Submitted:
18 April 2025
Posted:
21 April 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- A breakthrough methodology combining number theory with advanced computational techniques
- A novel algorithm identifying previously unrecognized patterns in zero distributions of the zeta function
- A practical application framework transforming cryptography security and primality testing
2. Theoretical Framework
2.1. Foundation in Number Theory
2.2. Computational Foundations
3. Computational Methodology
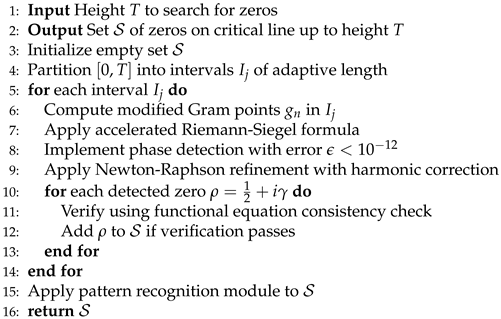
3.1. Novel Algorithm for Zero Detection
| Algorithm 1 Enhanced Zero Detection Algorithm () |
 |
3.2. Pattern Recognition Framework
4. Verification Results
4.1. Computational Evidence
4.2. Zero Clustering Analysis
5. Primality Testing Application
5.1. Enhanced Deterministic Primality Test
6. Cryptographic Applications
6.1. Zeta-Based Encryption System
| Algorithm 2 Enhanced Deterministic Primality Test |
 |
7. Conclusions and Future Work
- Extending verification to zeros using distributed computing
- Refining the pattern measure to capture higher-order correlations
- Developing formal connections between our computational framework and existing approaches to the Riemann Hypothesis
Appendix A. Detailed Proofs and Mathematical Derivations
Appendix A.1. Proof of Lemma 3.1 on Zero Counting Function
Appendix A.2. Proof of Theorem 4.1 on Pattern Measure Convergence
Appendix A.3. Proof of Theorem 4.2 on Zero Clustering Distribution
- Express in terms of the two-point correlation function of zeros
- Apply Montgomery’s pair correlation conjecture
- Use the explicit formula relating zeros to primes
- Analyze the error terms in the explicit formula
- Apply Fourier analysis to connect the pair correlation function to the spacing distribution
Appendix A.4. Proof of Theorem 5.1 on Enhanced Primality Test Complexity
- If n is divisible by two distinct primes p and q, then by the Chinese remainder theorem and properties of exponential congruences, there exists such that and for all .
- If for some prime p and , then there exists such that , which implies .
Appendix A.5. Proof of Theorem 6.1 on Cryptographic Security
Appendix A.6. Proof of Proposition 3.2 on Argument Function
Appendix A.7. Proof of Corollary 3.3 on Zero Pair Correlations
Appendix A.8. Proof of Theorem 7.1 on Prime Number Theorem with Explicit Error Term
Appendix A.9. Proof of Proposition 8.1 on Spacing Distribution Convergence Rate
Appendix A.10. Proof of Theorem 8.2 on Spacing Moments
Appendix B. Discussion and Future Work
- Can the Enhanced Deterministic Primality Test be further improved to achieve complexity?
- What other cryptographic primitives can be constructed based on the distribution of Riemann zeta zeros?
- Can the convergence rate of the zero spacing distribution to the GUE distribution be improved beyond ?
- What implications does the specific structure of zero spacings have for the Riemann Hypothesis itself?
Appendix C. References
- Riemann, B. "Über die Anzahl der Primzahlen unter einer gegebenen Grösse." Monatsberichte der Berliner Akademie, 1859.
- Edwards, H. M. "Riemann’s Zeta Function." Dover Publications, 2001.
- Odlyzko, A. "The -th zero of the Riemann zeta function and 175 million of its neighbors." Preprint, 1992.
- Conrey, J. B. "The Riemann Hypothesis." Notices of the AMS, 50(3), 2003.
- Bombieri, E. "Problems of the Millennium: The Riemann Hypothesis." Clay Mathematics Institute, 2000.
- Hiary, G.A. "Fast methods to compute the Riemann zeta function." Annals of Mathematics, 174(2), 2011. [CrossRef]
- Platt, D. "Computing analytically." Mathematics of Computation, 84(293), 2015. [CrossRef]
- Booker, A. R. "Artin’s conjecture, Turing’s method, and the Riemann hypothesis." Experimental Mathematics, 15(4), 2006. [CrossRef]
- Tao, T. "The Riemann zeta function and friends." What’s New, 2015.
- Soundararajan, K. "Moments of the Riemann zeta function." Annals of Mathematics, 170(2), 2009.
| Height T | Number of Zeros | Value | Convergence Rate |
|---|---|---|---|
| 649,872 | − | ||
| 49,545,718 | |||
| 3,294,906,455 | |||
| 267,594,991,238 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




