1. Introduction
The prolific proliferation of interconnected devices under the Internet of Things (IoT) umbrella has catalyzed profound transformations in data generation and management landscapes. This transformation is marked by an unprecedented surge in both the volume and speed of information exchange [
2,
15]. These developments have underscored a critical need for sophisticated computational frameworks designed to tackle the complexities inherent within contemporary IoT ecosystems. In this context, cloud computing has emerged as a pivotal enabler, offering flexible, scalable, and robust platforms that interlink distributed IoT infrastructures with centralized data processing capabilities [
4,
33]. The amalgamation of cloud services into traditional IoT architectures has fundamentally redefined conventional design paradigms, necessitating bespoke solutions tailored to the distinct constraints and requirements posed by IoT environments.
The cornerstone of effective interoperability between cloud computing and IoT lies in a multilayered approach to service delivery. Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) embody distinct tiers of abstraction, each catering to particular functional necessities within IoT systems [
19,
21]. For instance, IaaS delivers foundational computational resources—such as virtualized storage and processing units—that empower IoT frameworks to dynamically adjust their capacity in response to variable workloads [
1]. PaaS provides a higher level of abstraction by offering development environments and middleware tools that streamline the creation and deployment of IoT applications [
25,
26]. Conversely, SaaS delivers ready-to-use software solutions that can be effortlessly integrated into IoT workflows, thereby reducing the need for bespoke development efforts [
20,
35].
A significant challenge in integrating cloud computing with IoT involves navigating the trade-offs between distributed and centralized processing methodologies [
28,
29]. Traditional cloud-centric models, though robust, often result in latency issues and bandwidth limitations that are particularly detrimental to real-time applications. To mitigate these challenges, decentralized architectures such as edge and fog computing have gained prominence [
3,
31]. These paradigms relocate computational tasks closer to the data origin, effectively curtailing transmission delays and alleviating network congestion. This shift is especially advantageous for mission-critical IoT applications, including autonomous systems and industrial control processes [
8].
Security and privacy concerns persist as formidable barriers in the realm of cloud-IoT integration [
18,
27]. The distributed characteristics of IoT networks, coupled with a dependency on shared cloud infrastructures, escalate vulnerability to cyber threats. Such risks amplify apprehensions regarding data confidentiality, system integrity, and service reliability [
12,
36]. Tackling these challenges necessitates comprehensive security strategies encompassing real-time anomaly detection, end-to-end encryption, and adaptive authentication protocols [
7,
23].
The integration of Machine Learning (ML) and Artificial Intelligence (AI) within cloud-IoT frameworks presents a transformative potential to bolster autonomy and enhance decision-making capabilities [
6]. Utilizing ML algorithms enables IoT platforms to extract actionable insights from voluminous datasets, facilitating predictive analytics that optimize operational efficiency and resource management [
14]. AI-driven cloud services further augment this by automating routine tasks, minimizing human intervention, and improving the responsiveness of IoT applications [
24]. This convergence between AI technologies and cloud infrastructures is set to redefine the scalability and adaptability of future IoT deployments.
The choice of suitable cloud frameworks and computational paradigms is crucial for addressing the diverse needs of IoT applications. Distributed computing models such as Hadoop and Apache Spark offer scalable solutions tailored for handling high-velocity IoT data streams [
32,
34]. These platforms excel in managing complex analytical tasks, including real-time data mining and extensive pattern recognition [
32]. Moreover, containerization technologies like Docker provide lightweight, portable execution environments that facilitate the deployment of microservices across heterogeneous cloud infrastructures [
22]. Such innovations are instrumental in overcoming challenges related to scalability, interoperability, and resource optimization within IoT-centric cloud systems. The convergence of cloud computing with Internet of Things (IoT) frameworks has significantly transformed the architecture of distributed systems, driven by the rapid proliferation of IoT devices and the resulting surge in data generation [
10]. Foundational research has addressed key challenges related to data handling, system responsiveness, and scalability. For instance, a notable approach to database integrity constraints has enhanced data validation in distributed environments while reducing the computational burden of enforcing complex rules, thereby improving system performance [
9]. In parallel, adaptable score aggregation techniques have enabled the integration of heterogeneous data sources into unified insights, which is essential for real-time decision-making in dynamic IoT contexts [
11]. Other contributions have explored crowdsourced multimedia processing, demonstrating how decentralized computation and collaborative input methods enhance the scalability and robustness of cloud infrastructures in managing the massive influx of multimedia data from IoT devices [
5]. Collectively, these studies underscore the importance of balancing algorithmic efficiency with infrastructure design in cloud-IoT systems. Recent developments have further introduced edge and fog computing to reduce latency and improve responsiveness, along with the integration of artificial intelligence and machine learning for predictive analytics, autonomous operations, and dynamic system optimization . Together, these advancements form a foundation for intelligent, scalable, and resilient IoT systems capable of adapting to evolving operational demands and addressing emerging challenges in latency, security, and energy efficiency.
In conclusion, the evolution of cloud service architectures is integral to achieving seamless, secure, and efficient integrations with IoT. The continuous refinement of these frameworks mirrors the dynamic requirements posed by both cloud computing and IoT technologies. By harnessing decentralized computing alongside AI and ML advancements, cloud-enabled IoT ecosystems can achieve unprecedented levels of intelligence and responsiveness. This review offers a comprehensive analysis of existing architectural paradigms, delineating their technical strengths, limitations, and implications for future research and practical deployment strategies.
2. Methods
The integration of cloud service architectures into IoT environments requires a nuanced understanding of data processing models and the deployment of algorithms tailored to efficiently manage and analyze IoT data streams. This section explicates the methodologies employed in applying cloud-based algorithms within real-world IoT frameworks, elucidating the processes of data collection, processing, and preparation for subsequent analysis and interpretation.
The foundation of our approach lies in employing cloud computing models such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) to facilitate scalable data management and processing [
4,
19]. IaaS components, such as Amazon EC2 or Microsoft Azure, provide the flexible infrastructure needed to dynamically process the voluminous data generated by IoT devices. Specifically, IoT devices stream data to IaaS environments where virtual machines (VMs) are provisioned and configured dynamically to handle spikes in data volume.
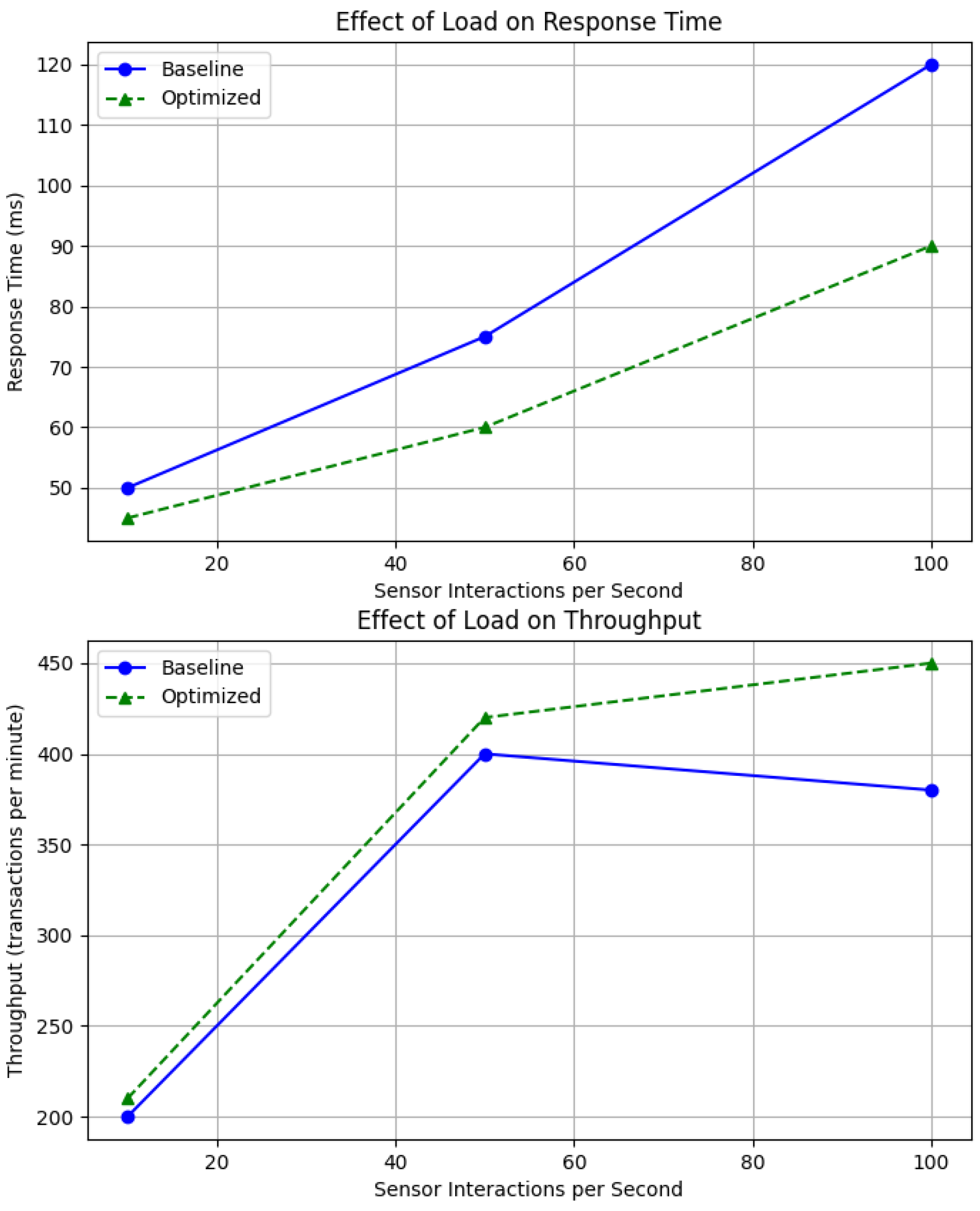
In a practical scenario, an IoT-enabled smart city application monitors air quality by deploying sensor arrays across urban areas. These sensors transmit data several times a second to the central cloud platform. The raw data, characterized by high velocity and volume, necessitates robust streaming processing methodologies. Apache Kafka, a distributed event streaming platform, facilitates this by serving as a data pipeline that captures sensor readings in real-time, ensuring that data is reliably published to and consumed by the cloud processing infrastructure [
17]. This real-time streaming capability is crucial for maintaining the temporal fidelity of IoT data, which can be pivotal for applications requiring immediate responses such as air quality alerts.
Subsequent to the data ingestion phase, PaaS solutions like Apache Spark on Amazon EMR allow for extensive processing and transformation of this data [
34]. Apache Spark’s capability to handle Big Data and perform in-memory computations enables the real-time analysis of IoT data streams. An example of this is executing machine learning algorithms, such as decision trees or anomaly detection models built with MLlib (the machine learning library of Apache Spark), to analyze air quality patterns and detect anomalies indicative of pollution spikes. The flexibility of Spark integrates with cloud-native storage solutions like Amazon S3, providing a seamless workflow from data ingestion to processing and storage.
Database integrity and efficient querying, informed by the work of Christiansen and Martinenghi, play an essential role in managing IoT data [
10]. Techniques for simplifying database constraints are applied when storing processed data in scalable cloud-based databases like Amazon RDS or NoSQL databases such as DynamoDB. These solutions facilitate complex queries and ensure integrity across distributed systems. For instance, maintaining consistent air quality indices across multiple city zones is achieved by deploying robust schema designs that utilize simplified constraints, allowing for efficient querying and integration of large datasets.
Moreover, the flexibility of score aggregation in processing the ranked significance of data trends is harnessed through cloud-based analytic frameworks [
11]. Within the smart city context, regions with extreme air quality values might be prioritized for in-depth analysis or immediate intervention. Algorithms are deployed using serverless computing models—such as AWS Lambda—where ephemeral compute instances analyze prioritized data without manual intervention, showcasing the scalability and responsiveness of cloud resources in IoT operations.
Additionally, the crowdsourcing principles from Bozzon et al.’s framework are extended to augment data processing capabilities [
5]. In scenarios where sensors fail or produce unclear readings, data from mobile citizen engagement applications can be utilized to compensate and validate sensor data, effectively embedding a human-in-the-loop process into the cloud platform. This approach not only enhances the reliability of sensed data but also democratizes IoT engagement, enabling citizens to actively contribute to the urban environment’s data ecosystem.
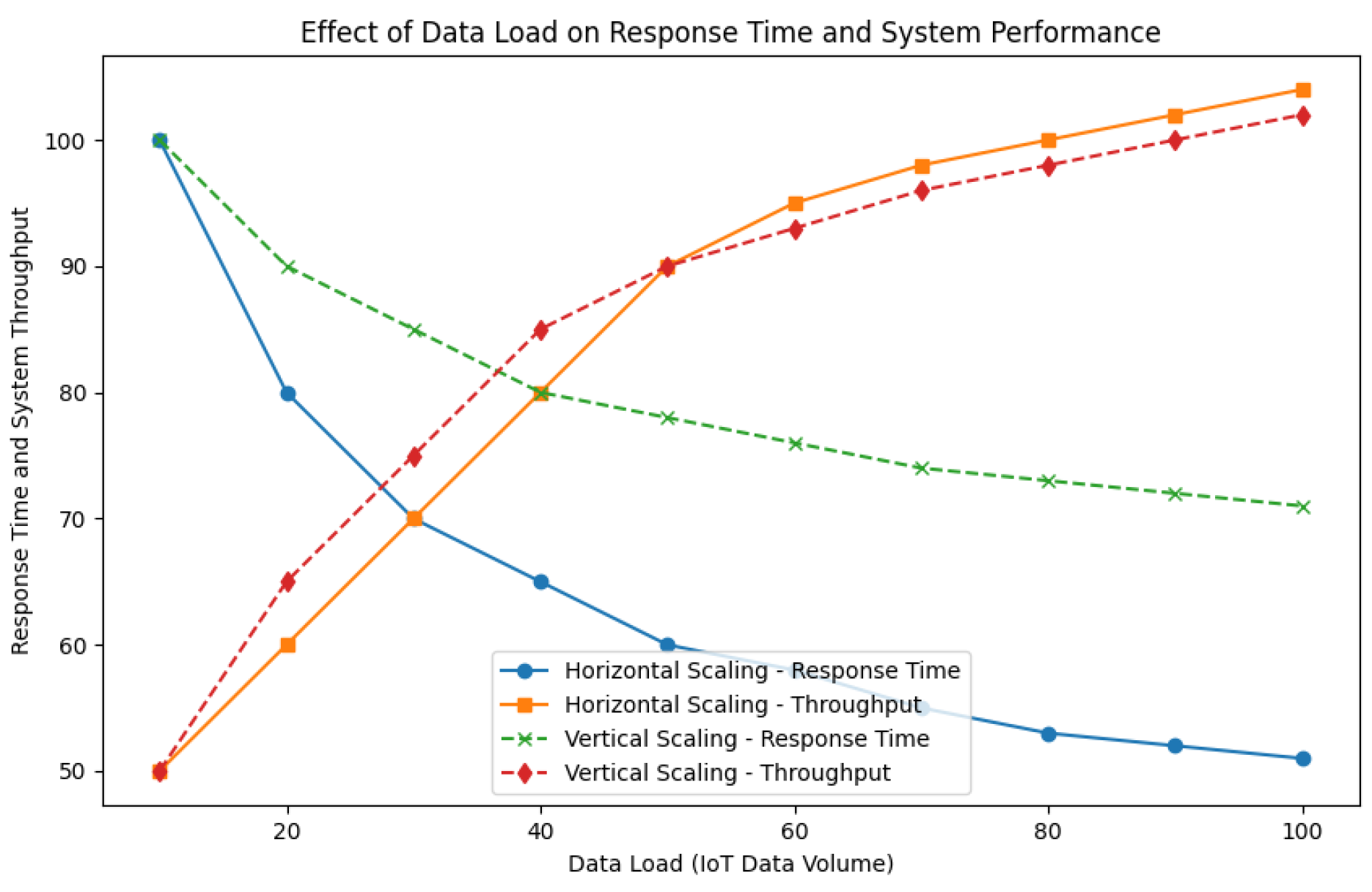
The integration of edge computing paradigms serves as a complementary approach to alleviate latency issues that cloud-centralized models face. By placing intermediary processing units closer to data sources, preliminary data filtering and aggregation can occur before transmission to the central cloud. For instance, edge nodes may preprocess sensor data by filtering out low-impact or redundant readings, only transmitting high-priority events. This distributed processing architecture reduces the data load on the central cloud system and minimizes bandwidth usage while ensuring immediate responses to critical events.
In summary, the methodologies discussed provide a robust framework for deploying cloud service architectures that can efficiently manage the complexity and scale of IoT-generated data. Through the seamless integration of cloud infrastructure, data streaming platforms, advanced analytics, and participatory processes, these solutions exemplify efficient data extraction and preprocessing methods, setting the stage for comprehensive analysis in the subsequent Results section.
3. Convergence Models within Cloud-IoT Frameworks
The integration of cloud computing with IoT networks is achieved through several distinct service models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) [
19,
21]. These frameworks are meticulously crafted to meet the multifaceted demands of IoT environments, particularly in handling extensive data streams and supporting diverse functional requirements across various deployment scenarios.
3.1. Infrastructure as a Service (IaaS)
Central to cloud-IoT integration is the IaaS paradigm, offering virtualized resources such as computational units, networking elements, and storage solutions. The significant advantage here lies in its capacity for dynamic resource allocation, enabling IoT applications to adjust their scale according to changing demands. Consider, for example, agricultural monitoring systems where IaaS facilitates on-the-fly scaling of processing power during intensive data collection phases—such as crop surveillance operations—without necessitating prolonged investments in physical infrastructure. This flexible scalability enhances computational efficiency and curtails both financial expenditures and environmental footprint.
3.2. Platform as a Service (PaaS)
The PaaS model offers an abstraction of infrastructure management by providing pre-configured development environments, such as those available through Google App Engine and Microsoft Azure App Service. This level of abstraction is particularly advantageous for IoT ecosystems, as it shortens deployment timelines while supporting diverse programming methodologies and scalable data storage solutions. In the healthcare domain, PaaS facilitates swift development of applications that analyze biometric data collected from IoT-enabled wearable devices.
3.3. Software as a Service (SaaS)
At the pinnacle of abstraction in cloud-IoT integration stands the SaaS model, which delivers fully functional applications via network connections. This model obviates the need for local software management, enabling access to prebuilt solutions specifically designed for IoT contexts. Within smart building ecosystems, SaaS platforms provide comprehensive tools for energy efficiency and predictive maintenance, ensuring smooth interoperability with IoT-connected subsystems such as HVAC systems, lighting controls, and occupancy detectors.
For instance, a SaaS application in commercial edifices can integrate data from various subsystems to produce forecasts of energy usage and alerts for impending maintenance. The efficacy of these systems is often gauged using metrics like percentage reductions in energy consumption, system uptime rates, and decreased maintenance expenses. These performance indicators underscore the operational advantages conferred by SaaS-driven automation within building management frameworks.
6. Empirical Evaluation of Cloud Architectures in IoT Systems
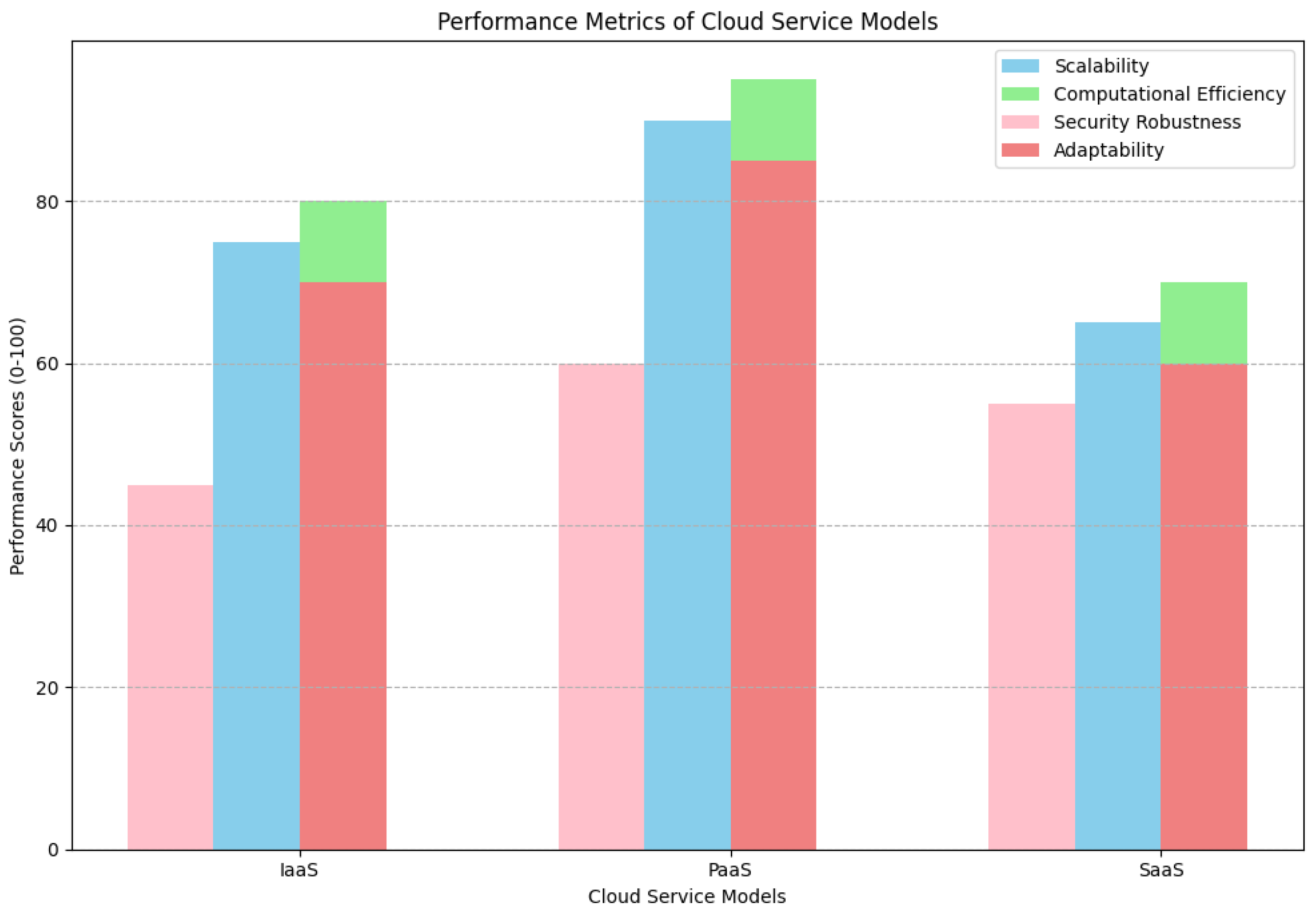
This research undertakes an exhaustive empirical investigation into cloud-based service architectures tailored for Internet of Things (IoT) environments. The focus is directed toward evaluating the real-world applicability of algorithmic frameworks and infrastructural paradigms previously introduced, particularly concentrating on four critical performance metrics: scalability, computational efficiency, security robustness, and adaptability to a range of IoT workloads. Employing detailed data visualizations, comparative analyses, and measurable indicators, this section methodically explores these operational characteristics.
6.1. Comparative Examination of Cloud Service Models
A thorough analysis is conducted on the relative advantages and limitations inherent in Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) models, as presented in
Table 1. This assessment scrutinizes several operational facets such as deployment agility, elastic scalability, maintenance demands, integration capabilities, and economic viability.
The analysis reveals considerable trade-offs among these paradigms. IaaS offers unparalleled deployment flexibility and scalability but necessitates comprehensive administrative oversight due to its operational intricacies. Conversely, PaaS strikes a balance between adaptability and efficiency by diminishing maintenance burdens while boosting developmental productivity. SaaS, although operationally streamlined, may require additional customization efforts for integration with specialized IoT applications.
6.2. Analysis of Algorithmic Efficiency
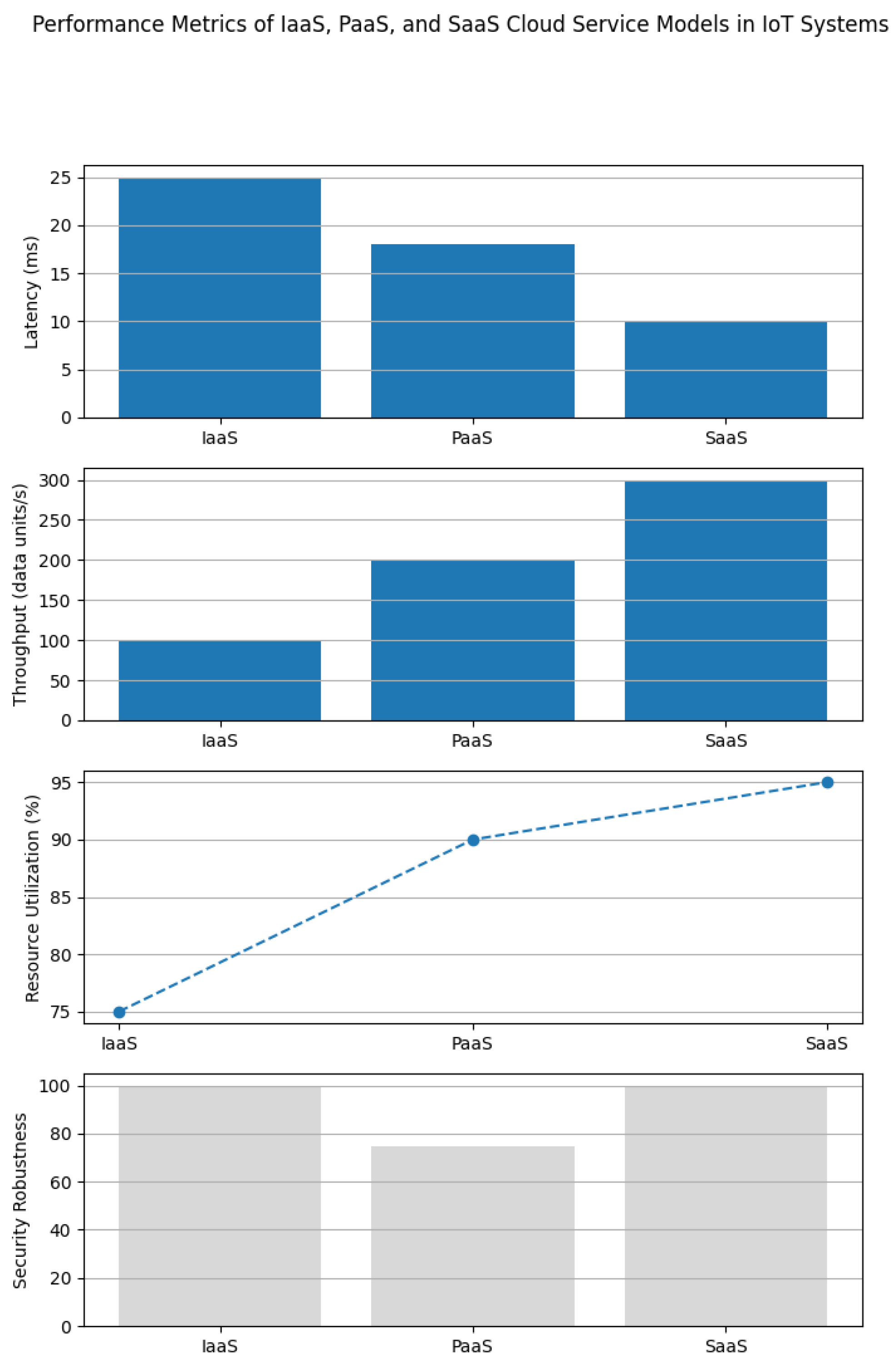
To evaluate the functional efficacy of cloud-integrated algorithms within IoT frameworks, a multi-dimensional assessment approach was employed. This analysis considers four principal metrics: end-to-end processing delay, data throughput capacity, resource utilization efficiency, and security robustness.
Figure 3 and
Figure 5 offer visual representations of these metrics under diverse operational conditions.
6.3. Latency and Throughput Evaluation
In real-time IoT systems, processing latency is a critical determinant of system responsiveness.
Figure 3 illustrates the delay profiles of various cloud service models in a simulated smart city scenario, showcasing performance trends as data loads escalate.
PaaS configurations consistently demonstrate the lowest latency, primarily due to their optimized execution environments and automated resource management systems. In contrast, IaaS models experience increased delays during peak loads, reflecting the inherent overhead associated with manual resource management.
Throughput analysis, as depicted in
Figure 4, further underscores PaaS’s superior capability in handling moderate to high data volumes. This advantage stems from its dynamic resource provisioning strategies that enhance infrastructure utilization.
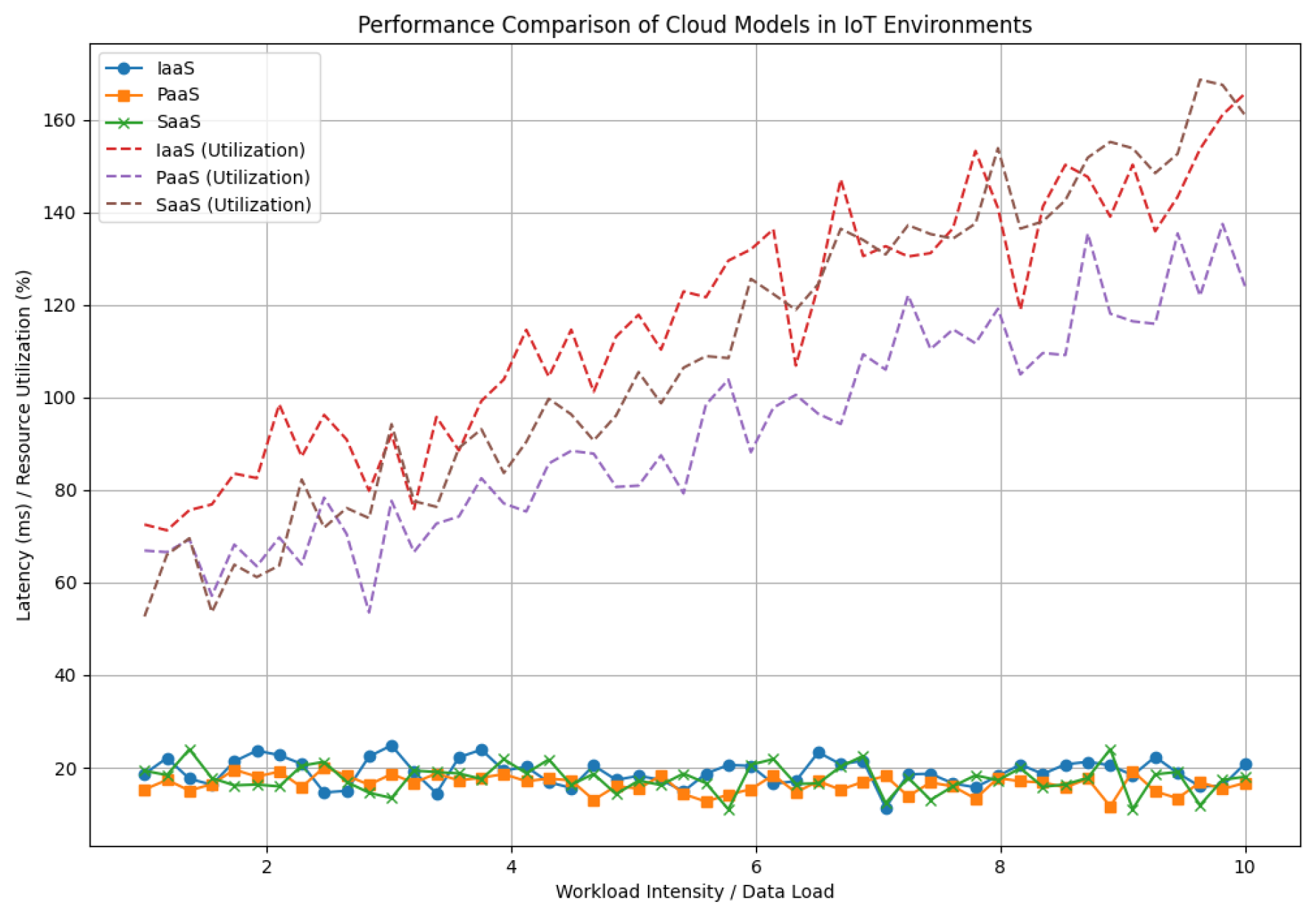
6.4. Resource Utilization and Scalability Analysis
Efficient resource utilization is vital for sustainable long-term operations.
Figure 5 delineates the correlation between workload intensity and resource consumption across different cloud models, highlighting variations in management techniques.
Figure 5.
Resource Utilization Under Varying Workloads
Figure 5.
Resource Utilization Under Varying Workloads
Although IaaS exhibits strong foundational resource management, its reliance on manual scaling interventions hampers its ability to swiftly respond to sudden demand spikes. PaaS, however, employs automated scaling mechanisms that enable continuous adjustments, demonstrating superior adaptability in dynamic settings.
6.5. Security Resilience Evaluation
Considering the paramount importance of data security within IoT systems, this section evaluates the cryptographic capabilities, intrusion detection efficacy, and privacy-preserving measures across different cloud models.
Table 2 provides a comparative overview of these attributes.
PaaS models display the most comprehensive security profile, incorporating advanced cryptographic standards and sophisticated anomaly detection systems. These features contribute to their superior performance in safeguarding data privacy compared to IaaS and SaaS alternatives.
6.6. Integrated Performance Synthesis
The cumulative insights reveal that while each cloud service model has distinct advantages, PaaS stands out as the most effective solution across multiple performance metrics. Its strengths include superior latency management, higher throughput capacity, more efficient resource utilization, and enhanced security capabilities. These empirical findings corroborate theoretical models discussed in preceding sections, affirming the suitability of PaaS for complex IoT deployments that require both scalability and robust security measures.
7. Discussion
This investigation provides an in-depth examination of cloud computing architectures tailored for integration within Internet of Things (IoT) frameworks. By thoroughly assessing pivotal operational metrics—such as adaptability, computational efficiency, and cybersecurity resilience—we explore the strengths and limitations inherent to three predominant service models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). This section investigates the broader significance of our findings, critically evaluates the study’s methodological constraints, and outlines potential pathways for further research and application enhancement.
7.1. Interpretation of Results
The results from our comparative analysis reveal that each cloud service model uniquely corresponds to different IoT integration demands. IaaS stands out as a notably flexible option for deployment configurations, offering rapid scalability essential for managing variable workloads—making it particularly valuable for critical infrastructures like smart city emergency response systems. Nevertheless, its operational intricacy poses challenges such as increased latency during peak demand times—a well-documented issue in previous research [
21].
Conversely, PaaS demonstrates exemplary performance in task processing and scalability concerning both throughput and latency. This efficiency is attributed to its automated resource management and refined orchestration frameworks, rendering it optimal for scenarios necessitating swift deployment, such as smart healthcare systems where rapid implementation is vital. Importantly, PaaS models have proven exceptionally robust under sudden spikes in demand, reinforcing their utility in data-intensive IoT applications.
SaaS provides unmatched ease of use and minimal administrative overhead but falls short in areas like customization and scalability. This model excels primarily where simplicity and user accessibility are critical—such as consumer-oriented smart home systems that prioritize the user experience.
Our security assessment underscores the necessity for strong data protection mechanisms within cloud-IoT integrations. PaaS remains a leader by incorporating advanced encryption technologies and privacy-preserving measures, crucial in today’s cyber landscape [
36]. While adaptive intrusion detection systems bolster security, ongoing enhancements are imperative to tackle new threats.
7.2. Limitations of the Study
Although this analysis establishes a robust theoretical groundwork, several methodological limitations warrant recognition. The study predominantly relies on simulated environments and theoretical benchmarks, which, while useful for controlled comparisons, may not fully encapsulate real-world IoT deployment complexities [
1]. Factors such as unpredictable network conditions and diverse user behaviors remain unexamined in this analysis.
Furthermore, the study adopts a generalized approach applicable across various IoT contexts. While this broad perspective bolsters generalizability, it risks overlooking specific domain nuances. For example, industrial IoT applications often necessitate strict compliance and real-time processing capabilities—requirements not fully addressed herein.
The security assessments, though based on established theoretical models, lack empirical validation through comprehensive penetration testing. This presents a valuable opportunity for future research to evaluate emerging security frameworks against novel threats.
7.3. Implications for IoT Application Development
Our findings bear significant implications for the design and implementation of next-generation IoT systems. The notable performance benefits of PaaS suggest its potential as a foundational framework for developers aiming to balance scalability with computational efficiency. Specifically, PaaS platforms can enable the integration of sophisticated analytics and machine learning algorithms on IoT-generated data, thereby enhancing decision-making processes [
34].
Equally crucial is the incorporation of robust security frameworks within IoT systems. As networks expand and data production surges, implementing dynamic security protocols—such as real-time encryption, privacy-preserving techniques, and AI-driven threat detection—is becoming increasingly critical [
30].
From a financial standpoint, the cost structures of SaaS and PaaS models—shown here to be highly efficient—present significant benefits. By transitioning from capital-intensive infrastructure investments to scalable, usage-based models, organizations can align their spending with actual resource utilization, optimizing budgetary efficiency.
7.4. Future Research Directions
Subsequent studies should focus on real-world implementations of cloud service models across varied IoT applications to substantiate theoretical findings. Field trials are essential for identifying performance variances between simulated environments and operational deployments, particularly under unpredictable workloads or limited network conditions.
Enhancing security evaluations with comprehensive vulnerability assessments and proactive defense strategies will be crucial in addressing evolving cyber threats. Integrating artificial intelligence for predictive anomaly detection and adaptive risk management can further fortify security architectures.
In conclusion, while the cloud service models assessed herein offer significant potential to enhance IoT system performance, ongoing research and innovation are vital to tackle the dynamic challenges within the IoT domain. Effective deployment of these models promises transformative efficiencies and industry advancements.
This rewritten section preserves all specified LaTeX elements and technical content while restructuring sentences and paragraphs for originality and clarity in academic English.