Submitted:
09 November 2023
Posted:
09 November 2023
You are already at the latest version
Abstract
Keywords:
1. INTRODUCTION
- A. Definition of IDS, IPS and IDPS
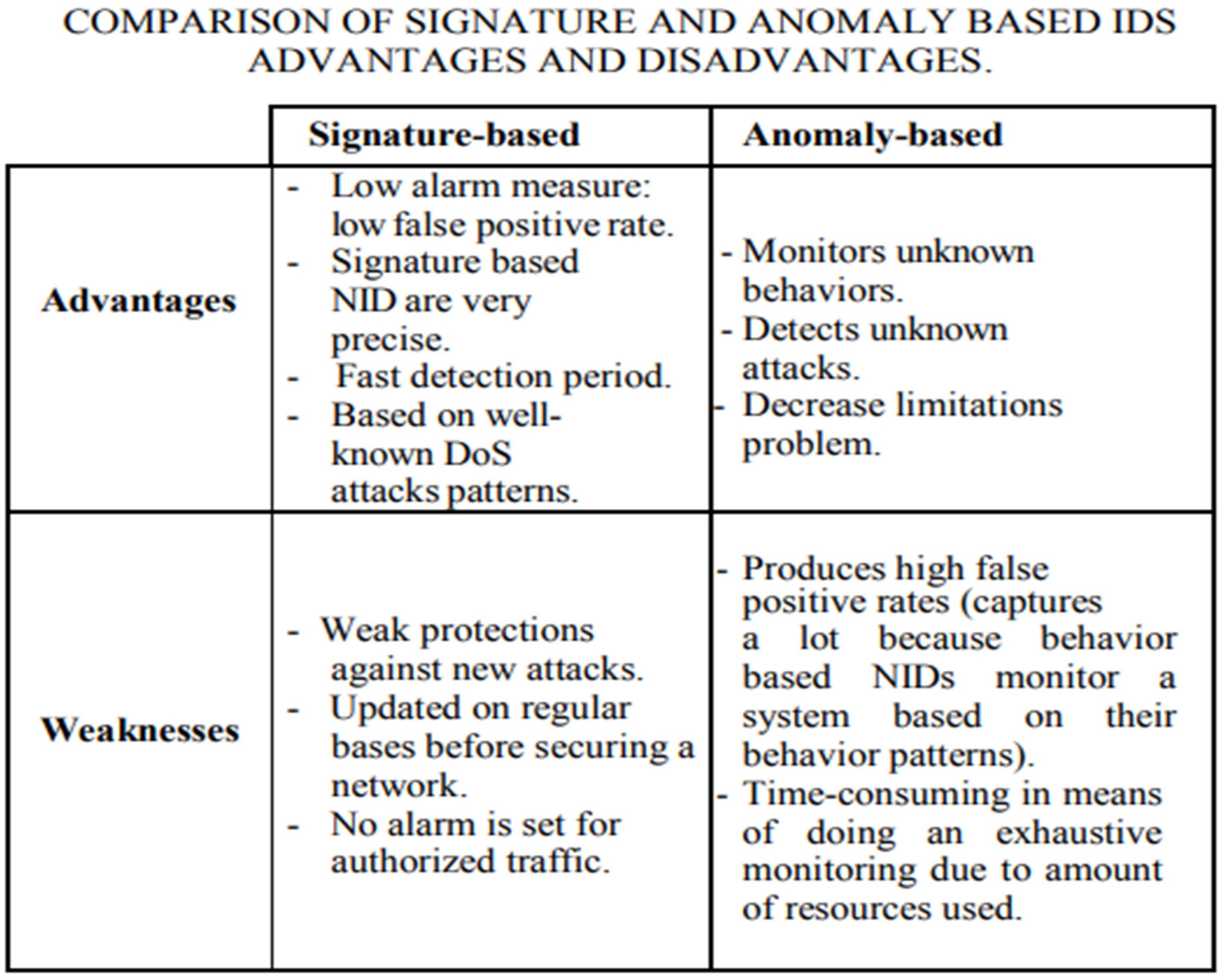 |
- B. Importance of IDPS
- C. Overview of the proposed solution
2. COMPONENTS OF IDPS
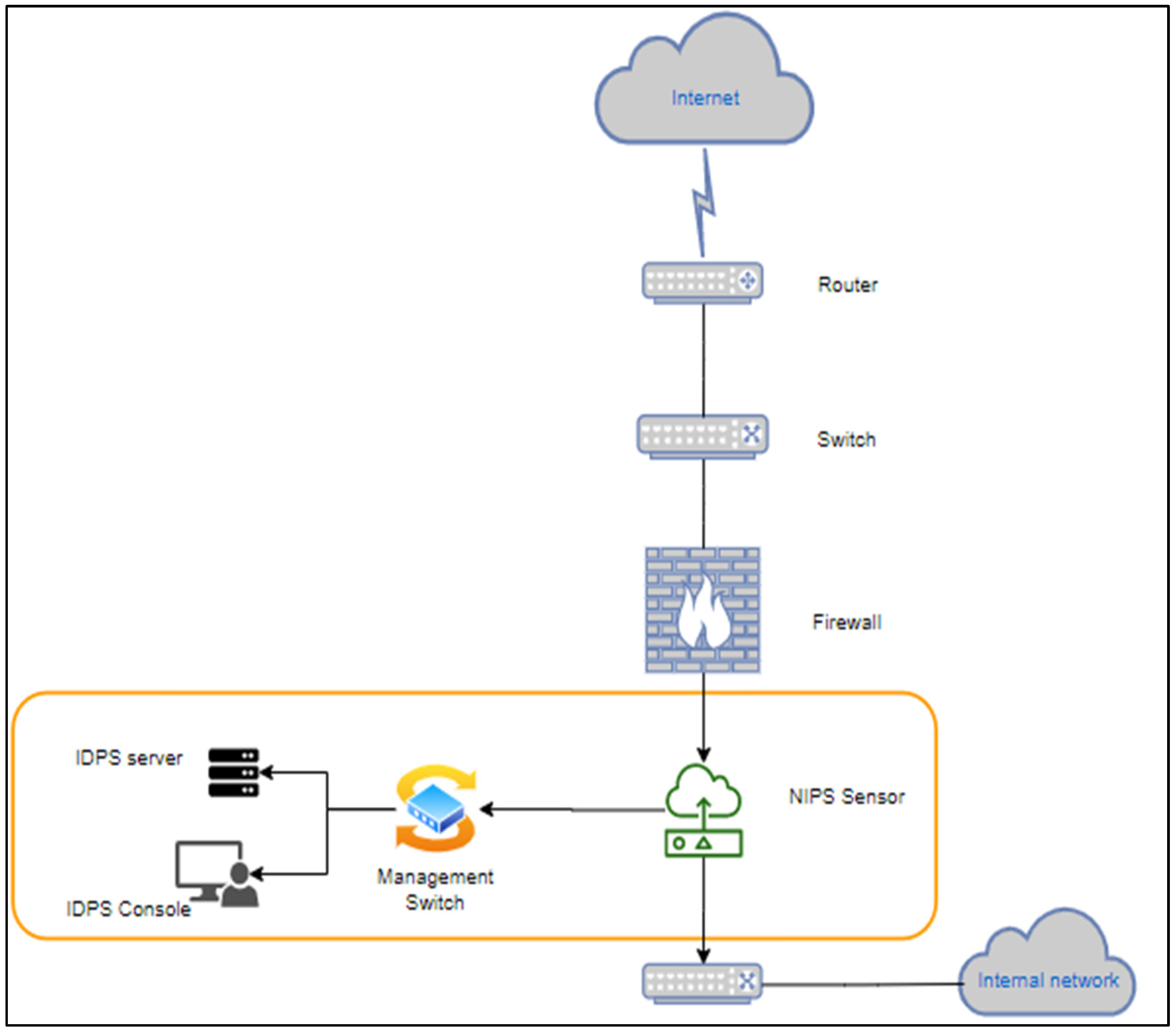
- Source of Data
- Data collection capabilities of a NIPS:
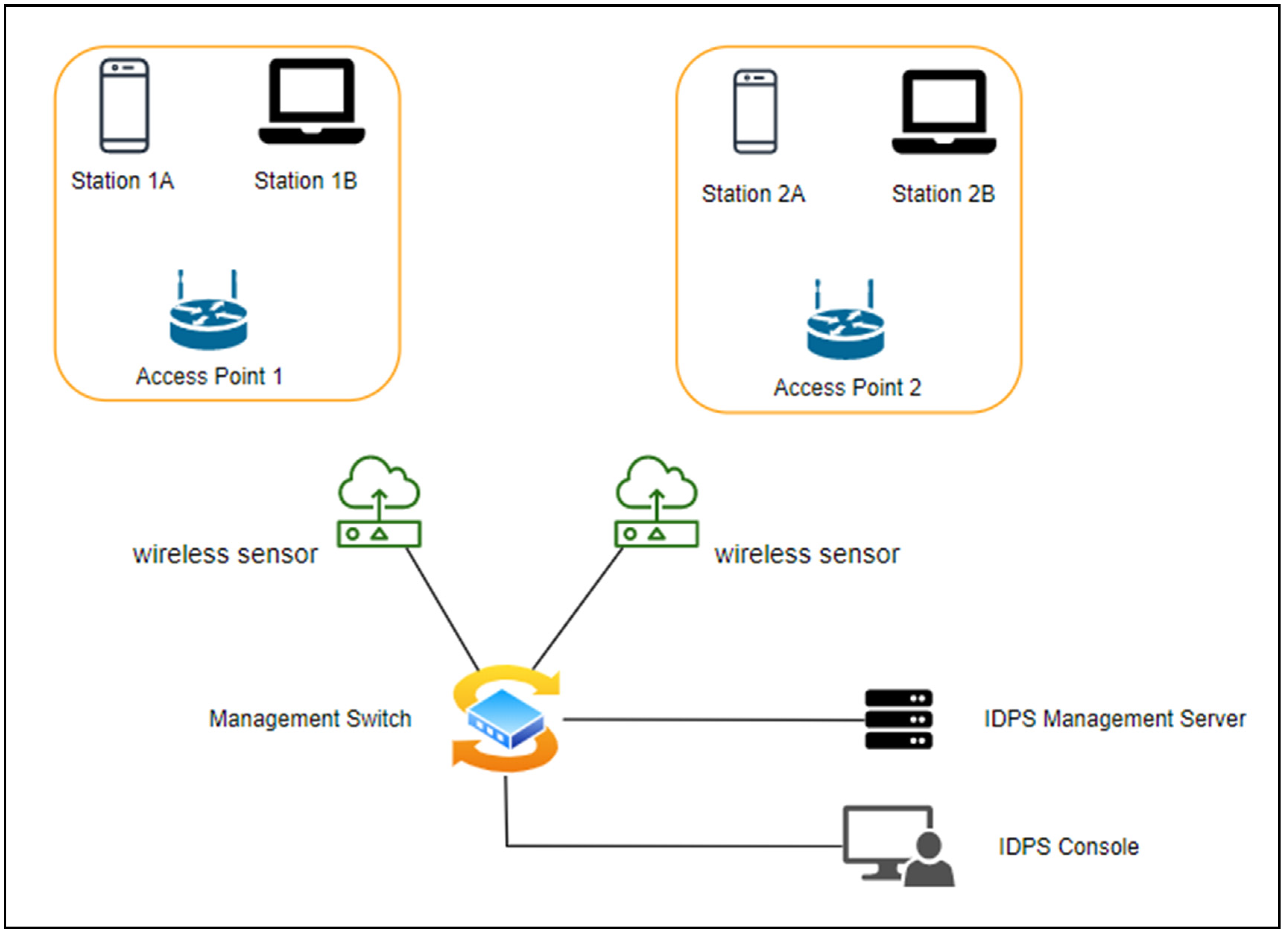
- Data collection capabilities of a WIPS:
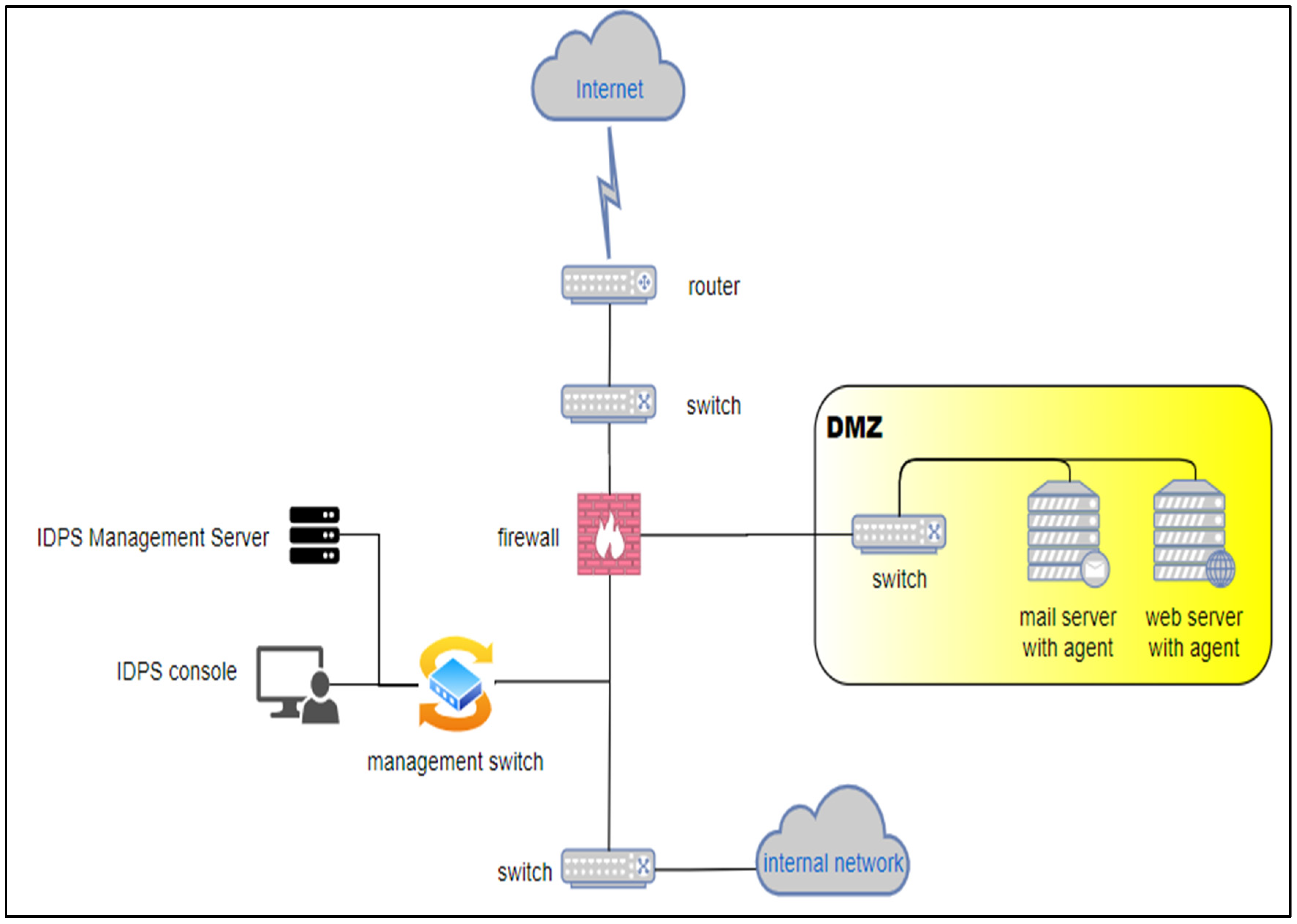
- Data collection capabilities of a HIPS:
- Logging Capabilities of the proposed IPS
- Shelf-life control and data storage
- B.
- Analysis Engine
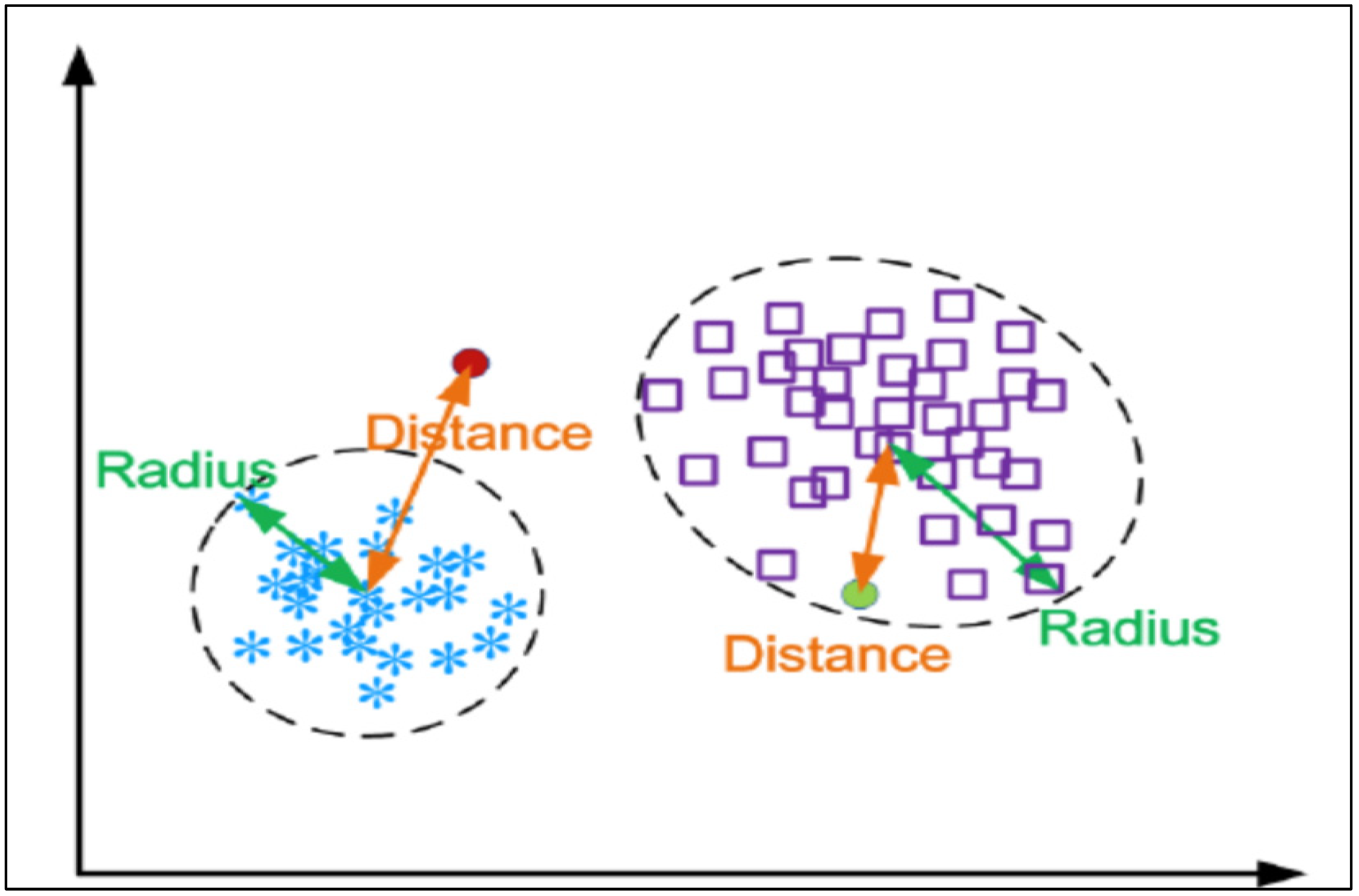
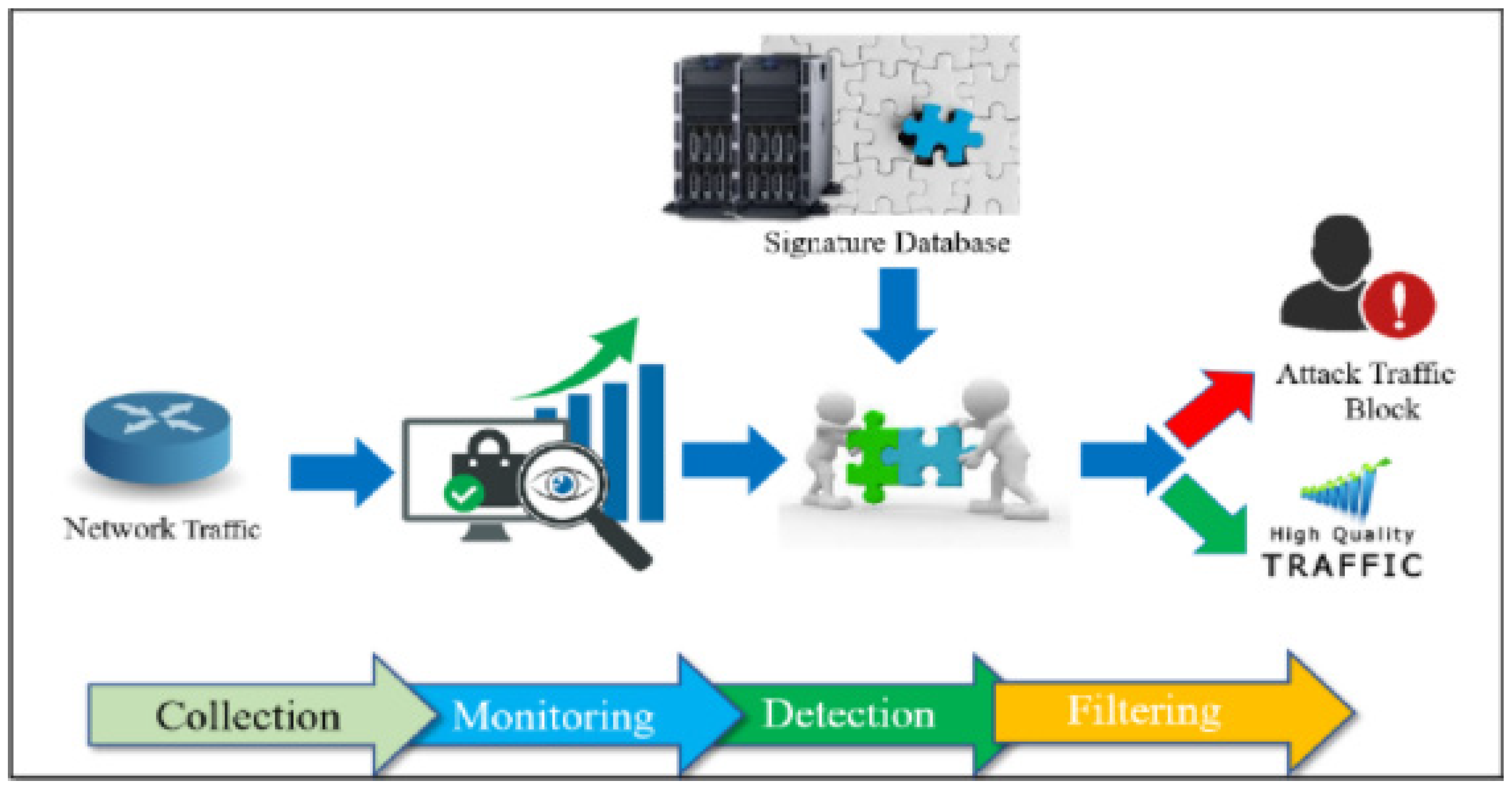
- Rule-Based anomaly detection
- Rule-Based Penetration Identification
- C.
- Preventive action
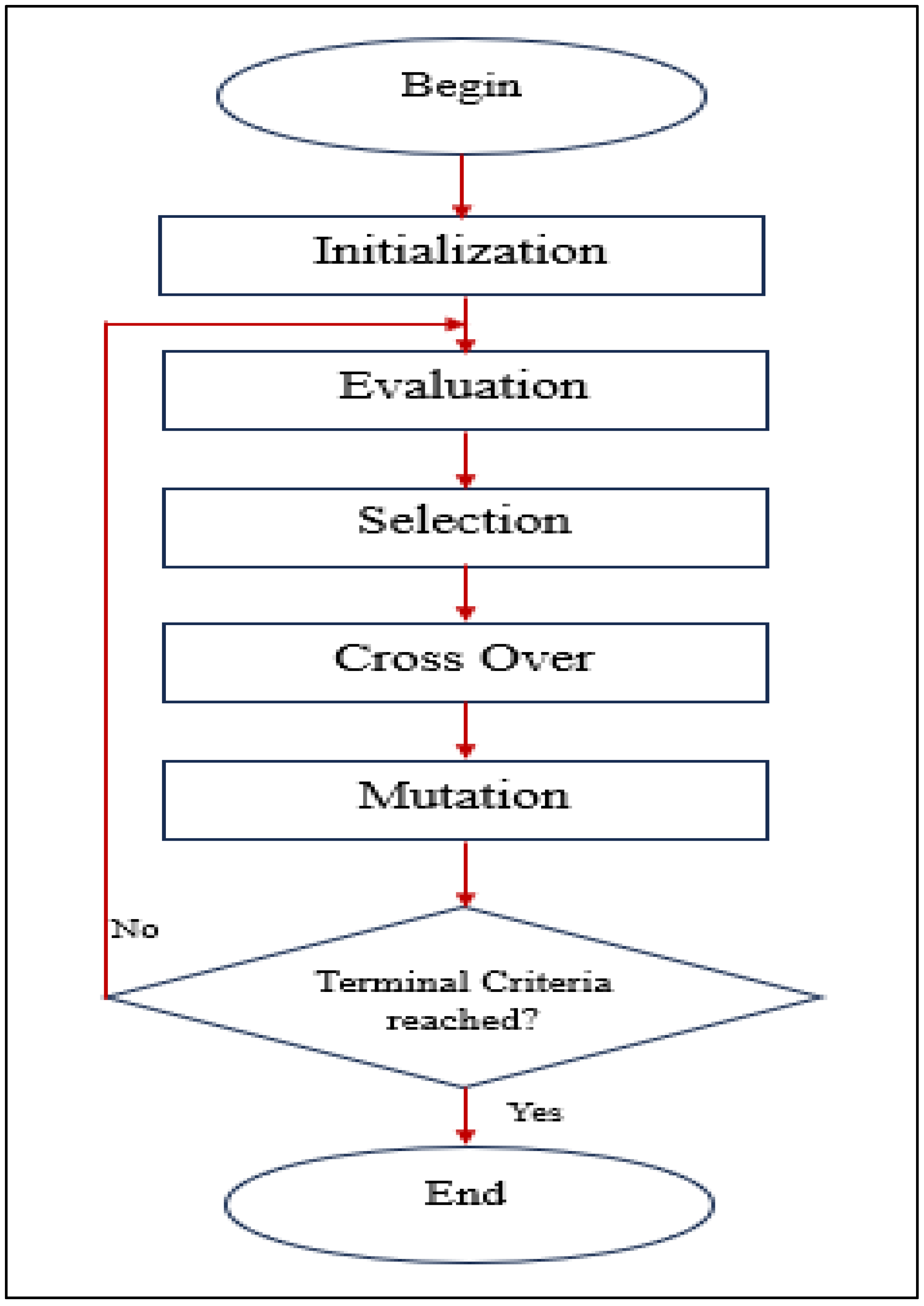
- D.
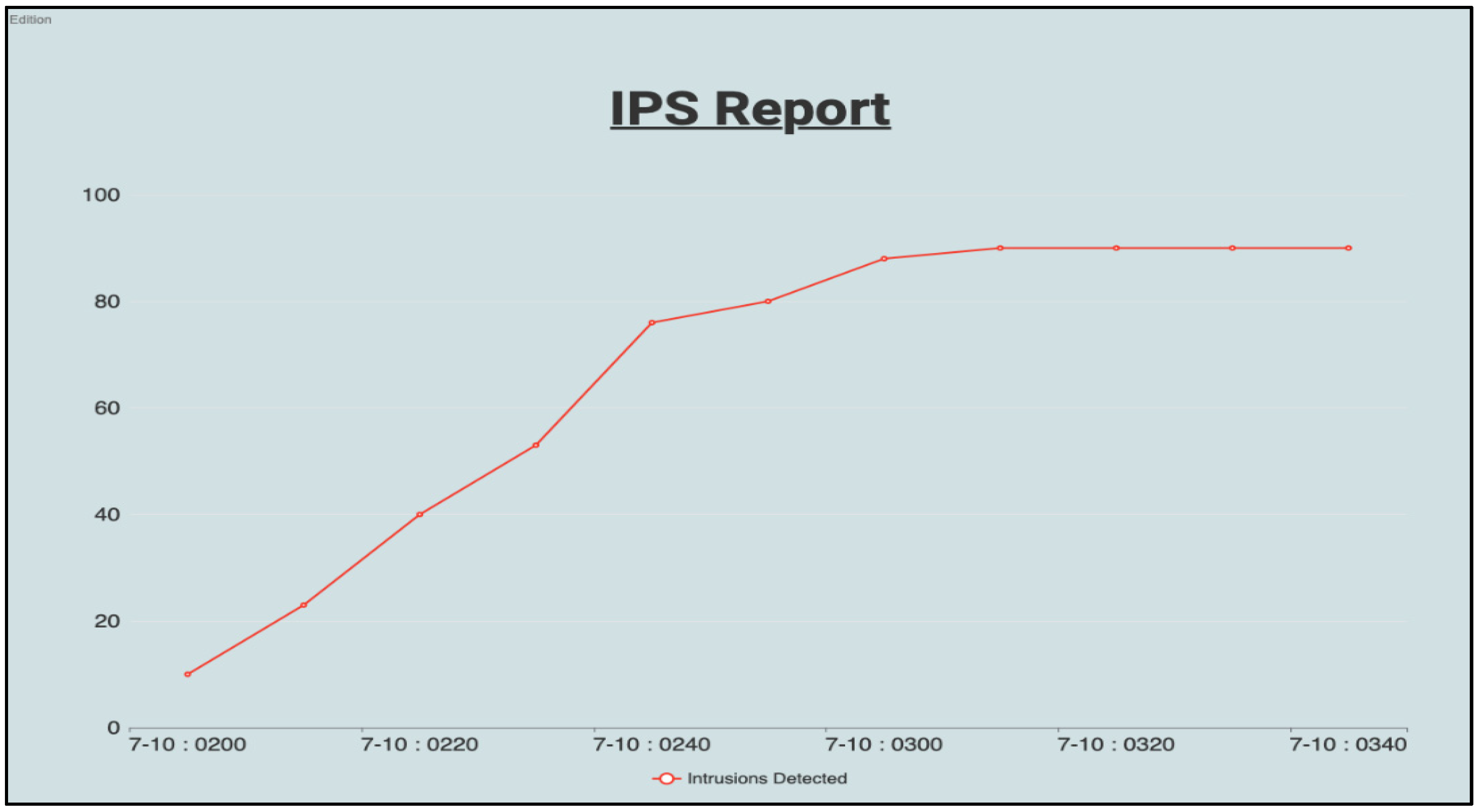
- Reporting
3. FUTURE PROSPECTS
- A.
- Advancements in IDPS and its potential impact on cybersecurity
- B.
- Discussion of potential challenges and solutions
4. CONCLUSION
References
- Abusitta, A., Bellaiche, M., Dagenais, M., & Halabi, T. (2019b). A deep learning approach for proactive multi-cloud cooperative intrusion detection system. Future Generation Computer Systems, 98, 308–318. [CrossRef]
- Adeyemo, V. E., Abdullah, A., Jhanjhi, N. Z., Supramaniam, M., & Balogun, A. O. (2019). Ensemble and Deep-Learning Methods for Two-Class and Multi-Attack Anomaly Intrusion Detection: An Empirical study. International Journal of Advanced Computer Science and Applications, 10(9). [CrossRef]
- Alferidah, D. K., & Jhanjhi, N. Z. (2020). Cybersecurity Impact over Bigdata and IoT Growth. 2020 International Conference on Computational Intelligence (ICCI). [CrossRef]
- Almusaylim, Z. A., & Jhanjhi, N. Z. (2018). A review on smart home present state and challenges: linked to context-awareness internet of things (IoT). Wireless Networks, 25(6), 3193–3204. [CrossRef]
- Almrezeq, N. (2021). Cyber security attacks and challenges in Saudi Arabia during COVID-19. Turkish Journal of Computer and Mathematics Education (TURCOMAT), 12(10), 2982-2991.
- Almusaylim, A. Z., Jhanjhi, NZ, & Alhumam, A.(2020). Detection and mitigation of RPL rank and version number attacks in the internet of things: SRPL-RP. Sensors, 20(21), 5997.
- Annadurai, C., Nelson, I., Devi, K. N., Ramachandran, M., Jhanjhi, N. Z., Masud, M., & Sheikh, A. M. (2022). Biometric Authentication-Based Intrusion Detection using Artificial intelligence internet of things in smart city. Energies, 15(19), 7430. [CrossRef]
- Anomalies Detection and Proactive Defence of Routers Based on Muttiple Information Learning (2019). [online] Available at: <https:/Awww.researchgate.net/publication/334718382_Anomalies_Detection_and_Proactive_Defence_of_Routers_Based_on_Multiple_Information_Learning> [Accessed 12 October 2021].
- Arxiv.org. 2020. A review on outlier/anomaly detection in time series data. [online] Available at: <https://arxiv.org/pdf/2002.04236.pdf> [Accessed 12 October 2021].
- Bartwal, U., Mukhopadhyay, S., Negi, R., & Shukla, S. (2022). Security orchestration, automation, and response engine for deployment of behavioural honeypots. 2022 IEEE Conference on Dependable and Secure Computing (DSC). [CrossRef]
- Brook, C., 2018. What is Deep Packet Inspection? How It Works, Use Cases for DPI, and More. [online] Digital Guardian. Available at: <https://digitalguardian.com/blog/what-deep-packet-inspection-how-it-works- use-cases-dpi-and-more> [Accessed 12 October 2021].
- Certificationkits.com. (2017). CCNA Security: Network Based vs Host Based Intrusion Detection & Prevention - CertificationKits.com. [online] Available at: https://www.certificationkits.com/cisco-certification/ccna-security-certification- topics/ccna-security-implement-ips-with-sdm/ccna-security-network-based-vs- host-based-intrusion-detection-a-prevention/ [Accessed 18 Oct. 2021].
- Chickowski, E., 2020. Deep packet inspection explained. [online] AT&T Business. Available at: <https://cybersecurity.att.com/blogs/security- essentials/what-is-deep-packet-inspection> [Accessed 12 October 2021].
- Clements, J. & Lao, Y., 2018. Backdoor attacks on neural network operations. 2018 IEEE Global Conference on Signal and Information Processing (GlobalSIP). Comodo Security Solutions, Inc (2020).
- Conrad, E., Misenar, S. and Feldman, J. (2017). Domain 7. Eleventh Hour CISSPID, [online] pp.145-183. Available at: https://www.sciencedirect.comitopics/computer-science/network-based- intrusion-detection-system [Accessed 18 Oct. 2021].
- Din, A. (2021). Taking Host Intrusion Prevention System (HIPS) Apart. [online] Heimdal Security Blog. Available at: https://heirndalsecurity.com/blog/taking- host-intrusion-prevention-system-hips-aparu [Accessed 16 Oct. 2021].
- Faadooengineers.com. 2021. Rule Based Intrusion Detection. [online] Available at: <http://www.faadooengineers.com/online-study/post/cse/network-management-and-securuty/637/rule-based-intrusion-detection> [Accessed 12 October 2021].
- Fahad Ahmed. (2023). The Evolution of Antivirus Software to Face Modern Threats. Security Intelligence. https://securityintelligence.com/posts/antivirus-evolution-to-face-modern-threats/.
- Forcepoint. (2019). What is an Intrusion Prevention System (IPS)? [online] Available at: https://www.forcepoint.com/cyber-edu/intrusion-prevention-system-ips [Accessed 16 Oct. 2021].
- Fortinet. 2021. What Is Deep Packet Inspection (DPI)? I Fortinet. [online] Available at: <https://www.fortinet.com/resources/cyberglossary/dpi-deep-packet-inspection>[Accessed 12 October 2021].
- GeeksforGeeks. (2019). Intrusion Prevention System (IPS) - GeeksforGeeks. [online] Available at: https://www.geeksforgeeks.org/intrusion-prevention-system-ips/ (Accessed 18 Oct. 2021].
- GEORGE, A. SHAJI., GEORGE, A. S. HOVAN., T. Baskar, & Pandey, D. (2021). XDR: The Evolution of Endpoint Security Solutions -Superior Extensibility and Analytics to Satisfy the Organizational Needs of the Future. Zenodo (CERN European Organization for Nuclear Research). [CrossRef]
- Hamid, B., Jhanjhi, N. Z., Humayun, M., Khan, A. F., & Alsayat, A. (2019). Cyber Security Issues and Challenges for Smart Cities: A survey. 2019 13th International Conference on Mathematics, Actuarial Science, Computer Science and Statistics (MACS). [CrossRef]
- Hayes, B. (2017). Introduction to intrusion detection and prevention technologies. [online] SearchSecurity. Available at: https://searchsecurity.techtarget.com/tip/Introduction-to-intrusion-detection- and-prevention-technologies [Accessed 16 Oct. 2021].
- Henriques, J. et al., 2020. Combining K-means and XGBoost models for anomaly detection using log datasets. MDPI. Available at: <https://www.mdpi.com/2079-9292/9/7/1164/htm> [Accessed October 12, 2021].
- Hossain Faruk, M. J., Shahriar, H., Valero, M., Barsha, F. L., Sobhan, S., Khan, M. A., Whitman, M., Cuzzocrea, A., Lo, D., Rahman, A., & Wu, F. (2021). Malware detection and prevention using Artificial Intelligence Techniques. 2021 IEEE International Conference on Big Data (Big Data). [CrossRef]
- Humayun, M., Jhanjhi, N. Z., Talib, M., Shah, M. H., & Suseendran, G. (2021). Cybersecurity for data science: issues, opportunities, and challenges. In Lecture notes in networks and systems (pp. 435–444). [CrossRef]
- Humayun, M., Niazi, M., Almufareh, M. F., Jhanjhi, N. Z., Mahmood, S., & Alshayeb, M. (2022). Software-as-a-service security challenges and best practices: A multivocal literature review. Applied Sciences, 12(8), 3953.
- Humayun, M., Jhanjhi, N. Z., & Almotilag, A. (2022). Real-time security health and privacy monitoring for Saudi highways using cutting-edge technologies. Applied Sciences, 12(4), 2177.
- Intrusion Prevention Systems I Benefits of Intrusion Prevention Systems. [online] Comodo. Available at: https:/Iwww.comodo.com/intrusion-prevention-systems.php [Accessed 16 Oct. 2023.
- Hussain, S. Tahir, M. Humayun, M. F. Almufareh, N. Z. Jhanjhi and F. Qamar, "Health Monitoring System Using Internet of Things (IoT) Sensing for Elderly People," 2022 14th International Conference on Mathematics, Actuarial Science, Computer Science and Statistics (MACS), Karachi, Pakistan, 2022, pp. 1-5. [CrossRef]
- Jacob, D. (2023, July 31). The Role of AI in Enhancing Antivirus Security. Techjockey.com Blog. https://www.techjockey.com/blog/role-of-ai-in-antivirus-security.
- Jayakumar, P., Brohi, S. N., & Jhanjhi, N. Z. (2021). Artificial Intelligence and Military Applications: Innovations, Cybersecurity Challenges & Open Research Areas. Preprints. [CrossRef]
- Juniper.net. 2019. Anomaly Detection Rules - TechLibrary - Juniper Networks. [online] Available at:<https://www.juniperneVdocumentation/en_USIsa7.4.0/jsa-users guide/topics/concept/concept-jsa-user-anomaly-detection-rules.html> [Accessed 12 October 2021].
- Just Firewalls. (2020). What is a Wireless Intrusion Prevention System (WIPS)? Wi-Fi Security That's No Longer Up in the Air - Just Firewalls. [online] Available at: https://www.justfirewalls.corriNvhat-is-a-wireless-intrusion-prevention-system/ [Accessed 15 Oct. 2021].
- Kaur, M., Singh, A., Verma, S., Kavita, Jhanjhi, N. Z., & Talib, M. N. (2021). FANET: Efficient routing in flying ad hoc networks (FANETs) using firefly algorithm. In Intelligent Computing and Innovation on Data Science: Proceedings of ICTIDS 2021 (pp. 483-490). Springer Singapore.
- Khraisat, A., & Alazab, A. (2021). A critical review of intrusion detection systems in the internet of things: Techniques, deployment strategy, validation strategy, attacks, public datasets and challenges. Cybersecurity, 4(1). [CrossRef]
- Khraisat, A., Gonda!, I., Vamplew, P. and Kamruzzaman, J. (2019). Survey of intrusion detection systems: techniques, qalaseta and challenges. Cybersecurity, 2(1).
- Khraisat, A., Gondal, I., Vamplew, P., & Kamruzzaman, J. (2019). Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity, 2(1). [CrossRef]
- Kiourti, P. et al., 2020. Trojdrl: Evaluation of backdoor attacks on Deep Reinforcement Learning. 2020 57th ACM/IEEE Design Automation Conference (DAC).
- Kumar, K., Verma, S., Jhanjhi, N. Z., & Talib, M. N. (2020, December). A Survey of The Design and Security Mechanisms of The Wireless Networks and Mobile Ad-Hoc Networks. In IOP Conference Series: Materials Science and Engineering (Vol. 993, No. 1, p. 012063). IOP Publishing.
- Kwon, H. (2020). Detecting backdoor attacks via class difference in deep neural networks. IEEE Access, pp.1-1.
- Lambora, A., Gupta, K., & Chopra, K. (2019). Genetic algorithm- A literature review. 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon). [CrossRef]
- Learn About Intrusion Detection and Prevention Staying Open for Business. (n.d.). [online] Available at: https://www.junipernet/documentation/en_US/leam- about/LA_I ntrusion Detectionand Prevention.pdf.
- Li, J., Su, J., Chen, R., Wang, X. and Chen, S., 2018. Practical privacy- preserving deep packet inspection outsourcing. Concurrency and Computation: Practice and Experience, 31(22).
- Li, T., Ma, J., Shen, Y., & Pei, Q. (2019). Anomalies detection and proactive defence of routers based on multiple information learning. Entropy, 21(8), 734. [CrossRef]
- Lies De Kimpe, Michel Walrave, Pieter Verdegem, Koen Ponnet. (2021) What we think we know about cybersecurity: an investigation of the relationship between perceived knowledge, Internet trust, and protection motivation in a cybercrime context. Behaviour & Information Technology 0:0, pages 1-13.
- loulianou, Philokypros, Vasilakis, Vasileios orcid.org/0000-0003-4902-8226, Moscholios, loannis et aL(1 more author) (Accepted: 2018) A Signature-based Intrusion Detection System for the Internet of Things,.. In: Information and Communication Technology Form, 11-13 Jul 2018, (In Press).
- Manageengine.com. 2021. IDS/IPS tools - monitoring. [online] Available at: <https://www.manageengine.conVproducts/eventlog/ids-ips-monitoring- reporting.html> [Accessed 12 October 2021].
- Mazhar, N., Salleh, R., Asif, M. and Zeeshan, M. (2020). SDN based Intrusion Detection and Prevention Systems using Manufacturer Usage Description: A Survey. International Journal of Advanced Computer Science and.
- Mohammad Masdari, Hemn Khezri,A survey and taxonomy of the fuzzy signature-based Intrusion Detection Systems,Applied Soft Computing, Volume 92,2020,106301,1SSN 1568-4946, https://doi.org/10.1016/j.asoc.2020.106301.
- Muzammal, S. M., Murugesan, R. K., & Jhanjhi, N. Z. (2021, March). Introducing mobility metrics in trust-based security of routing protocol for internet of things. In 2021 National Computing Colleges Conference (NCCC) (pp. 1-5). IEEE.
- Nawaz, A. (2021). Feature engineering based on hybrid features for malware detection over Android framework. Turkish Journal of Computer and Mathematics Education (TURCOMAT), 12(10), 2856-2864.
- N. Sharma, A. Chakrabarti, and V. E. Balas, Eds., Data Management, AONILO and Innovation. Singapore: Springer Singapore, 2020.
- Ncsc.gov.uk. 2019. What is an antivirus product? Do I need one?.[online] Available at: <https://www.ncsc.gov.uk/guidance/what-is-an-antivirus-product> [Accessed 12 October 2021].
- Nunez, Juan E.; Tchegui Donfack, Roger W.; Rohit, Rohit; and Horn, Hayley (2022) "Self-Learning Algorithms for Intrusion Detection and Prevention Systems (IDPS)," SMU Data Science Review: Vol. 6: No. 2, Article 20, https://scholar.smu.edu/datasciencereview/vol6/iss2/20.
- Nyunt, K. S., & Zaman, N. (2015). The Effectiveness of Big Data in Social Networks. In Advances in data mining and database management book series. IGI Global. [CrossRef]
- Online.visual-paradigm.com. 2021. Visual Paradigm Online - Suite of Powerful Tools. [online] Available at: <https://online.visual-paradigm.com> [Accessed 19 October 2021].
- Osama Faker and Erdogan Dogdu. 2019. Intrusion Detection Using Big Data and Deep Learning Techniques. In Proceedings of the 2019 ACM Southeast Conference (ACM SE '19). Association for Computing Machinery, New York, NY, USA, 86–93. [CrossRef]
- Panagiotou, P. et al., 2021. Host-based intrusion detection using signature-based and AI-driven anomaly detection methods. Information & Security: An International Journal, 50, pp.37-48.
- Ponnusamy, V., Aun, Y., Jhanjhi, N. Z., Humayun, M., & Almufareh, M. F. (2022). IoT wireless intrusion detection and network Traffic Analysis. Computer Systems Science and Engineering, 40(3), 865–879. [CrossRef]
- Ponnusamy, V., Aun, Y., Jhanjhi, N. Z., Humayun, M., & Almufareh, M. F. (2022b). IoT wireless intrusion detection and network Traffic Analysis. Computer Systems Science and Engineering, 40(3), 865–879. [CrossRef]
- Ponnusamy, V., Humayun, M., Jhanjhi, N. Z., Aun, Y., & Almufareh, M. F. (2022). Intrusion detection systems in internet of things and mobile Ad-Hoc networks. Computer Systems Science and Engineering, 40(3), 1199–1215. [CrossRef]
- Ponnusamy, V., Rafique, K., & Zaman, N. (2019). Employing recent technologies for improved digital governance. IGI Global.
- Prajapati, P., Bhatt, B., Zalavadiya, G., Ajwalia, M., & Shah, P. (2021). A review on recent intrusion detection systems and intrusion prevention systems in IOT. 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence). [CrossRef]
- Queen A. Aigbefo, Yvette Blount, Maurido Marrone. (2020) The influence of hardiness and habit on security behaviour intention. Behaviour & Information Technology 0:0, pages 1-20.
- Quincozes, S. E., Albuquerque, C., Passos, D., & Mossé, D. (2021). A survey on intrusion detection and Prevention Systems in digital substations. Computer Networks, 184, 107679. [CrossRef]
- Romeo, M.D.S., 2019. An intrusion detection system (IDS) in the internet of things (I0T) devices for Smart Home. International Journal of Psychosocial Rehabilitation, 23(4), pp.1217-1227.
- Saeed, S., Zaman, N., Naqvi, M., Humayun, M., & Ahmed, S. (2020). Ransomware: A Framework for Security Challenges in Internet of Things. [CrossRef]
- Sangkaran, T., Abdullah, A., & JhanJhi, N. Z. (2020). Criminal network community detection using graphical analytic methods: A survey. EAI Endorsed Transactions on Energy Web, 7(26), e5-e5.
- Safensoft.com. (2020). Host Intrusion Prevention System (HIPS). [online] Available at: http://www.safensoft.com/hips/ [Accessed 16 Oct. 2021].
- Saylor Academy. 2020. CS406: Rule-based IDS I Saylor Academy. [online] Available at:.
- Scarfone, K. and Mell, P. (n.d.). Guide to Intrusion Detection and Prevention Systems (IDPS) (Draft) Recommendations of the National Institute of Systems (IDPS) (Draft) Recommendations of the National Institute of Standards and Technology. [online].
- SearchSecurity. 2017. What is antivirus software (antivirus program)? - Definition from Whatls.com. [online] Available at <https://searchsecurity.techtarget. com/definition/antivirus-software> [Accessed 19 October 2021].
- Seong, T. B., Ponnusamy, V., Jhanjhi, N. Z., Annur, R., & Talib, M. (2021). A comparative analysis on traditional wired datasets and the need for wireless datasets for IoT wireless intrusion detection. Indonesian Journal of Electrical Engineering and Computer Science, 22(2), 1165. [CrossRef]
- Services, P. and (AMP), A., 2021. What Is Antivirus Protection?. [online] Cisco. Available at:.
- Shurman, M. M., Khrais, R. M., & Yateem, A. A. (2019). IOT denial-of-service attack detection and prevention using hybrid ids. 2019 International Arab Conference on Information Technology (ACIT). [CrossRef]
- Sharma, U., Nand, P., Chatterjee, J. M., Jain, V., Jhanjhi, N. Z., & Sujatha, R. (Eds.). (2022). Cyber-Physical Systems: Foundations and Techniques. John Wiley & Sons.
- Shafiq, D. A., Jhanjhi, N. Z., & Abdullah, A. (2021, March). Machine learning approaches for load balancing in cloud computing services. In 2021 National Computing Colleges Conference (NCCC) (pp. 1-8). IEEE.
- Snehi, Jyoti. (2020). Diverse Methods for Signature based Intrusion Detection Schemes Adopted https://csrc.nist.gov/csrc/media/oublications/so/800-94/rev-1/draft/documents/draftsp800-94-rev1.pdf.
- Taylor, C. (2019). Network-Based Intrusion Prevention - CyberHoot. [online] CyberHoot. Available at: https://cyberhoot.com/cybrary/intrusion-prevention/ [Accessed 16 Oct. 2021].
- Thapa, Suman & Mailewa, Akalanka. (2020). THE ROLE OF INTRUSION DETECTION/PREVENTION SYSTEMS IN MODERN COMPUTER NETWORKS: A REVIEW...
- Tsukermarj E., 2020. What is an intrusion detection system (IDS)= Designing a Machine Learning Intrusion Detection System...
- Ubing, A. A., Jasmi, S. Z. A., Abdullah, A., Zaman, N., & Supramaniam, M. (2019). Phishing Website Detection: An Improved Accuracy through Feature Selection and Ensemble Learning. International Journal of Advanced Computer Science and Applications, 10(1). [CrossRef]
- Umich.edu. (2021). Intrusion Prevention System Benefits / U-M Information and Technology Services. [online] Available at: https://its.umich.edu/enterprise/wifi-networks/network-security/ips/benefits [Accessed 16 Oct. 2021].
- Verizon Fios. 2021. What is Antivirus - Definition, Meaning & Explanation. [online] Available at: <https://www.verizon.com/info/definitions/antivirus/> [Accessed 12 October 2021].
- Vijayalakshmi, B., Ramar, K., Zaman, N., Verma, S., Kaliappan, M., Vijayalakshmi, K., Vimal, S., Kavita, & Ghosh, U. (2021). An attention-based deep learning model for traffic flow prediction using spatiotemporal features towards sustainable smart city. International Journal of Communication Systems, 34(3). [CrossRef]
- VMware. (2021). Intrusion Prevention System. [online] Available at: https://www.vmware.comttopics/glossary/content/intrusion-prevention-system [Accessed 16 Oct. 2021].
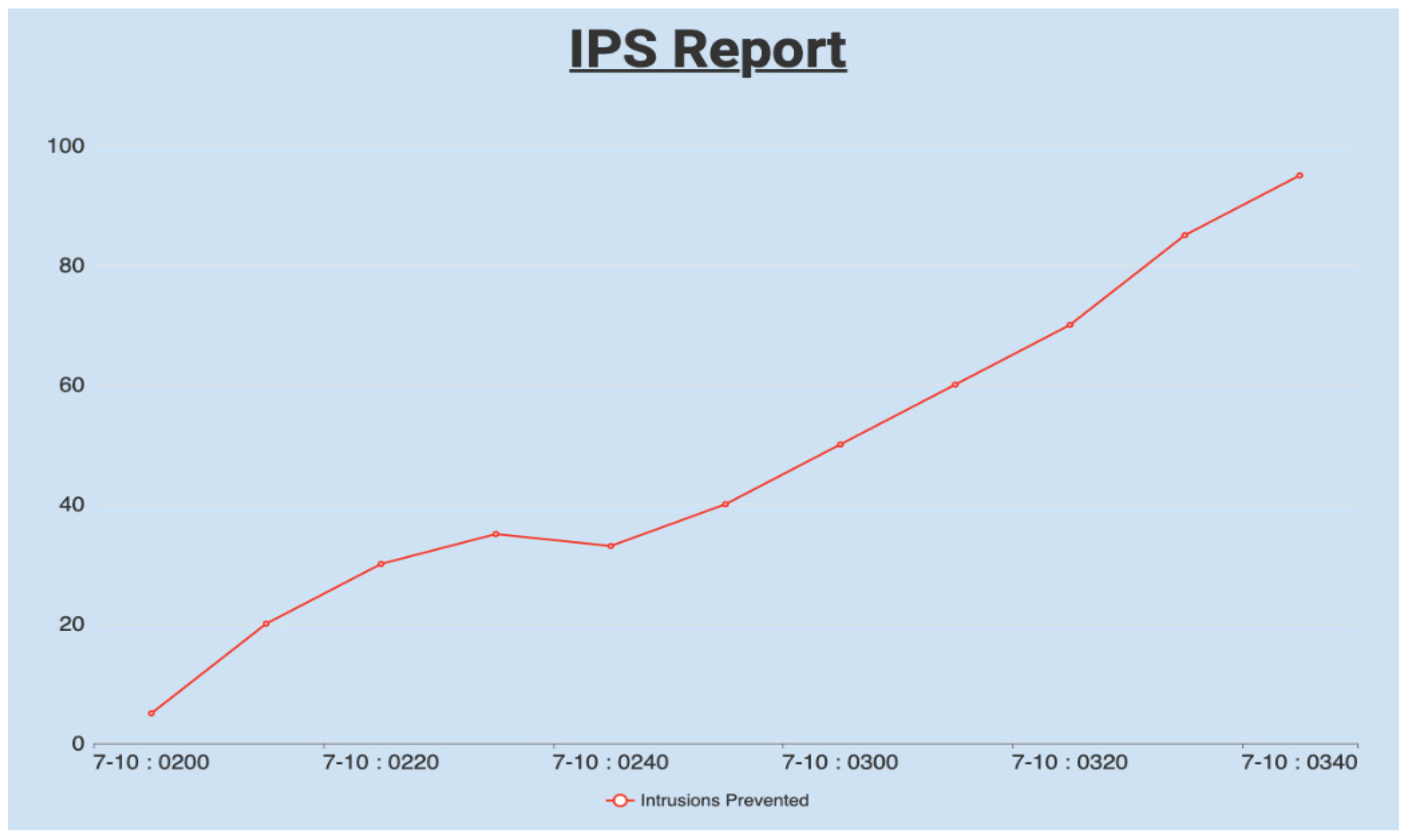
- Watchguard.com. 2021. Intrusions (IPS) Report. [online] Available at: <https://www.watchguard.com/help/docs/help-center/en-US/Content/en-US/WG-Cloud/Devices/reports/report_intrusiont ips.html> [Accessed 12 October 2021].
- Webroot.com. 2021. What is Antivirus Software. [online] Available at: https://www.webroot.com/us/en/resourcesnips-articles/what-is-anti-virus-software [Accessed 12 October 2021].
- Wireless Intrusion Prevention System (WIPS). (n.d.). [online] Available at: https://usa.ingrammicro.com/media/Documents/vendors/w/watchguard/tech_brief_wips_081616.pdf [Accessed 18 Oct. 2021].
- Zahra, F., Jhanjhi, N., Khan, N. A., Brohi, S. N., Masud, M., & Aljahdali, S. (2022). Protocol-Specific and Sensor Network-Inherited Attack Detection in IoT Using Machine Learning. Applied Sciences, 12(22), 11598. [CrossRef]
- Zahra, F., Jhanjhi, N. Z., Brohi, S. N., Khan, N. A., Masud, M., & AlZain, M. A. (2022). Rank and wormhole attack detection model for RPL-based internet of things using machine learning. Sensors, 22(18), 6765.
- Zaman, N., Ahmad, M., Khan, M. S., & Hussain, M. (2022a). The Impact of Cyber Attacks on E-Governance During the COVID-19 Pandemic. In Advances in electronic government, digital divide, and regional development book series (pp. 123–140). IGI Global. [CrossRef]
- Zaman, N., Humayun, M., & Almuayqil, S. (2021). Cyber Security and Privacy Issues in Industrial Internet of Things. Computer Systems Science and Engineering, 37(3), 361–380. [CrossRef]
- Zaman, N., Hussain, K., Abdullah, A. B., Humayun, M., & Tavares, J. M. R. S. (2022). Information Security Handbook. In CRC Press eBooks. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





