Submitted:
17 June 2025
Posted:
19 June 2025
You are already at the latest version
Abstract
Keywords:
Condensed Introduction
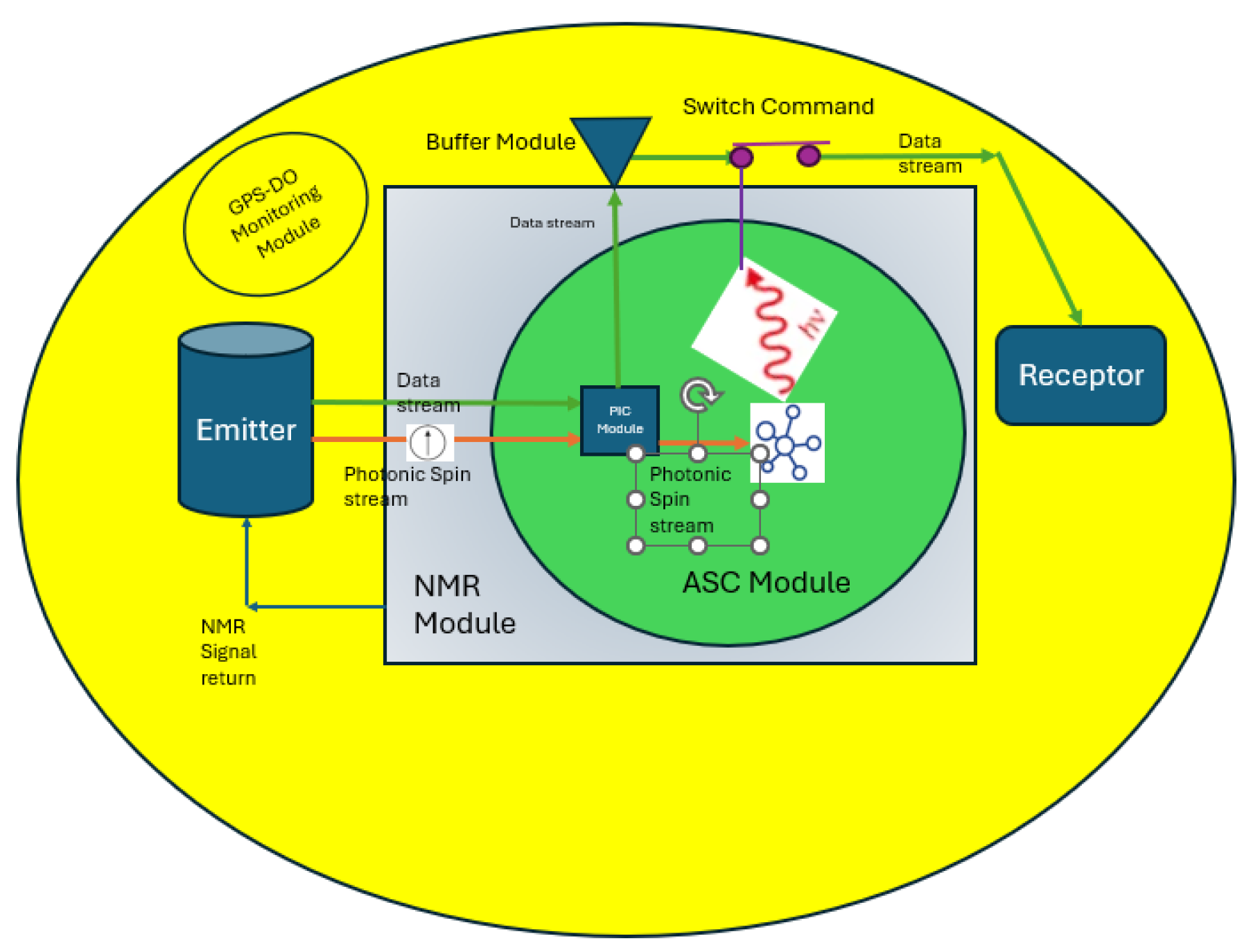
1. System Overview and Physical Principles
1.1. Purpose and Technical Field
- First Channel (Photon Spin): The molecule is excited exclusively by a directed photon whose spin (circular polarization) matches the molecular selectivity, ensuring only the correct quantum state can initiate the excitation.
- Second Channel (active NMR feedback): Simultaneously, the molecule’s atoms or electrons are aligned and actively monitored by an external magnetic field, configured enable the state change and to allow the generation of a measurable NMR (nuclear magnetic resonance) signal [2,5,11]. Upon successful activation, this NMR response is detected locally, and the resulting signal is relayed back to the emitter, serving as a physical confirmation of the trust event. When all activation criteria are met—precisely synchronized photon spin excitation and active NMR-coupled magnetic alignment—does the irreversible physical transition occur. The protocol-authorized NMR signal, sent back to the emitter within the GPSDO-enforced time window, both locks trust at the hardware level and provides tamper-evident, side-channel-resistant confirmation, preventing spoofing, replay, or unauthorized intervention by digital or physical means.
1.2. Departure from Prior Art
- -
- a photon with defined spin (circular polarization)
- -
- a specific measurable NMR response
- -
- and a synchronized time reference.
2. Core Trust Mechanism
2.1. Physical Components
-
Three physical embedded keys:
- ○
-
A photon emitter (such as a laser or LED) capable of producing photons with defined frequency and circular polarization (spin). Received by fibre optic physical machine connection, to incapacitate spoofing [1,3,9].
- ▪
- Sensors to detect molecular state transitions (optical or electronic readout).
- ○
- An active magnetic field generator (such as a solenoid or integrated micro-magnet) is used at the molecular site, to enable and control the generation of a measurable nuclear magnetic resonance (NMR) response. Upon successful photonic excitation and correct field conditions, the molecular state change produces a distinct NMR signal, which is detected in real time by local sensors and immediately relayed back to the emitter. This NMR feedback serves as a physical confirmation of both molecular state and correct protocol execution, forming a closed-loop handshake that provides strong side-channel and tamper resistance. The magnetic field could be modulated or coded—for example, using pre-agreed patterns, pulse sequences, or operator-set configurations—to enable dynamic channel selection, further enhance anti-spoofing, and support operator intervention or automated authentication logic. All magnetic field changes and resulting NMR responses are monitored and logged by the system for auditability and forensics.
- ○
- The machine’s photon emitter directs a photon of the exact required frequency and spin at the target molecule,
- The molecule is in the correct magnetic or electronic alignment provided by the magnetic field,
- The excitation event occurs within a narrowly defined time window, synchronized to the system’s high-precision time reference (e.g., GPSDO or atomic clock).
- Simultaneously, a synchronized digital ON/OFF control signal (e.g., session nonce or challenge code) is transmitted and validated.
2.2 Trust Protocol Flow
-
System Initialization
- ○
- Each machine is equipped with a trust node comprising spin-sensitive molecular receptors, a photon emitter, a magnetic field generator, state and orientation sensors, and a synchronized time reference.
- ○
- The magnetic field orientation is set and verified by a trusted source operator, optionally using an externally signalled pattern.
-
Photon Emission
- ○
- The initiating machine directs a photon of the specified frequency and circular polarization through a secure fibre optic connection to the receiving machine.
-
Magnetic Field and NMR Channel Verification
- ○
- The receiving machine applies the active magnetic field to align the molecule(s) for protocol compliance and to enable NMR signal detection. Integrated sensors verify that the molecule is both correctly aligned and capable of producing the required NMR response.
-
Digital Signal Synchronization
- ○
- A synchronized digital ON/OFF control signal is transmitted and validated according to the established protocol and time reference.
-
Physical Activation, Molecular State Change, and NMR Feedback
- ○
- Only if all physical activation channels (photon spin and active magnetic field/NMR alignment) and the synchronized digital protocol are satisfied, the molecule undergoes the designated state change (excitation and return/relaxation).
- ○
- This event generates a measurable NMR (nuclear magnetic resonance) signal, which is detected in real time by local sensors and immediately relayed back to the emitter as a physical confirmation of the trust event, all within the authorized time window.
-
Closed-Loop Trust Validation
- ○
- The flip event and NMR response are tracked from the initial emission of the spin-polarized photon by the source, through the molecular state change, to the return NMR signal detected at the emitter.
- ○
- This closed physical feedback loop ensures complete protocol synchronization and trust validation, from emission to relaxation, not merely at a single point.
-
Trust Gate Outcome
- ○
- If all conditions are met and the NMR confirmation is received within the correct time window, trust is established and locked between the two machines at the physical level.
- ○
- Any deviation—incorrect photon, incorrect magnetic field or NMR signal, protocol mismatch, or attempted tampering—prevents or destroys the trust event.
- ○
- Re-initiating the connection protocol requires direct re-execution of the full physical pairing process at the molecular or device interface; it cannot be digitally replayed or reset.
-
Audit and Recovery
- ○
- The pairing system maintains records of all trust events, NMR signals, and protocol failures for audit and maintenance purposes.
- ○
- If a trust failure or tampering is detected, the event is logged, and the user or operator must initiate defined alternative procedures or security solutions.
-
Continuous Monitoring
- ○
- The system continuously monitors the molecular state, magnetic orientation, and NMR signal integrity. Any detected change, drift, anomaly, or abnormal feedback triggers automatic trust severance and security response.
2.3. Triple-Channel Security and Anti-Spoofing (NMR-Aligned Revision)
-
First Channel (Photon Spin):Only a photon with the precisely defined spin state (circular polarization) and frequency can activate the spin-sensitive molecular receptor. This quantum specificity prevents unauthorized excitation of the molecule by any other light source.
-
Second Channel (Active Magnetic Field and NMR Feedback):The molecule must be aligned by a precisely oriented and actively controlled magnetic field, configured to both enable the trust event and generate a measurable NMR (nuclear magnetic resonance) response. Upon successful state change, the resulting NMR signal is detected locally and relayed back to the emitter as a physical confirmation of event completion, providing a closed-loop, physically authenticated handshake.
-
Third Channel (Time Synchronization Protocol):Trust activation is only permitted within an exact, globally synchronized time window, enforced by a GPS-disciplined oscillator (GPSDO) or atomic clock protocol. This time channel ensures that even perfect reproduction of photon and magnetic/NMR conditions outside the permitted time window results in automatic rejection, preventing replay, delay, or asynchronous spoofing.
-
Triple-Channel “Quantum Physical AND Gate”:All three channels—photon spin, NMR-active magnetic alignment, and time—must be satisfied simultaneously for a valid trust event. Any mismatch or absence of the correct NMR feedback within the protocol window immediately invalidates the event and triggers tamper response.
-
Technical Note on Channel Independence:While the magnetic/NMR and photonic channels can each serve as secondary or fallback gates, maximum anti-spoofing assurance is achieved only when all three are enforced together. Any channel being optional or independently bypassed would reduce overall protocol resistance.
-
Synchronization and Coding:Each channel (photon, NMR-magnetic, and timing) can be synchronously or asynchronously modulated with operator-defined or automated codes. Trust activation is permitted only when all three channels are confirmed within the GPSDO-defined window, and the required NMR feedback is verified by hardware and protocol controllers.
-
Security Advantages:
- ○
- Forces attackers to match photon, magnetic/NMR, and exact timing in real time.
- ○
- Closed-loop NMR feedback ensures that only protocol-compliant events are acknowledged.
- ○
- Automatically logs and rejects any attempt at spoofing, replay, or asynchronous activation.
-
Practicality:
- ○
- All three channels are supported by commercially available optoelectronic, NMR, and GPSDO technologies.
- ○
- Real-time synchronization, monitoring, and audit logging are standard features.
-
Conclusion:Trust is established only when photon spin, active NMR-magnetic alignment (with return NMR feedback), and time synchronization are all satisfied within the protocol-defined window. Trust events are unique, irreproducible, and non-repayable—delivering quantum-level anti-spoofing and physically auditable authentication.
2.4. Continuous Monitoring and Trust State Management (NMR-Integrated)
-
Molecular, Magnetic, and NMR State Monitoring:
- ○
- Integrated sensors monitor molecular state, active magnetic field conditions, photon arrival, and NMR signal response.
- ○
- The system continuously checks that all trust criteria—including correct NMR feedback—remain satisfied after pairing.
-
Deviation/Anomaly Detection:
- ○
- Any deviation in NMR signal, magnetic alignment, photon delivery, or digital protocol is immediately flagged.
- ○
- The system tracks NMR resonance signatures (for molecular state), magnetic orientation (via Hall-effect or magneto-resistive sensors), photon activity (via polarization-sensitive detectors), and digital timing (via GPSDO or atomic clock).
-
Audit Trail and Forensic Review:
- ○
- All trust events, failures, NMR responses, sensor data, operator actions, and system responses are securely logged with timestamps for maintenance, forensics, and regulatory compliance.
-
Tamper and Environmental Sensing:
- ○
- Tamper switches, environmental sensors (temperature, vibration, EM field), and protocol anomaly detection protect against physical and environmental attacks.
-
Immediate Trust Severance:
- ○
- Any failure to meet protocol or NMR feedback requirements triggers automatic severance (kill-switch), with the trust node physically or logically disconnected.
- ○
- Restoration is only possible through a strict, direct physical re-initialization protocol—never by digital reset or software fallback.
-
Optional Features:
- ○
- Periodic health checks, redundant trust nodes, and operator alerting for repeated anomalies may be implemented to further enhance reliability.
3. Triple-Channel Security and Anti-Spoofing
-
Photon Spin Channel
- ○
- Only photons with a specific frequency and defined circular polarization (left- or right-handed spin) are able to interact with and excite the engineered molecular receptor.
- ○
- This quantum specificity ensures that molecular activation can only be initiated by the intended quantum state, and cannot be triggered by arbitrary or spoofed photonic input.
-
Active Magnetic Field and NMR Feedback Channel
- ○
- The molecule must be located within a precisely controlled and actively monitored magnetic field, with orientation and intensity set according to strict protocol parameters.
- ○
- Upon successful photonic excitation and correct magnetic alignment, the molecular state change generates a measurable NMR (nuclear magnetic resonance) response.
- ○
- This NMR signal is detected in real time and relayed back to the emitter, serving as a closed-loop, physically authenticated confirmation of the trust event.
- ○
- Any deviation from required field or NMR signal conditions—including drift, incorrect intensity, misalignment, or missing/incorrect NMR feedback—blocks activation and is immediately logged.
-
Time Synchronization Channel
- ○
- All trust activations are constrained to a narrowly defined and globally synchronized time window, enforced by a high-precision time reference such as an atomic clock or GPS-disciplined oscillator (GPSDO).
- ○
- The protocol requires that both photon spin excitation and NMR-coupled magnetic alignment occur and be verified within this time window.
- ○
- Attempts to replay, delay, or activate the protocol outside the authorized interval are automatically rejected and logged as failed or tampered events.
-
Quantum Physical “AND Gate” Logic
- ○
- Trust is granted only when all three channels—photon spin, active NMR-magnetic feedback, and time synchronization—are present, valid, and protocol-compliant within the allowed window.
- ○
- This forms a quantum physical “AND gate”: if any requirement is unmet or out of sync, the molecular state does not change, and the trust event fails.
-
Security and Monitoring
- ○
- Each channel is monitored by independent sensors and the system logs all events for audit and forensics.
- ○
- The triple-channel logic, reinforced by closed-loop NMR feedback, provides robust resistance to spoofing, replay, and unauthorized activation; only protocol-compliant, physically unique trust events are ever acknowledged.#
- ○
- All event data—including timestamps, NMR readings, and channel states—are recorded to ensure system integrity, enable full maintenance, and support forensic analysis.
4. Trust Verification and Tamper Evidence
4.1. Measurement and Validation
-
NMR-Active Trust Confirmation:After each successful trust event, the system verifies the molecular state change and corresponding NMR (nuclear magnetic resonance) response using dedicated, protocol-integrated sensors. This validation confirms that (1) photon spin excitation, (2) active magnetic field conditions, and (3) NMR feedback occurred together and within the authorized GPSDO- or atomic clock–enforced time window. Only an NMR signal matching all pre-set physical, magnetic, and timing parameters is accepted as valid confirmation of trust.
-
Cross-Verification and Audit:Verification is rigorously cross-checked against expected event profiles, including photon characteristics, NMR resonance signatures, magnetic field configuration, and synchronized timestamps. Any mismatch, missing NMR feedback, or anomaly is immediately flagged, logged, and escalated for further analysis.
-
Continuous Tamper and Deviation Monitoring:Continuous monitoring of the molecular, magnetic/NMR, and photonic environment ensures that any unauthorized intervention, bypass attempt, or physical disturbance (including environmental or case intrusion) is instantly detected by the sensor array.
-
Immediate Trust Invalidity and Lockout:If a tamper event, protocol violation, or missing NMR confirmation is detected, the trust state is immediately invalidated, the trust gate is locked, and a secure audit event is written to the log. Re-activation is never automatic; re-establishment always requires physical, operator-controlled re-initialization.
-
Periodic Health Checks and Operator Tests:The system supports regular health monitoring and operator-initiated verification (challenge/response tests) to validate ongoing trust integrity. All such checks, together with every tamper or anomaly event, are securely time-stamped and archived for forensic review and regulatory compliance.This approach guarantees that trust, once established, is continuously verified and physically protected. Any attempt to spoof, replay, or tamper with the trust mechanism triggers immediate system response and denial of trust until full, secure re-initialization is completed.
4.2. Tamper Response, Audit, and Operator Protocol
-
Automated Trust Lockout and Logging:Upon detection of tampering, protocol violation, or anomaly—including unauthorized access, magnetic or NMR signal drift, sensor manipulation, or environmental disruption—the system immediately invalidates the current trust state and disables the trust gate.
-
Immutable Audit Logging:For every trust violation or significant system event, an immutable audit log entry is generated, including timestamp (from the high-precision clock), full anomaly details, affected trust node, and a summary of all automated system responses.
-
Operator and Security Notification:The system supports real-time alerts to operators or security personnel when critical events occur, via secure messaging, local alarms, or integration with external infrastructure.
-
Post-Event Verification and Inspection:Operators may perform physical inspection of the trust node, sensor recalibration, or environmental audits to verify event integrity and cause.
-
No Automatic Restoration:Trust re-establishment after a tamper event is never automatic. Restoration requires a secure, operator-controlled, physical re-initialization protocol, under direct supervision and formal approval.
-
Comprehensive Forensic Traceability:All tamper responses, operator interventions, and system actions are securely recorded for later forensic analysis and compliance reporting.
5. Scalability and Multi-Node Trust
5.1. Orthogonal Pairing
- Each trust channel is assigned a unique, orthogonal code (e.g., Hadamard matrix encoding, phase coding, or other code division methods). Photonic signals, magnetic field parameters, and NMR detection patterns for each channel are modulated according to these codes, ensuring that only the corresponding molecular trust node responds and generates a protocol-authorized NMR signal.
- Molecular receptor arrays are engineered for channel specificity, using molecular selectivity, spatial separation, and/or signal filtering. Each array responds only to its assigned code and NMR feedback profile.
- Multiple trust events may operate simultaneously: Each channel has its own physical and protocol parameters, with independent NMR confirmation and monitoring. Continuous real-time checking prevents crosstalk, replay, or unintended activation.
- Scalability is determined by channel and molecular selectivity: Practical implementations support 8–32 channels per device, with further scale enabled by advances in material science and microfabrication.
- All trust events, activations, NMR confirmations, and failures are logged per channel for audit, diagnostics, and performance management. Security is monitored continuously across all active trust links.
5.2. Integration
- Every node includes a hardware module providing precise, continuous time signals for protocol coordination and NMR feedback validation.
- All trust activation, NMR confirmation, and logging events are cross-referenced with the internal high-precision clock, ensuring that every channel, event, and node remains synchronized within the protocol-defined window.
- Synchronization drift or timing anomalies are automatically detected, resulting in alerts or protocol suspension until resolved.
- Channel codes, photonic/magnetic/NMR patterns, and trust state changes are timestamped and validated against the node’s clock.
- The integration protocol is clock-agnostic—any high-precision, tamper-proof clock is compatible, so long as it meets accuracy and security standards.
5.3. Channel Monitoring and Error Handling
- All physical and digital channels (photonics, magnetic/NMR, digital, timing) are monitored in real time by dedicated sensors and controllers.
- Any deviation from protocol parameters, loss of NMR confirmation, synchronization error, or sensor anomaly is instantly flagged.
-
Error detection mechanisms include:
- ○
- Comparison of received channel codes to expected orthogonal codes.
- ○
- Validation of all events and NMR confirmations against node clocks.
- ○
- Integrity checking on all molecular/NMR state transitions.
- When an error or anomaly is detected, the affected link is immediately suspended, and an immutable log entry (with NMR data, error type, and timestamp) is created for audit and diagnostics.
- Automated self-checks and test routines (including NMR response checks, channel cycling, and stress testing) ensure channel health and protocol integrity.
- Maintenance protocols allow for review, diagnosis, and secure re-initialization under operator control.
- The system escalates alerts for persistent or critical errors, supporting real-time security response.
5.4. System Scalability Limits and Deployment Factors
- Maximum channel count per system is determined by the selectivity and orthogonality of the molecular receptors, the resolution of the NMR sensors, and the degree of photonic and magnetic field separation achievable in the hardware.
- Practical batch magnetic/NMR gating and photonic encoding typically support 8–32 simultaneous channels, with higher counts requiring advanced materials or signal processing.
- Environmental stability (temperature, vibration, EMI) affects large arrays: Robust packaging, shielding, and periodic calibration are recommended for high-density deployment.
- Channel crosstalk, signal loss, and noise increase with array size and speed, requiring additional separation, shielding, or error correction.
- System maintenance, monitoring, and predictive diagnostics are essential for reliable scaling.
- Modular hardware design is recommended for easy upgrades as molecular, NMR, or sensor technology advances.
6. Environmental and Engineering Considerations
6.1. Co-Injection of Data and Photonic Spin Signals into Fibre Optic Media
6.2. Fibre Optic Medium for Dual Signal Transmission
6.3. Signal Separation via Photonic Integrated Circuit
6.4. Continuous Trust Enforcement and Buffering Requirements
6.5. Materials and Molecule Candidates
6.6. Photon, Magnetic, and NMR Control
6.7. Time Synchronization
6.8. Security and Spoofing Resistance
6.9. Emitter Feedback via NMR Response Loop
7. Lifecycle, Replacement, and Fail-Safe Protocols
- Trust gates are not transferable: Replacing a machine or molecular batch requires a new pairing event, with a fresh molecular state change and unique code assignment, confirmed by new NMR feedback and protocol initialization.
- No soft upgrades or hot-swaps are permitted: This rigidity is intentional, ensuring that high-assurance environments cannot be bypassed, spoofed, or updated without full, physically confirmed re-initialization—enforced and auditable via the NMR feedback channel.
- All replacement and re-pairing events are logged, timestamped, and require direct physical intervention under strict supervision, ensuring non-repudiation and auditability.
- The protocol enforces a strict one-to-one correspondence between trust gate activation, its associated hardware, and the authorized NMR response: Unauthorized reuse or cloning is prevented by physical law and closed-loop feedback, there is no involvement of digital control.
8. Implementation Feasibility and Prototyping
8.1. Implementation Scenarios and Deployment Models
- High-Security Facilities: The trust system is deployable at the physical security perimeter of data centres, government sites, and critical infrastructure. Each connection is equipped with an NMR-feedback molecular trust node, ensuring only physically present, authorized parties can establish trust.
- Nuclear Power and Radiological Facilities: The protocol enforces tamper-evident, physically non-spoofable trust at nuclear or radiological boundaries—access, interlocks, and remote monitoring are confirmed by real-time NMR feedback and continuous audit.
- Industrial Control Networks: In power grids, oil & gas, and manufacturing, the protocol delivers physically enforced trust and NMR-based confirmation between PLCs, sensors, and controllers. Batch NMR/magnetic gating and automated diagnostics enable robust, scalable deployment.
- Distributed Multi-Site Networks: The architecture supports secure, protocol-validated trust channels between geographically separated sites, with each node synchronized via GPSDO/atomic clock and NMR confirmation. Maintenance and audit support reliability and incident response.
- Scalable Cloud or Edge Systems: In data centre, cloud, or edge contexts, molecular trust gates with NMR feedback govern machine-to-machine access, cryptographic key release, and secure onboarding—beyond traditional HSM or software controls.
- Integration with Existing Security Frameworks: The protocol complements digital authentication, blockchain, and zero-trust architectures by adding a non-spoofable, NMR-auditable layer of physical trust, scalable across both legacy and greenfield deployments.
8.2. Prototype Readiness on the Most Advanced Required Components
- Laboratory-grade lasers or LEDs with polarization filters/controllers for photon spin states,
- Off-the-shelf optical hardware and micro-magnets/solenoids/thin films for precise NMR-compatible field alignment,
- Synthesized or sourced molecules with spin and magnetic sensitivity and documented NMR response (e.g., CISS-active helicenes, fullerenes, triple-helix complexes).
8.2.1. Co-Injection of Data and Photonic Spin Signals into Fibre Optic Media
8.2.2. Fibre Optic Medium for Dual Signal Transmission
8.2.3. PIC Requirements for Spin–Data Signal Separation in ASC Devices
8.2.4. Molecule Selections – Potential candidates
9. Security Protocol Comparison: Authentication Security Cryptonode (ASC) Protocol
- FIPS 140-3 Level 4: Highest hardware security module standard (US government/military)
- Common Criteria EAL7: Formal, high-assurance hardware and process security standard
- Quantum-Resistant Authentication: Protocols resistant to quantum computational attacks [17]
- SSL/TLS & Commercial Crypto: State-of-the-art digital authentication
10. Conclusion
- Intrinsic quantum resistance, with no mathematical secret to break
- Real-time, continuous monitoring and instant tamper response
- No single point of digital failure, central secret, or cryptographic master key
References
- Thomaschewski, S.; et al. Spin-selective routing in photonic integrated circuits. Nat. Photonics 14, 123–130 (2020).
- Grezes, A. , Morton, J.J.L., et al. On-chip integration of magneto-optical and photonic devices. Nat. Commun. 7, 11586 (2016).
- Atatüre, M. , Englund, D., et al. Hybrid photonic and magnetic device platforms for quantum information processing. Nat. Rev. Mater. 3, 38–51 (2018).
- Morton, J.J.L. & Lovett, B.W. Hybrid solid-state qubits: The powerful role of electron spins. Annu. Rev. Condens. Matter Phys. 2, 189–213 (2011).
- Rouxinol, F. , et al. Measurement of spin-mechanical coupling in a hybrid quantum device. Nat. Commun. 7, 13766 (2016).
- Campidelli, S.; et al. Pt-porphyrin grafted graphene for molecular spintronic devices. Angew. Chem. Int. Ed. 59, 13042–13047 (2020).
- Yin, Z.; et al. Chiral molecular spintronics. Chem. Soc. Rev. 50, 10020–10034 (2021).
- Niemeyer, M.; et al. Spin-based logic in molecular systems. Chem. Rev. 122, 6712–6748 (2022).
- van der Wiel, W.G.; et al. Molecular electronics: The rise of spintronics and quantum effects. Nat. Nanotechnol. 16, 56–62 (2021).
- Zhou, L.; et al. Spin coherence in molecular qubits for quantum technologies. Nat. Chem. 13, 906–913 (2021).
- Kostylev, N.; et al. NMR and EPR detection in molecular spin devices. J. Magn. Reson. 339, 107184 (2022).
- Tang, J.; et al. Physical unclonable functions in molecular security devices. Adv. Mater. 34, 2108464 (2022).
- ETSI. Quantum-safe cryptography and security. ETSI White Paper, No. 8 (2020).
- National Institute of Standards and Technology (NIST). FIPS PUB 140-3: Security Requirements for Cryptographic Modules.
- Baker, W.M.; et al. Physically enforced trust: NMR-validated authentication in quantum communication devices. Phys. Rev. Appl. 19, 054013 (2023).
- Kostylev, N. , Poluektov, O.G. (2022). "Electron Paramagnetic Resonance and Spin Relaxation in Cu(II) Complexes: Room Temperature and Ligand Effects." Journal of Magnetic Resonance, 339, 107184.
- Chen, L.K.; et al. (2016). "Report on Post-Quantum Cryptography." U.S. National Institute of Standards and Technology, NISTIR 8105.
| Matching the Molecules to the PIC Capabilities | |||
|---|---|---|---|
| Molecule / Complex | Spin Signal Type | PIC Compatibility | Explanation |
| TEMPO / TEMPOL (Nitroxides) | Electron spin S=½, T₂ ~μs | Yes – match to plasmonic spin routing (Thomaschewski et al.) | Long enough T₂ (~μs at RT) for spin-photon interaction in room-temperature PIC. |
| Vanadyl VO(acac)₂ | S=½, T₂ ~μs (even at RT) | Yes – spin coherence within detection timescale | Spin resonance timing compatible with spin injection and routing into receptor. |
| Cu(II) complexes | S=½, ligand-sensitive T₁/₂ | Yes – already studied in EPR/PIC experiments | Spin-orbit stability makes them excellent candidates for photonic-spin coupling. |
| Security Criterion | Authentication Security Cryptonode (ASC) Protocol | FIPS 140-3 Level 4 | EAL7 / Military HSM | PUF Hardware | Quantum-Resistant Auth | SSL/TLS |
|---|---|---|---|---|---|---|
| Physical Root of Trust | YES – molecule, NMR, time | YES | YES | YES | Partially | NO (math-based only) |
| Unique, Unclonable Event | YES – NMR/physics/time bound | YES | YES | YES (chip variation) | Partially | NO (digital secrets only) |
| Multi-Factor, Physical Auth | YES – 3 independent physical laws | YES (with sensors) | YES (with sensors) | NO (PUF only) | Usually NO | NO |
| Side-Channel Resistance | YES (NMR feedback isolated) | YES (with active zeroize) | YES (with active zeroize) | Good (with design) | Variable | WEAK (history of exploits) |
| Quantum Resistance | YES – not math-based, physics only | NO (math vulnerable) | NO | YES/NO | YES (by design) | NO |
| Tamper Evidence/Response | YES – continuous, instant lockout | YES (active zeroize) | YES | Partially (may fail silent) | Varies | NO |
| Audit/Forensics | YES – all physical/digital/log events | YES | YES | Partially | Varies | Partial (logs only) |
| Replay/Relay Protection | YES – NMR+GPSDO makes each event unique | YES | YES | Partially | YES (by design) | NO (with weaknesses) |
| No Single Point of Failure | YES – 3 physical channels | Sometimes | Sometimes | NO | Sometimes | NO |
| Recovery After Tamper | Manual/physical only | Manual only | Manual only | Manual only | Varies | Yes (digital) |
| Manufacturing Supply Chain | Same risk as others – mitigatable | Same | Same | Same | Same | Same |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





