1. Introduction
With the rapid development and wide application of new-generation information technologies such as cloud computing, big data, the Internet of Things, and artificial intelligence [
1,
2,
3,
4]. Nowadays, the dissemination of multimedia data such as digital images on the Internet has become increasingly prevalent. At the same time, however, the rapidly developing digital signal processing technology has brought many security problems to the communication and transmission of digital images on the Internet. Secure transmission and access of digital images in the open network environment have attracted more and more attention from researchers [
5,
6,
7,
8,
9,
10,
11]. Image encryption transforms a meaningful image into an unrecognized noise-like one, and is an effective method to ensure the security of digital images. Chaos systems have received the researchers’ attention due to their inherent properties of sensitivity to initial conditions, ergodicity, and random behavior [
12,
13].
In recent years, many chaotic image encryption schemes have been presented. Pareek et al. proposed an image encryption algorithm by employing two logistic maps [
14]. In the image encryption scheme, the initial conditions for both logistic maps are derived using an external secret key, and eight different types of operations are exploited to encrypt the image pixels. Given the shortcomings of the small parameter space of the Logistic map, Zhang et al. [
15] designed an image encryption algorithm by employing discrete exponential chaotic maps to improve image confusion and diffusion. Zhu and Sun [
12] presented a modified skew tent map and its application in image encryption. The proposed modified tent map to generate the plaintext-dependent secret keys set. The diffusion operation with cipher output feedback ensures that the cipher image is dependent on both the initial keys and the plaintext image. In [
16], the Camellia block cipher and the logistic chaotic map are used to encrypt images. It scrambles the image using the Cat map and generates the round mask and the post-whitening key with the logistic map. However previous chaos-based image encryption schemes are built on low-dimensional chaotic maps. The low-dimensional chaotic systems have small keyspace, and the generated chaotic sequence has poor randomness. Kumar et al. employed multiple chaotic maps for image encryption [
17]. In this scheme, the Logistic map is introduced to shuffle the pixels of the plaintext image, and Arnold's cat map is used in the diffusion process. Those encryption schemes based on low-dimensional chaotic sequences [
12,
14,
15,
16,
17] cannot effectively resist statistical attacks.
Later, the hyperchaotic maps have been investigated to design more secure image encryption schemes due to their high randomness and ergodicity. Ref. [
18] proposed a Lorenz-based image encryption algorithm with a perceptron model. It extended the periodicity of the Lorenz chaotic map by dynamically adjusting the chaotic system’s parameters. The modified Lorenz chaotic map is used to produce three sets of the pseudo-random sequence. Akhshani et al. presented a hierarchy of 2D piecewise chaotic maps with an invariant measure and developed a new image encryption scheme by using significant properties of these chaotic maps such as ergodicity, sensitivity to the initial condition, and random-like behavior [
19]. The famous Chen hyperchaotic system is used to generate the shuffling matrix and the diffusing matrix in Ref. [
20]. Firstly, the Chen hyper-chaotic system is used to shuffle the position of the image pixels. Hua et al. built a new 2D chaotic system (called 2D-LSM) using the Logistic and Sine maps, and the 2D-LSM chaotic map is further used to devise a new image encryption algorithm based on the image content [
21]. To enhance the encryption effectiveness, Ye et al. proposed a chaotic encryption scheme combining a 3D logistic map and the secure hash algorithm-3 (SHA-3) [
22]. Wang et al. proposed a color image encryption method by employing 4D chaotic maps and DNA encoding [
23]. In the encryption scheme, the rules of DNA encoding are controlled by four chaotic sequences generated by the new 4D chaotic system. Gong et al. designed a new 4D chaotic system with coexisting asymmetric attractors [
24]. Theoretical analysis of phase portrait, bifurcation diagram, and Lyapunov exponent, and its applications in random number generator (RNG) and image encryption verified the feasibility of the new 4D chaotic map.
Recently, the compound chaotic system has been an effective approach for image encryption [
25,
26,
27] because it showed better randomness and noise-like behaviors than other chaos. Zhu et al. proposed a 2D composite discrete chaotic system (CDCS) [
28]. To obtain a good permutation effect, the new CDCS system is used for the bit-level permutation and the pixel-level diffusion. In 2017, they developed another compound homogeneous hyper-chaotic system (CHHCS) that is employed to permutate the plaintext image [
29]. In addition, dynamic LBP operations are used to diffuse each permutated pixel. Hua et al. introduced a cosine-transform-based chaotic system (CTBCS) [
30]. The CTBCS is exploited to generate three chaotic maps, one of these maps is used to design an image encryption algorithm where the high-efficiency scrambling is used to separate adjacent pixels and the random order substitution is used to spread a small change in the plaintext image to all pixels of the cipher-image. Gao et al. presented an image encryption algorithm by coupling the sine map and the tent map [
31]. The bit rearrangement is used to further improve the composite sine-tent map. Image pixels are encrypted by applying the most significant bit substitution, scrambling, and diffusion. To overcome bandwidth and security issues simultaneously, Yadav et al. devised a joint image compression and encryption scheme using hybrid chaotic maps [
32]. The Absolute Moment Truncation Coding approach is used for compression and Arnold’s Cat and Henon maps are applied to the compressed image for encryption. To improve the chaotic characteristics, Zhang and Liu [
33] designed a compound Sine-Piecewise Linear Chaotic Map (SPWLCM) and proposed an image encryption algorithm using this SPWLCM chaos and DNA coding. Wang and Du developed two chaotic systems: 1D Logistic-Chebyshev map (1DLCM) and Logistic-Chebyshev coupled map lattices (LCDCML) [
34]. LCDCML uses 1DLCM as the dynamic coupling coefficient and further proposes a pixel-level and bit-level image encryption algorithm using these two new chaotic systems. In the encryption scheme, the image scrambling and diffusion are implemented with chaotic sequences generated by the LCDCML map. Basha et al. presented a bit-level color image encryption scheme using Logistic-Sine-Tent-Chebyshev (LSTC) map [
35]. The LSTC map, cyclic shifts, and the XOR operation are used for the mutual diffusion of two color components. The binary element is exchanged and transformed into another binary bit plane by using the LSTC map.
To obtain better randomness and ergodicity, we constructed a new hybrid chaotic map by coupling multiple chaotic maps and designed a new image encryption application for this compound chaotic map. The main contributions of this paper are summarized as follows: (1) Developed a new hybrid chaotic map by coupling Logistic, ICMIC, Tent, and Chebyshev maps (called HLITC). Performance evaluations by chaotic trajectory, Lyapunov exponent, and Kolmogorov entropy testify the new hybrid chaotic map has better key sensitivity to the initial value and larger control parameter space. (2) Proposed a chaotic image encryption algorithm using the presented HLITC system. In the encryption, key sequences generated by the HLITC map are used for image scrambling and diffusion stages. The spiral transformation controlled by the HLITC map is employed to scramble the pixels of the plaintext image, and the XOR operation dependent on the chaotic map is used for image diffusion. (3) The experiments demonstrate that the proposed encryption algorithm has high resistance to statistical attacks, differential attacks, and brute-force attacks, and it can achieve higher security than several previous chaotic image encryption algorithms.
The rest of the paper is organized as follows.
Section 2 introduces the classic chaotic maps and the new hybrid chaotic map. The new image encryption algorithm based on the HLITC system is presented in
Section 3. We discuss the experimental results in
Section 4 and conclude in
Section 5.
2. Construction of the Hybrid Chaotic Map
This section presents the new hybrid chaotic system by coupling Logistic, ICMIC, Tent, and Chebyshev maps (HLITC), and their properties. To prove the superiority of the HLITC system, a comparison between three sample chaotic maps is conducted in terms of chaotic trajectory, Lyapunov exponent, and Kolmogorov entropy.
2.1. Classic Chaotic Maps
2.1.1. Logistic Map
The Logistic map is a quadratic polynomial map, which is one of the typical maps representing complex nonlinear behavior. The mathematical expression is written as follows.
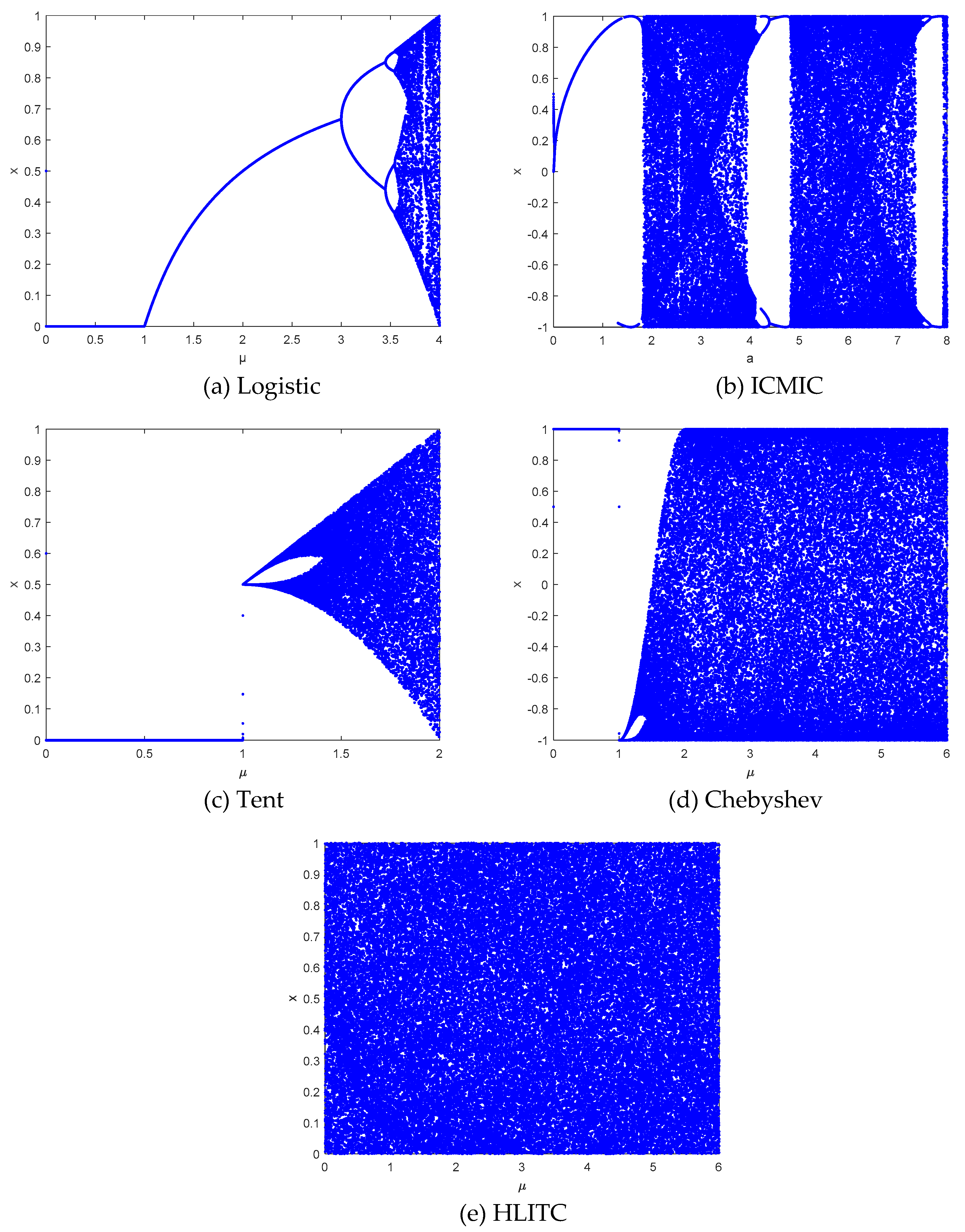
where μ is the bifurcation parameter, only when 3.5699456< μ ≤ 4, the Logistic map falls into the chaotic state. The bifurcation diagram of the Logistic map is shown in
Figure 1(a).
2.1.2. ICMIC Map
He et al. proposed a 1D iterative chaotic map with infinite collapses (ICMIC) [
36]. Compared with the Logistic map and Tent map, the ICMIC map has the advantages of uniform traversal and fast convergence. It can be expressed as
Figure 1(b) shows the corresponding bifurcation diagram.
2.1.3. Tent Map
Tent map is a piecewise linear map with a relatively uniform distribution. The bifurcation diagram for the tent map is represented in
Figure 1(c). It has been widely used in chaotic cryptography. Its mathematical expression is as follows.
where the control parameter
.
2.1.4. Chebyshev Map
Chebyshev map is one of 1D chaotic maps with good nonlinear dynamic characteristics.
Figure 1(d) is the bifurcation diagram for the Chebyshev map. When the control parameter
is greater than 1, chaos phenomenon begins to occur. When greater than 2, The map is in a chaotic state. It can be defined as follows.
2.2. Proposed HLITC Chaotic System
To enhance the randomness of chaotic systems, we design a new chaotic system by combining the Logistic map, ICMIC map, Tent map, and Chebyshev map. The main process of building the chaotic system is as follows:
First, compound ICMIC map and Logistic map, we have
To further skip blank windows, we change the parameter
to
. The compound ICMIC map can be rewritten as
Then compound the Chebyshev map and the Tent map, and modify control parameter
by
to avoid falling into blank areas. The compounded Chebyshev chaotic map is expressed as
Finally, to improve the randomness of the chaotic system, the modular function is used to integrate the compound Chebyshev map and the improved ICMIC map, and the hybrid HLITC chaotic system is produced. Its mathematical definition is as follows.
The improved HLITC map makes the chaotic sequence distribution more uniform and has a large parameter space range from
. It can avoid the stability window and the blank area. Its bifurcation diagram is illustrated in
Figure 1(e). From
Figure 1, it can be seen that the HLITC map has a larger parameter space and better randomness than the traditional chaotic maps.
2.3. Chaotic Behaviours
In this section, Lyapunov Exponent (LE), and information entropy are further used to analyze the dynamics of the HLITC chaotic system.
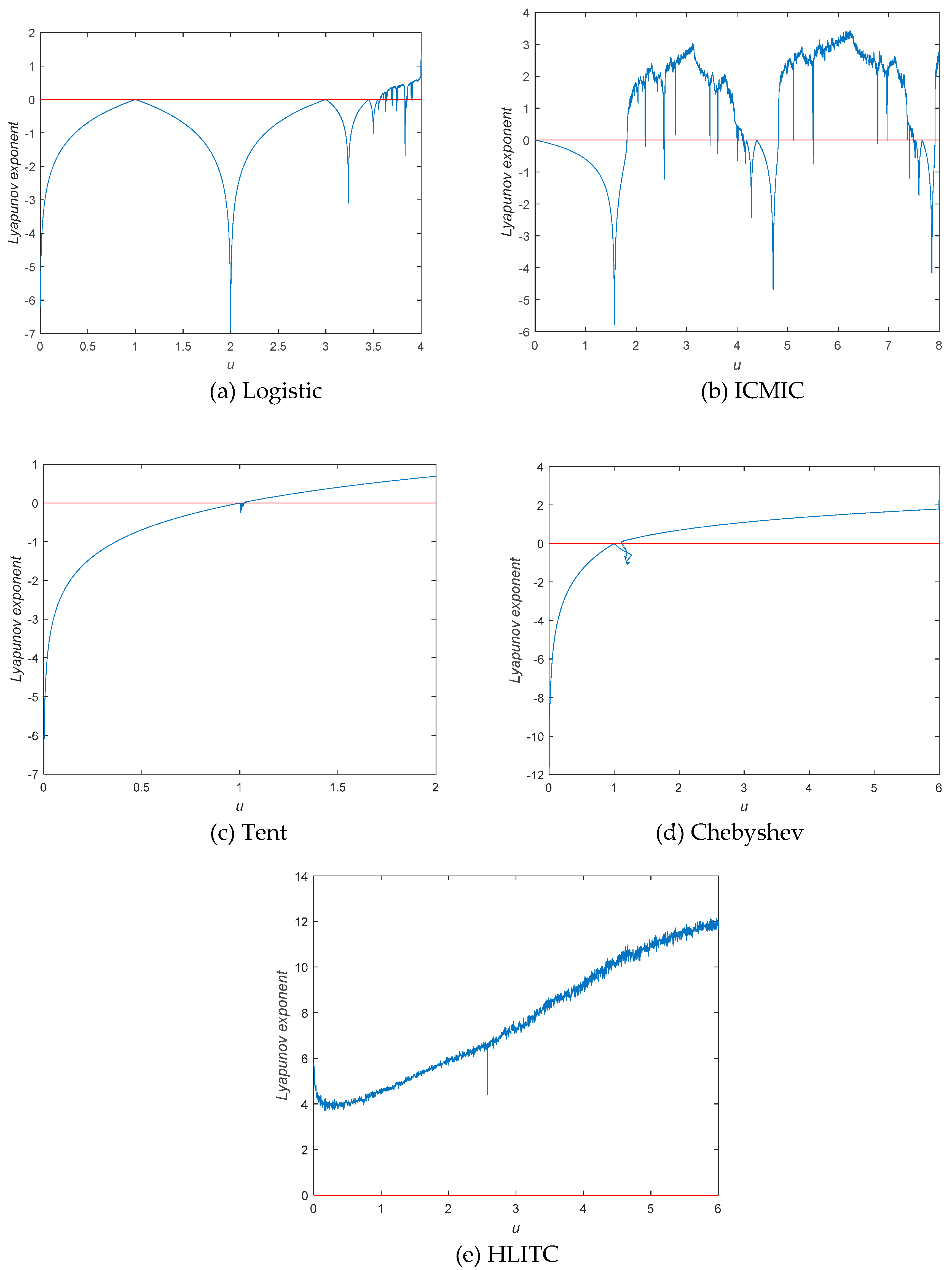
Figure 2 shows the comparison between Logistic, ICMIC, Tent, Chebyshev, and HLITC for the parameter Lyapunov Exponent. From
Figure 2, It can be found that all the LE values of the HLTIC map for all control parameter values are greater than 0. So, the HLITC map has more chaotic behaviors than the classic chaotic maps in terms of LE.
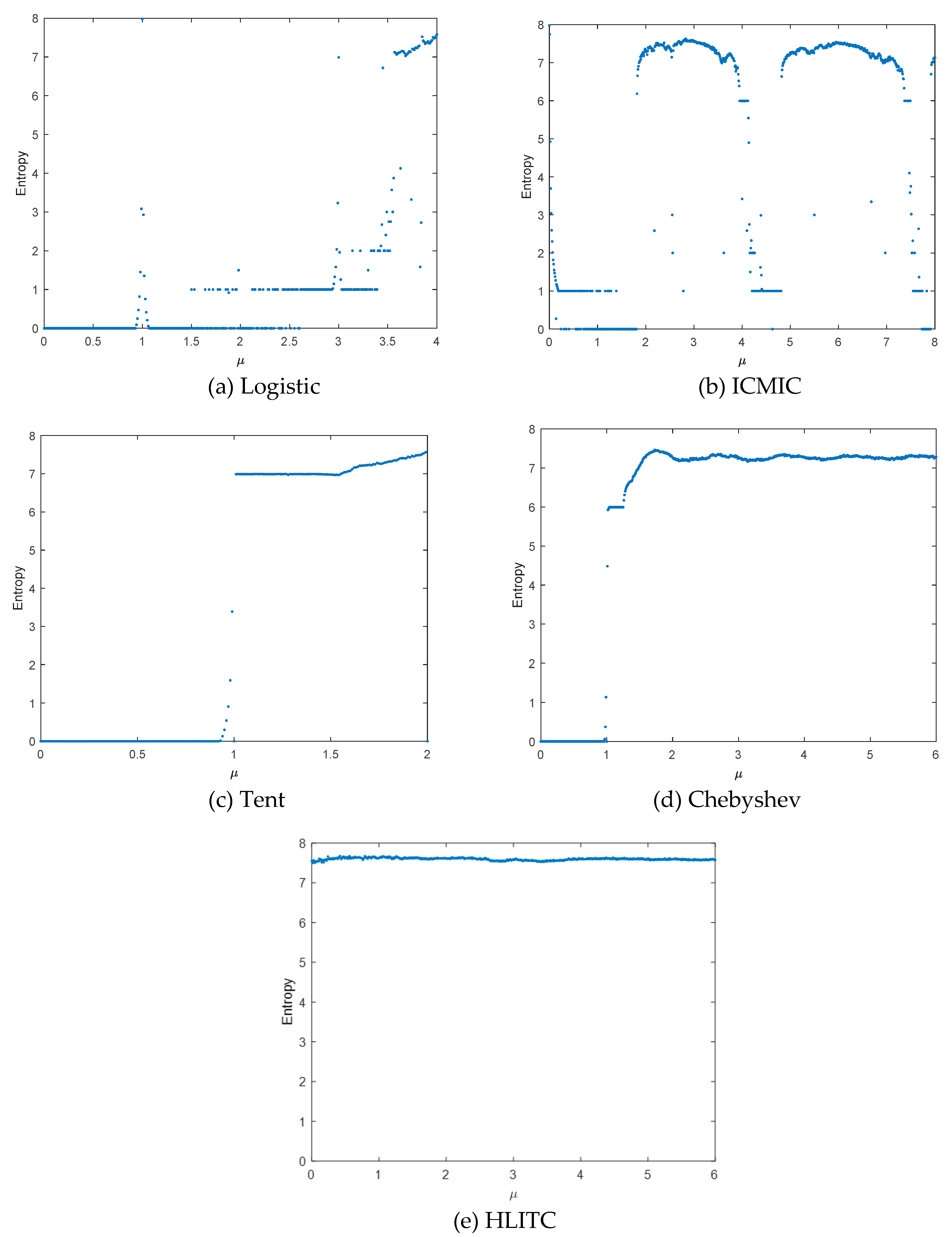
Information entropy is usually used to measure the uncertainty of a variable. The greater the uncertainty of variables, the higher the information entropy, and it is defined as
where
,
is the probability of
, and
L = 256 for gray-scale images. The maximum value of information entropy is 8 for the grayscale images.
Figure 3 shows the information entropy diagrams of different chaotic maps. It can be seen that the entropy values of output sequences generated by the proposed HLITC map are close to the ideal value 8, which indicates the HTLITC map has better unpredictability than the above-mentioned traditional chaotic maps.
2.4. Randomness Test
To further test the randomness of the HLITC map, the NIST SP800 test is performed on the chaotic sequences generated by the HTLITC system. The NIST randomness testing has 15 performance tests which are accessed by P-value. If the P-value is less than 0.01, the randomness of the tested sequence is poor, and if the P-value is greater than or equal to 0.01, the randomness of the tested sequence is good.
In the testing, the chaotic sequence generated by the HLITC map is first converted into a binary sequence and then the NIST randomness testing is performed. The test results are listed in
Table 1. From
Table 1, it can be seen that the chaotic sequence produced by the new HLITC system has good randomness among all 15 indicators tested by NIST, and all P-values are greater than 0.01, indicating that the generated chaotic sequence has good randomness.
3. Image Encryption Based on Hybrid HLITC Map
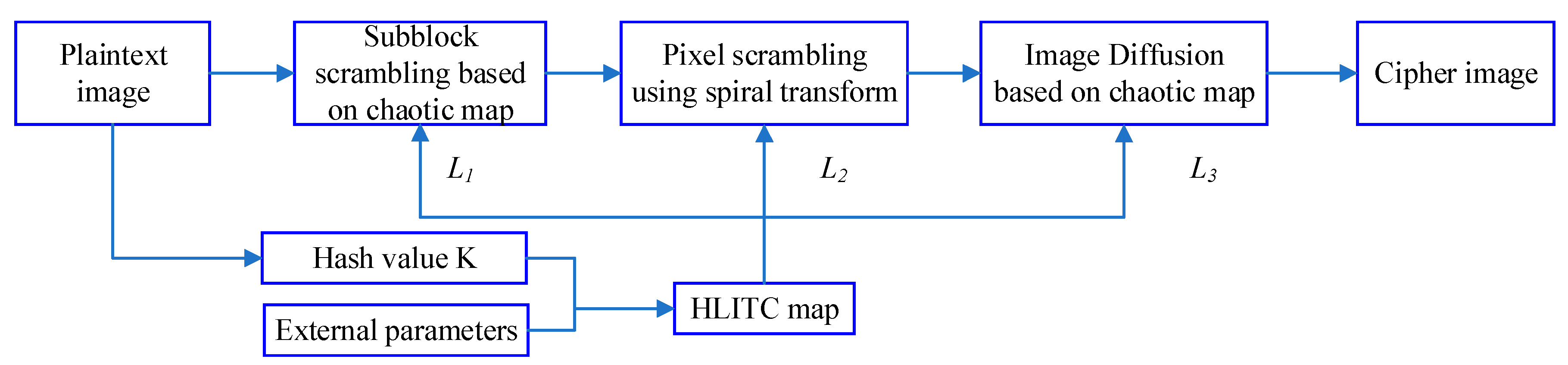
This section introduces the proposed image encryption algorithms based on spiral transformation and chaos maps. The proposed image encryption algorithm based on the HLITC map is composed of three stages, i.e., key generation, image scrambling, and image diffusion process as illustrated in
Figure 4.
3.1. Key Generation
To enhance the security and enlarge the key space, the hash value of the plaintext image and external parameters are employed to produce the control parameters and initial values of the proposed HLITC map. Assume that the original image is denoted as . The detailed process of key generation is illustrated as follows.
Step 1: Obtain the hash value K of the plaintext image by applying the SHA-256 hash function.
Step 2: Divide the hash value K into 32 segments with each of one byte. Thus, K can be expressed as ,, where i=1,2,…,…,32, and is an integer in the interval [0, 255].
Step 3: Set the secret keys
, i=1,2,3 as the external parameters, and generate the initial values
and control parameters
.
Step 4: Iterate the HLITC map for times using and as the initial values and the control parameters, and generate 3 chaotic sequences , , . Their length is , , and , respectively. To minimize the nonperiodic effect, the firstvalues are discarded, where is the size of the original image.
Step 5: Produce 3 random integer sequences
for image scrambling and image diffsion.
where
B is the number of elements of an image subblock,
is the number of image subblocks.
3.2. Image encryption
In this method, to enhance the pseudo-randomness of image scrambling, the arbitrary points spiral transformation based on a chaotic map is used for image scrambling, and the XOR operation of chaotic control is introduced in the pixel diffusion process to further improve the encryption effect.
3.2.1. Image scrambling based on a spiral transformation
The image scrambling process consists of image sub-block scrambling based on chaos control and pixel scrambling based on arbitrary points spiral transformation. The detailed scrambling process is as follows.
Step 1: Divide the plaintext image into subblock of size , i.e. .
Step 2: Use a chaotic sequence of length to scramble each image subblock , and so the scrambled image is obtained.
Step 3: Generate a chaotic sequence by utilizing the average of each image subblock .
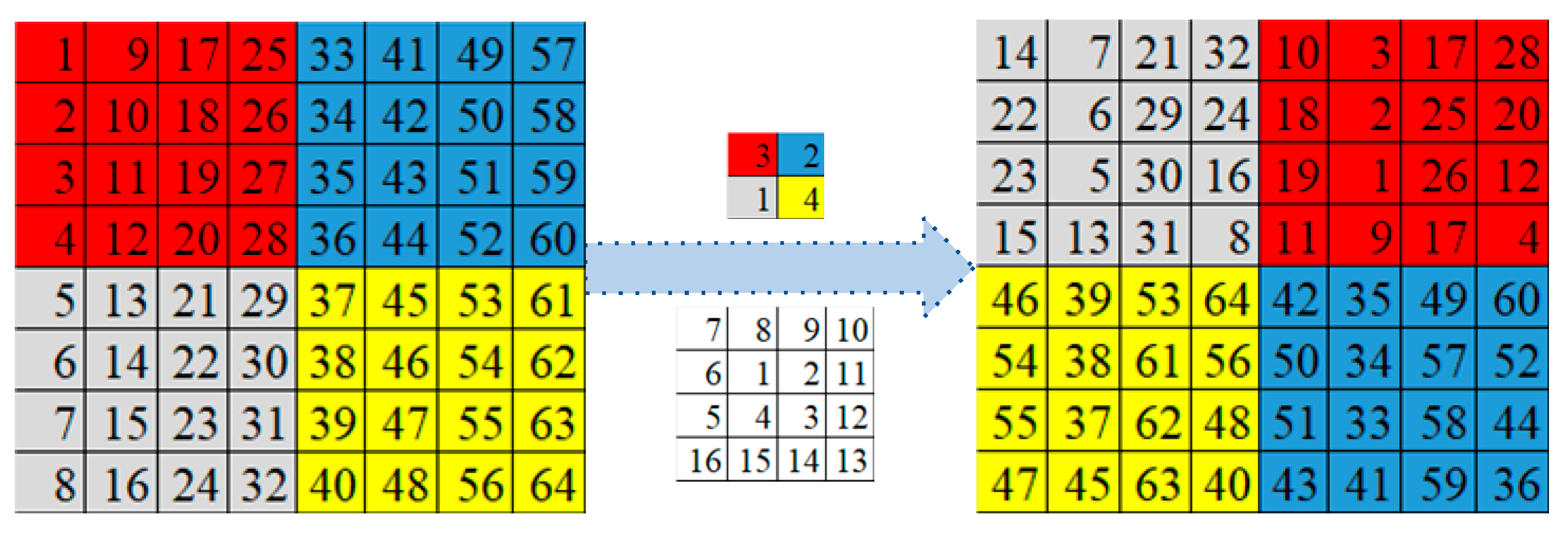
Step 4: According to the random starting point , we perform the spiral transformation on all the pixels within each image subblock to obtain the scrambled image .
Figure 5 shows an example of image scrambling based on spiral transformation.
3.2.2. Image diffusion based on chaotic map
Step 1: Read scrambled image data P from the scrambled image .
Step 2: Reshape matrix P to sequence of length .
Step 3: Perform XOR operation for image diffusion, the detailed process is written as follows.
Where Step 4: Reshape sequence E to a matrix of size to obtain the final encrypted image .
The proposed image encryption system is symmetric, and the decryption algorithm is the inverse process of the encryption algorithm.
Figure 1.
Dynamics comparison with Bifurcation diagrams: (a) Logistic, (b) ICMIC, (c) Tent, (d) Chebyshev and (e) HLITC.
Figure 1.
Dynamics comparison with Bifurcation diagrams: (a) Logistic, (b) ICMIC, (c) Tent, (d) Chebyshev and (e) HLITC.
Figure 2.
Lyapunov exponent diagrams of different chaotic maps: (a) Logistic, (b) ICMIC, (c) Tent, (d) Chebyshev, and (e) HLITC.
Figure 2.
Lyapunov exponent diagrams of different chaotic maps: (a) Logistic, (b) ICMIC, (c) Tent, (d) Chebyshev, and (e) HLITC.
Figure 3.
Dynamics comparison of different chaotic maps in terms of information entropy.
Figure 3.
Dynamics comparison of different chaotic maps in terms of information entropy.
Figure 4.
The image encryption process.
Figure 4.
The image encryption process.
Figure 5.
Image scrambling based on a spiral transformation.
Figure 5.
Image scrambling based on a spiral transformation.
Figure 6.
Results of image encryption and decryption. left column: plaintext image, center column: cipher image, and right column: decipher image (top to down: Lena, Peppers, Man, and Baboon).
Figure 6.
Results of image encryption and decryption. left column: plaintext image, center column: cipher image, and right column: decipher image (top to down: Lena, Peppers, Man, and Baboon).
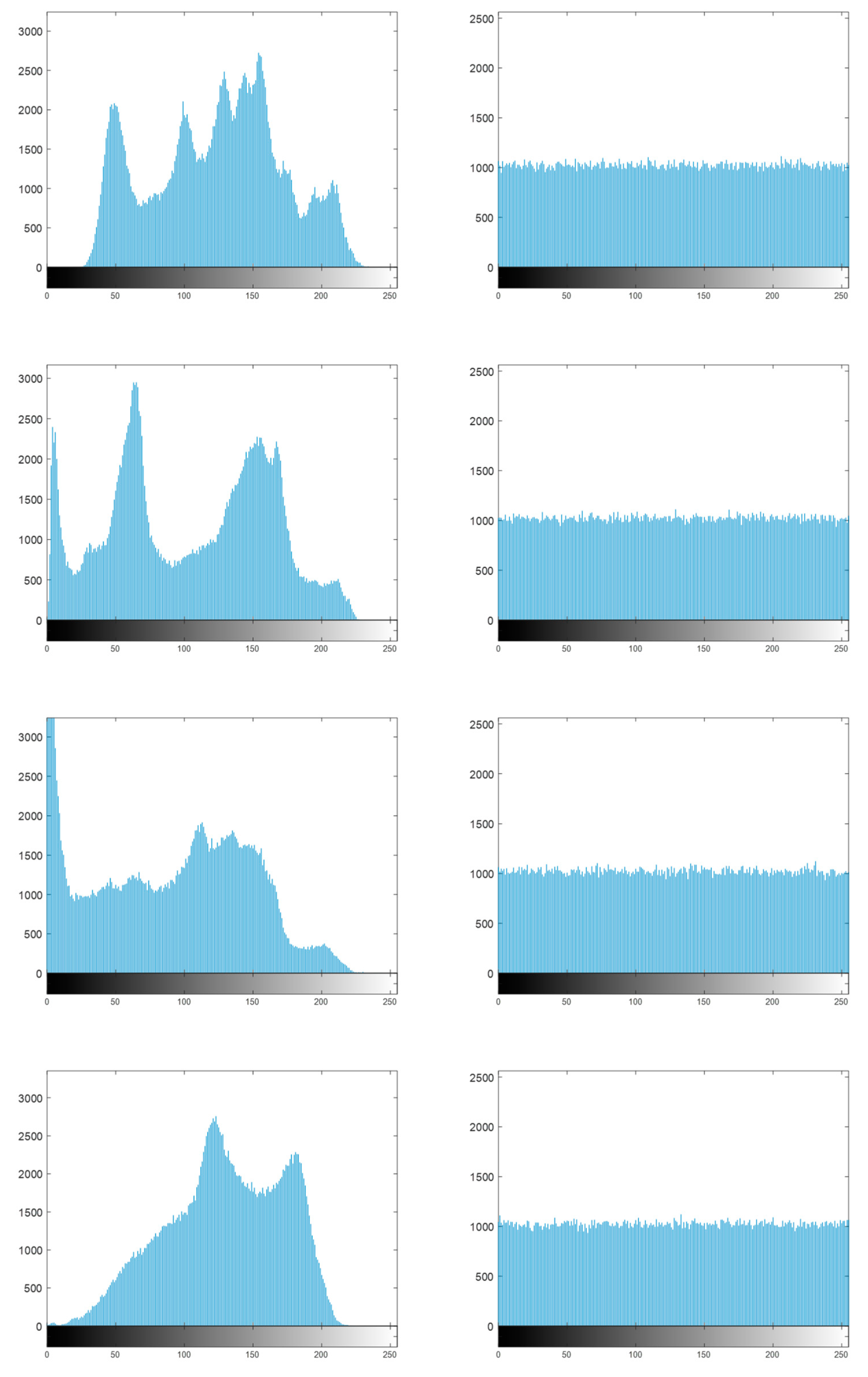
Figure 7.
Histogram analysis (top to down: Lena, Peppers, Man and Baboon).
Figure 7.
Histogram analysis (top to down: Lena, Peppers, Man and Baboon).
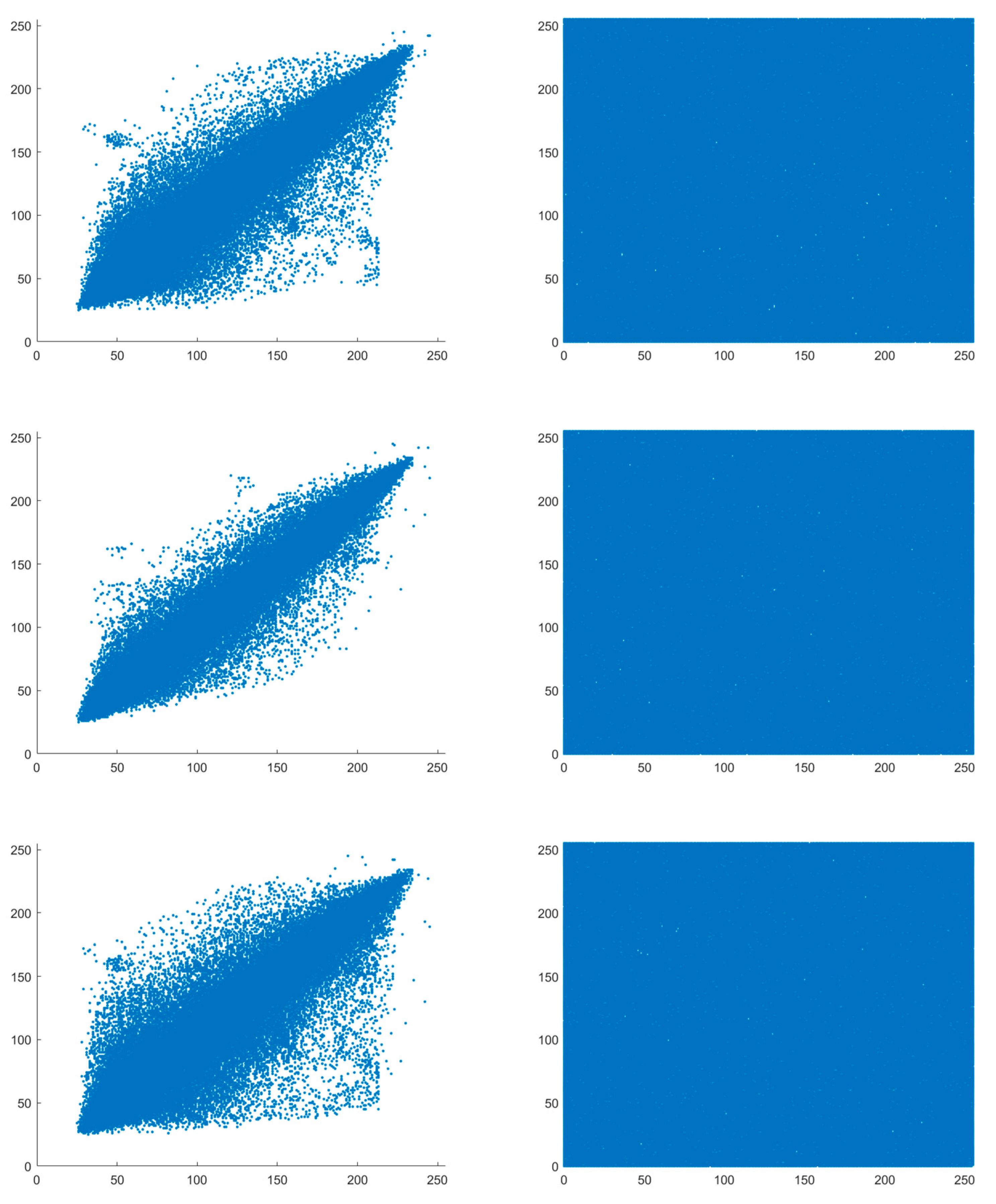
Figure 8.
Pixel correlation between Lena image and its ciphertext image in various directions (Left: plaintext image Right: ciphertext image, top to down: Horizontal, Vertical, and Diagonal).
Figure 8.
Pixel correlation between Lena image and its ciphertext image in various directions (Left: plaintext image Right: ciphertext image, top to down: Horizontal, Vertical, and Diagonal).
Table 1.
Results of NIST randomness test for HLITC.
Table 1.
Results of NIST randomness test for HLITC.
| Test Name |
P-value |
Results |
| Approximate entropy test |
0.9548 |
Success |
| Block frequency test |
0.0383 |
Success |
| Cumulative sums (forward) test |
0.2631 |
Success |
| FFT test |
0.2789 |
Success |
| Frequency test |
0.2919 |
Success |
| Linear complexity test |
0.8934 |
Success |
| Longest runs of ones test |
0.4398 |
Success |
| Nonoverlapping template matching test |
0.9961 |
Success |
| Overlapping template matching test |
0.4771 |
Success |
| Binary matrix rank test |
0.9562 |
Success |
| Runs test |
0.3959 |
Success |
| Serial test |
0.0297 |
Success |
| Maurer's universal statistical test |
0.4439 |
Success |
| Random excursions test |
0.3061 |
Success |
| Random excursions variant test |
0.0527 |
Success |
Table 2.
Histogram variance analysis of ciphertext image.
Table 2.
Histogram variance analysis of ciphertext image.
| Encryption method (ciphertext image) |
Histogram variance |
| [37] (Lena) |
242.4651 |
| [38] (Lena) |
124.6218 |
| [34] (Lena) |
68.9023 |
| Our method (Lena) |
31.5731 |
| Our method (Peppers) |
29.7752 |
| Our method (Man) |
32.6184 |
| Our method (Baboon) |
30.2543 |
Table 3.
Comparison of NPCR and UCAI results.
Table 3.
Comparison of NPCR and UCAI results.
| Metrics |
Our method |
[37] |
[38] |
| NPCR |
99.6627 |
99.6134 |
99.6283 |
| UCAI |
33.64 |
33.28 |
33.53 |
Table 4.
Information entropy comparison.
Table 4.
Information entropy comparison.
| Plaintext image |
Cipher text image |
[37] |
[38] |
| 7.4455 |
7.9986 |
7.9935 |
7.9926 |