Submitted:
15 October 2024
Posted:
15 October 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Preliminary Information
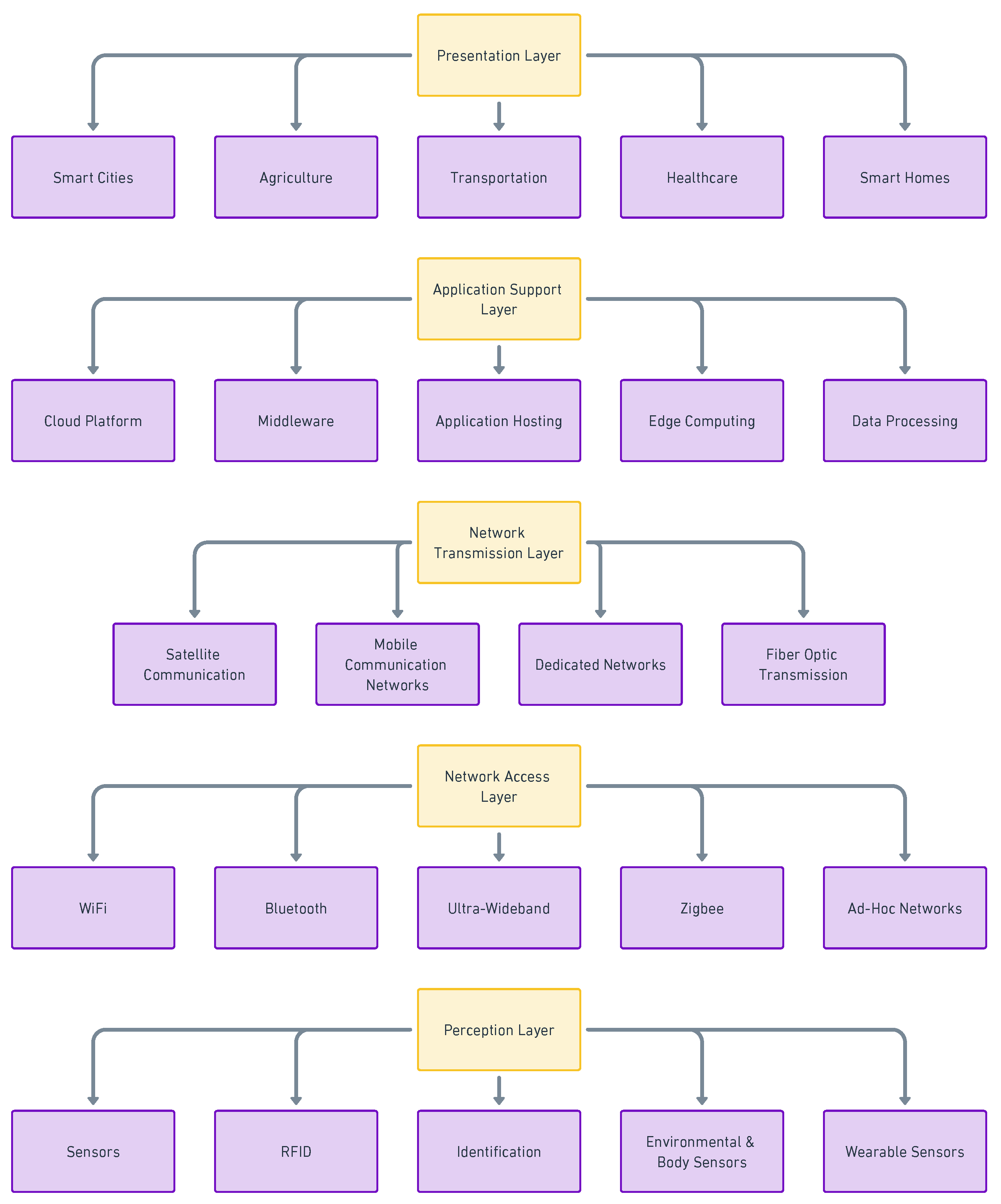
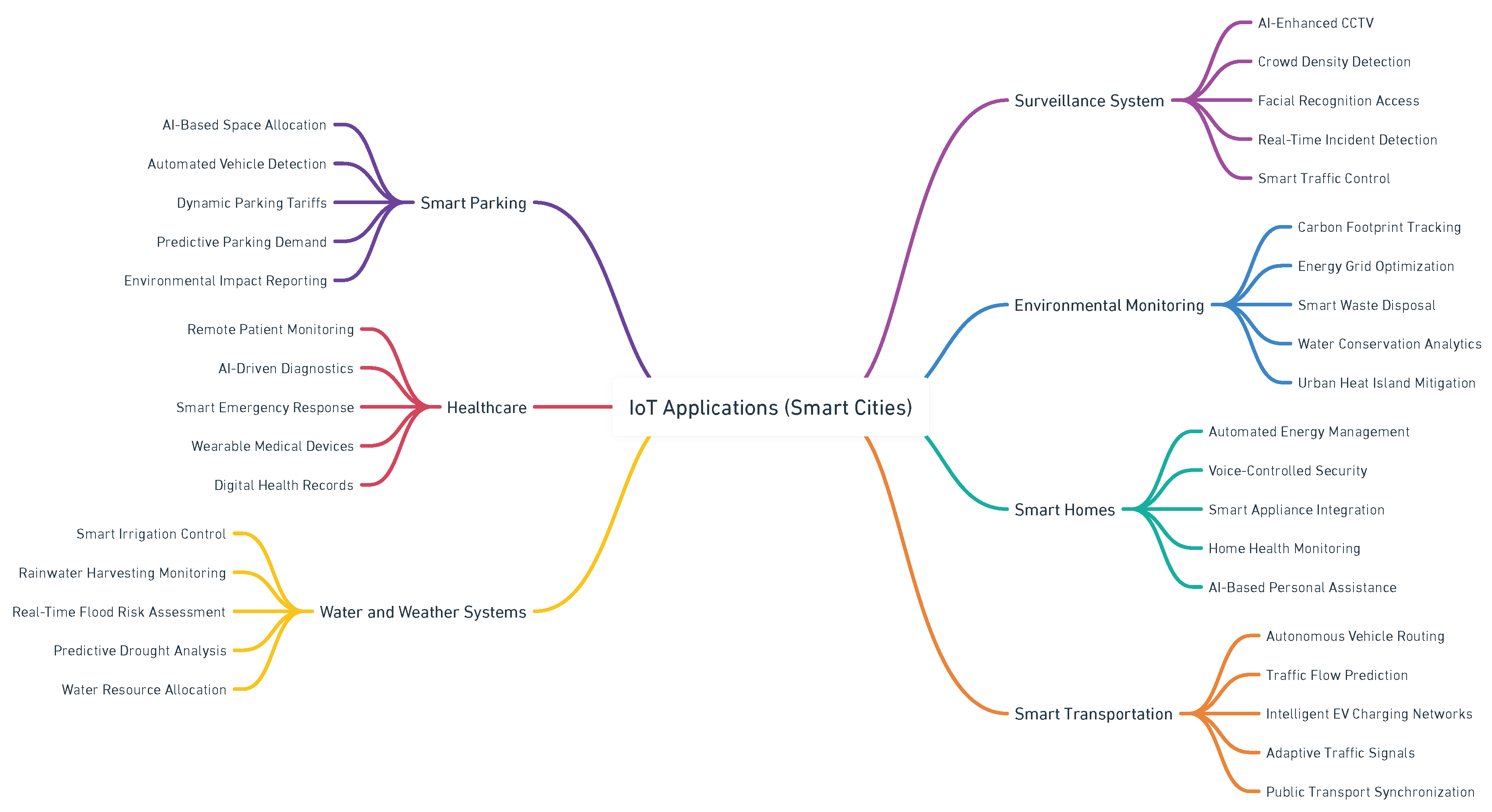
2.1. Internet of Things for Smart Cities & Transportation
2.2. Internet of Things Smart Home System
2.3. Internet of Medical Things
2.4. Internet of Agricultural Things
2.5. Internet of Battlefield Things
2.6. Commonly Used Protocols:
- ZigBee
- Dash7
- WiFi
- Cellular
- 6LoWPAN
- Bluetooth
- Bluetooth Low Energy (BLE)
- LoRa & LoRaWAN
- SigFox
- Narrowband Internet of Things (NB-IoT)
- Near Field Communication (NFC)
- Z-Wave
- Li-Fi
- Ultra-Wideband (UWB)
- Advanced Message Queuing Protocol (AMQP)
- Constrained Application Protocol (CoAP)
- Message Queuing Telemetry Transport Protocol (MQTT)
- Data Distribution Service (DDS)
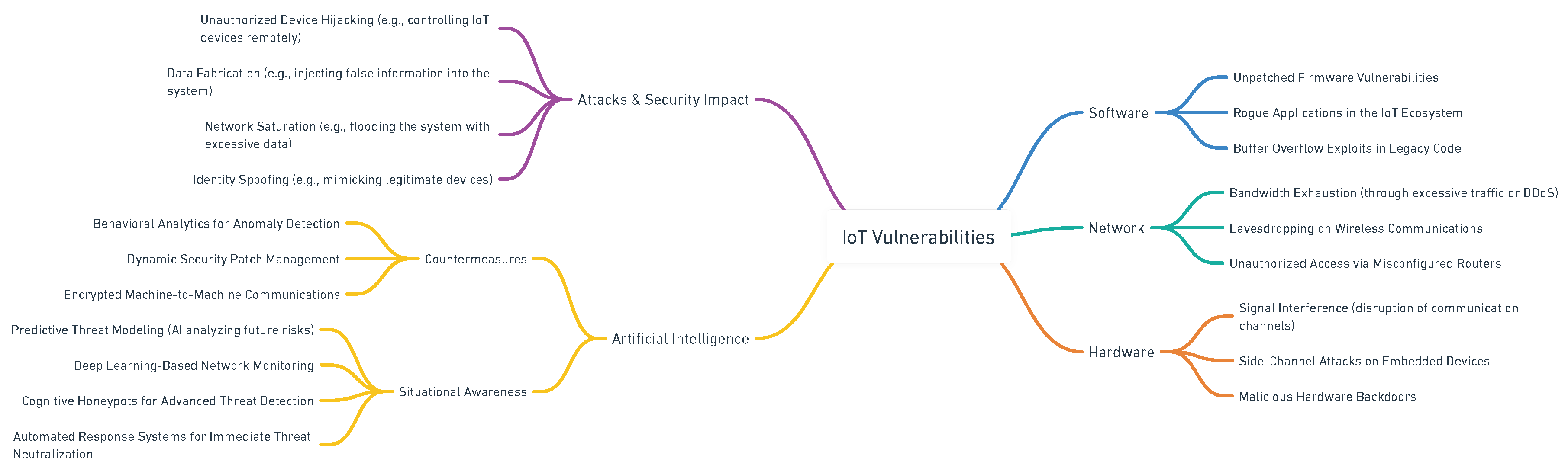
3. IoT Vulnerability Layers
3.1. Hardware Vulnerabilities
3.1.1. Radio Frequency Attacks
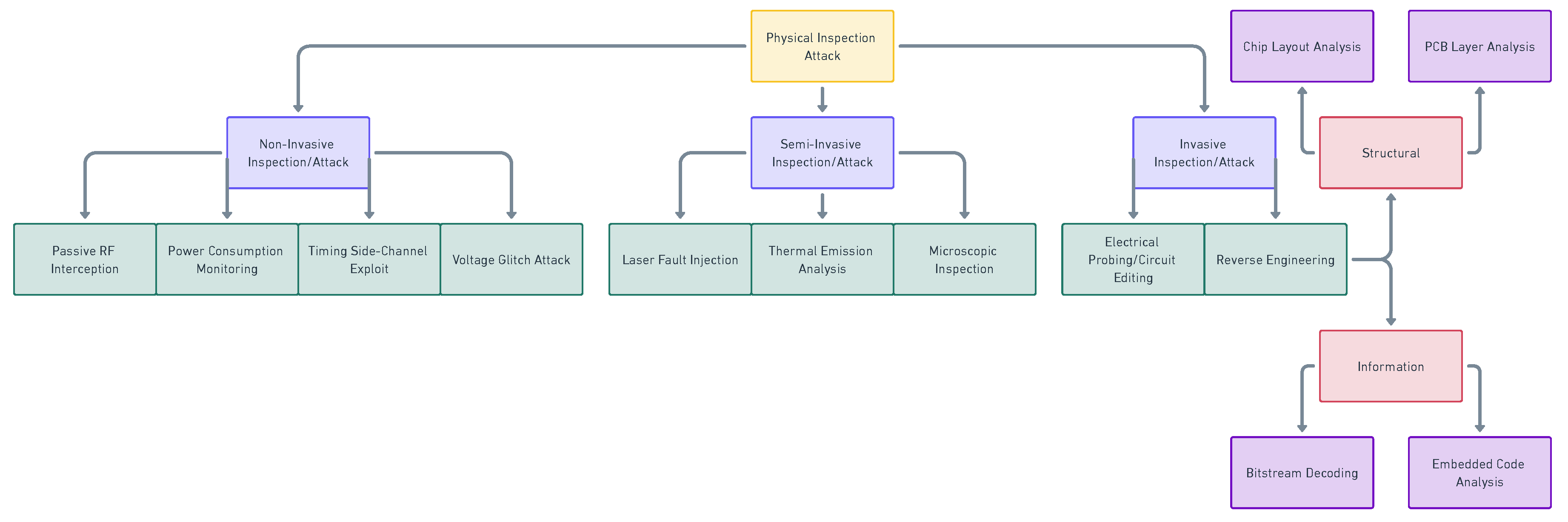
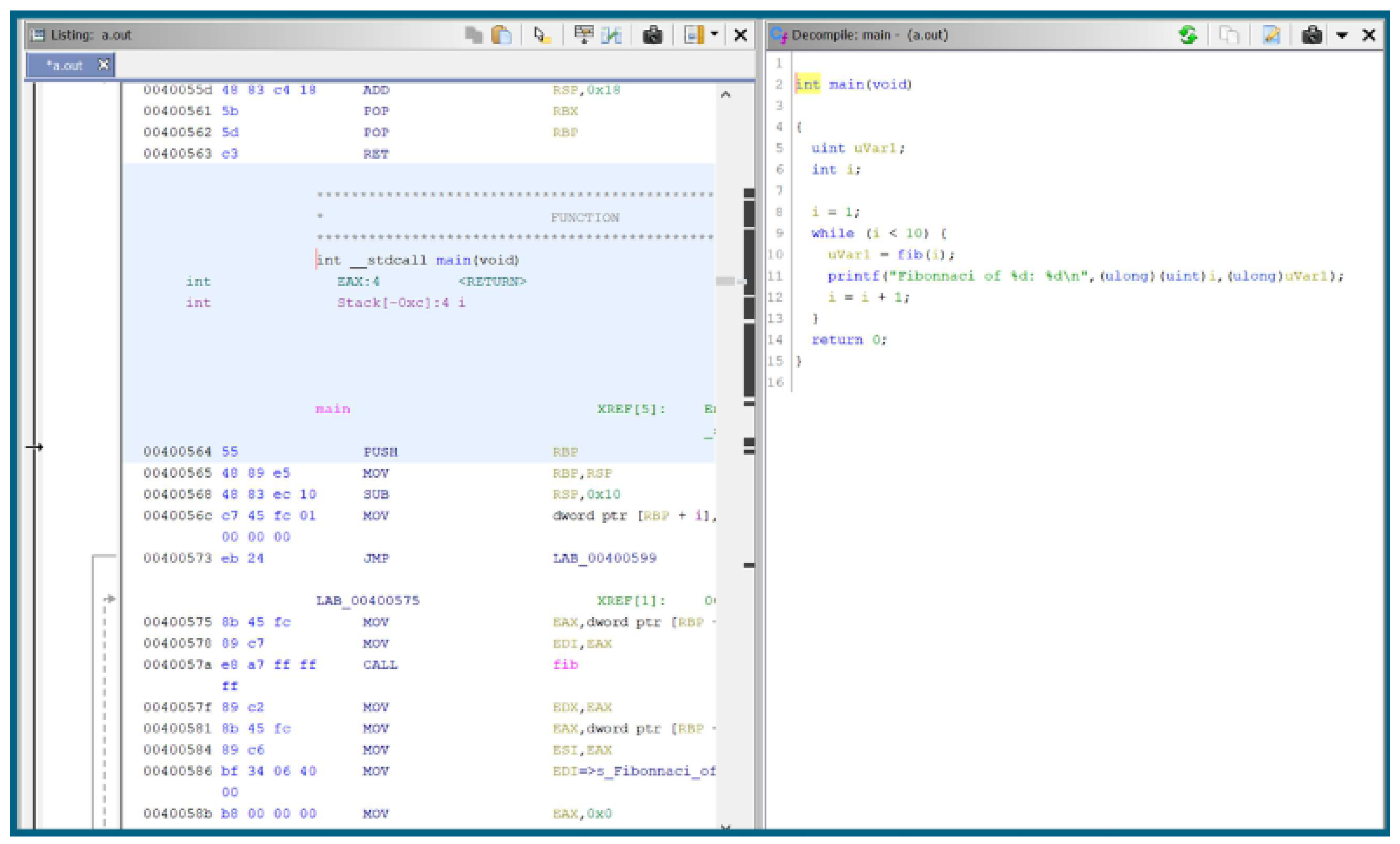
3.1.2. Hardware Reverse Engineering & Micro-probing
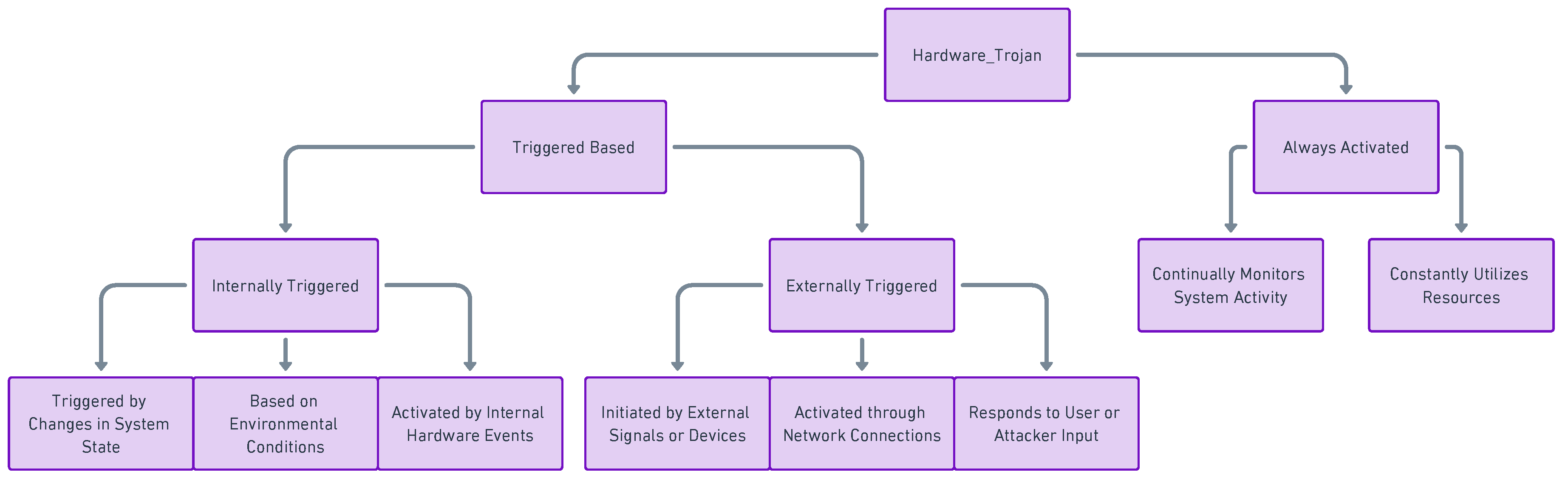
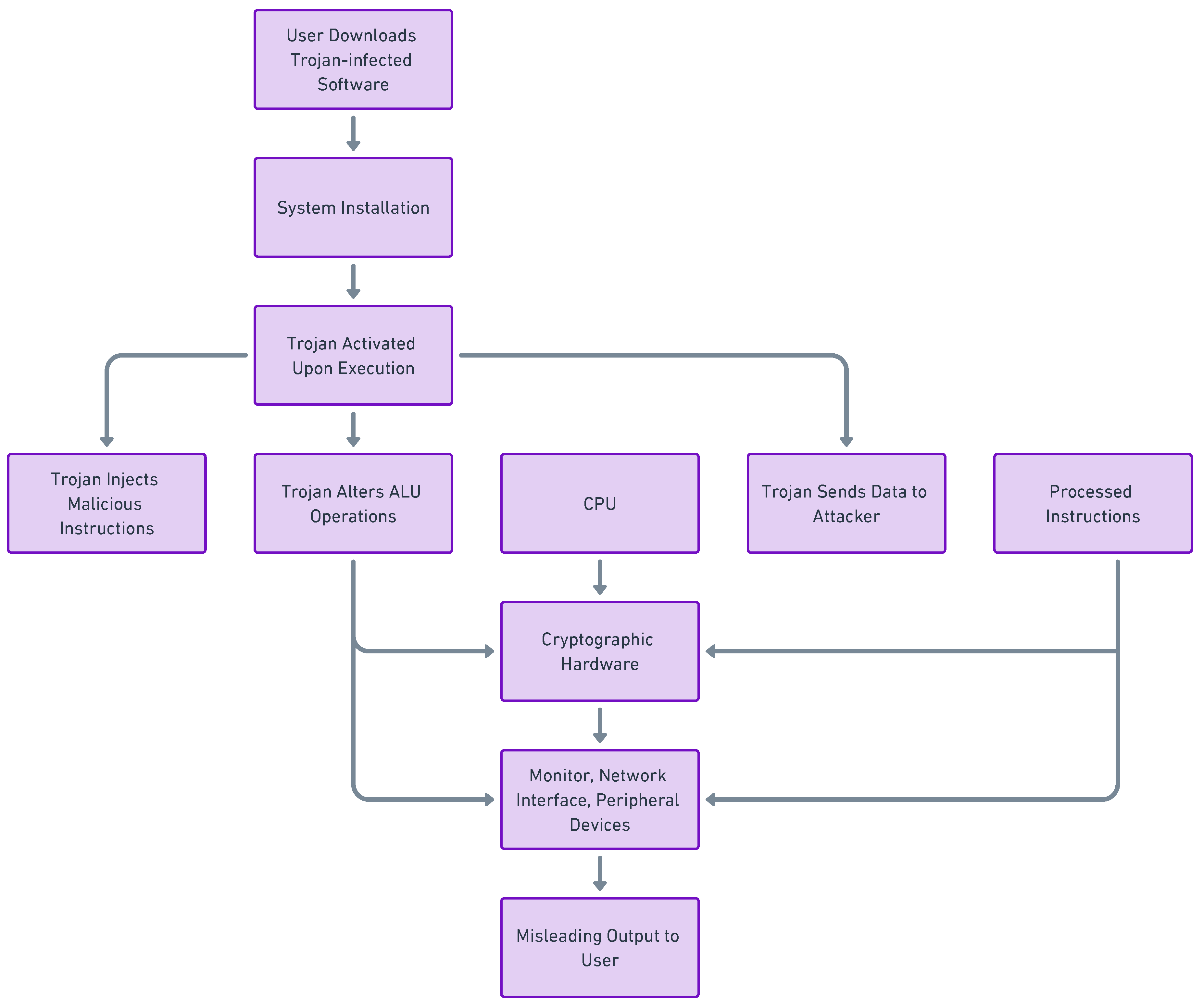
3.1.3. Implants & Hardware Trojans
3.2. Software Vulnerabilities
3.3. Network Vulnerabilities
3.3.1. WiFi & Ethernet Based Networks
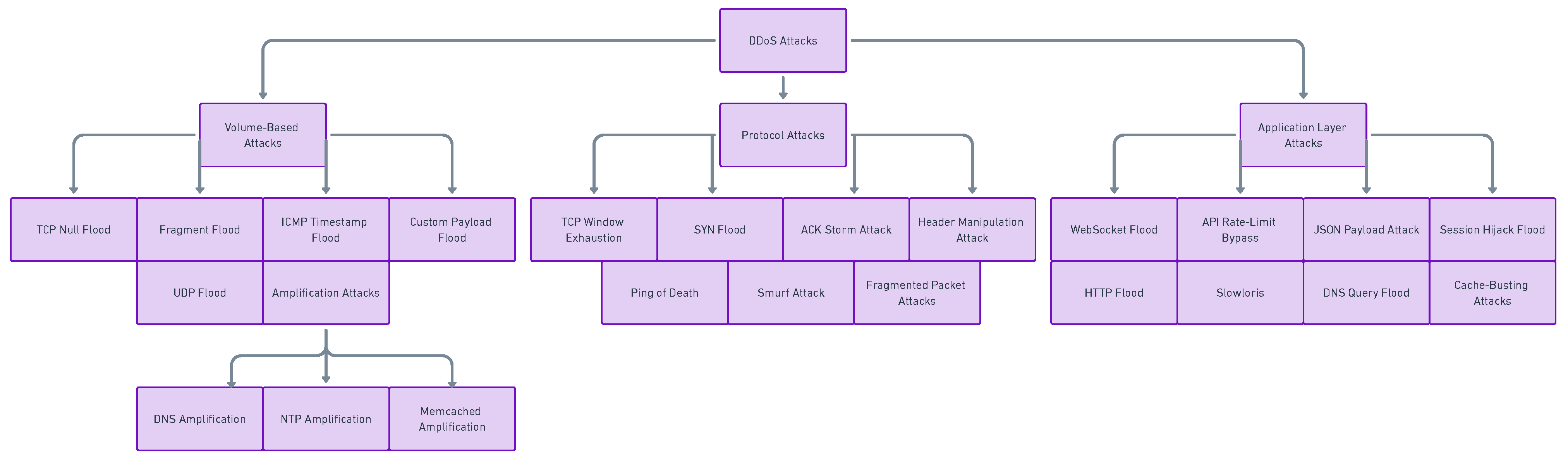
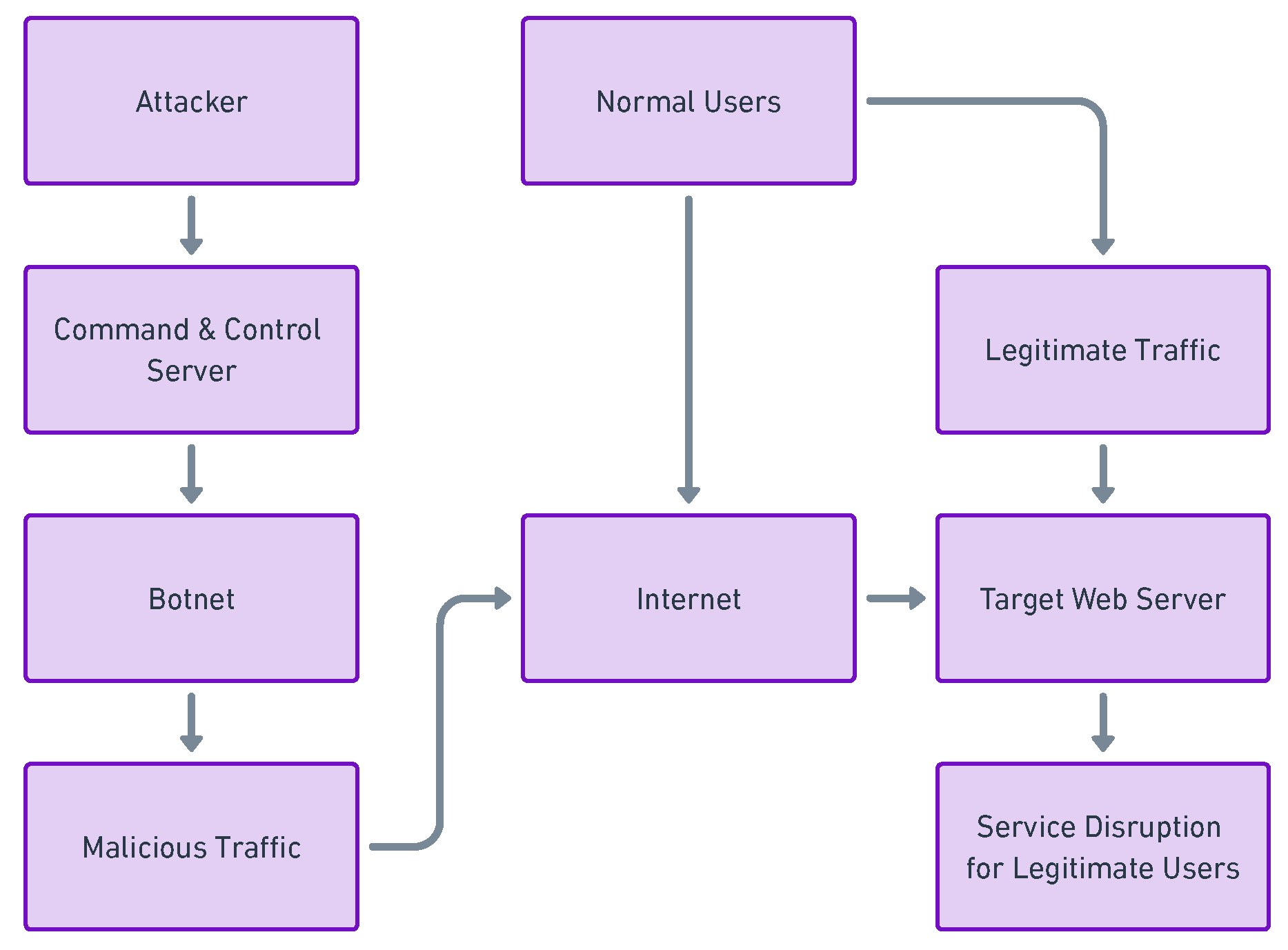
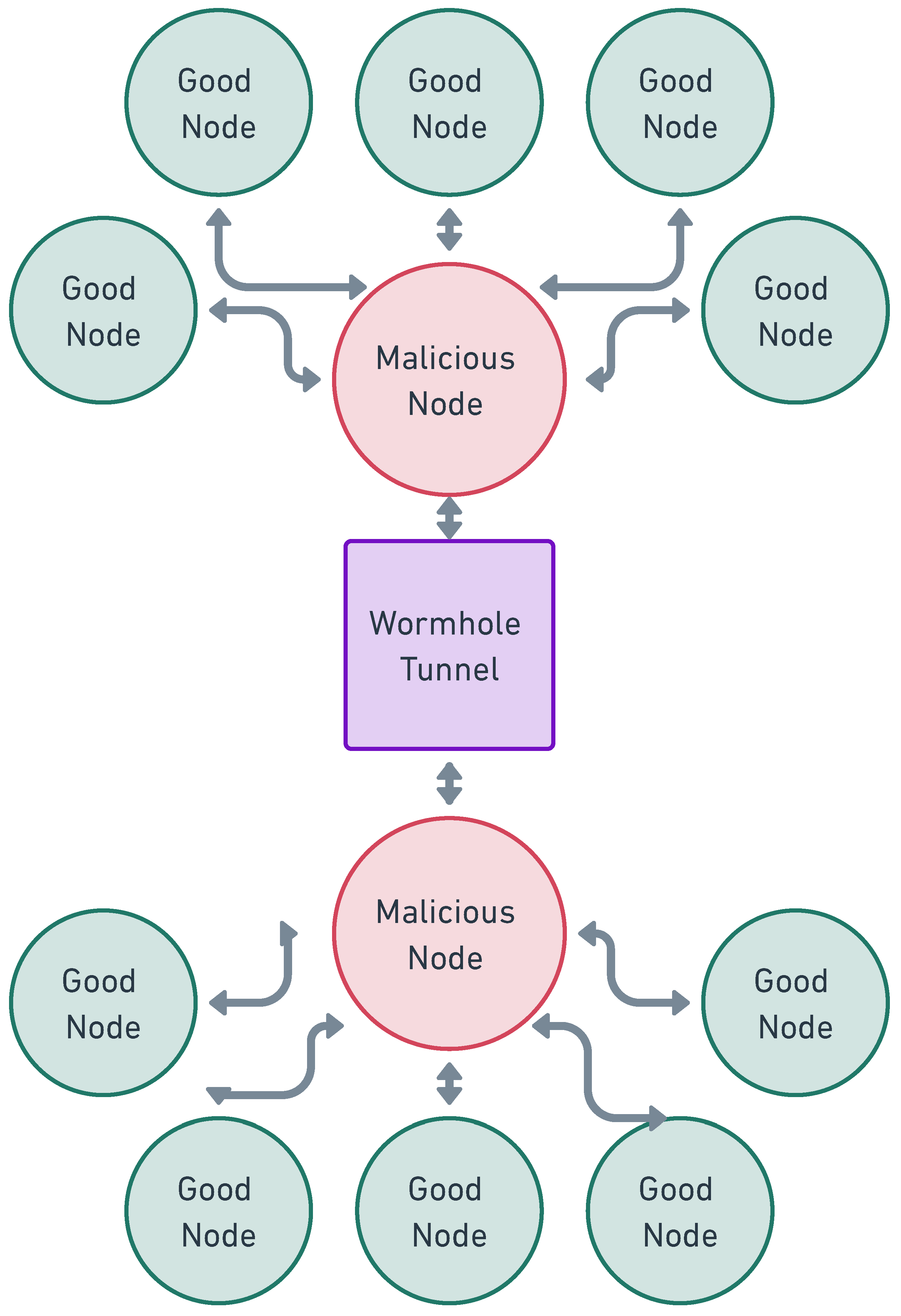
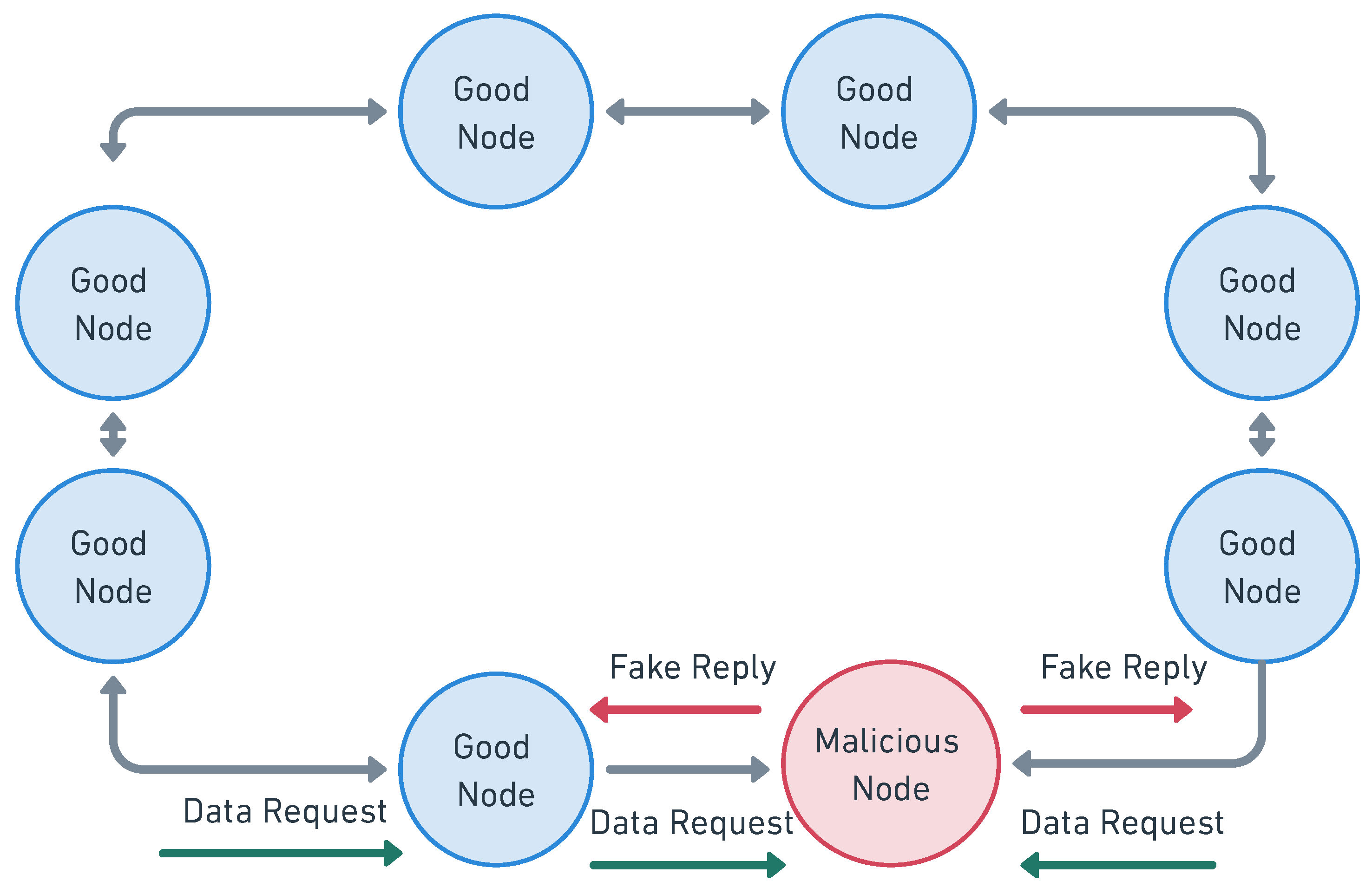
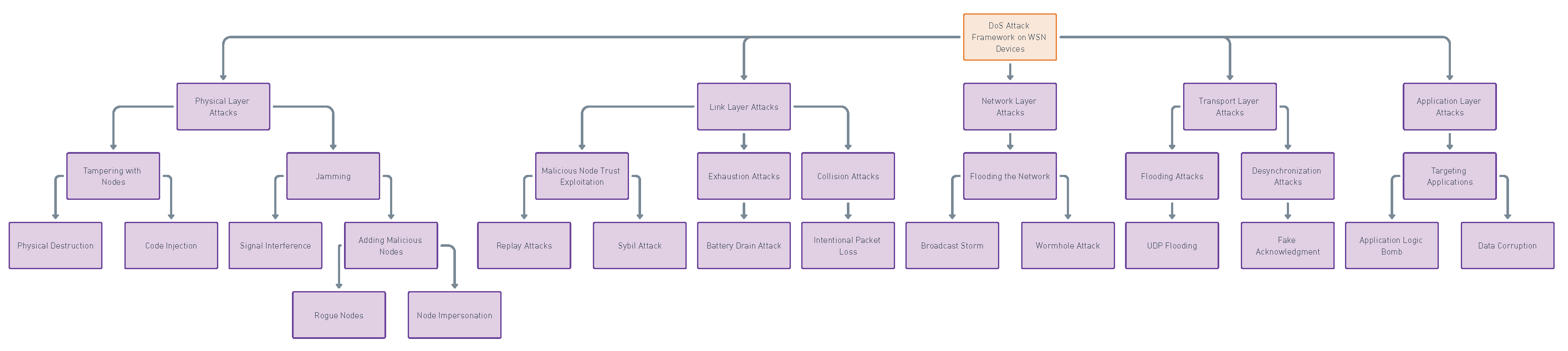
3.3.2. Wireless Sensor Networks
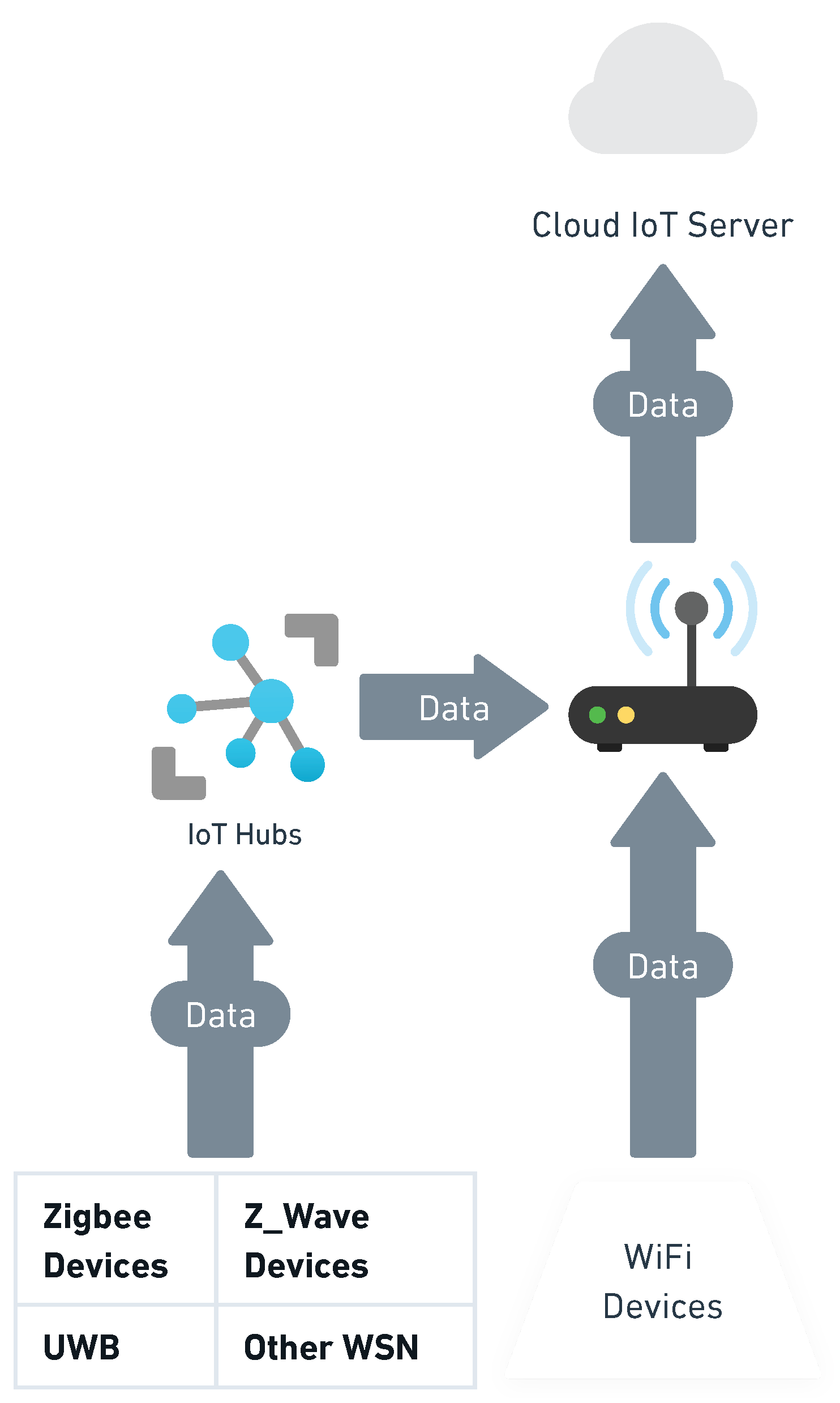
3.3.3. Cloud Based Networks
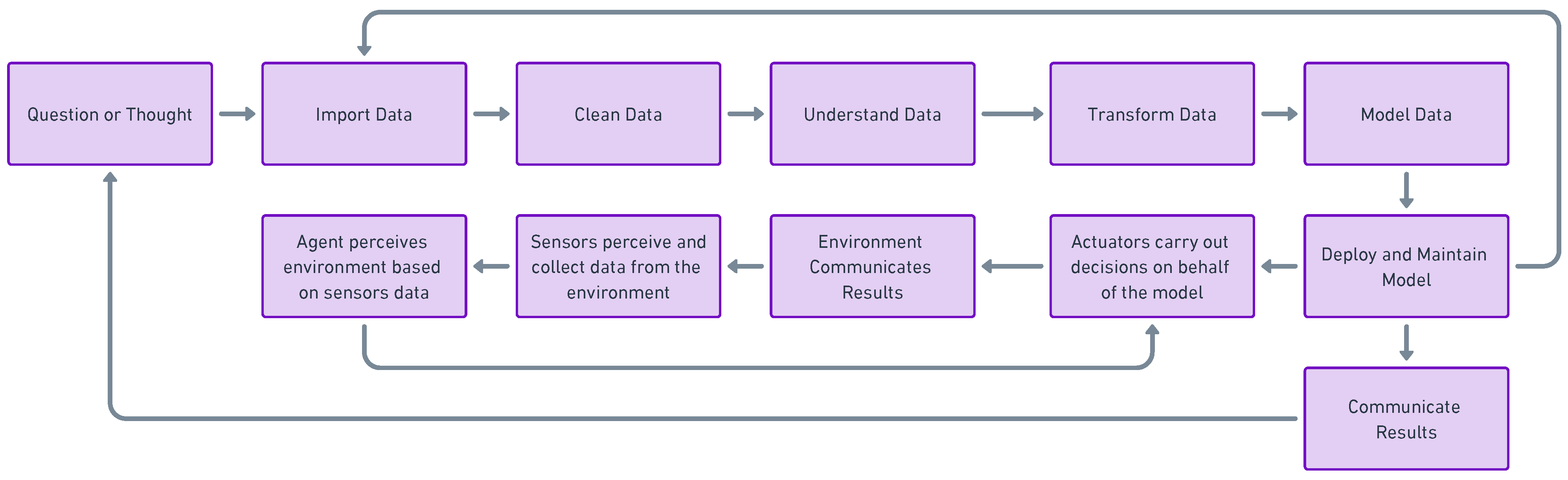
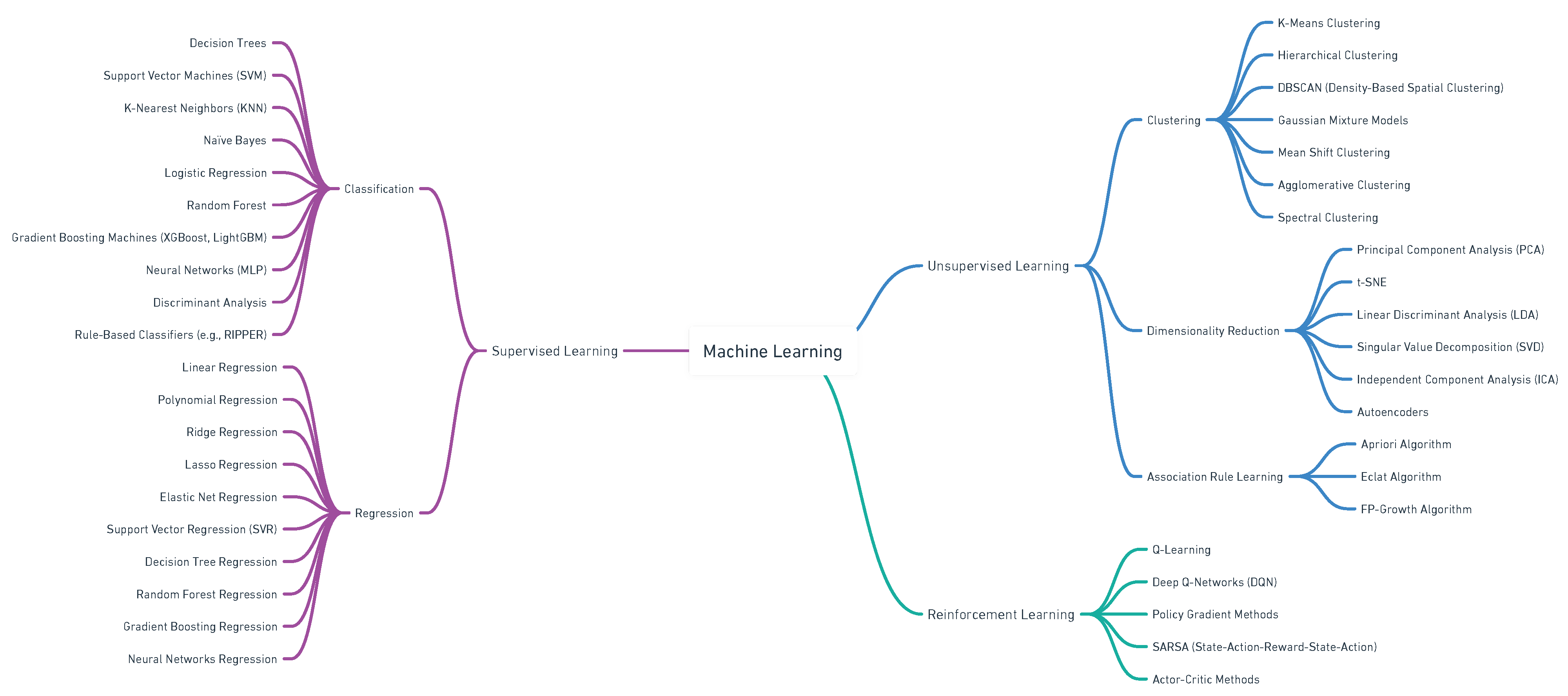
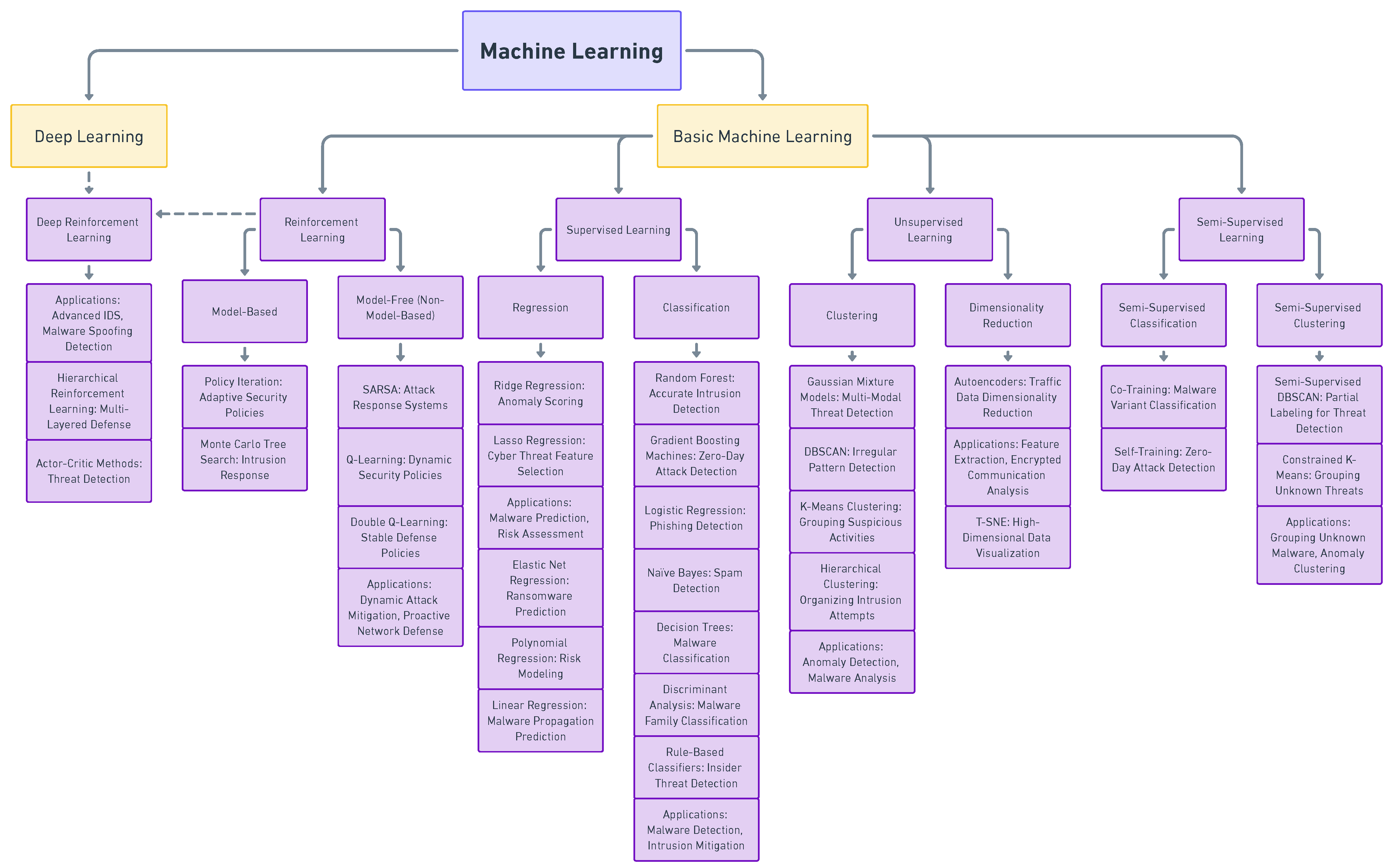
4. Artificial Intelligence
4.1. Artificial Intelligence General Overview
4.2. Artificial Intelligence & IoT
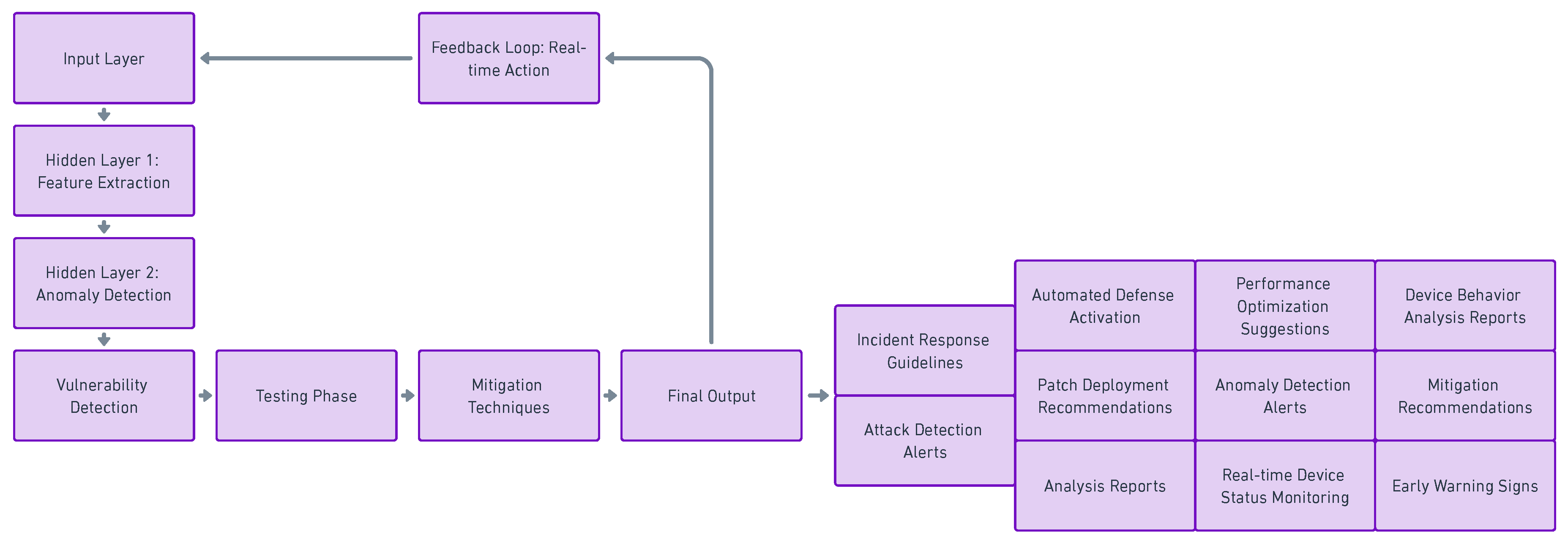
4.2.1. Learning Based Detection for Cybersecurity Use
4.2.2. Deep Learning for IoT Vulnerabilities
4.3. Issues with using Artificial Intelligence for IoT Security
5. The Cloud
5.1. Artificial Intelligence & The Cloud for IoT Security
5.2. Issues with using Artificial Intelligence with The Cloud for IoT Security
6. Conclusion and Future Research to be Worked
7. Acknowledgment
| Abbreviation | Full Form | Abbreviation | Full Form | Abbreviation | Full Form |
|---|---|---|---|---|---|
| 5G | Fifth Generation (Cellular Network) | 6LoWPAN | IPv6 over Low-Power Wireless Personal Area Networks | AES | Advanced Encryption Standard |
| AI | Artificial Intelligence | AIoT | Artificial Intelligence of Things | AMQP | Advanced Message Queuing Protocol |
| ARP | Address Resolution Protocol | BLE | Bluetooth Low Energy | CGM | Continuous Glucose Monitor |
| CoAP | Constrained Application Protocol | CPU | Central Processing Unit | DaaS | Desktop as a Service |
| DDoS | Distributed Denial of Service | DDS | Data Distribution Service | DL | Deep Learning |
| DoS | Denial of Service | E-DDoS | Energy-Oriented Distributed Denial of Service | ECG | Electrocardiogram |
| FaaS | Function as a Service | FPGA | Field-Programmable Gate Array | GPU | Graphics Processing Unit |
| HMI | Human-Machine Interface | HTTP | Hypertext Transfer Protocol | IaaS | Infrastructure as a Service |
| IC | Integrated Circuit | ICMP | Internet Control Message Protocol | ICP | Internet Cache Protocol |
| IDS | Intrusion Detection System | IEEE | Institute of Electrical and Electronics Engineers | IoAT | Internet of Agricultural Things |
| IoBT | Internet of Battlefield Things | IoMT | Internet of Medical Things | IoT | Internet of Things |
| IP | Internet Protocol | IPv6 | Internet Protocol Version 6 | JTAG | Joint Test Action Group |
| LAN | Local Area Network | LoRaWAN | Long Range Wide Area Network | LPWAN | Low-Power Wide-Area Network |
| LTE-A | Long-Term Evolution Advanced | ML | Machine Learning | MQTT | Message Queuing Telemetry Transport |
| NB-IoT | Narrowband Internet of Things | NFC | Near Field Communication | PaaS | Platform as a Service |
| PC | Personal Computer | PCB | Printed Circuit Board | QBit | Quantum Bit |
| SaaS | Software as a Service | SMTP | Simple Mail Transfer Protocol | SSL | Secure Sockets Layer |
| SYN | Synchronize | TCP | Transmission Control Protocol | TCP/IP | Transmission Control Protocol/Internet Protocol |
| TLS | Transport Layer Security | UDP | User Datagram Protocol | UAV | Unmanned Aerial Vehicle |
| UWB | Ultra-Wideband | V2I | Vehicle-to-Infrastructure | V2V | Vehicle-to-Vehicle |
| WEP | Wired Equivalent Privacy | Wi-Fi | Wireless Fidelity | WiMAX | Worldwide Interoperability for Microwave Access |
| WLAN | Wireless Local Area Network | WPA | Wi-Fi Protected Access | WPA2 | Wi-Fi Protected Access II |
| WPA3 | Wi-Fi Protected Access III | WSN | Wireless Sensor Network |
References
- Zhong, C.L.; Zhu, Z.; Huang, R.G. Study on the IOT Architecture and Gateway Technology 2015. pp. 196–199. [CrossRef]
- Pico-Valencia, P.; Holgado-Terriza, J.A.; Quiñónez-Ku, X. A Brief Survey of the Main Internet-Based Approaches. An Outlook from the Internet of Things Perspective 2020. pp. 536–542. [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Communications Surveys and Tutorials 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Singh, D.; Tripathi, G.; Jara, A.J. A survey of Internet-of-Things: Future vision, architecture, challenges and services 2014. pp. 287–292. [CrossRef]
- Arasteh, H.; Hosseinnezhad, V.; Loia, V.; Tommasetti, A.; Troisi, O.; Shafie-khah, M.; Siano, P. Iot-based smart cities: A survey 2016. pp. 1–6. [CrossRef]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of Things for Smart Cities. Internet of Things Journal, IEEE 2012, 1. [Google Scholar] [CrossRef]
- Sivapriyan, R.; Rao, K.M.; Harijyothi, M. Literature Review of IoT based Home Automation System 2020. pp. 101–105. [CrossRef]
- CardiacSense. Heart Rate Monitor Watch. https://www.cardiacsense.com/heart-rate-monitor-watch/, 2023. Accessed: June 2023.
- Islam, S.M.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K. The Internet of Things for Health Care: A Comprehensive Survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Farooq, M.S.; Riaz, S.; Abid, A.; Abid, K.; Naeem, M.A. A Survey on the Role of IoT in Agriculture for the Implementation of Smart Farming. IEEE Access 2019, 7, 156237–156271. [Google Scholar] [CrossRef]
- SeeTree. About Us. https://www.seetree.ai/about-seetree, 2017. Accessed: September 2023.
- Shachar, O.; Yushchuk, M.; Salton-Morgenstern, G. Recurrent pattern image classification and registration, Jan, 2020.
- Kott, A.; Swami, A.; West, B.J. The Internet of Battle Things. Computer 2016, 49, 70–75. [Google Scholar] [CrossRef]
- Russell, S.; Abdelzaher, T. The Internet of Battlefield Things: The Next Generation of Command, Control, Communications and Intelligence (C3I) Decision-Making 2018. pp. 737–742. [CrossRef]
- Farahani, S. ZigBee Wireless Networks and Transceivers; Newnes, 2011.
- Ergen, S.C. ZigBee/IEEE 802.15. 4 Summary. UC Berkeley, September 2004, 10, 11. [Google Scholar]
- Elahi, A.; Gschwender, A. ZigBee Wireless Sensor and Control Network; Pearson Educ.: London, U.K., 2009. [Google Scholar]
- Norair, J. Introduction to DASH7 technologies. Dash7 alliance low power RF technical overview 2009, pp. 1–22.
- Piromalis, D.; Arvanitis, K.; Sigrimis, N. DASH7 mode 2: A promising perspective for wireless agriculture. IFAC Proceedings Volumes 2013, 46, 127–132. [Google Scholar] [CrossRef]
- Ayoub, W.; Samhat, A.E.; Nouvel, F.; Mroue, M.; Prévotet, J.C. Internet of Mobile Things: Overview of LoRaWAN, DASH7, and NB-IoT in LPWANs Standards and Supported Mobility. IEEE Communications Surveys and Tutorials 2019, 21, 1561–1581. [Google Scholar] [CrossRef]
- Czyz, J.; Luckie, M.J.; Allman, M.; Bailey, M. Don’t forget to lock the back door! A characterization of IPv6 network security policy. Proc. NDSS, 2016.
- Lashkari, A.H.; Danesh, M.M.S.; Samadi, B. A survey on wireless security protocols (WEP, WPA and WPA2/802.11 i) 2009. pp. 48–52.
- Kohlios, C.P.; Hayajneh, T. A comprehensive attack flow model and security analysis for Wi-Fi and WPA3. Electronics 2018, 7, 284. [Google Scholar] [CrossRef]
- Alliance, W.F. Wi-Fi Alliance Official Website. https://www.wi-fi.org/. Accessed: September 2023.
- Banerji, S.; Chowdhury, R.S. On IEEE 802.11: Wireless Lan Technology. International Journal of Mobile Network Communications &Telematics 2013, 3, 45–64. [Google Scholar] [CrossRef]
- Ezhilarasan, E.; Dinakaran, M. A review on mobile technologies: 3G, 4G and 5G. 2017 second international conference on recent trends and challenges in computational models (ICRTCCM). IEEE, 2017, pp. 369–373.
- Akyildiz, I.F.; Gutierrez-Estevez, D.M.; Reyes, E.C. The evolution to 4G cellular systems: LTE-Advanced. Physical communication 2010, 3, 217–244. [Google Scholar] [CrossRef]
- Zhang, Y.; Årvidsson, A. Understanding the characteristics of cellular data traffic. Proceedings of the 2012 ACM SIGCOMM workshop on Cellular networks: operations, challenges, and future design, 2012, pp. 13–18.
- Chettri, L.; Bera, R. A comprehensive survey on Internet of Things (IoT) toward 5G wireless systems. IEEE Internet of Things Journal 2019, 7, 16–32. [Google Scholar] [CrossRef]
- Zeqiri, R.; Idrizi, F.; Halimi, H. Comparison of Algorithms and Technologies 2G, 3G, 4G and 5G. 2019 3rd International Symposium on Multidisciplinary Studies and Innovative Technologies (ISMSIT). IEEE, 2019, pp. 1–4.
- Shelby, Z.; Bormann, C. 6LoWPAN: The wireless embedded Internet; John Wiley & Sons, 2011.
- Mulligan, G. The 6LoWPAN architecture. Proceedings of the 4th workshop on Embedded networked sensors, 2007, pp. 78–82.
- Mulligan, G. The 6LoWPAN architecture 2007. pp. 78–82.
- Baker, N. ZigBee and Bluetooth: Strengths and weaknesses for industrial applications. Computing and Control Engineering 2005, 16, 20–25. [Google Scholar] [CrossRef]
- Bisdikian, C. An overview of the Bluetooth wireless technology. IEEE Communications Magazine 2001, 39, 86–94. [Google Scholar] [CrossRef]
- Tosi, J.; Taffoni, F.; Santacatterina, M.; Sannino, R.; Formica, D. Performance evaluation of bluetooth low energy: A systematic review. Sensors 2017, 17, 2898. [Google Scholar] [CrossRef]
- Group, B.S.I. Technology Overview. https://www.bluetooth.com/learn-about-bluetooth/tech-overview/. Accessed: September 2023.
- Haxhibeqiri, J.; De Poorter, E.; Moerman, I.; Hoebeke, J. A survey of LoRaWAN for IoT: From technology to application. Sensors 2018, 18, 3995. [Google Scholar] [CrossRef]
- Khutsoane, O.; Isong, B.; Abu-Mahfouz, A.M. IoT devices and applications based on LoRa/LoRaWAN. IECON 2017-43rd Annual Conference of the IEEE Industrial Electronics Society. IEEE, 2017, pp. 6107–6112.
- Lavric, A.; Petrariu, A.I.; Popa, V. Long range sigfox communication protocol scalability analysis under large-scale, high-density conditions. IEEE Access 2019, 7, 35816–35825. [Google Scholar] [CrossRef]
- Fourtet, C.; Ponsard, B. An introduction to Sigfox radio system. In LPWAN Technologies for IoT and M2M Applications; Elsevier, 2020; pp. 103–118.
- Sigfox. Sigfox 0G Technology. https://www.sigfox.com/, 2023. Accessed: May 2023.
- Ratasuk, R.; Vejlgaard, B.; Mangalvedhe, N.; Ghosh, A. NB-IoT system for M2M communication 2016. pp. 1–5. [CrossRef]
- Coskun, V.; Ok, K.; Ozdenizci, B. Near field communication (NFC): From theory to practice; JohnWiley & Sons, 2011.
- Coskun, V.; Ozdenizci, B.; Ok, K. A survey on near field communication (NFC) technology. Wireless personal communications 2013, 71, 2259–2294. [Google Scholar] [CrossRef]
- Danbatta, S.J.; Varol, A. Comparison of Zigbee, Z-Wave, Wi-Fi, and bluetooth wireless technologies used in home automation. 2019 7th International Symposium on Digital Forensics and Security (ISDFS). IEEE, 2019, pp. 1–5.
- Alliance, Z.W. Z-Wave Official Website. https://www.z-wave.com/. Accessed: September 2023.
- Bhavya, R.; Lokesh, M. A Survey on Li-Fi Technology. An International Journal of Engineering & Technology 2016, 3. [Google Scholar]
- Haas, H.; Yin, L.; Wang, Y.; Chen, C. What is LiFi? Journal of Lightwave Technology 2016, 34, 1533–1544. [Google Scholar] [CrossRef]
- LiFi.co. How LiFiWorks. https://lifi.co/how-lifi-works/, 2023. Accessed: May 2023.
- Zhuang, W.; Shen, X.; Bi, Q. Ultra-wideband wireless communications. Wireless communications and mobile computing 2003, 3, 663–685. [Google Scholar] [CrossRef]
- Hirt, W. Ultra-wideband radio technology: overview and future research. Computer Communications 2003, 26, 46–52. [Google Scholar] [CrossRef]
- Aiello, G.; Rogerson, G. Ultra-wideband wireless systems. IEEE Microwave Magazine 2003, 4, 36–47. [Google Scholar] [CrossRef]
- Naik, N. Choice of effective messaging protocols for IoT systems: MQTT, CoAP, AMQP and HTTP 2017. pp. 1–7. [CrossRef]
- Fernandes, J.L.; Lopes, I.C.; Rodrigues, J.J.; Ullah, S. Performance evaluation of RESTful web services and AMQP protocol. 2013 Fifth international conference on ubiquitous and future networks (ICUFN). IEEE, 2013, pp. 810–815.
- Betzler, A.; Gomez, C.; Demirkol, I.; Paradells, J. CoAP congestion control for the internet of things. IEEE Communications Magazine 2016, 54, 154–160. [Google Scholar] [CrossRef]
- Chen, Y.; Kunz, T. Performance evaluation of IoT protocols under a constrained wireless access network. 2016 International Conference on Selected Topics in Mobile & Wireless Networking (MoWNeT), 2016, pp. 1–7. [CrossRef]
- (OMG), O.M.G. The real-time publish-subscribe wire protocol DDS interoperability wire protocol specification. OMG, Version 2.2 2014.
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Communications Surveys and Tutorials 2019, 21. [Google Scholar] [CrossRef]
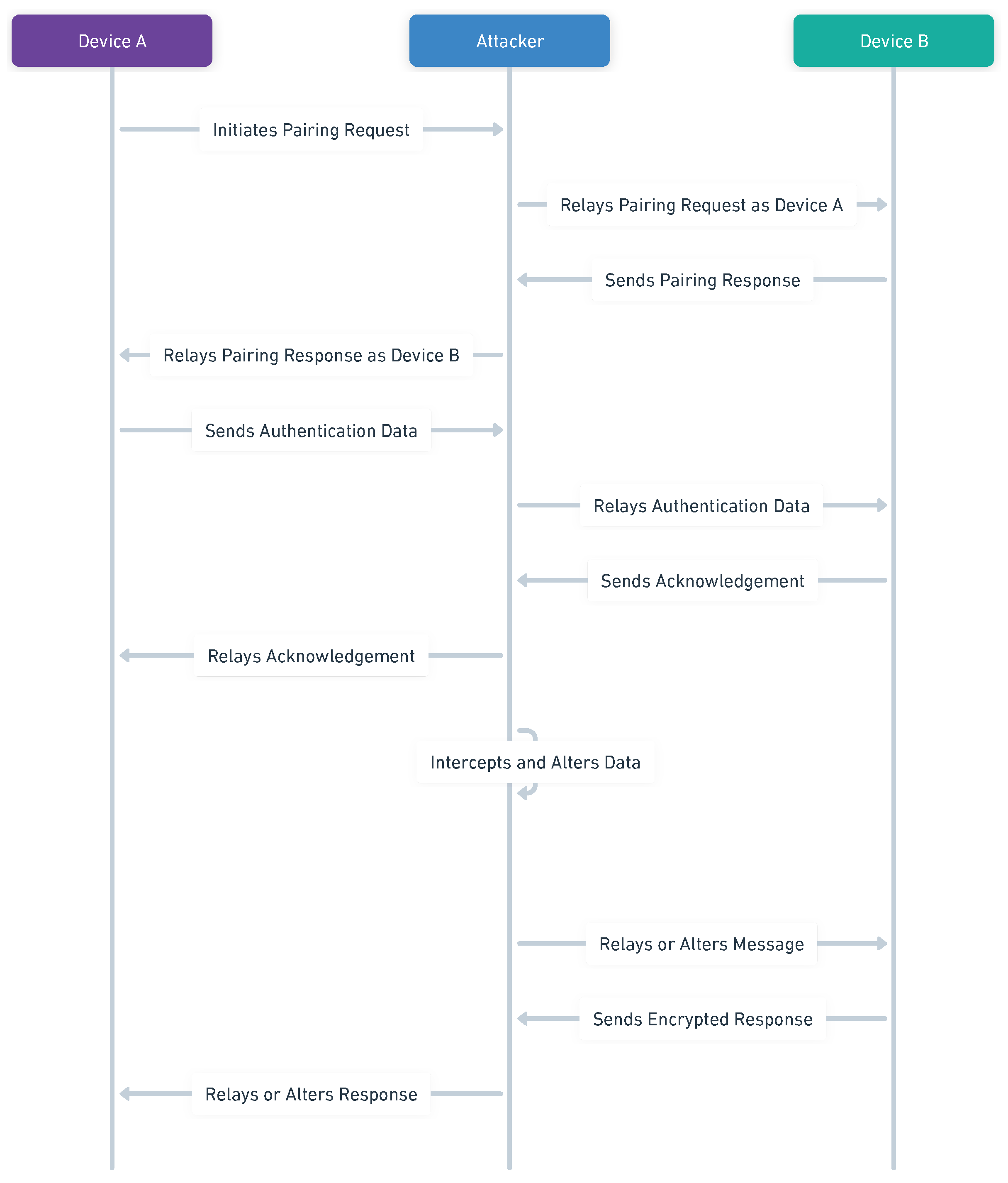
- Haataja, K.; Toivanen, P. Two practical man-in-the-middle attacks on Bluetooth secure simple pairing and countermeasures. IEEE Transactions on Wireless Communications 2010, 9, 384–392. [Google Scholar] [CrossRef]
- Rahman, M.T.; Shi, Q.; Tajik, S.; Shen, H.; Woodard, D.L.; Tehranipoor, M.; Asadizanjani, N. Physical Inspection & Attacks: New Frontier in Hardware Security. 2018 IEEE 3rd International Verification and Security Workshop (IVSW), 2018, pp. 93–102. [CrossRef]
- Wurm, J.; Hoang, K.; Arias, O.; Sadeghi, A.R.; Jin, Y. Security analysis on consumer and industrial IoT devices. Proc. 21st Asia South Pac. Design Autom. Conf. (ASP-DAC), 2016, pp. 519–524.
- Bou-Harb, E.; Fachkha, C.; Pourzandi, M.; Debbabi, M.; Assi, C. Communication security for smart grid distribution networks. IEEE Commun. Mag. 2013, 51, 42–49. [Google Scholar] [CrossRef]
- Koley, S.; Ghosal, P. Addressing Hardware Security Challenges in Internet of Things: Recent Trends and Possible Solutions. 2015 IEEE 12th Intl Conf on Ubiquitous Intelligence and Computing and 2015 IEEE 12th Intl Conf on Autonomic and Trusted Computing and 2015 IEEE 15th Intl Conf on Scalable Computing and Communications and Its Associated Workshops (UIC-ATC-ScalCom), 2015, pp. 517–520. [CrossRef]
- Pan, Z.; Mishra, P. Design of AI Trojans for Evading Machine Learning-based Detection of Hardware Trojans. 2022 Design, Automation & Test in Europe Conference & Exhibition (DATE), 2022, pp. 682–687. [CrossRef]
- Gaydos, M.G.;Wallace, N.L.; Brown, R.G. Reverse Engineering and Embedded Processor Analysis. Technical report, Sandia National Lab.(SNL-NM), Albuquerque, NM (United States), 2020.
- Tushir, B.; Dalal, Y.; Dezfouli, B.; Liu, Y. A Quantitative Study of DDoS and E-DDoS Attacks on WiFi Smart Home Devices. IEEE Internet of Things Journal 2021, 8, 6282–6292. [Google Scholar] [CrossRef]
- Ashfaq, M.F.; Malik, M.; Fatima, U.; Shahzad, M.K. Classification of IoT based DDoS Attack using Machine Learning Techniques. 2022 16th International Conference on Ubiquitous Information Management and Communication (IMCOM), 2022, pp. 1–6. [CrossRef]
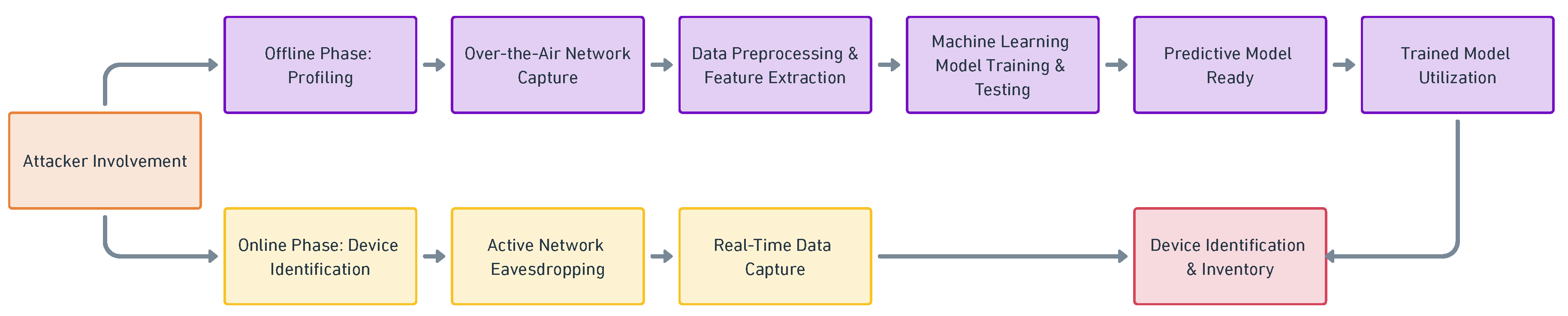
- Alyami, M.; Alharbi, I.; Zou, C.; Solihin, Y.; Ackerman, K. WiFi-based IoT Devices Profiling Attack based on Eavesdropping of EncryptedWiFi Traffic. 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), 2022, pp. 385–392. [CrossRef]
- Sinha, S.; G, K. Network layer DoS Attack on IoT System and location identification of the attacker. 2021 Third International Conference on Inventive Research in Computing Applications (ICIRCA), 2021, pp. 22–27. [CrossRef]
- Kumavat, K.S.; Gomes, J. Performance Evaluation of IoT-enabled WSN system With and Without DDoS Attack. 2023 International Conference for Advancement in Technology (ICONAT), 2023, pp. 1–5. [CrossRef]
- Siddiqui, M.N.; Malik, K.R.; Malik, T.S. Performance Analysis of Blackhole and Wormhole Attack in MANET Based IoT. 2021 International Conference on Digital Futures and Transformative Technologies (ICoDT2), 2021, pp. 1–8. [CrossRef]
- Tatar, E.E.; Dener, M. Wormhole Attacks in IoT Based Networks. 2021 6th International Conference on Computer Science and Engineering (UBMK), 2021, pp. 478–482. [CrossRef]
- Verma, M.K.; Dwivedi, R.K. A Survey on Wormhole Attack Detection and Prevention Techniques in Wireless Sensor Networks. 2020 International Conference on Electrical and Electronics Engineering (ICE3), 2020, pp. 326–331. [CrossRef]
- Ali, S.; Khan, M.A.; Ahmad, J.; Malik, A.W.; ur Rehman, A. Detection and prevention of Black Hole Attacks in IOT & WSN. 2018 Third International Conference on Fog and Mobile Edge Computing (FMEC), 2018, pp. 217–226. [CrossRef]
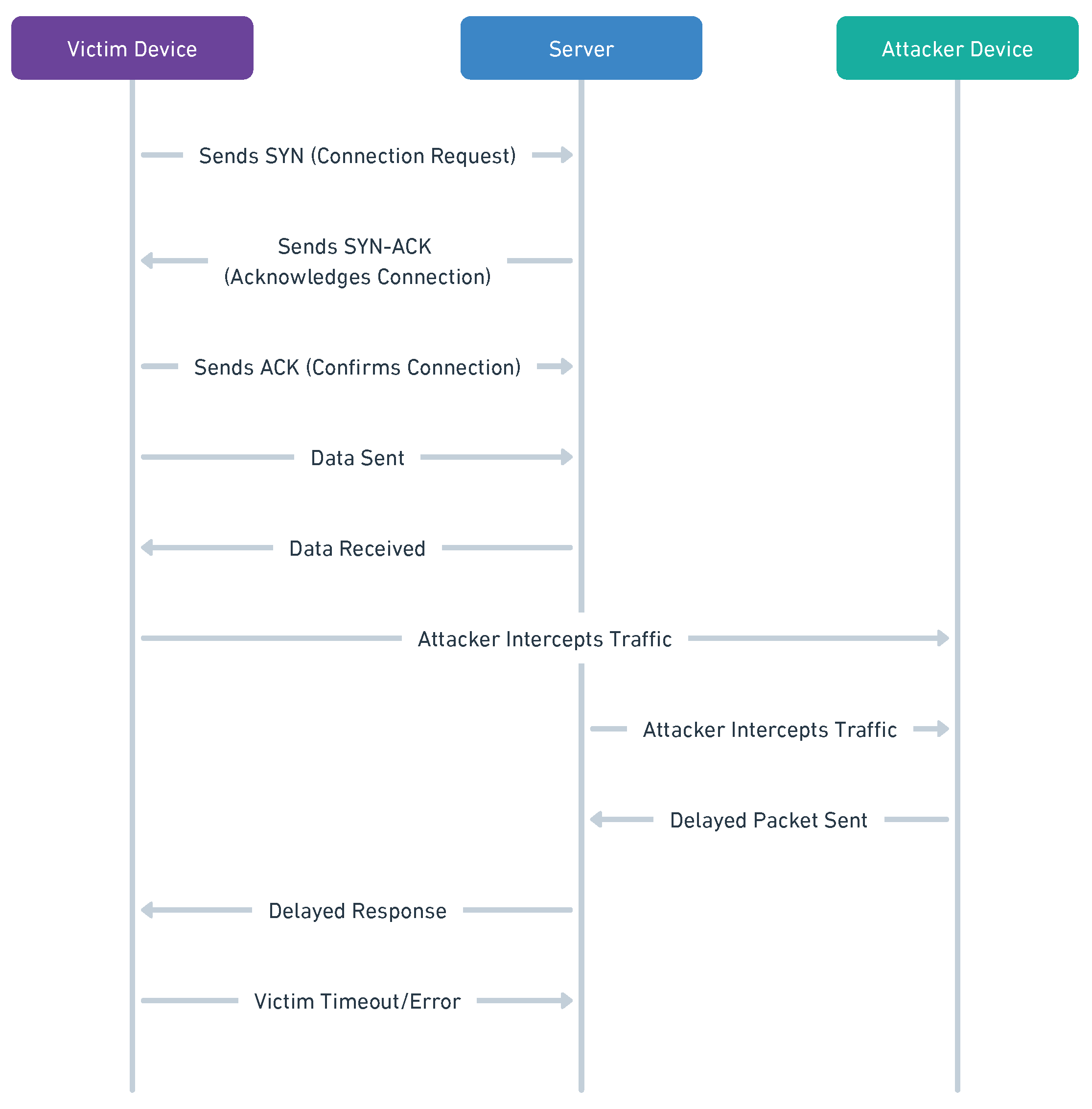
- Fu, C.; Zeng, Q.; Chi, H.; Du, X.; Valluru, S.L. IoT Phantom-Delay Attacks: Demystifying and Exploiting IoT Timeout Behaviors. 2022 52nd Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), 2022, pp. 428–440. [CrossRef]
- Fu, C.; Zeng, Q.; Chi, H.; Du, X.; Valluru, S.L. Iot phantom-delay attacks: Demystifying and exploiting iot timeout behaviors. 2022 52nd Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). IEEE, 2022, pp. 428–440.
- Nassi, B.; Nassi, D.; Ben-Netanel, R.; Mirsky, Y.; Drokin, O.; Elovici, Y. Phantom of the adas: Phantom attacks on driver-assistance systems. Cryptology ePrint Archive 2020. [Google Scholar]
- Whalen, S. An introduction to arp spoofing. Node99 [Online Document] 2001, 563. [Google Scholar]
- Kim, D.W.; Jang, H.Y.; Kim, K.W.; Shin, Y.; Park, S.H. Design characteristics of studies reporting the performance of artificial intelligence algorithms for diagnostic analysis of medical images: results from recently published papers. Korean journal of radiology 2019, 20, 405–410. [Google Scholar] [CrossRef] [PubMed]
- Hussain, F.; Hussain, R.; Hassan, S.A.; Hossain, E. Machine Learning in IoT Security: Current Solutions and Future Challenges. IEEE Communications Surveys & Tutorials 2020, 22, 1686–1721. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q.; Zein-Sabatto, S. An efficient deep-learning-based detection and classification system for cyber-attacks in IoT communication networks. Electronics 2020, 9, 2152. [Google Scholar] [CrossRef]
- Zhang, J.; Pan, L.; Han, Q.L.; Chen, C.; Wen, S.; Xiang, Y. Deep learning based attack detection for cyber-physical system cybersecurity: A survey. IEEE/CAA Journal of Automatica Sinica 2021, 9, 377–391. [Google Scholar] [CrossRef]
- Handa, A.; Sharma, A.; Shukla, S.K. Machine learning in cybersecurity: A review. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery 2019, 9, e1306. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Communications Surveys & Tutorials 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Zohuri, B.; Moghaddam, M. Deep learning limitations and flaws. Mod. Approaches Mater. Sci 2020, 2, 241–250. [Google Scholar] [CrossRef]
- Raji, I.D.; Kumar, I.E.; Horowitz, A.; Selbst, A. The fallacy of AI functionality. Proceedings of the 2022 ACM Conference on Fairness, Accountability, and Transparency, 2022, pp. 959–972.
- Hou, L.; Zhao, S.; Xiong, X.; Zheng, K.; Chatzimisios, P.; Hossain, M.S.; Xiang, W. Internet of things cloud: Architecture and implementation. IEEE Communications Magazine 2016, 54, 32–39. [Google Scholar] [CrossRef]
- Lin, Y.; Shao, L.; Zhu, Z.; Wang, Q.; Sabhikhi, R.K. Wireless network cloud: Architecture and system requirements. IBM Journal of Research and Development 2010, 54, 4–1. [Google Scholar] [CrossRef]
- Varia, J. Cloud architectures. White Paper of Amazon, jineshvaria. s3. amazonaws. com/public/cloudarchitectures-varia. pdf 2008, 16. [Google Scholar]
- Wilder, B. Cloud architecture patterns: using microsoft azure; " O’Reilly Media, Inc.", 2012.
- Wan, J.; Yang, J.; Wang, Z.; Hua, Q. Artificial intelligence for cloud-assisted smart factory. IEEE Access 2018, 6, 55419–55430. [Google Scholar] [CrossRef]
- Chang, Z.; Liu, S.; Xiong, X.; Cai, Z.; Tu, G. A Survey of Recent Advances in Edge-Computing-Powered Artificial Intelligence of Things. IEEE Internet of Things Journal 2021, 8, 13849–13875. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Satapathy, U.; Patnaik, S. Survey on IoT security: Challenges and solution using machine learning, artificial intelligence and blockchain technology. Internet of Things 2020, 11, 100227. [Google Scholar] [CrossRef]
- Ghosh, A.; Chakraborty, D.; Law, A. Artificial intelligence in Internet of things. CAAI Transactions on Intelligence Technology 2018, 3, 208–218. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





