Submitted:
27 March 2023
Posted:
29 March 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. PUF and Machine Learning attack on PUF
3. Related Works
4. Contribution
- ∎
- We suggested using the Veda theorem to lengthen the key in order to avoid the the large number of device to collect PUF keys.
- ∎
- Conventional XOR PUF requires 64 times response generation using 64 challenges. Whereas the presented paper only requires one 64-bit challenge which eliminates the requirement of challenge key size. Moreover, 13 times response generation is required instead of 64 times.
- ∎
- After applying the Vedic theory, we obtained nearly optimal uniqueness, randomness, and reliability values of PUFs.
- ∎
- We found that the ML accuracy for the VEDA sequence was 49.80%, indicating that the VEDA PUF is vulnerable to ML assault.
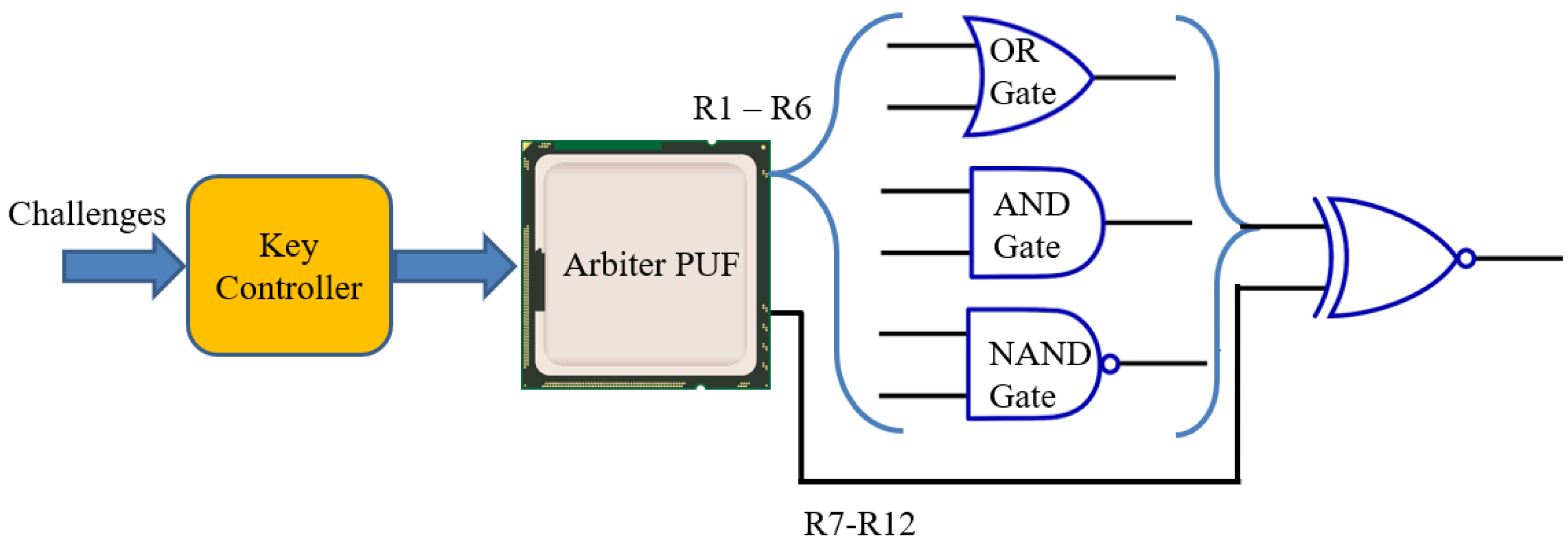
5. Proposed VXorPUF: A Hybrid XOR Arbiter PUF for Robust Security in IoMT
- Challenge extension using key controller: The original challenge will pass through key controller where Verdic principle will be applied. The controller will produce extended challenge . The produced key will be divided into 12 partial 64-bit challenges which is represented by . If the requirement of processing controller is valid then it will process further otherwise drop the challenge.
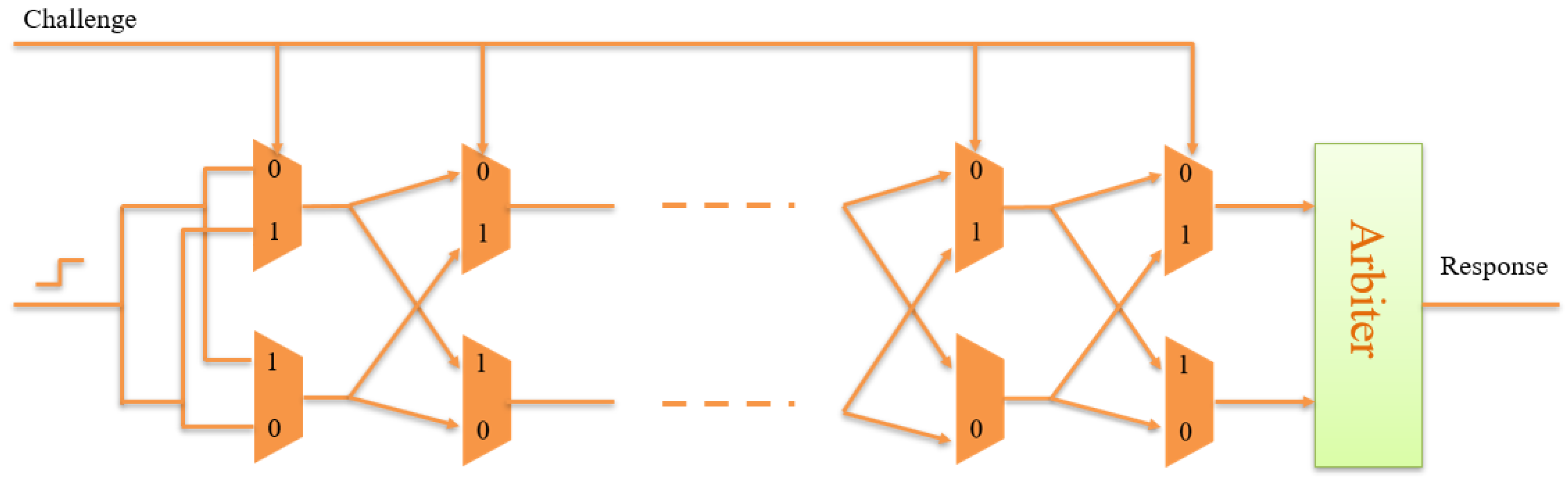
- PUF response generation: Partial challenges will act as input challenge of the PUF. Each challenge will generate unique response for each challenge. In this stage 12 responses will be generated using 64-bit Arbiter PUF.
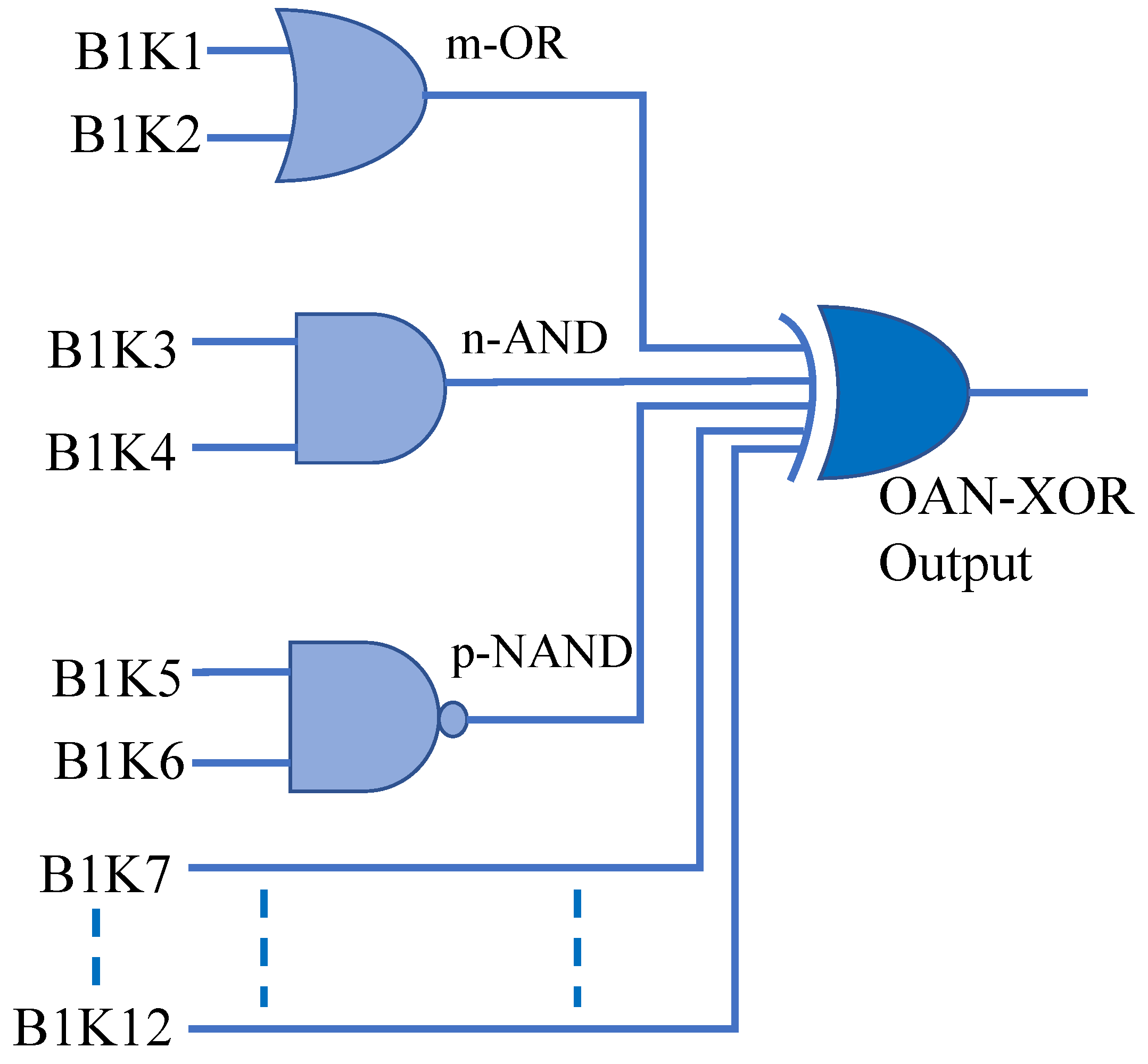
- VXorPUF response production: After inserting the PUF responses into the OR-AND-NAND block, PUF output is received. This block will generate 64-bit output using 12 64-bit responses. For example, to generate first output bit, bit-1 of first 2 responses will go to AND gate, next two responses first bit will go to NAND gate, first bit of fifth and sixth response will be used as input of OR gate. Three output of logic gates and first bit of response seven to twelve will be the input an XOR gate. The XOR gate will produce the first bit of the output. Consequently, rest bits will be generated and finally the input challenge of the key controller and the VedaPUF output will be saved in a secure database.
| Algorithm 1: Device Enrollment Phase |
 |
6. Experimental Results
6.1. Uniqueness
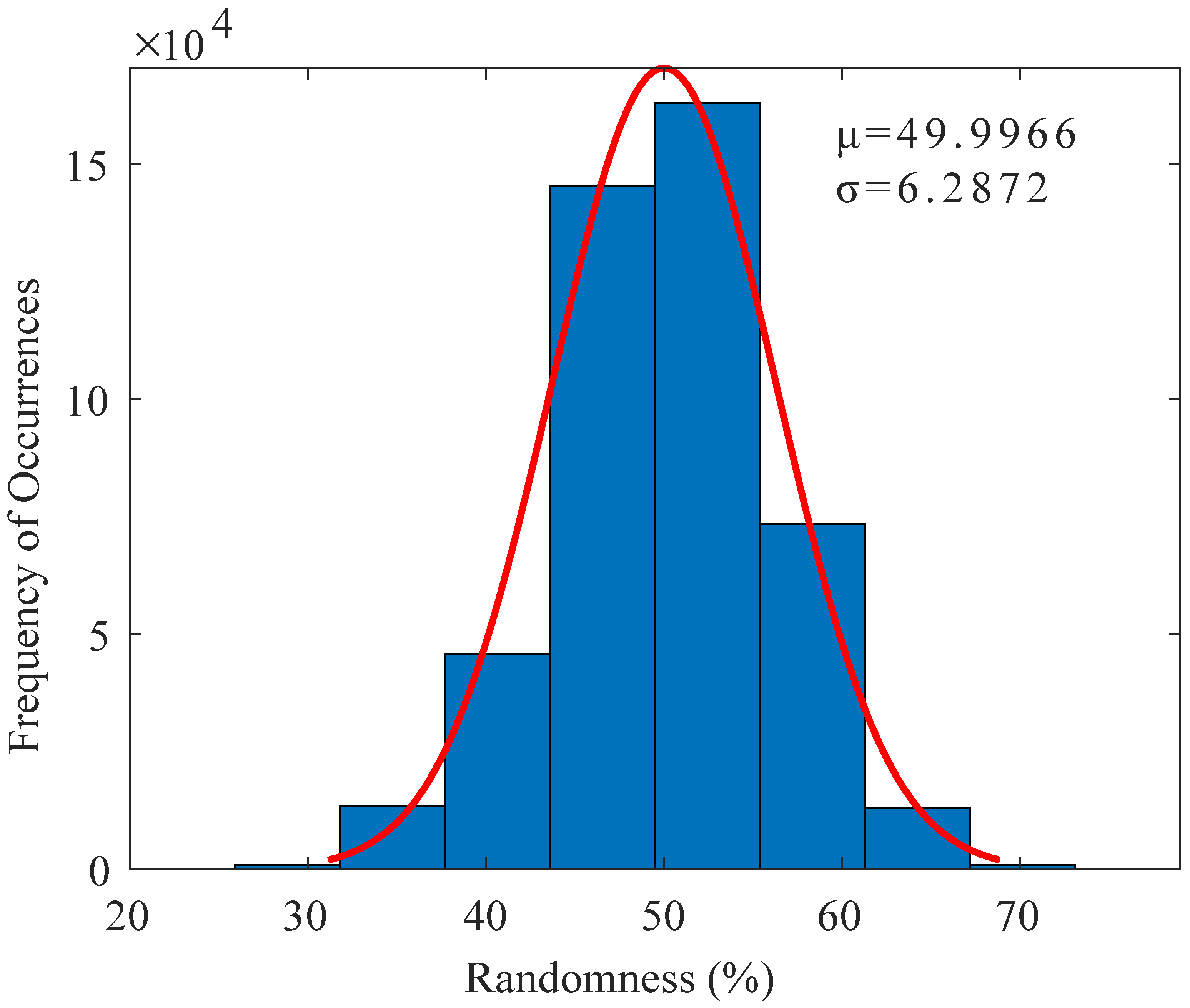
6.2. Randomness
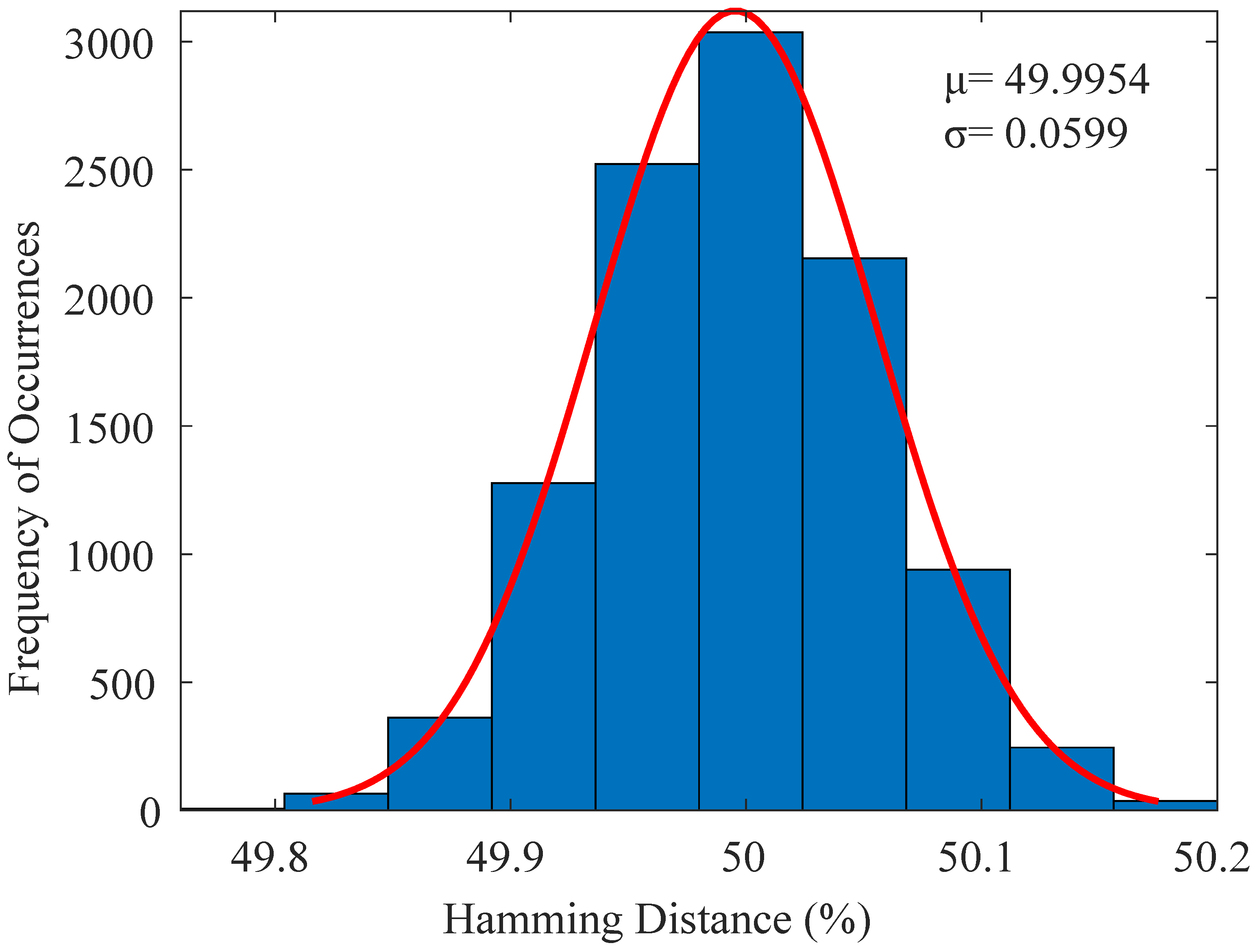
6.3. Reliability
6.4. Uniformity of OAN-XOR-PUF
-
Uniformity of m-OR-PUF:If all m inputs are 0’s, the output of the OR logic operation will be "0". Uniformity of OR is expressed as,We can observe that, particularly when m is large, m-OR-PUF shows a bias toward response "1".
-
Uniformity of n-AND-PUF:The output of the AND logic operation will be "1" if all n inputs are 1’s. The expression for uniformity of AND is,We can observe that n-AND-PUF tends to favor the response "0," particularly when n is large.
-
Uniformity of p-NAND-PUF:If all p inputs are 1’s, the output of the NAND logic operation will be "0". Uniformity of NAND is expressed as,
-
Uniformity of OAN-PUF:The response of OAN-PUF is ’1’, if one of the OR, AND, NAND PUF is ’1’ and all three equal ’1’. The m-OR, n-AND, and p-NAND logic gates all have two inputs, hence m=n=p=2 in this situation.. The OAN-PUF uniformity is defined as follows:After doing the OAN-PUF calculation, we have demonstrated that the (m,n,p)-OAN-PUF uniformity is 43.75%, which is near to the ideal values of 0.5 %. The m-OR-PUF and n-AND-biased PUF’s uniformity does not spread and has no high impact on the (m,n,p)-OAN-PUF’s final uniformity.
6.5. Machine Learning Method
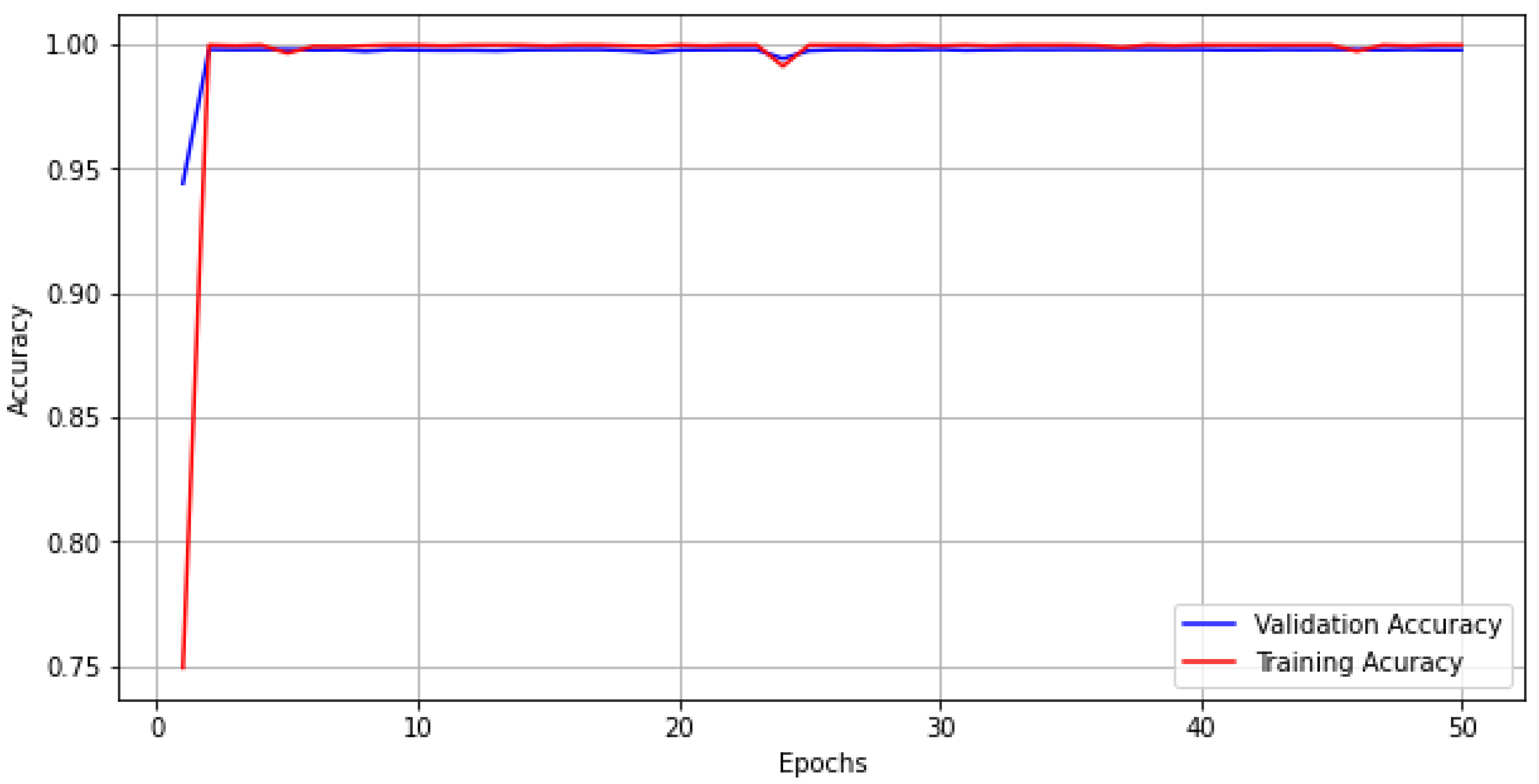
- Pre-Processing Stage: Figure 9 shows the training and validation accuracy of pre-processing stage. At this stage, the input and output data were both 64 bits.Accuracy is around 99.78% using activation function ReLU and optimizer Adam. ReLU and Adam outperformed other optimizer and activation functions when such factors were taken into account.
- Final Stage: Figure 10 depicts the last stage’s training and validation accuracy.After submitting the 64 bit response to the AON-XOR operation, 64 bit data were obtained and used for machine learning at this stage. With the activation function ReLU and Adam optimizer, accuracy is around 49.80%. At this stage, different activation functions and optimizer were tested to compare them and forecast the most accurate model.
7. Conclusion and Future Works
References
- Razdan, S.; Sharma, S. Internet of Medical Things (IoMT): Overview, Emerging Technologies, and Case Studies. IETE Technical Review 2021, pp. 1–14.
- Vaiyapuri, T.; Binbusayyis, A.; Varadarajan, V. Security, privacy and trust in iomt enabled smart healthcare system: A systematic review of current and future trends. International Journal of Advanced Computer Science and Applications 2021, 12, 731–737. [Google Scholar] [CrossRef]
- Hodgkiss, J.; Djahel, S. Securing Fuzzy Vault Enabled Authentication in Body Area Networks-Based Smart Healthcare. IEEE Consumer Electronics Magazine 2022, 11, 6–16. [Google Scholar] [CrossRef]
- King, J.; Awad, A.I. A distributed security mechanism for resource-constrained IoT devices. Informatica 2016, 40. [Google Scholar]
- Shoaran, M.; Haghi, B.A.; Taghavi, M.; Farivar, M.; Emami-Neyestanak, A. Energy-efficient classification for resource-constrained biomedical applications. IEEE Journal on Emerging and Selected Topics in Circuits and Systems 2018, 8, 693–707. [Google Scholar] [CrossRef]
- Mahmud, M.I.; Abdelgawad, A.; Yanambaka, V.P.; Yelamarthi, K. Packet Drop and RSSI Evaluation for LoRa: An Indoor Application Perspective. In Proceedings of the Proceedings of IEEE 7th World Forum on Internet of Things (WF-IoT), 2021, pp. 913–914. [CrossRef]
- Khor, J.H.; Sidorov, M.; Woon, P.Y. Public Blockchains for Resource-Constrained IoT Devices—A State-of-the-Art Survey. IEEE Internet of Things Journal 2021, 8, 11960–11982. [Google Scholar] [CrossRef]
- Siddiqi, M.A.; Tsintzira, A.A.; Digkas, G.; Siavvas, M.G.; Strydis, C. Adding Security to Implantable Medical Devices: Can We Afford It? In Proceedings of the Proceedings of EWSN; 2021; pp. 67–78. [Google Scholar]
- Wang, W.; Qiu, C.; Yin, Z.; Srivastava, G.; Gadekallu, T.R.; Alsolami, F.; Su, C. Blockchain and PUF-based lightweight authentication protocol for wireless medical sensor networks. IEEE Internet of Things Journal 2021. [Google Scholar] [CrossRef]
- Monrat, A.A.; Schelén, O.; Andersson, K. A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access 2019, 7, 117134–117151. [Google Scholar] [CrossRef]
- Kouhizadeh, M.; Sarkis, J. Blockchain practices, potentials, and perspectives in greening supply chains. Sustainability 2018, 10, 3652. [Google Scholar] [CrossRef]
- Al-Jaroodi, J.; Mohamed, N. Blockchain in Industries: A Survey. IEEE Access 2019, 7, 36500–36515. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telematics and informatics 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Diedhiou, O.N.; Diallo, C. An IoT mutual authentication scheme based on PUF and blockchain. In Proceedings of the 2020 International Conference on Computational Science and Computational Intelligence (CSCI). IEEE, 2020, pp. 1034–1040.
- Asif, R.; Ghanem, K.; Irvine, J. Proof-of-PUF enabled blockchain: Concurrent data and device security for internet-of-energy. Sensors 2020, 21, 28. [Google Scholar] [CrossRef] [PubMed]
- Suragani, R.; Nazarenko, E.; Anagnostopoulos, N.A.; Mexis, N.; Kavun, E.B. Identification and Classification of Corrupted PUF Responses via Machine Learning. In Proceedings of the 2022 IEEE International Symposium on Hardware Oriented Security and Trust (HOST). IEEE, 2022, pp. 137–140.
- Lim, D.; Lee, J.; Gassend, B.; Suh, G.; van Dijk, M.; Devadas, S. Extracting secret keys from integrated circuits. IEEE Transactions on Very Large Scale Integration (VLSI) Systems 2005, 13, 1200–1205. [Google Scholar] [CrossRef]
- Zerrouki, F.; Ouchani, S.; Bouarfa, H. A survey on silicon PUFs. Journal of Systems Architecture 2022, 127, 102514. [Google Scholar] [CrossRef]
- Lee, J.; Lim, D.; Gassend, B.; Suh, G.; van Dijk, M.; Devadas, S. A technique to build a secret key in integrated circuits for identification and authentication applications. In Proceedings of the 2004 Symposium on VLSI Circuits. Digest of Technical Papers (IEEE Cat. No.04CH37525), 2004, pp. 176–179. [CrossRef]
- Zalivaka, S.S.; Ivaniuk, A.A.; Chang, C.H. Reliable and modeling attack resistant authentication of arbiter PUF in FPGA implementation with trinary quadruple response. IEEE Transactions on Information Forensics and Security 2018, 14, 1109–1123. [Google Scholar] [CrossRef]
- Kroeger, T.; Cheng, W.; Guilley, S.; Danger, J.L.; Karimi, N. Effect of aging on PUF modeling attacks based on power side-channel observations. In Proceedings of the 2020 Design, Automation & Test in Europe Conference & Exhibition (DATE). IEEE, 2020, pp. 454–459.
- Maiti, A.; McDougall, L.; Schaumont, P. The impact of aging on an FPGA-based physical unclonable function. In Proceedings of the 2011 21st International Conference on Field Programmable Logic and Applications. IEEE, 2011, pp. 151–156.
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D.; Sadeghi, A.R.; Ranasinghe, D.C. Modeling attack resilient reconfigurable latent obfuscation technique for PUF based lightweight authentication. arXiv preprint arXiv:1706.06232 2017. arXiv:1706.06232 2017.
- Santikellur, P.; Bhattacharyay, A.; Chakraborty, R.S. Deep learning based model building attacks on arbiter PUF compositions. Cryptology ePrint Archive 2019. [Google Scholar]
- Wisiol, N.; Thapaliya, B.; Mursi, K.T.; Seifert, J.P.; Zhuang, Y. Neural Network Modeling Attacks on Arbiter-PUF-Based Designs. IEEE Transactions on Information Forensics and Security 2022, 17, 2719–2731. [Google Scholar] [CrossRef]
- Gassend, B.; Lim, D.; Clarke, D.; Van Dijk, M.; Devadas, S. Identification and authentication of integrated circuits. Concurrency and Computation: Practice and Experience 2004, 16, 1077–1098. [Google Scholar] [CrossRef]
- Rührmair, U.; Sehnke, F.; Sölter, J.; Dror, G.; Devadas, S.; Schmidhuber, J. Modeling attacks on physical unclonable functions. In Proceedings of the Proceedings of the 17th ACM conference on Computer and communications security, 2010, pp. 237–249.
- Kwarteng, E.; Cebe, M. A survey on security issues in modern Implantable Devices: Solutions and future issues. Smart Health 2022, p. 100295.
- Koutras, D.; Stergiopoulos, G.; Dasaklis, T.; Kotzanikolaou, P.; Glynos, D.; Douligeris, C. Security in IoMT communications: A survey. Sensors 2020, 20, 4828. [Google Scholar] [CrossRef] [PubMed]
- Hatzivasilis, G.; Soultatos, O.; Ioannidis, S.; Verikoukis, C.; Demetriou, G.; Tsatsoulis, C. Review of security and privacy for the Internet of Medical Things (IoMT). In Proceedings of the Proceedings of 2019 15th international conference on distributed computing in sensor systems (DCOSS). IEEE, 2019, pp. 457–464.
- Rahman, M.; Jahankhani, H. Security vulnerabilities in existing security mechanisms for IoMT and potential solutions for mitigating cyber-attacks. In Proceedings of Information Security Technologies for Controlling Pandemics; Springer, 2021; pp. 307–334.
- Kumar, P.; Gupta, G.P.; Tripathi, R. An ensemble learning and fog-cloud architecture-driven cyber-attack detection framework for IoMT networks. Computer Communications 2021, 166, 110–124. [Google Scholar] [CrossRef]
- Nandy, S.; Adhikari, M.; Khan, M.A.; Menon, V.G.; Verma, S. An intrusion detection mechanism for secured IoMT framework based on swarm-neural network. IEEE Journal of Biomedical and Health Informatics 2021, 26, 1969–1976. [Google Scholar] [CrossRef]
- Almogren, A.; Mohiuddin, I.; Din, I.U.; Almajed, H.; Guizani, N. Ftm-iomt: Fuzzy-based trust management for preventing sybil attacks in internet of medical things. Proceedings of IEEE Internet of Things Journal 2020, 8, 4485–4497. [Google Scholar] [CrossRef]
- Papaioannou, M.; Karageorgou, M.; Mantas, G.; Sucasas, V.; Essop, I.; Rodriguez, J.; Lymberopoulos, D. A survey on security threats and countermeasures in internet of medical things (IoMT). Transactions on Emerging Telecommunications Technologies 2022, 33, e4049. [Google Scholar] [CrossRef]
- Karmakar, K.K.; Varadharajan, V.; Tupakula, U.; Nepal, S.; Thapa, C. Towards a security enhanced virtualised network infrastructure for Internet of Medical Things (IoMT). In Proceedings of the Proceedings of 2020 6th IEEE conference on network softwarization (NetSoft). IEEE, 2020, pp. 257–261.
- Wazid, M.; Das, A.K.; Rodrigues, J.J.; Shetty, S.; Park, Y. IoMT malware detection approaches: analysis and research challenges. IEEE Access 2019, 7, 182459–182476. [Google Scholar] [CrossRef]
- Sadhu, P.; Yanambaka, V.P.; Abdelgawad, A.; Yelamarthi, K. NAHAP: PUF-Based Three Factor Authentication System for Internet of Medical Things. IEEE Consumer Electronics Magazine 2022, pp. 1–1. [CrossRef]
- Yoon, S.; Kim, B.; Kang, Y. Multiple PUF-based lightweight authentication method in the IoT. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC); 2021; pp. 1198–1200. [Google Scholar] [CrossRef]
- Yanambaka, V.P.; Mohanty, S.P.; Kougianos, E.; Puthal, D. PMsec: Physical Unclonable Function-Based Robust and Lightweight Authentication in the Internet of Medical Things. Proceedings of IEEE Transactions on Consumer Electronics 2019, 65, 388–397. [Google Scholar] [CrossRef]
- Satamraju, K.P.; Balakrishnan, M. A Secured Healthcare Model for Sensor Data Sharing With Integrated Emotional Intelligence. IEEE Sensors Journal 2022, 22, 16306–16313. [Google Scholar] [CrossRef]
- Hu, Y.; Jiang, Y.; Wang, W. Compact PUF Design With Systematic Biases Mitigation on Xilinx FPGAs. IEEE Access 2022, 10, 22288–22300. [Google Scholar] [CrossRef]
- Khalafalla, M.; Gebotys, C. PUFs Deep Attacks: Enhanced Modeling Attacks Using Deep Learning Techniques to Break The Security of Double Arbiter PUFs. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE); 2019; pp. 204–209. [Google Scholar] [CrossRef]
- Wisiol, N.; Thapaliya, B.; Mursi, K.T.; Seifert, J.P.; Zhuang, Y. Neural Network Modeling Attacks on Arbiter-PUF-Based Designs. IEEE Transactions on Information Forensics and Security 2022, 17, 2719–2731. [Google Scholar] [CrossRef]
- Wang, S.J.; Chen, Y.S.; Li, K.S.M. Modeling Attack Resistant PUFs Based on Adversarial Attack Against Machine Learning. IEEE Journal on Emerging and Selected Topics in Circuits and Systems 2021, 11, 306–318. [Google Scholar] [CrossRef]
- Wang, Y.; Xi, X.; Orshansky, M. Lattice PUF: A strong physical unclonable function provably secure against machine learning attacks. In Proceedings of the 2020 IEEE International Symposium on Hardware Oriented Security and Trust (HOST). IEEE, 2020, pp. 273–283.
- Zhuang, H.; Xi, X.; Sun, N.; Orshansky, M. A strong subthreshold current array PUF resilient to machine learning attacks. IEEE Transactions on Circuits and Systems I: Regular Papers 2019, 67, 135–144. [Google Scholar] [CrossRef]
- Zhang, J.; Xu, C.; Law, M.K.; Jiang, Y.; Zhao, X.; Mak, P.I.; Martins, R.P. A 4T/Cell Amplifier-Chain-Based XOR PUF With Strong Machine Learning Attack Resilience. IEEE Transactions on Circuits and Systems I: Regular Papers 2021, 69, 366–377. [Google Scholar] [CrossRef]
- Ali, R.; Zhang, D.; Cai, H.; Zhao, W.; Wang, Y. A Machine Learning Attack-Resilient Strong PUF Leveraging the Process Variation of MRAM. IEEE Transactions on Circuits and Systems II: Express Briefs 2022.
- Canaday, D.; Barbosa, W.A.; Pomerance, A. A Novel Attack on Machine-Learning Resistant Physical Unclonable Functions. In Proceedings of the 2022 IEEE International Symposium on Hardware Oriented Security and Trust (HOST). IEEE, 2022, pp. 25–28.
- Wang, S.J.; Chen, Y.S.; Li, K.S.M. Modeling attack resistant PUFs based on adversarial attack against machine learning. IEEE Journal on Emerging and Selected Topics in Circuits and Systems 2021, 11, 306–318. [Google Scholar] [CrossRef]
- Yanambaka, V.P.; Mohanty, S.P.; Kougianos, E.; Baniya, B.K.; Rout, B. Veda-PUF: A PUF based on Vedic Principles for Robust Lightweight Security for IoT. In Proceedings of the IEEE International Symposium on Smart Electronic Systems (iSES); 2021; pp. 400–405. [Google Scholar] [CrossRef]
- Yao, J.; Pang, L.; Su, Y.; Zhang, Z.; Yang, W.; Fu, A.; Gao, Y. Design and Evaluate Recomposited OR-AND-XOR-PUF. IEEE Transactions on Emerging Topics in Computing 2022. [Google Scholar] [CrossRef]
- Maiti, A.; Gunreddy, V.; Schaumont, P. A Systematic Method to Evaluate and Compare the Performance of Physical Unclonable Functions. Cryptology ePrint Archive, Paper 2011/657, 2011. https://eprint.iacr.org/2011/657.

| ML Stages | Amount of Data | Training | Testing |
| Pre-Processing | 500000 | 400000 | 100000 |
| Final Stage | 455732 | 364585 | 91147 |
| Accuracy | Optimizer | ||
| ReLU | ELU | Sigmoid | |
| 49.80% | 49.85% | 50.00% | Adam |
| 49.85% | 49.88% | 50.00% | SGD |
| 49.94% | 49.85% | 50.23% | RMSProp |
| 50.19% | 50.14% | 49.90% | Adadelta |
| 49.93% | 49.82% | 49.89% | Adagrad |
| 50.18% | 50.11% | 50.22% | Adamax |
| 50.17% | 50.05% | 49.95% | Nadam |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





