Submitted:
11 April 2024
Posted:
11 April 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- ✓ To meticulously identify and analyse the myriad cybersecurity threats confronting fintech companies, encompassing both traditional and emerging risks.
- ✓ To delve into the intricate regulatory landscape governing the fintech sector, discerning its nuances and assessing its profound impact on cybersecurity practices.
- ✓ To critically evaluate the efficacy of existing cybersecurity measures implemented by fintech organizations, gauging their effectiveness in mitigating threats and safeguarding sensitive financial data.
- ✓ To formulate practical and actionable recommendations tailored to bolster cybersecurity and enhance data privacy standards within the dynamic fintech ecosystem.
- ✓ By shedding light on the evolving cybersecurity risks within the financial industry, this study illuminates the shifting threat landscape and underscores the imperative for proactive risk management strategies.
- ✓ Through an in-depth exploration of the regulatory framework, this research elucidates the intricate interplay between regulatory mandates and cybersecurity practices, offering valuable insights into compliance requirements and governance considerations for fintech entities.
- ✓ By offering actionable suggestions for enhancing cybersecurity posture, this study empowers fintech companies to fortify their defences and proactively mitigate cyber threats, thereby bolstering resilience and trust in the digital financial ecosystem.
- ✓ As a scholarly contribution, this research enriches the existing body of knowledge on the convergence of fintech, cybersecurity, and data privacy, advancing understanding and informing future research endeavours in this burgeoning field.
- ✓ What are the predominant challenges and vulnerabilities confronting fintech organizations in terms of cybersecurity, and how have these threats evolved over time?
- ✓ How does the regulatory landscape, including compliance requirements and regulatory frameworks, influence cybersecurity practices and risk management strategies within the fintech sector?
- ✓ To what extent are the existing cybersecurity measures adopted by fintech companies effective in mitigating cyber risks and safeguarding sensitive financial information?
Literature Review
- How to secure the infrastructure.
- How to secure and control devices.
- How to secure of local and global networks, as well as securing and protecting the perimeter.
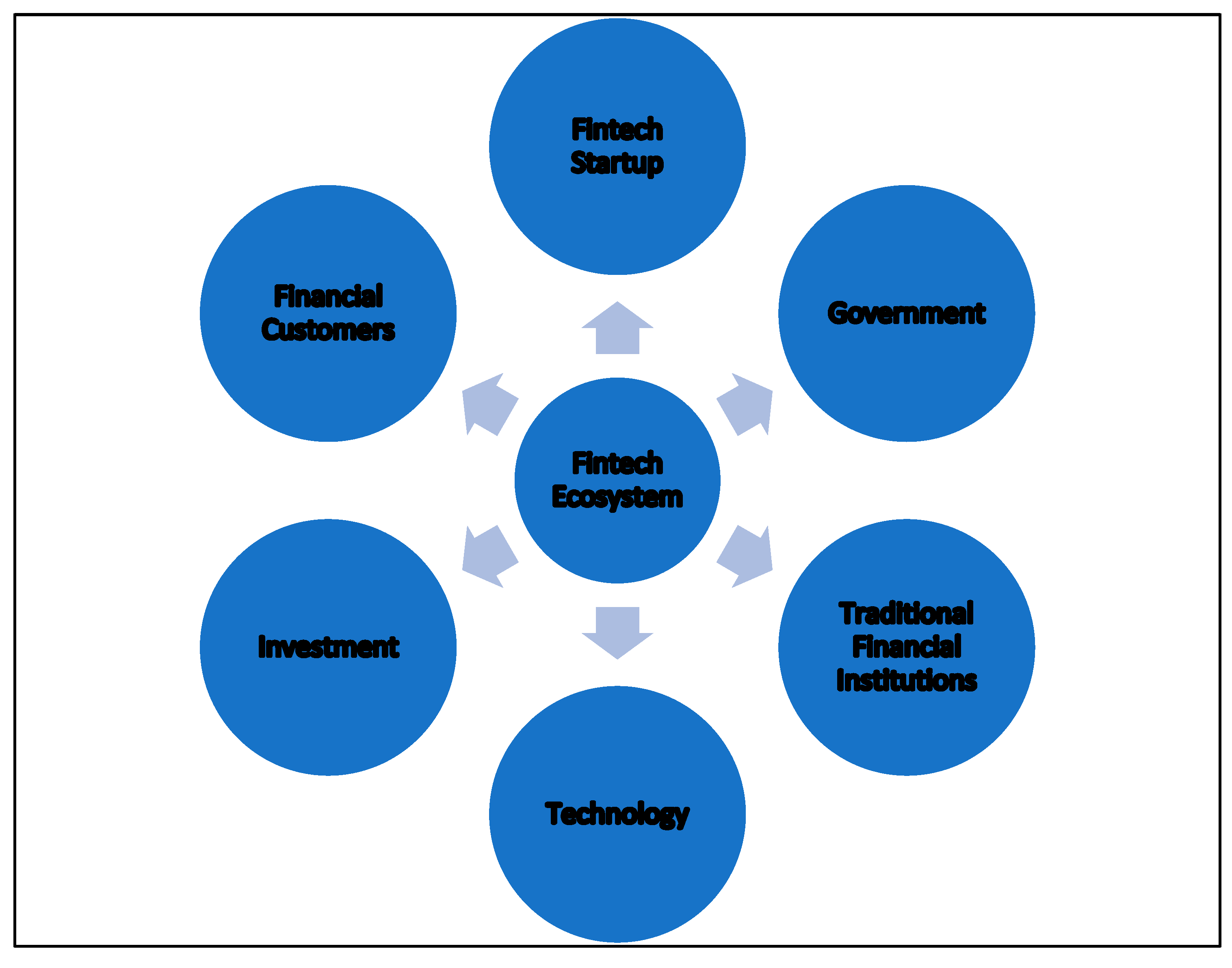
Cybersecurity and Data Privacy Solutions
- Encryption: Encrypting sensitive data in transit and at rest using solid algorithms like AES and RSA can significantly increase its security (Kavitha et al., 2022). Encryption helps to ensure that even if the data is accessed, it cannot be understood without the proper decryption key.
- Authentication: Implementing multi-factor authentication (MFA) protocols beyond traditional passwords can further strengthen access security. It may include biometric authentication, one-time passwords, or hardware tokens.
- Security Assessments: Regularly conducting penetration testing and vulnerability scanning helps identify and address security gaps before attackers can exploit them. Security assessments can also include risk assessments and security audits to evaluate the effectiveness of existing security measures.
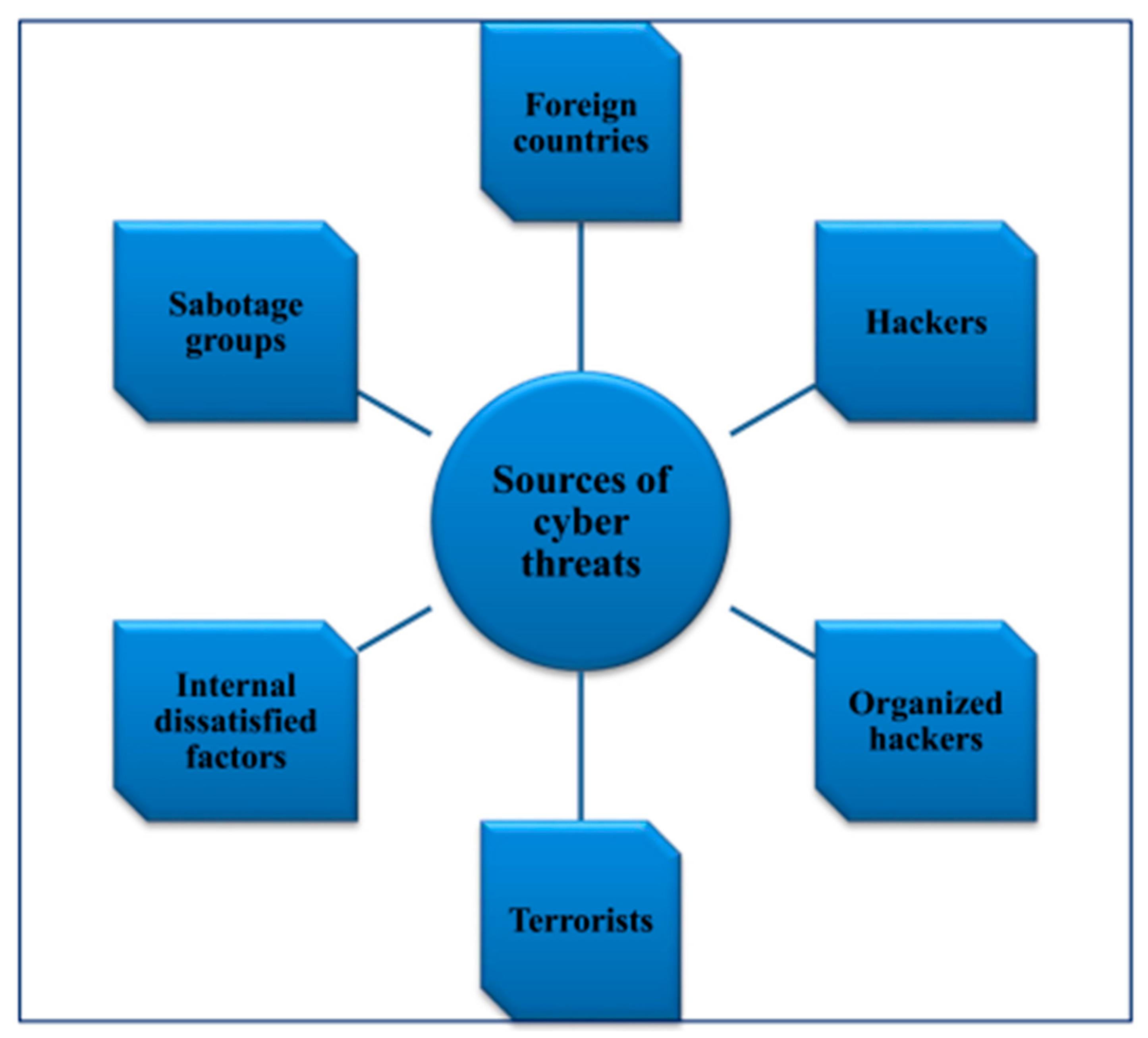
Common Cyber Security Threats for the Fintech
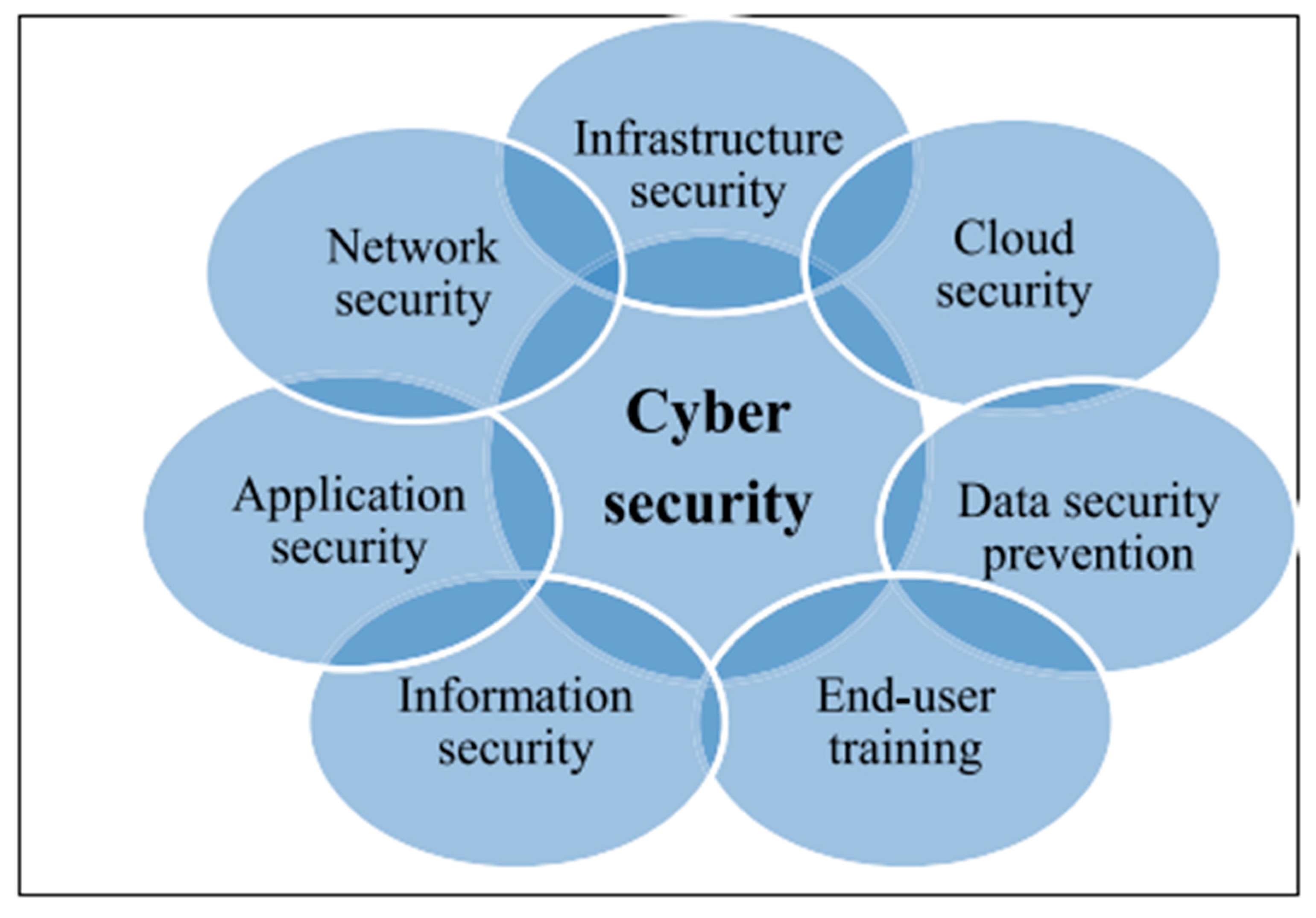
Solutions
2. Materials and Methods
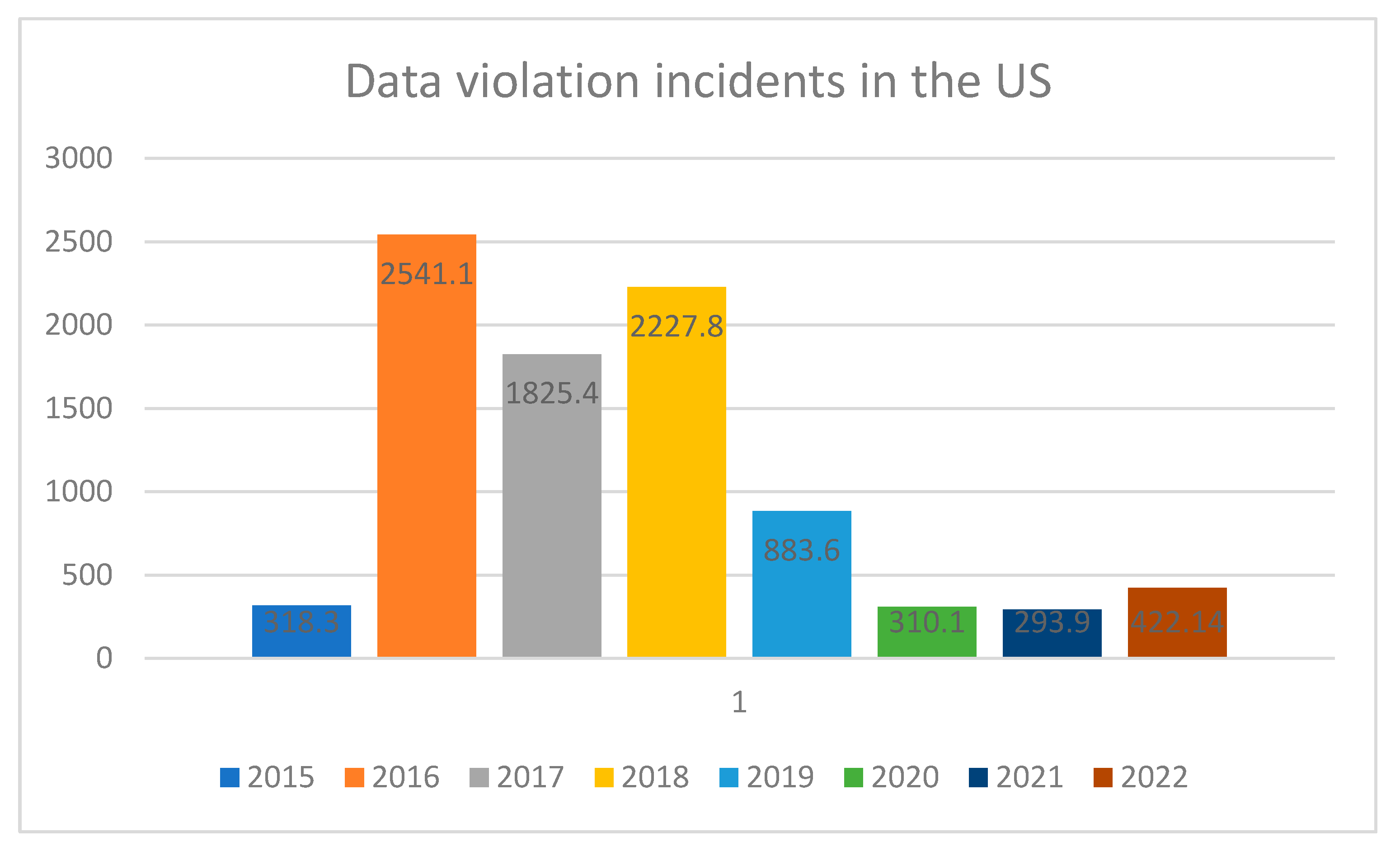
3. Results and Discussion
| Category | Loss in $ Million |
|---|---|
| Investment | $ 3,311.74 |
| Business email Compromise | $ 2,742.35 |
| Tech Support | $ 806.55 |
| Personal Data breach | $ 742.44 |
| Confidence fraud | $ 735.88 |
| Real estate | $ 396.93 |
| Non-payment/ non-delivery | $ 281.77 |
| Credit card/ Check fraud | $ 264.15 |
| Government impersonation | $ 240.55 |
| Identity theft | $ 189.21 |
| Spoofing | $ 107.93 |
| Advanced fee | $ 104.33 |
4. Challenges and Future Directions
Future Research Efforts Should Focus on:
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Arner, D. W. , Barberis, J., & Buckley, R. P. (2016). The Evolution of FinTech: A New Post-Crisis Paradigm? Georgetown Journal of International Law, 47(4), 1271-1320.
- Apostu, S. A. , Panait, M., Vasa, L., Mihaescu, C., & Dobrowolski, Z. (2022). NFTs and Cryptocurrencies—The Metamorphosis of the Economy under the Sign of Blockchain: A Time Series Approach. Mathematics, 10(17), 3218.
- Barberis Nicholas, 2018, Handbook of Behavioral Economics: Applications and Foundations 1, North-Holland, Volume 1,2018, Pages 79-175, ISSN 2352-2399,ISBN 9780444633743, ttps://doi.org/10.1016/bs.hesbe.2018.07.001.
- Becker, M. , 2019, Privacy in the digital age: comparing and contrasting individual versus social approaches towards privacy. Ethics Inf Technol 21, 307–317 (2019). [CrossRef]
- Brooks Charles, J. , Christopher Grow, Philip Craig, Donald Short, 2018, Cybersecurity Essentials, ISBN:9781119362395, John Wiley & Sons, Inc.
- Catalini, Christian and Gans, Joshua S., Some Simple Economics of the Blockchain (April 20, 2019). Rotman School of Management Working Paper No. 2874598, MIT Sloan Research Paper No. 5191-16, Available at SSRN: https://ssrn.com/abstract=2874598. [CrossRef]
- Cha D., C. Pae, S.-B. Seong, J.Y. Choi, H.-J. Park, (2019), Automated diagnosis of ear disease using ensemble deep learning with a big otoendoscopy image database, EBioMedicine, 45 (2019), pp. 606-614.
- Chen, L. , Wang, W., Nagarajan, M., Wang, S., Sheth, A., 2012. Extracting diverse sentiment expressions with target-dependent polarity from twitter. In: Proceedings of the International AAAI Conference on Web and Social Media, vol. 6, no. 1, pp. 50–57.
- Claessens, Stijn and Frost, Jon and Turner, Grant and Zhu, Feng, Fintech Credit Markets Around the World: Size, Drivers and Policy Issues (September 1, 2018). BIS Quarterly Review September 2018, Available at SSRN: https://ssrn.com/abstract=3288096.
- Creado, Y., & Ramteke, V. (2020, May 2). Active cyber defense strategies and techniques for banks and financial institutions. [CrossRef]
- Cocco, L. , Pinna, A., & Marchesi, M. (2017). Banking on Blockchain: Costs Savings Thanks to theBlockchain Technology. Future Internet, 9(3), 25. [CrossRef]
- (3) (PDF) FinTech in Banks: Opportunities and Challenges. Available from: https://www.researchgate.net/publication/344646568_FinTech_in_Banks_Opportunities_and_Challenges [accessed Mar 19 2024].
- Cukier, K. , & Zhu, H. (2018). Big Data, Big Risks: Toward Sustainable Cybersecurity in Financial Technology. Journal of Cybersecurity, 4(1), 1-17.
- Cumming Sean P., Chris Searle, Janie K. Hemsley, Finlay Haswell, Hannah Edwards, Sam Scott, Aleks Gross, Desmond Ryan, Jeff Lewis, Paul White, Andrew Cain, Siobhan B. Mitchell, Robert M. Malina, (2018), Biological maturation, relative age and self-regulation in male professional academy soccer players: A test of the underdog hypothesis, Psychology of Sport and Exercise,Volume 39, 2018, Pages 147-153, ISSN 1469-0292. [CrossRef]
- European Banking Authority. (2018). Guidelines on the Security Measures for Operational and Security Risks of Payment Services Under Directive (EU) 2015/2366 (PSD2). Retrieved from https://www.eba.europa.eu/sites/default/documents/files/documents/10180/2263108/1f74ebf0-c7b2-4e89-ade0-16ebea24cc7d/EBA-GL-2018-07%20%28Guidelines%20on%20security%20measures%20for%20operational%20and%20security%20risks%20of%20payments%20services%20under%20PSD2%29.pdf.
- Financial Stability Oversight Council. (2020). Annual Report. Retrieved from https://home.treasury.gov/policy-issues/financial-sanctions/faqs/1085.
- Gai, K., Qiu, M., & Sun, X. (2018, February 1). A survey on FinTech. Journal of Network and Computer Applications, 103, 262-273. [CrossRef]
- Gai, K. , Qiu, M., & Sun, X. (2020). Blockchain Cybersecurity in Financial Technology Applications: A Case Study of Ant Financial. Journal of Information Security and Applications, 50, 102417.
- International Association of Privacy Professionals (IAPP). (2019). The Growing Global Focus on Privacy: 2019 Privacy Governance Report. Retrieved from https://iapp.org/resources/article/the-growing-global-focus-on-privacy-2019-privacy-governance-report/.
- Hasan, Rashedul, Mohammad Kabir Hassan and Sirajo Aliyu.(2020) “Fintech and Islamic Finance: Literature Review and Research Agenda.” International Journal of Islamic Economics and Finance (IJIEF) (2020): n. pag.
- Kshetri, N. (2017). Can blockchain strengthen the Internet of Things? IT Professional, 19(4), 68-72.
- Manta, O. , Folcut, O., & Militaru, L. (2023). ARTIFICIAL INTELLIGENCE, INTEGRITY, AND OPPORTUNITY IN INSURTECH. Journal of Information Systems & Operations Management, 17(1), 97-110.
- Milian Eduardo Z., Mauro de M. Spinola, Marly M. de Carvalho, (2019), ,Fintechs: A literature review and research agenda, Electronic Commerce Research and Applications, Volume 34, 2019, 100833, ISSN 1567-4223. [CrossRef]
- Miroshnychenko Ivan, Barontini Roberto, Testa Francesco, 2017, Green practices and financial performance: A global outlook, Journal of Cleaner Production, Volume 147, 2017, Pages 340-351, ISSN 0959-6526. [CrossRef]
- Oraca, M U., & Craciun, L F. (n.d), 2023, The Rise of FinTech and the Need for Robust Cybersecurity Measures.
- Petrosyan A., 2023, Leading cyber-crime victim loss categories U.S. 2022, https://www.statista.com/statistics/234987/victim-loss-cyber-crime-type/.
- R K. (2023, October 11). Examining The Role of Fintech in Financial Inclusion and Its Impact on Financial Services to Underbanked Population in India. [CrossRef]
- RX Advanced Technologies LTD, 2024, ResilientX Security is the leading provider of cutting-edge cyber security solutions for Security testing, Posture Management, Security rating and Risk monitoring, https://resilientx.com/blog/ibm-cost-of-a-data-breach-report-2023-what-we-learn-from-it/.
- Sangwan, V., Prakash, P., & Singh, S. (2020). Financial technology: A review of extant literature. Studiesin Economics and Finance, 37(1), 71–88. [CrossRef]
- (3) (PDF) FinTech in Banks: Opportunities and Challenges. Available from: https://www.researchgate.net/publication/344646568_FinTech_in_Banks_Opportunities_and_Challenges [accessed Mar 19 2024].
- Smith, A. N. , & Smith, B. L. (2018). FinTech: Addressing Cybersecurity Risks. Journal of Technology Research, 9, 1-16.
- Suryono, R R., Budi, I., & Purwandari, B. (2020, December 21). Challenges and Trends of Financial Technology (Fintech): A Systematic Literature Review. Information, 11(12), 590-590. [CrossRef]
- Tong L, Yan W and Manta O (2022) Artificial Intelligence Influences Intelligent Automation in Tourism: A Mediating Role of Internet of Things and Environmental, Social, and Governance Investment. Front. Environ. Sci. 10:853302. [CrossRef]
- Uddin, H., Ali, H., & Hassan, M K. (2020, August 18). Cybersecurity hazards and financial system vulnerability: a synthesis of literature. Risk Management, 22(4), 239-309. [CrossRef]
- Varshney, S., Munjal, D., Bhattacharya, O., Saboo, S., & Aggarwal, N. (2020, December 16). Big Data Privacy Breach Prevention Strategies. 2020 IEEE International Symposium on Sustainable Energy, Signal Processing and Cyber Security (iSSSC). [CrossRef]
- World Economic Forum. (2019). Advancing Cyber Resilience: Principles and Tools for Boards. Retrieved from http://www3.weforum.org/docs/WEF_Advancing_Cyber_Resilience_Principles_and_Tools_for_Boards_2019.pdf.
- Woods A., 2022, https://www.startupdaily.net/podcasts/suds-with-adviser-ratings-founder-angus-woods-on-the-rise-of-fintech-the-great-tech-jobs-crisis-paying-advisors-and-mental-health-for-kids/.
- Yermack, David, Corporate Governance and Blockchains (November 28, 2016). Review of Finance, Forthcoming, Available at SSRN: https://ssrn.com/abstract=2700475. [CrossRef]
- Yong Xu, Ling Yuan, Hyoungsuk Lee, Sabrine Baire, Joanna Nakonieczny, Xin Zhao, Fintech Development and Firm Technological Innovation Efficiency: Empirical Findings in China, IEEE Transactions on Engineering Management, 71, (3881-3891), (2024). [CrossRef]
- Yuchong Li, Qinghui Liu, 2021, A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments, Energy Reports, Volume 7, Pages 8176-8186, ISSN 2352-4847. [CrossRef]
- Contributors, F. (2023, July 10). The Challenges and Opportunities of Data Privacy and Security in the Fintech Ecosystem. https://www.financemagnates.com/fintech/data/the-challenges-and-opportunities-of-data-privacy-and-security-in-the-fintech-ecosystem/.
- Kavitha, A., Rao, B S., Akhtar, D N., Rafi, D S M., Singh, P., Das, S., & Manikandan, D G. (2022, June 30). A Novel Algorithm to Secure Data in New Generation Health Care System from Cyber Attacks Using IoT. International journal of electrical & electronics research, 10(2), 270-275. [CrossRef]
- Challenges of using artificial intelligence. (2024, January 1). https://www2.deloitte.com/us/en/pages/consulting/articles/challenges-of-using-artificial-intelligence.html.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





