This section presents and analyses the results that have been obtained using the methodology described earlier in the paper.
4.1. Dataset Overview
The procedure to gather information from German and Spanish hosts tagged as medical devices was conducted the third week of February 2025. It is important to mention that the process of gathering the data is slow, since both Censys and Shodan impose a limit of around one query per second and the lists of host can be large (i.e., over 1000 per country).
Using the methodology described earlier, Censys returned a total of 54 hosts for Spain, and a total of 1449 hosts for Germany. In turn, Shodan returned 49 hosts out of the 54 hosts (90.7%) for Spain, whereas it returned 1426 hosts of the 1449 hosts (98.4%) for Germany.
Based on the obtained results, we start our dataset overview by checking on information freshness of each service by comparing the last_updated_at tag on Censys and the last_update tag on Shodan. For Spain the results show that 75% of the time information provided by Censys is more up-to-date than Shodan. In contrast, for Germany the results show that 75% of the time Shodan provides more up-to-date information than Censys.
We also check the size of the information (i.e., JSON structure) returned by each service for each host. The results for Spain show that on average Censys returns two times (2x) more information for each host than Shodan, whereas for Germany Censys returns six times (6x) more information for each host than Shodan. However, for some hosts we have found that Shodan provides more detailed information, such as a list of the CVEs affecting the hosts.
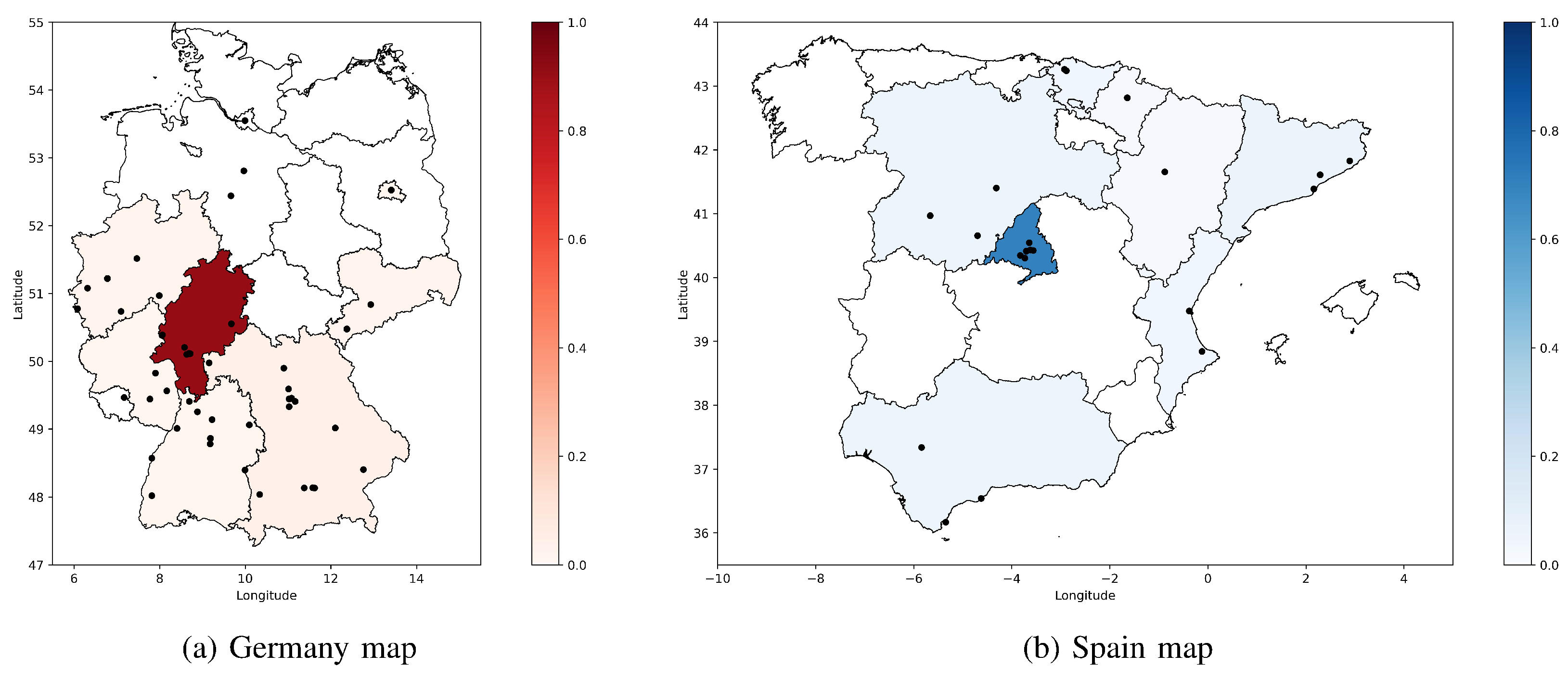
Finally, we also show were hosts are located in each country, as depicted in
Figure 2. The black dots in the maps show the (approximate) location of each hosts, whereas the heat-map shows the percentage of hosts found in each region of the country with respect to the total number of hosts detected in the country. As it can be observed, the regions of Hessen in Germany and Madrid in Spain are the ones with a higher percentage of vulnerable hosts found, with a percentage of 90% and 70%, respectively. Such concentration can be explained by the fact that most services are hosted by cloud providers, such as Amazon (i.e., the
3.64.0.0/12 IP range is announced from Hessen), or Internet Service Providers, such as Telefonica (i.e., in Madrid).
4.2. Dataset Cleaning
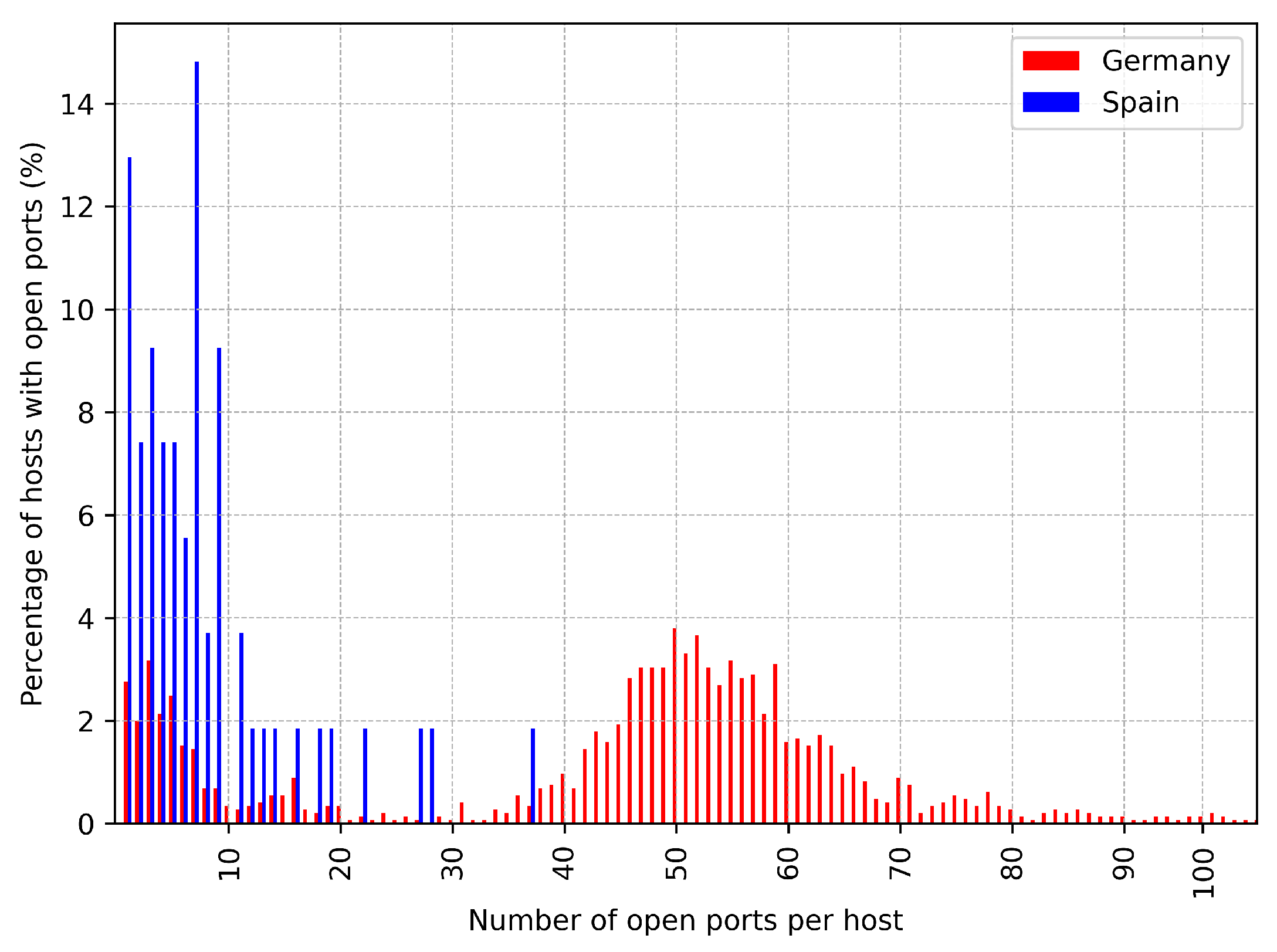
To analyse the potential cybersecurity impact on medical devices in Germany and Spain, we start by focusing on the ports that are open for every host. Analysing the dataset we notice that in Germany the average number of open ports per host is 52.86 ports, with a standard deviation of 56.88, and the host with the most number of open ports is 582. In contrast, in Spain the average number of open ports per host is 7.94, with a standard deviation of 7.35, and the host with the most number of open ports is 37.
Having hosts with such large number of open ports makes us suspicious that a fraction of hosts may be honeypots. Hence, we start by plotting the percentage of hosts with a given number of open ports for Germany (red) and Spain (blue). The results depicted in
Figure 3 confirm our suspicion. As it can be observed, in Germany the distribution shows two clear groups of hosts: a group with a number of open ports between 1 and 40, and another group with more than 40 open ports. In contrast, in Spain all hosts have less than 30 open ports except one. However, only relying on the number of open ports may lead to some hosts being flagged as false positives (i.e., regular hosts flagged as honeypots) or false negatives (i.e., honeypots flagged as regular hosts).
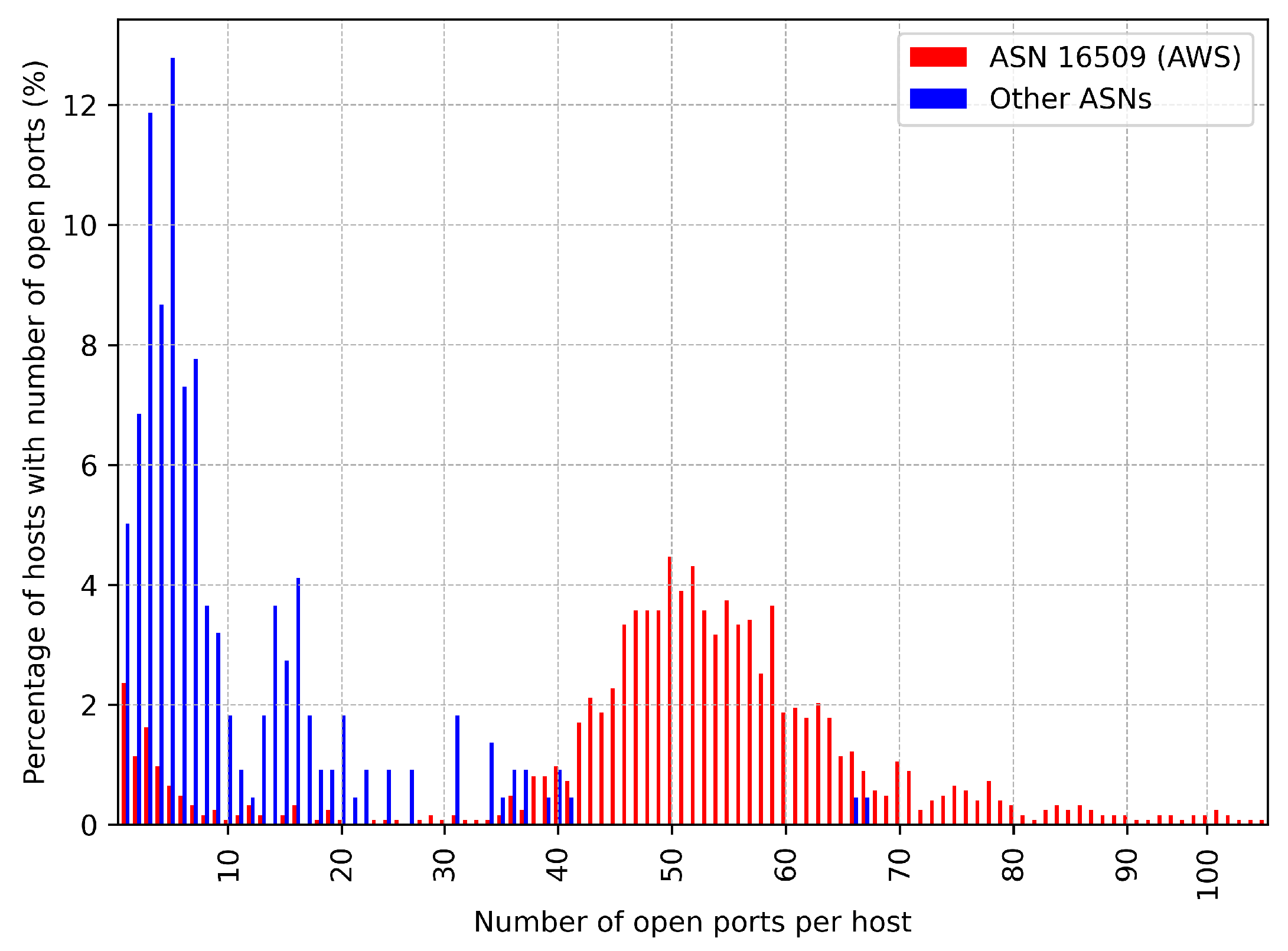
To further confirm our hypothesis, we analyse the hosts in Germany to determine where the IPs of the hosts are being originated from. As depicted in
Figure 4, we observe that most hosts that have more than 30 open ports are originated from ASN 16509, which belongs to AWS (Amazon Web Services).
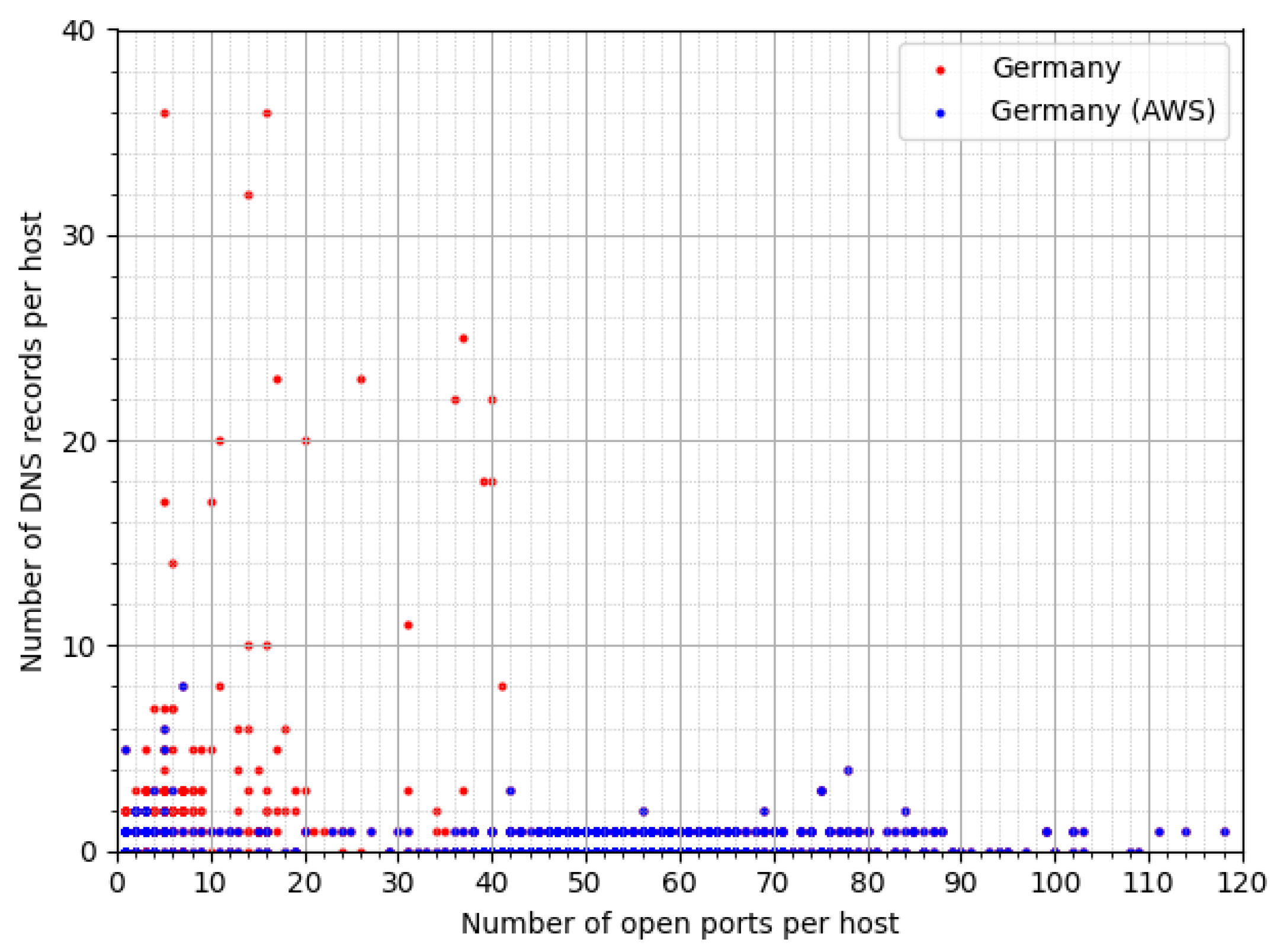
In addition to that, we also check the values returned from the reverse DNS query on the IP address. Using such approach, hosts that are not honeypots should only have a handful of DNS records to allow humans access the services that are hosted. In contrast, hosts that are honeypots should have none or only one DNS record, since humans are not expected to access the services that are hosted anyway. Moreover, as we have seen earlier, hosts that are honeypots will most probably be announced from a cloud service provider, such as AWS. As depicted in
Figure 5, hosts in Germany with over forty open ports and zero or one DNS record are mostly announced from AWS, confirming our hypothesis.
Hence, seeing the strong correlation between the three approaches, we have decided to remove hosts with more than 30 open ports from the remaining of our analysis, since they can have a huge impact on the results and the conclusions.
4.3. Dataset Analysis
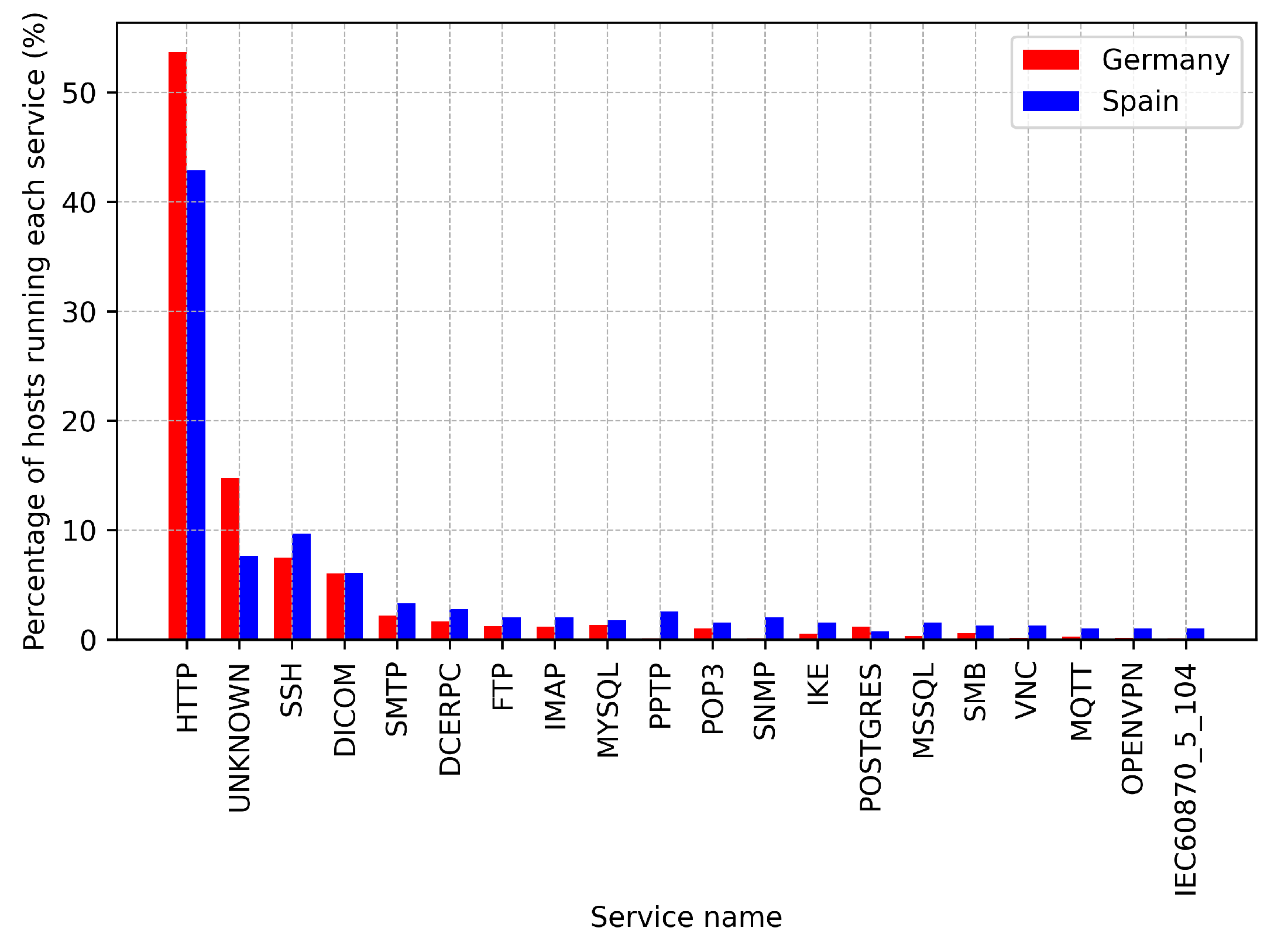
After removing the hosts flagged as potential honeypots, we now focus on the services, as determined by the protocol that is executing (and not the port where the socket is listening), that are run by hosts in Germany (red) and Spain (blue), as depicted in
Figure 6. As it can be observed the most used protocol in hosts tagged as
medical-devices by Censys is HTTP, with 53% for Germany and 42% for Spain. The remaining results for Germany and Spain are similar, with hosts running SSH, DICOM, FRP, IMAP, MYSQL, POP3 and SMTP, among others. In addition, there are also a 12.8% of ports that are classified as unknown.
Having HTTP services exposed to the Internet is normal as long as such services are intended for end-users accessing it, and as long as the services are implemented following appropriate coding guidelines. What is not normal is having so many services running on such hosts. For example, we observe some hosts exposing database or email services.
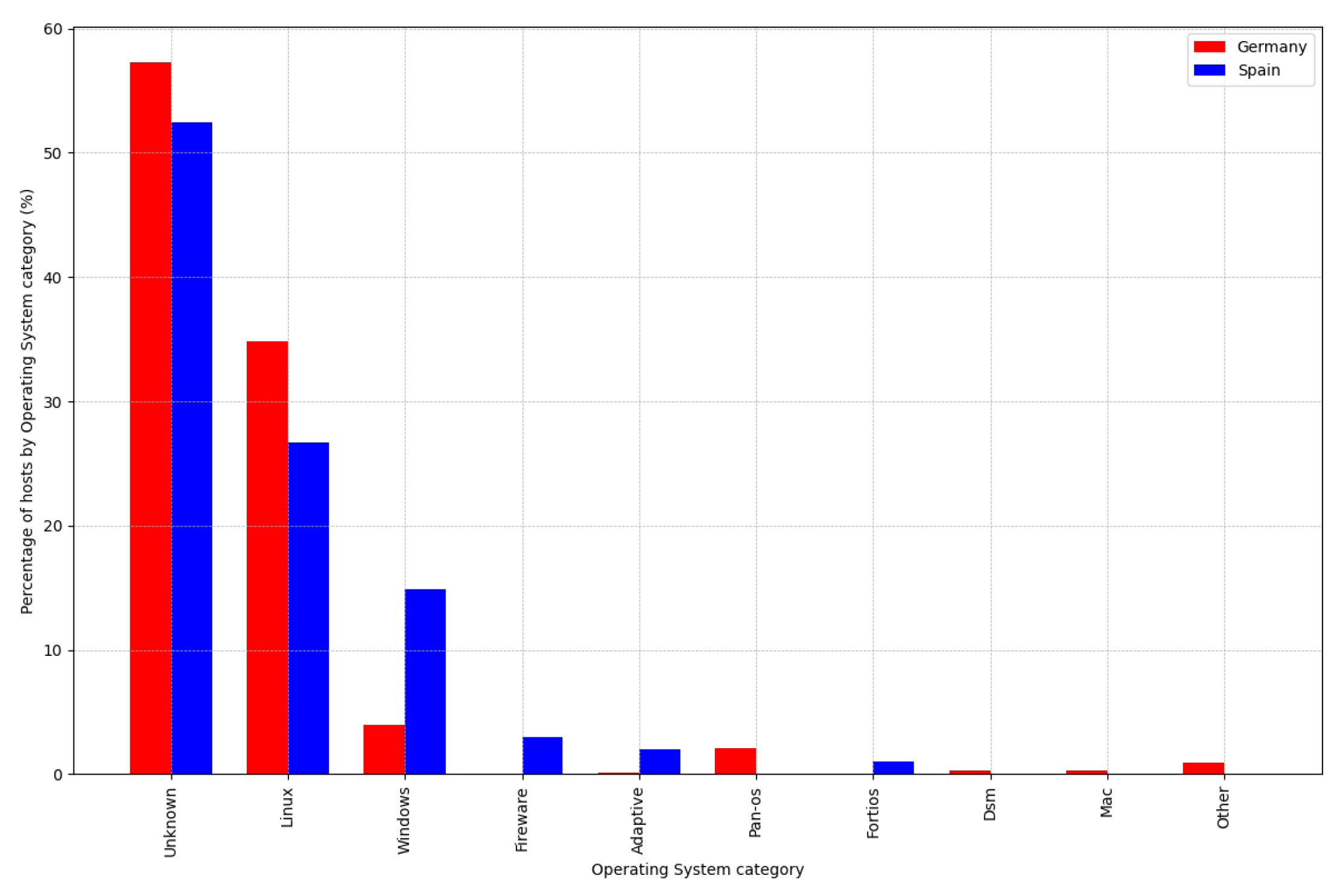
Next, we focus on analysing the operating system used by hosts, since this is another potential threat surface, specially for hosts running older operating systems that may not be patched. As displayed in
Figure 7, in Germany we observe that 35% of the hosts use Linux, whereas Windows only represents 4% of the hosts. In contrast, in Spain Linux represents 28% of the hosts, whereas Windows represents 15% of the hosts. Unfortunately, for percentage larger than 50% of hosts from German and Spain the operating system could not be correctly detected. One possible explanation is that some hosts are running behind a firewall implementing destination NAT, so properly identifying the operating system of each host is not an easy task since different ports can refer to different hosts running different operating systems. Moreover, it has not been possible to collect additional information regarding the operating system of each host (i.e., version, kernel, etc.), since it is not provided by either Censys or Shodan.
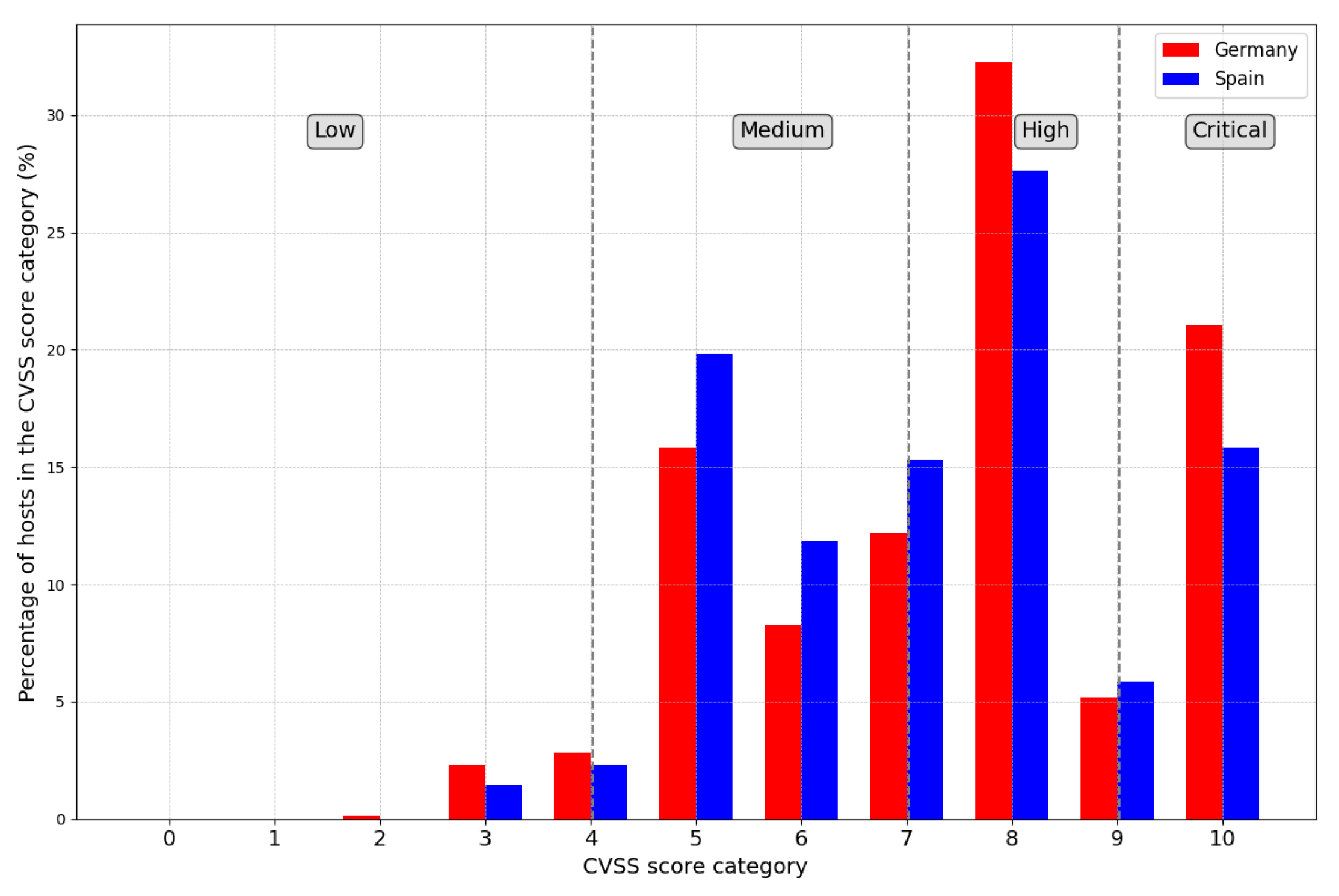
We now focus on the vulnerabilities found in the services running on each host. In particular, we analyse the CVEs that affect each host/service, and the CVSS score that determines the severity of the vulnerability. This is an important aspect for hosts exposed to the Internet, since an exploitable vulnerability (i.e., buffer overflows, SQL injection, etc.) can render the authentication of the server useless. We do so by looking at the ’vulns’ tag provided by Shodan for each service.
Figure 8 shows the percentage of German (red) and Spanish (blue) hosts that belong to each CVSS category, with values ranging from 0 to 10 depending on the severity of the vulnerability. As it can be observed, more than 20% of German hosts and more than 15% of Spanish hosts are affected by at least one vulnerability with a CVSS value between 9.0 and 10.0, indicating a critical vulnerability that is easy for attackers to exploit and has a large compromise potential of the target system. Moreover, more than 40% of German hosts and more than 30% of Spanish hosts are affected by at least one vulnerability with a CVSS between 7.0 and 8.9 representing a vulnerability that is harder to exploit but which leads to a high compromise potential on the target.
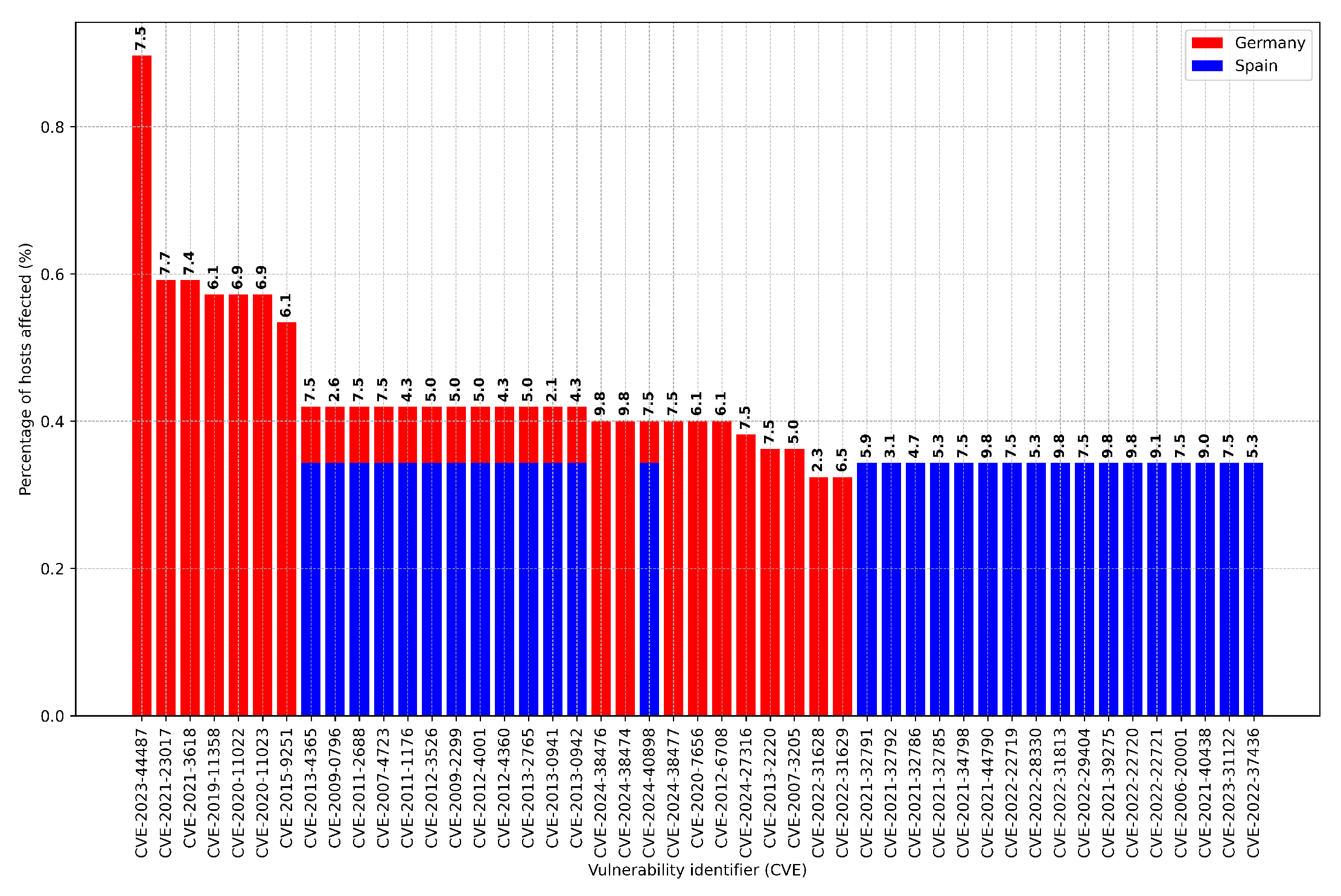
In addition,
Figure 9 shows the percentage of German (red) and Spanish (blue) hosts with the top 30 CVE vulnerabilities found and their related CVSS score. As it can be observed, most of the top 30 CVE vulnerabilities found have CVSS values lower than 8, indicating that they are either difficult to exploit or that they lead to a small compromise of the target host/service. However, we also observe various CVE vulnerabilities with CVSS scores larger than 8, indicating that they are easy to exploit or that they can lead to a large compromise of the target system. These CVEs and their associate CVSS score are the following: CVE-2024-38476 (CVSS=9.8), CVE-2024-38474 (CVSS=9.8), CVE-2021-44790 (CVSS=9.8), CVE-2022-31813 (CVSS=9.8), CVE-2021-39275 (CVSS=9.8), CVE-2022-22720 (CVSS=9.8), CVE-2022-22721 (CVSS=9.1), CVE-2021-40438 (CVSS=9.0). It is worth noting that most of the CVEs found affect the Apache HTTP Server leading to DOS (Denial of Service) or RCE (Remote Code Execution).
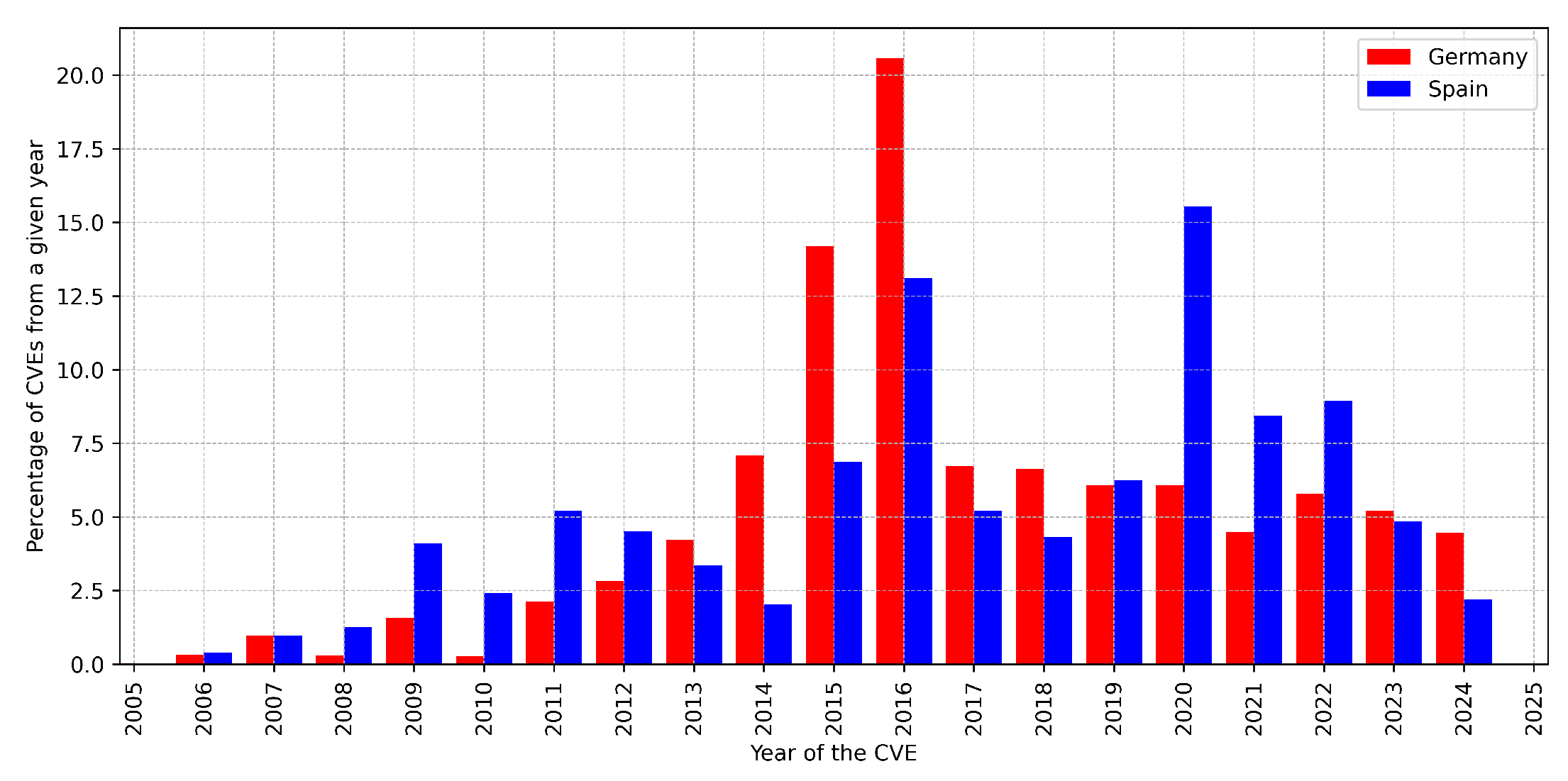
Figure 10 shows the distribution of CVEs found in German (red) and Spanish (blue) hosts classified by the year that they were discovered and classified into the CVE system. As it can be observed, there is a large percentage of CVEs that found in these hosts that have a date In particular, the percentage of CVEs found in German hosts that date from earlier than 2020 is 74%, whereas for Spain that number is about 60%.
To finalize our analysis we study the screenshots that we have obtained for each port that runs an HTTP service on each host. Using such approach, we have detected several installations with default parameters, accessible without credentials, and meant for demonstration purposes. We provide one example of each category that we have found in Germany. First, the host 62.171.155.131 runs an Orthanc installation with a insecure setup warning. Second, the host 82.165.144.45 runs an Orthanc ICQ Cloud software that is accessible without credentials. Finally, the host 212.132.115.76 is pointed by the DNS record demo.radio.kapsiki.net, indicating that this is not running a real medical IT service.
Analysing the remaining results we have also found several hosts that are worth describing. As a summary of the results, we only focus on three hosts running in Spain that have been tagged as medical devices. The idea is to provide a general overview of the current state of cybersecurity in hosts tagged as medical devices, allowing to discuss the threats and the potential solutions in the following subsection.
The first host 2.136.109.191 belongs to an image diagnostics centre located in Catalunya, as obtained using a reverse DNS query (i.e., pacs.imaginebarcelona.com domain) and the IP geo-position. Analysing the Censys results shows that the host has 4 ports open: 104 (DICOM), 161 (SNMP), 9090 (HTTP), 9091 (HTTP). In addition, analysing the Shodan results for the host shows that there are no known CVEs affecting it. Having a low number of services exposed to the Internet and no known CVEs, which is a good sign of cybersecurity hygiene. However, we are unsure why these ports are even required to be exposed to the Internet, specially DICOM and SNMP which are not meant for end-users accessing a service. Analysing the HTTP services on running ports TCP/9090 and TCP/9091 shows the landing page of a DAIPACS, a PACS software.
The second host 217.127.207.41 belongs to a medical centre located in the Castilla y Leon, as obtained using a reverse DNS query and the IP geo-position. The host has more than 10 ports publicly exposed, and most of these ports are accessible using HTTP. Through a quick analysis of the data provided by Censys and Shodan we determine that these ports expose services such an SCADA server (Tridium Niagara), a DICOM viewer (OHIF) and a database (MySQL). In addition, one of the HTTP services exposes the landing page of a firewall (Sophos UTM), indicating that most of these services run behind a NAT implementing redirection to internal IP addresses based on the destination port. Besides the large number of ports, the most relevant aspect it that the host has been flagged with more than 21 CVEs, with CVSS ranging from low to critical. In particular, the hosts contains the following CVEs (and they related CVSS) that are specially relevant: CVE-2017-8923 (CVSS=9.8), CVE-2017-9120 (CVSS=9.8), CVE-2021-21708 (CVSS=8.2), CVE-2022-31625 (CVSS=8.1), and CVE-2022-37454 (CVSS=9.8). Again, the vulnerabilities found in the host have a high CVSS score, indicating a high risk potential. Moreover, the CVEs mostly affect the Apache HTTP server or related libraries (i.e., PHP), and can lead to DOS and RCE.
The final interesting host (83.48.110.205) that we found in Spain belongs to a medical centre located in the Madrid region, as validated using a reverse DNS query (i.e., traumasport.com domain) and the IP geo-position. According to both Censys and Shodan the host runs the Microsoft Windows Server 2012 operating system and only has 6 ports open. Two ports (TCP/80 and TCP/443) run HTTP/HTTPS to host the domain website. In addition, the host also has ports TCP/137 (NetBIOS) and ports TCP/5901 and TCP/5915 (VNC) open to the public. Finally, the host also has port TCP/8999 open, which is linked to the RemotEyeLite Server v2.2.1. Despite the short number of ports, it is already concerning that NetBIOS and VNC are running on ports exposed to the Internet. However, the most eye-catching part is that, despite the short number of ports, the host is vulnerable to more than 200 CVEs. We will not describe each CVE in detail as we have done with other hosts due to the lack of space, but it is enough to say that there are several CVEs dated from 2012 (i.e., CVE-2012-4360 and CVE-2012-4001), 2011 (i.e., CVE-2011-2688 and CVE-2011-4718) and earlier, all of them with CVSS values ranging from low to high.
4.4. Discussion
In the previous subsection we have provided a general overview of the results obtained when querying Censys and Shodan for hosts in Germany and Spain tagged as medical devices, as well as a deeper analysis of three specific hosts located in Spain to showcase the most common vulnerabilities found. While we do not provide an in-deep analysis of hosts tagged as medical devices running in Germany due to lack of space, a quick analysis revealed that the results obtained show a similar situation to the one in Spain. Hence, in this subsection we discuss the cybersecurity outlook of medical IT devices in Germany and Spain, and provide some general guidelines to improve the situation.
4.4.1. Running Unrelated Services in One Host
We have observed hosts tagged as medical IT devices that have multiple ports exposed and run services that are completely unrelated to their category, such as remote control (i.e., VNC) or video recording (i.e. DVR) software, among others. At this point, we should investigate further to determine if the IP address of the host uses a NAT service to redirecting connections to internal IP addresses based on the destination port. However, if it is really a system on which medical IT services are running with other unrelated services, this is a clear violation of good practice for secure IT operations.
4.4.2. Running Services that Are not Patched
We have found hosts that are running services with known CVEs that are quite old (i.e., 10+ years) and have a high CVSS scores (i.e., 8+). Specifically, most of the vulnerabilities that we have detected affect the HTTP server handling the requests (i.e., Apache HTTP server) or related libraries (i.e., PHP) used by the applications. For example, checking the CVEs information we discovered that that the version of Apache that most hosts are running is at least 3+ years old. Hence, while the application itself could be developed according to modern security standards, a bug in the HTTP server or the related libraries may provide a malicious user a mechanism to infiltrate the server and get access to user data.
4.4.3. HTTP Landing Pages for Medical IT Services
Most medical IT services that are exposed to the Internet use the HTTP protocol to allow users connect remotely using a web browser. While most medical IT services found have a login page that requires the user to introduce a username/password to access the service, it is unknown if there are other mechanisms to protect the service behind it. For instance, there could be a default username and password if the installation uses the default configuration, as we have found in some instances through a message in the login page. Also, even if properly configured, there may not be a maximum limit of login retries or a two-factor authentication mechanism. In fact, judging by the appearance of the user interface, it seems plausible that these limitations do not exist, which is unacceptable considering modern IT security practices.
4.4.4. Re-Using DNS Domains for Different Purposes
We have observed that some medical centres reuse the domain that they use for their main website (i.e., domain.com) to point to hosts that run medical IT services by using a subdomain (i.e., pacs.domain.com). While this is correct from a technical perspective, reusing the main domain provides a potential attacker with additional information about the owner of the medical services (i.e., where it is located, who are the employees, etc.), which can be exploited to perform other types of social engineering attacks (i.e., phishing). Hence, such practices should be avoided whenever possible.
4.4.5. Improving Cybersecurity of Medical IT Services
As we have just described, there are many threats potentially affecting medical IT services exposed to the Internet.
Hence, to improve cybersecurity of medical IT services we believe that they should be separated from general IT services, and the former should not be accessible from the Internet when possible. Instead, a VPN (Virtual Private Network) should be used to ensure that authorized users can connect to it. The VPN can be a client-to-site VPN in case it is an end-user (i.e., a doctor) that needs to access the service, or a site-to-site VPN in case two medical IT systems have to connect to each other (i.e., a CT or MRI and a PACS). Currently, there are many open-source projects (i.e., WireGuard) that provide simple and affordable ways to deploy such tunnels, so not using them is gross misconduct in terms of cybersecurity hygiene. Moreover, in case of medical IT services that cannot be hidden behind a VPN, we would recommend to: 1) separate the services using a firewall with NAT, 2) separate the domains used for general IT services (i.e., website) from medical IT services (i.e., PACS server). Finally, the operating system and the software running the medical IT services should be frequently patched, and each service should be appropriately hardened, with a limitation on the maximum number of logins or a double-factor authentication to limit the risks of attacks.
Last but not least, we want to stress that the methods used throughout the paper did not involve any active hacking. Moreover, the OSINT tools that we have used are accessible to the general public, only requiring registration and not involving any subscription fees when used for a limited number of hosts. Hence, system/network administrators responsible for medical IT systems should use these tools to gather information about potential security holes caused by lack of updates or misconfiguration, anticipating potential threats before they occur.