Submitted:
05 January 2024
Posted:
08 January 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- Unauthorized Access: Use better pseudo-random generation for a key stream like elliptic curve implementation of DSA because rc4 does not provide authentication [6].
- Impersonation Attack and Replay Attack: The protocol has a few flaws, including a failure to key compromise impersonation, an unreliable password-changing process, imperfect shared verification and an internal attack drawback [10].
- Low Response Time: Rc4 and affine cipher do not work on response time, they only work on the security of encryption and decryption [6]. The approach does not apply to the text if the main length is too long in text and the keys are handed over to a third party, which is a major flaw in symmetric encryption [3]. However, need to optimize the encryption and decryption time, as well as the hyperparameter, to boost our performance [11]. The security has been greatly improved. As a result, this paper provided this comprehensive literature review to contribute to the work by filling in the gaps in existing surveys.
- Dictionary Attack: A dictionary attack is a type of assault for which the encoded phrases are very similar to terms found in a dictionary, making it easy for hackers to break the plain text.
1.1. Contributions
- The encryption and decryption time of the message has been described in this scheme paper.
- Extract different features (Time, Security) and discover networking methods.
- Prevents dictionary, plaintext and other passive attacks.
- Identified current gaps
2. Literature Review
2.1 Problem Statement
2.2 Solution
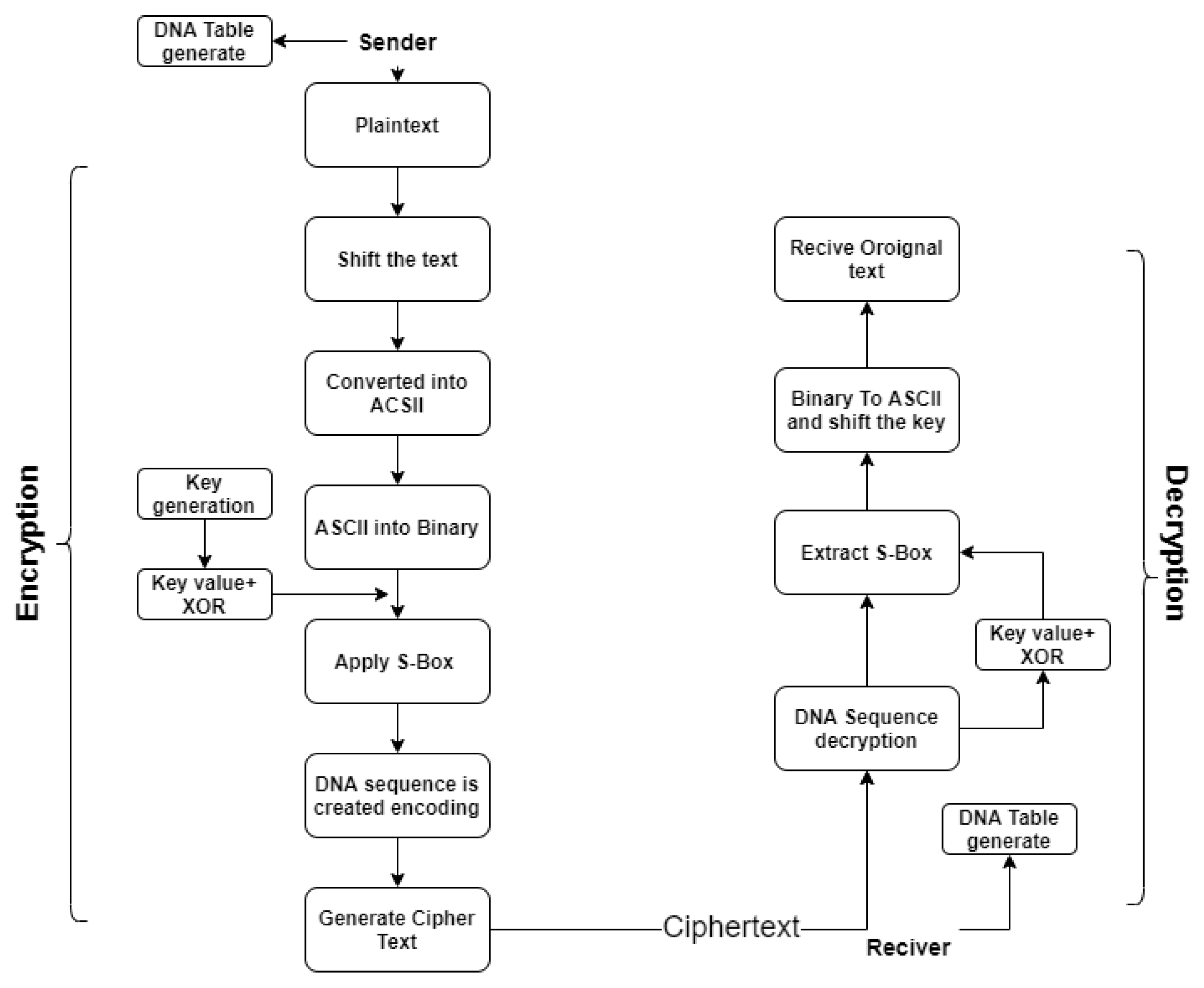
3. Efficient Cryptographic Scheme for SMS (ECSS)
3.1 Proposed Scheme
3.2 Encryption and Decryption Procedure
3.3 Encryption Process
3.4 Algorithm
3.5. Decryption
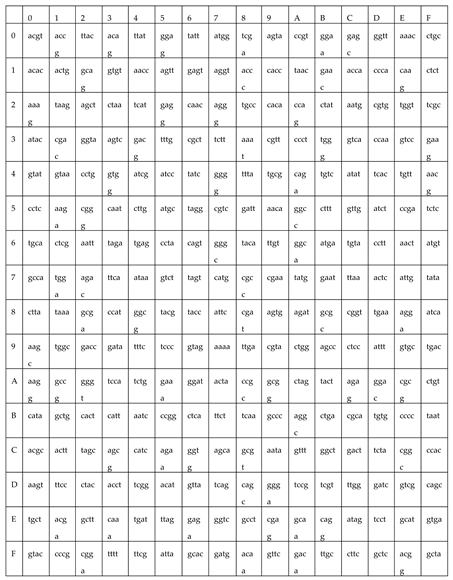
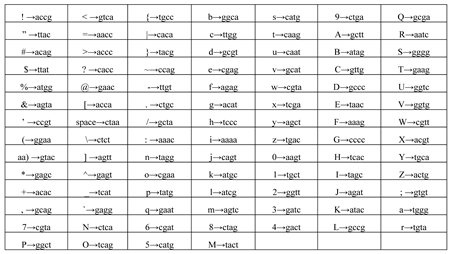
4. Mathematical Modeling
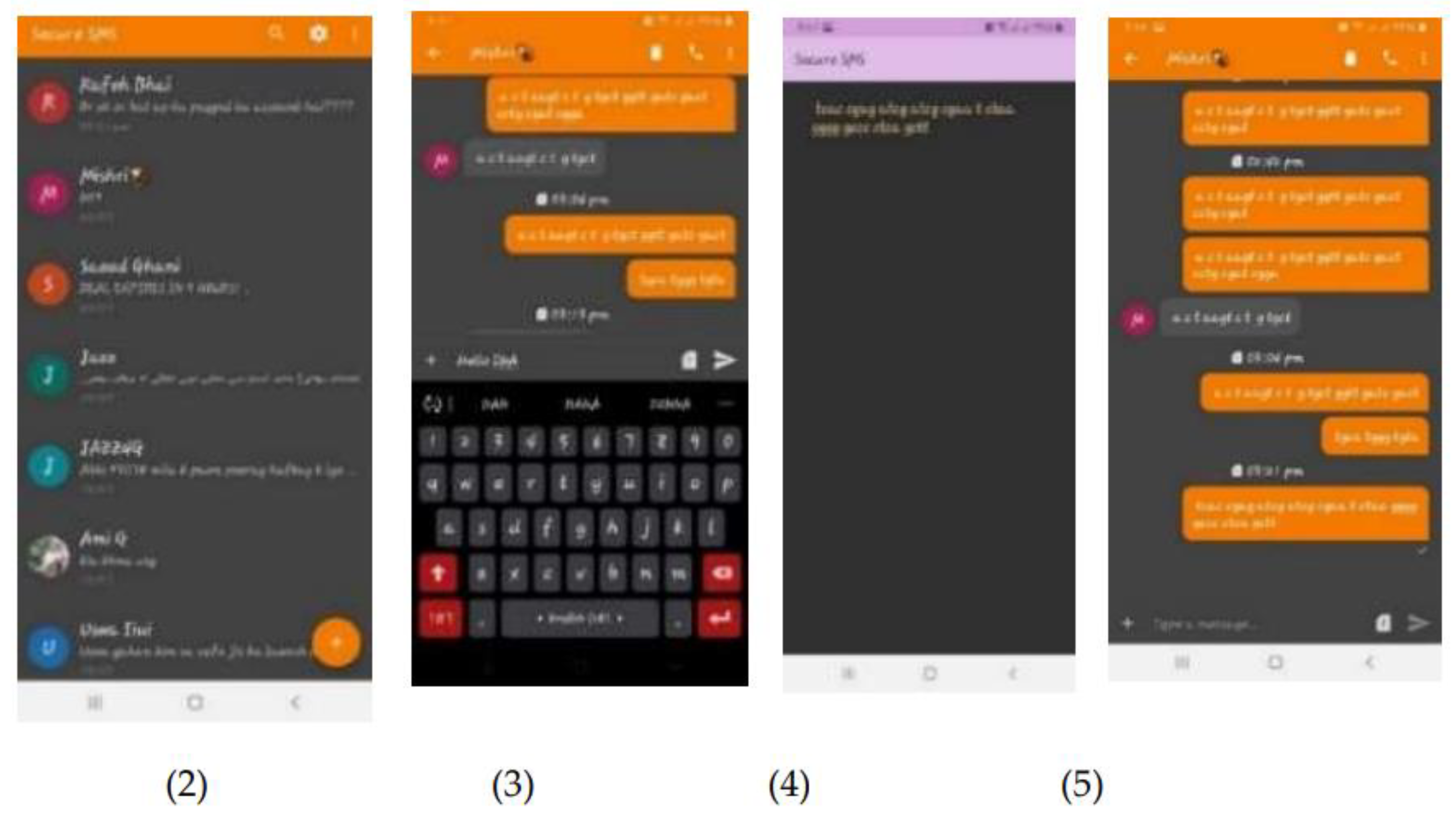
5. Simulation
6. Results and Discussion
6.1. Attacks
6.1.1. Plaintext Attack
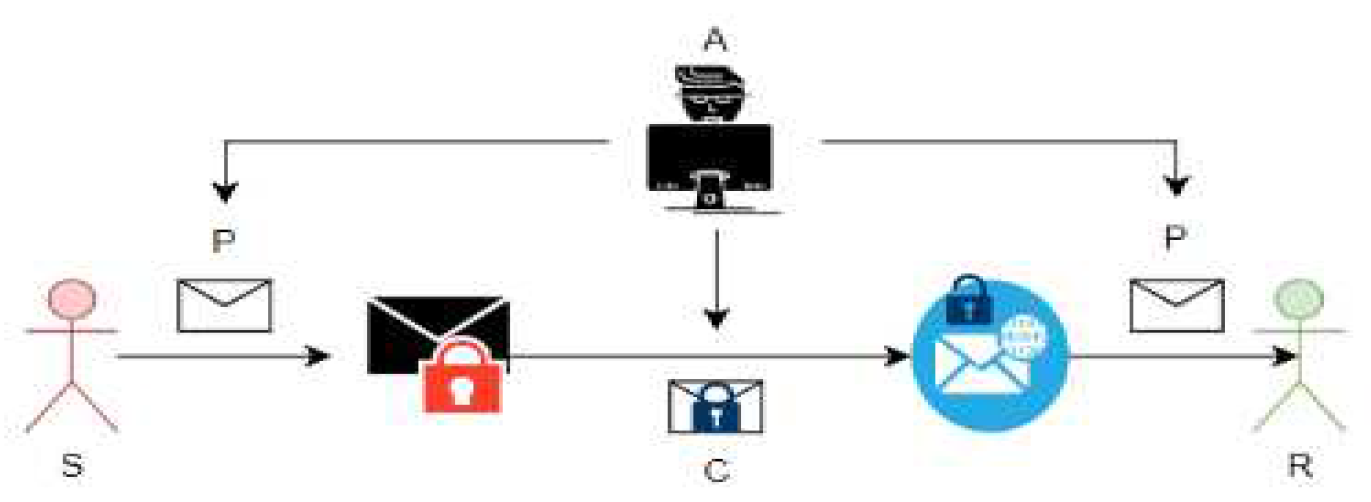
6.1.2. Dictionary Attack
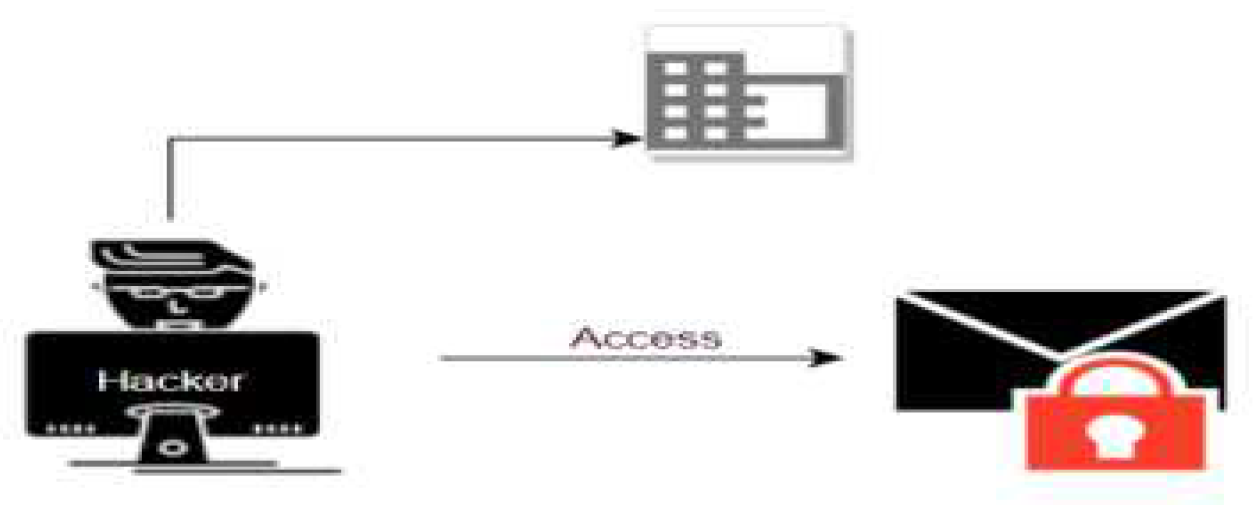
6.1.3. Man in the Middle Attack
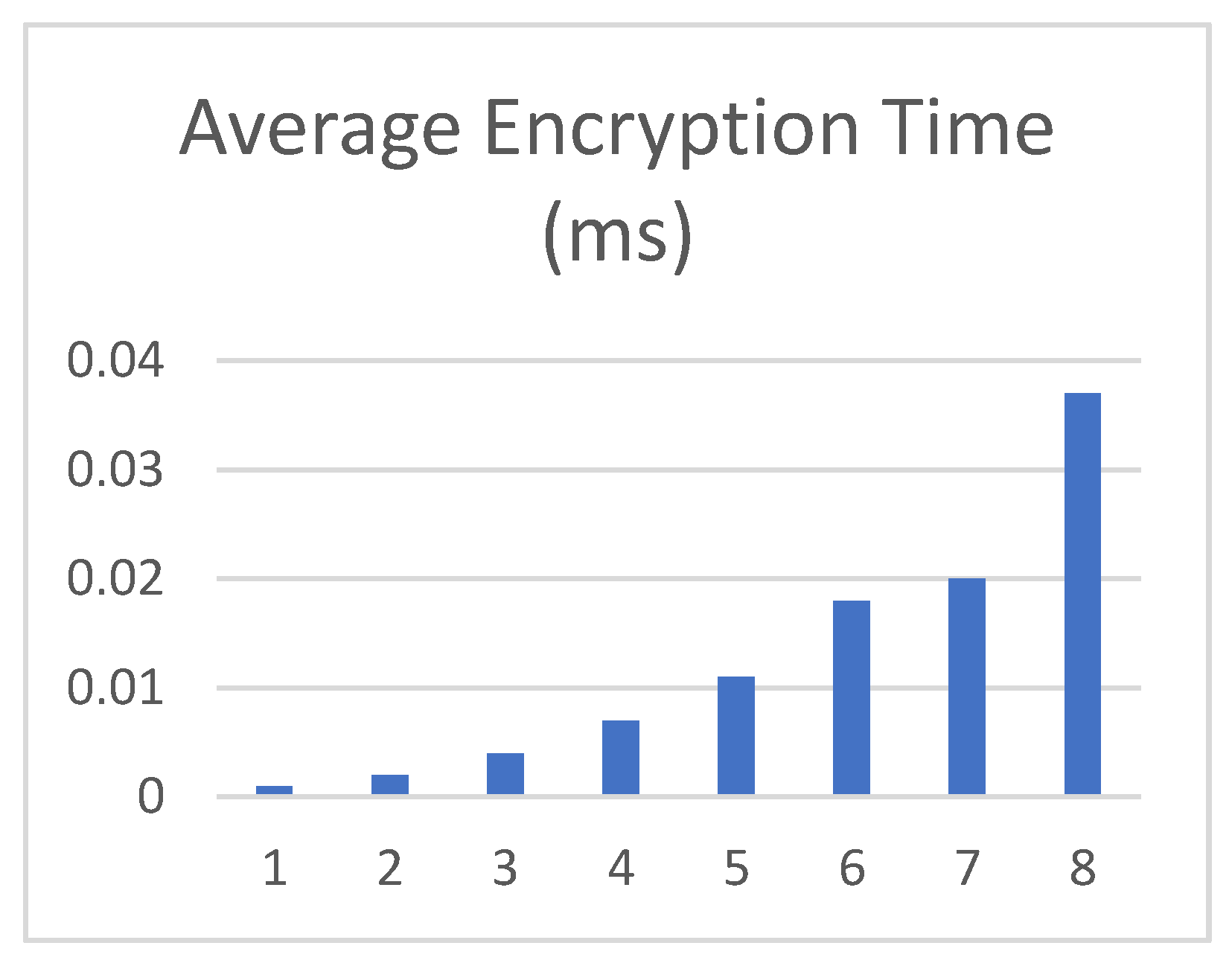
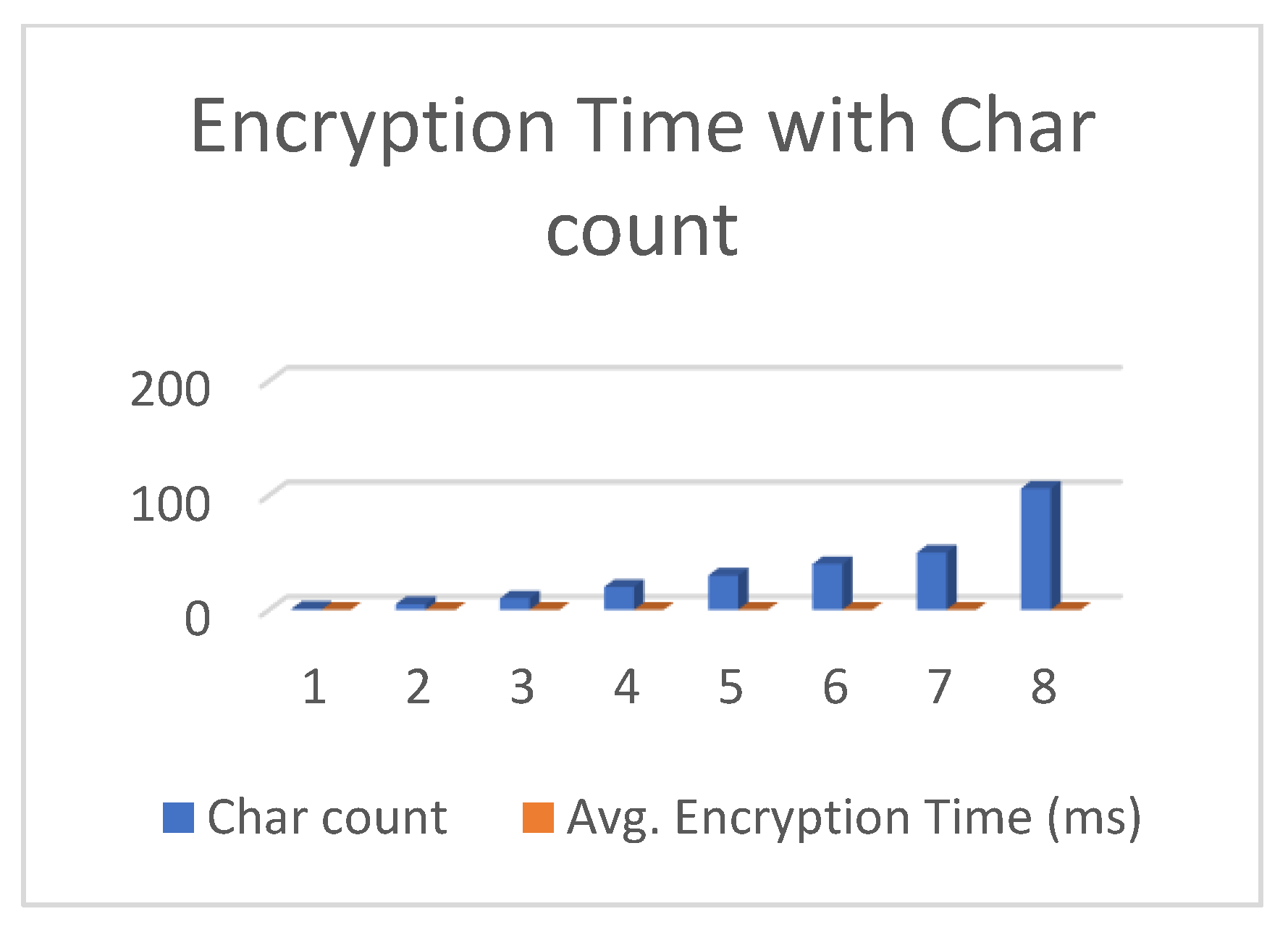
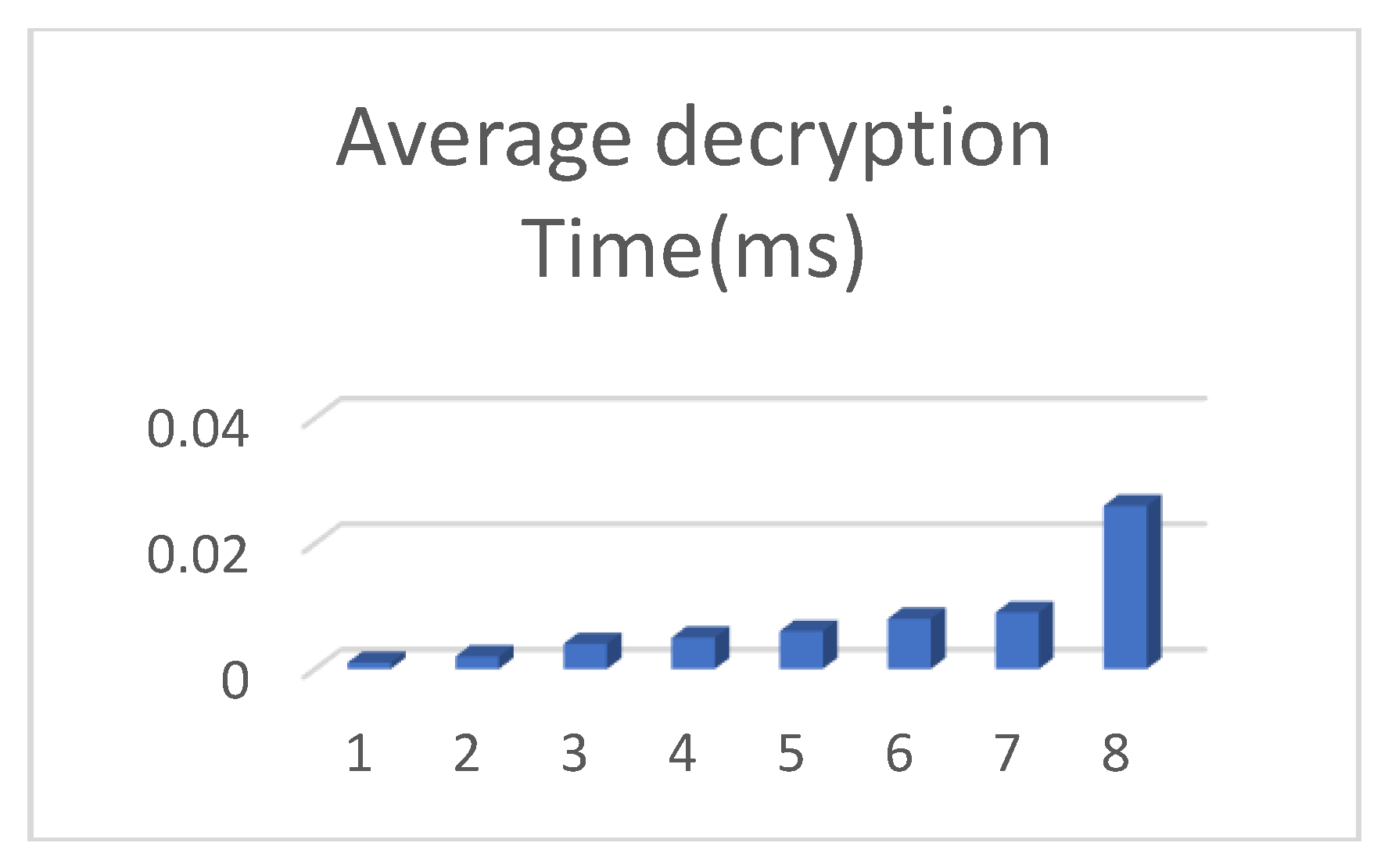
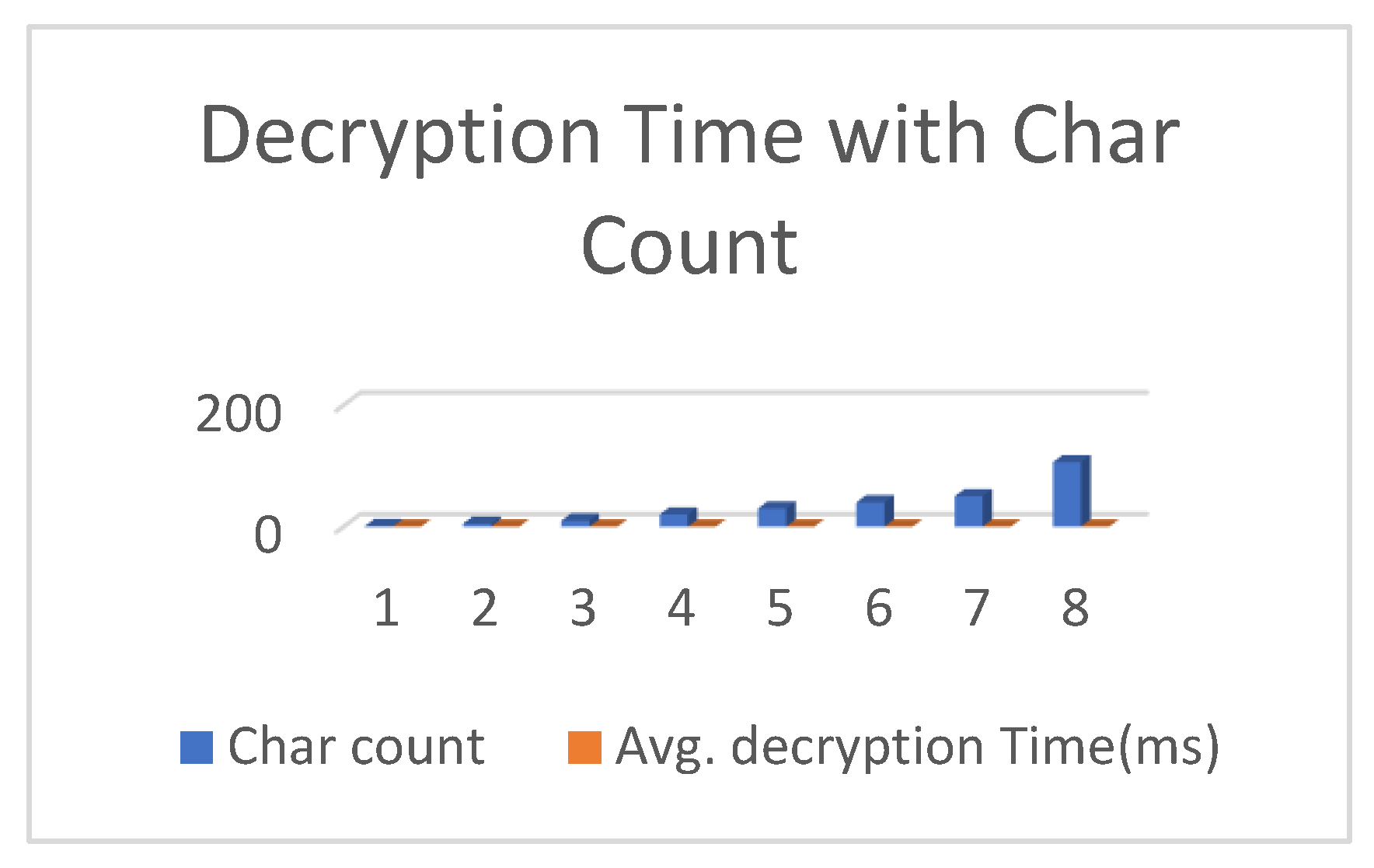
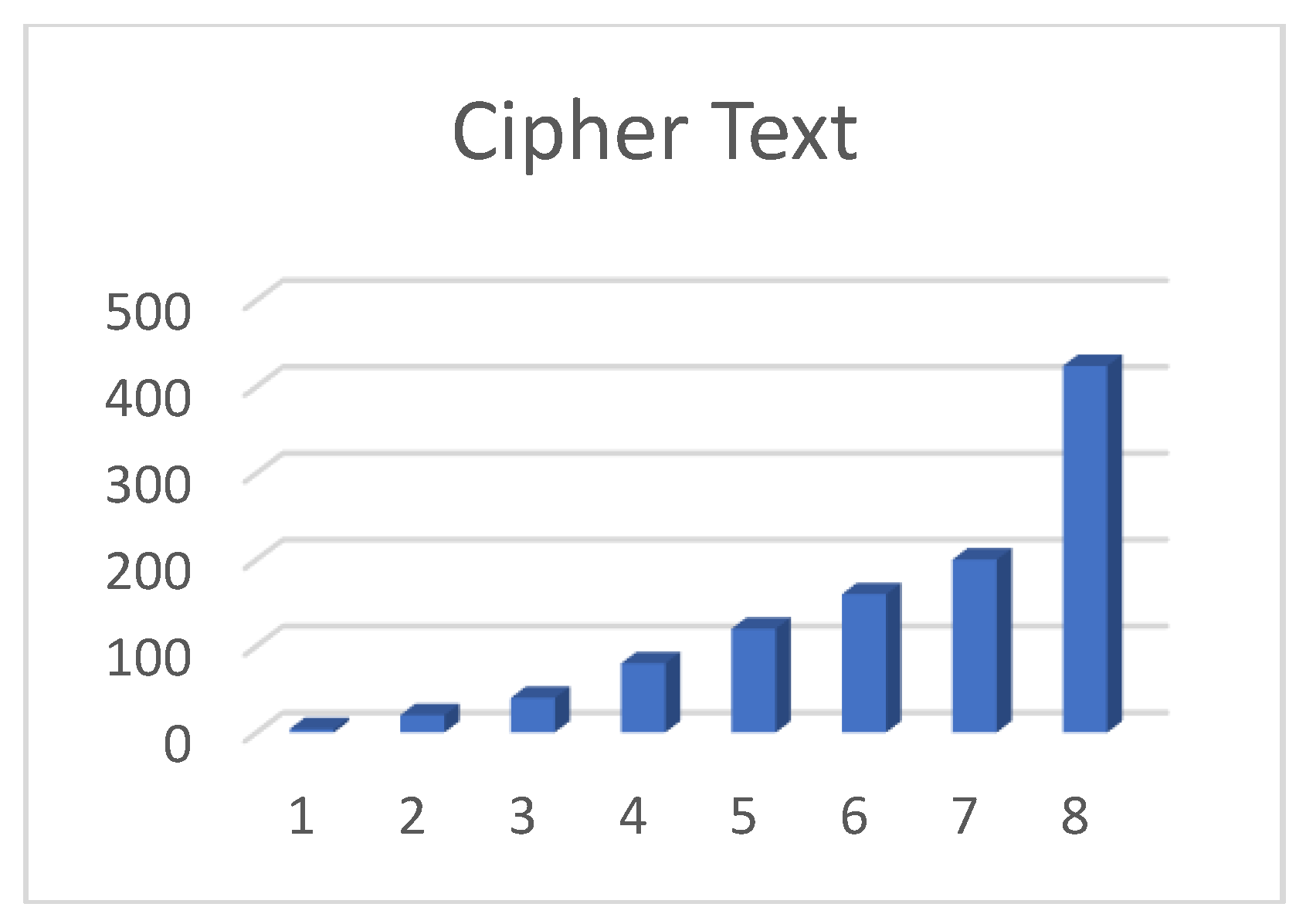
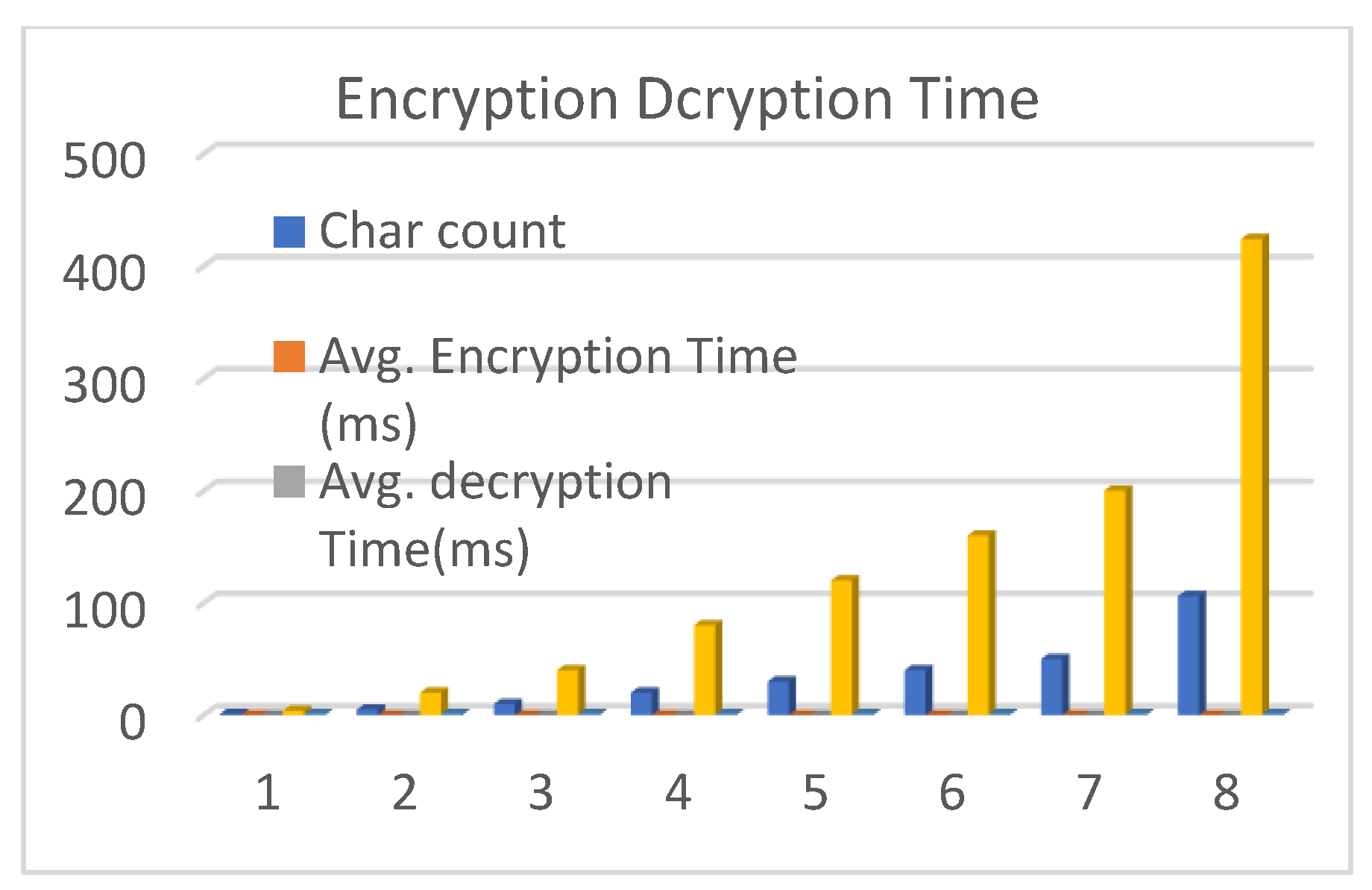
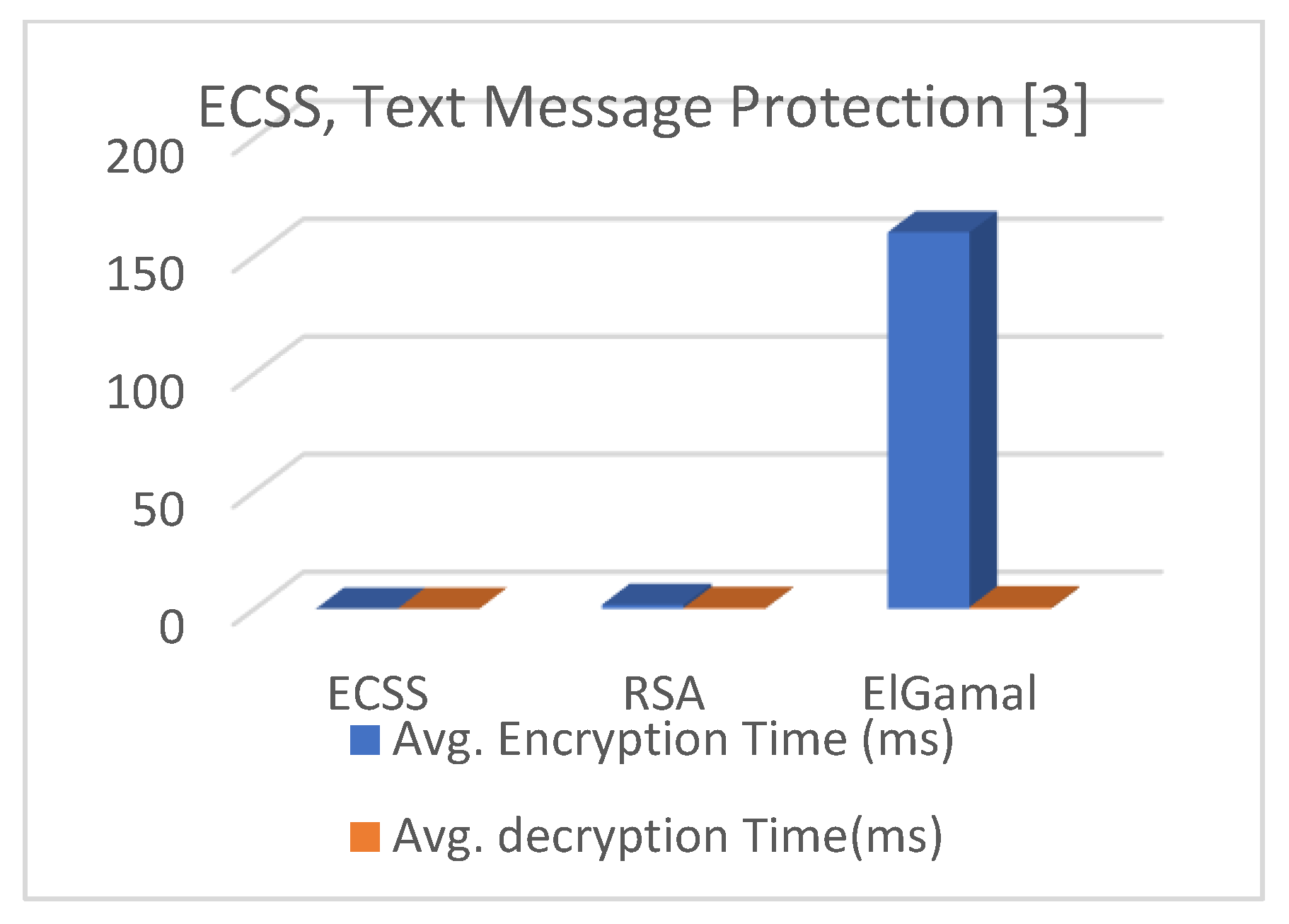
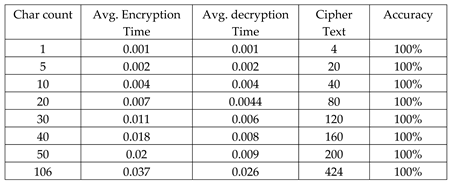
6.2. Computational Time
6.3. The Computational Time of Encryption
6.4. The Computational Time of Decryption
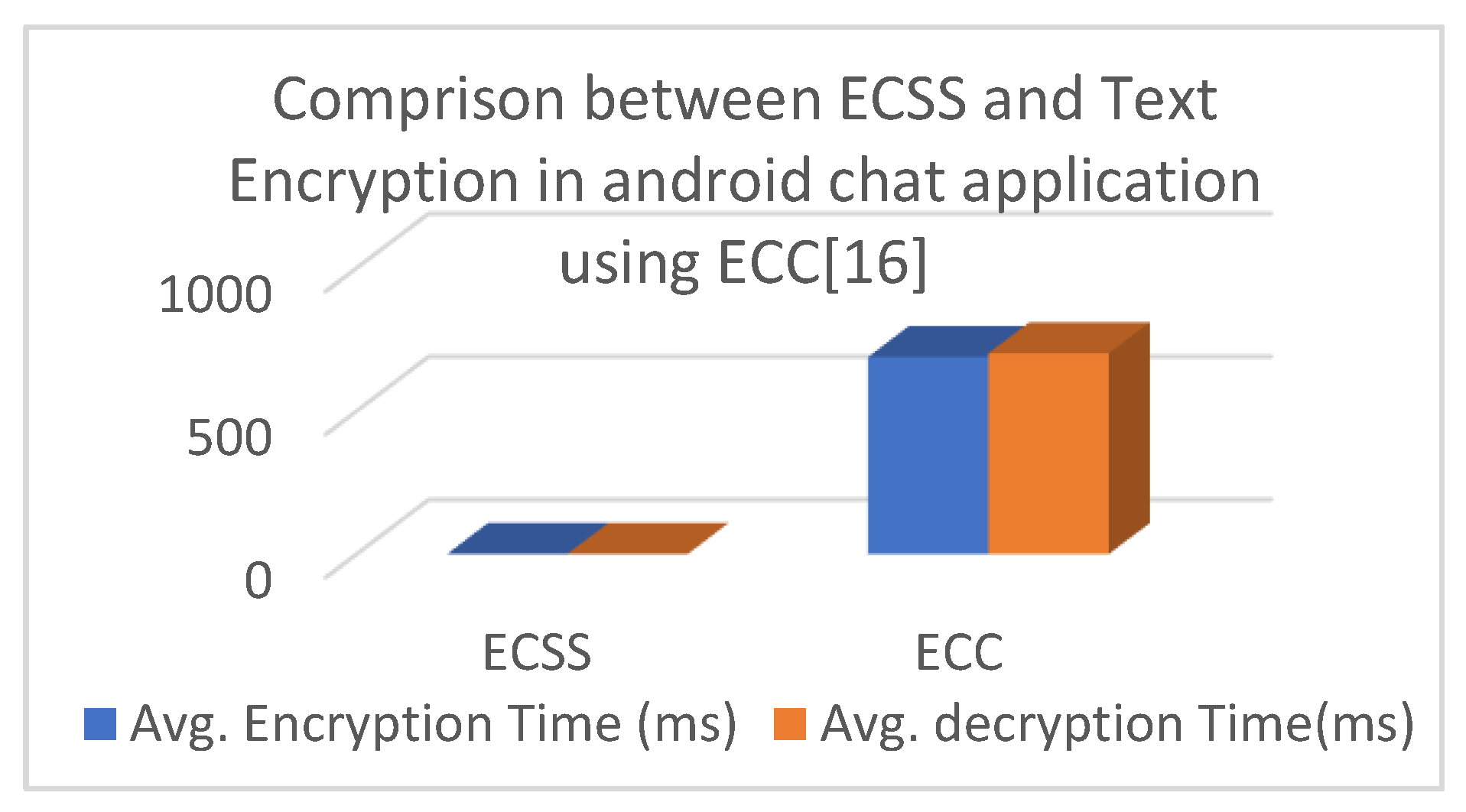
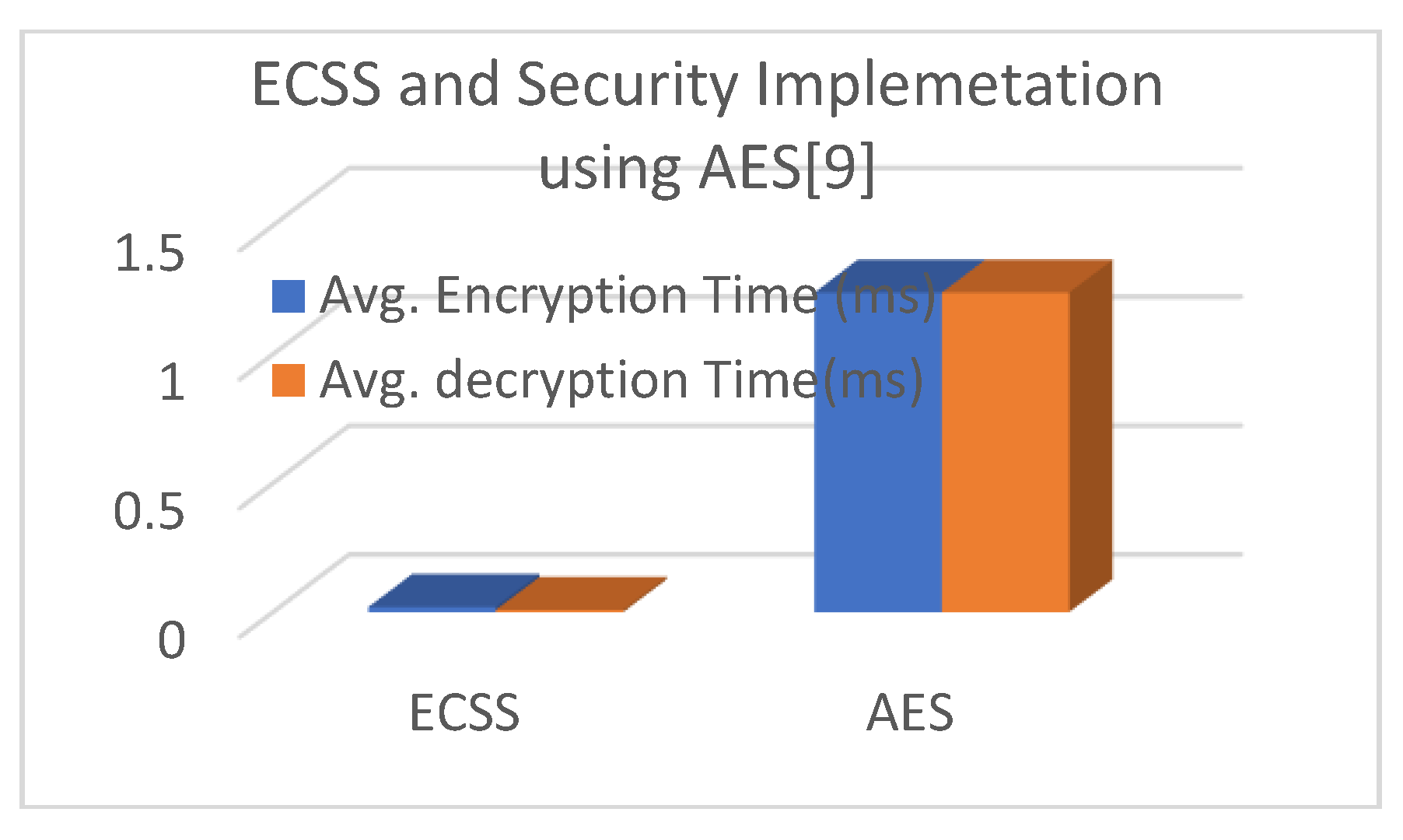
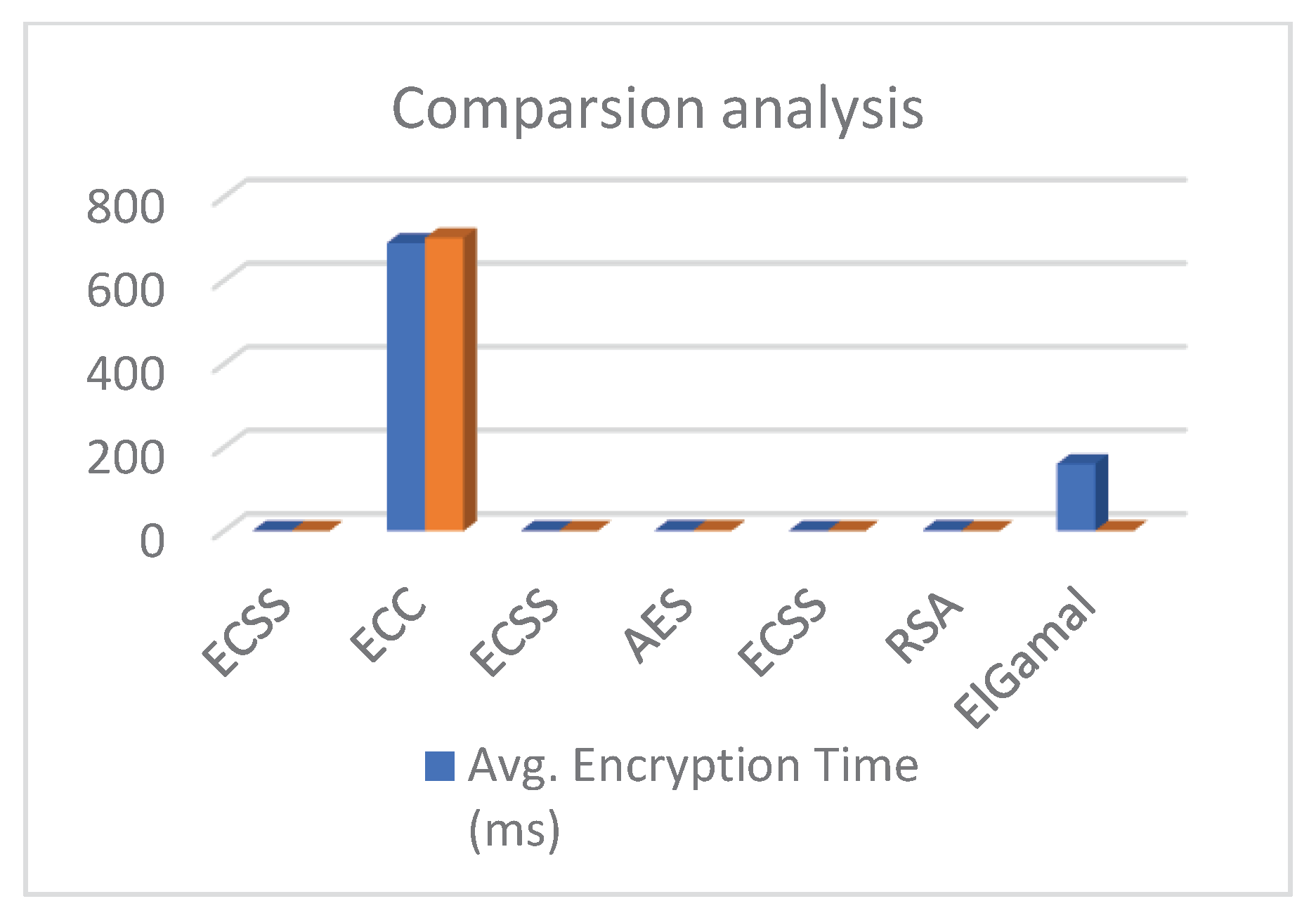
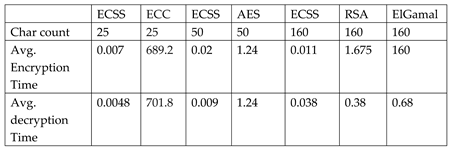
6.5. Comparison Analysis
7. Conclusions
References
- DataReportal, “Digital 2020 Pakistan (January 2020) v01,” 04:10:26 UTC. Accessed: Jul. 19, 2022. [Online]. Available: https://www.slideshare.net/DataReportal/digital-2020-pakistan-january-2020-v01.
- “Mobile Operating System Market Share Pakistan,” StatCounter Global Stats. https://gs.statcounter.com/os-market-share/mobile/pakistan (accessed Jul. 21, 2022).
- Starikovskiy, A. Zhgilev and N. Shevchenko, “Text Messages Protection System,” 8th Annual International Conference on Biologically Inspired Cognitive Architectures, BICA, Moscow, Russia 2017, vol. 123, pp. 457–466, 2018. [CrossRef]
- F. Ramdhansya, E. Ariyanto and H. H. Nuha, “Implementasi Advanced Encryption Standard (AES) Pada Sistem Kunci Elektronik Kendaraan Berbasis Sistem Operasi Android Dan Mikrokontroler Arduino,” Seminar Nasional Informatika 2014 Neliti.com. [Online]. Available: https://media.neliti.com/media/publications/175408-ID-implementasi-advanced-encryption-standar.pdf, 2019.
- M. W. Khan, “SMS Security in Mobile devices: A Survey,” International Journal Advanced Networking and Applications vol. 05, no. 02, pp. 1873-1882, 2013.
- S. Sitompul, N. H. Pasaribu and E. B. Nababan, “Hybrid RC4 and Affine Ciphers to Secure Short Message Service on Android,” in 2018 Third International Conference on Informatics and Computing (ICIC), IEEE, Palembang, Indonesia, pp. 1–6, 2018. [CrossRef]
- S. Tahira, A. Ullah, H. Ashraf and M. Sher, “Efficient security associations establishment using IPSec in IMS after handover in NGMN.” Journal of Internet Technology vol.20, no.2, pp.359-367,2019.
- H. Ashraf, A. Ullah, S. Tahira and M. Sher, “Efficient certificate based One-pass Authentication Protocol for IMS.” 1134 Journal of Internet Technology vol.20, no. 4, pp.1133-1143,2019.
- D. Nurmalasari, E. Mulyana and M. Irfan, “Security implementation of the Internet of Things using the Advanced Encryption Standard (AES) Algorithm,” in 2019 IEEE 5th International Conference on Wireless and Telematics (ICWT), IEEE, Yogyakarta, pp. 1–4, 2019. [CrossRef]
- B. Ahamed and M. Krishnamoorthy, “SMS Encryption and Decryption using Modified Vigenere Cipher Algorithm,” Journal of the Operations Research Society of China, vol. 10, pp.1-14, 2020. [CrossRef]
- Natanael and D. Suryani, “Text Encryption in Android Chat Applications using Elliptical Curve Cryptography (ECC),” The 3rd International Conference on Computer Science and Computational Intelligence (ICCSCI 2018), vol. 135, Indonesia, pp. 283–291, 2018. [CrossRef]
- P. U. Siahaan, “An overview of the RC4 Algorithm,” IOSR Journal of Computer Engineering (IOSR-JCE) vol. 18, pp 67-73,2016. [CrossRef]
- K. Rathi, U. Karabiyik, T. Aderibigbe and H. Chi, “Forensic analysis of encrypted instant messaging applications on Android,” in 6th International Symposium on Digital Forensic and Security (ISDFS), IEEE, Turkey, pp. 1–6,2018. [CrossRef]
- A. Dawood and O. I. Hammadi, “An analytical study for some drawbacks and weakness points of the AES Cipher (Rijndael Algorithm),” A Scientific Quarterly Refereed Journal, vol. 2, no. 2, pp.111-118. 2017. [CrossRef]
- “Snapshot.” Accessed: Jul. 19, 2022. [Online]. Available: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard.
- N. H. UbaidurRahman, C. Balamurugan and R. Mariappan, “A novel DNA computing based encryption and decryption algorithm,” International Conference on Information and Communication Technologies (ICICT 2014), vol. 46, India, pp. 463–475, 2015. [CrossRef]
- H. Al-Mahdi, M. Alruily, O. R.Shahin and K. Alkhaldi, “Design and analysis of DNA encryption and decryption technique based on asymmetric cryptography system,” (IJACSA) International Journal of Advanced Computer Science and Applications, vol. 10, no. 2, 2019. [CrossRef]
- Z. K. Abdalrdha, F. N. Abbas and I. H. AL-Qinani, “Subject review: SMS encryption for android mobile using the encryption algorithm,” International Journal of Engineering Research and Advanced Technology (IJERAT), vol. 05, no. 10, pp. 01–08, 2019. [CrossRef]
- Vidhya, S. Sivabalan and R. Rathipriya, “Hybrid key generation for RSA and ECC,” Fourth International Conference on Communication and Electronics Systems (ICCES), IEEE, India, pp. 35-40 2019. [CrossRef]
- H. Ali and A. M. Sagheer, “Design of an android application for secure chatting,” International Journal of Computer Network and Information Security, vol. 9, no. 2, pp. 29–35, 2017. [CrossRef]
- T. Mandge and V. Choudhary, “A DNA encryption technique based on matrix manipulation and secure key generation scheme,” 2013 International Conference on Information Communication and Embedded Systems (ICICES), Chennai, India, pp. 47-52, 2013. [CrossRef]
- M. S. Hossain, K. M. R. Alam, M. R. Biswas and Y. Morimoto, “A DNA cryptographic technique based on dynamic DNA sequence table,” 19th International Conference on Computer and Information Technology (ICCIT), Dhaka, Bangladesh, pp. 270-275, 2016. [CrossRef]
- E.Ibrahim, M. I. Moussa and H. M. Abdalkader, “A Symmetric Encryption Algorithm based on DNA Computing,” International Journal of Computer Applications, vol. 97, no. 16, pp. 41–45, 2014. [CrossRef]
- M. Imran, M. Rashid, A. Raza Jafri and M. Najam-ul-Islam, “ACryp-Proc: Flexible Asymmetric Crypto Processor for Point Multiplication,” IEEE Access, vol. 6, pp. 22778–22793, 2018. [CrossRef]
- N. Borodzhieva and P. K. Manoilov, “Training module with graphical user interface for encryption and decryption using affine ciphers applied in cryptosystems,” 2014 IEEE 20th International Symposium for Design and Technology in Electronic Packaging (SIITME), Bucharest, Romania, pp. 281-286, 2014. [CrossRef]
- S. Shukla and P. Verma, “Implementation of Affine Substitution Cipher with Keyed Transposition Cipher for Enhancing Data Security,” International Journal of Advanced Research in Computer Science and Software Engineering 4, no.1, pp. 236-241, 2014.
- D. Luciano and G. Prichett, “Cryptology: from Caesar Ciphers to public-key Cryptosystems,” Mathematical Association of America, vol. 18, no. 1, pp. 2–17, Jan. 1987. [CrossRef]
- M. Biswas, and N. Sakeef and H. Siddique, “Exploring network security using Vigenere Multiplicative cipher encryption and implementation,” Research Square, 2020. [CrossRef]
- R. Rifki, A. Septiarini and H. Rahmania, “Cryptography using random RC4 stream cipher on SMS for Android-based smartphones,” International Journal of Advanced Computer Science and Applications(IJACSA), vol. 9, no. 12, 2018. [CrossRef]
- P. Jindal and B. Singh, “RC4 encryption-A literature survey,” International Conference on Information and Communication Technologies (ICICT 2014), vol. 46, Kochi, pp. 697–705, 2015. [CrossRef]
- N. Kumar and P. Chaudhary, “Performance Evaluation of Encryption/Decryption Mechanisms to Enhance Data Security,” Indian Journals of Science and Technology, vol. 9, no. 20, pp.1-10, 2016. [CrossRef]
- Al-Mahdi, O. R.Shahin, Y. Fouad and K. Alkhaldi, “Design and analysis of DNA Binary Cryptography Algorithm for Plaintext,” International Journal of Engineering and Technology (IJET), vol. 10, no. 3 , pp. 699–706, Jun. 2018. [CrossRef]
- R. Rayarikar, S. Upadhyay and P. Pimpale, “SMS Encryption using AES Algorithm on Android,” International Journal of Computer Applications, vol. 50, no. 19, pp. 12–17, 2012.
- Almusaylim, Z., Jhanjhi, N. Z., & Alhumam, A. (2020). Detection and mitigation of RPL rank and version number attacks in the internet of things: SRPL-RP. Sensors, 20(21), 5997. [CrossRef]
- Humayun, M., Jhanjhi, N. Z., Talib, M. N., Shah, M. H., & Suseendran, G. (2021). Cybersecurity for Data Science: Issues, Opportunities, and Challenges. Intelligent Computing and Innovation on Data Science: Proceedings of ICTIDS 2021, 435-444. [CrossRef]
- Kok, S. H., Azween, A., & Jhanjhi, N. Z. (2020). Evaluation metric for crypto-ransomware detection using machine learning. Journal of Information Security and Applications, 55, 102646. [CrossRef]
- Shafiq, M., Ashraf, H., Ullah, A., Masud, M., Azeem, M., Jhanjhi, N. Z., & Humayun, M. (2021). Robust Cluster-Based Routing Protocol for IoT-Assisted Smart Devices in WSN. Computers, Materials & Continua, 67(3). [CrossRef]
- Hussain, K., Hussain, S. J., Jhanjhi, N. Z., & Humayun, M. (2019, April). SYN flood attack detection based on bayes estimator (SFADBE) for MANET. In 2019 International Conference on Computer and Information Sciences (ICCIS) (pp. 1-4). IEEE. [CrossRef]
- Lim, M., Abdullah, A., Jhanjhi, N. Z., & Supramaniam, M. (2019). Hidden link prediction in criminal networks using the deep reinforcement learning technique. Computers, 8(1), 8. [CrossRef]
- Kumar, T., Pandey, B., Mussavi, S. H. A., & Zaman, N. (2015). CTHS based energy efficient thermal aware image ALU design on FPGA. Wireless Personal Communications, 85, 671-696. [CrossRef]
- Verma, S., Kaur, S., Rawat, D. B., Xi, C., Alex, L. T., & Jhanjhi, N. Z. (2021). Intelligent framework using IoT-based WSNs for wildfire detection. IEEE Access, 9, 48185-48196. [CrossRef]
- Khalil, M. I., Jhanjhi, N. Z., Humayun, M., Sivanesan, S., Masud, M., & Hossain, M. S. (2021). Hybrid smart grid with sustainable energy efficient resources for smart cities. sustainable energy technologies and assessments, 46, 101211. [CrossRef]
- Diwaker, C., Tomar, P., Solanki, A., Nayyar, A., Jhanjhi, N. Z., Abdullah, A., & Supramaniam, M. (2019). A new model for predicting component-based software reliability using soft computing. IEEE Access, 7, 147191-147203. [CrossRef]
- Aldughayfiq, B., Ashfaq, F., Jhanjhi, N. Z., & Humayun, M. (2023, April). Yolo-based deep learning model for pressure ulcer detection and classification. In Healthcare (Vol. 11, No. 9, p. 1222). MDPI. [CrossRef]
- Aldughayfiq, B., Ashfaq, F., Jhanjhi, N. Z., & Humayun, M. (2023). A Deep Learning Approach for Atrial Fibrillation Classification Using Multi-Feature Time Series Data from ECG and PPG. Diagnostics, 13(14), 2442. [CrossRef]
- Hussain, S. J., Ahmed, U., Liaquat, H., Mir, S., Jhanjhi, N. Z., & Humayun, M. (2019, April). IMIAD: intelligent malware identification for android platform. In 2019 International Conference on Computer and Information Sciences (ICCIS) (pp. 1-6). IEEE. [CrossRef]
- Sennan, S., Somula, R., Luhach, A. K., Deverajan, G. G., Alnumay, W., Jhanjhi, N. Z., ... & Sharma, P. (2021). Energy efficient optimal parent selection based routing protocol for Internet of Things using firefly optimization algorithm. Transactions on Emerging Telecommunications Technologies, 32(8), e4171. [CrossRef]
- Wassan, S., Chen, X., Shen, T., Waqar, M., & Jhanjhi, N. Z. (2021). Amazon product sentiment analysis using machine learning techniques. Revista Argentina de Clínica Psicológica, 30(1), 695.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





