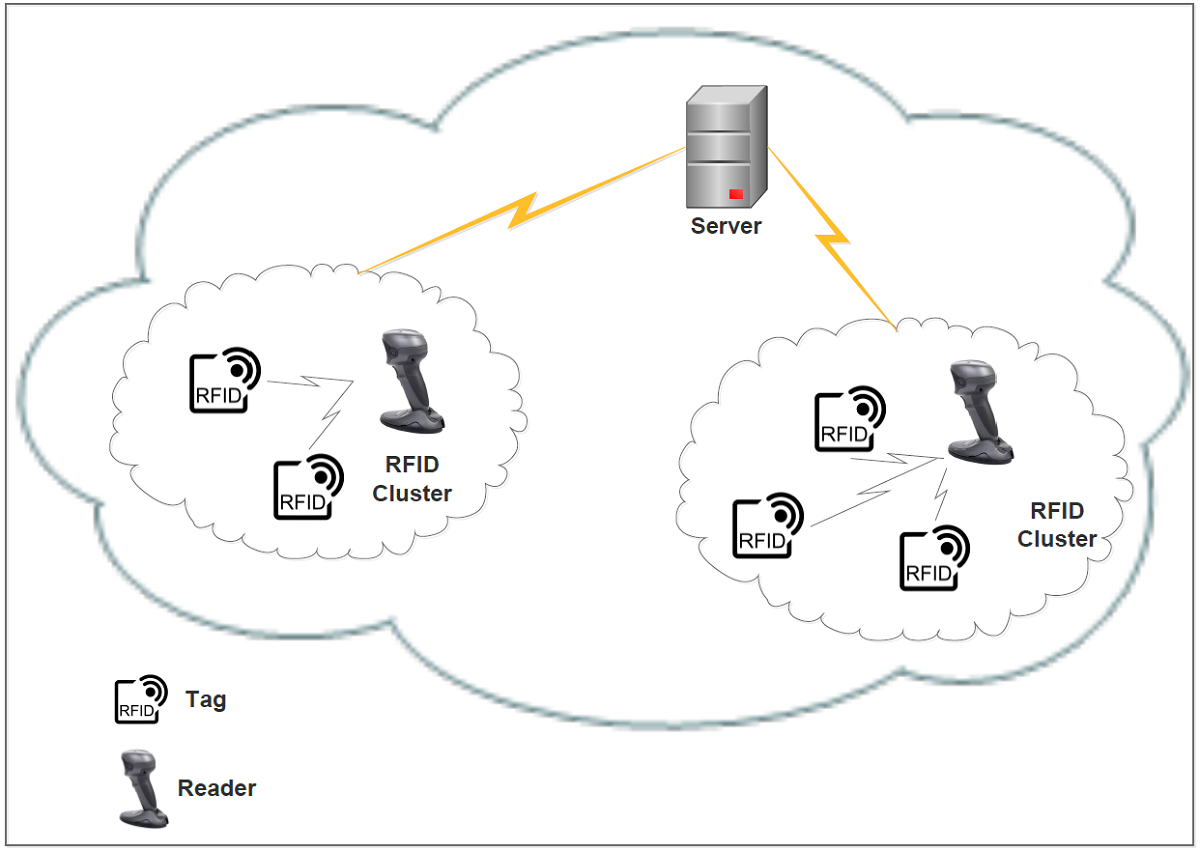
Radio Frequency Identification (RFID) devices use radio waves to relay identifying information to an electronic reader using low-cost RFID Tag. RFID is expected to replace the conventional bar-code identification system due to its advantage like real-time recognition of a considerable number of objects. However, in RFID systems an attacker can get the tag that may lead to various security threats, and the limited computation power of RFID tags can cause delay. Lightweight authentication protocols proposed using cryptographic algorithms (one-way hash function, symmetric key encryption/decryption, and exclusive-OR) in order to cope with these problems. One such lightweight cryptographic protocol has been presented by Gope and Hwang using RFID systems. However, it analyzed in this article that their protocol is infeasible and vulnerable to Collision Attack, Denial-of-service (DoS), and Stolen verifier Attacks. A realistic, lightweight authentication protocol has been presented in this article to ensure protection against the mentioned attacks for IoT based RFID system. The proposed protocol has been formally analyzed using BAN logic and ProVerif as well as also analyzed informally using security requirement. The results show that the proposed protocol outperforms the existing protocols not only in security enhancements but also in terms of computation and communication complexity. Furthermore, the proposed protocol has also been analyzed for storage complexity.