Submitted:
14 August 2023
Posted:
16 August 2023
You are already at the latest version
Abstract
Keywords:
I. Introduction
| consensus algorithm | tasks of reaching agreements | time overhead to reach agreements |
|---|---|---|
| BGP | 4 | exponential |
| PBFT | 4 | exponential |
| DAG | 3 | polynomial |
| LCAG | 2 | polynomial |
II. Related Work
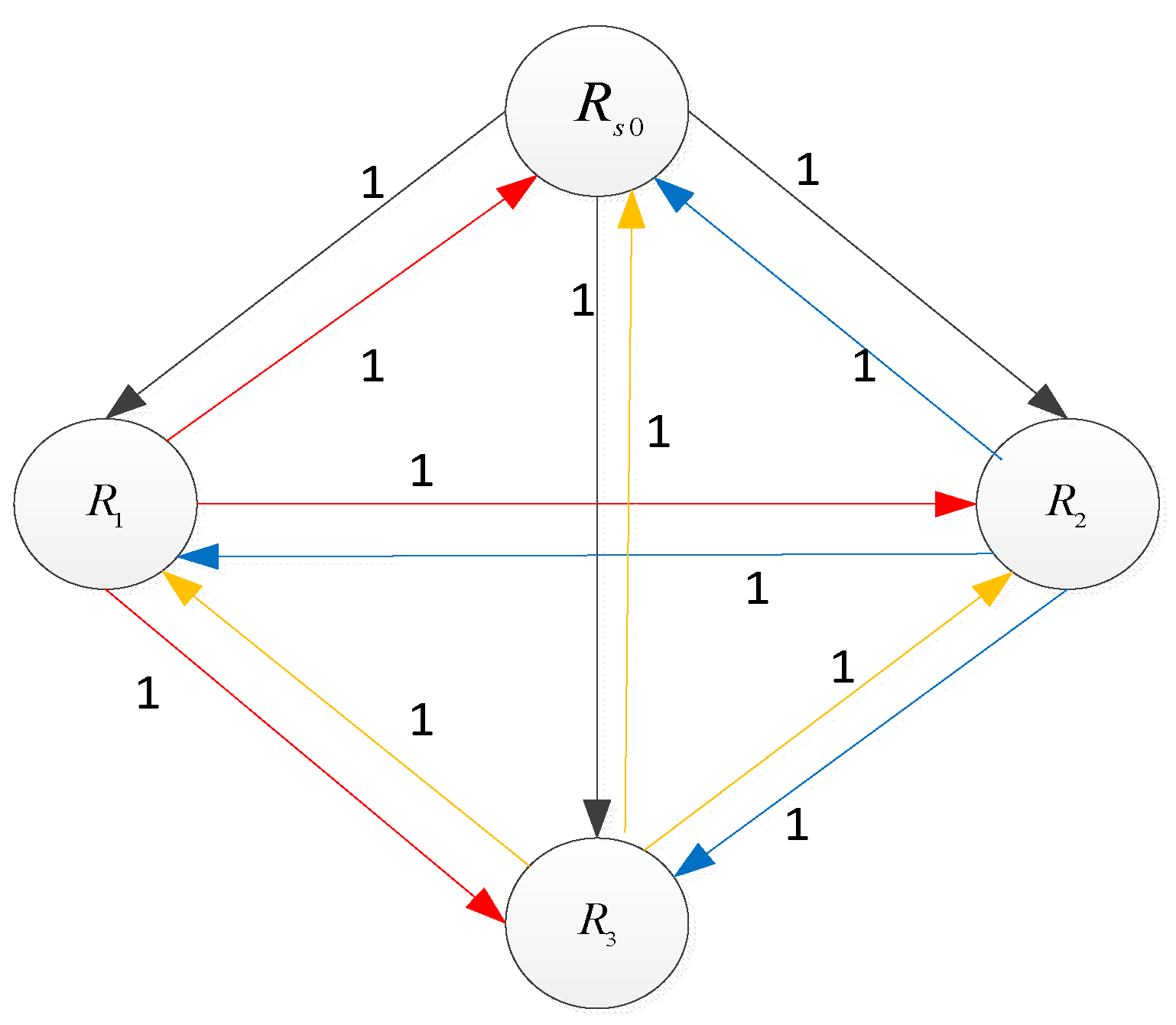
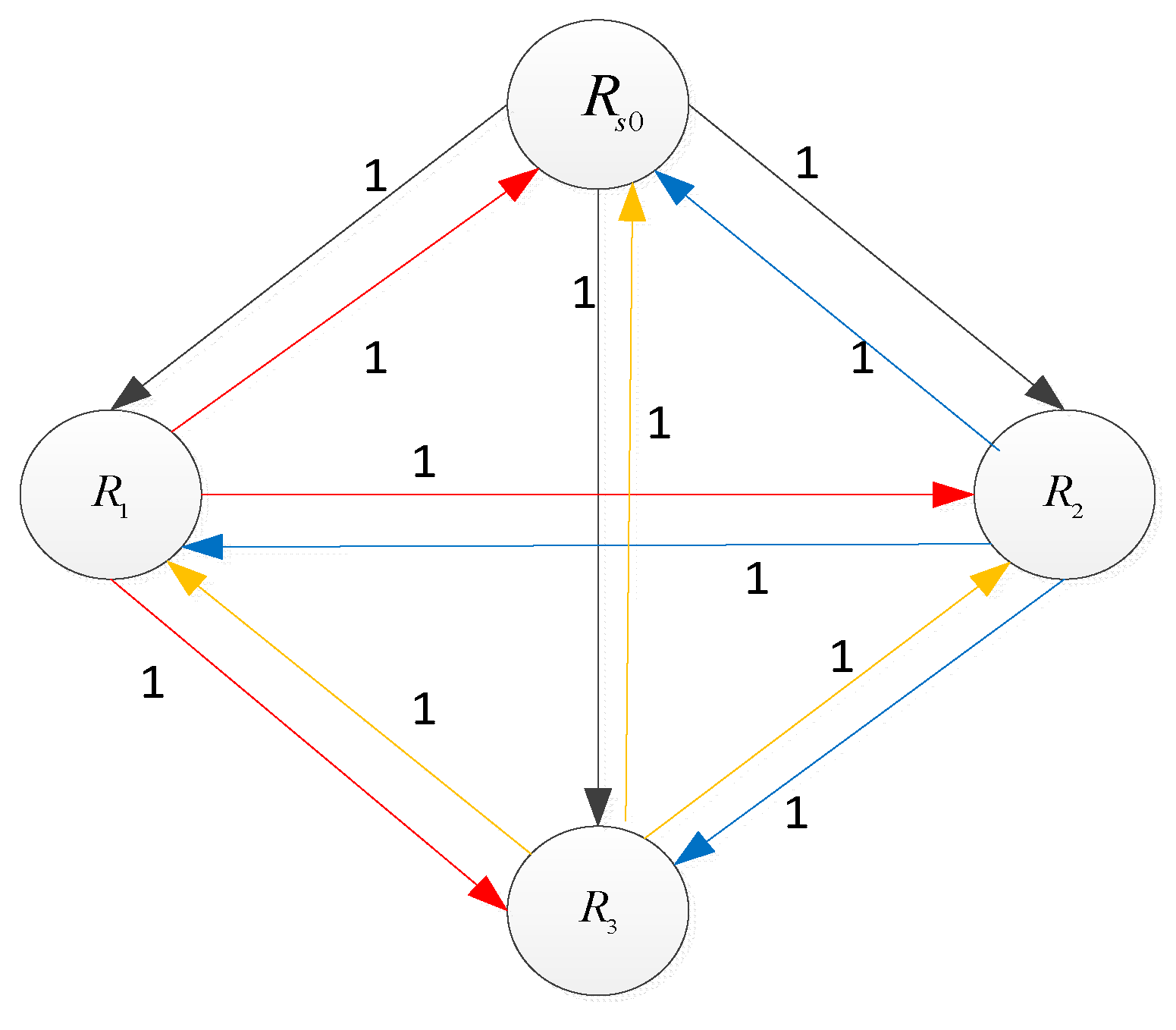
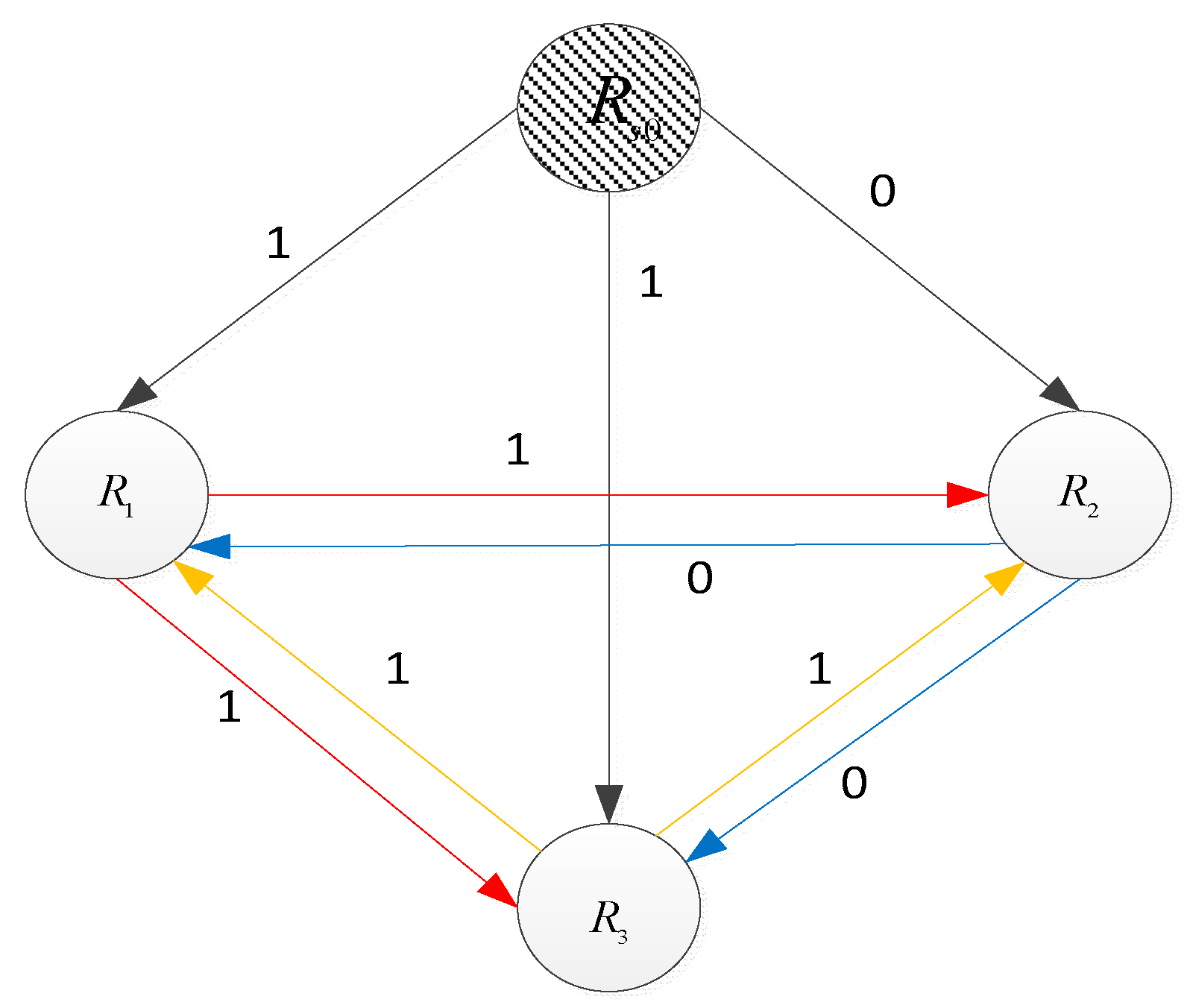
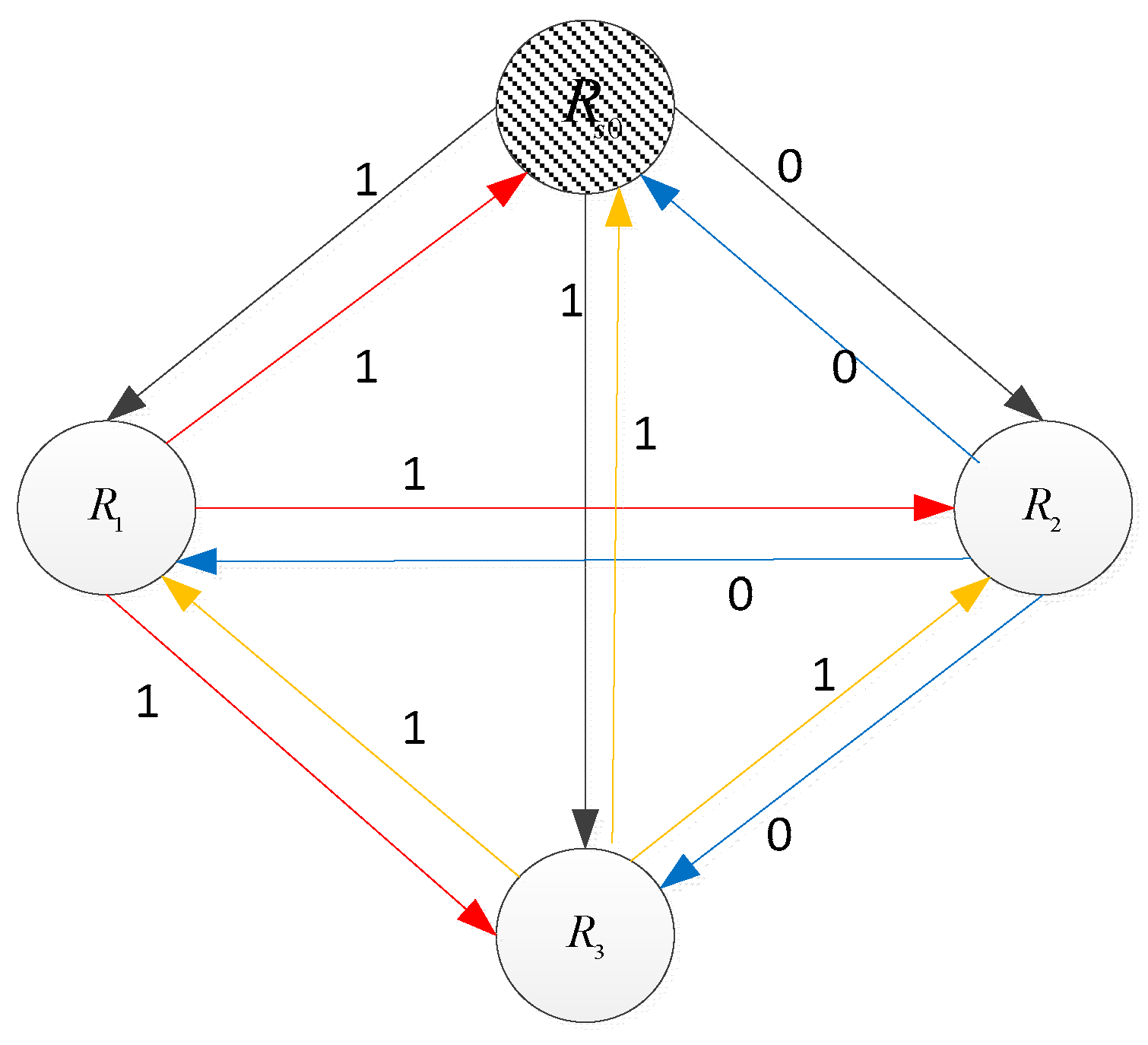
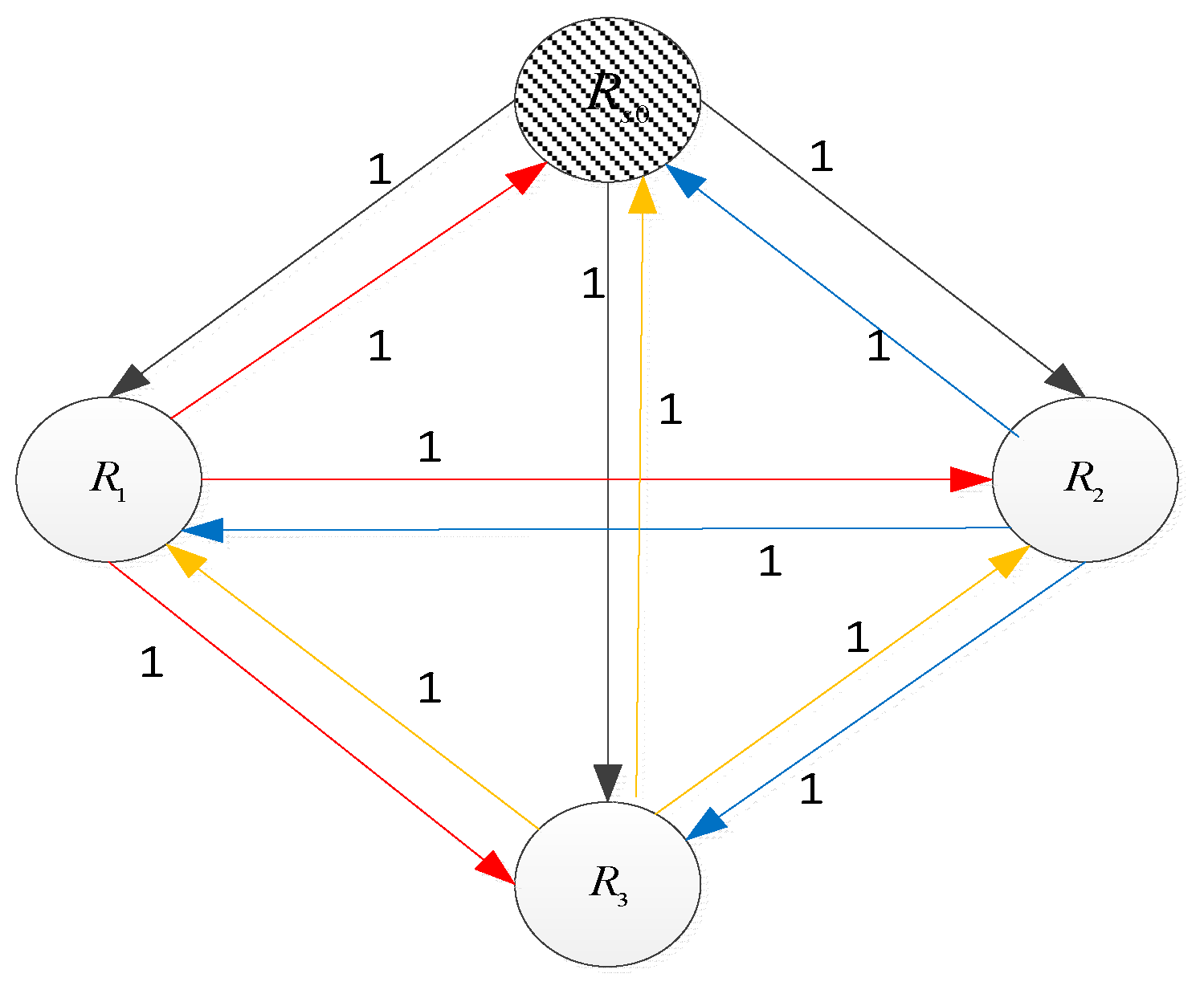
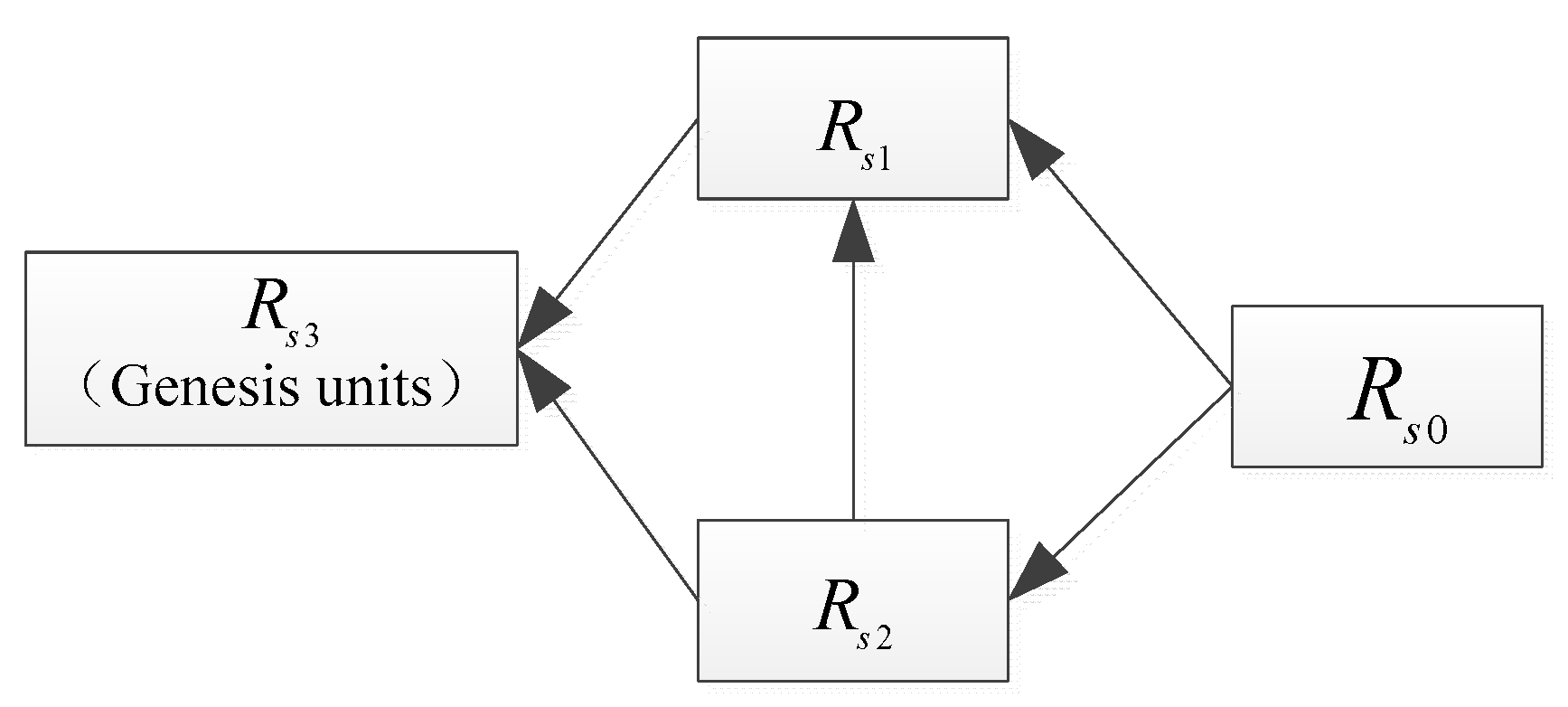
III. The Lcag Algorithm
A. The Related Graph Theory
B. LCAG’s Design
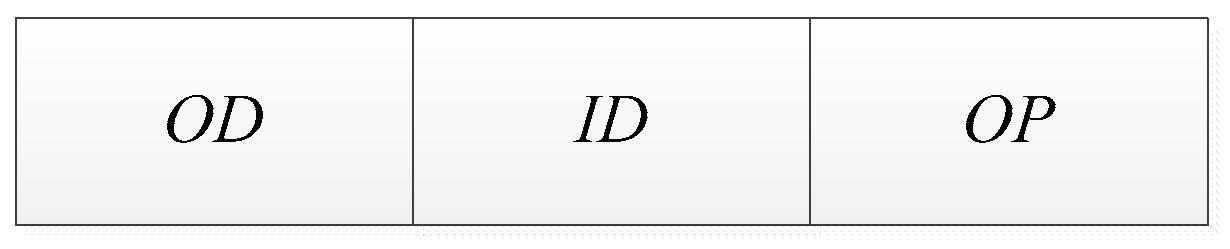
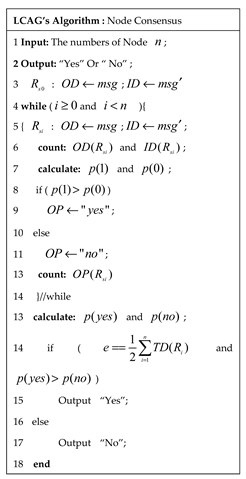 |
C. LCAG’s Provable Security Analysis
IV. Experiment
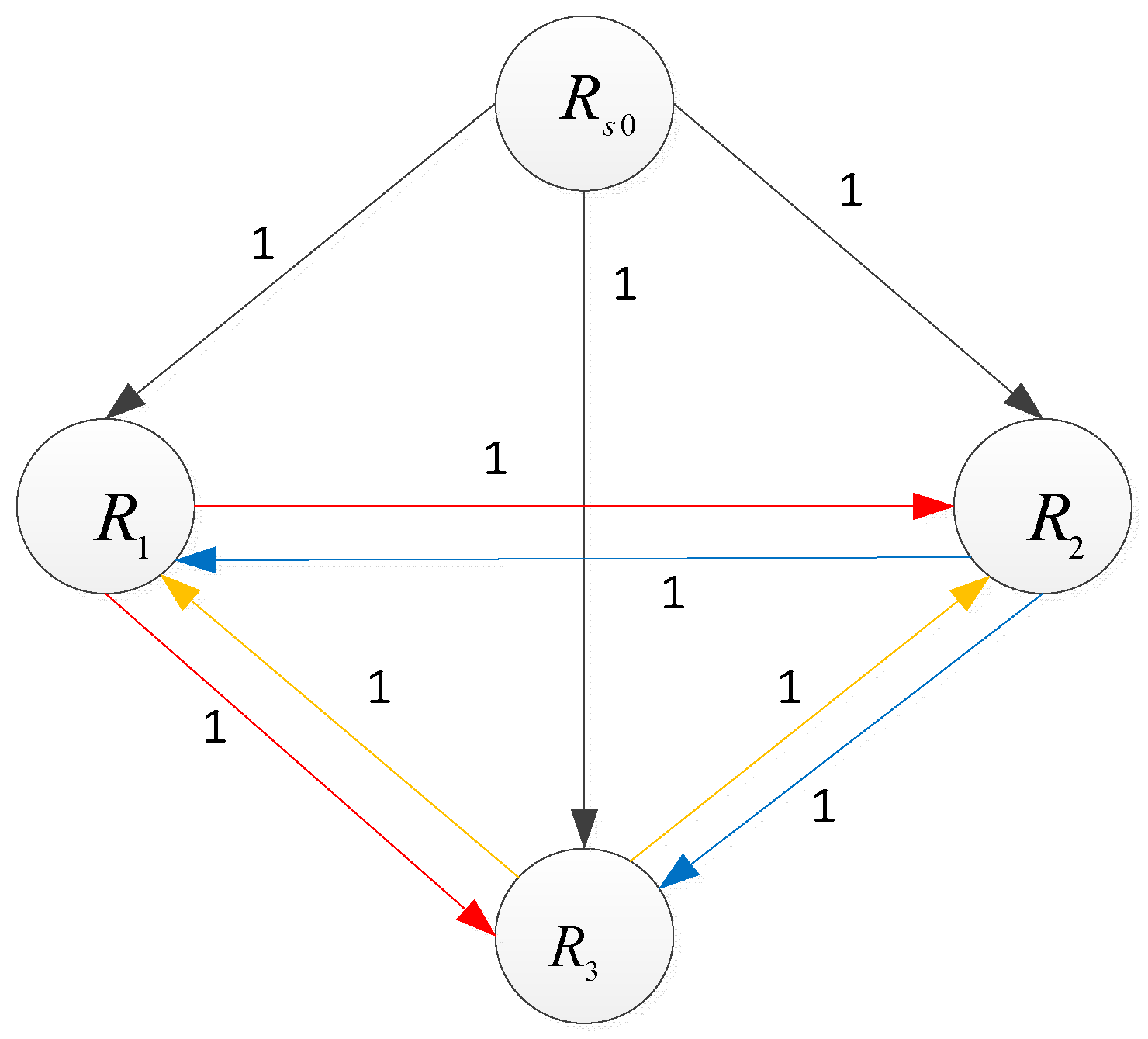
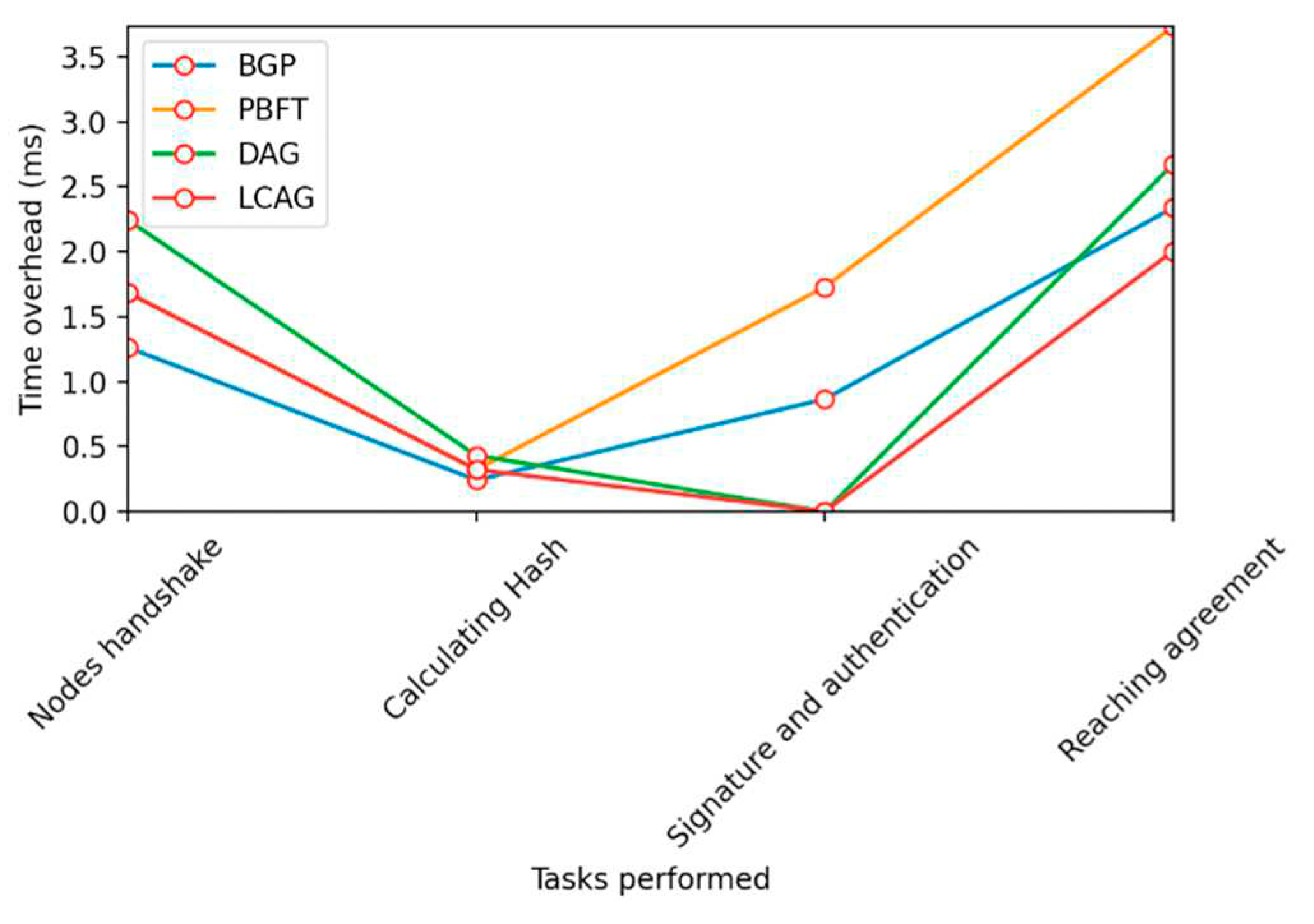
A. The Ideal Situation
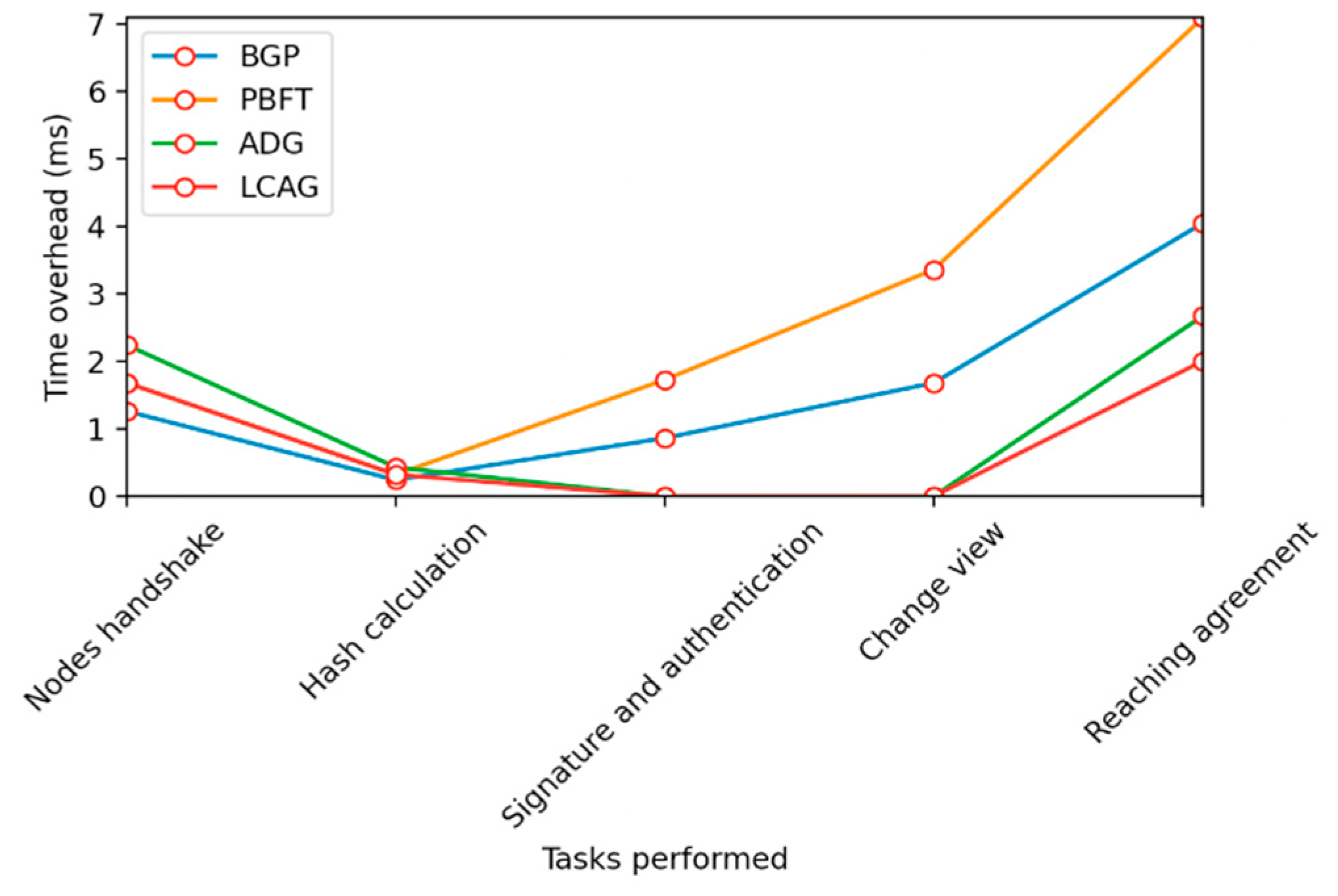
B. The Situation with Disloyal Nodes
C. Experiment Analysis
| Consensus algorithm | Transmitting messages | Calculating Hash | Signature and authentication | View change |
|---|---|---|---|---|
| BGP | √ | √ | √ | √ |
| PBFT | √ | √ | √ | √ |
| DAG | √ | √ | ||
| LCAG | √ | √ |
| Consensusalgorithm | Nodes handshake | Calculating Hash | Signature and authentication | Reachingagreement |
|---|---|---|---|---|
| BGP | 1.2609 | 0.2421 | 0.8637 | 2.3667 |
| PBFT | 1.6812 | 0.3228 | 1.7274 | 3.7314 |
| DAG | 2.2416 | 0.4304 | 0 | 2.672 |
| LCAG | 1.6812 | 0.3228 | 0 | 2.004 |
 |
| Consensusalgorithm | Nodes handshake | Calculating Hash | Signature and authentication | View change | Reaching agreement |
|---|---|---|---|---|---|
| GP | 1.2609 | 0.2421 | 0.8637 | 1.6812 | 4.0479 |
| PBFT | 1.6812 | 0.3228 | 1.7274 | 3.3624 | 7.0938 |
| DAG | 2.2416 | 0.4304 | 0 | 0 | 2.672 |
| LCAG | 1.6812 | 0.3228 | 0 | 0 | 2.004 |
V. Conclusion and Future Work
References
- NAKAMOTO, S. Bitcoin: A peer-to-peer electronic cash system[EB/OL]. 2008. https://bitcoin.org/bitcoin.
- Cheng CF, et al. Reaching Consensus with Byzantine Faulty Controllers in Software-Defined Networks. Wireless Communications and Mobile Computing. 2021 Apr 12;2021.
- Yazdinejad A, et al. Slpow: Secure and low latency proof of work protocol for blockchain in green iot networks. In2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring) 2020 (pp. 1-5). IEEE. 25 May.
- LAMPORT L, SHOSTAK R E, PEASE M C. The Byzantine Generals Problem[J]. ACM Transactions on Programming Languages and Systems (TOPLAS) 1982, 4, 382–401. [Google Scholar] [CrossRef]
- LIU Yi-Zhong, LIU Jian-Wei,ZHANG Zong-Yang,XU Tong-Ge,YU Hui1. Overview on Blockchain Consensus Mechanisms. Journal of Cryptologic Research 2019, 6, 395–432. [Google Scholar]
- CASTRO M, LISKOV B. Practical Byzantine fault tolerance[C]. In: Proceedings of the Third USENIX Symposium on Operating Systems Design and Implementation (OSDI). 1: New Orleans, LA, USA, –25, 1999, 22 February 1999; 25.
- Sergio, D.L. : DagCoin: a cryptocurrency without blocks. https://bitslog.wordpress.
- Demers, Alan, et al. "Epidemic algorithms for replicated database maintenance." Acm Sigops Operating Systems Review 22.
- YUAN Yong, NI Xiao-Chun, ZENG Shuai,WANG Fei-Yue. Blockchain Consensus Algorithms: The State of the Art and Future Trends. ACTA AUTOMATICA SINICA. 2018, 44, 2011−2022.
- LAMPORT, L. The part-time parliament[J]. ACM Transactions on Computer Systems (TOCS) 1998, 16, 133–169. [Google Scholar] [CrossRef]
- Cowling J, Myers D, Liskov B, Rodrigues R, Shrira L. HQ replication: A hybrid quorum protocol for Byzantine fault tolerance. In: Proc. of the 7th Symp. on Operating Systems Design and Implementation. Berkeley: USENIX Association, 2006.
- Xu Hao, Long Yu, Liu Zhiqiang, Liu Zhen, Gu Dawu. Dynamic Practical Byzantine Fault Tolerance. 2018.
- ABRAHAM I, GUETA G, MALKHI D. Hot-stuff the linear, optimal-resilience, one-message BFT devil[EB/OL]. 2018. https://arxiv.org/pdf/1803.05069.pdf.
- GOLAN-GUETA G, ABRAHAM I, GROSSMAN S, et al. SBFT: A scalable decentralized trust infrastructure for Blockchains[EB/OL]. 2018. https://arxiv.org/pdf/1804.01626.pdf.
- GAO Zheng-Feng, ZHENG Ji-Lai,TANG Shu-Yang,LONG Yu,LIU Zhi-Qiang, LIU Zhen,GU Da-Wu. State-of-the-art Survey of Consensus Mechanisms on DAG-based Distributed Ledger. Journal of Software, 2020, 31, 1124−1142.
- Chong B. State-of-the-Art and Future Trends of Blockchain Based on DAG Structure[C]// International Workshop on Structured Object-Oriented Formal Language and Method. 2018.
- RUIZHANG,RUIXU,LING LIU. Security and Privacy on Blockchain. ACM Comput. Surv. 5: Article 51 (19), 20 July 5111.
- Yang R, Yu F R, Si P, et al. Integrated Blockchain and Edge Computing Systems: A Survey, Some Research Issues and Challenges[J]. 1: IEEE Communications Surveys & Tutorials 2019, PP(99), 2019.
- Liu W, Cao B, Zhang L, et al. A Distributed Game Theoretic Approach for Blockchain-based Offloading Strategy[C]// IEEE International Conference on Communications. IEEE, 2020.
- S Lee, M Kim, J Lee, RH Hsu, TQS Quek. Latency Modeling of Hyperledger Fabric for Blockchain-based IoT (BC-IoT) Networks. https://arxiv.org/abs/2102.09166.
- Yin B, Wu Y, Hu T, et al. An Efficient Collaboration and Incentive Mechanism for Internet of Vehicles (IoV) With Secured Information Exchange Based on Blockchains[J]. IEEE Internet of Things Journal 2019, PP(99):1-1.
- Qiu C, Yu F R, Xu F, et al. 28 October 2018; 18.
- Jiang X, Yu F R, Song T, et al. Blockchain-Enabled Cross-Domain Object Detection for Autonomous Driving: A Model Sharing Approach[J]. IEEE Internet of Things Journal 2020, PP(99):1-1.
- Niu J, Li X, Gao J, et al. Blockchain-Based Anti-Key-Leakage Key Aggregation Searchable Encryption for IoT[J]. IEEE Internet of Things Journal 2020, 7, 1502–1518.
- Ma Zhaofeng,Wang Lingyun,Wang Xiaochang,Wang Zhen,Zhao Weizhe. Blockchain-Enabled Decentralized Trust Management and Secure Usage Control of IoT Big Data. 1: IEEE Internet of Things Journal PP(99).
- Hamdaoui B, Alkalbani M, Rayes A, et al. IoTShare: A Blockchain-Enabled IoT Resource Sharing On-Demand Protocol for Smart City Situation-Awareness Applications[J]. IEEE Internet of Things Journal 2020, PP(99):1-1.
- Cao B, Wang R, Sabbagh A, et al. Expected File-Delivery Time of DTN Protocol over Asymmetric Space Internetwork Channels[C]// 2018 6th IEEE International Conference on Wireless for Space and Extreme Environments (WiSEE). IEEE, 2018.
- Stefano Savazzi, Monica Nicoli and Vittorio Rampa. Federated Learning With Cooperating Devices: AConsensus Approach for Massive IoT Networks. IEEE INTERNET OF THINGS JOURNAL. 2022, 7, 4641–4654.
- Sujit Biswas, Kashif Sharif, Fan Li,et al. PoBT: A Lightweight Consensus Algorithm for Scalable IoT Business Blockchain. IEEE INTERNET OF THINGS JOURNAL. 2020, 7, 2343–2355.
- Zhiyuan Jiang, Zixu Cao, Bhaskar Krishnamachari,et al. SENATE: A Permissionless Byzantine Consensus Protocol in Wireless Networks for Real-Time Internet-of-Things Applications. IEEE INTERNET OF THINGS JOURNAL. 2020, 7, 2343–2355.
- R Chen, Y Li, Y Yu, H Li, W Susilo. Blockchain-based Dynamic Provable Data Possession for Smart Cities. IEEE Internet of Things Journal (Volume: 7, Issue: 5, 20),P: Page(s): 6576-6588. 20 May.
- Mehrdad Salimitari,,Mainak Chatterje,Yaser P.Fallah. A survey on consensus methods in blockchain for resource-constrained IoT networks. Internet of Things.Volume 11, 20, 100212. 20 September.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




