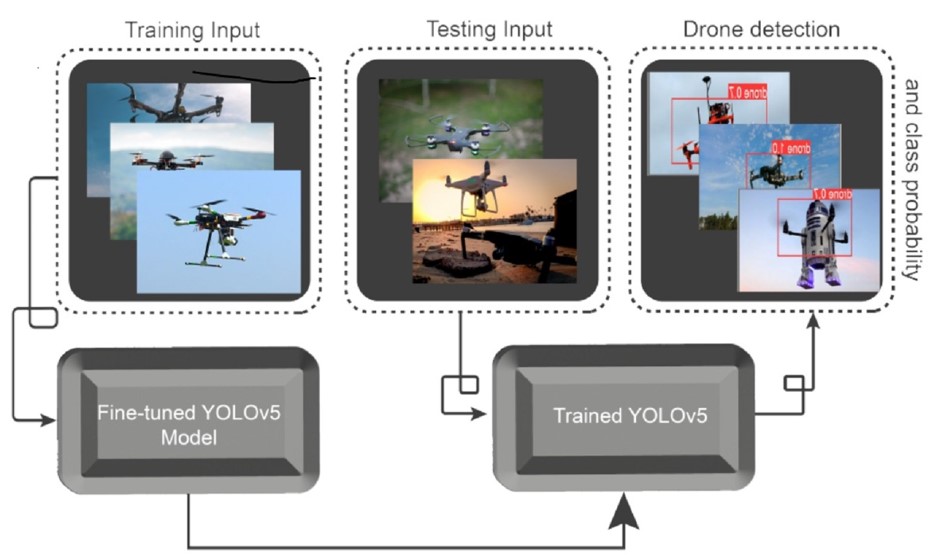
Recently, the use of drones/unmanned aerial vehicles (UAVs) has notably increased due to their broad commercial spread and low cost. The wide diffusion of drones increases the hazards of their misuse in illegitimate actions such as drug smuggling and terrorism. Thus, the surveillance and automated detection of drones are crucial for safeguarding restricted regions or special zones from illegal drone interventions. One of the most challenging issues in drone detection in surveillance videos is the apparent similarity of drones and birds against complex backgrounds. In this work, an automated image-based drone-detection system utilizing an advanced deep-learning-based object-detection method known as you only look once (YOLOv5) is introduced for protecting restricted regions or special zones from unlawful drone interventions. Due to the lack of sufficient data, transfer learning was utilized to pretrain the object-detection method to increase the performance. The experiments showed outstanding results, and an average precision of 94.7% was accomplished.