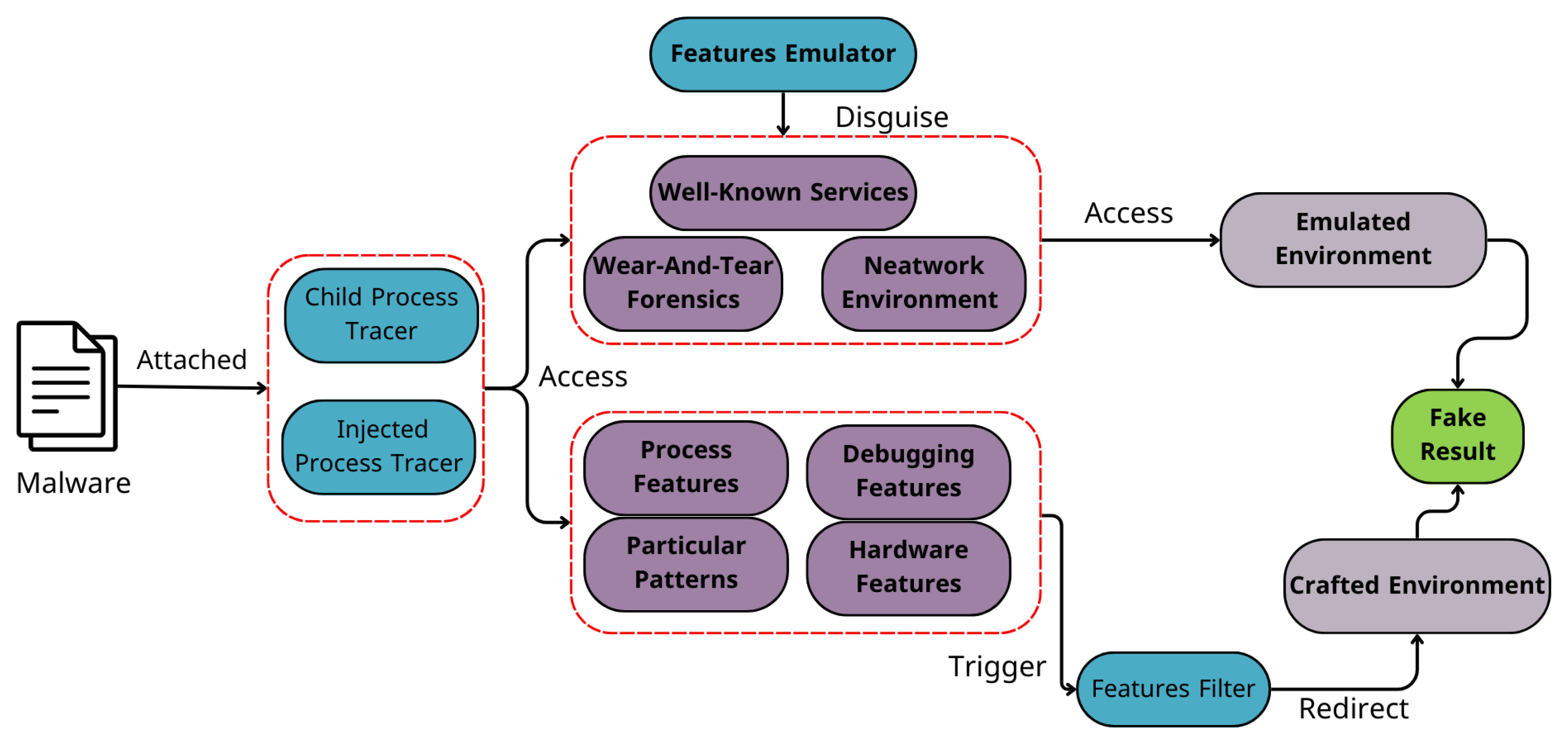
- Xie, C., Guo, Y., Shi, S., Sheng, Y., Chen, X., Li, C., & Wen, W. Envfaker: A method to reinforce linux sandbox based on tracer, filter and emulator against environmental-sensitive malware. In 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 2021 (pp. 667-677). IEEE. [CrossRef]
- Naseer, M., Rusdi, J. F., Shanono, N. M., Salam, S., Muslim, Z. B., Abu, N. A., & Abadi, I. Malware detection: issues and challenges. In Journal of Physics: Conference Series (Vol. 1807, No. 1, p. 012011). IOP Publishing. 2021. [CrossRef]
- BELEA, A. R. Methods for Detecting Malware Using Static, Dynamic and Hybrid Analysis. In Proceedings of the International Conference on Cybersecurity and Cybercrime-2023 2023 (pp. 258-265). Asociatia Romana pentru Asigurarea Securitatii Informatiei. [CrossRef]
- Gazzan, M., & Sheldon, F. T. Opportunities for Early Detection and Prediction of Ransomware Attacks against Industrial Control Systems. Future Internet, 2023, 15(4), 144. [CrossRef]
- Yamany, B. E. M., & Azer, M. A. SALAM Ransomware Behavior Analysis Challenges and Decryption. In 2021 Tenth International Conference on Intelligent Computing and Information Systems (ICICIS), 2021 (pp. 273-277). IEEE. [CrossRef]
- Fasna, V., & Swamy, R. Sandbox: A Secured Testing Framework for Applications, Journal of Technology & Engineering Sciences, 2022.
- Edukulla, S. K. Sandboxing Files Downloaded Via A Web Browser. Technical Disclosure Commons, 2020.
- Iqbal, A., Alobaidli, H., Guimaraes, M., & Popov, O. Sandboxing: aid in digital forensic research. In Proceedings of the 2015 Information Security Curriculum Development Conference, 2015 (pp. 1-5). [CrossRef]
- Yokoyama, A., Ishii, K., Tanabe, R., Papa, Y., Yoshioka, K., Matsumoto, T., ... & Rossow, C. Sandprint: Fingerprinting malware sandboxes to provide intelligence for sandbox evasion. In Research in Attacks, Intrusions, and Defenses: 19th International Symposium, RAID 2016, Paris, France, September 19-21, 2016, Proceedings 19 (pp. 165-187), 2016, Springer International Publishing. [CrossRef]
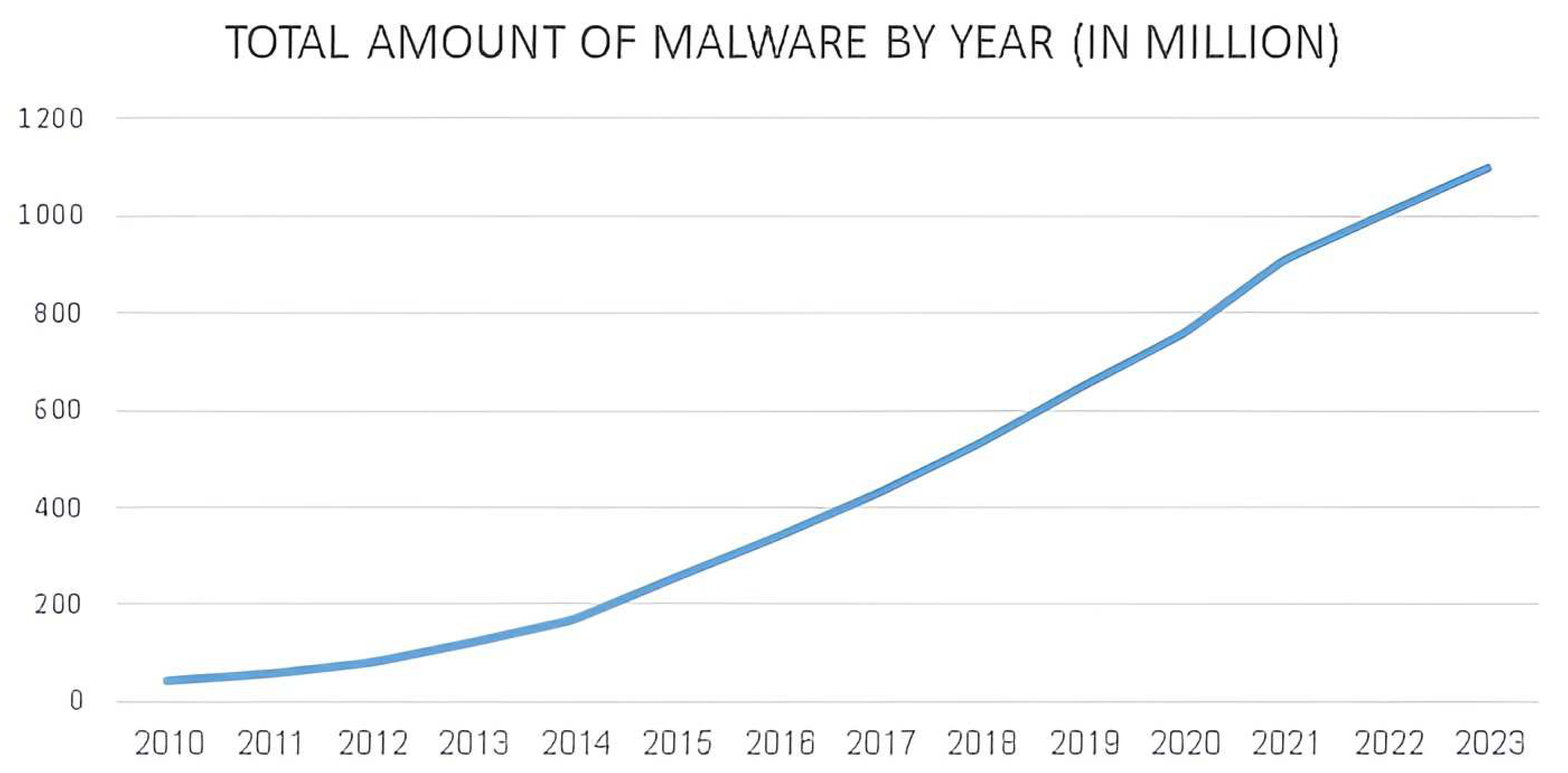
- Namanya, A. P., Cullen, A., Awan, I. U., & Disso, J. P. (2018, August). The world of malware: An overview. In 2018 IEEE 6th international conference on future internet of things and cloud (FiCloud), 2018 (pp. 420-427). IEEE. [CrossRef]
- Talukder, S. Tools and techniques for malware detection and analysis.arXiv preprint arXiv:2002.06819, 2020. arXiv:2002.06819, 2020.
- Kaur, N., Bindal, A. K., & PhD, A. A complete dynamic malware analysis. International Journal of Computer Applications, 2016, 135(4), 20-25. [CrossRef]
- Sethi, K., Chaudhary, S. K., Tripathy, B. K., & Bera, P. A novel malware analysis framework for malware detection and classification using machine learning approach. In Proceedings of the 19th international conference on distributed computing and networking, 2018, (pp. 1-4). [CrossRef]
- Küchler, A., Mantovani, A., Han, Y., Bilge, L., & Balzarotti, D. (2021, February). Does Every Second Count? Time-based Evolution of Malware Behavior in Sandboxes. In NDSS, 2021. [CrossRef]
- Denham, B., & Thompson, D. R. Ransomware and malware sandboxing. In 2022 IEEE 13th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), 2022, (pp. 0173-0179). IEEE. [CrossRef]
- Akhtar, M. S., & Feng, T. Malware Analysis and Detection Using Machine Learning Algorithms.Symmetry, (2022), 14(11), 2304. [CrossRef]
- Ijaz, M., Durad, M. H., & Ismail, M. Static and dynamic malware analysis using machine learning. In 2019 16th International bhurban conference on applied sciences and technology (IBCAST), (2019, January),(pp. 687-691). IEEE. [CrossRef]
- Ilić, S. Ž., Gnjatović, M. J., Popović, B. M., & Maček, N. D. A pilot comparative analysis of the Cuckoo and Drakvuf sandboxes: An end-user perspective. Vojnotehnički glasnik/Military Technical Courier,(2022),70(2), 372-392. [CrossRef]
- Le, H. V., & Ngo, Q. D. V-sandbox for dynamic analysis IoT botnet. IEEE Access, 2020, 8, 145768-145786. [CrossRef]
- Aboaoja, F. A., Zainal, A., Ghaleb, F. A., Al-rimy, B. A. S., Eisa, T. A. E., & Elnour, A. A. H. Malware detection issues, challenges, and future directions: A survey. Applied Sciences, (2022), 12(17), 8482. [CrossRef]
- Kachare, G. P., Choudhary, G., Shandilya, S. K., & Sihag, V. Sandbox Environment for Real Time Malware Analysis of IoT Devices. In International Conference on Computing Science, Communication and Security, 2022, (pp. 169-183). Cham: Springer International Publishing. [CrossRef]
- Suraneni, N. Malware Detection and Analysis, Culminating Experience Projects, 2022.
- Kamal, A., Derbali, M., Jan, S., Bangash, J. I., Khan, F. Q., Jerbi, H., ... & Ahmad, G. (2021). A User-friendly Model for Ransomware Analysis Using Sandboxing. Computers, Materials & Continua, 2021, 67(3). [CrossRef]
- Lee, S., Jeon, H., & Park, G. (2021). Design of automation environment for analyzing various IoT malware. Tehnički vjesnik, 2021, 28(3), 827-835. [CrossRef]
- Gibert, D., Mateu, C., & Planes, J. (2020). The rise of machine learning for detection and classification of malware: Research developments, trends and challenges. Journal of Network and Computer Applications, 2020, 153, 102526. [CrossRef]
- Al-Marghilani, A. (2021). Comprehensive Analysis of IoT Malware Evasion Techniques.Engineering, Technology & Applied Science Research, 2021, 11(4), 7495-7500. [CrossRef]
- Gazzan, M., & Sheldon, F. T. (2023). Opportunities for Early Detection and Prediction of Ransomware Attacks against Industrial Control Systems. Future Internet, 2023, 15(4), 144. [CrossRef]
- Jeffrey, N., Tan, Q., & Villar, J. R. (2023). A Review of Anomaly Detection Strategies to Detect Threats to Cyber-Physical Systems. Electronics, 2023, 12(15), 3283. [CrossRef]
- Jadhav, A., Vidyarthi, D., & Hemavathy, M. Evolution of evasive malwares: A survey. In 2016 International Conference on Computational Techniques in Information and Communication Technologies (ICCTICT), 2016 (pp. 641-646). IEEE. [CrossRef]
- Jamalpur, S., Navya, Y. S., Raja, P., Tagore, G., & Rao, G. R. K. (2018, April). Dynamic malware analysis using cuckoo sandbox. In 2018 Second international conference on inventive communication and computational technologies (ICICCT) (pp. 1056-1060). IEEE,2018. [CrossRef]
- Ali, M., Shiaeles, S., Papadaki, M., & Ghita, B. V. (2018, October). Agent-based vs agent-less sandbox for dynamic behavioral analysis. In 2018 Global Information Infrastructure and Networking Symposium (GIIS) (pp. 1-5). IEEE, 2018. [CrossRef]
- Botacin, M., Ceschin, F., Sun, R., Oliveira, D., & Grégio, A. (2021). Challenges and pitfalls in malware research. Computers & Security, 2021, 106, 102287. [CrossRef]
- Liu, S., Feng, P., Wang, S., Sun, K., & Cao, J. (2022). Enhancing malware analysis sandboxes with emulated user behavior. Computers & Security, 2022, 115, 102613. [CrossRef]
- Pilli, E. S., Joshi, R. C., & Niyogi, R. (2010). Network forensic frameworks: Survey and research challenges. digital investigation, 2010, 7(1-2), 14-27. [CrossRef]
| Malware Analysis Type | Advantages | Disadvantages | Tools and Technologies |
|---|---|---|---|
| Static Analysis | It requires little kernel overhead and can be completed in a brief run-time. | The accuracy of malware detection is also less in static analysis. | Virustotal, Google, PE Explorer, CEF Explorer, and Resource Hacker. |
| Dynamic Analysis | Discovers and verifies vulnerabilities that occur during run-time. | a large amount of kernel overhead that may cause the system to lag while it is analysis. | Wireshark, Process Monitor, Process Explorer, IDA Pro, OllyDbg. |
| Hybrid Analysis | Because it can detect malicious malware and reduce false negatives, it is more accurate than any other analysis type. | kernel overhead and cause systems to lag when being analyzed. | Ghidra, Windbg, gdb, Java Decompiler. |
| Sandboxing | Users can run files or programs in an isolated testing environment without affecting the application. | Making the testing environment resemble the actual production environment requires a certain set of skills. | Cuckoo Sandbox, AnyRun Sandbox, Joe Sandbox. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





