Submitted:
19 September 2023
Posted:
21 September 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Preliminaries
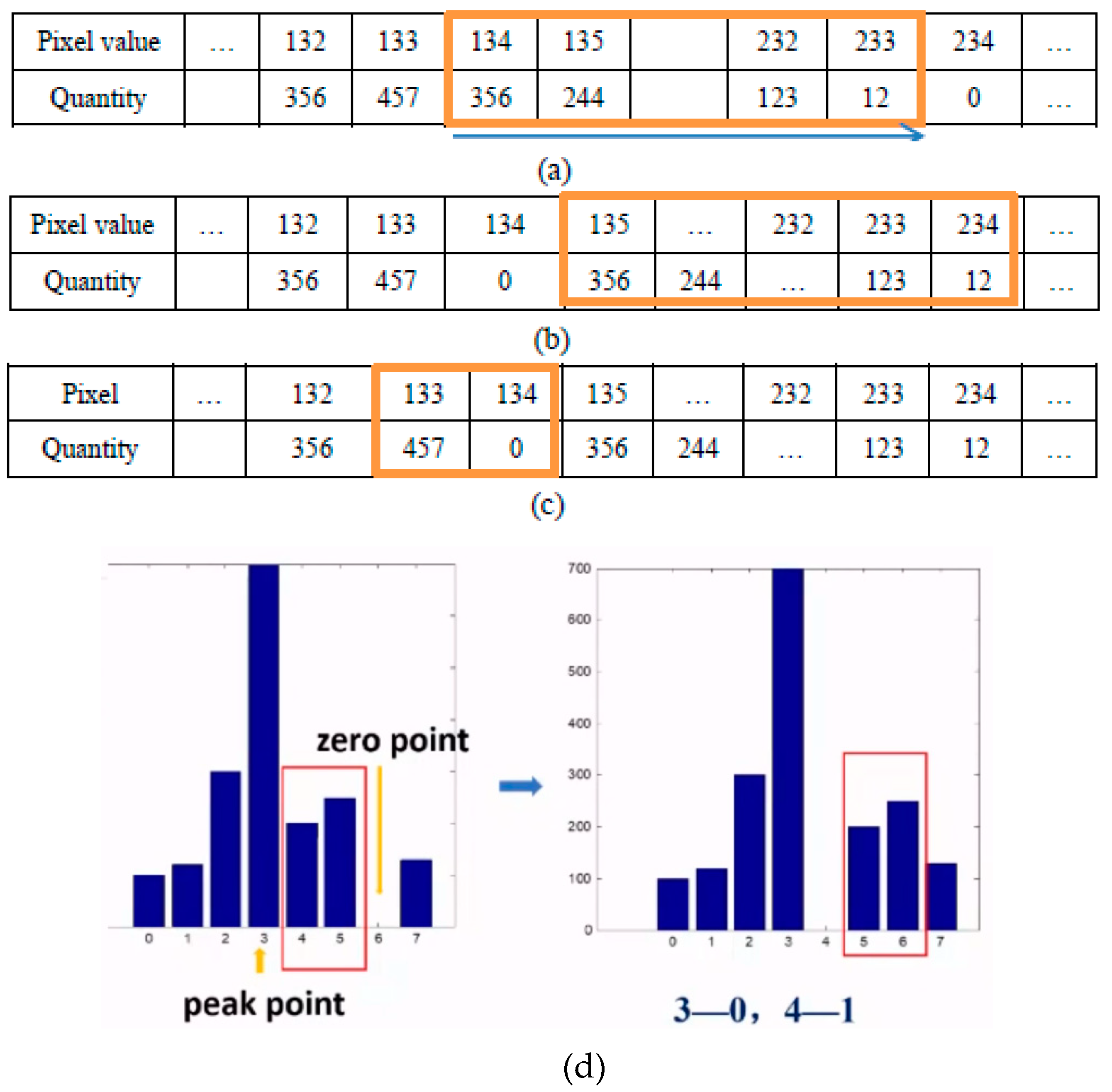
2.1. Reversible watermarking
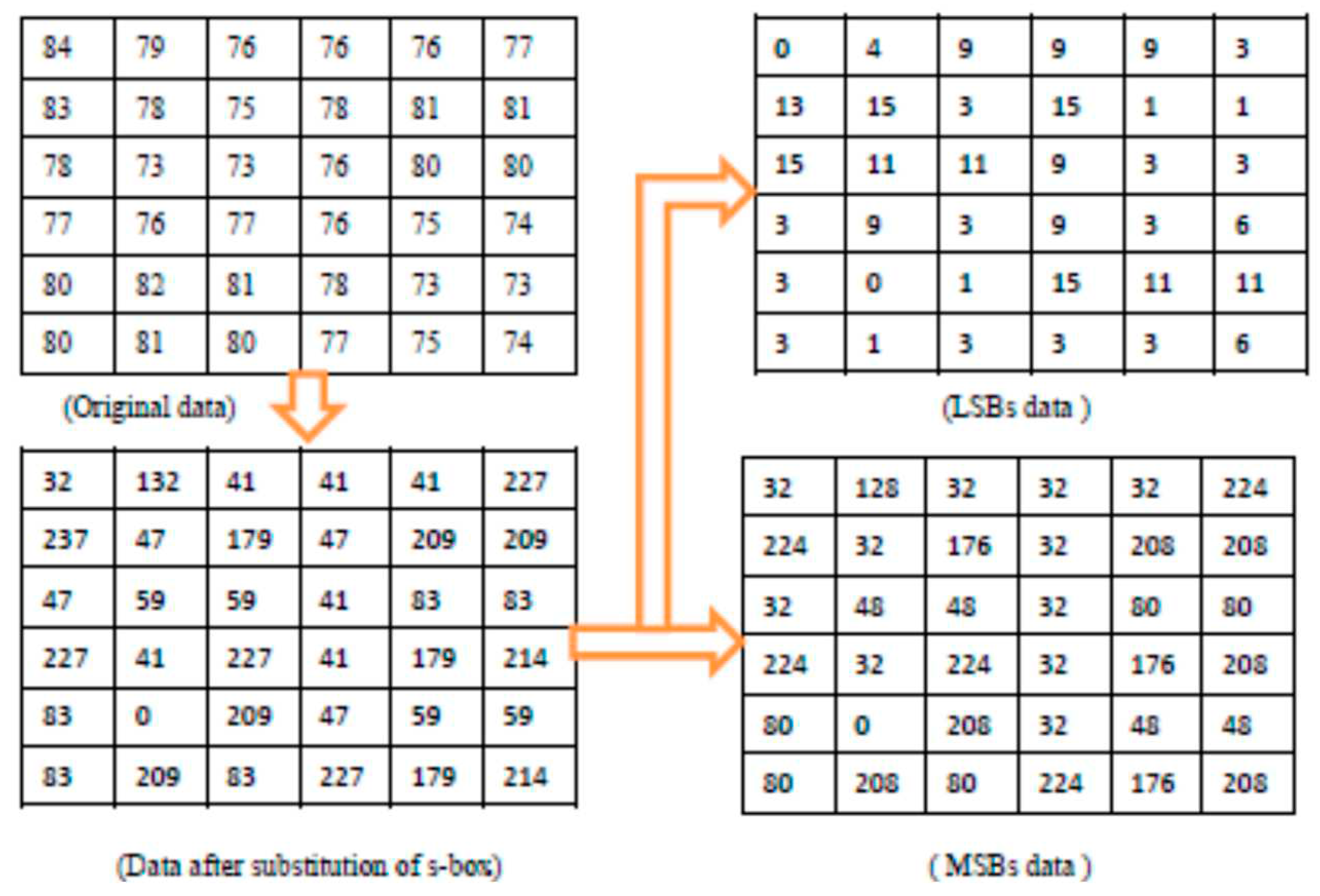
2.2. S-boxes
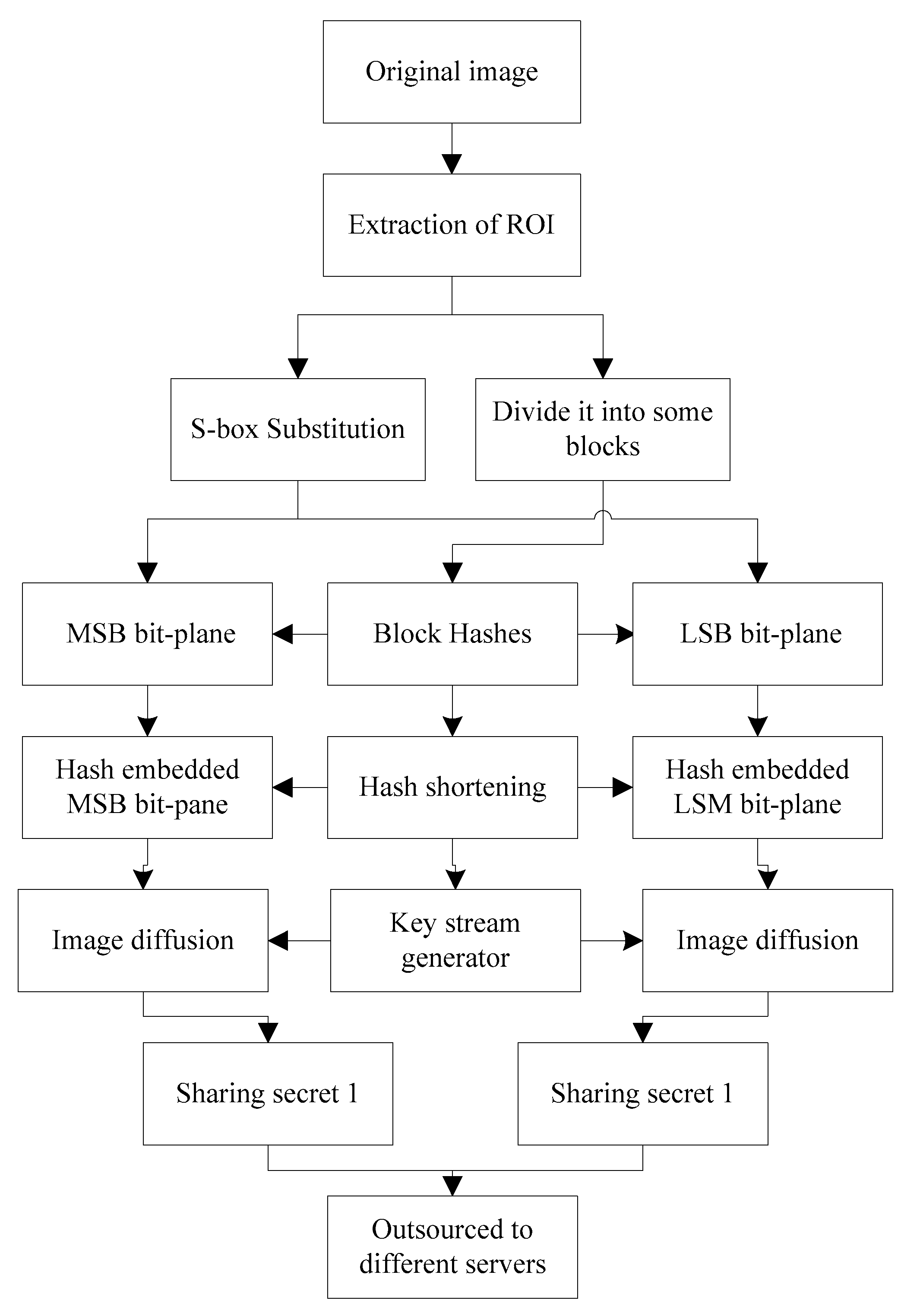
3. Proposed scheme
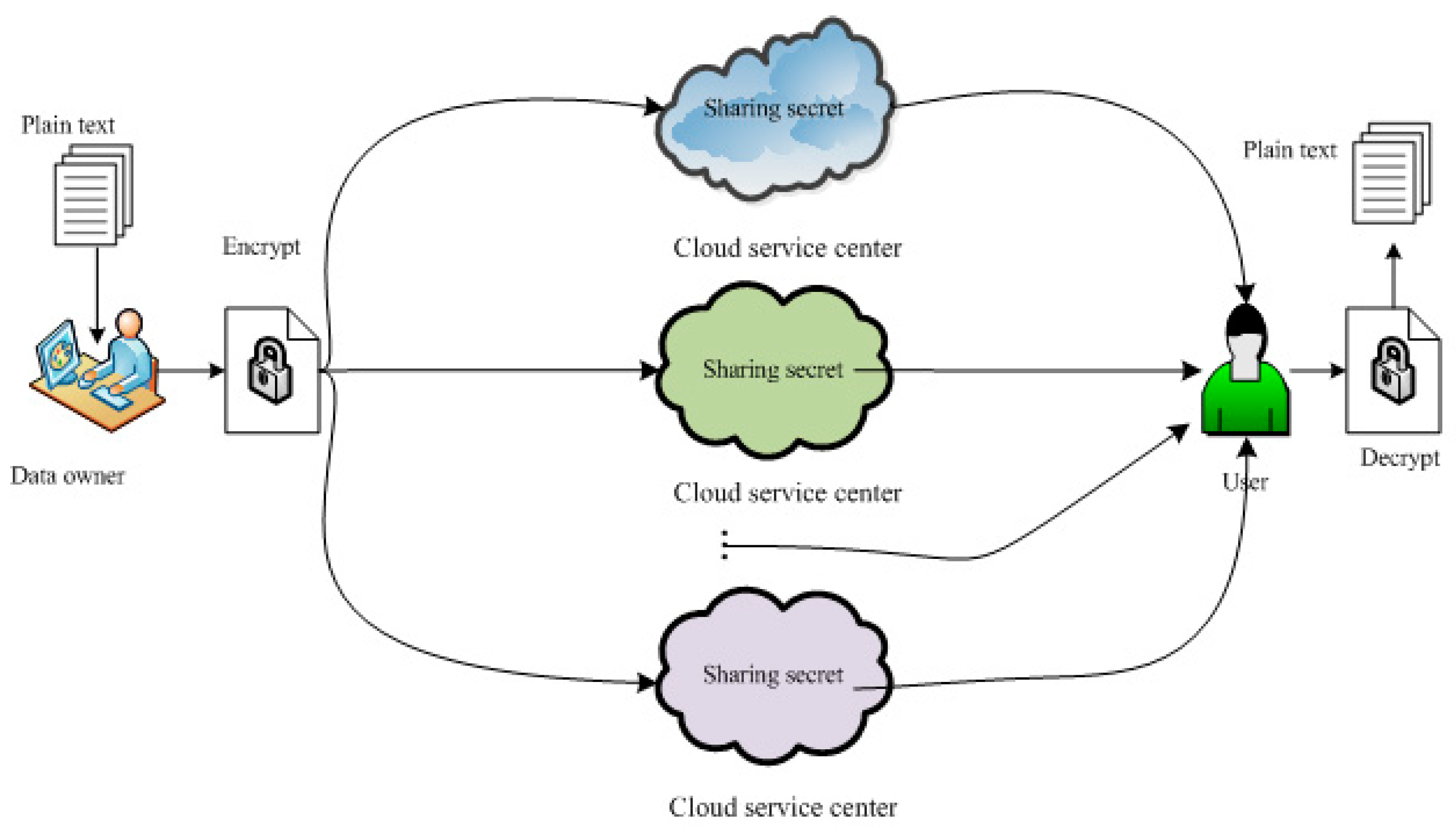
3.1. Generation of sharing secret
3.2. Restoration of original secret image
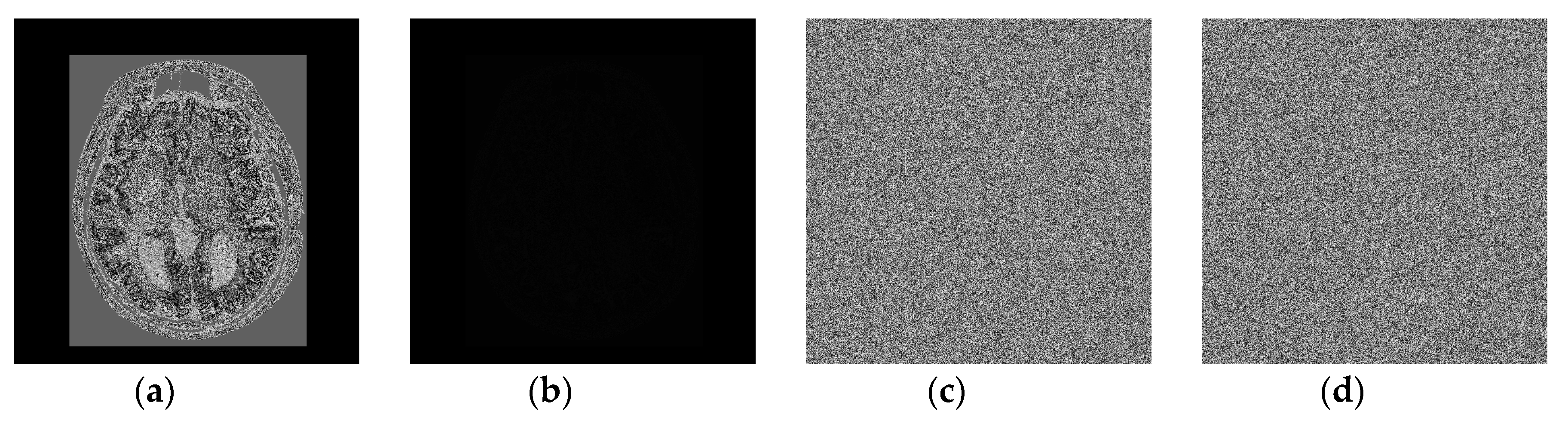
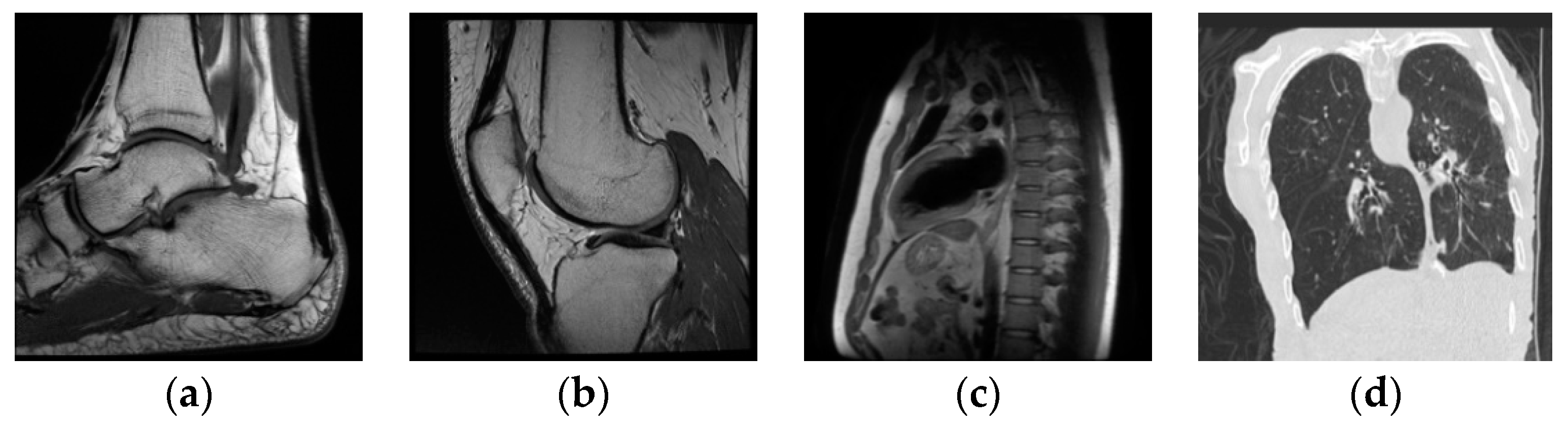
4. Experimental results and discussions
4.1. Experimental results
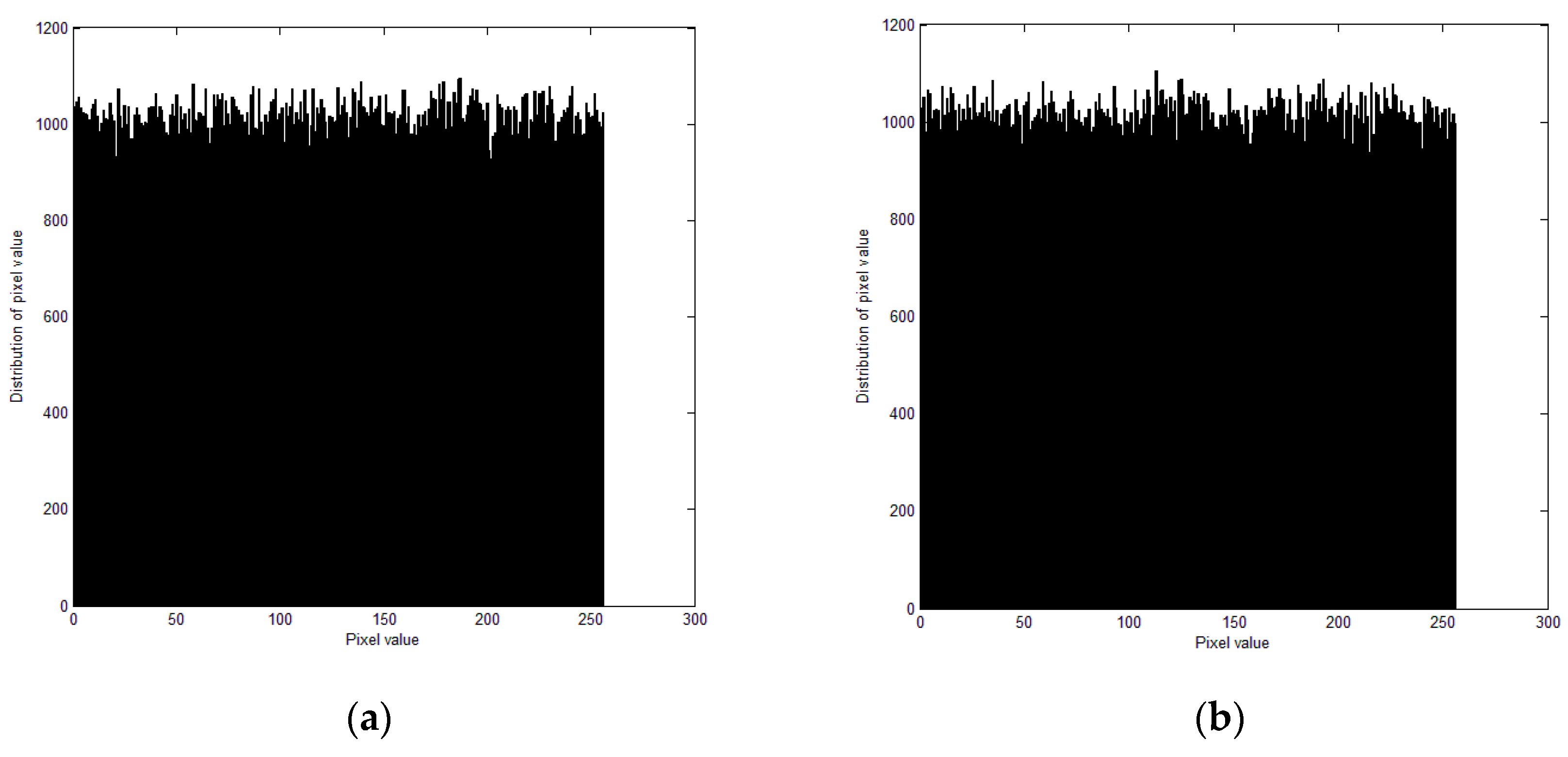
4.2. Security analysis of the proposed scheme
4.3. Privacy protection analysis
4.4. Tampers localization of restored image.
4.5. Comparison Analysis of Performance
- (1)
- Comparison with the existing encryption algorithms
- (2)
- Comparison with the existing Crypto-Watermarking algorithms
- (3)
- Comparison with newly proposed verifiable secret sharing for outsourcing images into cloud
5. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
References
- Keying Li and Hua Ma: Outsourcing decryption of multi-authority ABE cipher texts. International Journal of Network Security 2014, 16, 286–294.
- Arpita Banik, Zeba Shamsi, Dolendro Singh Laiphrakpam, An encryption scheme for securing multiple medical images. Journal of Information Security and Applications 2019, 49, 102398. [CrossRef]
- Praveen Kumar P, Syam Kumar P, Alphonse P. J.A. Attribute based encryption in cloud computing: A survey, gap analysis, and future directions. Journal of Network and Computer Applications 2018, 108, 37–52. [Google Scholar] [CrossRef]
- D. Agrawal, A. A. El, F. Emekci, A.Metwally and S. Wang: Secure data management service on cloud computing infrastructures, Proceedings of Service and Application Design Challenges in the Cloud, (2011) 57-80.
- J. L. Dautrich and C. V. Ravishankar: Security limitations of using secret sharing for data outsourcing, in Proc. of Proceedings of the 26th Annual IFIP WG 11.3 Conference on Data and Applications Security and Privacy, Paris, France, (2012) 145-160.
- Hui Zhu, Rongxing Lu, Cheng Huang et. al: An efficient privacy-preserving location-based services query scheme in outsourced cloud. IEEE Transactions on Vehicular Technology 2016, 65, 7729–7739. [Google Scholar] [CrossRef]
- Qin Zou, Jianfeng Wang, Jun Ye et. al: Efficient and secure encrypted image search in mobile cloud computing. Soft Computing 2016, 4, 1–11. [Google Scholar]
- Abandah, G.; Hussein, N.; Al-Haj, A. Crypto-based algorithms for secured medical image transmission. IET Inf. Secur. 2015, 9, 365–373. [Google Scholar] [CrossRef]
- Hua, Z.; Yi, S.; Zhou, Y. Medical image encryption using high-speed scrambling and pixel adaptive diffusion. Signal Process. 2018, 144, 134–144. [Google Scholar] [CrossRef]
- Kanso, A.; Ghebleh, M. An efficient and robust image encryption scheme for medical applications. Commun. Nonlinear Sci. Numer. Simul. 2015, 24, 98–116. [Google Scholar] [CrossRef]
- Fu, C.; Meng, W.-H.; Zhan, Y.-F.; Zhu, Z.-L.; Lau, F.C.; Tse, C.K.; Ma, H.-F. An efficient and secure medical image protection scheme based on chaotic maps. Comput. Biol. Med. 2013, 43, 1000–1010. [Google Scholar] [CrossRef]
- J. B. Lima, F.Madeiro, F.J.R.Sales, Encryption of medical images based on the cosine number transform. Signal Processing: Image Communication 2015, 35, 1–8. [Google Scholar]
- Huang, L.-C.; Tseng, L.-Y.; Hwang, M.-S. A reversible data hiding method by histogram shifting in high quality medical images. J. Syst. Softw. 2013, 86, 716–727. [Google Scholar] [CrossRef]
- Loan, N.A.; Parah, S.A.; Sheikh, J.A.; Akhoon, J.A.; Bhat, G.M. Hiding Electronic Patient Record (EPR) in medical images: A high capacity and computationally efficient technique for e-healthcare applications. J. Biomed. Informatics 2017, 73, 125–136. [Google Scholar] [CrossRef] [PubMed]
- Eswaraiah, R.; Reddy, E.S. Robust medical image watermarking technique for accurate detection of tampers inside region of interest and recovering original region of interest. IET Image Process. 2015, 9, 615–625. [Google Scholar] [CrossRef]
- Singh, A.K.; Dave, M.; Mohan, A. Hybrid technique for robust and imperceptible multiple watermarking using medical images. Multimedia Tools Appl. 2015, 75, 8381–8401. [Google Scholar] [CrossRef]
- Shiu, C.-W.; Chen, Y.-C.; Hong, W. Encrypted image-based reversible data hiding with public key cryptography from difference expansion. Signal Process. Image Commun. 2015, 39, 226–233. [Google Scholar] [CrossRef]
- Zhou, J.; Sun, W.; Dong, L.; Liu, X.; Au, O.C.; Tang, Y.Y. Secure Reversible Image Data Hiding Over Encrypted Domain via Key Modulation. IEEE Trans. Circuits Syst. Video Technol. 2015, 26, 441–452. [Google Scholar] [CrossRef]
- Singh, P.; Raman, B. Reversible data hiding for rightful ownership assertion of images in encrypted domain over cloud. AEU - Int. J. Electron. Commun. 2017, 76, 18–35. [Google Scholar] [CrossRef]
- Zhang, W.; Wang, H.; Hou, D.; Yu, N. Reversible Data Hiding in Encrypted Images by Reversible Image Transformation. IEEE Trans. Multimedia 2016, 18, 1469–1479. [Google Scholar] [CrossRef]
- Singh, P.; Raman, B. Reversible data hiding based on Shamir’s secret sharing for color images over cloud. Inf. Sci. 2018, 422, 77–97. [Google Scholar] [CrossRef]
- Wu, H.-Z.; Shi, Y.-Q.; Wang, H.-X.; Zhou, L.-N. Separable Reversible Data Hiding for Encrypted Palette Images With Color Partitioning and Flipping Verification. IEEE Trans. Circuits Syst. Video Technol. 2016, 27, 1620–1631. [Google Scholar] [CrossRef]
- Bouslimi, D.; Coatrieux, G. A crypto-watermarking system for ensuring reliability control and traceability of medical images. Signal Process. Image Commun. 2016, 47, 160–169. [Google Scholar] [CrossRef]
- Zope-Chaudhari, S.; Venkatachalam, P.; Buddhiraju, K.M. Secure Dissemination and Protection of Multispectral Images Using Crypto-Watermarking. IEEE J. Sel. Top. Appl. Earth Obs. Remote. Sens. 2015, 8, 5388–5394. [Google Scholar] [CrossRef]
- Xiang, T.; Hu, J.; Sun, J. Outsourcing chaotic selective image encryption to the cloud with steganography. Digit. Signal Process. 2015, 43, 28–37. [Google Scholar] [CrossRef]
- Gao, H.; Hu, M.; Gao, T.; Cheng, R. Random Grid and Reversible Watermarking-Based On Verifiable Secret Sharing for Outsourcing Images in Cloud. Int. J. Digit. Crime Forensics 2018, 10, 24–39. [Google Scholar] [CrossRef]
- Arsalan, M.; Qureshi, A.S.; Khan, A.; Rajarajan, M. Protection of medical images and patient related information in healthcare: Using an intelligent and reversible watermarking technique. Appl. Soft Comput. 2017, 51, 168–179. [Google Scholar] [CrossRef]
- Ping, P.; Zhang, X.; Yang, X.; Hashems, Y.A.A. A novel medical image encryption based on cellular automata with ROI position embedded. Multimedia Tools Appl. 2022, 81, 7323–7343. [Google Scholar] [CrossRef]
- Liu, Z.; Li, J.; Ai, Y.; Zheng, Y.; Liu, J. A robust encryption watermarking algorithm for medical images based on ridgelet-DCT and THM double chaos. J. Cloud Comput. 2022, 11, 1–20. [Google Scholar] [CrossRef]
- Xiaojun Qi, Xing Xin: A singular-value-based semi-fragile watermarking scheme for image content authentication with tamper localization. Journal of Visual Communication and Image Representation 2015, 30, 312–327. [CrossRef]
- Nasrin, M. Makbol, Bee Ee Khoo: A new robust and secure digital image watermarking scheme based on the integer wavelet transform and singular value decomposition. Digital Signal Processing 2014, 33, 134–147. [Google Scholar]
- Zhang Wenyin, Frank Y. Shih: Semi-fragile spatial watermarking based on local binary pattern operators. Optics Communications 2011, 284, 3904–3912. [Google Scholar] [CrossRef]
- Ni, Z. , Shi, Y.Q., Ansari, N., Su, W.: Reversible data hiding. IEEE Transactions on Circuits Systems for Video Technology. 2006, 16, 354–362. [Google Scholar]
- Souravlias, D.; Parsopoulos, K.E.; Meletiou, G.C. Designing bijective S-boxes using Algorithm Portfolios with limited time budgets. Appl. Soft Comput. 2017, 59, 475–486. [Google Scholar] [CrossRef]
- Pak, C.; Huang, L. A new color image encryption using combination of the 1D chaotic map. Signal Process. 2017, 138, 129–137. [Google Scholar] [CrossRef]
- A Pandey , BS Saini , B Singh ,An Integrated Approach Using Chaotic Map & Sample Value Difference Method for Electrocardiogram Steganography and OFDM Based Secured Patient Information Transmission. Journal of Medical Systems 2017, 41, 187.
- C. Zhu, A novel image encryption scheme based on improved hyper-chaotic sequences. Opt Communications. 2012, 285, 29–37. [Google Scholar] [CrossRef]
- [36] https://www.sirm.org/category/senza-categoria/covid-19/.
- https://radiopaedia.org/ Accessed April 9, 2020.
- https://www.kaggle.com/tawsifurrahman/covid19-radiography-database/ Accessed April 9, 2020. 9 April.


| Sbox | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 0 | 99 | 124 | 119 | 123 | 242 | 107 | 111 | 197 | 48 | 1 | 103 | 43 | 254 | 215 | 171 | 118 |
| 1 | 202 | 130 | 201 | 125 | 250 | 89 | 71 | 240 | 173 | 212 | 162 | 175 | 156 | 164 | 114 | 192 |
| 2 | 183 | 253 | 147 | 38 | 54 | 63 | 247 | 204 | 52 | 165 | 229 | 241 | 113 | 216 | 49 | 21 |
| 3 | 4 | 199 | 35 | 195 | 24 | 150 | 5 | 154 | 7 | 18 | 128 | 226 | 235 | 39 | 178 | 117 |
| 4 | 9 | 131 | 44 | 26 | 27 | 110 | 90 | 160 | 82 | 59 | 214 | 179 | 41 | 227 | 47 | 132 |
| 5 | 83 | 209 | 0 | 237 | 32 | 252 | 177 | 91 | 106 | 203 | 190 | 57 | 74 | 76 | 88 | 207 |
| 6 | 208 | 239 | 170 | 251 | 67 | 77 | 51 | 133 | 69 | 249 | 2 | 127 | 80 | 60 | 159 | 168 |
| 7 | 81 | 163 | 64 | 143 | 146 | 157 | 56 | 245 | 188 | 182 | 218 | 33 | 16 | 255 | 243 | 210 |
| 8 | 205 | 12 | 19 | 236 | 95 | 151 | 68 | 23 | 196 | 167 | 126 | 61 | 100 | 93 | 25 | 115 |
| 9 | 96 | 129 | 79 | 220 | 34 | 42 | 144 | 136 | 70 | 238 | 184 | 20 | 222 | 94 | 11 | 219 |
| 10 | 224 | 50 | 58 | 10 | 73 | 6 | 36 | 92 | 194 | 211 | 172 | 98 | 145 | 149 | 228 | 121 |
| 11 | 231 | 200 | 55 | 109 | 141 | 213 | 78 | 169 | 108 | 86 | 244 | 234 | 101 | 122 | 174 | 8 |
| 12 | 186 | 120 | 37 | 46 | 28 | 166 | 180 | 198 | 232 | 221 | 116 | 31 | 75 | 189 | 139 | 138 |
| 13 | 112 | 62 | 181 | 102 | 72 | 3 | 246 | 14 | 97 | 53 | 87 | 185 | 134 | 193 | 29 | 158 |
| 14 | 225 | 248 | 152 | 17 | 105 | 217 | 142 | 148 | 155 | 30 | 135 | 233 | 206 | 85 | 40 | 223 |
| 15 | 140 | 161 | 137 | 13 | 191 | 230 | 66 | 104 | 65 | 153 | 45 | 15 | 176 | 84 | 187 | 22 |
| Images for test | Coordinate of upper left of ROI | Coordinate of lower right of ROI |
|---|---|---|
| IM-0001-0004 | (102,118) | (405,453) |
| IM-0001-0010 | (83,70) | (434, 469) |
| IM-0001-0012 | (83,55) | (434,486) |
| IM-0001-0014 | (75,66) | (426,481) |
| IM-0001-0019 | (102,1) | (357,480) |
| IM-0002-0022 | (81,17) | (448,448) |
| Image | IM-0001-0004 | IM-0001-0010 | IM-0001-0012 | IM-0001-0014 | IM-0001-0019 | IM-0002-0022 |
| UACI | 0.3355 | 0.3339 | 0.3348 | 0.3343 | 0.3343 | 0.3351 |
| NPCR | 0.9961 | 0.9960 | 0.9959 | 0.9961 | 0.9961 | 0.9964 |
| Image | Sharing secret | Horizontal | Vertical | Diagonal |
| IM-0001-0004 | Sharing secret 1 | -0.0056 | -0.0073 | -0.0024 |
| Sharing secret 2 | -0.0011 | -0.0096 | -0.0107 | |
| IM-0001-0010 | Sharing secret 1 | -0.0105 | -0.0128 | 0.0198 |
| Sharing secret 2 | -0.01232 | 0.0016 | 0.0110 | |
| IM-0001-0012 | Sharing secret 1 | -0.0085 | -0.0131 | 0.0011 |
| Sharing secret 2 | -0.0016 | 0.0044 | 0.0001 | |
| IM-0001-0014 | Sharing secret 1 | -0.0217 | 0.0031 | -0.0026 |
| Sharing secret 2 | -0.0067 | 0.0088 | -0.0028 | |
| IM-0001-0019 | Sharing secret 1 | 0.0073 | -0.0022 | -0.0053 |
| Sharing secret 2 | 0.0021 | 0.0039 | 0.0011 | |
| IM-0001-0022 | Sharing secret 1 | 0.0018 | -0.0213 | 0.0016 |
| Sharing secret 2 | 0.0026 | -0.0136 | -0.0029 |
| The scheme | Integrity verification | Tamper localization |
| Ali Al-Haj [8] | Yes | No |
| Hua [9] | No | No |
| A. Kanso [10] | No | No |
| Chong Fu [11] | No | No |
| J.B. Lima [12] | No | No |
| Ping [28] | No | No |
| Proposed scheme | Yes | Yes |
| The scheme | Integrity verification | Tamper localization | Error in image recovery (ROI) |
| Priyanka [19] | No | No | / |
| Zhang [20] | No | No | No |
| Priyanka [21] | No | No | Yes |
| Wu [22] | No | No | No |
| Sangita [24] | No | No | Yes |
| Xiang [25] | No | No | No |
| Ping [28] | No | No | No |
| Liu [29] | No | No | No |
| Proposed scheme | Yes | Yes | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





