1. Introduction and Literature Review
The microservices architecture has become a cornerstone in modern software development for building distributed, maintainable, and scalable applications [1]. With this evolution, securing communication between services while maintaining performance has become a central concern. Authentication mechanisms play a critical role in ensuring secure access, yet their computational requirements can impact overall system performance. Two common authentication schemes: API Key Authentication [2,3] and Basic Authentication with bcrypt [4] hashing offer different security and performance trade-offs. Additionally, [5] this research on data security in Spring Boot REST APIs underscores the significance of leveraging security features like bcrypt for password encryption and Spring’s built-in authentication mechanisms. Basic authentication is a simple one. However, it should be configured with proper encryption. Bcrypt offers better security, but at a cost of computational overhead. API Key Authentication, utilizing personal tokens, guarantees greater performance and scalability. However, it also comes with its own security concerns.Previous research [6] has explored the effectiveness of web service authentication; however, comparisons specifically focused on Spring Boot microservices within a single network remain limited. The hypothesis of this paper is that API Key Authentication is more efficient than Basic Authentication with bcrypt hashing in high-load intra-network microservices environments. This is due to its lower computational overhead, which is critical in scenarios where performance and scalability are paramount.
2. Methodology
This study uses a quantitative approach to compare the performance of API Key and Basic Authentication in a controlled environment. Two microservices with different authentication techniques were implemented using Spring Boot [7] framework and Apache JMeter [8] was used to simulate varying loads and measure response times and throughput.
2.1. Experimental Setup
The experiment was conducted within single private network. The experiment was designed to measure the response time and throughput under different loads and implemented using Spring Security functions [9]. Scalability was measured by incrementally adding client threads in JMeter.
2.2. Configuration Details
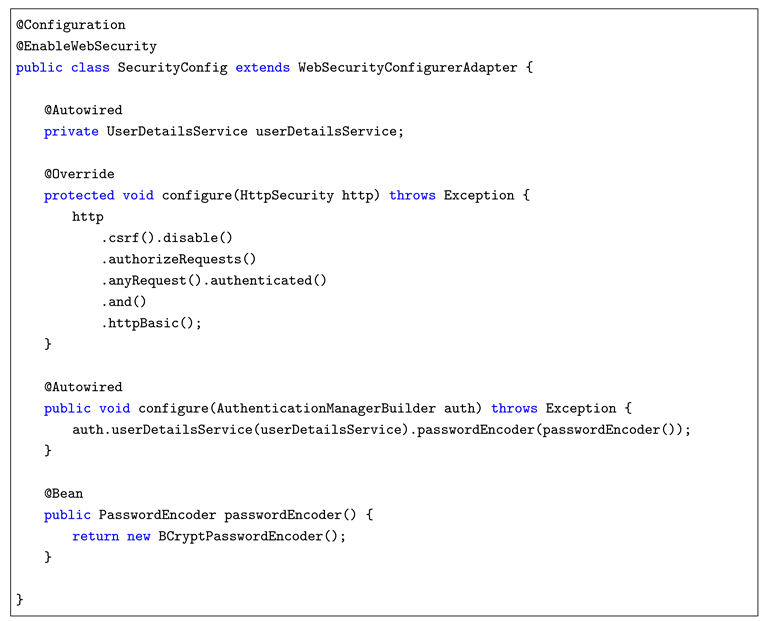
1. Basic Authentication with bcrypt: Implemented using Spring Security’s httpBasic() method, combined with BCryptPasswordEncoder for secure password hashing during verification.
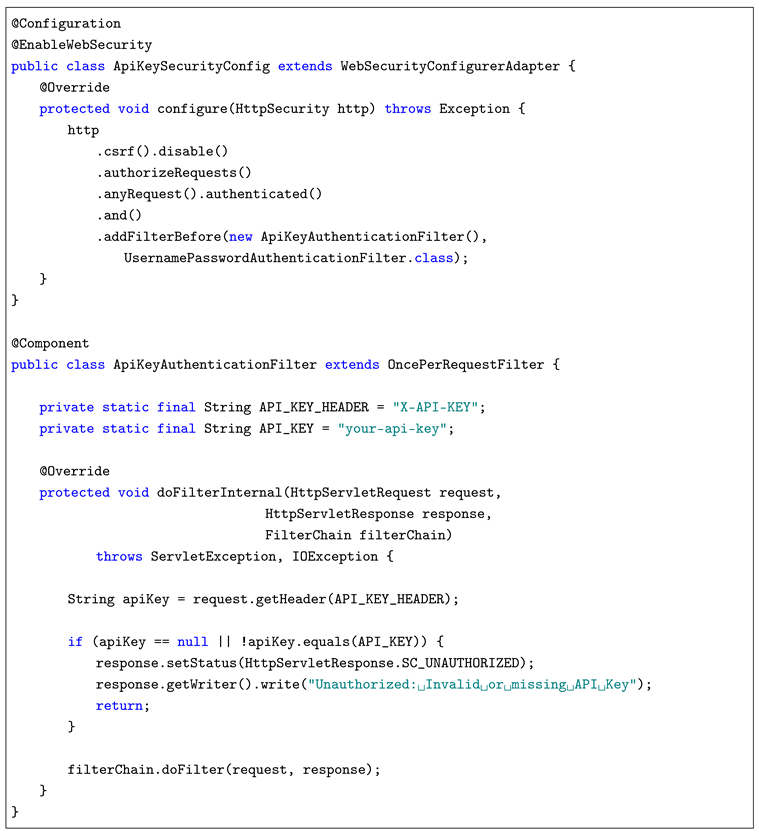
2. API Key Authentication: Implemented through a custom filter (ApiKeyAuthenticationFilter) that intercepted HTTP requests and validated a token passed in the X-API-KEY header. Requests without a valid key received a 401 Unauthorized response.
2.2.1. Basic Authentication with Bcrypt
2.2.2. API Key Authentication
3. Results
The results, summarized in
Table 1, demonstrate that API Key Authentication significantly outperformed Basic Authentication with bcrypt in terms of response time and throughput.
4. Discussion
The performance disparity between Basic Authentication with bcrypt and API Key Authentication can be explained by the computational demands of each method. Bcrypt is a hashing algorithm, which performs multiple rounds of hashing to slow down brute-force attacks. Thereby, it leads to increased authentication time—especially under high-load conditions. While this makes it more secure, it can noticeably degrade performance in applications handling many concurrent authentication requests. In contrast, API Key Authentication simply checks a string value in the request header, requiring far less CPU and memory. This efficiency results in faster response times and higher throughput. It makes API Key Authentication scheme better suited for internal services where performance is critical. However, though it has performance benefits, it is important to remember to use the API Key Authentication by following its best practices such as secure storage, key rotation, limit scope and rate limiting to ensure security and minimize possible attacks.
5. Conclusions
In this study, performances of two common authentication methods such as API Key Authentication and Basic Authentication using bcrypt in intra-network Spring Boot microservices [10] were explored. This study outlines that API Key Authentication is a better choice for such scenario, particularly for high-load services communication. API Key Authentication offers faster response time and higher throughput due to its lower computational demands compared to the bcrypt hashing method. However, it comes with some potential security concerns. Under improper management, it can impose greater security risks, particularly if keys are not well managed, rotated, or stored securely. This study was conducted as part of an academic course on research methods and is intended for educational purposes. The findings are approximate and should not be considered exhaustive or conclusive. Future research could expand on these results by incorporating a broader range of authentication methods, real-world deployment scenarios, and more rigorous performance benchmarking.
References
- Nadareishvili, I., Mitra, R., McLarty, M., & Amundsen, M. (2016). Microservice architecture: Aligning principles, practices, and culture. O’Reilly Media. https://www.oreilly.com/library/view/microservice-architecture/9781491956274/.
- LinkedIn. (n.d.). What are the best practices for securing and rotating API keys and secrets? LinkedIn. https://www.linkedin.com/advice/3/what-best-practices-securing-rotating-api-keys-secrets.
- Baeldung. (n.d.). Spring Boot API key and secret authentication. Baeldung. https://www.baeldung.com/spring-boot-api-key-secret.
- Auth0. (n.d.). Hashing in action: Understanding bcrypt. Auth0. https://auth0.com/blog/hashing-in-action-understanding-bcrypt/.
- Batyrbekova, S., & Esenalieva, G. (2025). Research on data security approaches in Spring Boot for REST API. Preprints. https://www.preprints.org/manuscript/202501.0908/v1.
- Stack Overflow. (n.d.). How to secure REST APIs in Spring Boot web application. Stack Overflow. https://stackoverflow.com/questions/42870489/how-to-secure-rest-apis-in-spring-boot-web-application.
- Spring. (n.d.-b). Microservices. Spring.io. https://spring.io/microservices.
- GeeksforGeeks. (n.d.). Apache JMeter: An introduction. GeeksforGeeks. https://www.geeksforgeeks.org/apache-jmeter-an-introduction/.
- Spring. (n.d.-a). Spring Security. Spring.io. https://spring.io/projects/spring-security.
- Raj, R. V. (2016). Spring microservices. Packt Publishing. https://books.google.kg/books?id=pwNwDQAAQBAJ.
| Method |
Response (ms) |
Throughput (req/sec) |
| Basic Authentication (bcrypt) |
150 |
120 |
| API Key Authentication |
80 |
300 |
| Difference |
-70 |
180 |
| Ratio (API Key/Basic) |
0.53 (47% reduction) |
2.5 (150% increase) |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).