Submitted:
17 March 2023
Posted:
20 March 2023
You are already at the latest version
Abstract
Keywords:
I. Introduction
II. Methodology and Computational Experiment
III. Computational Instruments
IV. Strategies
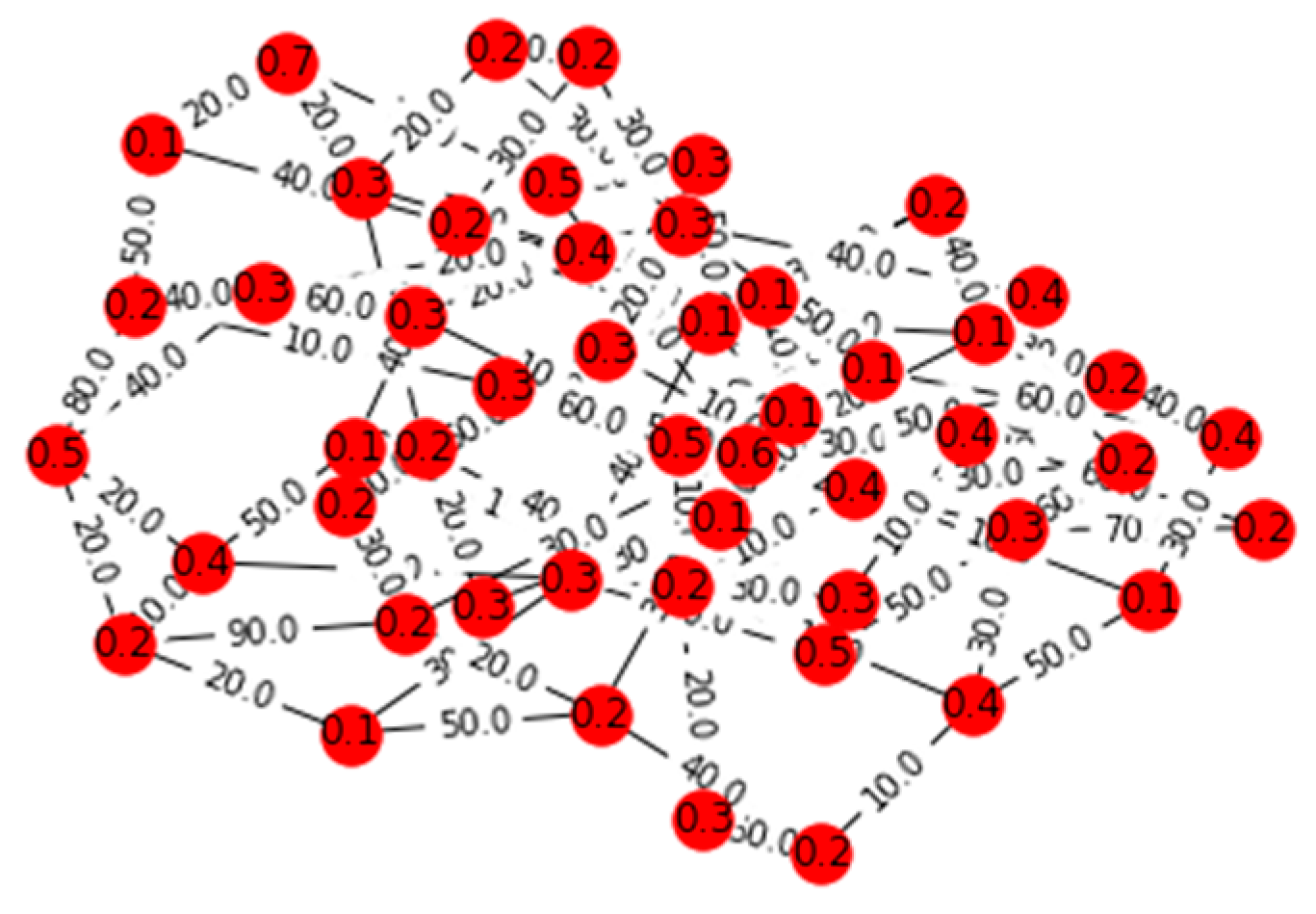
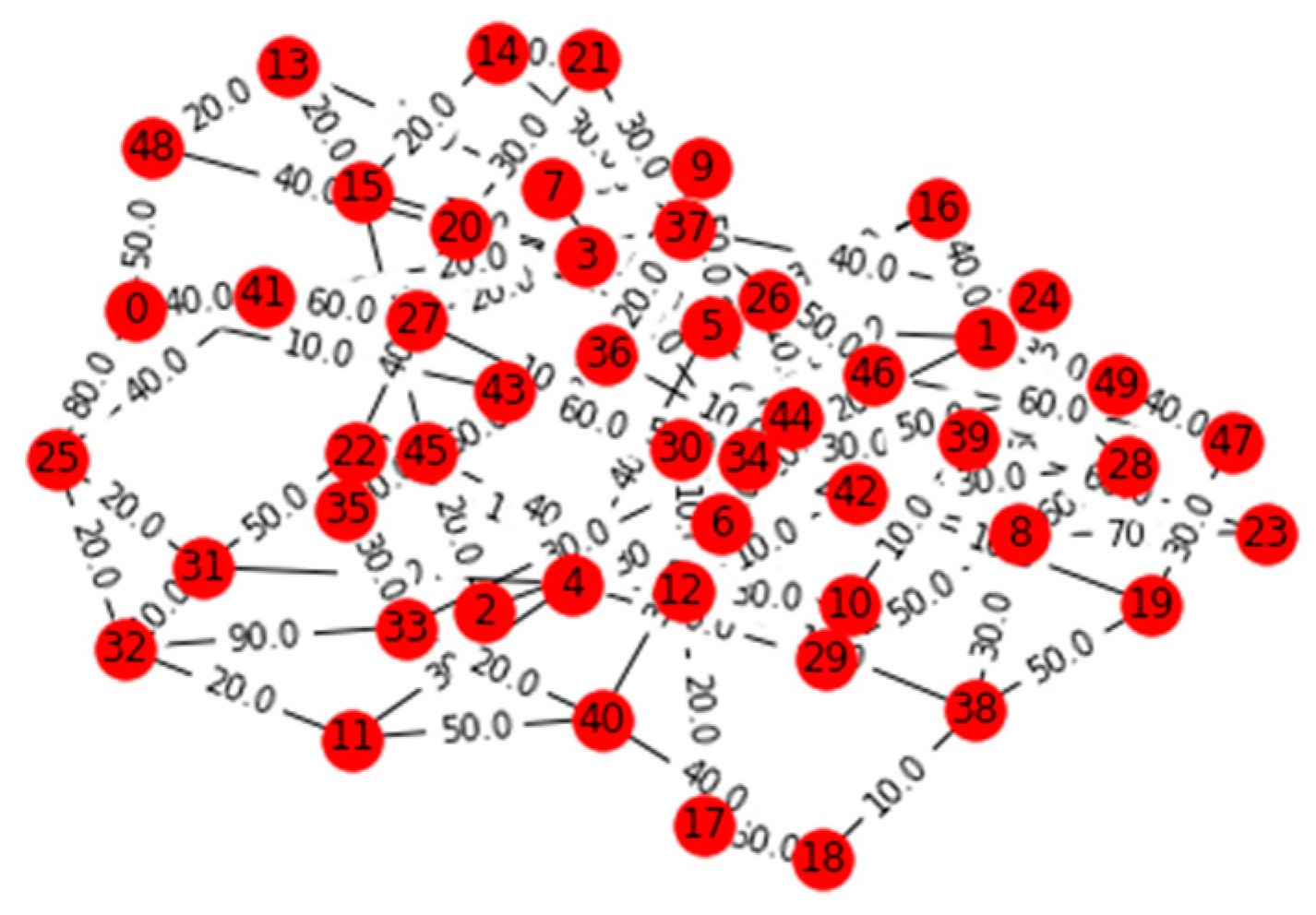
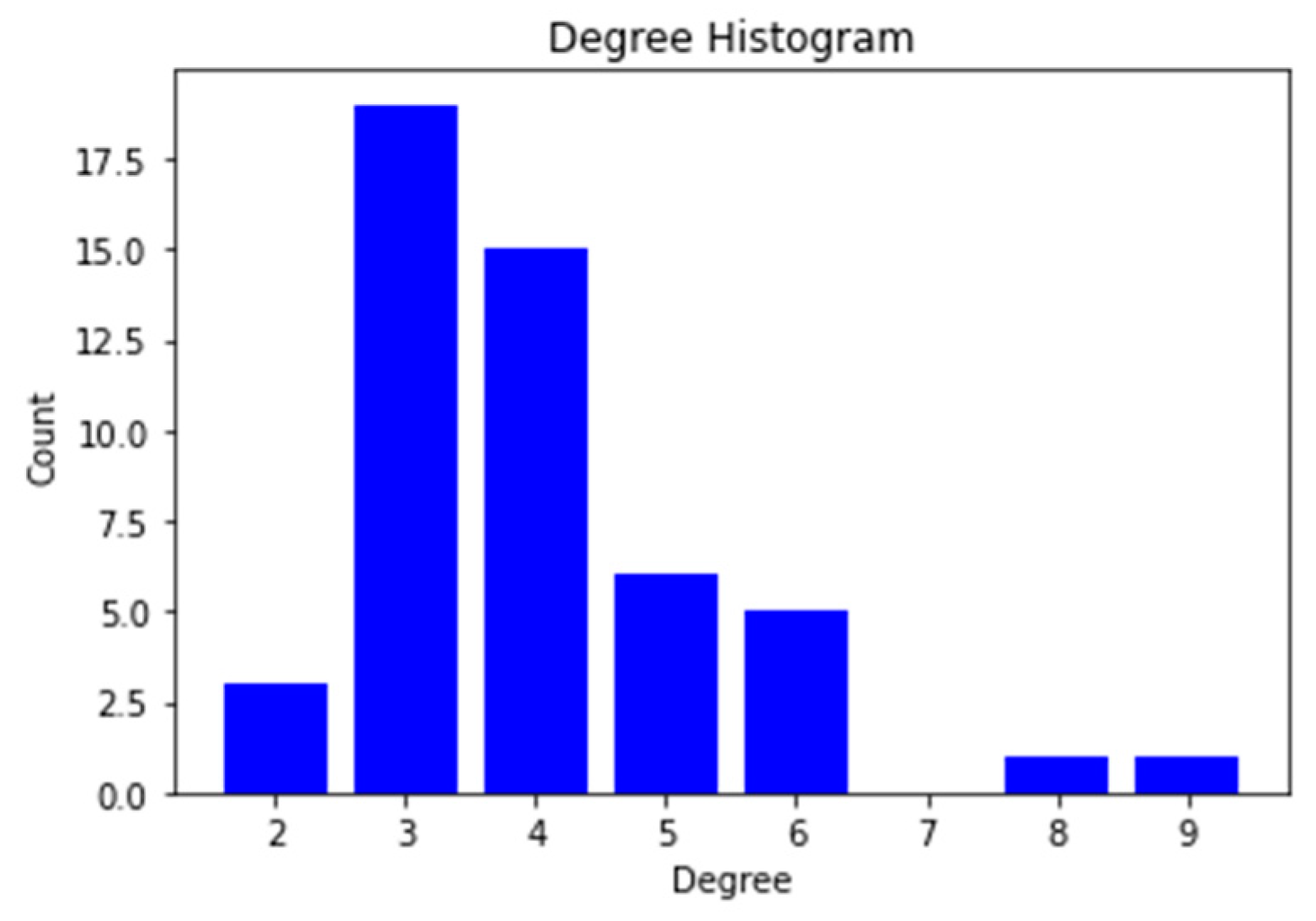
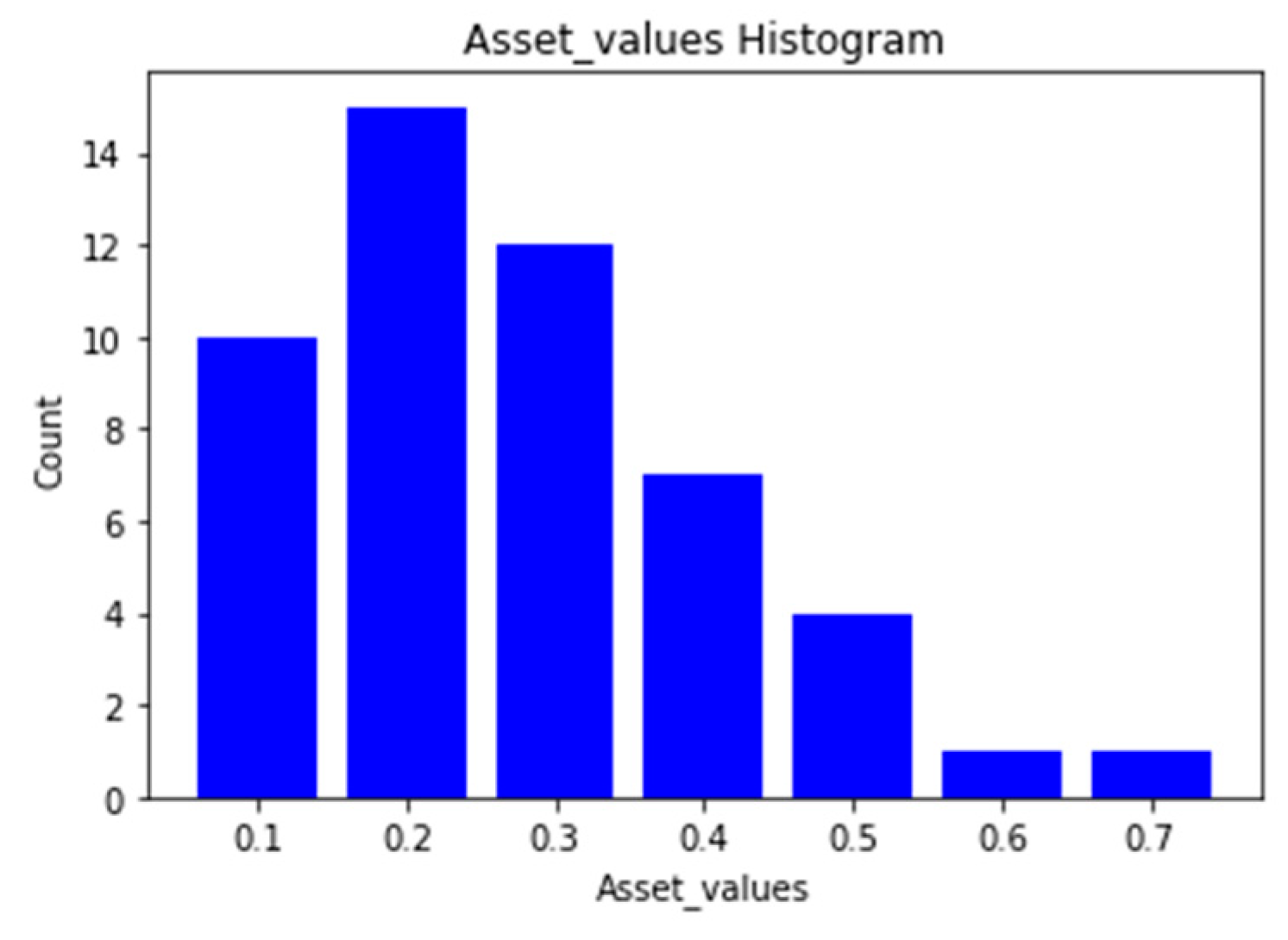
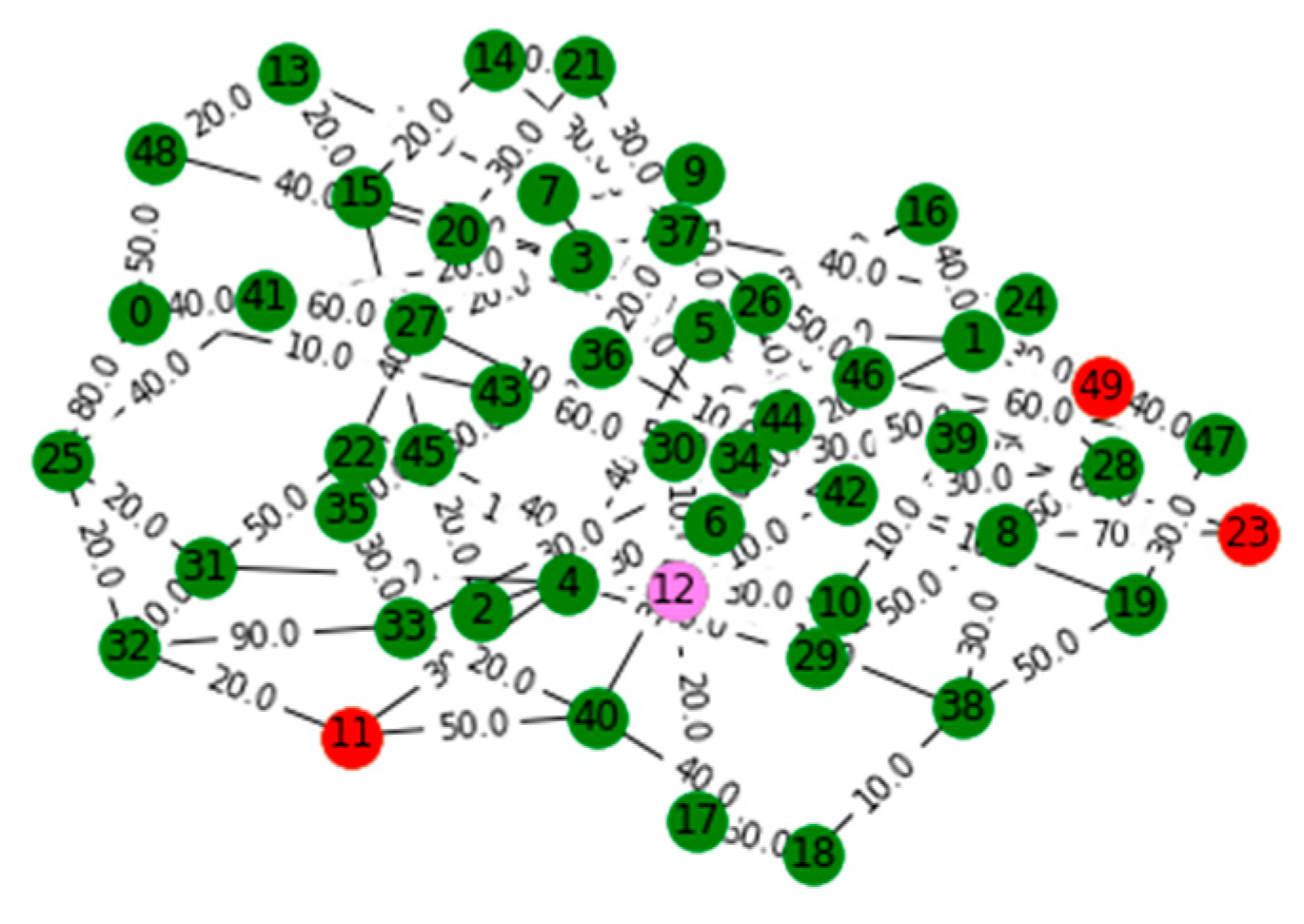
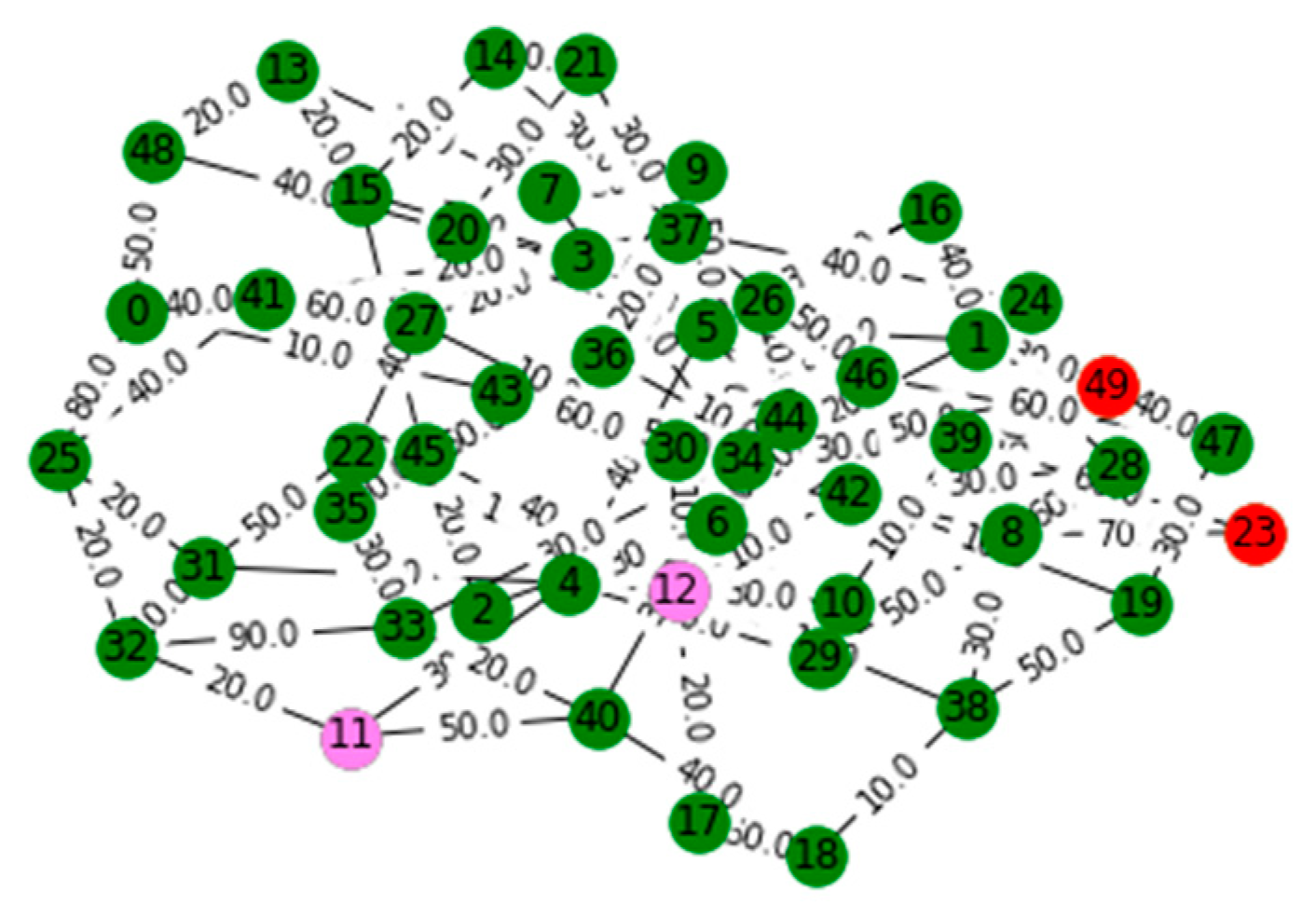
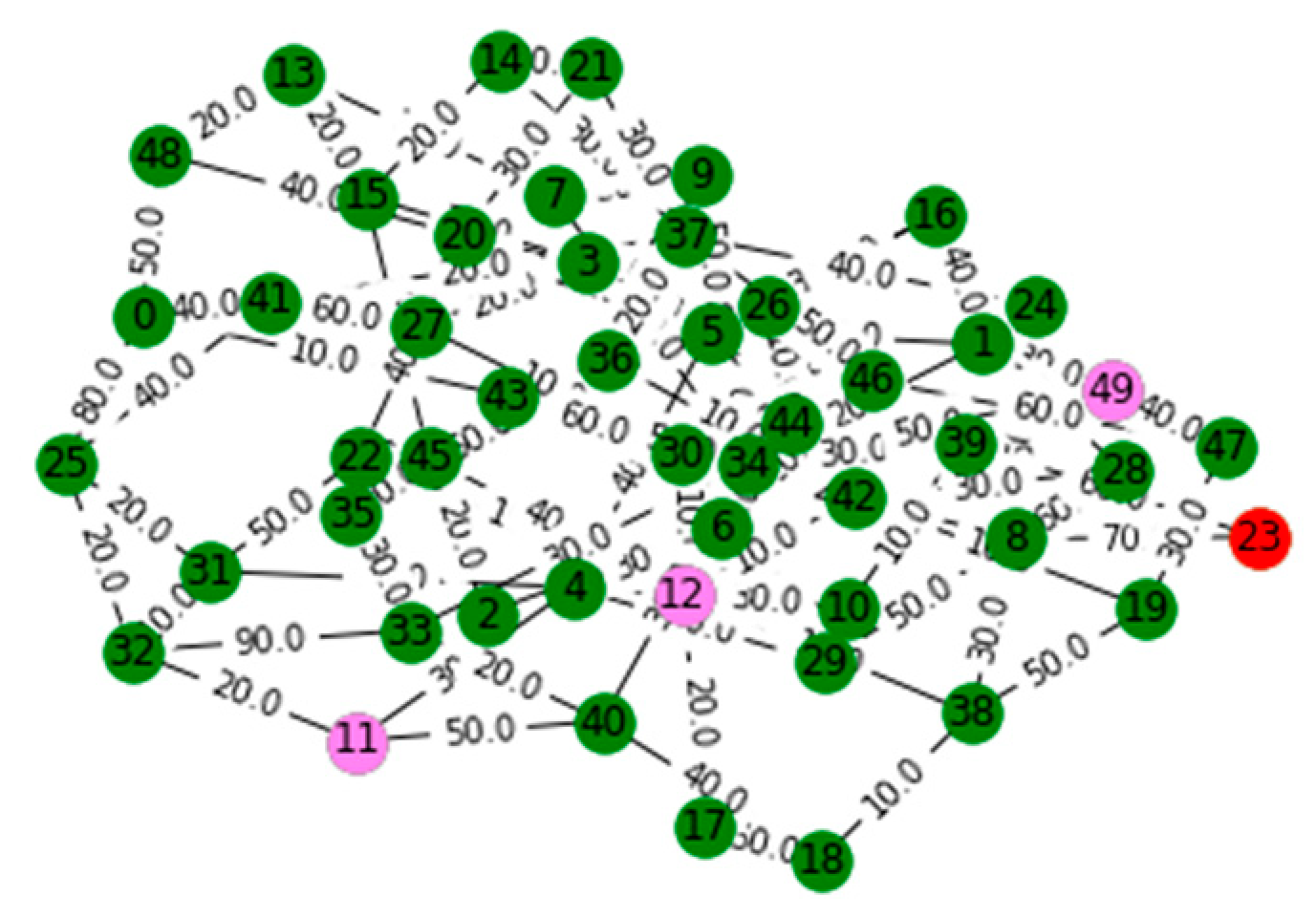
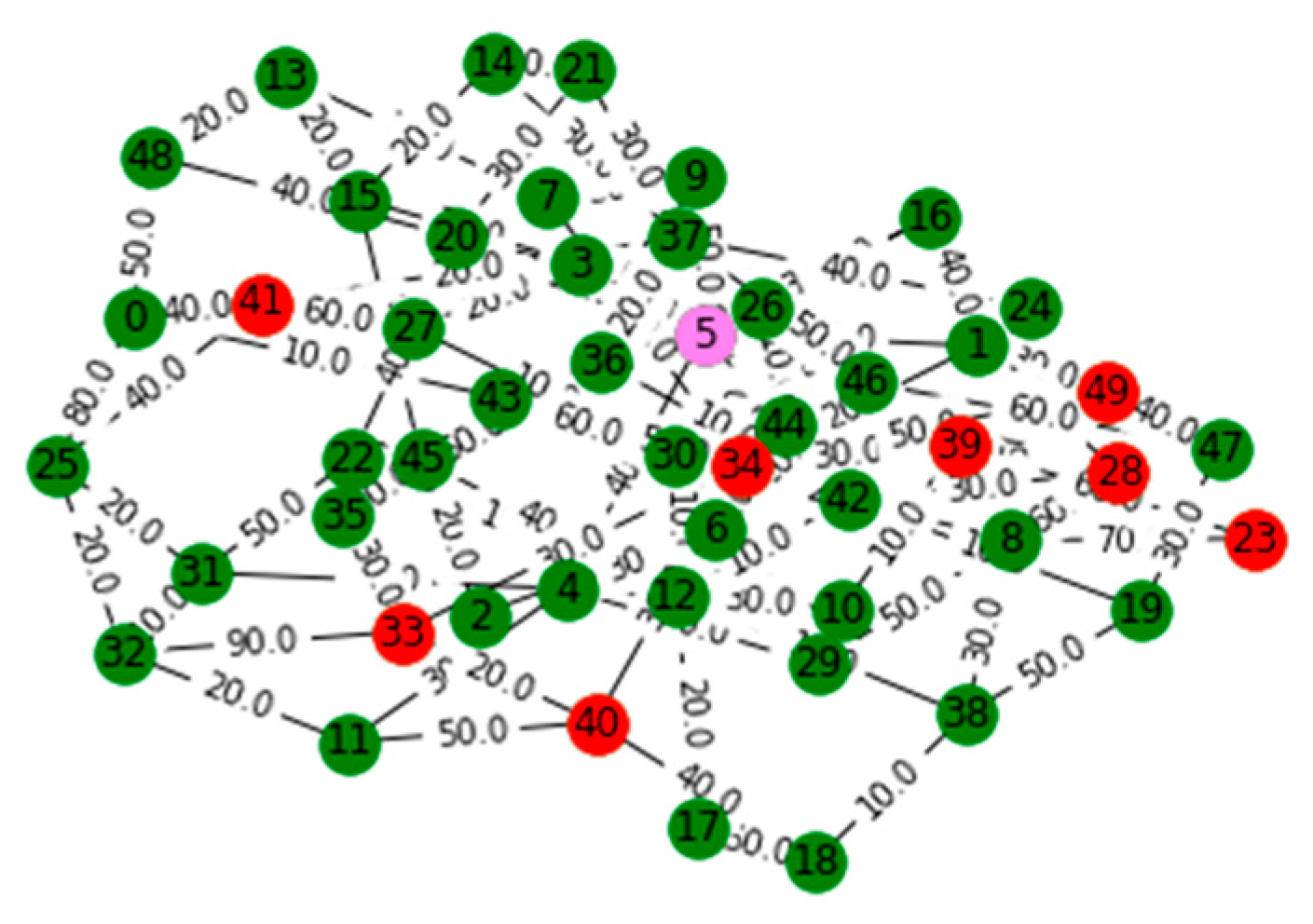
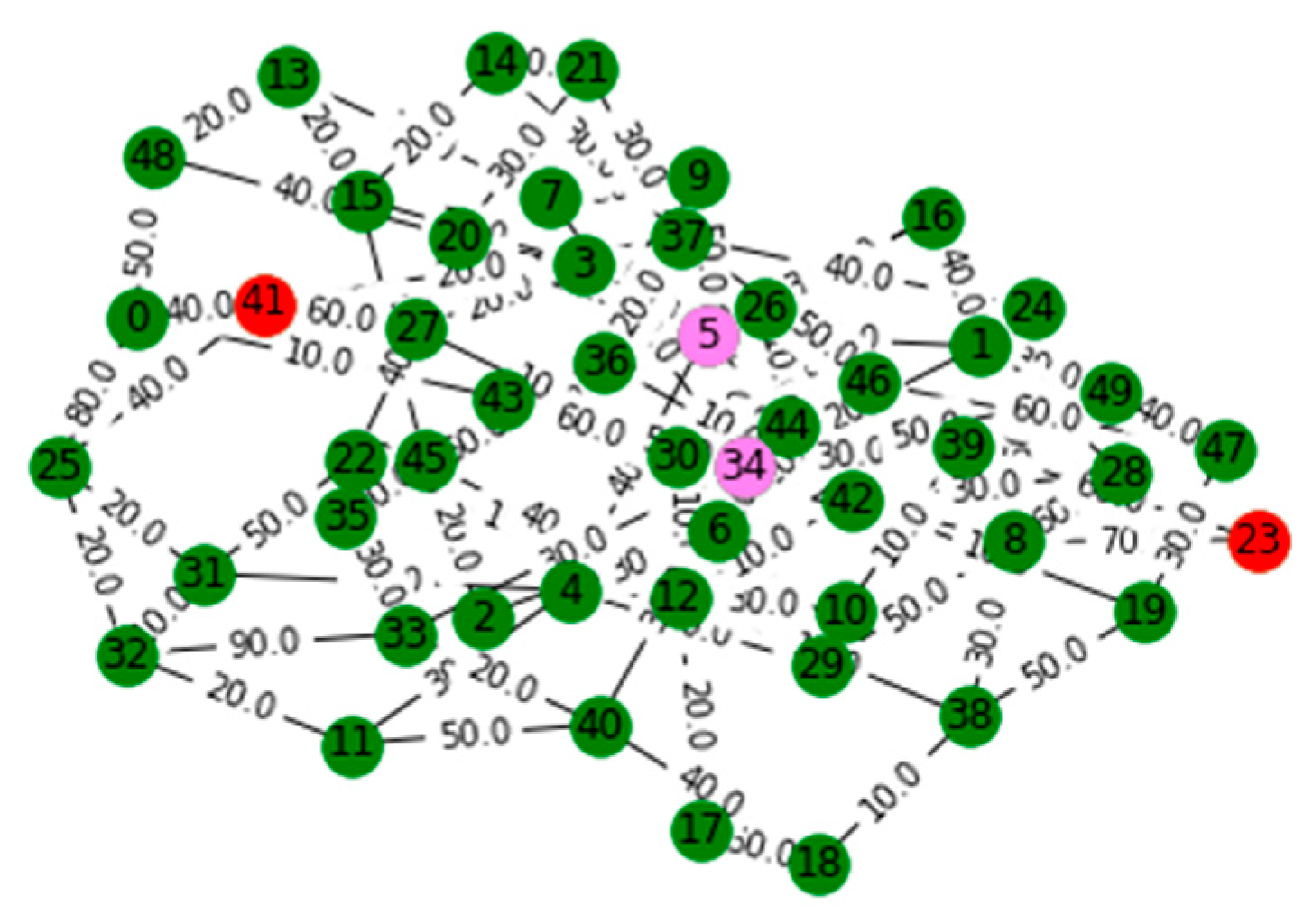
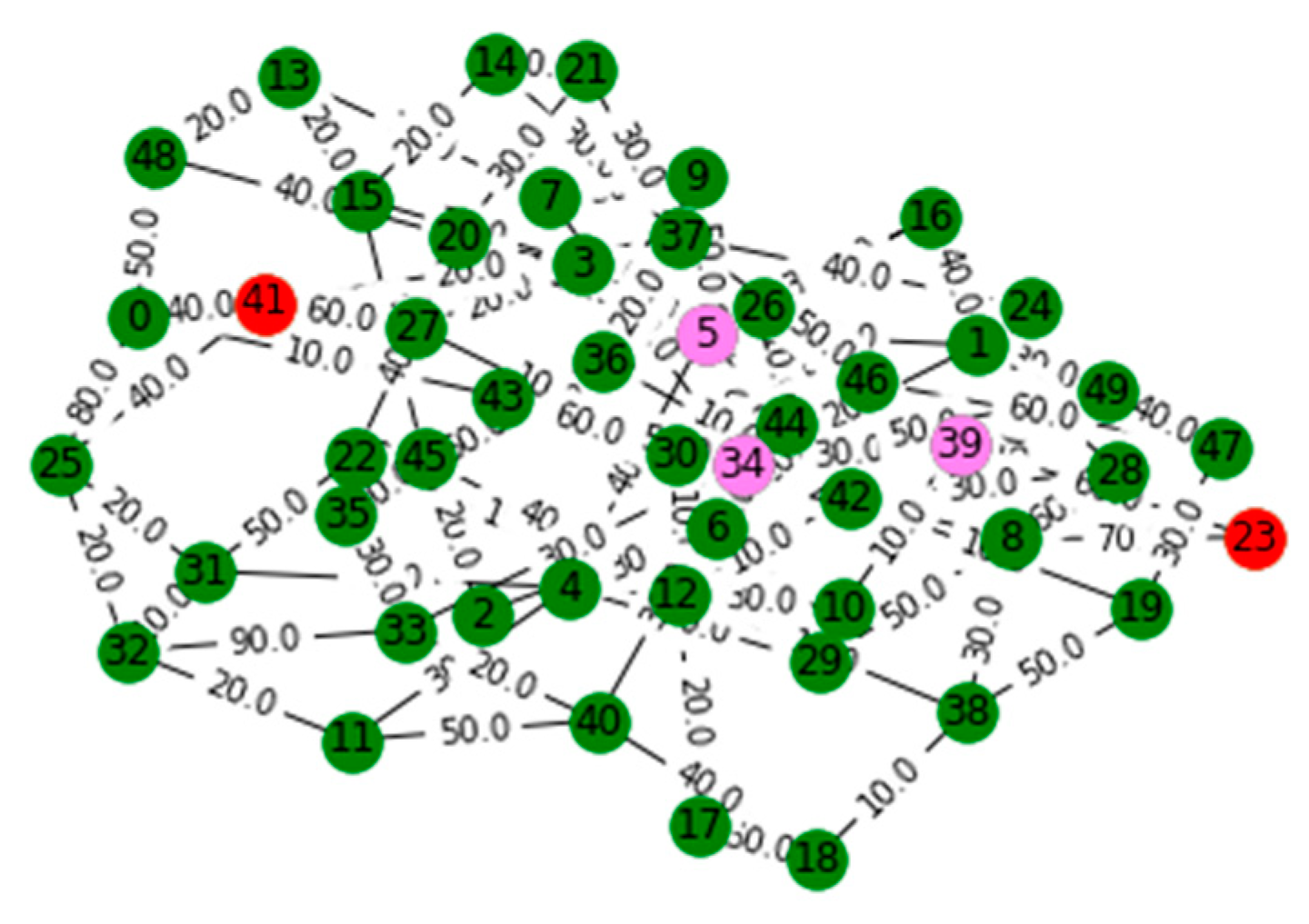
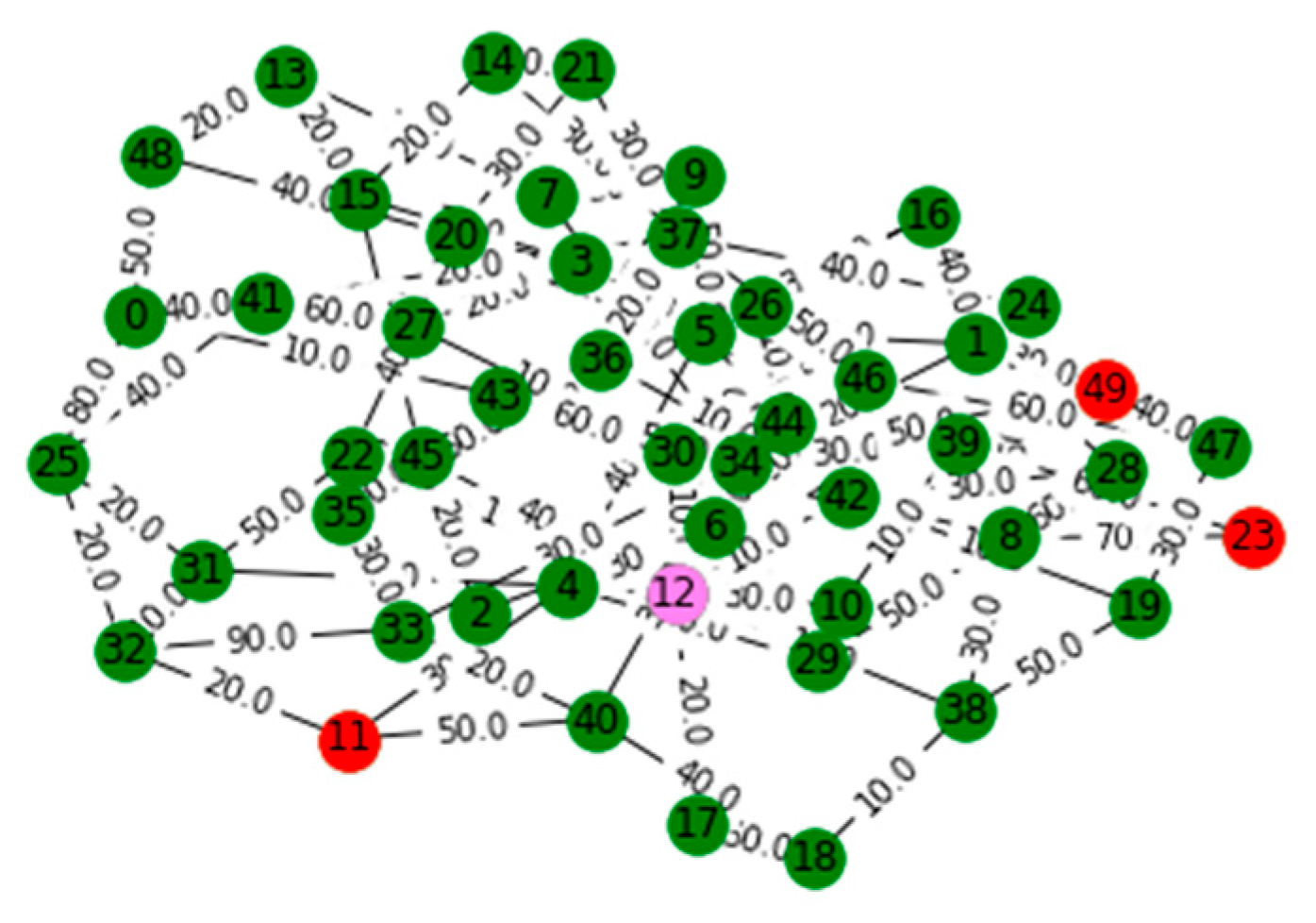
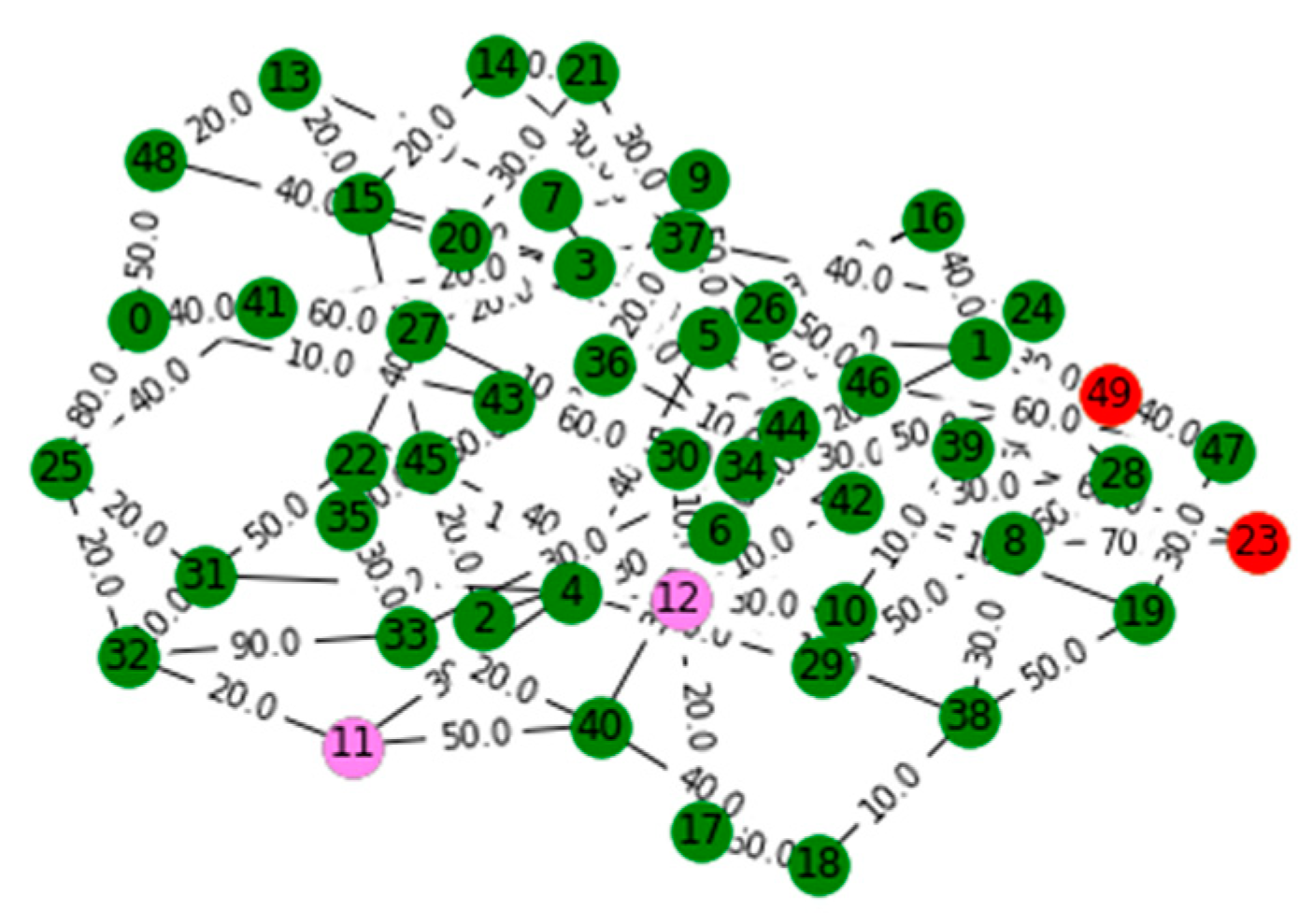
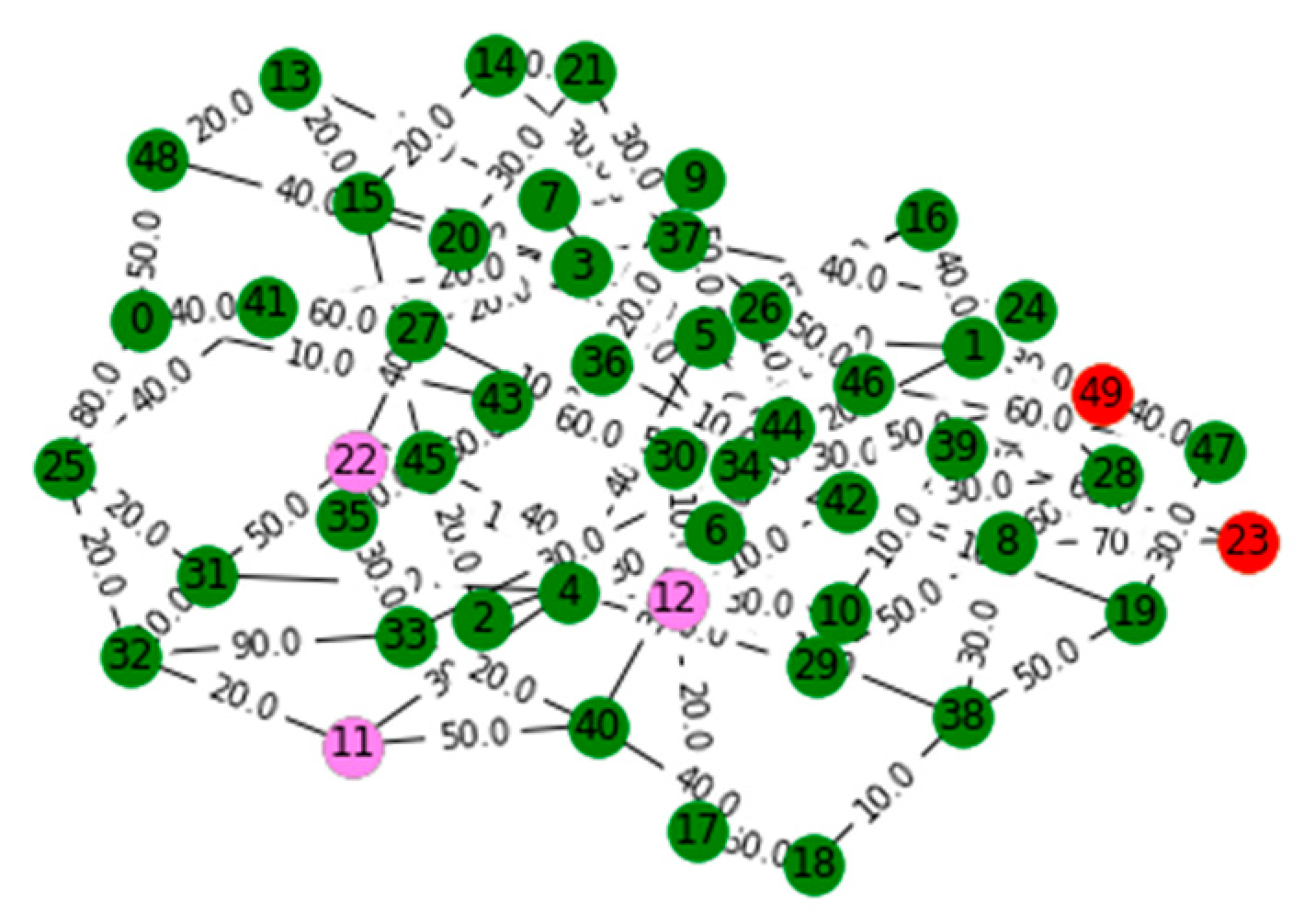
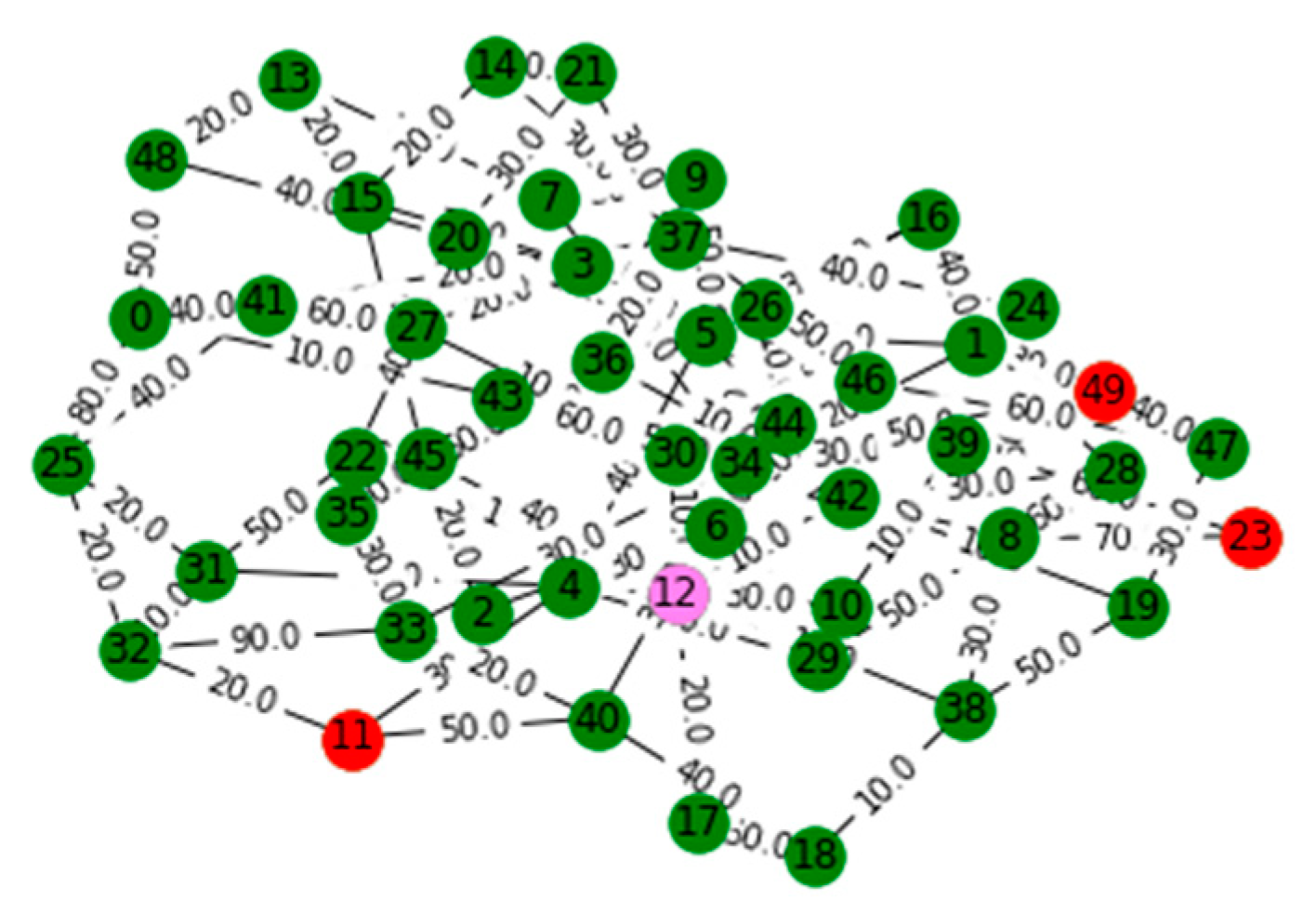
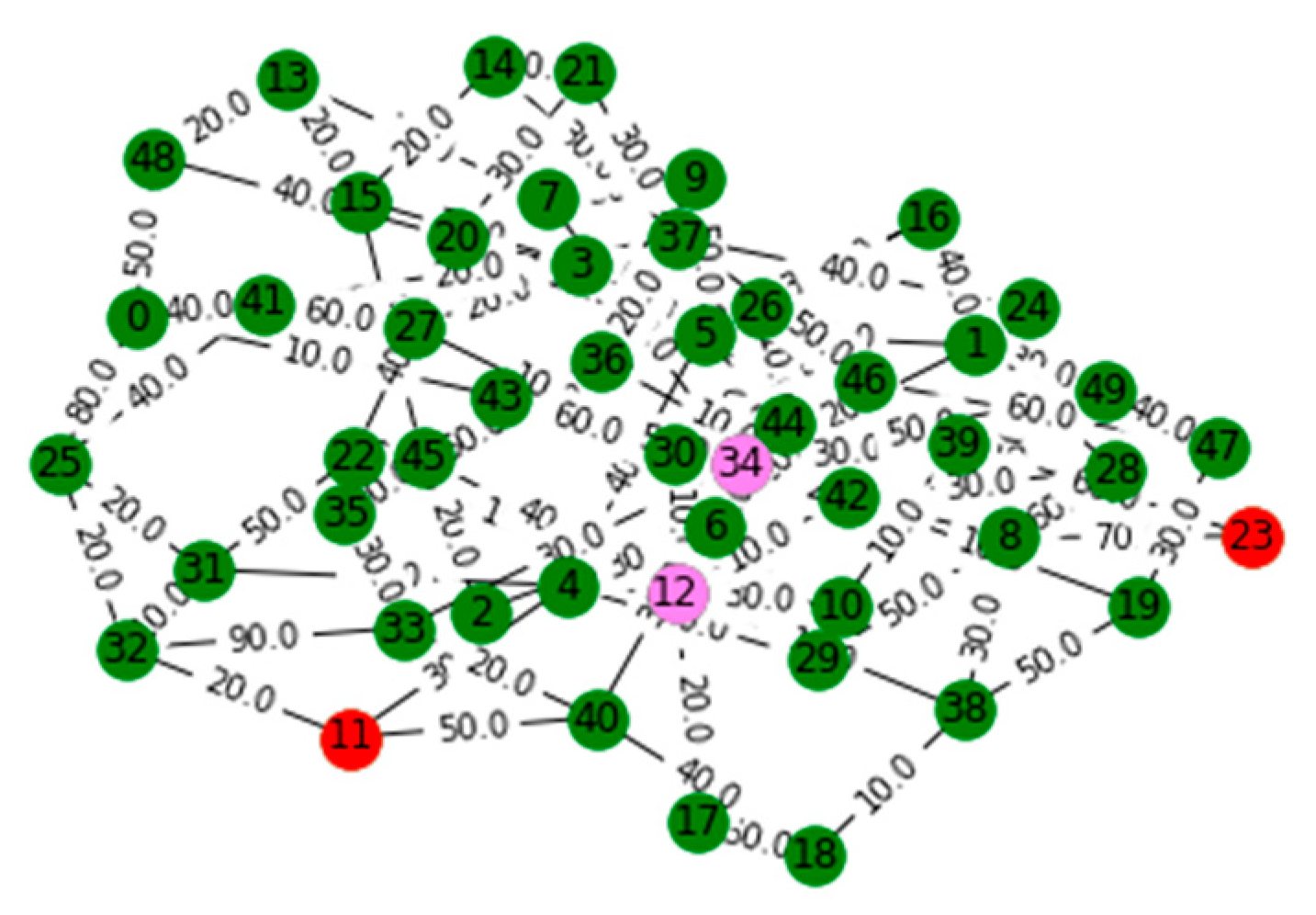
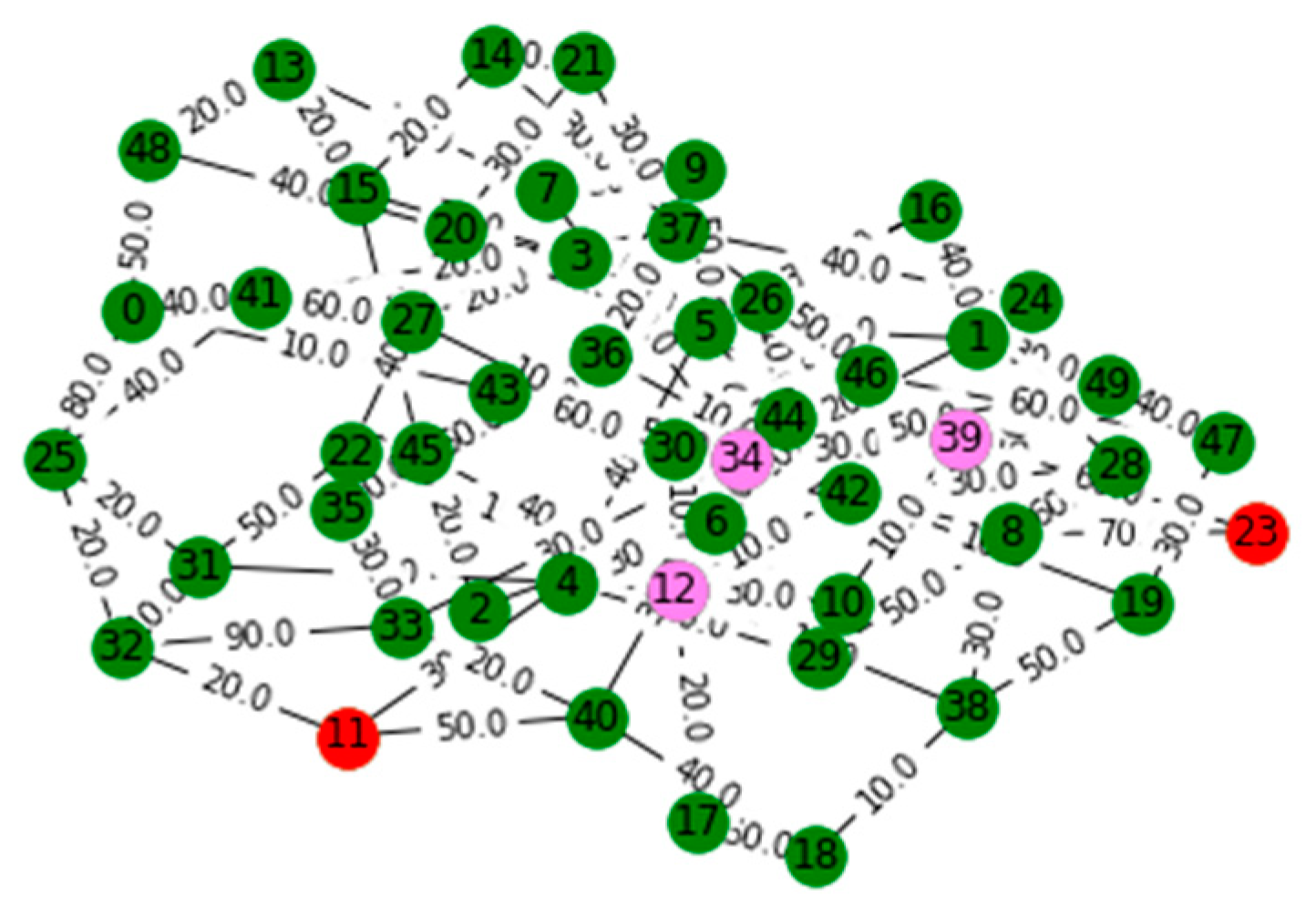
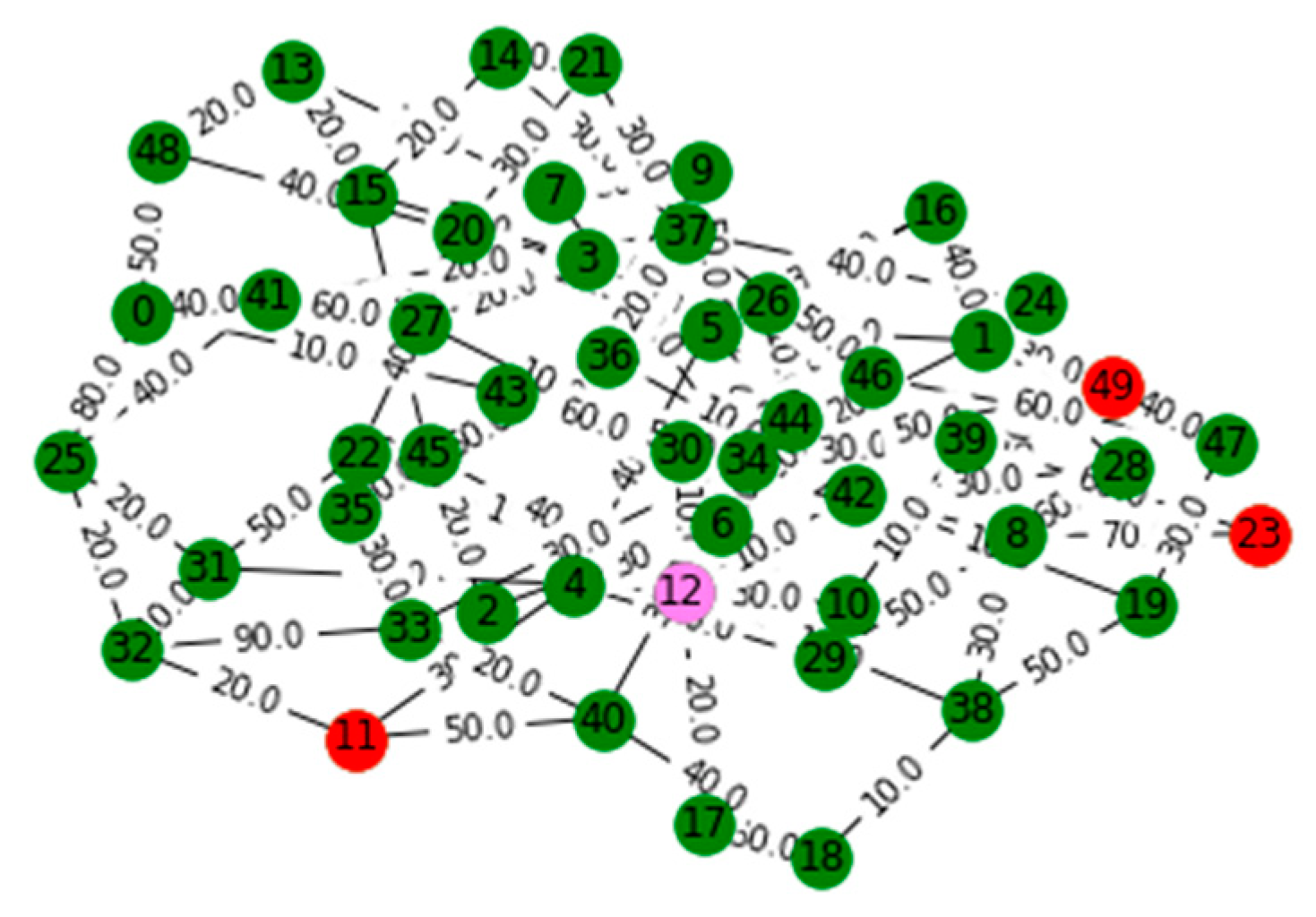
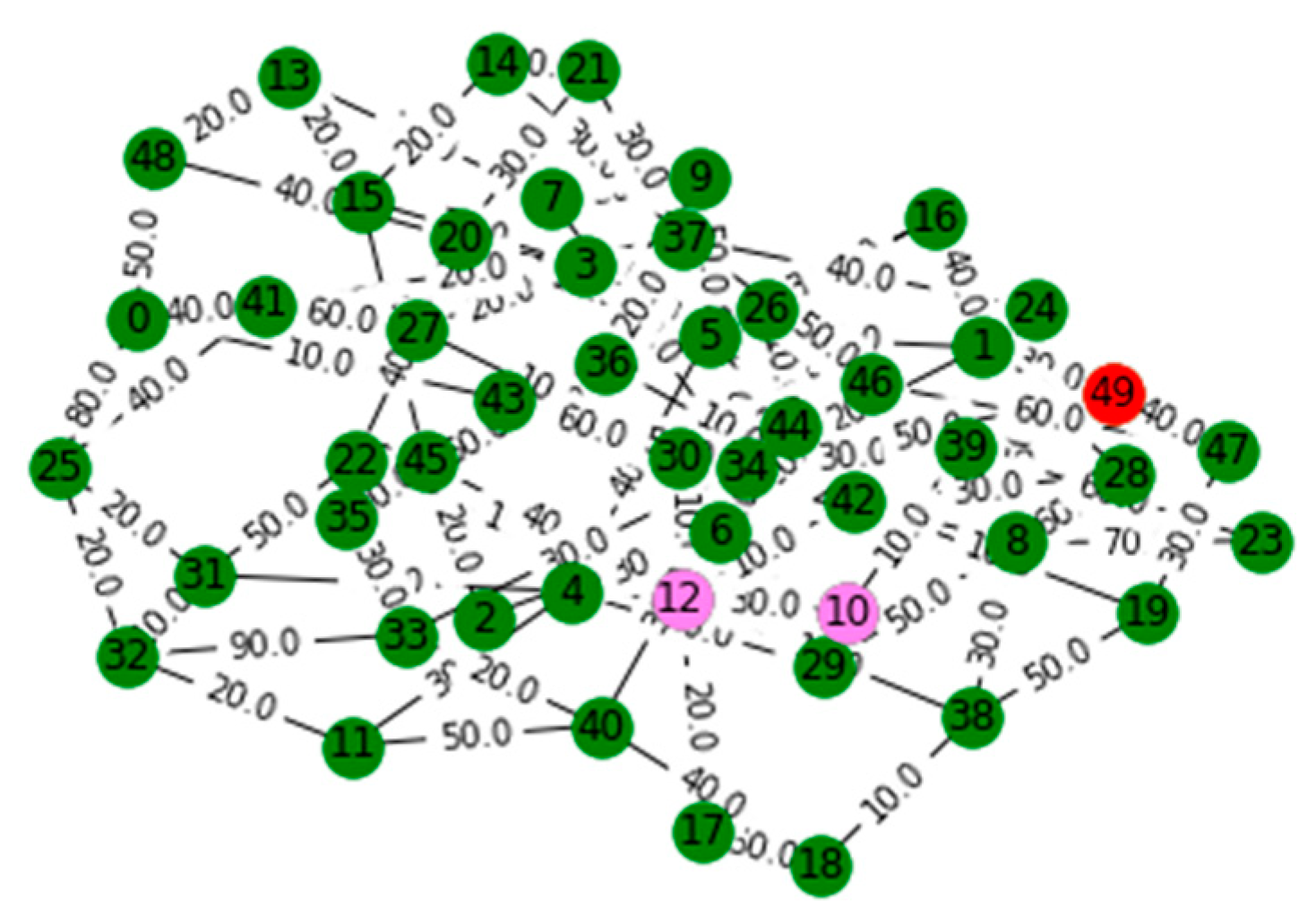
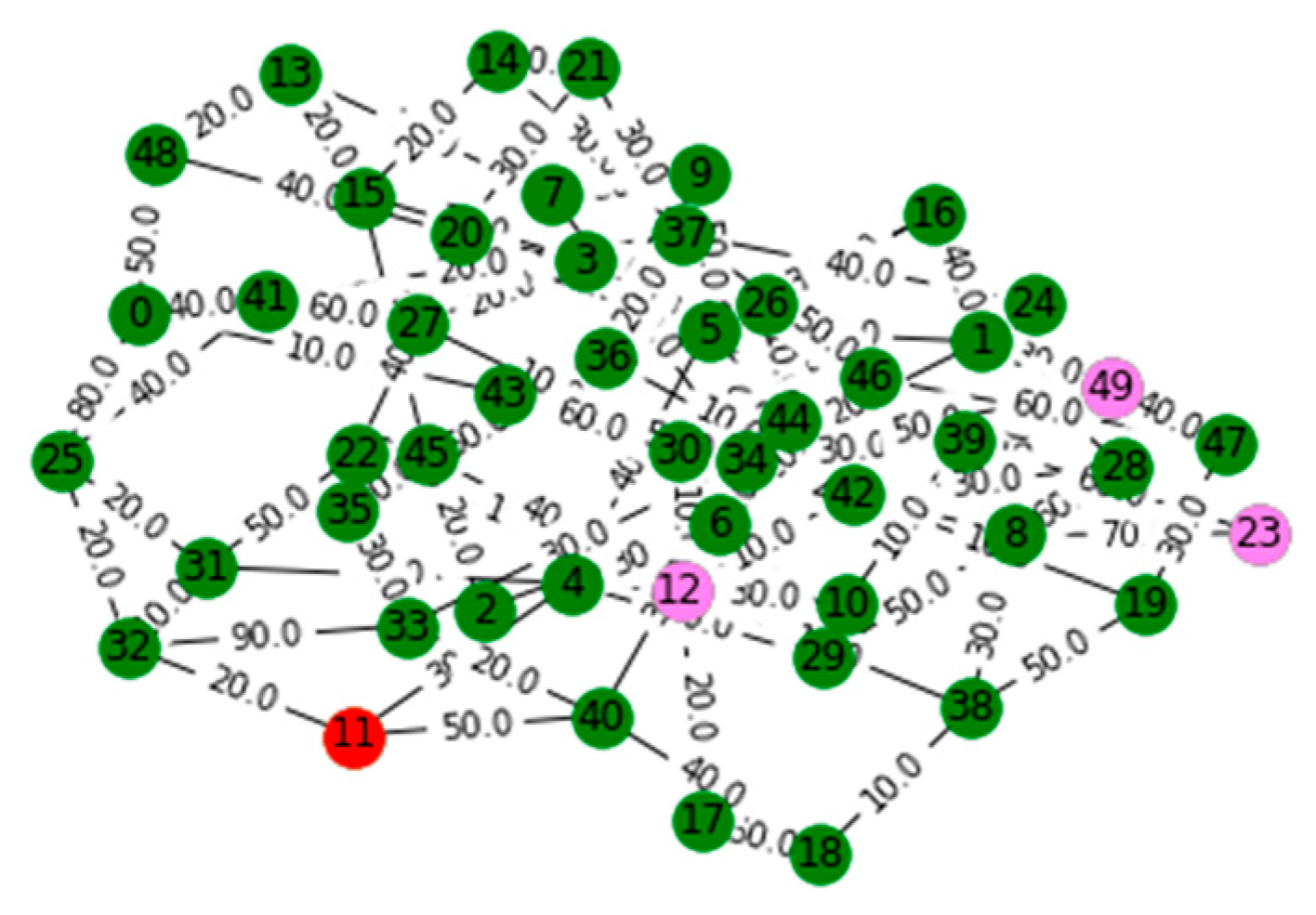
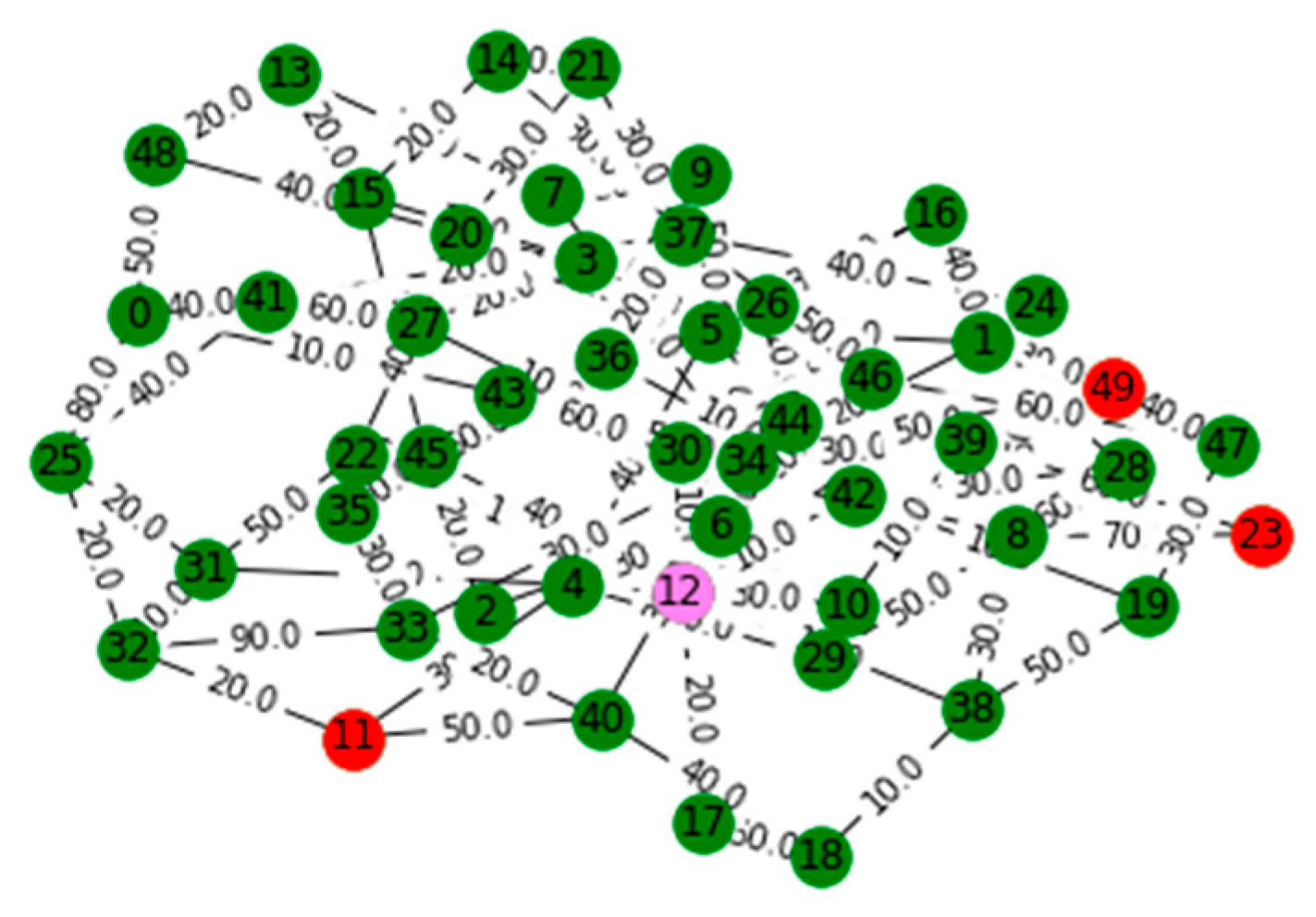
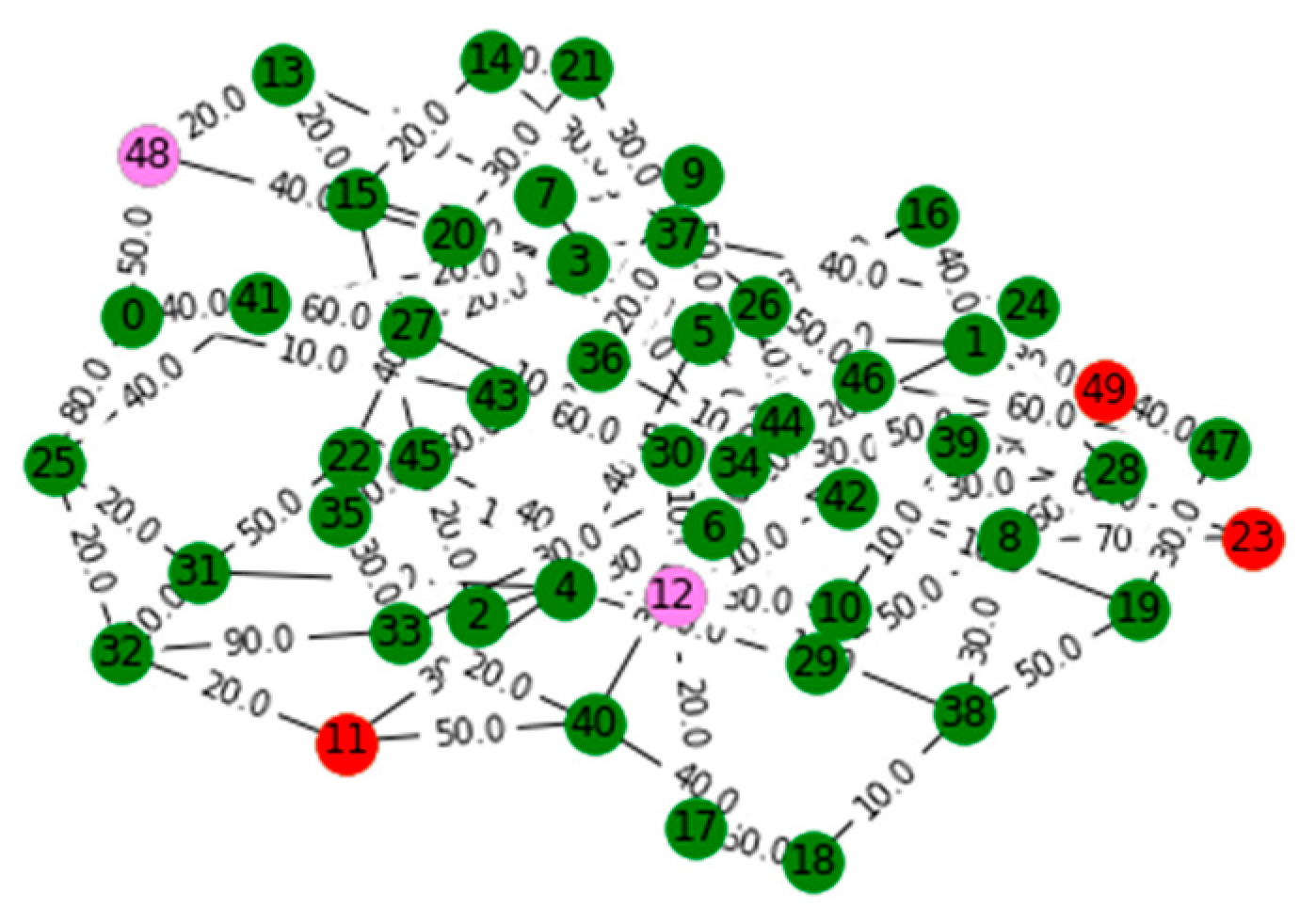
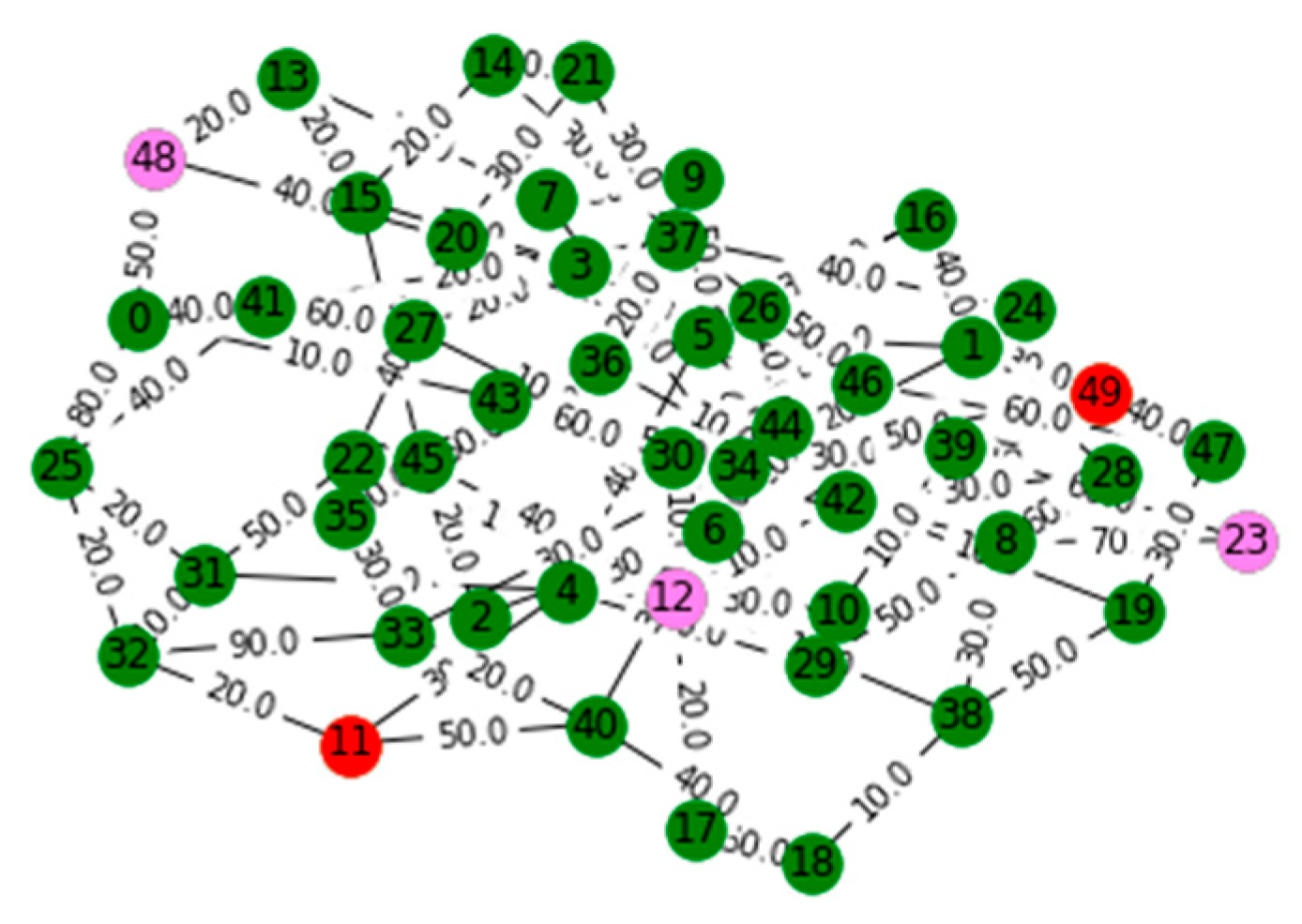
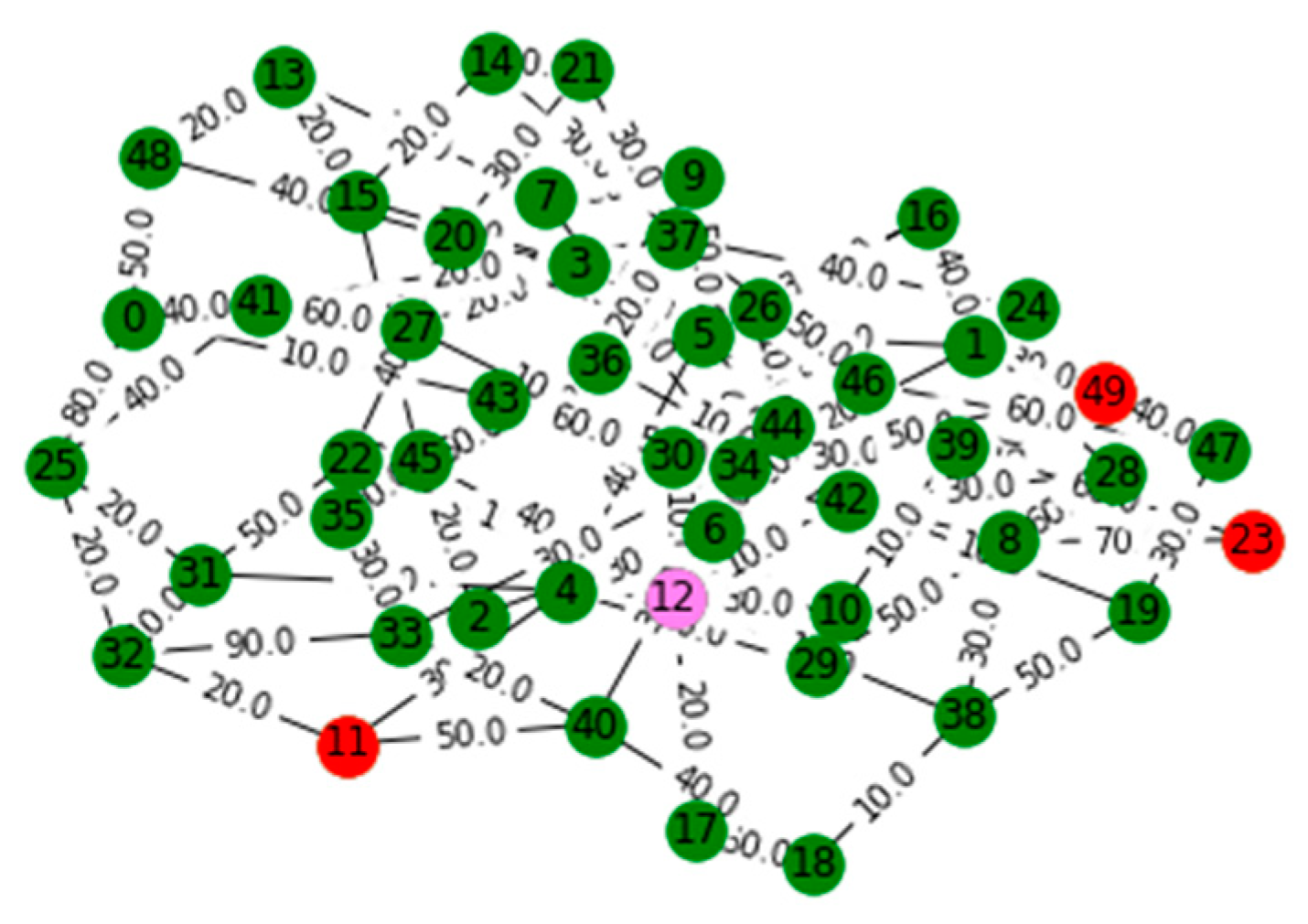
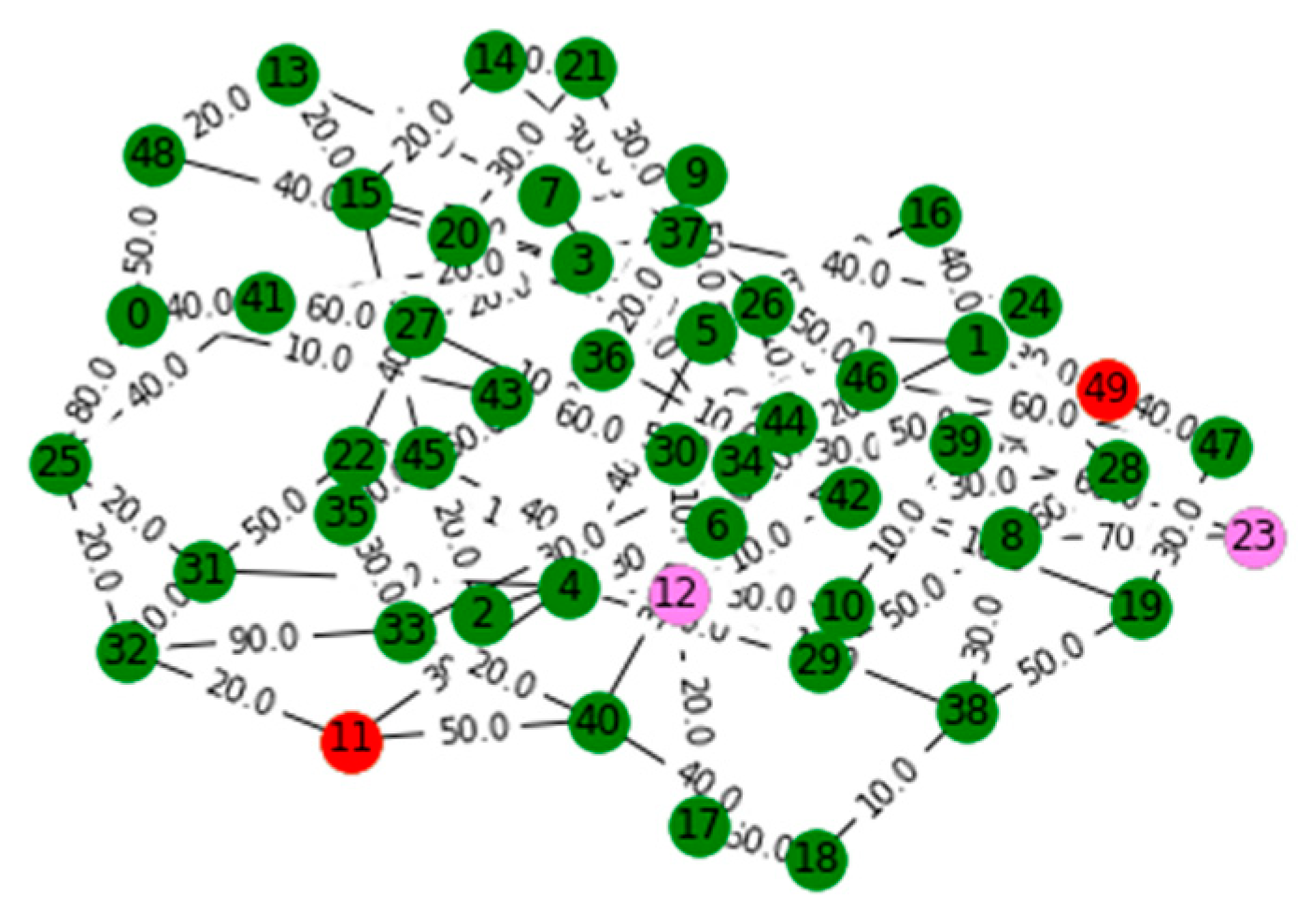
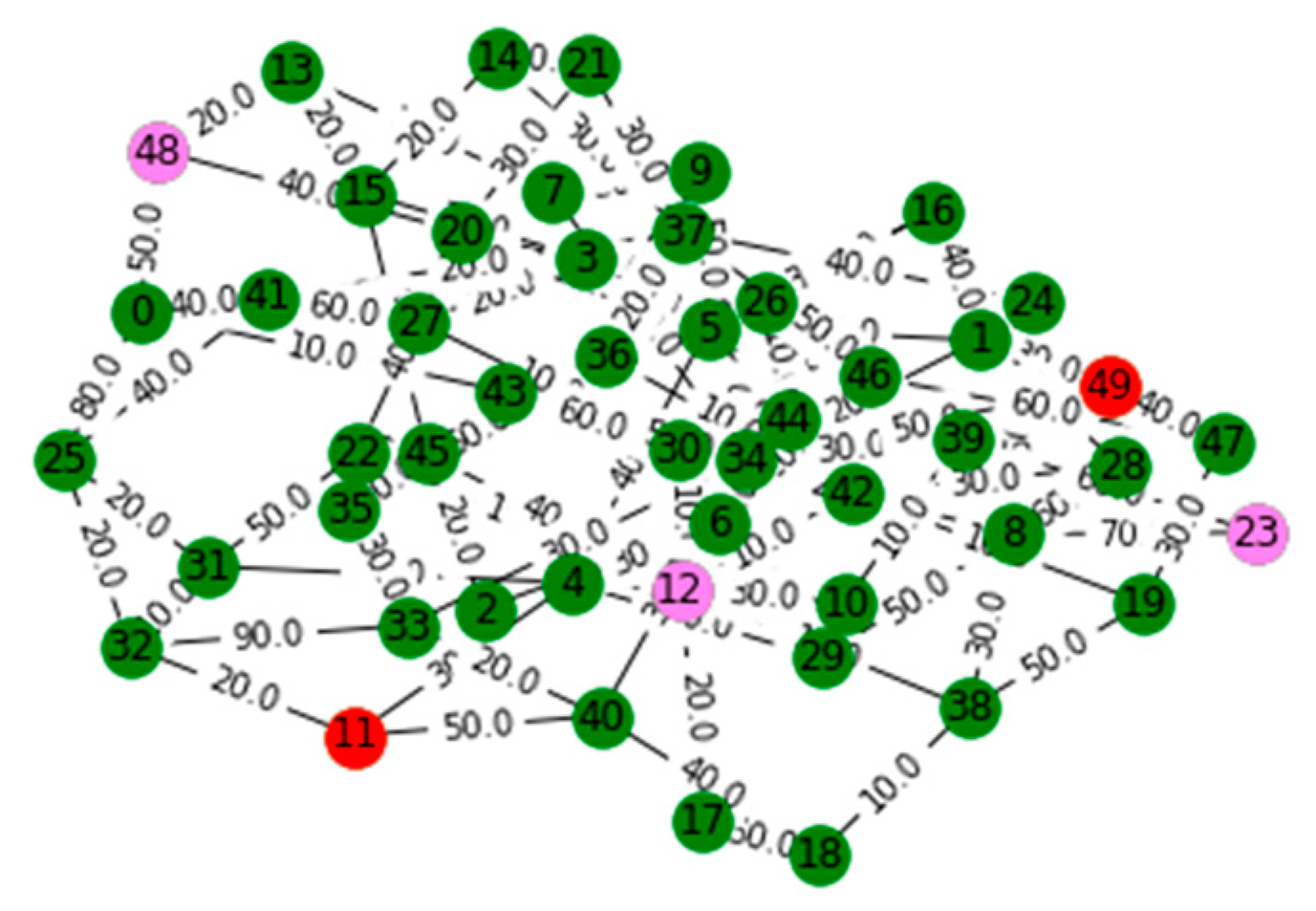
V. Computational Results
Conclusions
References
- Air, Countering, and Missile Threats. "Joint Publication 3-01." United States Joint Chief of Staff: Washington, DC, USA (2017).(starting as 1.).
- Han, Chan Y., Brian J. Lunday, and Matthew J. Robbins. "A game theoretic model for the optimal location of integrated air defense system missile batteries." INFORMS Journal on Computing 28.3 (2016): 405-416. [CrossRef]
- Ulrik Brandes: A Faster Algorithm for Betweenness Centrality. Journal of Mathematical Sociology 25(2):163-177, 2001. [CrossRef]
- Ulrik Brandes: On Variants of Shortest-Path Betweenness Centrality and their Generic Computation. Social Networks 30(2):136-145, 2008. [CrossRef]
- Linton C. Freeman: Centrality in networks: I. Conceptual clarification. Social Networks 1:215-239, 1979.
- pg. 201 of Wasserman, S. and Faust, K., Social Network Analysis: Methods and Applications, 1994, Cambridge University Press.
- Langville, Amy N., and Carl D. Meyer. "A survey of eigenvector methods for web information retrieval." SIAM review 47.1 (2005): 135-161. [CrossRef]
- Phillip Bonacich. “Power and Centrality: A Family of Measures.” American Journal of Sociology 92(5):1170–1182, 1986. [CrossRef]
- Mark E. J. Newman: Scientific collaboration networks. II. Shortest paths, weighted networks, and centrality. Physical Review E 64, 016132, 2001. [CrossRef]
- Duncan J. Watts and Steven H. Strogatz, Collective dynamics of small-world networks, Nature, 393, pp. 440–442, 1998. [CrossRef]
- Telesford, Qawi K., et al. "The ubiquity of small-world networks." Brain connectivity 1.5 (2011): 367-375. [CrossRef]
- Saramäki, Jari, et al. "Generalizations of the clustering coefficient to weighted complex networks." Physical Review E 75.2 (2007): 027105. [CrossRef]
- Kaiser, Marcus. "Mean clustering coefficients: the role of isolated nodes and leafs on clustering measures for small-world networks." New Journal of Physics 10.8 (2008): 083042. [CrossRef]
- Craven, B. D., and Sardar MN Islam. "Ordinary least-squares regression." The SAGE dictionary of quantitative management research (2011): 224-228.
- Wilkening, Dean A. "A simple model for calculating ballistic missile defense effectiveness." Science & Global Security 8.2 (2000): 183-215. [CrossRef]
- Sanderson, Dan. Programming Google App Engine with Python: Build and Run Scalable Python Apps on Google's Infrastructure. " O'Reilly Media, Inc.", 2015.
- Summerfield, Mark. Programming in Python 3: a complete introduction to the Python language. Addison-Wesley Professional, 2010.
- Hagberg, Aric, Pieter Swart, and Daniel S Chult. Exploring network structure, dynamics, and function using NetworkX. No. LA-UR-08-05495; LA-UR-08-5495. Los Alamos National Lab.(LANL), Los Alamos, NM (United States), 2008.
- McKinney, Wes. "pandas: a foundational Python library for data analysis and statistics." Python for high performance and scientific computing 14.9 (2011): 1-9.
- McKinney, Wes. Python for data analysis: Data wrangling with Pandas, NumPy, and IPython. " O'Reilly Media, Inc.", 2012.
- Ari, Niyazi, and Makhamadsulton Ustazhanov. "Matplotlib in python." 2014 11th International Conference on Electronics, Computer and Computation (ICECCO). IEEE, 2014. [CrossRef]
- Virtanen, Pauli, et al. "SciPy 1.0: fundamental algorithms for scientific computing in Python." Nature methods 17.3 (2020): 261-272. [CrossRef]
- McKinney, Wes, Josef Perktold, and Skipper Seabold. "Time series analysis in python with statsmodels." Jarrodmillman Com (2011): 96-102. [CrossRef]
- Pedregosa, Fabian, et al. "Scikit-learn: Machine learning in Python." the Journal of machine Learning research 12 (2011): 2825-2830.
- Barabási, Albert-László. "Scale-free networks: a decade and beyond." science 325.5939 (2009): 412-413. [CrossRef]
- Pran, Rakib Hassan, and Ljupco Todorovski. "Predicting Hidden Links and Missing Nodes in Scale-Free Networks with Artificial Neural Networks." arXiv preprint arXiv:2109.12331 (2021).
- Kadison, Richard V. "The Pythagorean theorem: I. The finite case." Proceedings of the National Academy of Sciences 99.7 (2002): 4178-4184. [CrossRef]
- Finney, Ross L. "Dynamic proofs of Euclidean theorems." Mathematics Magazine 43.4 (1970): 177-185. [CrossRef]
- Attebury, Ramirose, et al. "Google docs: a review." Against the Grain 20.2 (2008): 9. [CrossRef]
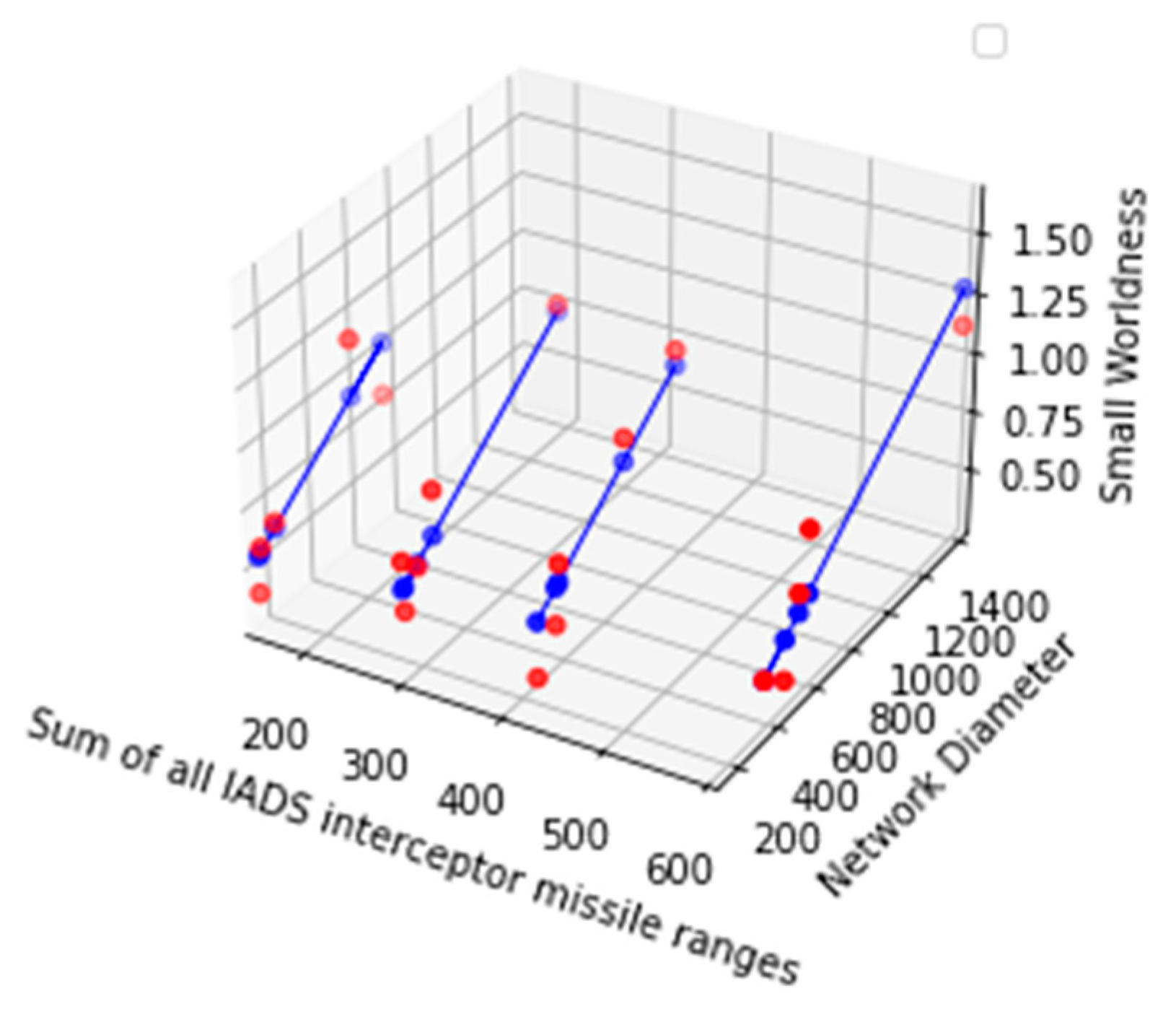
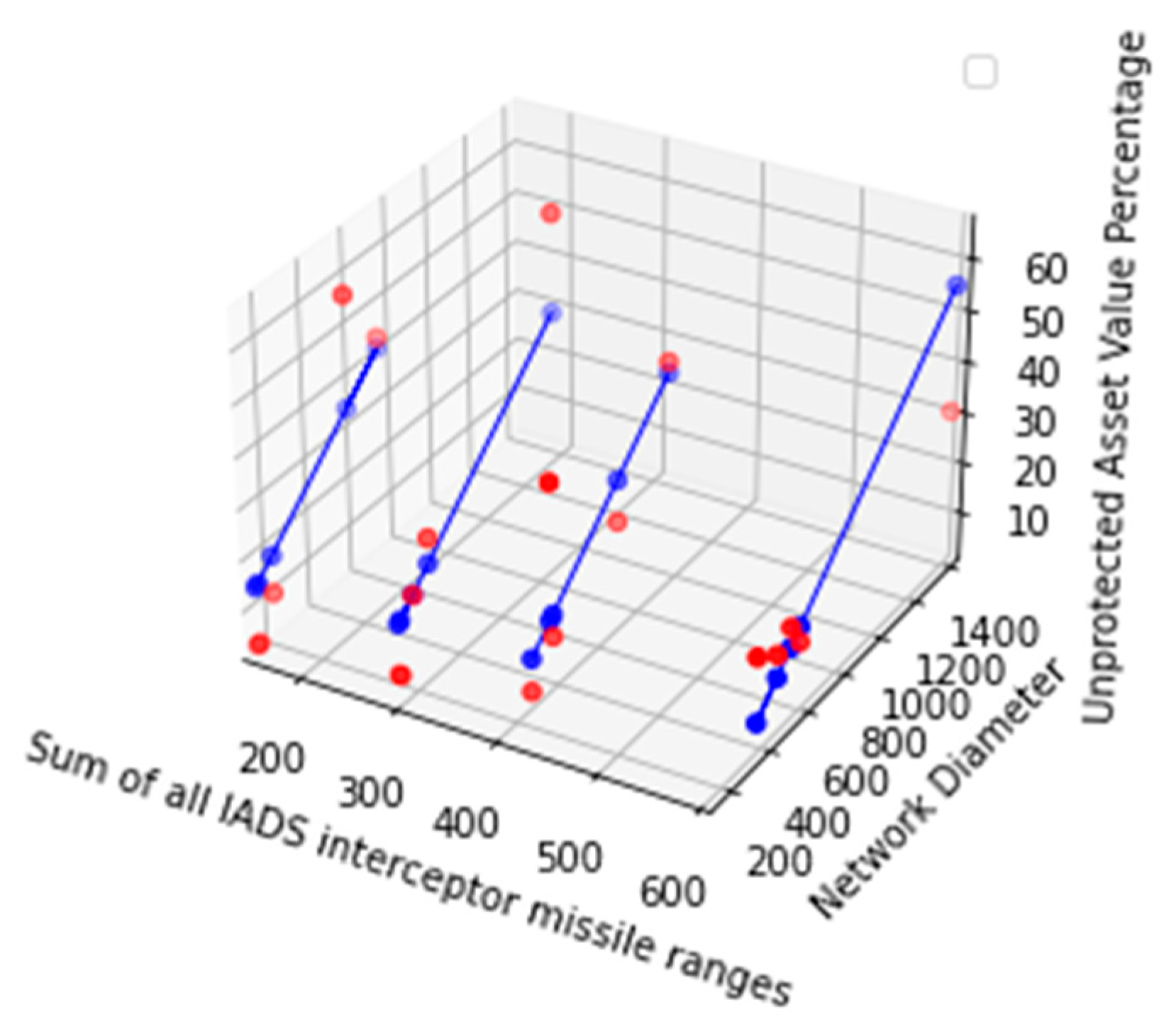
| Strategy number | Generated weighted edge location network’s small worldness | Generated weighted edge location network’s node number |
Generated weighted edge location network’s Diameter |
Generated weighted edge location network’s Minimum edge length and Maximum edge length (Minimum,Maximum) |
Generated weighted edge location network total asset value |
IADS missile batteries Interceptor missile ranges in kilometer |
IADS missile batteries interceptor missile’s interceptor probability | After placing IADS missile batteries, total Unprotected asset value |
After placing IADS missile batteries, total Unprotected asset value Percentage (Worst Case Scenario ) |
| Strategy_1 |
≈0.39692 |
50 |
123.0 km |
(20.5 km, 184.5 km) |
≈14.9 |
80 km, 70 km |
98% | 1.6 | ≈12.52349% |
| Strategy_2 |
≈0.39692 |
50 |
123.0 km |
(20.5 km, 184.5 km) |
≈14.9 |
80 km, 70 km |
98% | 1.6 | ≈12.52349% |
| Strategy_3 |
≈0.39692 |
50 |
123.0 km |
(20.5 km, 184.5 km) |
≈14.9 |
80 km, 70 km |
98% | 0.6 | ≈5.94631% |
| Strategy_4 |
≈0.39692 |
50 |
123.0 km |
(20.5 km, 184.5 km) |
≈14.9 |
80 km, 70 km |
98% | 1.8 | ≈13.83893% |
| Strategy_5 |
≈0.39692 |
50 |
123.0 km |
(20.5 km, 184.5 km) |
≈14.9 |
80 km, 70 km |
98% | 0.2 | ≈3.315436% |
| Strategy_6 |
≈0.39692 |
50 |
123.0 km |
(20.5 km, 184.5 km) |
≈14.9 |
80 km, 70 km |
98% | 1.0 | ≈8.577181% |
| Strategy_7 |
≈0.39692 |
50 |
123.0 km |
(20.5 km, 184.5 km) |
≈14.9 |
80 km, 70 km |
98% | 1.0 | ≈8.577181% |
| Strategy_1 | ≈0.582777 | 50 | 133.0 km | (19 km, 171.0 km) | ≈14.4 |
80 km, 70 km |
98% |
0.3 |
≈4.0416667% |
| Strategy_2 | ≈0.582777 | 50 | 133.0 km | (19 km, 171.0 km) | ≈14.4 |
80 km, 70 km |
98% |
0.3 |
≈4.0416667% |
| Strategy_3 | ≈0.582777 | 50 | 133.0 km | (19 km, 171.0 km) | ≈14.4 |
80 km, 70 km |
98% | 0.9 | ≈8.1250000% |
| Strategy_4 | ≈0.582777 | 50 | 133.0 km | (19 km, 171.0 km) | ≈14.4 |
80 km, 70 km |
98% | 0.4 |
≈4.7222222% |
| Strategy_5 | ≈0.582777 | 50 | 133.0 km | (19 km, 171.0 km) | ≈14.4 |
80 km, 70 km |
98% |
0.2 |
≈3.3611111% |
| Strategy_6 | ≈0.582777 | 50 | 133.0 km | (19 km, 171.0 km) | ≈14.4 |
80 km, 70 km |
98% |
0.3 |
≈4.0416667% |
| Strategy_7 | ≈0.582777 | 50 | 133.0 km | (19 km, 171.0 km) | ≈14.4 |
80 km, 70 km |
98% |
0.3 |
≈4.0416667% |
| Strategy_1 | ≈0.640091 | 50 | 200.0 km | (20.0 km, 160.0 km) | ≈14.3 |
80 km, 70 km |
98% | 4.1 | ≈30.097902% |
| Strategy_2 | ≈0.640091 | 50 | 200.0 km | (20.0 km, 160.0 km) | ≈14.3 |
80 km, 70 km |
98% | 4.5 |
≈32.839161% |
| Strategy_3 | ≈0.640091 | 50 | 200.0 km | (20.0 km, 160.0 km) | ≈14.3 |
80 km, 70 km |
98% | 3.3 | ≈24.615385% |
| Strategy_4 | ≈0.640091 | 50 | 200.0 km | (20.0 km, 160.0 km) | ≈14.3 |
80 km, 70 km |
98% | 1.3 | ≈10.90909% |
| Strategy_5 | ≈0.640091 | 50 | 200.0 km | (20.0 km, 160.0 km) | ≈14.3 |
80 km, 70 km |
98% | 1.3 | ≈10.90909% |
| Strategy_6 | ≈0.640091 | 50 | 200.0 km | (20.0 km, 160.0 km) | ≈14.3 |
80 km, 70 km |
98% | 2.7 | ≈20.503497% |
| Strategy_7 | ≈0.640091 | 50 | 200.0 km | (20.0 km, 160.0 km) | ≈14.3 |
80 km, 70 km |
98% | 2.4 | ≈18.447552% |
| Strategy_1 |
≈0.807039 |
50 | 710.0 km |
(10 km, 70 km) |
≈15.4 |
80 km, 70 km |
98% | 10.5 | ≈68.181818% |
| Strategy_2 |
≈0.807039 |
50 | 710.0 km |
(10 km, 70 km) |
≈15.4 |
80 km, 70 km |
98% |
12.5 |
≈81.545455% |
| Strategy_3 |
≈0.807039 |
50 | 710.0 km |
(10 km, 70 km) |
≈15.4 |
80 km, 70 km |
98% | 7.2 | ≈47.818182% |
| Strategy_4 |
≈0.807039 |
50 | 710.0 km |
(10 km, 70 km) |
≈15.4 |
80 km, 70 km |
98% |
10.6 |
≈69.454545% |
| Strategy_5 |
≈0.807039 |
50 | 710.0 km |
(10 km, 70 km) |
≈15.4 |
80 km, 70 km |
98% |
6.6 |
≈44.00% |
| Strategy_6 |
≈0.807039 |
50 | 710.0 km |
(10 km, 70 km) |
≈15.4 |
80 km, 70 km |
98% |
6.6 |
≈44.00% |
| Strategy_7 |
≈0.807039 |
50 | 710.0 km |
(10 km, 70 km) |
≈15.4 |
80 km, 70 km |
98% |
6.6 |
≈44.00% |
| Strategy_1 |
≈1.145887 |
50 |
560.0 km |
(10 km, 80 km) |
≈14.1 |
80 km, 70 km |
98% |
9.2 |
≈65.943262% |
| Strategy_2 |
≈1.145887 |
50 |
560.0 km |
(10 km, 80 km) |
≈14.1 |
80 km, 70 km |
98% | 9.2 | ≈65.943262% |
| Strategy_3 |
≈1.145887 |
50 |
560.0 km |
(10 km, 80 km) |
≈14.1 |
80 km, 70 km |
98% | 8.4 | ≈60.382979% |
| Strategy_4 |
≈1.145887 |
50 |
560.0 km |
(10 km, 80 km) |
≈14.1 |
80 km, 70 km |
98% | 8.4 | ≈60.382979% |
| Strategy_5 |
≈1.145887 |
50 |
560.0 km |
(10 km, 80 km) |
≈14.1 |
80 km, 70 km |
98% |
7.9 |
≈56.907801% |
| Strategy_6 |
≈1.145887 |
50 |
560.0 km |
(10 km, 80 km) |
≈14.1 |
80 km, 70 km |
98% | 8.4 | ≈60.382979% |
| Strategy_7 |
≈1.145887 |
50 |
560.0 km |
(10 km, 80 km) |
≈14.1 |
80 km, 70 km |
98% | 7.9 | ≈56.907801% |
| Strategy number | Generated weighted edge location network’s small worldness | Generated weighted edge location network’s node number |
Generated weighted edge location network’s Diameter |
Generated weighted edge location network’s Minimum edge length and Maximum edge length (Minimum,Maximum) |
Generated weighted edge location network total asset value |
IADS missile batteries Interceptor missile ranges in kilometer |
IADS missile batteries interceptor missile’s interceptor probability | After placing IADS missile batteries, total Unprotected asset value |
After placing IADS missile batteries, total Unprotected asset value Percentage (Worst Case Scenario ) |
| Strategy_1 | ≈0.423134 | 50 | 210.0 km |
(35 km, 315 km) |
13.8 |
110 km, 90 km, 80 km |
98% | 0.9 | ≈8.39130% |
| Strategy_2 | ≈0.423134 | 50 | 210.0 km |
(35 km, 315 km) |
13.8 |
110 km, 90 km, 80 km |
98% | 1.0 | ≈9.101449% |
| Strategy_3 | ≈0.423134 | 50 | 210.0 km |
(35 km, 315 km) |
13.8 |
110 km, 90 km, 80 km |
98% | 0.6 | ≈6.26087% |
| Strategy_4 | ≈0.423134 | 50 | 210.0 km |
(35 km, 315 km) |
13.8 |
110 km, 90 km, 80 km |
98% | 0.1 | ≈2.71014% |
| Strategy_5 | ≈0.423134 | 50 | 210.0 km |
(35 km, 315 km) |
13.8 |
110 km, 90 km, 80 km |
98% | 0.0 | 2.0% |
| Strategy_6 | ≈0.423134 | 50 | 210.0 km |
(35 km, 315 km) |
13.8 |
110 km, 90 km, 80 km |
98% | 0.4 | ≈4.84058% |
| Strategy_7 | ≈0.423134 | 50 | 210.0 km |
(35 km, 315 km) |
13.8 |
110 km, 90 km, 80 km |
98% | 0.4 | ≈4.84058% |
| Strategy_1 | ≈0.564176 | 50 | 270.0 km |
(18 km, 144 km) |
15.0 |
110 km, 90 km, 80 km |
98% | 4.7 | ≈32.706667% |
| Strategy_2 | ≈0.564176 | 50 | 270.0 km |
(18 km, 144 km) |
15.0 |
110 km, 90 km, 80 km |
98% | 5.5 | ≈37.933333% |
| Strategy_3 | ≈0.564176 | 50 | 270.0 km |
(18 km, 144 km) |
15.0 |
110 km, 90 km, 80 km |
98% | 4.7 | ≈32.706667% |
| Strategy_4 | ≈0.564176 | 50 | 270.0 km |
(18 km, 144 km) |
15.0 |
110 km, 90 km, 80 km |
98% | 2.1 | ≈15.72% |
| Strategy_5 | ≈0.564176 | 50 | 270.0 km |
(18 km, 144 km) |
15.0 |
110 km, 90 km, 80 km |
98% | 2.1 | ≈15.72% |
| Strategy_6 | ≈0.564176 | 50 | 270.0 km |
(18 km, 144 km) |
15.0 |
110 km, 90 km, 80 km |
98% | 4.5 | ≈31.4% |
| Strategy_7 | ≈0.564176 | 50 | 270.0 km |
(18 km, 144 km) |
15.0 |
110 km, 90 km, 80 km |
98% | 4.5 | ≈31.4% |
| Strategy_1 |
≈0.640606 |
50 | 200.0 km |
(25 km, 225 km) |
15.7 |
110 km, 90 km, 80 km |
98% | 0.3 | ≈3.872611% |
| Strategy_2 |
≈0.640606 |
50 | 200.0 km |
(25 km, 225 km) |
15.7 |
110 km, 90 km, 80 km |
98% | 1.1 | ≈8.866242% |
| Strategy_3 |
≈0.640606 |
50 | 200.0 km |
(25 km, 225 km) |
15.7 |
110 km, 90 km, 80 km |
98% | 2.4 | ≈16.980891% |
| Strategy_4 |
≈0.640606 |
50 | 200.0 km |
(25 km, 225 km) |
15.7 |
110 km, 90 km, 80 km |
98% | 1.1 | ≈8.866242% |
| Strategy_5 |
≈0.640606 |
50 | 200.0 km |
(25 km, 225 km) |
15.7 |
110 km, 90 km, 80 km |
98% | 0.1 | ≈2.6242038% |
| Strategy_6 |
≈0.640606 |
50 | 200.0 km |
(25 km, 225 km) |
15.7 |
110 km, 90 km, 80 km |
98% | 1.0 | ≈8.2420382% |
| Strategy_7 |
≈0.640606 |
50 | 200.0 km |
(25 km, 225 km) |
15.7 |
110 km, 90 km, 80 km |
98% | 1.0 | ≈8.2420382% |
| Strategy_1 | ≈0.829442 | 50 | 345.0 km |
(23 km, 184 km) |
15.4 |
110 km, 90 km, 80 km |
98% | 5.1 | ≈34.454545% |
| Strategy_2 | ≈0.829442 | 50 | 345.0 km |
(23 km, 184 km) |
15.4 |
110 km, 90 km, 80 km |
98% | 8.9 | ≈58.636363% |
| Strategy_3 | ≈0.829442 | 50 | 345.0 km |
(23 km, 184 km) |
15.4 |
110 km, 90 km, 80 km |
98% | 8.0 | ≈52.909090% |
| Strategy_4 | ≈0.829442 | 50 | 345.0 km |
(23 km, 184 km) |
15.4 |
110 km, 90 km, 80 km |
98% | 4.1 | ≈28.090909% |
| Strategy_5 | ≈0.829442 | 50 | 345.0 km |
(23 km, 184 km) |
15.4 |
110 km, 90 km, 80 km |
98% | 3.5 | ≈24.272727% |
| Strategy_6 | ≈0.829442 | 50 | 345.0 km |
(23 km, 184 km) |
15.4 |
110 km, 90 km, 80 km |
98% | 5.8 | ≈38.90909% |
| Strategy_7 | ≈0.829442 | 50 | 345.0 km |
(23 km, 184 km) |
15.4 |
110 km, 90 km, 80 km |
98% | 6.2 | ≈41.454545% |
| Strategy_1 | ≈1.16390 | 50 | 960.0 km |
(20 km, 160 km) |
14.2 |
110 km, 90 km, 80 km |
98% | 10.5 | ≈74.464789% |
| Strategy_2 | ≈1.16390 | 50 | 960.0 km |
(20 km, 160 km) |
14.2 |
110 km, 90 km, 80 km |
98% | 10.8 | ≈76.535211% |
| Strategy_3 | ≈1.16390 | 50 | 960.0 km |
(20 km, 160 km) |
14.2 |
110 km, 90 km, 80 km |
98% | 10.8 | ≈76.535211% |
| Strategy_4 | ≈1.16390 | 50 | 960.0 km |
(20 km, 160 km) |
14.2 |
110 km, 90 km, 80 km |
98% | 10.3 | ≈73.084507% |
| Strategy_5 | ≈1.16390 | 50 | 960.0 km |
(20 km, 160 km) |
14.2 |
110 km, 90 km, 80 km |
98% | 9.4 | ≈66.873239% |
| Strategy_6 | ≈1.16390 | 50 | 960.0 km |
(20 km, 160 km) |
14.2 |
110 km, 90 km, 80 km |
98% | 10.2 | ≈72.394366% |
| Strategy_7 | ≈1.16390 | 50 | 960.0 km |
(20 km, 160 km) |
14.2 |
110 km, 90 km, 80 km |
98% | 11.2 | ≈79.295775% |
| Strategy number | Generated weighted edge location network’s small worldness | Generated weighted edge location network’s node number |
Generated weighted edge location network’s Diameter |
Generated weighted edge location network’s Minimum edge length and Maximum edge length (Minimum,Maximum) |
Generated weighted edge location network total asset value |
IADS missile batteries Interceptor missile ranges in kilometer |
IADS missile batteries interceptor missile’s interceptor probability | After placing IADS missile batteries, total Unprotected asset value |
After placing IADS missile batteries, total Unprotected asset value Percentage (Worst Case Scenario ) |
| Strategy_1 |
≈0.25351 |
50 | 270.0 km |
(45 km, 405 km) |
14.1 |
120 km, 110 km, 90 km, 80 km |
98% | 2.4 | ≈18.68085% |
| Strategy_2 | ≈0.25351 | 50 | 270.0 km |
(45 km, 405 km) |
14.1 |
120 km, 110 km, 90 km, 80 km |
98% | 3.8 | ≈28.4113% |
| Strategy_3 | ≈0.25351 | 50 | 270.0 km |
(45 km, 405 km) |
14.1 |
120 km, 110 km, 90 km, 80 km |
98% | 1.7 | ≈13.8156% |
| Strategy_4 | ≈0.25351 | 50 | 270.0 km |
(45 km, 405 km) |
14.1 |
120 km, 110 km, 90 km, 80 km |
98% | 1.4 | ≈11.730% |
| Strategy_5 | ≈0.25351 | 50 | 270.0 km |
(45 km, 405 km) |
14.1 |
120 km, 110 km, 90 km, 80 km |
98% | 0.3 | ≈4.0851% |
| Strategy_6 | ≈0.25351 | 50 | 270.0 km |
(45 km, 405 km) |
14.1 |
120 km, 110 km, 90 km, 80 km |
98% | 1.9 | ≈15.20567% |
| Strategy_7 | ≈0.25351 | 50 | 270.0 km |
(45 km, 405 km) |
14.1 |
120 km, 110 km, 90 km, 80 km |
98% | 1.6 | ≈13.120567% |
| Strategy_1 |
≈0.405311 |
50 | 360.0 km |
(60 km, 540 km) |
13.2 |
120 km, 110 km, 90 km, 80 km |
98% | 4.9 | ≈38.378788% |
| Strategy_2 |
≈0.405311 |
50 | 360.0 km |
(60 km, 540 km) |
13.2 |
120 km, 110 km, 90 km, 80 km |
98% | 6.9 | ≈53.227272% |
| Strategy_3 |
≈0.405311 |
50 | 360.0 km |
(60 km, 540 km) |
13.2 |
120 km, 110 km, 90 km, 80 km |
98% | 6.2 | ≈48.030303% |
| Strategy_4 |
≈0.405311 |
50 | 360.0 km |
(60 km, 540 km) |
13.2 |
120 km, 110 km, 90 km, 80 km |
98% | 5.7 | ≈44.318181% |
| Strategy_5 |
≈0.405311 |
50 | 360.0 km |
(60 km, 540 km) |
13.2 |
120 km, 110 km, 90 km, 80 km |
98% | 5.3 | ≈41.34848% |
| Strategy_6 |
≈0.405311 |
50 | 360.0 km |
(60 km, 540 km) |
13.2 |
120 km, 110 km, 90 km, 80 km |
98% | 7.7 | ≈59.2% |
| Strategy_7 |
≈0.405311 |
50 | 360.0 km |
(60 km, 540 km) |
13.2 |
120 km, 110 km, 90 km, 80 km |
98% | 5.6 | ≈43.575757% |
| Strategy_1 | ≈0.652449 | 50 | 375.0 km |
(25 km, 200 km) |
16.2 |
120 km, 110 km, 90 km, 80 km |
98% | 5.2 | ≈33.45679% |
| Strategy_2 | ≈0.652449 | 50 | 375.0 km |
(25 km, 200 km) |
16.2 |
120 km, 110 km, 90 km, 80 km |
98% | 4.6 | ≈29.82716% |
| Strategy_3 | ≈0.652449 | 50 | 375.0 km |
(25 km, 200 km) |
16.2 |
120 km, 110 km, 90 km, 80 km |
98% | 3.0 | ≈20.14815% |
| Strategy_4 | ≈0.652449 | 50 | 375.0 km |
(25 km, 200 km) |
16.2 |
120 km, 110 km, 90 km, 80 km |
98% | 3.6 | ≈23.7778% |
| Strategy_5 | ≈0.652449 | 50 | 375.0 km |
(25 km, 200 km) |
16.2 |
120 km, 110 km, 90 km, 80 km |
98% | 1.5 | ≈11.074074% |
| Strategy_6 | ≈0.652449 | 50 | 375.0 km |
(25 km, 200 km) |
16.2 |
120 km, 110 km, 90 km, 80 km |
98% | 5.1 | ≈32.85185% |
| Strategy_7 | ≈0.652449 | 50 | 375.0 km |
(25 km, 200 km) |
16.2 |
120 km, 110 km, 90 km, 80 km |
98% | 4.7 | ≈30.4321% |
| Strategy_1 |
≈0.934170 |
50 | 697.0 km |
(17 km, 119 km) |
14.6 |
120 km, 110 km, 90 km, 80 km |
98% | 6.7 | ≈46.9726% |
| Strategy_2 |
≈0.934170 |
50 | 697.0 km |
(17 km, 119 km) |
14.6 |
120 km, 110 km, 90 km, 80 km |
98% | 8.6 | ≈59.7260% |
| Strategy_3 |
≈0.934170 |
50 | 697.0 km |
(17 km, 119 km) |
14.6 |
120 km, 110 km, 90 km, 80 km |
98% | 6.8 | ≈47.64383% |
| Strategy_4 |
≈0.934170 |
50 | 697.0 km |
(17 km, 119 km) |
14.6 |
120 km, 110 km, 90 km, 80 km |
98% | 5.7 | ≈40.26027% |
| Strategy_5 |
≈0.934170 |
50 | 697.0 km |
(17 km, 119 km) |
14.6 |
120 km, 110 km, 90 km, 80 km |
98% | 3.0 | ≈22.136986% |
| Strategy_6 |
≈0.934170 |
50 | 697.0 km |
(17 km, 119 km) |
14.6 |
120 km, 110 km, 90 km, 80 km |
98% | 3.1 | ≈22.8082% |
| Strategy_7 |
≈0.934170 |
50 | 697.0 km |
(17 km, 119 km) |
14.6 |
120 km, 110 km, 90 km, 80 km |
98% | 4.0 | ≈28.849315% |
| Strategy_1 |
≈1.11291 |
50 | 960.0 km |
(15 km, 135 km) |
16.1 |
120 km, 110 km, 90 km, 80 km |
98% | 9.7 | ≈61.043478% |
| Strategy_2 |
≈1.11291 |
50 | 960.0 km |
(15 km, 135 km) |
16.1 |
120 km, 110 km, 90 km, 80 km |
98% | 10.3 | ≈64.695652% |
| Strategy_3 |
≈1.11291 |
50 | 960.0 km |
(15 km, 135 km) |
16.1 |
120 km, 110 km, 90 km, 80 km |
98% | 11.4 | ≈71.39130% |
| Strategy_4 |
≈1.11291 |
50 | 960.0 km |
(15 km, 135 km) |
16.1 |
120 km, 110 km, 90 km, 80 km |
98% | 11.8 | ≈73.826089% |
| Strategy_5 |
≈1.11291 |
50 | 960.0 km |
(15 km, 135 km) |
16.1 |
120 km, 110 km, 90 km, 80 km |
98% | 7.0 | ≈44.608696% |
| Strategy_6 |
≈1.11291 |
50 | 960.0 km |
(15 km, 135 km) |
16.1 |
120 km, 110 km, 90 km, 80 km |
98% | 9.7 | ≈61.043478% |
| Strategy_7 |
≈1.11291 |
50 | 960.0 km |
(15 km, 135 km) |
16.1 |
120 km, 110 km, 90 km, 80 km |
98% | 10.0 | ≈62.869565% |
| Strategy number | Generated weighted edge location network’s small worldness | Generated weighted edge location network’s node number |
Generated weighted edge location network’s Diameter |
Generated weighted edge location network’s Minimum edge length and Maximum edge length (Minimum,Maximum) |
Generated weighted edge location network total asset value |
IADS missile batteries Interceptor missile ranges in kilometer |
IADS missile batteries interceptor missile’s interceptor probability | After placing IADS missile batteries, total Unprotected asset value |
After placing IADS missile batteries, total Unprotected asset value Percentage (Worst Case Scenario ) |
| Strategy_1 | ≈0.344096 | 50 |
480.0 km |
(80.0 km, 640.0 km) |
16.2 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 3.3 | ≈21.96296% |
| Strategy_2 | ≈0.344096 | 50 |
480.0 km |
(80.0 km, 640.0 km) |
16.2 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 3.8 | ≈24.987654% |
| Strategy_3 | ≈0.344096 | 50 |
480.0 km |
(80.0 km, 640.0 km) |
16.2 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 4.5 | ≈29.2222% |
| Strategy_4 | ≈0.344096 | 50 |
480.0 km |
(80.0 km, 640.0 km) |
16.2 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 3.8 | ≈24.98765% |
| Strategy_5 | ≈0.344096 | 50 |
480.0 km |
(80.0 km, 640.0 km) |
16.2 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 2.3 | ≈15.91358% |
| Strategy_6 | ≈0.344096 | 50 |
480.0 km |
(80.0 km, 640.0 km) |
16.2 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 4.0 | ≈26.19753% |
| Strategy_7 | ≈0.344096 | 50 |
480.0 km |
(80.0 km, 640.0 km) |
16.2 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 3.7 | ≈24.382716% |
| Strategy_1 | ≈0.431319 | 50 | 375.0 km |
(75.0 km, 675.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 8.6 | ≈59.333% |
| Strategy_2 | ≈0.431319 | 50 | 375.0 km |
(75.0 km, 675.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 10.5 | 72.0% |
| Strategy_3 | ≈0.431319 | 50 | 375.0 km |
(75.0 km, 675.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 5.3 | ≈37.3333% |
| Strategy_4 | ≈0.431319 | 50 | 375.0 km |
(75.0 km, 675.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 4.4 | ≈31.333% |
| Strategy_5 | ≈0.431319 | 50 | 375.0 km |
(75.0 km, 675.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 2.6 | ≈19.33333% |
| Strategy_6 | ≈0.431319 | 50 | 375.0 km |
(75.0 km, 675.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 7.3 | ≈50.66667% |
| Strategy_7 | ≈0.431319 | 50 | 375.0 km |
(75.0 km, 675.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 4.6 | ≈32.6666% |
| Strategy_1 | ≈0.652398 | 50 | 550.0 km |
(50.0 km, 400.0 km) |
15.3 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 5.5 | ≈37.228758% |
| Strategy_2 | ≈0.652398 | 50 | 550.0 km |
(50.0 km, 400.0 km) |
15.3 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% |
6.9 |
≈46.196078% |
| Strategy_3 | ≈0.652398 | 50 | 550.0 km |
(50.0 km, 400.0 km) |
15.3 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 6.4 | ≈42.993464% |
| Strategy_4 | ≈0.652398 | 50 | 550.0 km |
(50.0 km, 400.0 km) |
15.3 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% |
4.7 |
≈32.104575% |
| Strategy_5 | ≈0.652398 | 50 | 550.0 km |
(50.0 km, 400.0 km) |
15.3 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 2.6 | ≈18.65359% |
| Strategy_6 | ≈0.652398 | 50 | 550.0 km |
(50.0 km, 400.0 km) |
15.3 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 6.8 | ≈45.555556% |
| Strategy_7 | ≈0.652398 | 50 | 550.0 km |
(50.0 km, 400.0 km) |
15.3 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 5.1 | ≈34.666667% |
| Strategy_1 |
≈0.880917 |
50 | 600.0 km |
(40.0 km, 360.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% |
4.9 |
≈34.666667% |
| Strategy_2 |
≈0.880917 |
50 | 600.0 km |
(40.0 km, 360.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 6.7 | ≈46.666667% |
| Strategy_3 |
≈0.880917 |
50 | 600.0 km |
(40.0 km, 360.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 5.5 | ≈38.666667% |
| Strategy_4 |
≈0.880917 |
50 | 600.0 km |
(40.0 km, 360.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 4.4 | ≈31.33333% |
| Strategy_5 |
≈0.880917 |
50 | 600.0 km |
(40.0 km, 360.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 1.8 | 14.0% |
| Strategy_6 |
≈0.880917 |
50 | 600.0 km |
(40.0 km, 360.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 6.5 | ≈45.333333% |
| Strategy_7 |
≈0.880917 |
50 | 600.0 km |
(40.0 km, 360.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 5.7 | ≈40.00% |
| Strategy_1 |
≈1.12557 |
50 |
1425.0 km |
(25.0 km, 250.0 km) |
14.0 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 6.5 | ≈47.5% |
| Strategy_2 |
≈1.12557 |
50 |
1425.0 km |
(25.0 km, 250.0 km) |
14.0 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 7.9 | ≈57.3% |
| Strategy_3 |
≈1.12557 |
50 |
1425.0 km |
(25.0 km, 250.0 km) |
14.0 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 7.5 | ≈54.5% |
| Strategy_4 |
≈1.12557 |
50 |
1425.0 km |
(25.0 km, 250.0 km) |
14.0 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 7.1 | ≈51.7% |
| Strategy_5 |
≈1.12557 |
50 |
1425.0 km |
(25.0 km, 250.0 km) |
14.0 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 4.1 | ≈30.7% |
| Strategy_6 |
≈1.12557 |
50 |
1425.0 km |
(25.0 km, 250.0 km) |
14.0 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 6.6 | ≈48.2% |
| Strategy_7 |
≈1.12557 |
50 |
1425.0 km |
(25.0 km, 250.0 km) |
14.0 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 6.9 | ≈50.3% |
| Strategy number | Generated weighted edge location network’s small worldness | Generated weighted edge location network’s node number |
Generated weighted edge location network’s Diameter |
Generated weighted edge location network’s Minimum edge length and Maximum edge length (Minimum,Maximum) |
Generated weighted edge location network total asset value |
IADS missile batteries Interceptor missile ranges in kilometer |
IADS missile batteries interceptor missile’s interceptor probability | After placing IADS missile batteries, total Unprotected asset value |
After placing IADS missile batteries, total Unprotected asset value Percentage (Worst Case Scenario ) |
| Strategy_5 |
≈0.39692 |
50 |
123.0 km |
(20.5 km, 184.5 km) |
≈14.9 |
80 km, 70 km |
98% | 0.2 | ≈3.315436% |
| Strategy_5 | ≈0.582777 | 50 | 133.0 km | (19 km, 171.0 km) | ≈14.4 |
80 km, 70 km |
98% |
0.2 |
≈3.3611111% |
| Strategy_5 | ≈0.640091 | 50 | 200.0 km | (20.0 km, 160.0 km) | ≈14.3 |
80 km, 70 km |
98% | 1.3 | ≈10.90909% |
|
Strategy_5Or, Strategy_6Or, Strategy_7 |
≈0.807039 |
50 | 710.0 km |
(10 km, 70 km) |
≈15.4 |
80 km, 70 km |
98% |
6.6 |
≈44.00% |
| Strategy_5 |
≈1.145887 |
50 |
560.0 km |
(10 km, 80 km) |
≈14.1 |
80 km, 70 km |
98% |
7.9 |
≈56.907801% |
| Strategy_5 | ≈0.423134 | 50 | 210.0 km |
(35 km, 315 km) |
13.8 |
110 km, 90 km, 80 km |
98% | 0.0 | 2.0% |
|
Strategy_4 Or, Strategy_5 |
≈0.564176 | 50 | 270.0 km |
(18 km, 144 km) |
15.0 |
110 km, 90 km, 80 km |
98% | 2.1 | ≈15.72% |
| Strategy_5 |
≈0.640606 |
50 | 200.0 km |
(25 km, 225 km) |
15.7 |
110 km, 90 km, 80 km |
98% | 0.1 | ≈2.6242038% |
| Strategy_5 | ≈0.829442 | 50 | 345.0 km |
(23 km, 184 km) |
15.4 |
110 km, 90 km, 80 km |
98% | 3.5 | ≈24.272727% |
| Strategy_5 | ≈1.16390 | 50 | 960.0 km |
(20 km, 160 km) |
14.2 |
110 km, 90 km, 80 km |
98% | 9.4 | ≈66.873239% |
| Strategy_5 | ≈0.25351 | 50 | 270.0 km |
(45 km, 405 km) |
14.1 |
120 km, 110 km, 90 km, 80 km |
98% | 0.3 | ≈4.0851% |
| Strategy_5 |
≈0.405311 |
50 | 360.0 km |
(60 km, 540 km) |
13.2 |
120 km, 110 km, 90 km, 80 km |
98% | 5.3 | ≈41.34848% |
| Strategy_5 | ≈0.652449 | 50 | 375.0 km |
(25 km, 200 km) |
16.2 |
120 km, 110 km, 90 km, 80 km |
98% | 1.5 | ≈11.074074% |
| Strategy_5 |
≈0.934170 |
50 | 697.0 km |
(17 km, 119 km) |
14.6 |
120 km, 110 km, 90 km, 80 km |
98% | 3.0 | ≈22.136986% |
| Strategy_5 |
≈1.11291 |
50 | 960.0 km |
(15 km, 135 km) |
16.1 |
120 km, 110 km, 90 km, 80 km |
98% | 7.0 | ≈44.608696% |
| Strategy_5 | ≈0.344096 | 50 |
480.0 km |
(80.0 km, 640.0 km) |
16.2 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 2.3 | ≈15.91358% |
| Strategy_5 | ≈0.431319 | 50 | 375.0 km |
(75.0 km, 675.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 2.6 | ≈19.33333% |
| Strategy_5 | ≈0.652398 | 50 | 550.0 km |
(50.0 km, 400.0 km) |
15.3 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 2.6 | ≈18.65359% |
| Strategy_5 |
≈0.880917 |
50 | 600.0 km |
(40.0 km, 360.0 km) |
14.7 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 1.8 | 14.0% |
| Strategy_5 |
≈1.12557 |
50 |
1425.0 km |
(25.0 km, 250.0 km) |
14.0 |
200 km, 120 km, 110 km, 90 km, 80 km |
98% | 4.1 | ≈30.7% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





