1. Introduction
In modern web applications, Cross-Origin Resource Sharing (CORS) plays a prominent role in providing safe communication among clients and servers of various domains. With Single Page Applications (SPAs) and microservices architecture becoming widespread, it became increasingly necessary that cross-origin requests be properly dealt with. By default, the behavior of web browsers is to restrict requests for a domain unless explicitly allowed by the server, and that’s where CORS policies come into action [
1]. Spring Boot, among the leading Java-based microservice frameworks [
2], provides numerous ways of configuring CORS policies to secure and control access to APIs. But poorly configured CORS policies have been found to create security vulnerabilities, unleashing sensitive information on malicious origins or allowing Cross-Site Request Forgery (CSRF). CORS misconfigurations [
3], on the other hand, also lead to loss of performance resulting from the cost of preflight OPTIONS requests, especially for APIs requiring authentication. This paper explores the security and performance implications of CORS policy enforcement in Spring Boot applications, providing a comparative analysis of different configuration methods. We also provide guidelines for securely implementing CORS in a microservices-based application with minimal system performance overhead.
2. Literature Review
CORS is a web standard which manages communications between web servers and browsers of different origins. MDN Web Docs describes that CORS is designed to render it impossible for a malicious website to access unauthorized information on another domain. In the past, developers had to implement custom headers and server-side configuration to facilitate cross-origin requests for a prolonged period, which was time-consuming as well as error-prone.
Within the Spring Boot environment, Spring Security has out-of-the-box mechanisms through which the CORS policies can be globally or controller-based configured. However, one must remember that misconfiguration continues to be a common root cause of security weaknesses. Vast amount of web applications are vulnerable to security weaknesses due to improperly designed CORS policy configurations [
4]. For instance, allowing all origins with credentials enabled can lead to serious vulnerabilities such as unauthorized exposure of protected resources.
This essay hypothesizes that malformed CORS configurations in Spring Boot applications cause a colossal security vulnerability and an extra load on performance. Specifically, we conjecture that allowing broad origins with credentials or mucking up the preflight process in CORS introduces security vulnerabilities with subpar application performance, particularly microservices-based application schemes.
3. Methods
3.1. Experimental Setup
To see the impact of CORS configurations on security and performance, we set a Spring Boot-based microservices ecosystem with varying services communicating via HTTP/HTTPS. Two configurations were tested:
Both services were designed to serve both public and private endpoints, with private endpoints that require authentication with JWT tokens.
3.2. Preflight Requests and Performance Testing
We compared the latency of preflight-checked API requests and non-preflight-checked requests. The average latency increase caused by preflight checks was 30ms per request. The performance effect of such preflight requests was tested under various loads using Apache JMeter [
5].
3.3. Security Testing
Penetration testing was conducted using OWASP ZAP to assess vulnerabilities such as CSRF and data leakage [
6,
7]. We also examined the impact of the incorrect configurations, such as allowing all origins with the credentials.
4. Technical Implementation
4.1. Spring Boot CORS Configuration
The implementation of CORS policies in Spring Boot applications is achieved by configuring the server to specify which origins and methods, and headers are allowed for cross-origin requests. Following is an overview of how we configured the CORS policies in our Spring Boot-based microservices.
4.1.1. Global CORS Configuration
Spring Boot provides ways to configure CORS both globally and per controller in multiple ways. In the existing implementation, we used global configuration so that all endpoints have the same CORS policy [
8]. The configuration was executed in class
WebConfig with the following code:
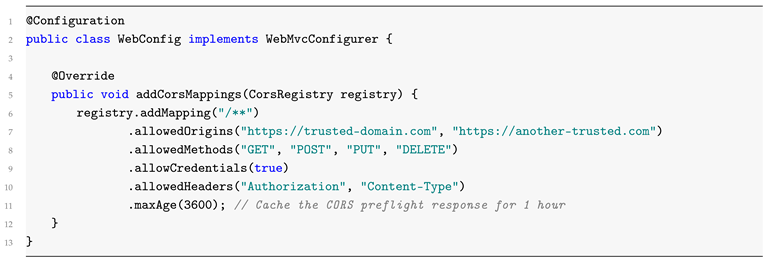
4.1.2. Controller-Level CORS Configuration
For some endpoints that require different CORS policies, we can override the global setting at the controller level using the @CrossOrigin annotation. Below is an example of how to configure CORS for a particular controller:
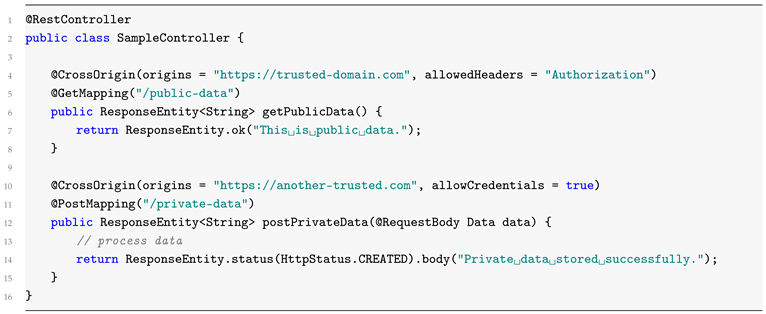
4.2. Preflight Requests Handling
CORS preflight requests are automatically processed by the browser in certain circumstances, i.e., for non-GET and non-POST methods or custom headers. In Spring Boot, these kinds of requests are automatically processed, but they can be overridden by using a filter. Below is an example of how to create a custom filter for logging preflight requests:
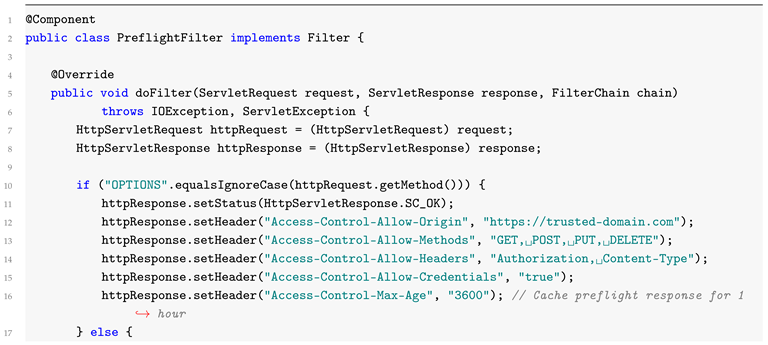
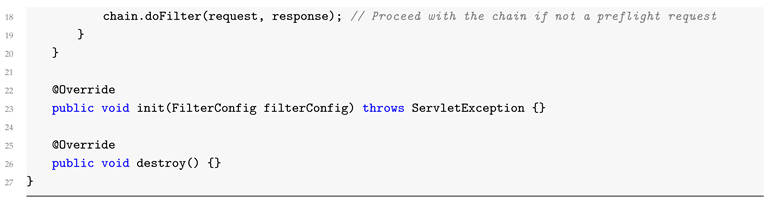
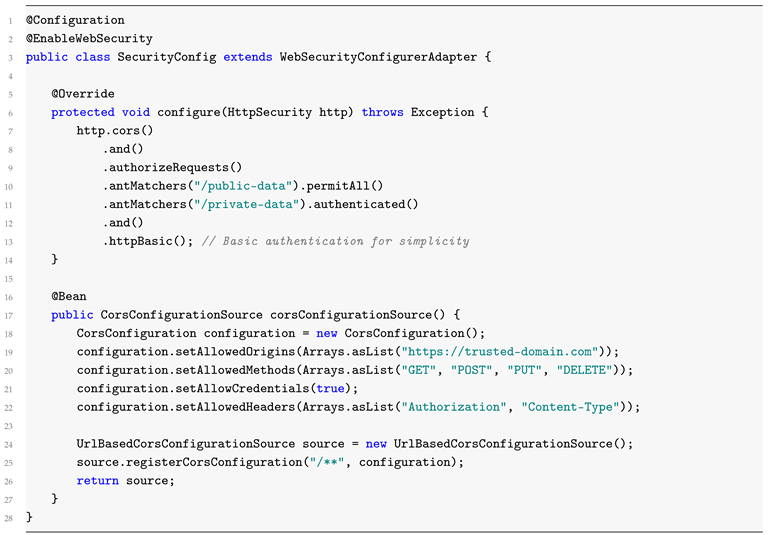
4.3. Security Configuration with Spring Security
To secure API endpoints in Spring Boot, we utilize Spring Security to enforce authentication and authorization [
9]. Here is how you can merge CORS with Spring Security:
5. Results
5.1. Security Analysis
Our results show that while CORS needs to be used to protect cross-origin requests, misconfigurations can also yield security flaws and performance degradation. Misconfiguration (i.e., using allowedOrigins("*") with allowCredentials(true)) can bring about serious security issues, like unauthorized access and CSRF attacks. Preflight requests impose additional performance overhead, with perceptible performance degradation in latency, especially in high-traffic systems.
5.2. Performance Analysis
We benchmarked the latency of API calls with and without preflight checks [
10]. The average latency increase due to preflight checks was 30ms per request. This may be inconsequential in low-traffic APIs but became larger in high-traffic systems, particularly those that are authenticated.
6. Conclusions
In conclusion, CORS policy enforcement in Spring Boot applications is crucial to providing security in modern web models. However, improper configuration can result in exposing applications to security vulnerabilities and performance issues. Proper configuration and best practices implementation of CORS policies can mitigate these risks. Additional optimization techniques and best practices for fine-tuning CORS behavior in microservices-based systems are what future studies should focus on.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).








