1. Introduction
Cryptography, or cryptology, has its roots in the Ancient Greek words ‘kryptós’, meaning hidden or secret, ‘graphein’, signifying to write, and ‘logia’, denoting study [
1]. It is a pivotal element in modern-day security, grounded in cryptographic algorithms constructed around the ‘computational hardness assumption’ [
2]. Its practical applications are manifold and integral in various domains, including:
- (a)
Secure Transactions: It underpins chip-based payment cards, digital currencies, computer passwords, and military communications, ensuring the security and integrity of transactions [
3];
- (b)
Cybersecurity and Encrypted Communications: Cryptography is fundamental in securing communications through encryption, exemplified by technologies like Hypertext Transfer Protocol Secure (HTTPS) and Pretty Good Privacy (PGP).
- (c)
Cryptocurrencies and Crypto-economics: It employs a range of cryptographic techniques such as Zero Knowledge Proofs (ZKP), cryptographic keys, and cryptographic hash functions, which are pivotal in maintaining the security and integrity of digital assets and transactions.
In cryptographic science, several encryption algorithms stand out for their widespread adoption and inherent security. The Advanced Encryption Standard (AES) is a symmetric encryption algorithm renowned for its robustness and security, serving as a benchmark in the field. Another notable symmetric encryption algorithm is the Triple Data Encryption Algorithm (3DEA), also known as 3DES (Triple DES). This algorithm is distinctive for its thrice encryption methodology using the Data Encryption Standard (DES) cipher, a technique known as the Data Encryption Algorithm (DEA), originally derived from the Lucifer cipher [
4].
The RSA Public-Key Encryption Algorithm, developed by Ron Rivest, Adi Shamir, and Leonard Adleman, is foundational in public key cryptography, offering an asymmetric encryption solution [
5].
Complementing these encryption algorithms are regulatory compliances to safeguard individual privacy and data security. The IPAA is a pivotal regulatory standard focusing explicitly on individual privacy protection. The PCI-DSS is a comprehensive set of security standards ensuring that companies accepting, processing, storing, or transmitting credit card information uphold a secure environment. Lastly, the GDPR [
6], [
7] is a paramount regulation mandating personal data protection and privacy for individuals within the European Union and the European Economic Area. These regulations and advanced encryption algorithms form the bedrock of modern-day cryptographic practices, ensuring a harmonious balance between technological advancement and individual privacy and security.
Rationale
The advent of digital transformation has accentuated the importance of securing communication and information, making cryptography a cornerstone in the realm of information security. Public Key Cryptography, a pivotal component of cryptographic practices, is integral in maintaining confidentiality, ensuring integrity, and establishing trust in digital communications. However, the evolving threat landscape and the emergence of sophisticated attack vectors necessitate a comprehensive understanding of the vulnerabilities and potential repercussions associated with cryptographic practices. The rationale behind this study lies in exploring the multifaceted aspects of Public Key Cryptography, delving into the intricacies of potential attacks, and elucidating the consequential impacts of key compromises. By intertwining theoretical insights with practical implications, this study aims to contribute to the nuanced understanding of cryptographic security, inform policy development, and foster the implementation of robust cryptographic practices in the face of evolving cyber threats.
Objectives of the Study
To explore the vulnerabilities and potential attack vectors in Public Key Cryptography.
To analyse the consequences of key compromises on confidentiality, integrity, trust, and legal and reputational standing.
To elucidate the significance of key sizes and encryption algorithms in thwarting brute-force attacks.
To provide practical recommendations for enhancing cryptographic security and mitigating the risks associated with key compromises.
To contribute to the advancement of cryptographic research by offering a holistic perspective on the challenges and considerations in implementing cryptographic practices.
Research Questions
What are the vulnerabilities and potential attack vectors in Public Key Cryptography?
How do key compromises impact confidentiality, integrity, trust, and legal and reputational standing in cryptographic communications?
What is the significance of key sizes and encryption algorithms in enhancing the resilience of cryptographic systems against brute-force attacks?
What practical recommendations can be derived to fortify cryptographic security and mitigate the risks associated with key compromises?
Scope and Limitations
The scope of this study encompasses an extensive exploration of Public Key Cryptography, focusing on the vulnerabilities, attack vectors, and the consequential impacts of key compromises. It aims to provide a balanced perspective, integrating theoretical concepts with practical implications and offering insights into the enhancement of cryptographic security. However, the study has its limitations. The rapidly evolving nature of cyber threats and technological advancements may introduce new vulnerabilities and challenges that are not covered in this study. Additionally, the study primarily focuses on Public Key Cryptography and may not address the intricacies and considerations associated with other cryptographic practices. The recommendations provided are based on the current state of knowledge and may need to be revisited and adapted considering future developments in the field of cryptography.
2. Methodology
Research Design
The methodology for this study is designed to be qualitative, focusing on an in-depth exploration and analysis of Public Key Cryptography. The qualitative approach allows for a comprehensive understanding of the vulnerabilities, potential attack vectors, and the consequential impacts of key compromises in cryptographic practices. The study is structured to intertwine theoretical insights with practical implications, providing a holistic perspective on cryptographic security.
Data Collection
Data for this study is primarily collected from the interactive discourse with experts in the field, then presented in the research study, supplemented by a review of existing literature, scholarly articles, and publications in the field of cryptography. The discourse with experts serves as an interactive platform, facilitating the exchange of ideas, insights, and knowledge on various aspects of Public Key Cryptography. The literature review aids in contextualising the findings from the discourse within the broader academic and practical landscape, allowing for a more nuanced and informed analysis.
Data Analysis
The data analysis for this study is conducted through a thematic analysis of the discourse with experts and the reviewed literature. The thematic analysis enables the identification of key themes, patterns, and insights related to vulnerabilities, attack vectors, and impacts of key compromises in Public Key Cryptography. The analysis is focused on extracting meaningful insights regarding the significance of key sizes, encryption algorithms, and practical recommendations for enhancing cryptographic security. The findings from the analysis are then synthesised to provide a comprehensive understanding of the subject matter, contributing to the advancement of knowledge in the field of cryptographic research.
Validation Procedures
To ensure the validity and reliability of the findings, the study employs a triangulation approach, corroborating the insights gleaned from the chat with the existing body of literature and scholarly publications. This approach allows for the cross-verification of findings, enhancing the credibility and robustness of the study. Additionally, the study adheres to rigorous academic standards and ethical considerations, ensuring the integrity and authenticity of the research process and the derived insights.
In conclusion, the methodology chapter outlines the qualitative research design, data collection from chat discourse and literature review, thematic data analysis, and validation procedures employed to conduct an in-depth study on Public Key Cryptography. The structured approach to research design and analysis ensures the reliability and validity of the findings, contributing to the holistic understanding of cryptographic security and the implications of key compromises in the evolving digital landscape.
3. Introduction to Cryptography
Public Key (PK) Cryptography
Public Key (PK) cryptography, or asymmetric cryptography, is a cryptographic system that employs a pair of mathematically related keys: public and private. Unlike symmetric cryptography, which employs a single key for encryption and decryption, PK cryptography uses distinct keys for each operation.
The public key is available to anyone who wishes to communicate securely with the key holder. It is primarily employed for encryption and the validation of digital signatures. In contrast, the private key is kept secret and only known to the holder. It is utilised to decrypt messages encrypted with the corresponding public key and generate digital signatures.
The computational difficulty of deriving a private key from a public key is the source of PK cryptography's strength. Even though the public key is publicly accessible, dedicating the private key from it is computationally impossible. This property ensures that confidential information remains secure even if an adversary intercepts the public key.
PK cryptography enables secure communication and various cryptographic features, including key exchanges, digital signatures, and data encryption. It is the basis for numerous secure protocols and applications, such as secure email, secure web browsing (HTTPS), secure file transfer (SFTP), and secure messaging platforms.
Overall, PK cryptography offers secure and confidential communication between parties without requiring a shared secret key. It provides increased security, scalability, and adaptability in various applications and is crucial to contemporary cryptographic systems.
4. Key Concepts in the Cryptography Timeline
To generate a digital signature, the signatory must first create a key pair consisting of a private key and a public key. The private key is kept secure and not shared, while the public key is made available. Next, a unique hash of the document or message to be signed is generated using a hash function. This hash value represents the document's content uniquely. Using their private key, the signer encrypts the generated hash value, known as hash signing. This associates their signature with a specific document.
The result of this encryption process is the digital signature, which is a cryptographic representation of the signed hash value. The digital signature is unique to both the document and the signer. Creating a digital signature requires the signatory to generate a key pair, consisting of a private key and a public key. The private key is kept secure and not shared, while the public key is made available. Then, a unique hash value of the document or message to be signed is generated using a hash function. This hash value represents the content of the document in a unique way. The signer then encrypts the generated hash value using their private key, a method known as hash signing. This process associates their signature with the specific document.
The resulting product of this encryption process is the digital signature, which is a cryptographic representation of the signed hash value. This signature is unique to both the document and to the signer.
The signatory generates a key pair consisting of a private key and its corresponding public key. The private key is kept securely and not shared, whereas the public key is made available. The signatory must first generate a unique hash (a fixed-length numerical representation) of the document or message to be signed to generate a digital signature. A hash function is used for this purpose, and it generates a hash value that represents the document's content in a unique manner.
Using their private key, the signer encrypts the generated hash value. This procedure is known as hash signing. By encrypting the hash with their private key, the signer associates their signature with a particular document.
After the encryption process, the result is the digital signature. This signature is a cryptographic representation of the signed hash value. It is unique to both the document and the signer. To verify the signature, the recipient uses the signer's public key to decrypt it. Then, they obtain the original hash value. The recipient also independently computes the document's hash value using the same function as the signer.
Finally, the recipient compares the two hash values. They verify that the document has not been altered since adding the digital signature. This ensures the document's integrity.
Critical Concepts in Cryptography
Digital signatures provide a reliable method for authenticating the sender or originator of a digital document or message. By signing a document with their private key, the signatory guarantees that their identity is uniquely associated with the digital signature. The recipient can then confirm the sender's authenticity using the signatory's public key to validate the digital signature. This procedure establishes credibility and prevents unauthorised parties from assuming the signatory's identity. It enables parties to confirm the origin of a document or message.
Digital signatures are vital in preserving the integrity of digital documents and communications. When a signatory applies a digital signature to a document, it generates a cryptographic representation of its unique content. Even a single character change would result in a different hash value, invalidating the signature. By verifying the digital signature, the recipient can confirm that the document has not been altered since it was signed. This guarantees that the information remains intact and unaltered during transmission or storage, preventing unauthorised manipulation and providing assurance.
Non-repudiation is another important characteristic of digital signatures. Non-repudiation means that the signatory cannot deny their involvement or disown the document or message they signed. The digital signature is uniquely associated with the signer's private key, proving their intent and participation. This provides a strong legal basis and accountability for the signed document, preventing the signatory from later denying their actions.
Role of the Key Exchange
When two parties must establish a shared secret key over an unsecured communication channel, they can use Public Key (PK) cryptography. Each party creates a key pair consisting of a private key (kept confidential) and a public key (freely distributed).
Next, the parties exchange their public keys through an insecure channel directly or through a reliable third party. Then, each party uses the other party's public key to encrypt a random session key or secret key, which is transmitted to the other party.
Upon receiving the encrypted session key, each party uses its private key to decrypt the message and recover the session key. Both parties now have the same session key, a shared secret key. This key can be used with symmetric encryption algorithms to ensure secure communication and message exchange.
When two parties communicate using the Diffie-Hellman key exchange algorithm, a shared secret key is derived from their private keys and the other party's public key. This ensures that only the intended parties have access to the shared key. It is impossible for any other party listening to the communication to deduce the shared secret key without access to the private key. However, it is important to note that the Diffie-Hellman algorithm only provides key exchange and does not provide authentication or protection against man-in-the-middle attacks. Therefore, additional measures such as digital signatures or certificates are typically employed to ensure the authenticity and integrity of the exchanged public keys.
Cryptographic Key Size
Preventing brute-force attacks is crucial in ensuring the security of cryptographic keys, and the key size plays a vital role in achieving this. Essentially, brute-force attacks involve trying every possible key until the correct one is found. The larger the key size, the more extensive the search space, which refers to the total number of possible keys. For instance, a 128-bit key generates an astronomical number of keys, approximately 3.4 x 10^38. Brute-forcing such a vast search space would require an impractical amount of time and computational resources, making it practically impossible. As the key size increases, the time complexity of searching the space grows exponentially. Modern computers and even the most potent networks would require an impractical amount of time to successfully brute-force a large key. Therefore, larger key sizes act as a deterrent against brute-force attacks. Nevertheless, technological advances continually improve computational power, increasing brute-force attacks' efficiency.
Attackers can use specialised hardware (GPUs or dedicated FPGA devices) or distributed computing techniques (botnets) to accelerate the attack. Consequently, employing key sizes resistant to attackers' current and anticipated future computational capabilities is essential. Increasing the size of the key compensates for the increased computational capacity of potential attackers.
It is crucial to utilise a larger key size to ensure optimal security in a cryptographic system. This protects against potential advancements in cryptanalysis techniques that aim to identify weaknesses in encryption systems. A larger key size guarantees that the system remains secure in the event of new attacks, as the expanded key space is much more challenging to penetrate. However, it is essential to remember that a cryptographic system's security depends not entirely on the key size alone. Other factors like algorithm strength, implementation security, and key management practices significantly impact overall security. Therefore, selecting an appropriate key size based on current recommendations and best practices is imperative to prevent brute-force attacks and design a secure cryptographic system.
5. Impact of Private Key Compromise in Public-Key Cryptography
The compromise of a private key in public-key cryptography can have devastating effects on the security of the system and the information it protects. Here are some of the most significant effects of a major compromise:
An attacker can decrypt any messages or data encrypted with the corresponding public key if the private key is compromised. This compromises the privacy of sensitive information by allowing unauthorised access to encrypted communications, files, and any other data protected by the compromised key. An attacker with access to the private key can generate digital signatures that appear to be valid. This compromises the integrity of digitally signed messages or documents because an attacker can create fraudulent signatures that falsely authenticate their actions or tamper with the data integrity.
The compromise of a private key enables an attacker to assume the identity of the private key's owner. Using the private key, an attacker is able to impersonate a legitimate user and potentially gain unauthorised access to systems, services, or sensitive data associated with the compromised key. Public-key cryptography relies on the trust placed in an entity's public key. If the corresponding private key is compromised, the trust associated with the key pair is compromised. Other parties relying on the public key for encryption or authentication may no longer trust the compromised key, resulting in a breakdown in secure communication and possible disruption of trust relationships.
Once an attacker gains access to the private key, they can use it as a springboard to launch additional attacks. The compromised key can be used to conduct man-in-the-middle attacks, decrypt past or intercepted communications, or gain unauthorised access to other systems or resources protected by the compromised key. Once an attacker gains access to the private key, they can use it as a springboard to launch additional attacks. The compromised key can be used to conduct man-in-the-middle attacks, decrypt past or intercepted communications, or gain unauthorised access to other systems or resources protected by the compromised key.
Responding quickly to the incident is essential to mitigate the effects of a significant security breach. The compromised key should be revoked or rendered invalid, and affected parties should be notified to take the necessary steps, such as generating new key pairs, re-encrypting data, and re-establishing trust relationships. Regular key management practices, such as secure storage, protection against unauthorised access, and periodic key rotation, are required to minimise the effects of key compromises.
6. Cyber-Attacks on PK Cryptography
Cyber-assaults against Public Key (PK) Cryptography is a central concern in the modern digital landscape, where the relentless evolution of malicious tactics poses persistent threats to the security and integrity of cryptographic systems. PK Cryptography, a foundational element in securing digital communications, uses private and public keys to encrypt and decrypt information, ensuring confidentiality and authenticity in digital interactions.
However, the emergence of sophisticated cyberattacks aims to exploit vulnerabilities in this system to compromise private keys and gain unauthorised access to sensitive data. Brute-force attacks, for example, attempt to decipher encrypted messages by exhaustively exploring all possible private key combinations, utilising substantial computational power to penetrate the vast keyspace inherent to PK Cryptography.
The compromise of private keys can lead to many detrimental consequences, including breaches of confidentiality, erosion of trust, identity impersonation, and integrity compromise, which can have cascading effects on individual privacy, organisational security, and the overall reliability of digital communications. In addition, the legal and reputational repercussions of such breaches emphasise the need for robust cryptographic practises, vigilant security measures, and continuous advancements in cryptographic research to mitigate the risks associated with cyber-attacks and fortify PK Cryptography's resilience against the escalating threats in the cyber domain.
The multifaceted impact of cyber-attacks on PK Cryptography necessitates a comprehensive approach that integrates theoretical insights, practical implementations, and proactive risk management strategies to protect the security and integrity of cryptographic communications in an increasingly interconnected and vulnerable digital ecosystem.
7. Brute-Force Attack on PK Cryptography: Explaining the Concept and Its Limitations
A brute-force attack on Public Key (PK) cryptography occurs when an individual attempts to decrypt a secure message by systematically trying every possible private key. This type of attack is aimed directly at the cryptographic system, with the attacker relying on their computing power to test every possible key combination, hoping to find the correct one. The strength of PK cryptography lies in the vast keyspace it offers. This makes brute-force attacks computationally infeasible, particularly when dealing with long key sizes. The key space is so extensive that it is virtually impossible to explore all possibilities within a reasonable amount of time, even with substantial computational resources.
The Pivotal Role of Key Size in Thwarting Brute-Force Attacks
Search Space
In cryptographic systems, the size of the key directly affects the search space. A longer key size corresponds to a larger search space, exponentially increasing the number of potential keys an attacker must check during a brute-force attack. This expansion of possibilities significantly strengthens the cryptographic system's security, making it more resistant to breaches.
Time Complexity
The time complexity of a brute-force attack is inherent to the size of the key. A longer key increases complexity, necessitating additional time and computational power to explore all possible key combinations. This increased demand for computational resources and time acts as a deterrent, making brute-force attacks less appealing and more difficult for attackers to successfully execute.
Technological Advances
Constant technological advancements push the limits of computational capabilities. These developments could help attackers execute brute-force attacks more effectively. However, they also enable defenders to employ longer key sizes and more advanced cryptographic techniques, thereby balancing attack feasibility and defensive capabilities. To maintain security, staying abreast of technological advancements and adapting cryptographic practices is essential.
Security Margins
Technology advancements continue to push the limits of computational capabilities. These developments may enable brute-force attacks to be carried out more effectively. However, they also enable defenders to employ longer key sizes and more advanced cryptographic techniques, balancing attack viability and defensive capabilities. Staying abreast of technological advancements and adapting cryptographic practices to ensure long-term security is essential.
Technology advancements continuously push the limits of computational capabilities. These developments may enable brute-force attacks to be carried out more efficiently. However, they also enable defenders to employ longer key sizes and more complex cryptographic techniques, balancing attack feasibility and defensive capabilities. To ensure long-term security, it is essential to remain abreast of technological advancements and adjust cryptographic practices accordingly.
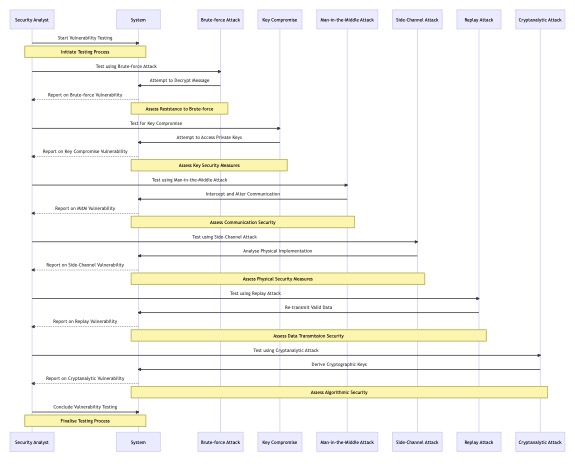
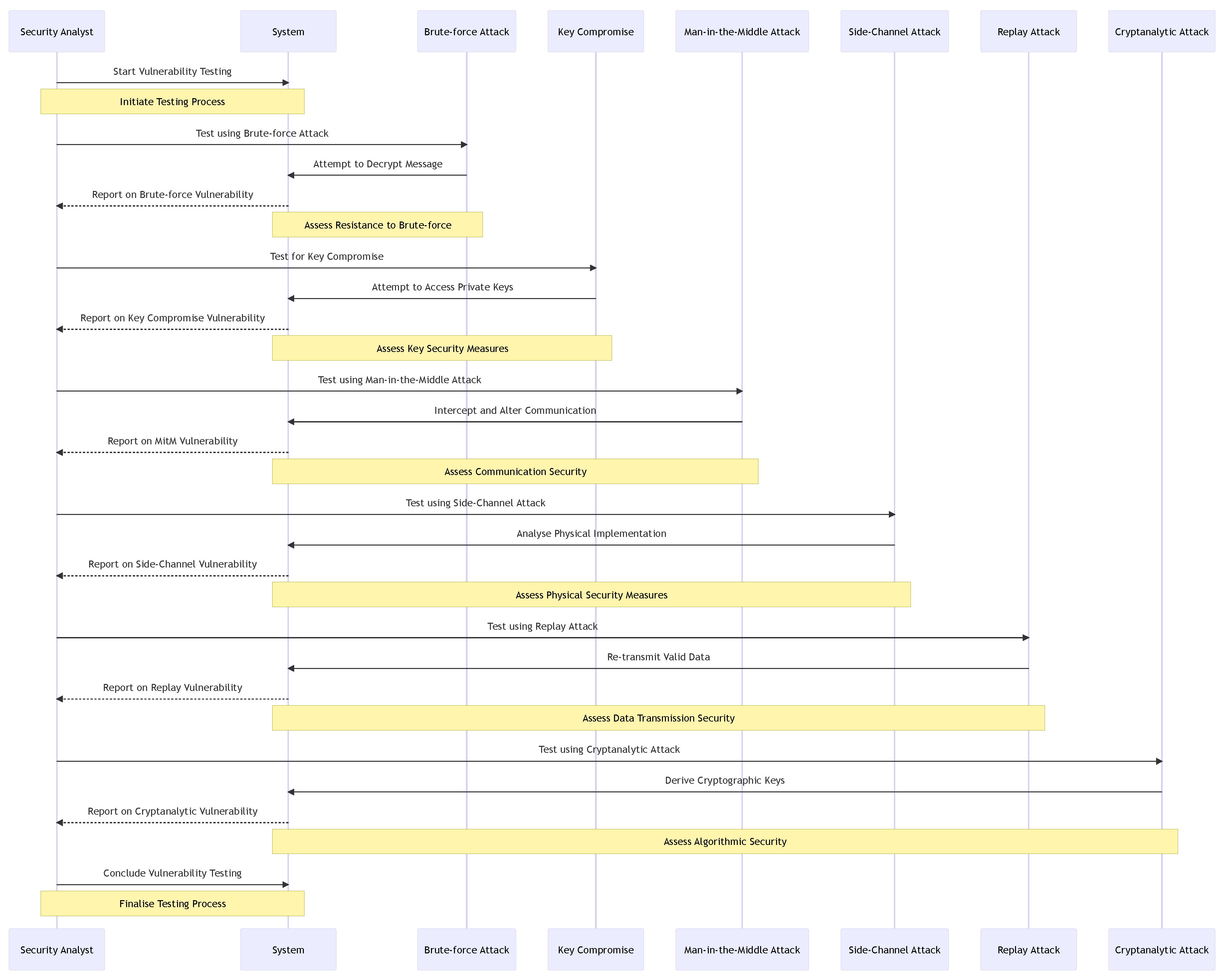
In we present a sequence diagram that illustrates how vulnerabilities are tested with individual attacks in a sequence for different vulnerabilities, using various attack methods in a systematic order.
Figure 1.
Sequence diagram for testing different vulnerabilities using various cyber-attack methods.
Figure 1.
Sequence diagram for testing different vulnerabilities using various cyber-attack methods.
8. Key Compromise
Importance of Protecting Private Keys
PK cryptography relies on the secrecy of the private key. If the private key is compromised through theft or unauthorised access, an attacker can decrypt any messages encrypted with the corresponding public key. Protecting private keys with strong encryption and proper access controls is crucial.
Key Compromise in Public Key Cryptography
Compromising cryptographic keys in Public Key (PK) cryptography can have far-reaching and multifaceted consequences, impacting various aspects of information security and trust. Herein, we explore the diverse repercussions of key compromise in PK cryptography.
Confidentiality Breach
A compromised key can result in a serious breach of confidentiality. Intruders who gain unauthorised access to private keys can decrypt sensitive data, exposing confidential information. This unauthorised access and disclosure can have negative effects on individuals and organisations, leading to a loss of privacy and the potential misuse of sensitive data.
Integrity Compromise
Information's accuracy and dependability are dependent upon its completeness and accuracy. A compromised key can enable malicious actors to alter the contents of encrypted messages, resulting in misinformation and data corruption. Such modifications can disrupt the normal flow of information and have ripple effects on dependent systems and decisions based on the altered data.
Identity Impersonation
In PK cryptography, compromised keys can facilitate identity impersonation. Attackers can use compromised keys to impersonate legitimate entities to gain unauthorised access to restricted resources and engage in malicious activities. This impersonation can result in unauthorised transactions and actions, causing considerable harm and confusion.
Trust Erosion
The foundation of secure communications is confidence. The compromise of cryptographic keys can erode trust between communicating parties because it raises questions about the authenticity and secrecy of the information being exchanged. The deterioration of trust can have lasting effects on relationships and collaborations between people, organisations, and systems.
Escalation of Attacks
A compromised key can allow an attacker to escalate their malicious activities. It can enable them to access additional resources, exploit vulnerabilities, and conduct more sophisticated and targeted attacks. The escalation of attacks can exacerbate damage and result in widespread security breaches.
Legal and Reputational Consequences
A compromised key can be a gateway for an adversary to escalate their malicious actions. It allows them to access additional resources, exploit vulnerabilities, and launch more sophisticated and targeted attacks. The escalation of attacks can intensify the damage and lead to widespread security breaches.
A compromised key can serve as a gateway for an attacker to escalate malicious activities. It can enable them to access additional resources, exploit vulnerabilities, and conduct more sophisticated and targeted attacks. The escalation of attacks can exacerbate the damage and result in widespread security breaches.
9. Man-in-the-Middle Attack on PK Cryptography
In a man-in-the-middle (MITM) attack, an attacker intercepts the communication between two parties and poses as each party to the other. The attacker can intercept the public keys exchanged during the key exchange process and replace them with their own. This allows the attacker to decrypt and read the messages exchanged between the legitimate parties. MITM attacks can be mitigated by using trusted public key infrastructure (PKI) and digital certificates.
How Attackers Intercept and Manipulate Communication
One of the main cybersecurity threats facing cryptographic systems is a Man-in-the-Middle (MitM) attack. This occurs when an unauthorised entity, the attacker, positions itself between two parties communicating. The attacker operates secretly by intercepting and manipulating the ongoing communication while remaining undetected by the authorised parties. This article explains the complex stages involved in the sophisticated methodology commonly used by attackers to orchestrate a MitM attack.
A Man-in-the-Middle (MitM) attack occurs when an unauthorised individual secretly positions themselves between two communicating parties. The unauthorised person then intercepts and manipulates the communication. These attacks often occur by intercepting transmissions, manipulating communication, and collecting sensitive information. The attacker may use various techniques to deceive the parties into thinking they're communicating directly and may even redirect traffic meant for one party to their system.
To safeguard against MitM attacks, it's essential to use secure communication protocols such as HTTPS, and verify the authenticity of digital certificates for secure connections. Robust end-to-end encryption should be employed for sensitive information, and it's crucial to frequently update software and devices to patch security holes. It's also wise to exercise caution when connecting to public or untrusted networks and to utilise a trusted and secure network infrastructure. Implementing these security measures can significantly reduce the risk of falling victim to MitM attacks.
Initially, the attacker gains access to the communication channel, a process known as Communication Interception. This can be achieved through numerous strategies, including exploiting insecure wireless networks, compromising essential network infrastructure such as routers or switches, or deploying malicious software within the target network or devices. Subsequently, the attacker situates themselves as a relay point, surreptitiously intercepting the traffic exchanged between the legitimate parties.
After the interception, the adversary engages in Entity Impersonation. Typically, they fabricate a false identity or impersonate a legitimate entity, employing techniques such as IP, MAC address, and DNS response spoofing to deceive communicating parties into believing they are in direct communication. In addition, attackers can employ ARP spoofing to redirect traffic to their system by associating their MAC address with the IP address of a legitimate entity.
With the intercepted communication in their possession, attackers manipulate the content, a stage known as Communication Manipulation. They can alter the messages or selectively obstruct, delay, or replay them, potentially leading to unauthorised actions or the disclosure of sensitive information. In addition, attackers may inject malicious code, such as malware or exploits, which compromises the security of the affected systems.
The final stage is Information Harvesting, in which attackers extract sensitive information, such as login credentials, financial information, or personal data, for malicious purposes such as identity theft, fraud, or to facilitate future attacks.
MitM attacks can manifest in various circumstances, such as insecure Wi-Fi networks, poorly encrypted connections, compromised network infrastructure, or by exploiting software and protocol vulnerabilities. It is essential to implement protective measures to strengthen defences against such attacks. These include the use of secure communication protocols such as HTTPS, which provides encryption and integrity validations; authenticating the legitimacy of digital certificates; employing robust end-to-end encryption for confidential data; implementing regular updates to address security vulnerabilities; exercising caution on public or untrusted networks; and employing secure and reputable network infrastructure. By adhering to these security protocols, the risk of falling victim to MitM attacks can be substantially reduced, thereby protecting sensitive data, and preserving the integrity of communication channels.
10. Side-Channel Attacks
Side-Channel Attacks and Their Impact on PK Cryptography
Side-channel attacks exploit information that is leaked during the execution of a cryptographic algorithm, such as timing data, power consumption, or electromagnetic radiation. An attacker may extract the private key by analysing this side-channel information. Side-channel attacks can be defended against countermeasures such as constant-time implementations and hardware protections.
Common Types of Side-Channel Attacks (Timing, Power, Electromagnetic)
Side-channel attacks extract sensitive data from a target system by exploiting data leaked through unintended channels, such as timing, power consumption, or electromagnetic emissions. Following are examples of typical side-channel attacks:
Timing Attacks
Timing attacks exploit variations in the execution time of cryptographic operations to obtain secret value information. By measuring the duration of specific operations, attackers can deduce sensitive data, such as secret keys. For instance, an adversary can measure the execution time of a cryptographic algorithm and use variations in execution time to deduce key bits.
Power Analysis Attacks
Attacks based on power analysis exploit the correlation between a device's power consumption and its internal computations. By analysing power consumption patterns during cryptographic operations, attackers can glean sensitive data, such as encryption keys. Power analysis attacks can be divided into two primary categories:
Simple Power Analysis (SPA): SPA involves analysing the power traces directly to identify patterns and extract information.
Differential Power Analysis (DPA): DPA involves statistically analysing multiple power traces to extract secret information. It is more powerful than SPA and can be used to attack even stronger countermeasures.
Electromagnetic Attacks
Electromagnetic attacks, or electromagnetic side-channel attacks (EM attacks), take advantage of electronic devices' electromagnetic radiation or emanations during operation. By capturing and analysing these emissions, attackers can extract sensitive information, such as encryption keys or processed data. EM attacks can be divided into two primary categories.:
Electromagnetic Emanation Analysis (EMA): EMA involves capturing and analysing the electromagnetic radiation emitted by a device to extract information.
Tempest Attacks: Tempest attacks involve capturing and analysing electromagnetic radiation from a distance to eavesdrop on a target system. These attacks can be conducted by monitoring electromagnetic signals that unintentionally leak from electronic devices.
Acoustic Attacks
Acoustic attacks utilise electronic devices' sound or acoustic emissions. An adversary can determine the device's internal state by analysing the sound produced during a cryptographic operation. For instance, an attacker could use a microphone with a high degree of sensitivity to record sound variations caused by CPU operations or key-dependent computations.
Optical Attacks
Optical attacks involve light emissions or variations in light intensity generated by electronic devices. Intruders can extract information by analysing light emissions during specific operations. During cryptographic computations, for instance, an adversary can detect light fluctuations caused by the fluctuating power consumption of a device.
These are only a few common side-channel attacks. Notably, side-channel attacks frequently necessitate physical proximity to the target device or specialised hardware for data capture and analysis. Implementing cryptographic algorithms with built-in protections, utilising secure hardware and software implementations, employing masking techniques, and implementing physical protections are countermeasures against side-channel attacks.
11. Quantum Computing Attacks
Quantum Computing on PK cryptography
Quantum computers have the potential to break many of the currently used public key algorithms, such as RSA and ECC (Elliptic Curve Cryptography). Shor's algorithm, for instance, can factor large numbers efficiently, thus breaking RSA. To mitigate quantum computing attacks, post-quantum cryptography algorithms that are resistant to quantum computing attacks are being developed and standardised.
12. Shor's Algorithm and Its Impact on RSA and ECC
Shor's algorithm is a quantum algorithm created in 1994 by the mathematician Peter Shor. It is designed to efficiently factor large composite numbers, which has significant implications for the security of RSA (Rivest-Shamir-Adleman) and ECC cryptographic schemes (Elliptic Curve Cryptography). Shor's algorithm, when executed on a large-scale quantum computer, can efficiently factorise large numbers, undermining RSA's security. ECC is also vulnerable to attacks using Shor's algorithm. Shor's algorithm can be adapted to solve the discrete logarithm problem efficiently on a large-scale quantum computer.
Impact on RSA
RSA is a popular algorithm for public-key encryption based on the difficulty of factoring large composite numbers into their prime factors. RSA's security is predicated on the assumption that factoring large numbers with traditional computers is computationally challenging. Nonetheless, Shor's algorithm, when executed on a large-scale quantum computer, can efficiently factorise large numbers, undermining RSA's security.
With Shor's algorithm, an attacker with a quantum computer could potentially factorise the large modulus used in RSA and derive the private key from the public key. This would allow the attacker to decrypt all encrypted messages, forge digital signatures, and potentially assume the identity of others.
Consequently, the security of RSA is compromised when large-scale quantum computers are present. Post-quantum cryptography (PQC) research focuses on developing quantum-resistant public-key encryption schemes as a countermeasure to this threat.
Impact on ECC
ECC is a widely used public-key cryptography scheme that operates on the mathematics of elliptic curves. Compared to other public-key algorithms such as RSA, it offers robust security with relatively small key sizes. However, ECC is also susceptible to Shor's algorithm-based attacks.
The discrete logarithm problem can be efficiently solved on a large-scale quantum computer by adapting Shor's algorithm. The discrete logarithm problem is the basis for ECC's security. An attacker could compromise the security of ECC by calculating the private key from the public key by solving the discrete logarithm problem.
Similar to RSA, the impact of Shor's algorithm on ECC has prompted research into developing post-quantum cryptographic algorithms that offer resistance to quantum attacks. These post-quantum ECC alternatives, also known as "quantum-resistant ECC" or "post-quantum ECC," aim to provide the same security guarantees as ECC, but in an era of quantum computing.
Shor's algorithm poses a significant threat to the security of RSA and ECC because, when executed on a large-scale quantum computer, it can efficiently break their underlying mathematical assumptions. In the presence of quantum computers, developing and adopting post-quantum cryptographic algorithms are crucial for ensuring secure communication and data protection.
Quantum-Safe Cryptography
Quantum-safe cryptography, or post-quantum cryptography (PQC), refers to cryptographic protocols and algorithms designed to withstand quantum computer attacks. Due to the potential danger posed by quantum computers to classical cryptographic systems, it is of the utmost importance in cybersecurity. Here are the reasons why quantum-safe cryptography is essential for cybersecurity:
Quantum computers pose a danger to classical cryptography. Quantum computers have the potential to break many of the widely used cryptographic algorithms that rely on the difficulty of problems, such as factoring large numbers (RSA) or computing discrete logarithms (Diffie-Hellman, ECC). Shor's quantum algorithm can efficiently factorise large numbers and solve the discrete logarithm problem, making these algorithms susceptible to attacks.
Quantum-safe cryptography is designed to provide long-term security assurance. Numerous cryptographic systems in use today necessitate the secure transmission and storage of data for extended durations, sometimes decades. The development and widespread adoption of quantum-safe algorithms ensures that data encrypted with these algorithms will remain secure in the face of future quantum computing advancements.
The transition to quantum-safe cryptography is not a process that occurs overnight. It calls for meticulous planning, development, standardisation, and adoption. By starting the transition early, organisations can ensure they are prepared for the quantum computing era and avoid potential vulnerabilities or compromises due to the sudden availability of quantum computers.
Multiple sectors, including the government, financial institutions, healthcare, and critical infrastructure, deal with highly sensitive and confidential data. Quantum-safe cryptography guarantees the continued security of these data against potential quantum computer attacks. Without the implementation of quantum-safe algorithms, sensitive data could be at risk of exposure and compromise.
Infrastructure and Systems Security: Quantum-safe cryptography is indispensable for securing vital infrastructure, networks, and systems. It provides a solid basis for secure communication, storage, authentication, digital signatures, and other cryptographic features. Quantum-safe algorithms assist in mitigating the risks associated with quantum attacks, ensuring the integrity and secrecy of sensitive data.
By adopting quantum-safe cryptography, organisations can protect their systems and infrastructure against the potential threats posed by quantum computers. This proactive approach enables them to maintain the secrecy, integrity, and accessibility of their data and systems despite the rapid evolution of technology.
Efforts are underway to develop and standardise quantum-safe cryptographic algorithms, such as lattice-based cryptography, code-based cryptography, and multivariate cryptography. These algorithms aim to resist attacks from classical and quantum computers, ensuring the security of sensitive information in a quantum computing era.
As the world moves toward a future with more powerful quantum computers, quantum-safe cryptography plays a crucial role in maintaining a strong cybersecurity posture, protecting sensitive data, and ensuring the security of critical systems and infrastructure.
13. Case Studies
Implementation of Smart Contracts in the Insurance Industry
Real-World Applications and Results
The implementation of smart contracts has revolutionised claims processing and policy management in the insurance industry. The use of blockchain-based smart contracts to automate the verification of events or conditions that trigger insurance payouts, thereby enabling instantaneous and transparent settlements, is illustrative. Not only has this application streamlined the insurance process, but it has also significantly reduced administrative costs, fostering greater trust between insurers and policyholders. Smart contracts' automation eliminates the lengthy waiting periods traditionally associated with insurance claims, enhancing customer satisfaction and operational efficiency.
Lessons Learned
Incorporating smart contracts in the insurance industry has highlighted the significance of transparency and automation in fostering trust and enhancing productivity. The lessons learned from these implementations highlight the need for continuous innovation to address policyholders' changing needs and expectations and to keep up with technological advancements in the fields of blockchain and smart contracts.
Implementation of Smart Contracts in Real Estate
Real-world Applications and Results
Real estate transactions, including property transfers, rental agreements, and escrow services, have been simplified and automated with the assistance of smart contracts. The use of smart contracts to facilitate secure and transparent ownership transfers and automate payment schedules, ensuring compliance with predefined rules and regulations, is a prime example. This technology has reduced the need for middlemen, enhancing the efficiency and safety of real estate transactions. Reducing the need for intermediaries has reduced associated costs and potential disputes, thereby making transactions more efficient and user-friendly.
Lessons Learned
The implementation of smart contracts in real estate transactions has highlighted the central role of technology in enhancing property transactions' security and efficacy. These applications have demonstrated the transformative potential of smart contracts in the real estate industry and paved the way for future innovations and refinements in applying blockchain technology in this field.
Implementation of Smart Contracts in Intellectual Property Management
Real-world Applications and Results
Intelligent contracts have emerged as a viable method for managing and safeguarding intellectual property rights. One example is the creation of smart contracts for automated licencing, royalty distribution, and tracking of usage rights. These contracts have provided a transparent and auditable system for managing intellectual property rights, allowing creators to receive fair compensation. The automation of royalty payments ensures that creators are promptly and accurately compensated based on the actual usage of their intellectual property, promoting fairness and transparency in intellectual property management.
Lessons Learned
The application of smart contracts in intellectual property management has revealed the blockchain's potential for ensuring equitable compensation and transparent management of intellectual assets. The insights gleaned from these implementations have highlighted the importance of developing robust and secure smart contracts to address the unique challenges associated with intellectual property rights and have encouraged the continuation of research and development in this area.
14. Discussion
Summary of Findings
Public-key cryptography employs a pair of keys consisting of a public key and a private key. The keys are mathematically related, but deriving one from the other is computationally impossible. The public key is widely disseminated, while the private key is kept confidential.
Encryption is the process of transforming plaintext (the original message) into ciphertext (the encrypted message) using the recipient's public key. The recipient is the only person who can decrypt the ciphertext using their private key.
Using the recipient's private key, decryption is the process of converting ciphertext back into plaintext. Only the recipient with the private key can decrypt the ciphertext and recover the original message.
In PK cryptography, digital signatures provide authentication and integrity verification. By applying a cryptographic algorithm to a message with the sender's private key, a digital signature is generated. Using the sender's public key, anyone can verify the signature, ensuring the message's authenticity and detecting tampering.
PKI is a system of policies, procedures, and technologies that manage the creation, distribution, and verification of digital certificates. It establishes trust by associating public keys with their respective entities and providing a secure communication and authentication framework.
Digital certificates are electronic documents issued by a reputable Certification Authority (CA) that bind the identity of an entity to its public key. Certificates include details such as the entity's name, public key, duration of validity, and the CA's digital signature. Digital certificates are utilised for authentication, encryption, and the validation of data integrity.
PK cryptography enables secure key exchange over an insecure channel between two parties. Parties can freely exchange their public keys, which enables them to derive a shared secret key without transmitting it directly. This shared secret key is then used for symmetric encryption to protect the secrecy and integrity of subsequent communications.
Comparison with Previous Research
This chat provides an in-depth examination of several facets of cryptography, focusing on the implications of key compromises in Public Key Cryptography and the complexities of brute-force attacks. Prior research in this field has primarily focused on the development of more secure cryptographic algorithms and their technical aspects. The current discussion, however, transcends the technical realm, delving into the multifaceted repercussions of key compromises and the practical implications of cryptographic practises. It offers a comprehensive perspective, intertwining technical, practical, and theoretical insights, thereby contributing to a more holistic understanding of the subject matter.
Theoretical and Practical Implications
This conversation has substantial theoretical ramifications, shedding light on the underlying cryptographic principles, inherent vulnerabilities, and potential attack vectors. It explains the fundamental concepts of cryptographic security, such as the significance of key sizes and the function of encryption algorithms and provides a theoretical framework for future research and development in this area.
The discussion emphasises the practical implications of key compromises in Public Key Cryptography, highlighting the importance of maintaining the confidentiality and integrity of cryptographic keys. It illuminates the practical difficulties associated with protecting keys and the repercussions of failing to do so, including breaches of confidentiality, trust erosion, and legal and reputational repercussions. These practical insights are essential for organisations and individuals to implement robust security measures and cryptographic practices to mitigate the risks associated with key compromises.
Recommendations for Future Research
Future research should investigate the creation of enhanced security protocols and encryption algorithms to bolster the resistance of cryptographic systems to key compromises and brute-force attacks. It is essential to investigate novel techniques for enhancing the security of private keys to combat the evolving threat landscape.
There is a need for more extensive research on the multifaceted effects of key compromises, focusing on the long-term effects on individuals, organisations, and overall trust in cryptographic communications. A comprehensive impact analysis can provide a deeper understanding of the repercussions of key compromises and inform the development of more effective mitigation strategies.
Future research should delve into user-centric security measures, examining end-users role in maintaining cryptographic security and the challenges of user compliance with security protocols. Research in this area can contribute to developing user-friendly security solutions and awareness programmes to enhance overall cryptographic security.
It is necessary to investigate further the legal and ethical factors associated with key compromises in Public Key Cryptography. Understanding the legal frameworks and ethical dilemmas surrounding cryptographic practises can inform the creation of cryptographic policies and ethical guidelines.
Analysis Due to the constant evolution of cyber threats, it is essential to conduct ongoing research to remain abreast of emerging attack vectors and vulnerabilities. An in-depth analysis of the advanced threat landscape can facilitate anticipating potential security challenges and the development of proactive defence mechanisms.
As a result of the constant evolution of cyber threats, ongoing research is necessary to stay abreast of new attack vectors and vulnerabilities. A comprehensive analysis of the advanced threat landscape can aid in anticipating potential security challenges and developing proactive defences.
15. Conclusion
Review of Key Findings
To maintain a strong cybersecurity posture, it is essential to be aware of potential attacks and to adopt secure practices. In the conclusion chapter, we focus more on why awareness and secure practices are essential.
The threat landscape constantly evolves, with new attack techniques and vulnerabilities appearing regularly. Awareness of potential attacks, such as phishing, malware, ransomware, social engineering, and distributed denial-of-service (DDoS) attacks, enables individuals and organisations to remain vigilant and take the necessary precautions for protection.
Personal and sensitive information, including financial data, intellectual property, and identities, is extremely valuable to attackers. Secure practices, such as strong passwords, encryption, multi-factor authentication, and data backups, protect this data and prevent unauthorised access, disclosure, or misuse.
Mitigation of Financial Losses: Cyberattacks can have severe financial implications, ranging from direct financial losses to operational disruptions and reputational damage. Individuals and organisations can reduce the likelihood of financial losses due to data breaches, system compromises, or fraudulent activities by being aware of potential attacks and implementing secure practices.
Privacy is a fundamental right, and protecting personal information is paramount. Individuals aware of privacy-related threats, such as data breaches and unauthorised surveillance, can take the necessary precautions to protect their privacy. Utilising privacy-enhancing technologies, exercising caution when sharing personal information online, and routinely reviewing privacy settings all protect privacy.
Prevention of Identity Theft: In the digital age, identity theft is a major concern. To impersonate individuals, commit financial fraud, or engage in other malicious activities, attackers may attempt to steal personal information. Individuals can recognise and avoid identity theft attempts by understanding techniques such as phishing, social engineering, and fake websites.
Prevention of Identity Theft: Identity theft is a major concern in the digital era. Attackers may attempt to steal personal information to impersonate individuals, commit financial fraud, or engage in other malicious activities. By being aware of techniques such as phishing, social engineering, and fake websites, individuals can recognise and avoid potential identity theft attempts.
Identity theft prevention is crucial in the digital age. Attackers may attempt to steal personal information to impersonate users, commit financial fraud, or engage in other malicious activities. By understanding techniques such as phishing, social engineering, and fake websites, individuals can identify and avoid potential identity theft attempts.
Prevention of Identity Theft: In the digital age, identity theft is a major concern. To impersonate individuals, commit financial fraud, or engage in other malicious activities, attackers may attempt to steal personal information. Individuals can recognise and avoid identity theft attempts by understanding techniques such as phishing, social engineering, and fake websites.
Awareness of potential attacks and adopting secure practices are crucial for protecting sensitive information, mitigating financial losses, protecting privacy, preventing identity theft, ensuring compliance, promoting a security culture, and proactively managing risks. Individuals and organisations can increase their resilience against cyber threats and contribute to a safer digital environment by remaining informed and adhering to secure practices.
Contributions of the Study
This research significantly contributes to the existing body of knowledge in the field of cryptography, focusing specifically on Public Key Cryptography. It provides a nuanced understanding of the potential vulnerabilities and the repercussions associated with key compromises. This study offers a holistic perspective on the challenges and considerations involved in implementing cryptographic practices by examining cryptographic security's theoretical foundations and practical implications. It goes beyond the technical aspects and delves into the real-world impacts, such as legal and reputational repercussions, thereby enriching the discussion on cryptographic security. This study's findings are crucial for informing future cryptographic research, policy development, and implementation, fostering a more secure and resilient digital environment.
Recommendations for Enhanced Awareness and Education in Practice
Organisations and individuals must be aware of the evolving threat landscape and potential cryptographic system attacks. Regular training and awareness programmes can be instrumental in fostering a security culture and ensuring the observance of secure procedures. Enhanced awareness and education are fundamental for protecting sensitive data, preventing identity theft, and mitigating financial losses.
Compliance with Regulations and Standards
It is essential to strictly follow cryptographic practices' regulations and standards. Regularly reviewing and updating security policies is necessary to comply with legal requirements and industry standards. By adhering to these regulations and standards, you can avoid legal penalties, maintain your reputation, and create a secure and ethical cryptographic environment.
Acknowledgements
Eternal gratitude to the Fulbright Visiting Scholar Project.
References
- H. G. Liddell, A greek-english lexicon. Harper, 1894.
- M. Braverman, Y. K. Ko, and O. Weinstein, “Approximating the best Nash Equilibrium in no (1ogn)-time breaks the exponential time hypothesis,” Proc West Mark Ed Assoc Conf, vol. 2015-Janua, no. January, pp. 970–982, 2015. https://doi.org/10.1137/1.9781611973730.66. [CrossRef]
- C. Paar and J. Pelzl, Understanding cryptography: a textbook for students and practitioners. Springer Science & Business Media, 2009.
- H. Feistel, “Block cipher cryptographic system,” Mar. 19, 1971.
- R. L. Rivest, A. Shamir, and L. Adleman, “A method for obtaining digital signatures and public-key cryptosystems,” Commun ACM, vol. 21, no. 2, pp. 120–126, 1978. [CrossRef]
- GDPR, “What is GDPR, the EU’s new data protection law? - GDPR.eu,” 2018. https://gdpr.eu/what-is-gdpr/ (accessed Jul. 07, 2023).
- ICO, “Information Commissioner’s Office (ICO): The UK GDPR,” UK GDPR guidance and resources, 2018. https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/lawful-basis/a-guide-to-lawful-basis/lawful-basis-for-processing/consent/ (accessed Jul. 08, 2023).
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).