Submitted:
03 February 2023
Posted:
10 February 2023
You are already at the latest version
Abstract
Keywords:
MSC: 11A41, 11A51
1. Introduction
2. Related Work
2.1. Traditional Wheel factorization method (WFM)
| Algorithm 1: WFM [33] |
 |
2.2. Forward WFM (FWFM)
| Algorithm 2: FactorBasis [33] |
|
1 Input: A composite integer
2 if return 2
3 if return 3
4 if return 5
5 if return 7
6 Otherwise return 1
7 Output: Either a prime number or 1.
|
| Algorithm 3: Forward Wheel Factoring Method (FWFM) [33] |
 |
2.3. Backward WFM (BWFM)
| Algorithm 4: TurnTest [33] |
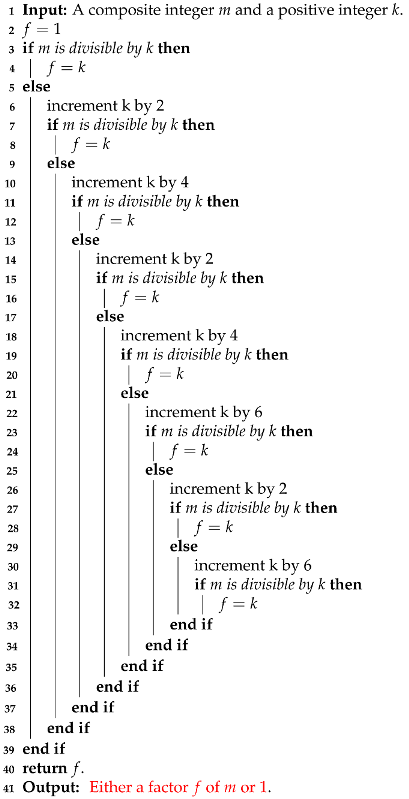 |
| Algorithm 5: Backward Wheel Factoring Method (BWFM) [33] |
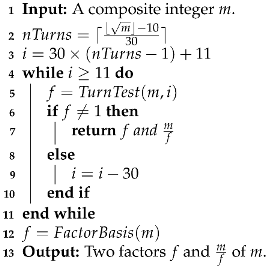 |
3. The Modified Wheel Factorization Method (MWFM)
| Algorithm 6: NewFactorBasis |
 |
| Algorithm 7: NewTurnTest |
 |
| Algorithm 8: Modified Wheel Factorization Method (MWFM) |
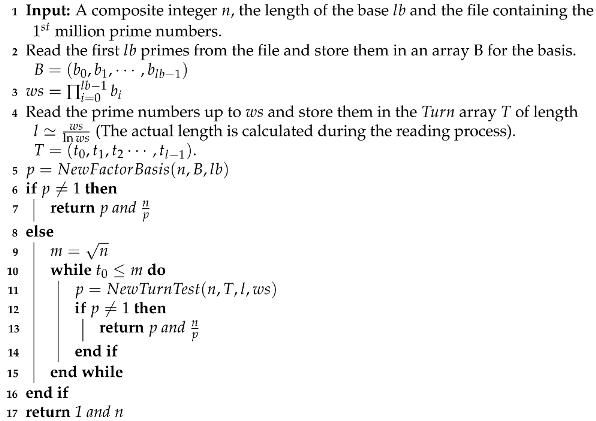 |
4. An Example
5. Experiments
5.1. Experimental Specifications
5.2. Execution Time
6. Discussion
- MWFM takes less time to execute than BWFM, except when the size equals 11 digits. See Table 2.
- On average, the percentage of improvement for MWFM over BWFM is . For all cases, the minimal and highest improvements are and , respectively. See Table 3.
- The running time of MWFM decreases as the wheel size increases from 4 to 8. See Table 4.
- The main disadvantage of MWFM is that it requires an array T, which will be rather huge if we use more than 8 prime integers as a basis.
- Another flaw is that the method does not employ a theoretical foundation to identify the optimal number of prime integers to use as a basis.
7. Conclusion
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Akchiche O., Khadir O. Factoring RSA moduli with primes sharing bits in the middle. Appl Algebra Eng. Commun. Comput. 2018, 29(3), 245–259. [CrossRef]
- Atanassov E., Georgiev D., Manev N. Number theory algorithms on GPU clusters. Modeling and Optimization in Science and Technologies, Springer 2014, (2), 131–138.
- Bahig HM., Nassr DI., Bhery A. Factoring RSA modulus with primes not necessarily sharing least significant bits.Appl Math Inform Sci2017, (11), 243 – 249. [CrossRef]
- Bahig HM., Nassr DI., Bhery A., Nitaj A. A unified method for private exponent attacks on RSA using lattices. Int J. Found. Comput. Sci. 2020, 31(2). 207 – 231. [CrossRef]
- Bahig HM., Mohammed A., Khaled A., AlGhadhban A., Bahig HM. Performance analysis of fermat factorization algorithms.Int J Adv Comput Sci Appl2020, 11(12), 340–350. [CrossRef]
- Bahig HM, Bahig HM, Kotb Y. Fermat factorization using a multi-core system. Int. J. Adv. Comput. Sci. Appl.2020, 11(4). [CrossRef]
- Brent RP. Some parallel algorithms for integer factorisation. In: Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinfor-matics)1999,(1685), 1–22.
- Durmus O., Cabuk UC., Dalkilic F. A study on the performance of base-m polynomial selection algorithm using GPU. 2020.
- Fathy K., Bahig H., Farag M. Speeding up multi- exponentiation algorithm on a multicore sys-tem. J. Egypt Math. Soc.2018, (26).
- Fathy KA., Bahig HM., Ragab AA. A fast parallel modular exponentiation algorithm. Arab. J. Sci. Eng.2018, (43). [CrossRef]
- Fujioka A., Suzuki K., Xagawa K., Yoneyama K. Strongly secure authenticated key exchange from factoring, codes, and lattices.Design Codes Cryptogr2015,(76), 469–504. [CrossRef]
- GMP. library, GNU multiple precision arithmetic library. https://gmplib. org/.
- Gulida KR., Ultanov IR. Comparative analysis of integer factorization algorithms using CPU and GPU. MANAS J Eng 2017, (5), 53–63.
- Varadharajan S., Raddum H. Factorization using binary decision diagrams. Cryptogr Commun. 2019, (11), 443–460. [CrossRef]
- Koundinya AK., Harish G., Srinath NK., Raghavendra GE., Pramod YV., Sandeep R., Punith KG. Performance analysis of parallel pollard′s RHO factoring algorithm. Int. J. Comput. Sci. Inform. Technol. 2013, (5). [CrossRef]
- Lenstra AK. Integer factoring. Designs Codes Cryptogr. 2000, (19), 101–128. [CrossRef]
- Menezes AJ., Katz J., van Oorschot PC., Vanstone SA. Handbook of Applied Cryptography. CRC Press1996.
- Montgomery PL. A survey of modern integer factorization algorithms. CWI Quart1994, (7), 337–366.
- Nassr DI., Bahig HM., Bhery A., Daoud SS. A new rsa vulnerability using continued fractions. In AICCSA 08 - 6th IEEE/ACS International Conference on Computer Systems and Applications2008, 694–701.
- Nimbalkar AB.. The digital signature schemes based on two hard problems: factorization and discrete logarithm.In: In: Bokhari M, Agrawal N, Saini D (eds) Cyber Security 2018, (729), 493–498. [CrossRef]
- OpenMP. https://www.openmp.org/.
- Peng WC., Wang BN., Hu F., Wang YJ., Fang XJ., Chen XY., Wang C. Factoring larger integers with fewer qubits via quantum annealing with optimized parameters.Sci. China Phys. Mech. Astron. 2019, (62). [CrossRef]
- Poulakis D. A public key encryption scheme based on factoring and discrete logarithm. J. Discrete Math. Sci. Cryptogr.2009, (12), 745–452. [CrossRef]
- Pritchard P. Explaining the wheel sieve. Acta Inform. 1982, (17), 477–485. [CrossRef]
- Rivest RL., Shamir A., Adleman LM. A method for obtaining digital signatures and public key cryptosystems.Commun ACM1987, 120–126. [CrossRef]
- Rubinstein-Salzedo S. Clever factorization algorithms and primality testing. 2018.
- Shor PW. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer.SIAM J. Comput. 1997, (26), 1484–1509. [CrossRef]
- Valenta L., Cohney S., Liao A., Fried J., Bodduluri S., Heninger N. Factoring as a service. In: Grossklags J., Preneel B. (eds) Financial cryptography and data security. 2017, (6903), 321–338.
- Wu L., Cai HJ., Gong Z. The integer factorization algorithm with pisano period. IEEE Access 2019, (7), 167250–167259. [CrossRef]
- Yan SY. Primality testing and integer factorization in public-key cryptography. advances in information security. Springer 2009 ,(11).
- Yan SY. Factoring Based Cryptography.2019, 217–286.
- Yan SY., James G. Can integer factorization be in p?. In: International Conference on Computational Inteligence for Modelling Control and Automation and International Conference on Intelligent Agents Web Technologies and International Commerce (CIMCA′06) 2006, 266–266. [CrossRef]
- Bahig HM., Nassr DI., Mohammed A., Khaled A., Bahig HM. Speeding up wheel factoring method. The Journal of Supercomputing2022. [CrossRef]
- Bahig, H.M.; Nassr, D.I.; Mahdi, M.A.; Bahig, H.M. Small Private Exponent Attacks on RSA Using Continued Fractions and Multicore Systems. Symmetry 2022, 14, 1897. [CrossRef]
- Hazem M. Bahig, Hatem M. Bahig and Yasser Kotb, Fermat Factorization using a Multi-Core System. International Journal of Advanced Computer Science and Applications(IJACSA), 2020, 11(4). [CrossRef]
- Zheng, M. Revisiting the Polynomial-Time Equivalence of Computing the CRT-RSA Secret Key and Factoring. Mathematics, 2022, 10, 2238. [CrossRef]
| Turn no. | init | |||||||
|---|---|---|---|---|---|---|---|---|
| 1 | 11 | 13 | 17 | 19 | 23 | 29 | 31 | 37 |
| 2 | 41 | 43 | 47 | 49 | 53 | 59 | 61 | 67 |
| 3 | 71 | 73 | 77 | 79 | 83 | 89 | 91 | 97 |
| 4 | 101 | 103 | 107 | 109 | 113 | 119 | 121 | 127 |
| 5 | 131 | 133 | 137 | 139 | 143 | 149 | 151 | 157 |
| 6 | 161 | 163 | 167 | 169 | 173 | 179 | 181 | 187 |
| 7 | 191 | 193 | 197 | 199 | 203 | 209 | 211 | 217 |
| 8 | 221 | 223 | 227 | 229 | 233 | 239 | 241 | 247 |
| 9 | 251 | 253 | 257 | 259 | 263 | 269 | 271 | 277 |
| 10 | 281 | 283 | 287 | 289 | 293 | 299 | 301 | 307 |
| 11 | 311 | 313 | 317 | 319 | 323 | 329 | 331 | 337 |
| 12 | 341 | 343 | 347 | 349 | 353 | 359 | 361 | 367 |
| 13 | 371 | 373 | 377 | 379 | 383 | 389 | 391 | 397 |
| 14 | 401 | 403 | 407 | 409 | 413 | 419 | 421 | 427 |
| 15 | 431 | 433 | 437 | 439 | 443 | 449 | 451 | 457 |
| No. of digits | BWFM | MWFM |
|---|---|---|
| 11 | 0.003 | 0.003 |
| 12 | 0.013 | 0.005 |
| 13 | 0.05 | 0.01 |
| 14 | 0.08 | 0.02 |
| 15 | 0.27 | 0.07 |
| 16 | 1.07 | 0.27 |
| 17 | 3.35 | 0.85 |
| 18 | 17.2 | 3.5 |
| 19 | 43.6 | 8.3 |
| 20 | 114 | 28.8 |
| No. of digits | Improvement |
|---|---|
| 11 | 0% |
| 12 | 62% |
| 13 | 80% |
| 14 | 75% |
| 15 | 74% |
| 16 | 75% |
| 17 | 75% |
| 18 | 80% |
| 19 | 81% |
| 20 | 75% |
| Average | 75% |
| No. of digits | MWFM with wheel size: | ||||
|---|---|---|---|---|---|
| 4 | 5 | 6 | 7 | 8 | |
| 18 | 15.7 | 9.2 | 6.2 | 4.6 | 3.5 |
| 19 | 31.3 | 17.8 | 12.5 | 8.8 | 8.3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





