Submitted:
08 March 2025
Posted:
11 March 2025
You are already at the latest version
Abstract
As the Internet of Things (IoT) continues expanding its footprint across various sectors, robust security systems to mitigate associated risks are more critical than ever. Intrusion Detection Systems (IDS) are fundamental in safeguarding IoT infrastructures against malicious activities. This systematic review aims to guide future research by addressing six pivotal research questions that underscore the development of advanced IDS tailored for IoT environments. Specifically, the review concentrates on applying Machine Learning (ML) and Deep Learning (DL) technologies to enhance IDS capabilities. It explores various feature selection methodologies aimed at developing lightweight IDS solutions that are both effective and efficient for IoT scenarios. Additionally, the review assesses different datasets and balancing techniques, which are crucial for training IDS models to perform accurately and reliably. Through a comprehensive analysis of existing literature, this review highlights significant trends, identifies current research gaps, and suggests future studies to optimize IDS frameworks for the ever-evolving IoT landscape.
Keywords:
1. Introduction
1.1. Threats and Security Measures in IoT
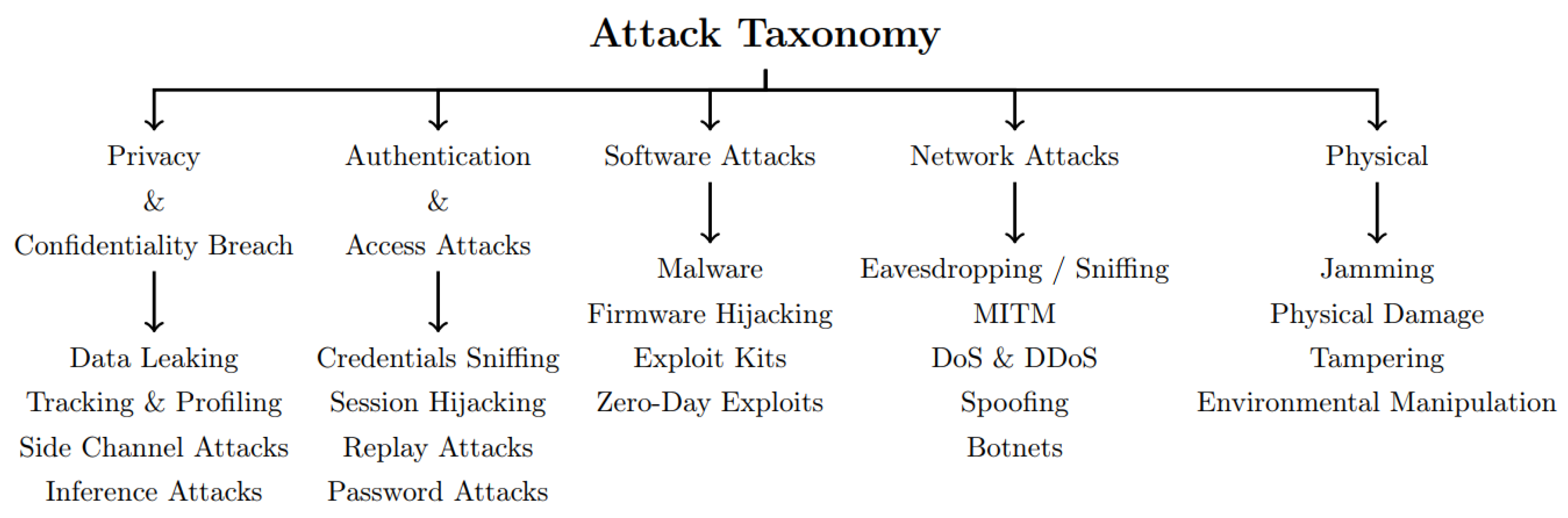
1.2. Limitations and Challenges Associated with IoT Security and Attack Taxonomy
- Hardware Limitations: IoT devices often have constrained computational power, memory, and energy resources, limiting complex security measures’ implementation. These inherent limitations make it challenging to deploy robust cryptographic and intrusion detection systems that are resource-intensive.
- Deployment and Scalability: The large-scale deployment of IoT devices complicates the management of security measures. A significant challenge is ensuring consistent security protocols across many devices without centralized control.
- Connectivity: IoT devices typically connect through heterogeneous networks that can be insecure or unreliable. This variability in connectivity exposes IoT systems to increased risks of network-based attacks.
- Heterogeneity: The diversity of IoT devices in terms of operating systems, hardware capabilities, and communication protocols complicates the implementation of uniform security strategies, thus hampering interoperability and seamless integration of security solutions.
- Embedded and Outdated Software: Many IoT devices run on embedded software that may not be regularly updated, leading to vulnerabilities. The lack of regular updates and patches increases the risk of security breaches.
- Big Data: The vast amount of data generated by IoT devices necessitates effective protection measures to ensure privacy and security. Managing the security of such large-scale data without compromising system performance is daunting.
- Dynamic Topology: The dynamic nature of IoT networks, where devices can frequently join and leave, makes it challenging to maintain a stable security infrastructure and manage the integrity of the network.
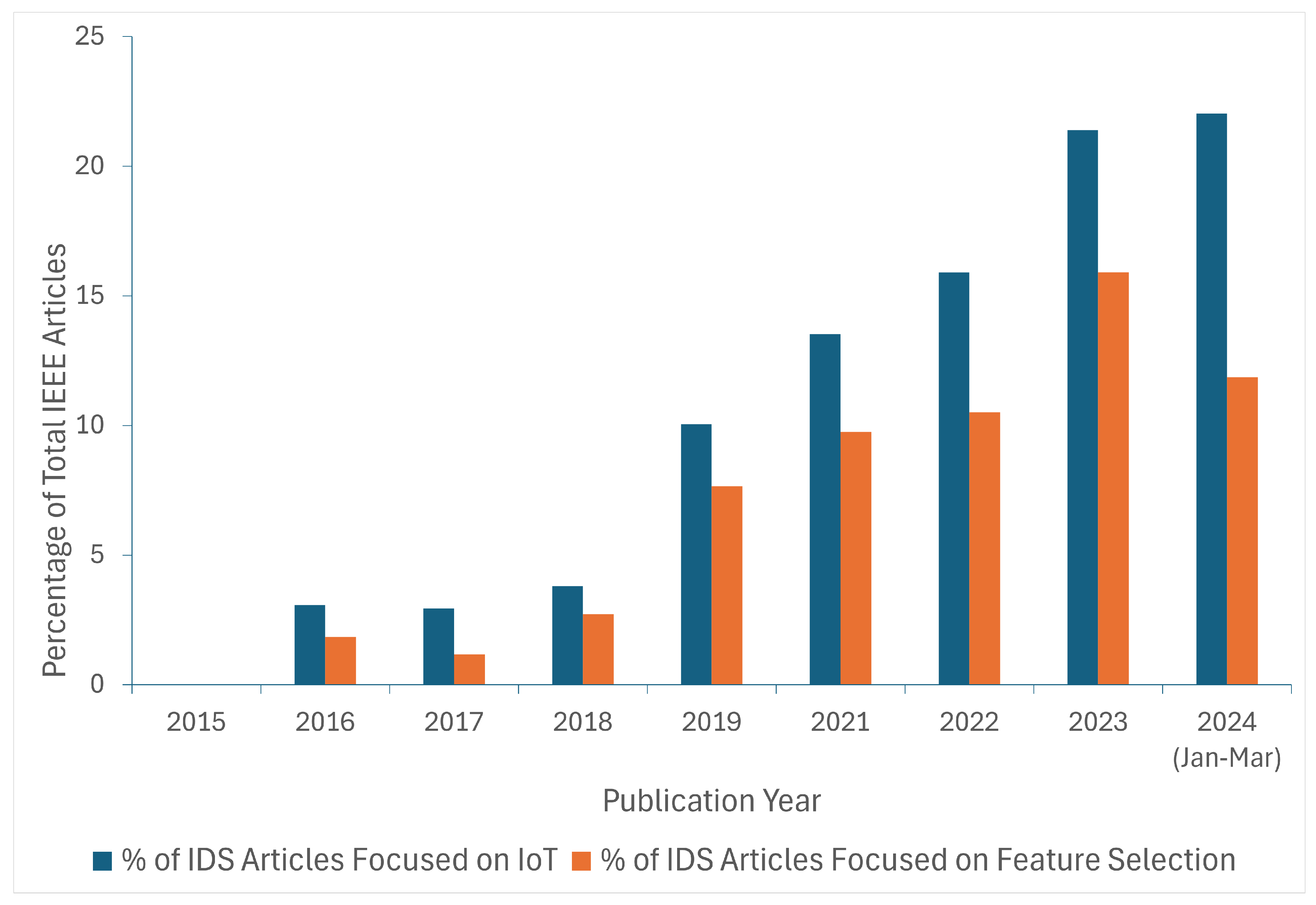
1.3. Trends in IDS Research: Focus on IoT and Feature Selection
1.4. Importance of Dataset Optimization in ML/DL-Based IDS Development
1.5. Contributions and Comparative Analysis
1.6. Structure of the Study
- Section 1: Introduction - Outlines the IoT landscape, security challenges, and the role of ML/DL in addressing these issues.
- Section 2: Research Methodology - Describes the methods used to gather and analyze relevant data systematically.
- Section 3: IDS Architectures and Advancements in IoT - Provides an in-depth exploration of various IDS architectures.
- Section 4: ML/DL Use in IDS - Examines how different ML and DL models enhance detection capabilities.
- Section 5: Optimizing IDS with Feature Selection - Discusses the critical role of feature selection in enhancing IDS efficiency.
- Section 6: Datasets and Data Balancing in IDS - Examins a range of datasets specific to IoT and broader network environments and discusses various techniques to ensure data balance, which is crucial for the effectiveness of IDS models in handling real-world uneven data distributions.
- Section 7: Observations, Challenges, and Future Directions - Reflects on the findings and outlines potential areas for future research.
- Section 8: Conclusion - Summarizes the essential findings and contributions of the study, emphasizing their implications for IoT security.
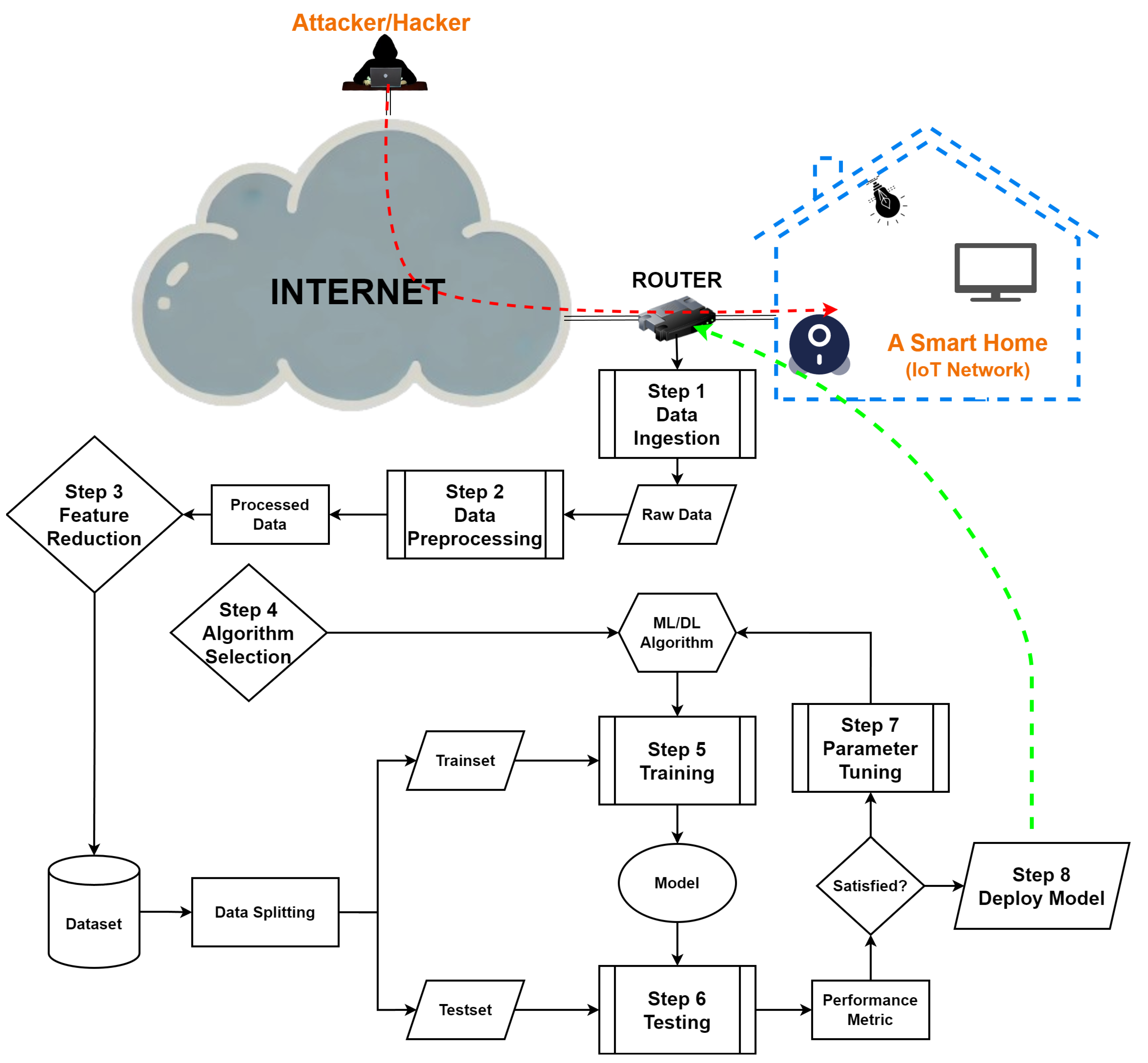
2. Research Methodology
2.1. Objectives and Research Questions
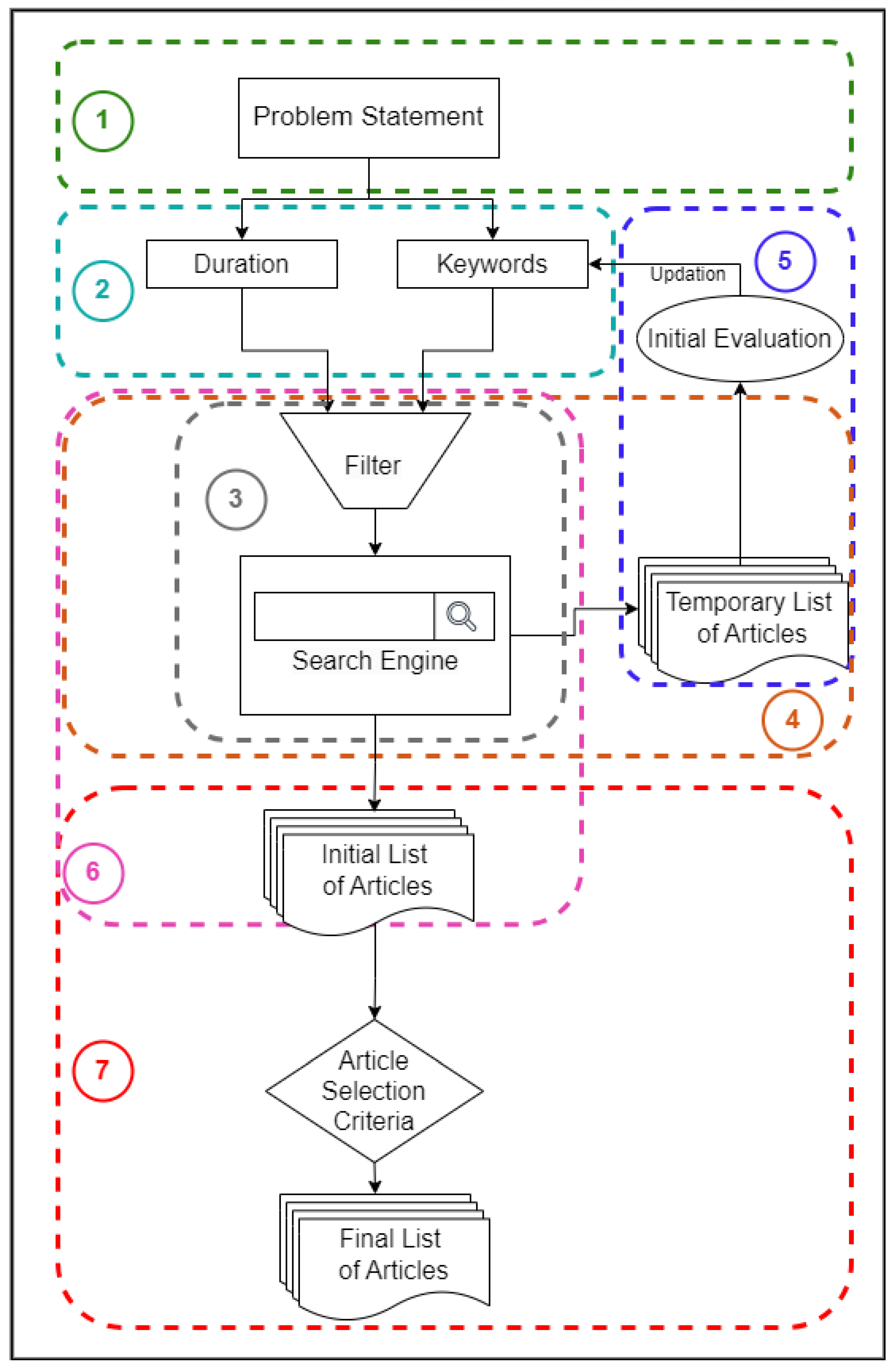
2.2. Research Study Selection
3. IDS Architectures and Advancements in IoT
3.1. Types of IDS and Their Applicability to IoT
3.2. Advances Through ML and DL
4. ML/DL Use in IDS
4.1. ML Application in IDS
4.1.1. Traditional Machine Learning Algorithms
- Logistic Regression (LR): Often used for binary classification tasks, LR models the probabilities for classification problems, such as distinguishing between normal and malicious activities [97].
- Support Vector Machine (SVM): SVM is robust in high-dimensional spaces, making it suitable for IDS where it constructs a hyperplane in a multidimensional space to separate different classes [70].
- Decision Trees (DT): DTs are popular for their simplicity and interpretability. They use a tree-like model of decisions and their possible consequences [68].
- Naïve Bayes (NB): This algorithm applies Bayes’ Theorem with the assumption of independence between features. It’s particularly effective in IDS for its speed and performance with large datasets [81].
- k-Nearest Neighbors (kNN): A non-parametric method for classifying data based on the closest training examples in the feature space [84].
4.1.2. Ensemble Learning Algorithms
- Random Forest (RF): An ensemble of Decision Trees, typically trained with the “bagging” method, RF is very effective in IDS due to its ability to reduce overfitting and improve model accuracy [66].
- AdaBoost: Works by combining multiple weak classifiers to form a robust classifier. AdaBoost is used in IDS to enhance classification accuracy by focusing more on complex cases [124].
- Gradient Boosting Machine (GBM): GBM builds an additive model in a forward stage-wise fashion; it allows for the optimization of arbitrary differentiable loss functions, making it versatile for various IDS tasks [75].
- Extreme Gradient Boosting (XGB): Known for its efficiency, flexibility, and portability, XGB delivers high performance and speed when processing large volumes of data [75].
- CatBoost: This algorithm excels in handling categorical features and is less prone to overfitting than other methods [98].
4.1.3. Innovative ML Implementations in IDS:
- RF in Smart Cities: The Anomaly Detection IoT (AD-IoT) system [66] utilizes the RF algorithm to detect compromised IoT devices within smart city networks. This system is designed for distributed fog networks, aiming to enhance the responsiveness and scalability of attack detection.
- Multi-Algorithm IDS for Smart Homes: Anthi et al. [67] developed a novel three-layer IDS for IoT networks within smart homes. This system employs multiple algorithms such as NB, Bayesian Networks (BN), DT, LR, SVM, and RF to classify device behaviors and detect malicious activities.
- DDoS Attack Detection: Chaudhary & Gupta [68] addressed significant security vulnerabilities associated with DDoS attacks through compromised IoT devices. The authors propose a new ML approach for efficient DDoS traffic detection within local network routers. Upon careful testing and evaluation, RF outperformed LR, SVM, and DT.
- Comprehensive Algorithm Evaluation: A study by Hasan et al. [69] evaluated the effectiveness of various ML algorithms like LR, SVM, DT, and RF in detecting attacks within IoT systems.
- Edge Computing in Smart Homes: The implementation discussed in [128] leverages an ML classifier, specifically a Radial Basis Function (RBF)- SVM, within a smart home system simulation developed on Alibaba ECS, focusing on enhancing network security detection using edge computing technology.
- DoS Protection with ML: Verma & Ranga [75] explored the application of various ML classifiers to protect IoT systems against DoS attacks, assessing their performance on prominent IoT datasets and implementing them on IoT-specific hardware.
- ML Classifier Evaluation Framework: The framework introduced by Shafiq et al. [81] incorporates a hybrid algorithm based on a bijective soft set approach to evaluate and select the most effective ML algorithm from several available options for identifying cyber-attacks in IoT networks.
- Network Intrusion Detection: The study by Kocher and Kumar [84] applied multiple ML classifiers to the recent UNSW-NB15 dataset to evaluate their performance in network intrusion detection.
4.2. DL Application in IDS
4.2.1. Traditional DL Algorithms
- Multi-Layer Perceptron (MLP): MLPs are fundamental neural networks with one or more hidden layers between input and output layers. They are effective for pattern recognition tasks due to their ability to learn non-linear decision boundaries [115].
- Artificial Neural Networks (ANN) and Deep Neural Networks (DNN): ANNs are the backbone of many DL approaches [65], with DNNs representing an extension of ANNs that contain multiple hidden layers [95]. These structures are adept at processing complex datasets commonly found in IDS. DNNs, in particular, enhance the capability to capture deeper levels of data abstraction.
- Convolutional Neural Networks (CNN): CNNs are particularly beneficial for feature extraction because they can process data in a grid-like topology, such as images or time series. They use convolutional layers to detect essential features automatically without any human supervision. CNNs are utilized in both one-dimensional (1D) and two-dimensional (2D) forms for analyzing network traffic and log data [79].
- Recurrent Neural Networks (RNN): RNNs are designed to handle sequential data, making them suitable for time-series analysis in IDS [77]. LSTM units [121] and Gated Recurrent Unit (GRU) [126] are enhancements over traditional RNNs, providing solutions to the vanishing gradient problem and improving the memory capacity of the model.
- Autoencoders (AE): AEs are used for unsupervised learning of efficient coding. They learn to compress (encode) the input into a more miniature representation and then reconstruct (decode) the output from this representation. Convolutional Variational Auto Encoders (CVAE) [72] is a type of AE that provides a probabilistic manner for describing observations in latent space.
- Generative Adversarial Networks (GAN): GANs involve two neural networks, a generator and a discriminator, which compete against each other. This structure is highly effective for generating new data samples. Conditional Generative Adversarial Networks (CGANs) extend GANs by adding a condition to the generation process, enhancing their applicability in IDS for generating realistic attack scenarios to test systems [87].
- Deep Belief Networks (DBN): DBNs are generative models that consist of multiple layers of stochastic, latent variables. They are effective in feature extraction and classification tasks [59].
4.2.2. Select Deep Learning Implementations in IDS:
- DDoS Attack Detection Using ANN: Soe et al. [65] developed a detection system tailored for IoT environments to identify DDoS attacks caused by malware like Mirai efficiently. This implementation leverages an ANN.
- Hybrid IDS Using DBN: In the work presented by Yang et al. [59], a hybrid IDS was proposed using DBN combined with a modified density peak clustering algorithm (MDPCA). This system segments the training data into manageable clusters, thereby reducing data imbalance and enhancing the detection of minority class attacks, while DBNs are used for high-level feature extraction.
- Three-Layer IDS for Smart Homes: The research by Latif et al. [64] introduced a novel three-layer IDS designed explicitly for Industrial Internet of Things (IIoT) networks. Using deep transfer learning (DTL) and a tri-layer architecture combining CNN, GA, and bootstrap aggregation.
- Innovative IDS with DNN and Transfer Learning: The study outlined by Qureshi et al. [72] utilized a DNN combined with ASTL. This approach integrates features extracted from a pre-trained network with original data features, enhancing the IDS’s capability to detect network security breaches.
- Hybrid CNN-LSTM Model for IoT Security: Roopak et al. [74] explored a hybrid CNN-LSTM model focused on combating DDoS attacks in IoT networks. This model efficiently handles spatial and temporal data, significantly improving the system’s capability to detect and respond to cybersecurity threats.
- Advanced RNN for Fog Computing: The implementation by Almiani et al. [77] detailed an advanced IDS tailored for the security needs of Fog computing environments essential for IoT. This system employed a multi-layered RNN to detect various cyber threats effectively.
4.3. Performance Measures in IDS
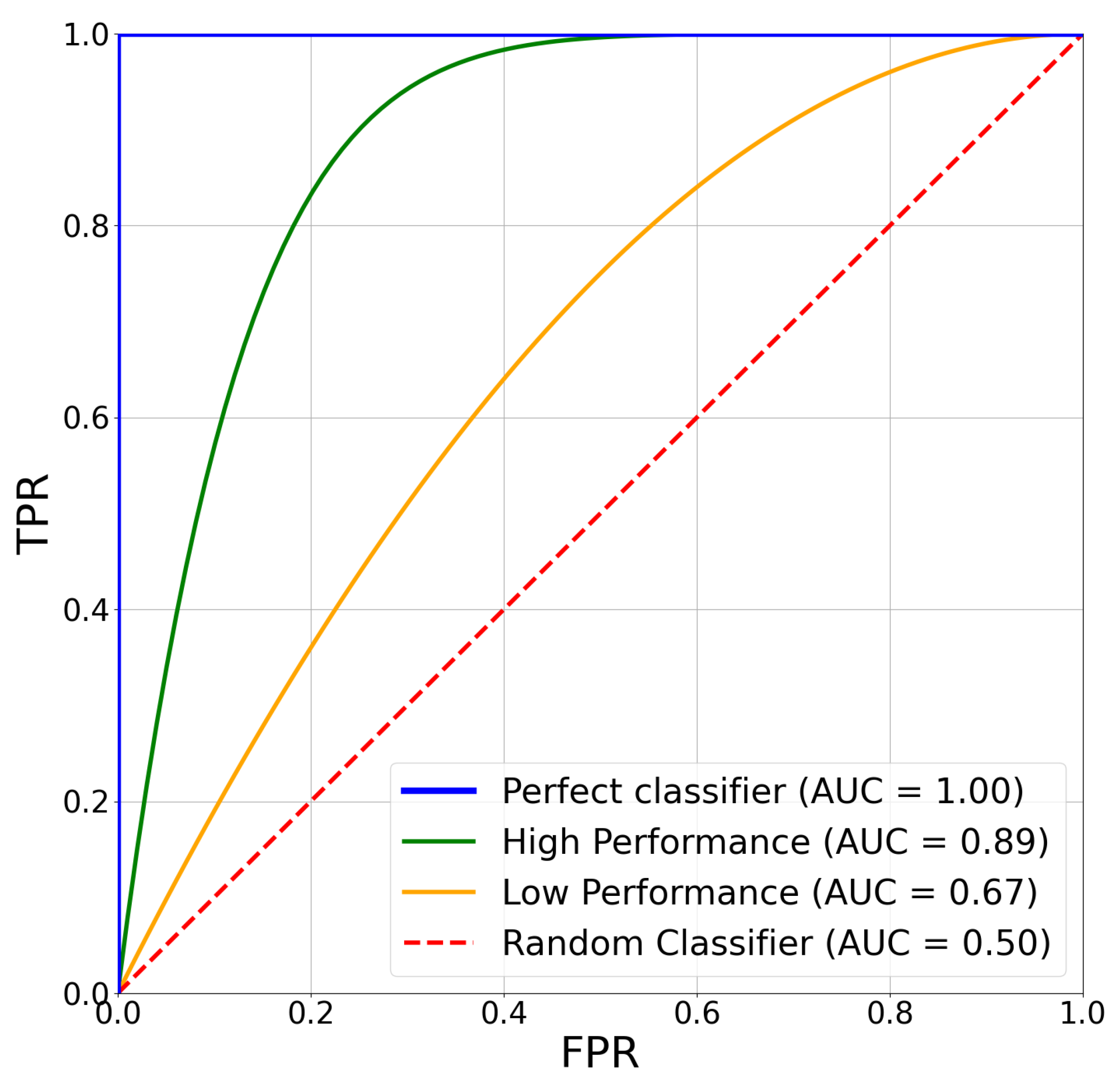
4.3.1. Confusion Matrix
- True Positives (TP): Correctly predicted positive observations.
- True Negatives (TN): Correctly predicted negative observations.
- False Positives (FP): Incorrectly predicted as positive, also known as Type I error.
- False Negatives (FN): Incorrectly predicted as negative, also known as Type II error.
4.3.2. Key Performance Metrics
- Perfect Classifier: This classifier reaches the top left corner of the plot, indicating a TPR of 1 with a FPR of 0. It has an AUC of 1.00.
- High-Performance Classifier: This classifier performs well with a high TPR and a low FPR, achieving an AUC of 0.88.
- Low-Performance Classifier: This classifier performs modestly, with an AUC of 0.65. It shows a higher FPR for a given TPR than the high-performance classifier.
- Random Classifier: This classifier performs no better than random guessing, resulting in an AUC of 0.50, represented by a diagonal line from (0,0) to (1,1).
5. Optimizing IDS with Feature Selection
5.1. Feature Selection & Types
- Filter Methods: These methods apply a statistical measure to assign a scoring to each feature. The measure ranks the features and is either selected to keep or removed from the dataset. Filter methods are generally faster and less computationally expensive than other feature selection methods because they do not involve training models. A common filter method is the correlation-based feature selection, which measures the correlation between each feature and the target variable [25].
- Wrapper Methods: Wrapper methods consider selecting a set of features as a search problem, where different combinations are prepared, evaluated, and compared to other combinations. A predictive model evaluates a combination of features and assigns a score based on model accuracy. Wrapper methods can be very computationally intensive and usually involve training a new model for each feature (or combination of features) added or removed [25].
- Embedded Methods: Embedded methods perform feature selection during the model training process and are specific to given learning algorithms. These methods integrate feature selection as part of the training process and are more efficient than wrapper methods since they include feature selection as part of the model construction process. Techniques like Lasso and Ridge regression are embedded methods that regularize coefficients to zero to reduce the number of features [130].
5.2. General Approaches for Feature Selection in IDS
5.2.1. Filter-Based Feature Selection in IDS
- Correlation:
- Measures the linear relationship between two variables, focusing on how closely changes in one variable are associated with changes in another. In IDS, correlation is used to select features that strongly relate to the detection of threats. For instance, the research by Woo et al. [131] and Dat-Thinh et al.[92] utilize correlation-based filters to streamline feature sets for enhanced intrusion detection accuracy.
- Information Gain (IG):
- Assesses how much information a feature provides about the class, calculating the reduction in entropy. IG has been effectively applied in IDS to filter out less informative features, enhancing model performance as shown in studies by Kasongo & Sun [132] and by Wirawan et al.[133].where is the entropy of the target variable, and is the conditional entropy of the target given feature f.
- Mutual Information (MI):
- A measure that captures the amount of information obtained about one random variable through another. It is instrumental in IDS for identifying features that share MI with the class attribute. The implementation of MI in IDS is evident in works like [134] and [58], where it helps select features that contribute significantly to classification accuracy.where is the joint probability distribution function of X and Y, and and are the marginal probability distribution functions of X and Y, respectively.
- Chi-Square:
- This test measures the lack of independence between a feature and the class. It is widely used in IDS to determine which features are statistically significant to the class outcomes. Chi-Square tests are highlighted in the works of Kocher & Kumar [84] and Gad et al. [109], helping to identify features strongly associated with the presence or absence of intrusions.where is the observed frequency, and is the expected frequency under the null hypothesis.
- Gain Ratio:
- An extension of IG that normalizes its values to reduce bias towards multi-valued features. This method is particularly effective in environments where features vary in the number of levels. Studies by Kumar & Gupta [85] and Albulayhi et al. [88] have employed the Gain Ratio to ensure a balanced consideration of feature importance across different feature types.where is the entropy of feature f.
5.2.2. Wrapper and Embedded Feature Selection in IDS
5.2.2.1. Wrapper Methods in IDS
- SVM-Based Wrapper: A study by Taher et al. [135] uses an SVM to evaluate feature subsets, aiming to maximize classification accuracy directly.
- Extra Tree (ET) Wrapper: The ET classifier serves as a wrapper in the study by Kasongo & Sun [136], assessing feature sets and leveraging its ensemble nature to evaluate feature importance effectively.
- Non-dominated Sorting Genetic Algorithm (NSGA) with LR: Khammassi & Krichen [137] combined the NSGA with LR in a wrapper approach to optimize feature combinations, balancing IDS complexity and performance.
- Rf Wrapper: Research by Kumar & Gupta [85] employs RF to evaluate features, utilizing its inherent feature importance measures to guide the selection process.
- Multiple Classifier Wrappers: The work by Rahman et al. [86] uses various classifiers, including SVM, DT, and NB, within a wrapper framework to identify the most compelling features for detecting network intrusions.
5.2.2.2. Embedded Methods in IDS
- DT Embedded Method: DT inherently evaluates feature importance during model training, effectively reducing the feature space without separate validation, as shown in the work of Sarker et al. [138].
- DL Embedding: Yu & Bian [139] employed CNN and DNN to automatically select features through their training process, adjusting weights in network layers that correspond directly to feature relevance.
- RF Regressor Embedded Method: As detailed in the work by Malathi and Padmaja [53], embedding feature selection within an RF Regressor allows for simultaneous learning and feature evaluation, enhancing the model’s focus on the most predictive features.
5.3. Nature-Inspired Optimization Algorithms for Feature Selection in IDS
5.3.1. Filter Implementation in IDS
- Reptile Search Algorithm (RSA): The authors Dahou et al. [56] utilized RSA for its efficiency in exploring and exploiting the search space, optimizing feature selection by mimicking reptilian motion, which significantly improves IDS performance.
- Spider Monkey Optimization (SMO): The study by Otoum et al. [96] employs SMO, inspired by the foraging behavior of spider monkeys, to optimize the selection of features, thereby enhancing the detection capabilities of IDS systems.
- Particle Swarm Optimization (PSO): PSO’s mechanism of social information sharing is utilized to guide the search towards optimal feature sets, significantly improving computational efficiency and detection rates in IDS [124].
- Improved Dynamic Sticky Binary PSO (IDSBPSO): This variant [106] introduces dynamic adjustments to particles’ behavior, sticking to promising areas of the search space to find the best feature subsets.
- African Vulture Optimization (AVO): Implemented by Alsirhani et al. [140], AVO draws inspiration from the scavenging behavior of vultures to efficiently scan and select optimal feature sets for IDS.
5.3.2. Wrapper Implementation in IDS
- Discrete Variant of the Cuttlefish Algorithm (DF-CFA): Al-Daweri et al. [141] apply this algorithm, which mimics the adaptive coloration of cuttlefish, to optimize the feature space and enhance model accuracy specifically tailored for intrusion detection.
- Firefly Optimization (FFO): Saraeian & Golchi [142] and Karthikeyan et al. [122] have implemented FFO algorithm for feature selection. It simulates the behavior of fireflies, which is particularly effective in finding global optima in the search space, thereby selecting the most relevant features for IDS.
- Genetic Algorithm (GA): GA’s evolutionary strategies are leveraged by Zhang et al. [143] to evaluate and select features that maximize the performance of the IDS.
- Flamingo Search Algorithm (FSA): This algorithm optimizes feature selection by mimicking the foraging behavior of flamingos, focusing on efficiently identifying relevant features to improve detection rates [60].
- Modified Equilibrium Optimization Algorithm (MEOA): This algorithm enhances traditional equilibrium optimization by introducing modifications that adapt better to the IDS’s requirements, selecting features that significantly boost system performance [62].
- Modified FFO: The work by Almuqren et al. [63] enhances the standard FFO algorithm to suit the complex feature spaces in IDS better, improving both the efficiency and accuracy of the intrusion detection system.
- Chaotic Binary Pelican Optimization Algorithm (CBPOA): As used by Alrowais et al. [111], this algorithm introduces a variation of POA using chaotic sequences, enhancing the exploration capabilities and ensuring a more diverse search for optimal features in IDS.
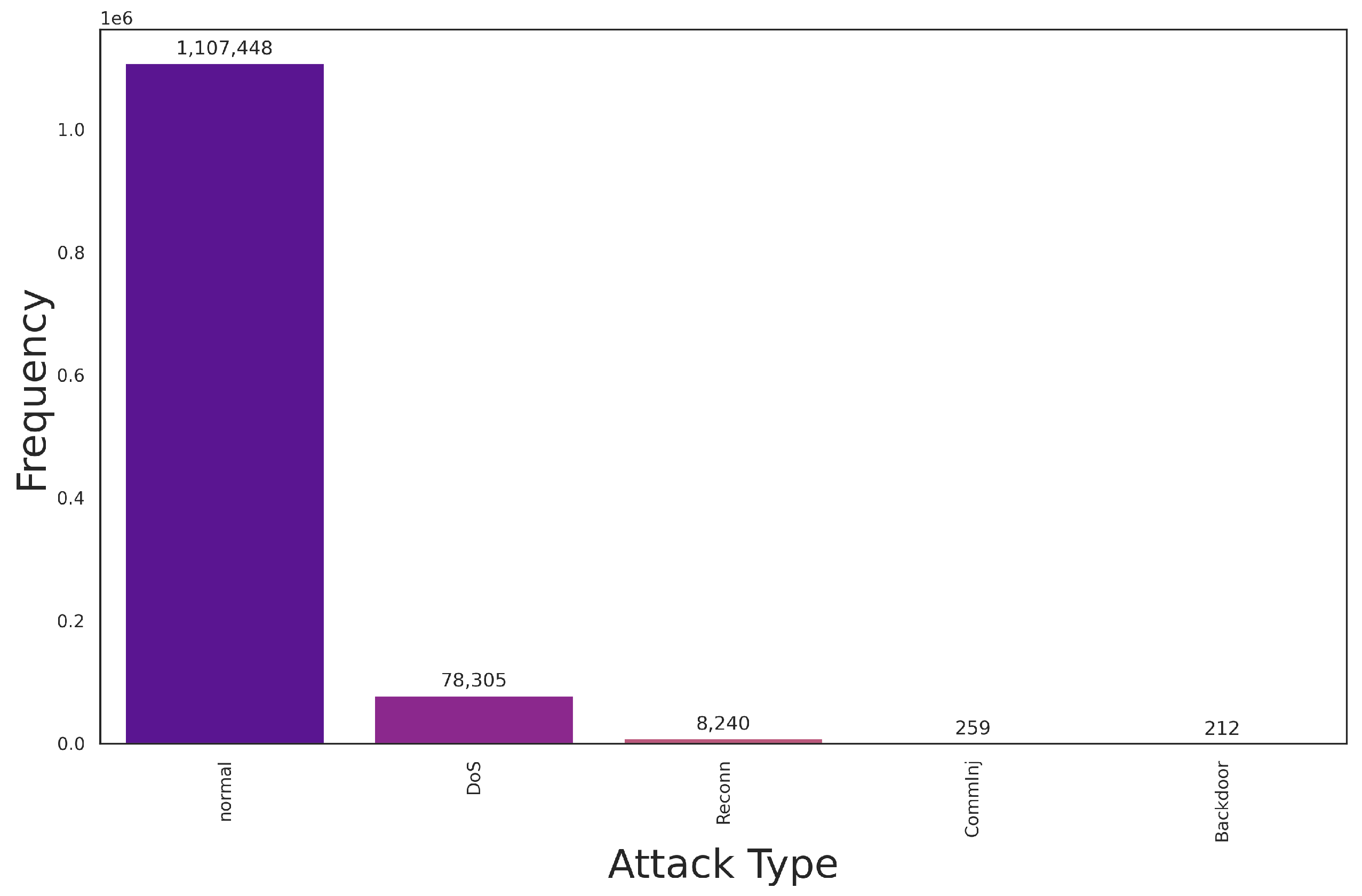
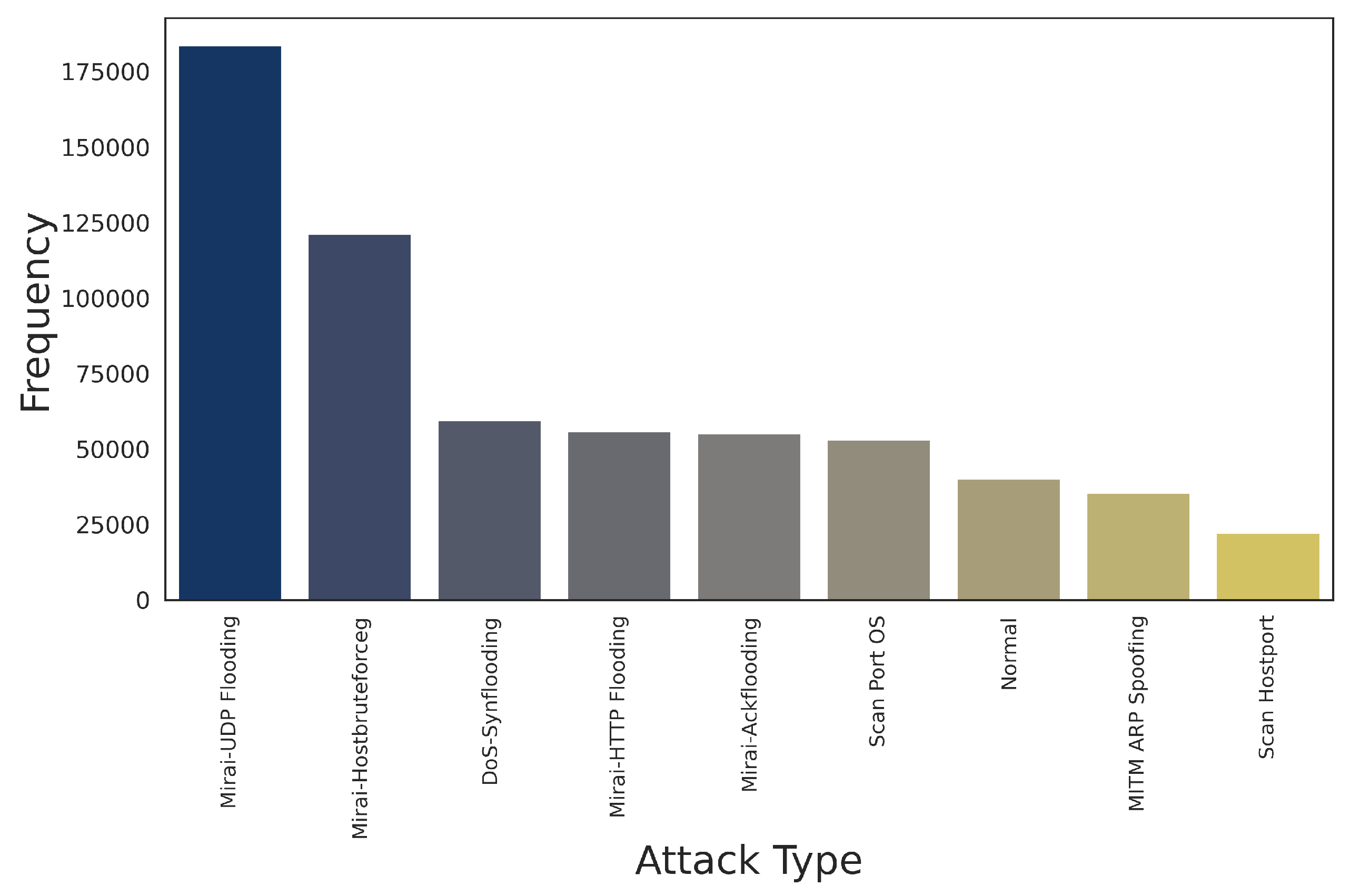
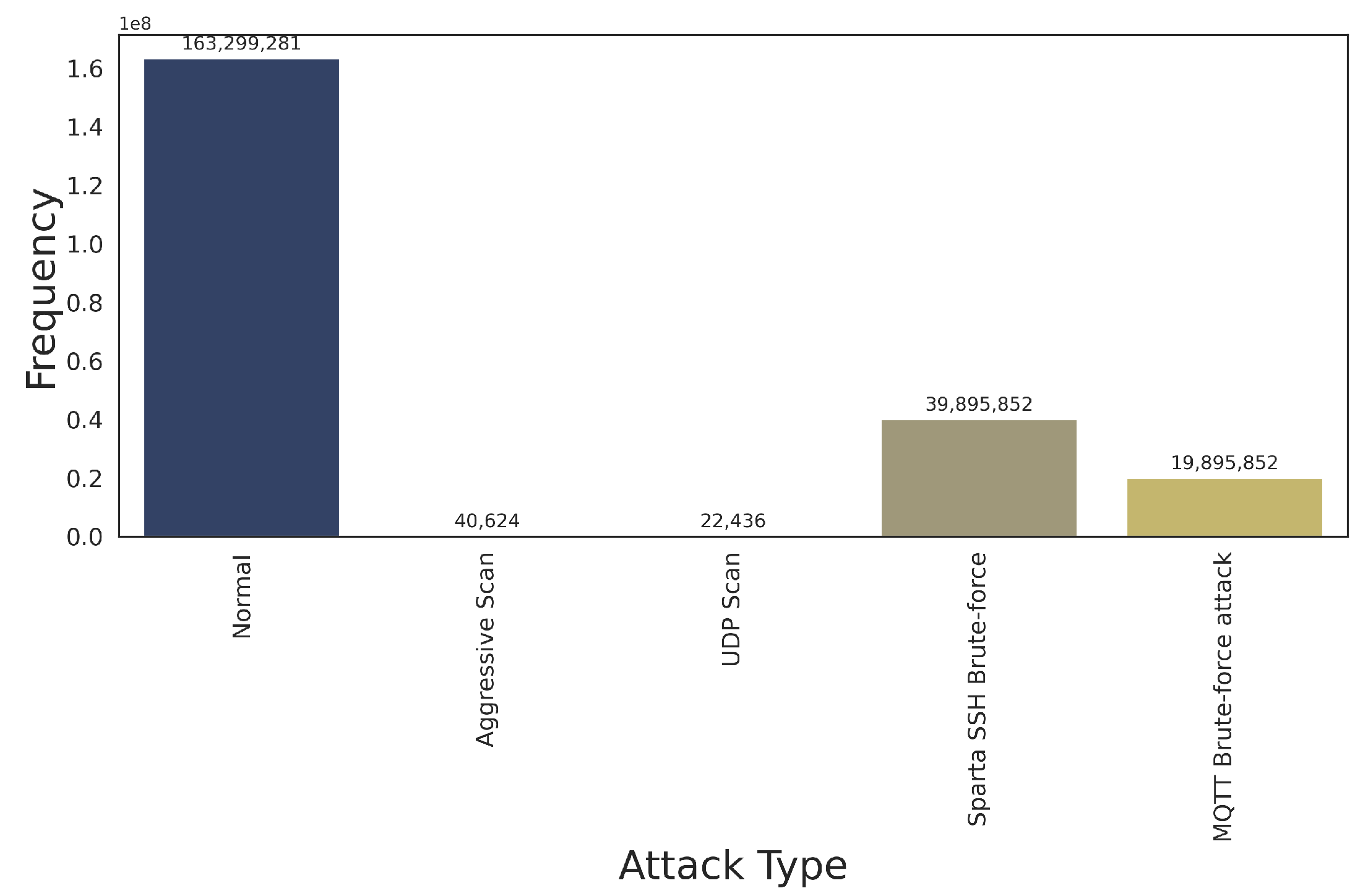
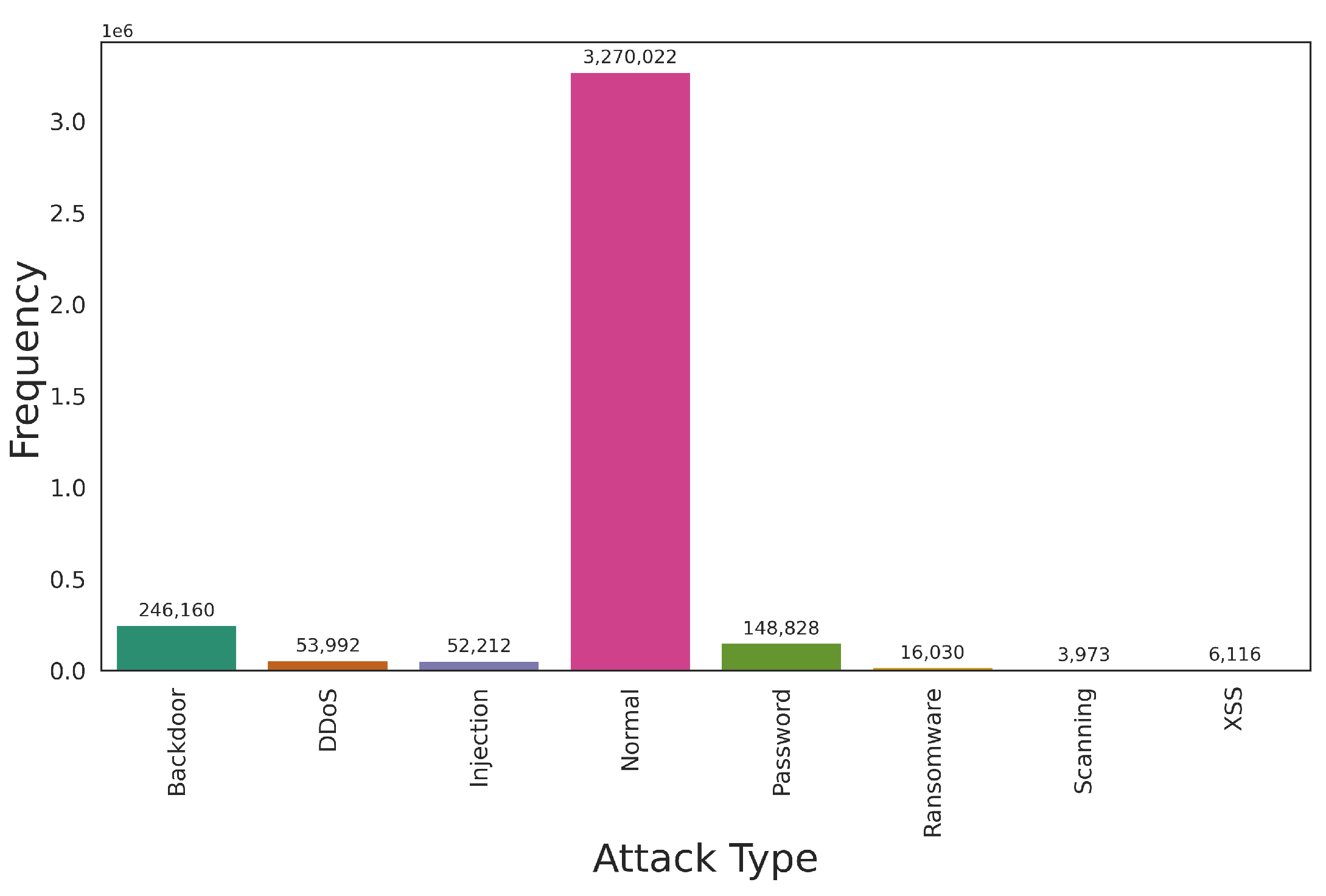
6. Datasets and Data Balancing in IDS
6.1. IDS Datasets
6.1.1. IoT IDS Datasets
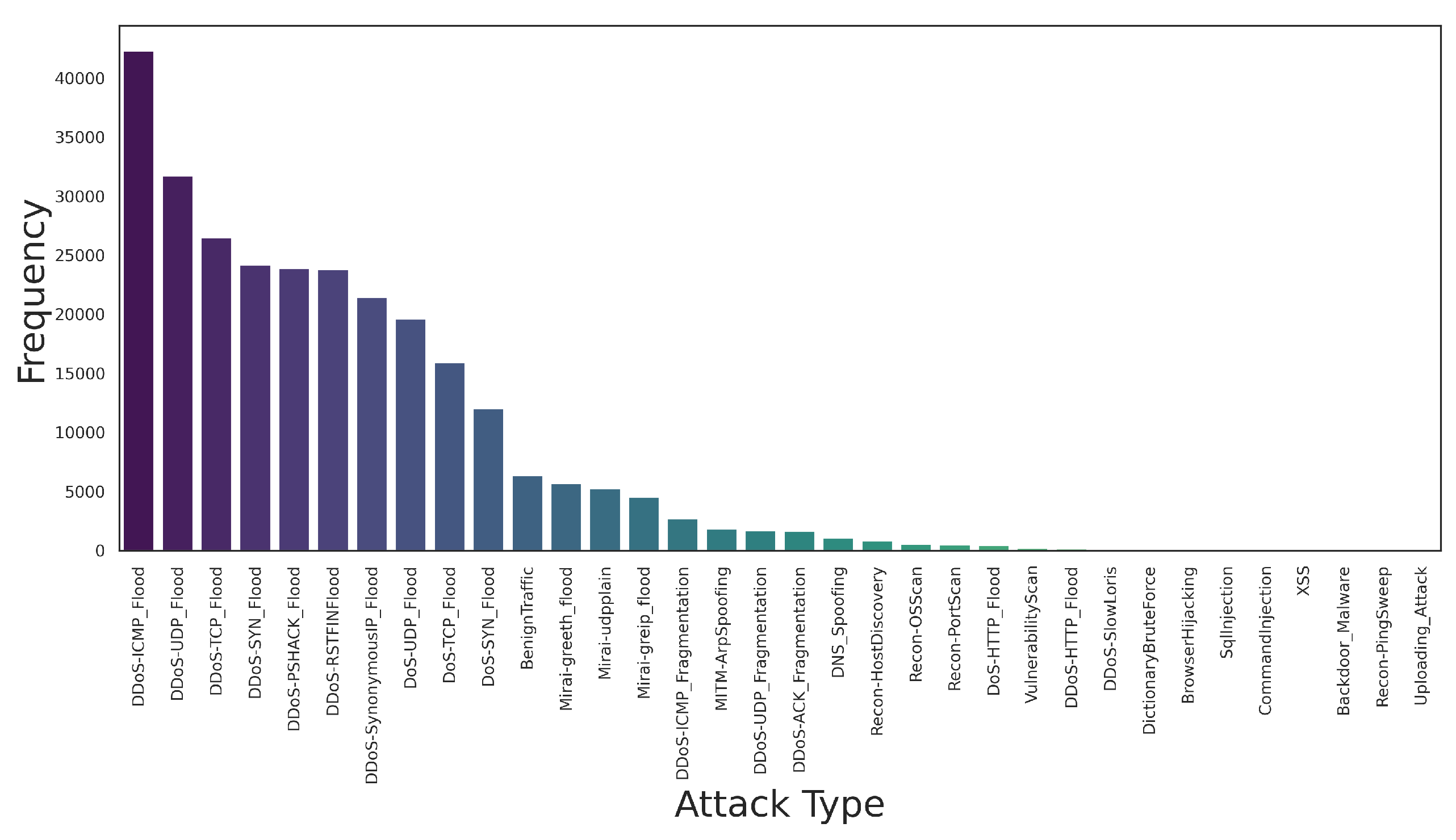
6.1.1.1. CICIoT2023 Dataset
6.1.1.2. Edge-IIoT Dataset
6.1.1.3. WUSTL-IIoT-2021 Dataset
6.1.1.4. IoTID20 Dataset
6.1.1.5. MQTT-IoT-IDS2020 Dataset
6.1.1.6. TON-IoT Dataset
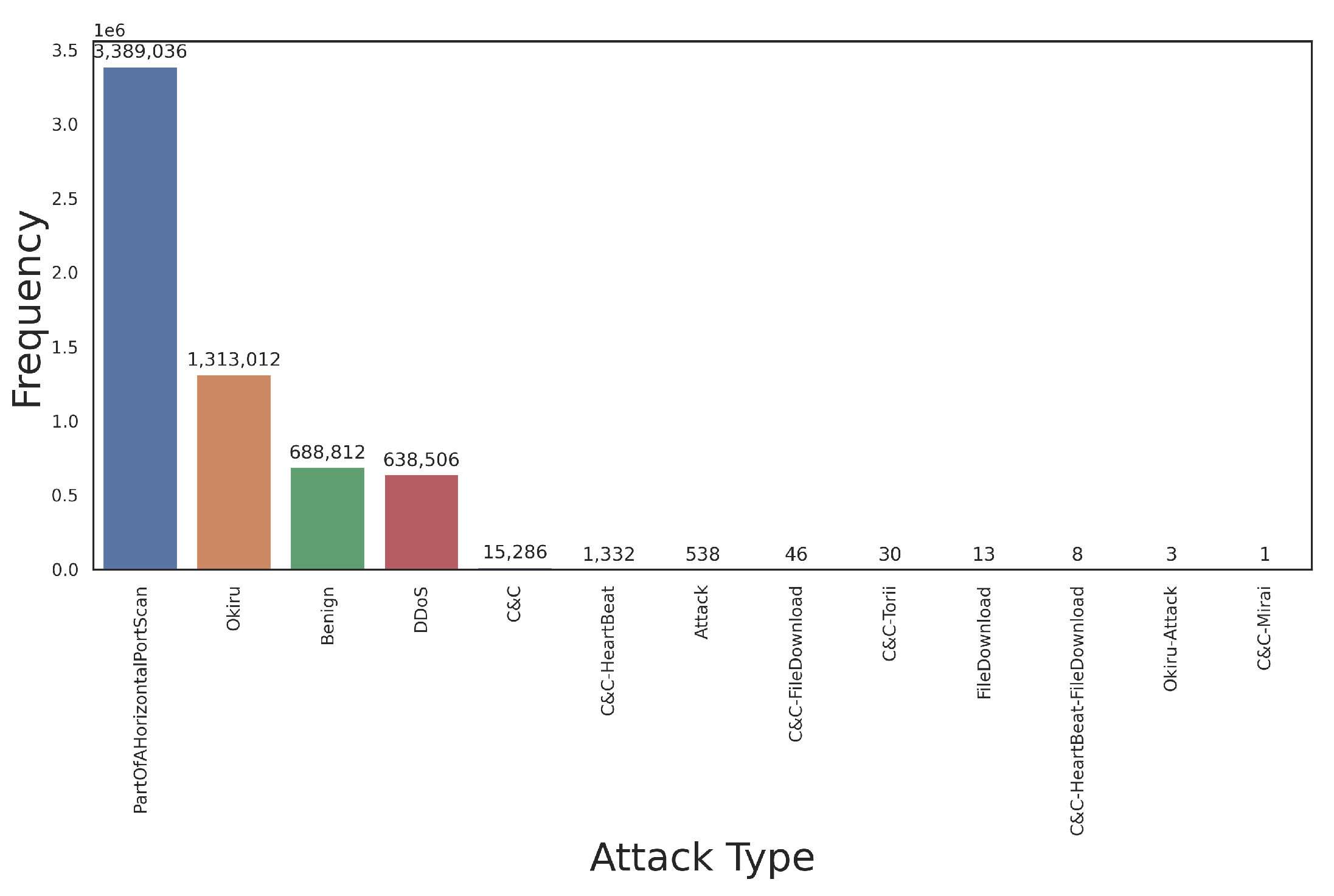
6.1.1.7. IoT-23 Dataset Overview
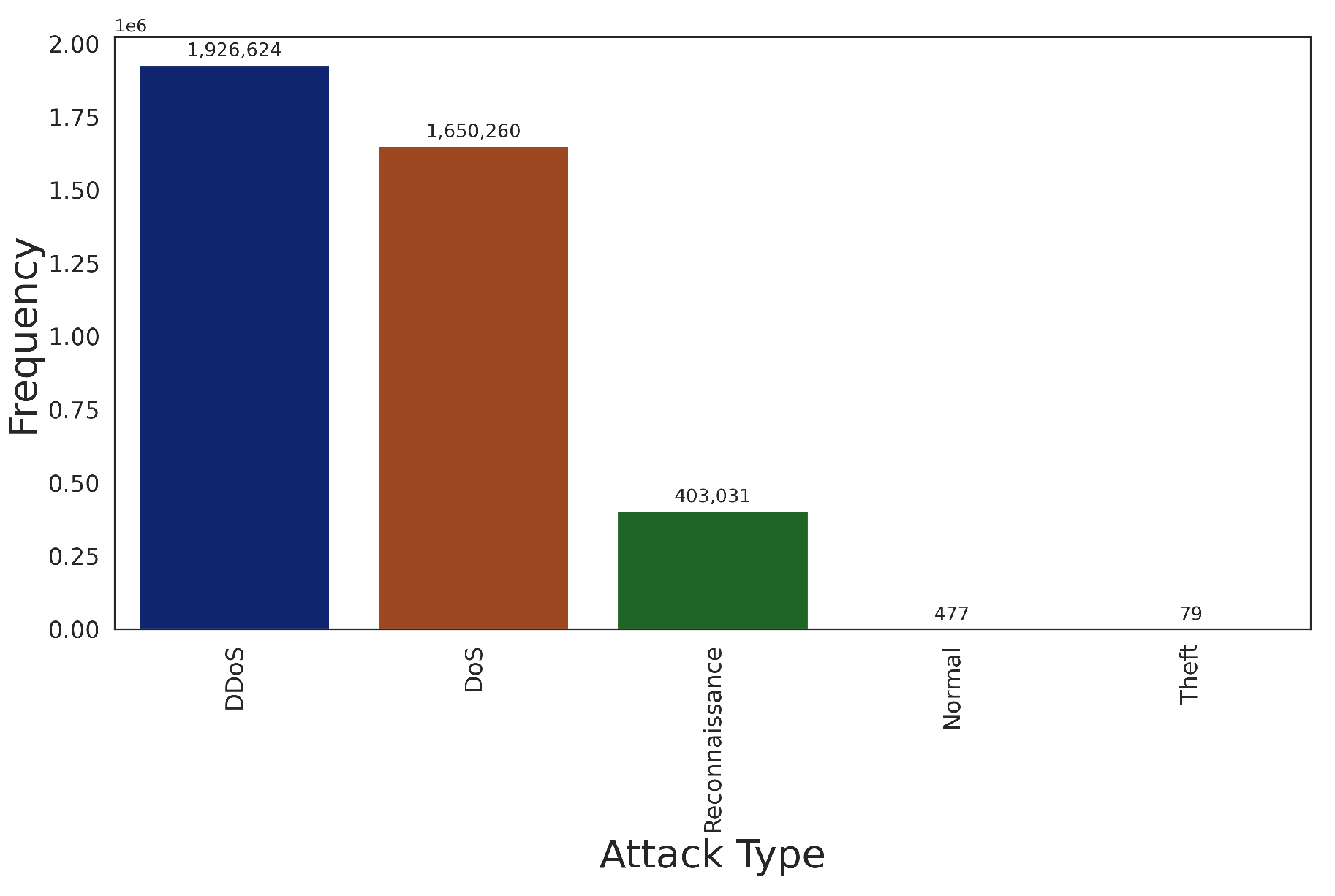
6.1.1.8. BOT-IoT Dataset Overview
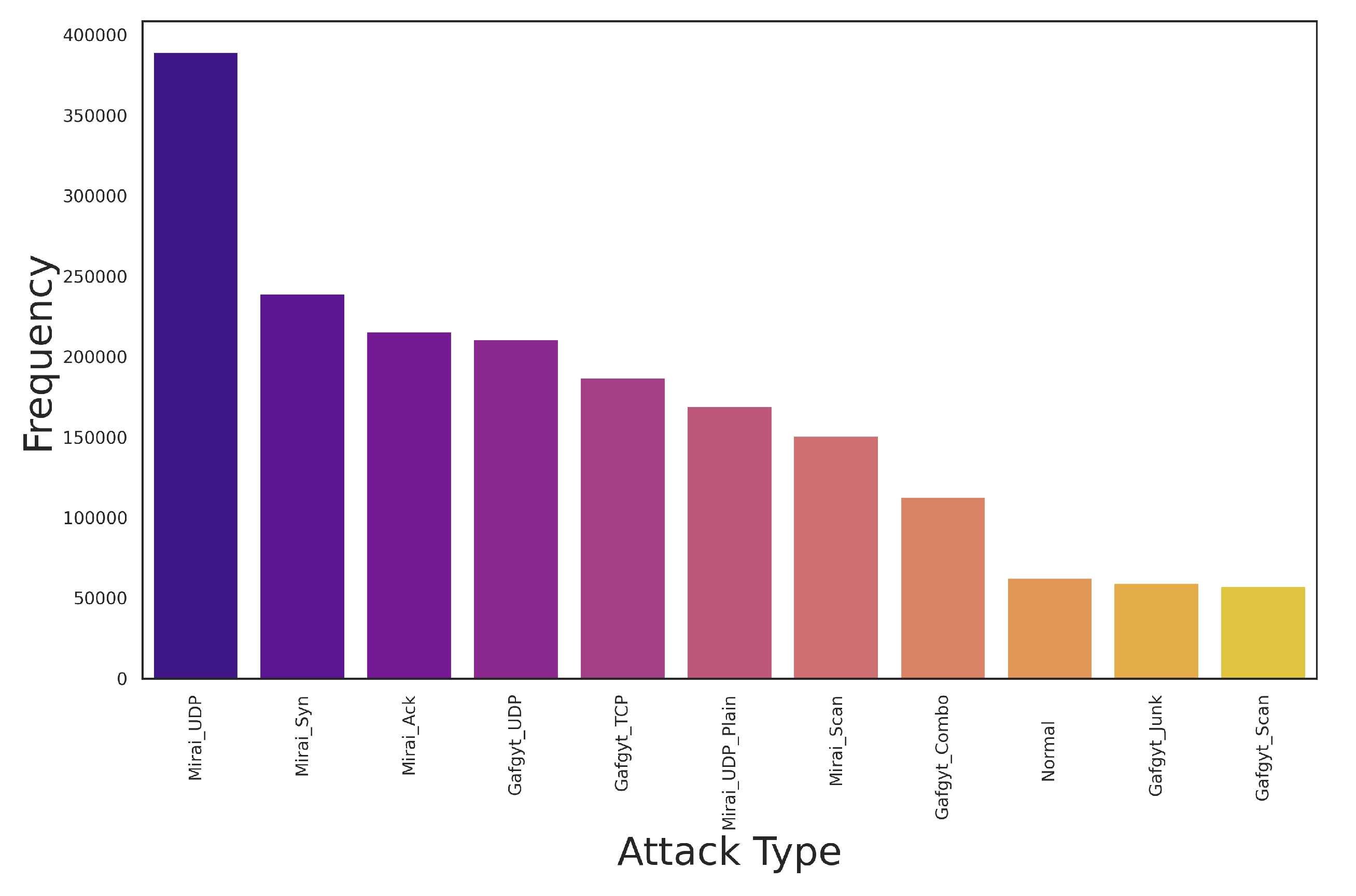
6.1.1.9. N-BAIOT Dataset Overview
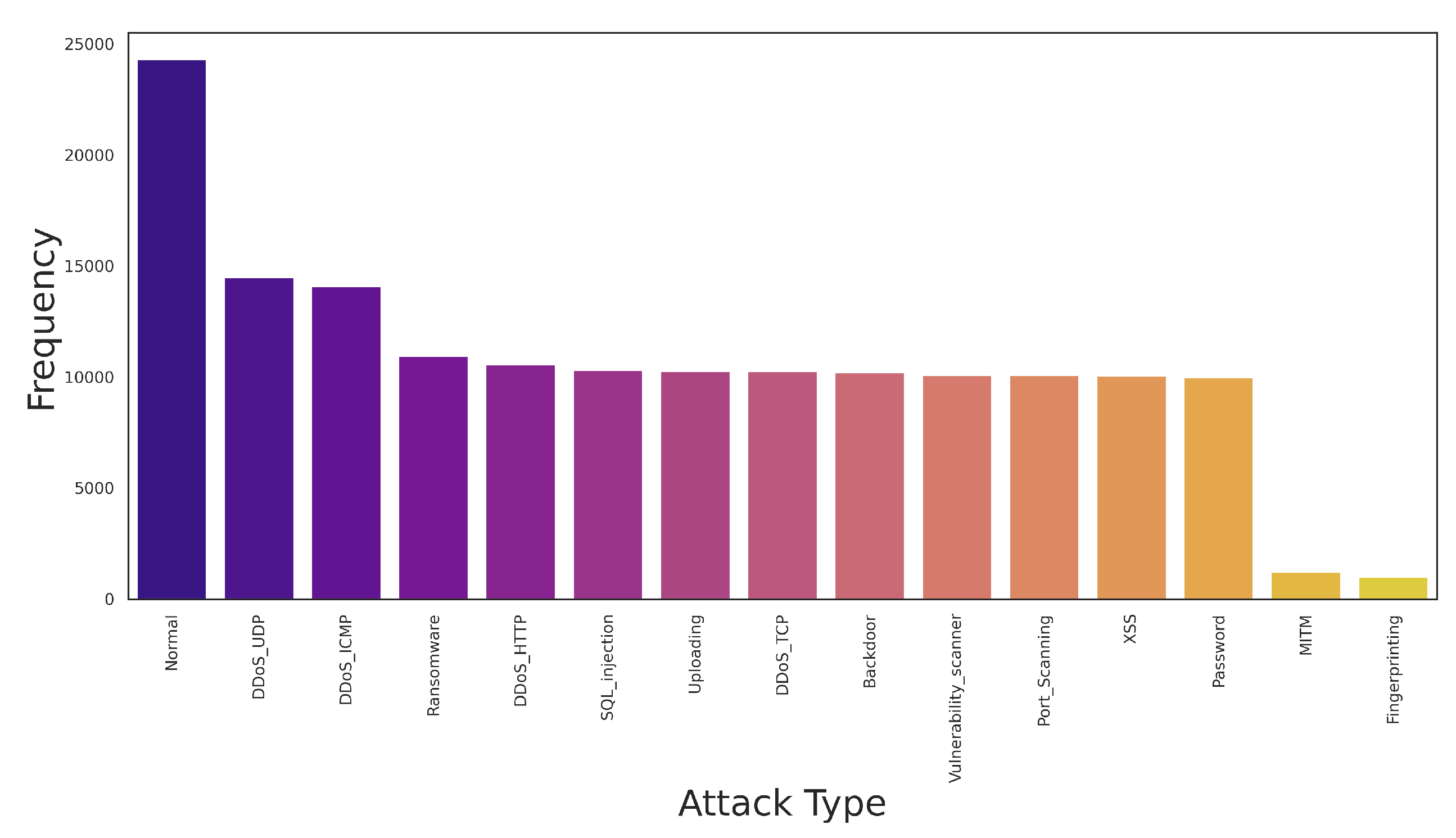
6.1.2. Regular IDS Datasets
6.2. Balancing IDS Datasets
6.2.1. Resampling Techniques
6.2.2. Algorithmic Approaches
6.2.3. Data Augmentation
7. Observations, Challenges, and Future Directions
7.1. Observations
- Advances in ML and DL: Integrating ML and DL in IDS has significantly improved detection capabilities, particularly in recognizing complex patterns and anomalies that traditional methods might miss. These approaches enhance the ability to detect sophisticated attacks, including zero-day vulnerabilities, by learning from large datasets.
- Shift from ML to DL Techniques: There is a noticeable trend toward employing DL techniques, such as CNN, for both feature extraction and attack detection. With their ability to process raw data and automatically extract features, DL models have shown superior performance in IDS tasks compared to traditional ML methods.
- Effectiveness of Feature Selection and Data Balancing: Techniques like feature selection and data balancing have been critical in optimizing IDS performance. Feature selection helps reduce model complexity and computational overhead, which is crucial for deployment in resource-constrained environments like IoT. Data balancing techniques such as SMOTE and GANs address the class imbalance issue, ensuring the models are trained on diverse attack scenarios.
- Increased Adoption of Hybrid and Ensemble Approaches: There has been a noticeable shift towards hybrid and ensemble IDS that combine multiple detection techniques or integrate various data handling strategies. This approach enhances the system’s robustness by leveraging the strengths of different methods, improving detection rates and accuracy.
- Emphasis on Real-Time Detection: The necessity for real-time threat detection has driven the development of IDS to analyze data streams in real-time, reducing the latency between threat identification and response. This capability is critical for mitigating cyber-attacks impact on IoT systems and networks.
7.2. Challenges
- Dynamic and Sophisticated Threats: Cyber threats are becoming more sophisticated, with attackers constantly developing new strategies to bypass security measures. IDS must evolve to detect zero-day attacks and advanced persistent threats, often exhibiting subtle and low-frequency characteristics.
- Big Data and Scalability Issues: The exponential growth in IoT devices results in massive data streams that IDS must process, often in real time. Scalability remains a formidable challenge, requiring efficient data management and processing capabilities to handle such volumes without degradation in performance.
- Resource Consumption and Lightweight IDS: Developing IDS that are both lightweight and efficient in resource consumption is critical, particularly for IoT environments where devices have limited processing power and battery life. Ensuring that IDS solutions do not overburden the host devices remains a significant challenge.
- Integration and Standardization: Integrating IDS seamlessly across diverse platforms and ensuring compatibility with new IoT protocols is increasingly challenging. There is also a lack of standardization in security protocols across devices and networks, complicating the deployment of universal solutions.
- Maintaining High Accuracy with Imbalanced Data: Imbalanced datasets, where some attack types are underrepresented, can lead to biased models that perform well on frequent classes but poorly on rare yet critical attack types. This remains a significant hurdle in developing robust IDS.
7.3. Future Directions
- Development of Adaptive Systems: Future IDS should focus on adaptability, utilizing online learning or transfer learning to continuously adjust to new data or attack patterns without full retraining cycles. This would help maintain high detection rates over time.
- Cross-Domain Security Solutions: There is a critical need for solutions operating across different network layers and environments—from edge devices to the cloud—providing end-to-end security. This includes developing IDS that can handle diverse IoT devices and communication protocols.
- Leveraging Emerging Technologies: Integrating innovative technologies like blockchain for decentralized data sharing and AI for predictive threat intelligence could significantly enhance the detection capabilities and reliability of IDS. Blockchain can ensure data integrity and traceability, while AI can predict and preemptively counter emerging threats.
- Enhanced Anomaly Detection Techniques: Investing in research that improves anomaly detection algorithms to reduce false positives and adapt to network traffic’s evolving behavior can help preemptively identify potential threats. This includes developing more sophisticated behavioral analysis techniques and anomaly detection models.
- Low-Cost, Energy-Efficient Solutions: Future research should also focus on developing low-cost, energy-efficient IDS solutions that can be widely adopted, especially in developing regions and applications with significant cost constraints. This includes optimizing algorithms for minimal resource consumption and developing hardware-accelerated IDS.
- Real-Time Adaptability and Response: Future IDS systems should incorporate mechanisms for real-time adaptability and automated response to detected threats. This includes integrating ML models that can dynamically update themselves based on new attack patterns and developing automated response strategies to mitigate threats as they are detected.
8. Conclusion
References
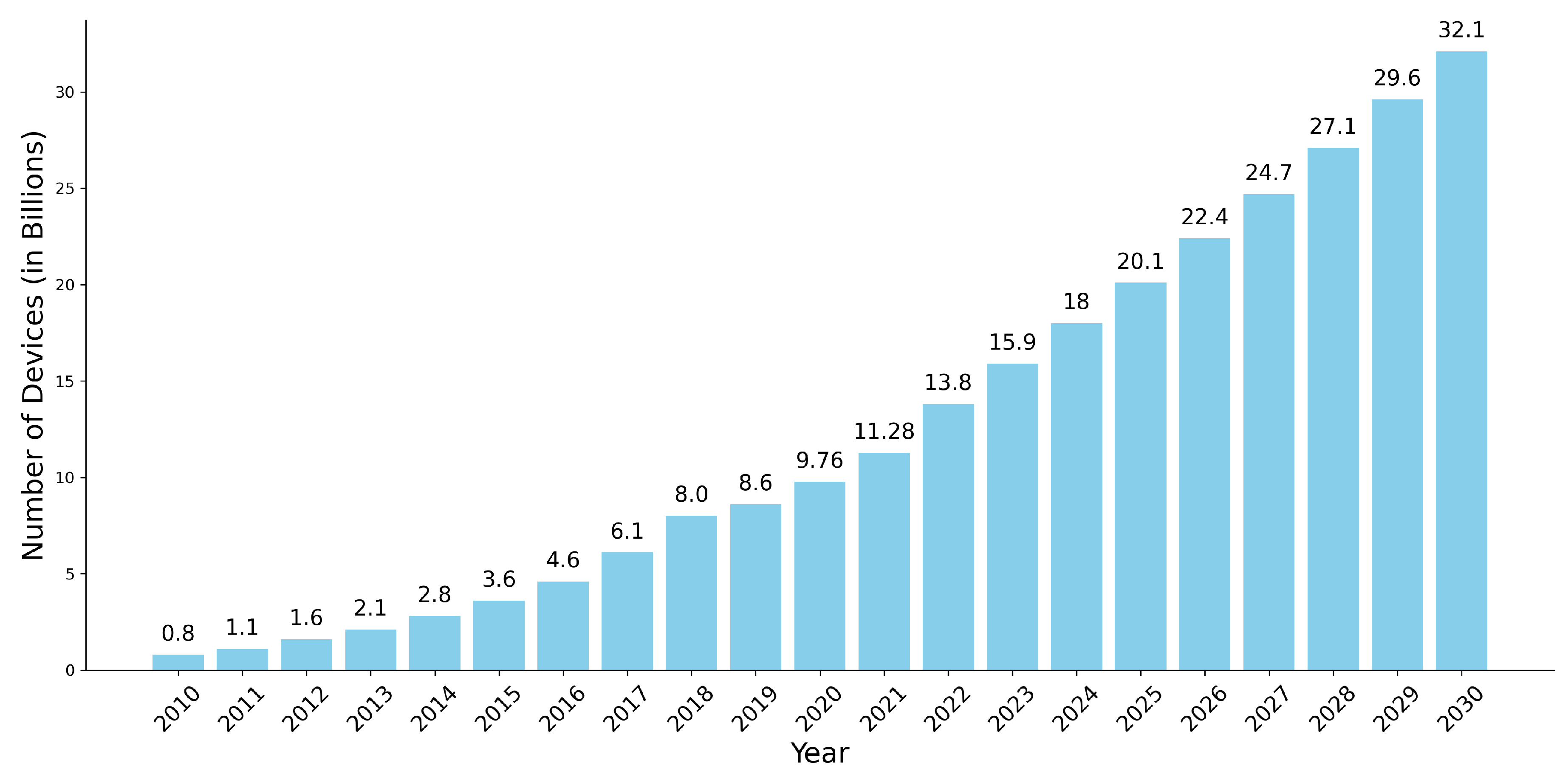
- Vailshery, L.S. Number of IoT connected devices worldwide 2022 to 2023, with forecasts from 2024 to 2033. https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/, 2022. Accessed: 2022-06-20.
- Duarte, F. Number of IoT devices. https://explodingtopics.com/blog/number-of-iot-devices, 2024. Accessed: 2024-02-19.
- Singh, H. IoT deconstructed. https://www.capgemini.com/insights/expert-perspectives/iot-deconstructed/, 2020. Accessed: 2024-02-11.
- Markets and Markets. IoT Market by Component (Hardware, Software Solutions and Services), Organization Size, Focus Area (Smart Manufacturing, Smart Energy and Utilities,and Smart Retail) and Region–Global Forecasts to 2026. https://www.marketsandmarkets.com/Market-Reports/internet-of-things-market-573.html, 2022. Accessed: 2023-10-18.
- van Kranenburg, R.; Bassi, A. IoT Challenges. Communications in Mobile Computing 2012, 1, 9. [Google Scholar] [CrossRef]
- Balaji, S.; Nathani, K.; Santhakumar, R. IoT Technology, Applications and Challenges: A Contemporary Survey. Wireless Personal Communications 2019, 108, 363–388. [Google Scholar] [CrossRef]
- Sobin, C.C. A Survey on Architecture, Protocols and Challenges in IoT. Wireless Personal Communications 2020, 112, 1383–1429. [Google Scholar] [CrossRef]
- Petrosyan, A. Increase of customers targeted by IoT malware 2022, by sector, 2023. Accessed: 2023-11-22.
- Petrosyan, A. Global annual number of IoT cyber attacks 2018-2022, 2023. Accessed: 2024-01-05.
- Staff, C. Guarding Against IoT Attacks: Strategies and Best Practices, 2024. Accessed: 2024-03-14.
- Infisim. 2024 IoT malware trends: Navigating the evolving landscape of cyber threats, 2024. Accessed: 2024-3-18.
- Daws, R. Luis Mirabal, Globalstar: Satellite IoT for increased efficiency and cost reduction, 2024. Accessed: 2024-06-15.
- TelenorIoT. AIoT to Emerge as the Defining Enabler of Digital Transformation, 2024. Accessed: 2024-02-12.
- Analytics, I. State of IoT Spring 2024, 2024. Accessed: 2024-01-03.
- Networks, P.A. 2023 Benchmark Report on IoT Security, 2023. Accessed: 2023-12-11.
- Daws, R. IoT Security Remains a Top Concern for Enterprises in 2024, 2024. Accessed: 2024-02-25.
- Dhanda, S.S.; Singh, B.; Jindal, P. Lightweight Cryptography: A Solution to Secure IoT. Wireless Personal Communications 2020, 112, 1947–1980. [Google Scholar] [CrossRef]
- Mousavi, S.K.; Ghaffari, A.; Besharat, S.; Afshari, H. Security of internet of things based on cryptographic algorithms: a survey. Wireless Networks 2021, 27, 1515–1555. [Google Scholar] [CrossRef]
- Santhosh Kumar, S.V.N.; Selvi, M.; Kannan, A. A Comprehensive Survey on Machine Learning-Based Intrusion Detection Systems for Secure Communication in Internet of Things. Computational Intelligence and Neuroscience 2023, 2023, 8981988. [Google Scholar] [CrossRef]
- Aldhaheri, A.; Alwahedi, F.; Ferrag, M.A.; Battah, A. Deep learning for cyber threat detection in IoT networks: A review. Internet of Things and Cyber-Physical Systems 2024, 4, 110–128. [Google Scholar] [CrossRef]
- Malhotra, P.; Singh, Y.; Anand, P.; Bangotra, D.K.; Singh, P.K.; Hong, W.C. Internet of Things: Evolution, Concerns and Security Challenges. Sensors 2021, 21. [Google Scholar] [CrossRef]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and Security: Challenges and Solutions. Applied Sciences 2020, 10. [Google Scholar] [CrossRef]
- Khanam, S.; Ahmedy, I.B.; Idna Idris, M.Y.; Jaward, M.H.; Bin Md Sabri, A.Q. A Survey of Security Challenges, Attacks Taxonomy and Advanced Countermeasures in the Internet of Things. IEEE Access 2020, 8, 219709–219743. [Google Scholar] [CrossRef]
- Bharati, S.; Podder, P. Machine and Deep Learning for IoT Security and Privacy: Applications, Challenges, and Future Directions. Security and Communication Networks 2022, 2022, 41. [Google Scholar] [CrossRef]
- Thakkar, A.; Lohiya, R. A survey on intrusion detection system: feature selection, model, performance measures, application perspective, challenges, and future research directions. Artificial Intelligence Review 2022, 55, 453–563. [Google Scholar] [CrossRef]
- Faiz, M.N.; Somantri, O.; Supriyono, A.R.; Wirawan, A. Impact of Feature Selection Methods on Machine Learning-based for Detecting DDoS Attacks : Literature Review. Journal of Informatics and Telecommunication Engineering 2022, 5, 305–314. [Google Scholar] [CrossRef]
- Halbouni, A.; Member, G.S. Machine Learning and Deep Learning Approaches for CyberSecurity : A Review. IEEE Access 2022, 10, 19572–19585. [Google Scholar] [CrossRef]
- Mijwil, M.; Salem, I.E.; Ismaeel, M.M. The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review. Iraqi Journal For Computer Science and Mathematics 2023, 4, 87–101. [Google Scholar] [CrossRef]
- Lyu, Y.; Feng, Y.; Sakurai, K. A Survey on Feature Selection Techniques Based on Filtering Methods for Cyber Attack Detection. Information 2023, 14. [Google Scholar] [CrossRef]
- Sarker, I.H.; Khan, A.I.; Abushark, Y.B.; Alsolami, F. Internet of Things (IoT) Security Intelligence: A Comprehensive Overview, Machine Learning Solutions and Research Directions. Mobile Networks and Applications 2023, 28, 296–312. [Google Scholar] [CrossRef]
- Sarker, I.H. Machine Learning for Intelligent Data Analysis and Automation in Cybersecurity: Current and Future Prospects. Annals of Data Science 2023, 10, 1473–1498. [Google Scholar] [CrossRef]
- Dasgupta, D.; Akhtar, Z.; Sen, S. Machine learning in cybersecurity: a comprehensive survey. The Journal of Defense Modeling and Simulation 2022, 19, 57–106. [Google Scholar] [CrossRef]
- Gyamfi, E.; Jurcut, A. Intrusion Detection in Internet of Things Systems: A Review on Design Approaches Leveraging Multi-Access Edge Computing, Machine Learning, and Datasets. Sensors 2022, 22. [Google Scholar] [CrossRef]
- Farooq, U.; Tariq, N.; Asim, M.; Baker, T.; Al-Shamma’a, A. Machine learning and the Internet of Things security: Solutions and open challenges. Journal of Parallel and Distributed Computing 2022, 162, 89–104. [Google Scholar] [CrossRef]
- Dixit, P.; Silakari, S. Deep Learning Algorithms for Cybersecurity Applications: A Technological and Status Review. Computer Science Review 2021, 39, 100317. [Google Scholar] [CrossRef]
- Adnan, A.; Muhammed, A.; Abd Ghani, A.A.; Abdullah, A.; Hakim, F. An Intrusion Detection System for the Internet of Things Based on Machine Learning: Review and Challenges. Symmetry 2021, 13. [Google Scholar] [CrossRef]
- Lansky, J.; Ali, S.; Mohammadi, M.; Majeed, M.K.; Karim, S.H.T.; Rashidi, S.; Hosseinzadeh, M.; Rahmani, A.M. Deep Learning-Based Intrusion Detection Systems: A Systematic Review. IEEE Access 2021, 9, 101574–101599. [Google Scholar] [CrossRef]
- Ahmad, Z.; Shahid Khan, A.; Wai Shiang, C.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Transactions on Emerging Telecommunications Technologies 2021, 32, e4150. [Google Scholar] [CrossRef]
- Thakkar, A.; Lohiya, R. A Review on Machine Learning and Deep Learning Perspectives of IDS for IoT: Recent Updates, Security Issues, and Challenges. Archives of Computational Methods in Engineering 2021, 28, 3211–3243. [Google Scholar] [CrossRef]
- Geetha, R.; Thilagam, T. A Review on the Effectiveness of Machine Learning and Deep Learning Algorithms for Cyber Security. Archives of Computational Methods in Engineering 2021, 28, 2861–2879. [Google Scholar] [CrossRef]
- Petticrew, M.; Roberts, H. Systematic Reviews in the Social Sciences: A Practical Guide; Blackwell Publishing, 2006. [CrossRef]
- Garcia-Teodoro, P.; Diaz-Verdejo, J.; Macia-Fernandez, G.; Vazquez, E. Anomaly-based network intrusion detection: Techniques, systems and challenges. Computers & Security 2014, 28, 18–28. [Google Scholar] [CrossRef]
- Sommer, R.; Paxson, V. Outside the Closed World: On Using Machine Learning for Network Intrusion Detection. In Proceedings of the Proceedings of the IEEE Symposium on Security and Privacy. [CrossRef]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications; 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Zuech, R.; Khoshgoftaar, T.M.; Wald, R. Intrusion detection and Big Heterogeneous Data: A Survey. Journal of Big Data 2015, 2. [Google Scholar] [CrossRef]
- Aminanto, E.; Kim, K. Deep Learning in Intrusion Detection System: An Overview 2016.
- Ahmed, M.; Mahmood, A.N.; Hu, J. A Survey of Network Anomaly Detection Techniques. Journal of Network and Computer Applications 2017, 60, 19–31. [Google Scholar] [CrossRef]
- Elnakib, O.; Shaaban, E.; Mahmoud, M.; Emara, K. EIDM: deep learning model for IoT intrusion detection systems. The Journal of Supercomputing 2023, 79, 13241–13261. [Google Scholar] [CrossRef]
- Elrawy, M.F.; Awad, A.I.; Hamed, H.F.A. Intrusion detection systems for IoT-based smart environments: a survey. Journal of Cloud Computing 2018, 7, 21. [Google Scholar] [CrossRef]
- Bhavsar, M.; Roy, K.; Kelly, J.; Olusola, O. Anomaly-based intrusion detection system for IoT application. Discover Internet of Things 2023, 3, 5. [Google Scholar] [CrossRef]
- García-Teodoro, P.; Díaz-Verdejo, J.; Maciá-Fernández, G.; Vázquez, E. Anomaly-based network intrusion detection: Techniques, systems and challenges. Computers & Security 2009, 28, 18–28. [Google Scholar] [CrossRef]
- Zeng, Y.; Qiu, M.; Zhu, D.; Xue, Z.; Xiong, J.; Liu, M. DeepVCM: A Deep Learning Based Intrusion Detection Method in VANET. In Proceedings of the 2019 IEEE 5th Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing, (HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS); 2019; pp. 288–293. [Google Scholar] [CrossRef]
- Malathi, C.; Padmaja, I.N. Identification of cyber attacks using machine learning in smart IoT networks. Materials Today: Proceedings 2023, 80, 2518–2523. [Google Scholar] [CrossRef]
- Hassan, M.M.; Gumaei, A.; Alsanad, A.; Alrubaian, M.; Fortino, G. A hybrid deep learning model for efficient intrusion detection in big data environment. Information Sciences 2020, 513, 386–396. [Google Scholar] [CrossRef]
- Xiao, G.; Li, J.; Chen, Y.; Li, K. MalFCS: An effective malware classification framework with automated feature extraction based on deep convolutional neural networks. Journal of Parallel and Distributed Computing 2020, 141, 49–58. [Google Scholar] [CrossRef]
- Dahou, A.; Abd Elaziz, M.; Chelloug, S.A.; Awadallah, M.A.; Al-Betar, M.A.; Al-qaness, M.A.A.; Forestiero, A. Intrusion Detection System for IoT Based on Deep Learning and Modified Reptile Search Algorithm. Computational Intelligence and Neuroscience 2022, 2022, 6473507. [Google Scholar] [CrossRef]
- Liang, X.; Znati, T. A Long Short-Term Memory Enabled Framework for DDoS Detection. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM); 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Pantelakis, V.; Bountakas, P.; Farao, A.; Xenakis, C. Adversarial Machine Learning Attacks on Multiclass Classification of IoT Network Traffic. In Proceedings of the Proceedings of the 18th International Conference on Availability, Reliability and Security, New York, NY, USA, 2023. [CrossRef]
- Yang, Y.; Zheng, K.; Wu, C.; Niu, X.; Yang, Y. Building an Effective Intrusion Detection System Using the Modified Density Peak Clustering Algorithm and Deep Belief Networks. Applied Sciences 2019, 9. [Google Scholar] [CrossRef]
- Alajmi, M.; Mengash, H.A.; Alqahtani, H.; Aljameel, S.S.; Hamza, M.A.; Salama, A.S. Automated Threat Detection Using Flamingo Search Algorithm With Optimal Deep Learning on Cyber-Physical System Environment. IEEE Access 2023, 11, 127669–127678. [Google Scholar] [CrossRef]
- Alamro, H.; Mahmood, K.; Aljameel, S.S.; Yafoz, A.; Alsini, R.; Mohamed, A. Modified Red Fox Optimizer With Deep Learning Enabled False Data Injection Attack Detection. IEEE Access 2023, 11, 79256–79264. [Google Scholar] [CrossRef]
- Aljebreen, M.; Alrayes, F.S.; Maray, M.; Aljameel, S.S.; Salama, A.S.; Motwakel, A. Modified Equilibrium Optimization Algorithm With Deep Learning-Based DDoS Attack Classification in 5G Networks. IEEE Access 2023, 11, 108561–108570. [Google Scholar] [CrossRef]
- Almuqren, L.; Alqahtani, H.; Aljameel, S.S.; Salama, A.S.; Yaseen, I.; Alneil, A.A. Hybrid Metaheuristics With Machine Learning Based Botnet Detection in Cloud Assisted Internet of Things Environment. IEEE Access 2023, 11, 115668–115676. [Google Scholar] [CrossRef]
- Latif, S.; Boulila, W.; Koubaa, A.; Zou, Z.; Ahmad, J. DTL-IDS: An optimized Intrusion Detection Framework using Deep Transfer Learning and Genetic Algorithm. Journal of Network and Computer Applications 2024, 221, 103784. [Google Scholar] [CrossRef]
- Soe, Y.N.; Santosa, P.I.; Hartanto, R. DDoS Attack Detection Based on Simple ANN with SMOTE for IoT Environment. In Proceedings of the 2019 Fourth International Conference on Informatics and Computing (ICIC); 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Alrashdi, I.; Alqazzaz, A.; Aloufi, E.; Alharthi, R.; Zohdy, M.; Ming, H. AD-IoT: Anomaly Detection of IoT Cyberattacks in Smart City Using Machine Learning. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC); 2019; pp. 0305–0310. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Słowińska, M.; Theodorakopoulos, G.; Burnap, P. A Supervised Intrusion Detection System for Smart Home IoT Devices. IEEE Internet of Things Journal 2019, 6, 9042–9053. [Google Scholar] [CrossRef]
- Chaudhary, P.; Gupta, B.B. DDoS Detection Framework in Resource Constrained Internet of Things Domain. In Proceedings of the 2019 IEEE 8th Global Conference on Consumer Electronics (GCCE); 2019; pp. 675–678. [Google Scholar] [CrossRef]
- Hasan, M.; Islam, M.M.; Zarif, M.I.I.; Hashem, M. Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet of Things 2019, 7, 100059. [Google Scholar] [CrossRef]
- Ioannou, C.; Vassiliou, V. Classifying Security Attacks in IoT Networks Using Supervised Learning. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS); 2019; pp. 652–658. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H.T. On the Feasibility of Deep Learning in Sensor Network Intrusion Detection. IEEE Networking Letters 2019, 1, 68–71. [Google Scholar] [CrossRef]
- Qureshi, A.S.; Khan, A.; Shamim, N.; Durad, M.H. Intrusion detection using deep sparse auto-encoder and self-taught learning. Neural Computing and Applications 2020, 32, 3135–3147. [Google Scholar] [CrossRef]
- Rezvy, S.; Luo, Y.; Petridis, M.; Lasebae, A.; Zebin, T. An efficient deep learning model for intrusion classification and prediction in 5G and IoT networks. In Proceedings of the 2019 53rd Annual Conference on Information Sciences and Systems (CISS); 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Roopak, M.; Tian, G.Y.; Chambers, J.A. Deep Learning Models for Cyber Security in IoT Networks. 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC) 2019, pp. 0452–0457.
- Verma, A.; Ranga, V. Machine Learning Based Intrusion Detection Systems for IoT Applications. Wireless Personal Communications 2020, 111, 2287–2310. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, P.; Wang, X. Intrusion Detection for IoT Based on Improved Genetic Algorithm and Deep Belief Network. IEEE Access 2019, 7, 31711–31722. [Google Scholar] [CrossRef]
- Almiani, M.; AbuGhazleh, A.; Al-Rahayfeh, A.; Atiewi, S.; Razaque, A. Deep recurrent neural network for IoT intrusion detection system. Simulation Modelling Practice and Theory 2020, 101, 102031. [Google Scholar] [CrossRef]
- Latif, S.; Zou, Z.; Idrees, Z.; Ahmad, J. A Novel Attack Detection Scheme for the Industrial Internet of Things Using a Lightweight Random Neural Network. IEEE Access 2020, 8, 89337–89350. [Google Scholar] [CrossRef]
- Li, Y.; Xu, Y.; Liu, Z.; Hou, H.; Zheng, Y.; Xin, Y.; Zhao, Y.; Cui, L. Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 2020, 154, 107450. [Google Scholar] [CrossRef]
- Roopak, M.; Tian, G.Y.; Chambers, J. An Intrusion Detection System Against DDoS Attacks in IoT Networks. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC); 2020; pp. 0562–0567. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Generation Computer Systems 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Song, H.M.; Woo, J.; Kim, H.K. In-vehicle network intrusion detection using deep convolutional neural network. Vehicular Communications 2020, 21, 100198. [Google Scholar] [CrossRef]
- Huč, A.; Trček, D. Anomaly Detection in IoT Networks: From Architectures to Machine Learning Transparency. IEEE Access 2021, 9, 60607–60616. [Google Scholar] [CrossRef]
- Kocher, G.; Kumar, G. Analysis of Machine Learning Algorithms with Feature Selection for Intrusion Detection Using UNSW-NB15 Dataset 2021. 13. [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R. Toward Design of an Intelligent Cyber Attack Detection System using Hybrid Feature Reduced Approach for IoT Networks. Arabian Journal for Science and Engineering 2021, 46, 3749–3778. [Google Scholar] [CrossRef]
- Rahman, M.A.; Asyhari, A.T.; Wen, O.W.; Ajra, H.; Ahmed, Y.; Anwar, F. Effective combining of feature selection techniques for machine learning-enabled IoT intrusion detection. Multimedia Tools and Applications 2021, 80, 31381–31399. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. A Framework for Anomaly Detection in IoT Networks Using Conditional Generative Adversarial Networks. IEEE Access 2021, 9, 165907–165931. [Google Scholar] [CrossRef]
- Albulayhi, K.; Abu Al-Haija, Q.; Alsuhibany, S.A.; Jillepalli, A.A.; Ashrafuzzaman, M.; Sheldon, F.T. IoT Intrusion Detection Using Machine Learning with a Novel High Performing Feature Selection Method. Applied Sciences 2022, 12. [Google Scholar] [CrossRef]
- Alghamdi, M.I. A Hybrid Model for Intrusion Detection in IoT Applications. Wireless Communications and Mobile Computing 2022, 2022, 4553502. [Google Scholar] [CrossRef]
- Adefemi Alimi, K.O.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S.; Alimi, O.A. Refined LSTM Based Intrusion Detection for Denial-of-Service Attack in Internet of Things. Journal of Sensor and Actuator Networks 2022, 11. [Google Scholar] [CrossRef]
- Banaamah, A.M.; Ahmad, I. Intrusion Detection in IoT Using Deep Learning. Sensors 2022, 22. [Google Scholar] [CrossRef] [PubMed]
- Dat-Thinh, N.; Xuan-Ninh, H.; Kim-Hung, L. MidSiot: A Multistage Intrusion Detection System for Internet of Things. Wireless Communications and Mobile Computing 2022, 2022, 9173291. [Google Scholar] [CrossRef]
- EMEC, M.; OZCANHAN, M.H. A Hybrid Deep Learning Approach for Intrusion Detection in IoT Networks. Advances in Electrical and Computer Engineering 2022, 22, 3–12. [Google Scholar] [CrossRef]
- Le, K.H.; Nguyen, M.H.; Tran, T.D.; Tran, N.D. IMIDS: An Intelligent Intrusion Detection System against Cyber Threats in IoT. Electronics 2022, 11. [Google Scholar] [CrossRef]
- Nguyen, X.H.; Nguyen, X.D.; Huynh, H.H.; Le, K.H. Realguard: A Lightweight Network Intrusion Detection System for IoT Gateways. Sensors 2022, 22. [Google Scholar] [CrossRef]
- Otoum, Y.; Liu, D.; Nayak, A. DL-IDS: a deep learning–based intrusion detection framework for securing IoT. Transactions on Emerging Telecommunications Technologies 2022, 33, e3803. [Google Scholar] [CrossRef]
- Raghuvanshi, A.; Singh, U.K.; Sajja, G.S.; Pallathadka, H.; Asenso, E.; Kamal, M.; Singh, A.; Phasinam, K. Intrusion Detection Using Machine Learning for Risk Mitigation in IoT-Enabled Smart Irrigation in Smart Farming. Journal of Food Quality 2022, 2022, 3955514. [Google Scholar] [CrossRef]
- Rani, D.; Gill, N.S.; Gulia, P.; Chatterjee, J.M. An Ensemble-Based Multiclass Classifier for Intrusion Detection Using Internet of Things. Computational Intelligence and Neuroscience 2022, 2022, 1668676. [Google Scholar] [CrossRef]
- Kayode Saheed, Y.; Idris Abiodun, A.; Misra, S.; Kristiansen Holone, M.; Colomo-Palacios, R. A machine learning-based intrusion detection for detecting internet of things network attacks. Alexandria Engineering Journal 2022, 61, 9395–9409. [Google Scholar] [CrossRef]
- Ullah, S.; Ahmad, J.; Khan, M.A.; Alkhammash, E.H.; Hadjouni, M.; Ghadi, Y.Y.; Saeed, F.; Pitropakis, N. A New Intrusion Detection System for the Internet of Things via Deep Convolutional Neural Network and Feature Engineering. Sensors 2022, 22. [Google Scholar] [CrossRef] [PubMed]
- Vishwakarma, M.; Kesswani, N. DIDS: A Deep Neural Network based real-time Intrusion detection system for IoT. Decision Analytics Journal 2022, 5, 100142. [Google Scholar] [CrossRef]
- Alrowais, F.; Althahabi, S.; Alotaibi, S.S.; Mohamed, A.; Hamza, M.A.; Marzouk, R. Automated Machine Learning Enabled Cybersecurity Threat Detection in Internet of Things Environment. Computer Systems Science and Engineering 2023, 45, 687–700. [Google Scholar] [CrossRef]
- Basati, A.; Faghih, M.M. DFE: efficient IoT network intrusion detection using deep feature extraction. Neural Computing and Applications 2022, 34, 15175–15195. [Google Scholar] [CrossRef]
- Gupta, L.; Salman, T.; Ghubaish, A.; Unal, D.; Al-Ali, A.K.; Jain, R. Cybersecurity of multi-cloud healthcare systems: A hierarchical deep learning approach. Applied Soft Computing 2022, 118, 108439. [Google Scholar] [CrossRef]
- Kaushik, S.; Bhardwaj, A.; Alomari, A.; Bharany, S.; Alsirhani, A.; Mujib Alshahrani, M. Efficient, Lightweight Cyber Intrusion Detection System for IoT Ecosystems Using MI2G Algorithm. Computers 2022, 11. [Google Scholar] [CrossRef]
- Sarwar, A.; Alnajim, A.M.; Marwat, S.N.K.; Ahmed, S.; Alyahya, S.; Khan, W.U. Enhanced Anomaly Detection System for IoT Based on Improved Dynamic SBPSO. Sensors 2022, 22. [Google Scholar] [CrossRef]
- Aldhyani, T.H.H.; Alkahtani, H. Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors 2022, 22. [Google Scholar] [CrossRef]
- Abdulameer, H.; Musa, I.; Al-Sultani, N. Three level intrusion detection system based on conditional generative adversarial network 2023. 13. [CrossRef]
- Gad, A.R.; Haggag, M.; Nashat, A.A.; Barakat, T.M. A Distributed Intrusion Detection System using Machine Learning for IoT based on ToN-IoT Dataset. International Journal of Advanced Computer Science and Applications 2022, 13. [Google Scholar] [CrossRef]
- Moody Alhanaya, K.H.A.A.S. Performance Analysis of Intrusion Detection System in the IoT Environment Using Feature Selection Technique. Intelligent Automation & Soft Computing 2023, 36, 3709–3724. [Google Scholar] [CrossRef]
- Alrowais, F.; Eltahir, M.M.; Aljameel, S.S.; Marzouk, R.; Mohammed, G.P.; Salama, A.S. Modeling of Botnet Detection Using Chaotic Binary Pelican Optimization Algorithm With Deep Learning on Internet of Things Environment. IEEE Access 2023, 11, 130618–130626. [Google Scholar] [CrossRef]
- Ashraf, S.N.; Manickam, S.; Zia, S.S.; Abro, A.A.; Obaidat, M.; Uddin, M.; Abdelhaq, M.; Alsaqour, R. IoT empowered smart cybersecurity framework for intrusion detection in internet of drones. Scientific Reports 2023, 13, 18422. [Google Scholar] [CrossRef]
- Jithish, J.; Alangot, B.; Mahalingam, N.; Yeo, K.S. Distributed Anomaly Detection in Smart Grids: A Federated Learning-Based Approach. IEEE Access 2023, 11, 7157–7179. [Google Scholar] [CrossRef]
- Lai, T.; Farid, F.; Bello, A.; Sabrina, F. Ensemble learning based anomaly detection for IoT cybersecurity via Bayesian hyperparameters sensitivity analysis. Cybersecurity 2024, 7, 44. [Google Scholar] [CrossRef]
- Lopez, M.M.; Shao, S.; Hariri, S.; Salehi, S. Machine Learning for Intrusion Detection: Stream Classification Guided by Clustering for Sustainable Security in IoT. In Proceedings of the Proceedings of the Great Lakes Symposium on VLSI 2023, New York, NY, USA, 2023. [CrossRef]
- Sarwar, N.; Bajwa, I.S.; Hussain, M.Z.; Ibrahim, M.; Saleem, K. IoT Network Anomaly Detection in Smart Homes Using Machine Learning. IEEE Access 2023, 11, 119462–119480. [Google Scholar] [CrossRef]
- Shtayat, M.M.; Hasan, M.K.; Sulaiman, R.; Islam, S.; Khan, A.U.R. An Explainable Ensemble Deep Learning Approach for Intrusion Detection in Industrial Internet of Things. IEEE Access 2023, 11, 115047–115061. [Google Scholar] [CrossRef]
- Usoh, M.; Asuquo, P.; Ozuomba, S.; Stephen, B.; Inyang, U. A hybrid machine learning model for detecting cybersecurity threats in IoT applications. International Journal of Information Technology 2023, 15, 3359–3370. [Google Scholar] [CrossRef]
- Zakariyya, I.; Kalutarage, H.; Al-Kadri, M.O. Towards a robust, effective and resource efficient machine learning technique for IoT security monitoring. Computers & Security 2023, 133, 103388. [Google Scholar] [CrossRef]
- Alazab, M.; Awajan, A.; Alazzam, H.; Wedyan, M.; Alshawi, B.; Alturki, R. A Novel IDS with a Dynamic Access Control Algorithm to Detect and Defend Intrusion at IoT Nodes. Sensors 2024, 24. [Google Scholar] [CrossRef]
- Hazman, C.; Guezzaz, A.; Benkirane, S.; Azrour, M. Enhanced IDS with Deep Learning for IoT-Based Smart Cities Security. Tsinghua Science and Technology 2024, 29, 929–947. [Google Scholar] [CrossRef]
- Karthikeyan, M.; Manimegalai, D.; RajaGopal, K. Firefly algorithm based WSN-IoT security enhancement with machine learning for intrusion detection. Scientific Reports 2024, 14, 231. [Google Scholar] [CrossRef] [PubMed]
- Yaras, S.; Dener, M. IoT-Based Intrusion Detection System Using New Hybrid Deep Learning Algorithm. Electronics 2024, 13. [Google Scholar] [CrossRef]
- Sun, Z.; An, G.; Yang, Y.; Liu, Y. Optimized machine learning enabled intrusion detection 2 system for internet of medical things. Franklin Open 2024, 6, 100056. [Google Scholar] [CrossRef]
- Morshedi, R.; Matinkhah, S.M.; Sadeghi, M.T. Intrusion Detection for IoT Network Security with Deep learning. Journal of AI and Data Mining 2024, 12, 37–55. [Google Scholar] [CrossRef]
- Kilichev, D.; Turimov, D.; Kim, W. Next–Generation Intrusion Detection for IoT EVCS: Integrating CNN, LSTM, and GRU Models. Mathematics 2024, 12. [Google Scholar] [CrossRef]
- Ayoob Almotairi, Samer Atawneh, O. A.K.; Khafajah, N.M. Enhancing intrusion detection in IoT networks using machine learning-based feature selection and ensemble models. Systems Science & Control Engineering 2024, 12, 2321381. [Google Scholar] [CrossRef]
- Hou, S.; Huang, X. Use of Machine Learning in Detecting Network Security of Edge Computing System. In Proceedings of the 2019 IEEE 4th International Conference on Big Data Analytics (ICBDA); 2019; pp. 252–256. [Google Scholar] [CrossRef]
- Ren, K.; Zeng, Y.; Zhong, Y.; Sheng, B.; Zhang, Y. MAFSIDS: a reinforcement learning-based intrusion detection model for multi-agent feature selection networks. Journal of Big Data 2023, 10, 137. [Google Scholar] [CrossRef]
- Alalhareth, M.; Hong, S.C. An Improved Mutual Information Feature Selection Technique for Intrusion Detection Systems in the Internet of Medical Things. Sensors 2023, 23. [Google Scholar] [CrossRef]
- Woo, J.; Song, J.Y.; Choi, Y.J. Performance Enhancement of Deep Neural Network Using Feature Selection and Preprocessing for Intrusion Detection. 2019 International Conference on Artificial Intelligence in Information and Communication (ICAIIC).
- Kasongo, S.M.; Sun, Y. A Deep Long Short-Term Memory based classifier for Wireless Intrusion Detection System. ICT Express 2020, 6, 98–103. [Google Scholar] [CrossRef]
- Wirawan Muhammad, A.; Feresa Mohd Foozy, C. ; Azhari, A. Machine Learning-Based Distributed Denial of Service Attack Detection on Intrusion Detection System Regarding to Feature Selection. International Journal Of Artificial Intelligence Research 2020, 4, 1–8. [Google Scholar] [CrossRef]
- Maslan, A.; Mohamad, K.M.B.; Feresa, B.M.F. Feature selection for DDoS detection using classification machine learning techniques. IAES International Journal of Artificial Intelligence (IJ-AI) 2020, 9, 137–145. [Google Scholar] [CrossRef]
- Taher, K.A.; Mohammed Yasin Jisan, B.; Rahman, M.M. Network Intrusion Detection using Supervised Machine Learning Technique with Feature Selection. In Proceedings of the 2019 International Conference on Robotics,Electrical and Signal Processing Techniques (ICREST); 2019; pp. 643–646. [Google Scholar] [CrossRef]
- Kasongo, S.M.; Sun, Y. A deep learning method with wrapper based feature extraction for wireless intrusion detection system. Computers & Security 2020, 92, 101752. [Google Scholar] [CrossRef]
- Khammassi, C.; Krichen, S. A NSGA2-LR wrapper approach for feature selection in network intrusion detection. Computer Networks 2020, 172, 107183. [Google Scholar] [CrossRef]
- Sarker, I.H.; Abushark, Y.B.; Alsolami, F.; Khan, A.I. IntruDTree: A Machine Learning Based Cyber Security Intrusion Detection Model. Symmetry 2020, 12. [Google Scholar] [CrossRef]
- Yu, Y.; Bian, N. An Intrusion Detection Method Using Few-Shot Learning. IEEE Access 2020, 8, 49730–49740. [Google Scholar] [CrossRef]
- Alsirhani, A.; Mujib Alshahrani, M.; Hassan, A.M.; Taloba, A.I.; Abd El-Aziz, R.M.; Samak, A.H. Implementation of African vulture optimization algorithm based on deep learning for cybersecurity intrusion detection. Alexandria Engineering Journal 2023, 79, 105–115. [Google Scholar] [CrossRef]
- Al-Daweri, M.S.; Zainol Ariffin, K.A.; Abdullah, S.; Md. Senan, M.F.E. An Analysis of the KDD99 and UNSW-NB15 Datasets for the Intrusion Detection System. Symmetry 2020, 12. [Google Scholar] [CrossRef]
- Saraeian, S.; Golchi, M.M. Application of Deep Learning Technique in an Intrusion Detection System. International Journal of Computational Intelligence and Applications 2020, 19, 2050016. [Google Scholar] [CrossRef]
- Zhang, J.; Ling, Y.; Fu, X.; Yang, X.; Xiong, G.; Zhang, R. Model of the intrusion detection system based on the integration of spatial-temporal features. Computers & Security 2020, 89, 101681. [Google Scholar] [CrossRef]
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23. [Google Scholar] [CrossRef] [PubMed]
- Ferrag, M.A. , Friha, O., Hamouda, D., Maglaras, L., Janicke, H.: Edge-IIoTset: A New Comprehensive Realistic Cyber Security Dataset of IoT and IIoT Applications: Centralized and Federated Learning. [CrossRef]
- Zolanvari, M.; Teixeira, M.A.; Gupta, L.; Khan, K.M.; Jain, R. WUSTL-IIOT-2021 Dataset for IIoT Cybersecurity Research, 2021.
- Ullah, I.; Mahmoud, Q.H. A Scheme for Generating a Dataset for Anomalous Activity Detection in IoT Networks. In Proceedings of the Advances in Artificial Intelligence; Goutte, C.; Zhu, X., Eds., Cham; 2020; pp. 508–520. [Google Scholar]
- Hindy, H. , Tachtatzis, C., Atkinson, R., Bayne, E., Bellekens, X.: MQTT-IoT-IDS2020: MQTT Internet of Things Intrusion Detection Dataset. [CrossRef]
- Moustafa, N. New Generations of Internet of Things Datasets for Cybersecurity Applications based Machine Learning: TON_IoT Datasets. In Proceedings of the Proceedings of the eResearch Australasia Conference, Brisbane, Australia; 2019. [Google Scholar]
- Garcia, S. , Parmisano, A., Erquiaga, M.J.: IoT-23: A Labeled Dataset with Malicious and Benign IoT Network Traffic. [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. B: the Development of Realistic Botnet Dataset in the Internet of Things for Network Forensic Analytics, 2018; arXiv:cs.CR/1811.00701].
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization. In Proceedings of the International Conference on Information Systems Security and Privacy; 2018. [Google Scholar]
- Aubet, F.; Pahl, M. DS2OS traffic traces, 2018.
- Mirsky, Y.; Doitshman, T.; Elovici, Y.; Shabtai, A. Kitsune: An Ensemble of Autoencoders for Online Network Intrusion Detection. In Proceedings of the The Network and Distributed System Security Symposium (NDSS) 2018, 2018. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Shabtai, A.; Breitenbacher, D.; Elovici, Y. N-BaIoT—Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders. IEEE Pervasive Computing 2018, 17, 12–22. [Google Scholar] [CrossRef]
- Ring, M.; Wunderlich, S.; Grüdl, D.; Landes, D.; Hotho, A. Creation of Flow-Based Data Sets for Intrusion Detection. Journal of Information Warfare 2017, 16, 40–53. [Google Scholar]
- Jazi, H.H.; Gonzalez, H.; Stakhanova, N.; Ghorbani, A.A. Detecting HTTP-based application layer DoS attacks on web servers in the presence of sampling. Computer Networks 2017, 121, 25–36. [Google Scholar] [CrossRef]
- Rabbani, M.; Rankothge, W. Enhancing Generalizability in DDoS Attack Detection Systems through Transfer Learning and Ensemble Learning Approaches. Webinar presented at the Canadian Institute for Cybersecurity, 2023. Q&A session with Dr. Windhya Rankothge included. [Google Scholar]
- Moustafa, N.; Slay, J. UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS); 2015; pp. 1–6. [Google Scholar] [CrossRef]
- García, S.; Grill, M.; Stiborek, J.; Zunino, A. An empirical comparison of botnet detection methods. Computers & Security 2014, 45, 100–123. [Google Scholar] [CrossRef]
- Shiravi, A.; Shiravi, H.; Tavallaee, M.; Ghorbani, A.A. Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Computers & Security 2012, 31, 357–374. [Google Scholar] [CrossRef]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications; 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Takakura, H. : Kyoto 2006+ Dataset. Data collection period: November 2006 to December 2015, Popularity Rank: 56. [CrossRef]
- Repository, U.M.L. KDD Cup 99 Data Set. Online, 1999.
- Zhang, H.; Huang, L.; Wu, C.Q.; Li, Z. An effective convolutional neural network based on SMOTE and Gaussian mixture model for intrusion detection in imbalanced dataset. Computer Networks 2020, 177, 107315. [Google Scholar] [CrossRef]
| Review Article | Year | Systematic Study |
IoT Focused |
ML | DL | Feature Selection |
Data Imbalance |
|---|---|---|---|---|---|---|---|
| Mijwil et al. [28] | 2023 | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ |
| Lyu et al. [29] | 2023 | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ |
| Sarker et al. [30] | 2023 | ✗ | ✓ | ✓ * | ✓ * | ✓ | ✗ |
| Sarker [31] | 2023 | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ |
| Dasgupta et al. [32] | 2022 | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ |
| Halbouni et al. [27] | 2022 | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ |
| Gyamfi et al. [33] | 2022 | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ |
| Farooq et al. [34] | 2022 | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ |
| Faiz et al. [26] | 2022 | ✗ | ✗ | ✓ | ✗ | ✓ * | ✗ |
| Bharati et al. [24] | 2022 | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ |
| Dixit et al. [35] | 2021 | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ |
| Adnan et al. [36] | 2021 | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ |
| Lansky et al. [37] | 2021 | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ |
| Ahmad et al. [38] | 2021 | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ |
| Thakkar et al. [39] | 2021 | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ |
| Geetha et al. [40] | 2021 | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ |
| This Systematic Review | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| *Discussed but not in detail. | |||||||
| S.No | Research Question | Research Objective |
|---|---|---|
| 1 | What are the prevalent types of cyberattacks targeting IoT devices, and what makes securing IoT ecosystems inherently challenging? | To study the spectrum of cyberattacks on IoT devices and understand the inherent challenges of securing IoT ecosystems. |
| 2 | What countermeasures are currently employed to safeguard IoT networks? | To explore the current strategies and technologies for IoT security, specifically focusing on the effectiveness and role of IDS in mitigating these threats. |
| 3 | Which ML and DL methodologies are currently applied in IDS, especially for IoT networks, and what are their associated challenges? | To identify and assess the ML and DL techniques utilized in IDS, highlighting their effectiveness and the challenges they face, particularly in IoT networks |
| 4 | What datasets are predominantly utilized for evaluating ML or DL-based IDS, and how are issues of data imbalance addressed within these datasets? | To investigate the security datasets frequently used for testing ML or DL-based IDS in both general and IoT-specific networks and to understand the methodologies implemented to tackle issues of data imbalance. |
| 5 | What feature selection strategies are employed in preparing datasets for IDS, and how do they contribute to developing lightweight IDS solutions? | To examine the feature selection strategies applied in preprocessing IDS datasets for IoT, identifying their contributions to the development of efficient and lightweight IDS models. |
| 6 | What are the emerging trends and future research directions for AI-powered lightweight IDS solutions in the IoT domain? | To identify emerging trends and future research directions in developing AI-powered lightweight IDS solutions for IoT ecosystems. |
| S.No | Keywords |
|---|---|
| 1 | Intrusion Detection System |
| 2 | Internet of Things |
| 3 | Security |
| 4 | Cyber Security |
| 5 | Network Security |
| 6 | Machine Learning |
| 7 | Deep Learning |
| 8 | Lightweight Intrusion Detection System |
| 9 | Feature Selection |
| 10 | Data (Im)Balance |
| Search Engine | Filters |
|---|---|
| IEEE Xplore | Publication Years: 2019 to 2024 |
| Springer | Article Type: Research Articles or Conference Proceedings |
| ScienceDirect | Language: English |
| Google Scholar | |
| ResearchGate |
| Reference | ML | DL | Algorithms |
| [65] | ✗ | ✓ | ANN |
| [59] | ✗ | ✓ | DBN |
| [66] | ✓ | ✗ | RF |
| [67] | ✓ | ✓ | NB, BN, DT, LR, SVM, RF, MLP |
| [68] | ✓ | ✗ | SVM, RF, LR, DT |
| [69] | ✓ | ✓ | LR, SVM, DT, RF, ANN |
| [70] | ✓ | ✗ | SVM |
| [71] | ✓ | ✗ | RBM Based Clustering |
| [72] | ✗ | ✓ | AE |
| [73] | ✗ | ✓ | DNN |
| [74] | ✗ | ✓ | MLP, CNN, LSTM |
| [75] | ✓ | ✓ | RF, AdaBoost, GBM, XGB, ETC, DT, MLP |
| [52] | ✗ | ✓ | CNN, LSTM |
| [76] | ✗ | ✓ | DBN |
| [77] | ✗ | ✓ | RNN |
| [78] | ✗ | ✓ | RaNN |
| [79] | ✗ | ✓ | CNN |
| [80] | ✗ | ✓ | CNN, LSTM |
| [81] | ✓ | ✗ | NB, BN, DT, RF, RT |
| [82] | ✗ | ✓ | DCNN |
| [83] | ✓ | ✗ | BIRCH |
| [84] | ✓ | ✗ | kNN, SGD, RF, LR, NB |
| [85] | ✓ | ✗ | RF, kNN, XGB |
| [86] | ✗ | ✓ | ANN |
| [87] | ✗ | ✓ | CGAN |
| [88] | ✓ | ✓ | Bagging, DT, kNN, MLP |
| [89] | ✗ | ✓ | CFNN |
| [90] | ✗ | ✓ | LSTM |
| [91] | ✗ | ✓ | CNN, LSTM, GRU |
| [56] | ✗ | ✓ | CNN |
| [92] | ✓ | ✓ | SVM, kNN, LDA, QDA, DT, MLP, LSTM, AE |
| [93] | ✗ | ✓ | BiLSTM, GRU |
| [94] | ✗ | ✓ | CNN |
| [95] | ✗ | ✓ | DNN |
| [96] | ✗ | ✓ | SDPN |
| [97] | ✓ | ✗ | SVM, LR, RF |
| [98] | ✓ | ✗ | RF, XGB, LGBM, CatBoost |
| [99] | ✓ | ✗ | XGB, CatBoost, kNN, SVM, QDA, NB |
| [100] | ✗ | ✓ | DCNN |
| [101] | ✗ | ✓ | DNN |
| [102] | ✓ | ✗ | RELM |
| [103] | ✗ | ✓ | CNN |
| [104] | ✗ | ✓ | ANN |
| [105] | ✓ | ✗ | LR, LDA, NB, DT, RF, SVM, GBM |
| [106] | ✓ | ✗ | RF |
| [107] | ✗ | ✓ | CNN, LSTM |
| [108] | ✓ | ✓ | SVM, NB, CGAN |
| [109] | ✓ | ✗ | kNN, XGB, DT, RF |
| [60] | ✗ | ✓ | MESNN |
| [110] | ✓ | ✗ | LR, DT, RF, NB, kNN, SVM |
| [63] | ✗ | ✓ | CNN, QRNN |
| [111] | ✗ | ✓ | CVAE |
| [112] | ✓ | ✓ | LR, DT, RF, NB, GRU, RNN, LSTM, BiLSTM |
| [113] | ✓ | ✓ | LR, FFNN, CNN, AE, Vanilla RNN, LSTM, GRU |
| [114] | ✓ | ✗ | Ensemble Learning |
| [115] | ✓ | ✓ | LR, SVM, MLP |
| [53] | ✓ | ✓ | Adaboost, NB, kNN, QDA, DT, RF, MLP |
| [58] | ✓ | ✓ | RF, DT, kNN, MLP |
| [116] | ✓ | ✓ | Adaboost, DT, RF, ANN, LSTM, AE |
| [117] | ✗ | ✓ | CNN |
| [118] | ✓ | ✗ | An Ensemble of RF, XG, kNN, DT |
| [119] | ✗ | ✓ | REDNN, REFDNN |
| [120] | ✗ | ✓ | LSTM |
| [121] | ✗ | ✓ | LSTM |
| [122] | ✓ | ✗ | SVM |
| [123] | ✗ | ✓ | CNN, LSTM |
| [64] | ✗ | ✓ | Deep Transfer Learning with GA |
| [124] | ✓ | ✗ | Adaboost, kNN, NB |
| [125] | ✗ | ✓ | CNN, LSTM |
| [126] | ✗ | ✓ | CNN, LSTM, GRU |
| [127] | ✓ | ✗ | NB, RF, kNN, SVM |
| Dataset | Year | IoT Specific? |
|---|---|---|
| CICIoT2023 [144] | 2023 | ✓ |
| EDGE-IIOTSET [145] | 2022 | ✓ |
| WUSTL-IIOT-2021 [146] | 2021 | ✓ |
| IOTID20 [147] | 2020 | ✓ |
| MQTT-IoT-IDS2020 [148] | 2020 | ✓ |
| TON-IoT [149] | 2020 | ✓ |
| IoT-23 [150] | 2019 | ✓ |
| BoT-IoT [151] | 2018 | ✓ |
| CSE-CICDIS2018 [152] | 2018 | ✗ |
| DS2OS [153] | 2018 | ✗ |
| Kitsune Network Attack Dataset [154] | 2018 | ✗ |
| N-BAIOT [155] | 2018 | ✓ |
| CIDDS001 [156] | 2017 | ✗ |
| CICDoS (2017) [157] | 2017 | ✗ |
| CIC-IDS2017 [158] | 2017 | ✗ |
| UNSW-NB15 [159] | 2015 | ✗ |
| CTU-13 [160] | 2013 | ✗ |
| ISCXIDS2012 [161] | 2012 | ✗ |
| ISCX NSL-KDD [162] | 2009 | ✗ |
| Kyoto 2006+ [163] | 2006 | ✗ |
| KDDCup99 [164] | 1999 | ✗ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





