1. Introduction
With the evolvement of technology, such as internet-connected wearables, enhanced reality, mobile devices, and the intrusion of social media in our lives, our individuality is exposed constantly. Data are retrieved from companies and individuals in many ways and sometimes without even our knowledge, for example from the Internet of Things devices (IoT) [
35] or even when we self-expose ourselves to social networks [
14,
51]. Self-exposed behavior may have a significant negative effect on individuals’ lives and Information and Communications Technology (ICT) users’ may find themselves as victims of thieves, scams, or impersonation. At the same time, third parties can use personal data in their favor in many ways such as to manipulate voting opinions [
21] or manipulate buying behavior through targeted advertising practices [
33,
41]. Thus, ICT users’ are vulnerable to privacy breaches, data misuse, and unauthorized access to their personal information.
Last decade the research on what influences privacy behavior showed a significant increment. Researchers, software houses, information security providers, and individuals are trying to find ways to enhance ICT users’ privacy behavior. Various studies have shown that ICT users’ state that they care about their personal data but they still disclose a vast amount of personal information when using internet-connected devices [
14,
51]. Many academics recognized this phenomenon as a “privacy paradox” [
18,
20,
27,
32]. Several studies have tried to identify the reasons behind ICT users’ privacy behavior identifying psychological, sociological, and behavioral factors for their actions [
18,
20,
27,
32]. Many researchers found various factors that influence privacy behavior and thus if we alter these factors we may influence ICT users’ privacy behavior actions, such as personal information disclosure or the application of privacy-protective controls, or the configuration of privacy settings.
From the above, we identify the necessity to confront two issues. First, we need to understand what affects privacy behavior, and second, it will be beneficial to understand how to influence ICT users’ protective privacy behavior. To address the first issue, we conducted an in-depth literature review on the factors affecting privacy behavior. Our recent research [
41] showed that behind ICT users’ privacy behavior, there are eleven dominant factors, including privacy concerns, trust, awareness, and others (further analyzed in
Section 5). In addition, we laid the groundwork for extending our research to the utilization of these factors for enabling privacy-protective behaviors and thus address the second issue. Our examination of learning methods showed that many researchers claim that experiential methods and practices have significant advantages over traditional education and learning [
12,
13,
15,
24,
26,
28,
36,
37,
38,
39,
44,
54]. Experiential learning is defined as the process whereby knowledge is created through the transformation of experience [
28]. Thus, in this paper, we propose to use experiential methods and practices to promote privacy-protective behaviors, taking into account the antecedents of privacy behavior. We identify methodologies and practices that are followed in the fields of philosophy, psychology, and sociology to influence someone’s behavior using experiential methods. We argue that this work can lay the ground for examining empirically how to guide ICT users’ existing privacy behavior to become more privacy-protective. To the best of our knowledge, this is the first research that is trying to encapsulate experiential learning methods and target modifying users’ privacy behavior. In summary, our paper addresses the following research questions:
Research Question 1. What empirical methods and practices have been followed in other fields, such as philosophy or psychology, to influence human behavior via experiential techniques and could be used in the field of information privacy towards enabling privacy-protective behaviors?
Research Question 2. How can we influence privacy behavior determinant factors to guide ICT users’ privacy behavior using experiential methods?
After the introduction, the paper continues with the sampling methodology of the literature review we performed. In
Section 3, we perform a literature review of experiential learning in the fields of philosophy, psychology, health, and sociology. In
Section 4, we provide an adjustment of the definitions we found during the literature review in the field of our expertise and we provide our conceptual scheme. In
Section 5, we propose an adaptation of the above definitions to our field and we provide an encapsulation between the theories we capture from our literature review and the privacy behavior factors. In
Section 6, we discuss our findings our model. Finally,
Section 7 concludes the paper and provides implications, possible solutions, and future research.
2. Literature Review Methodology
2.1. Sampling Methodology
For our search in the literature, we used the most recognized scientific search engines, such as Science Direct and Google Scholar. We refrained from imposing any limitations on the chronological range or publication types. Instead, we deemed journal articles and conference articles as suitable sources to yield acceptable outcomes. We used the keywords: experiential learning, experiential education, experiential learning methods in phycology, experiential learning methods in sociology, and experiential learning methods in philosophy. We also included several books that studied experiential methods and experiments that affect learning and education using experiential procedures in the above fields. These books are mostly in physical form and cannot be found online.
2.2. Exclusion Criteria
Applying the aforementioned methodology outlined above, our initial search yielded a substantial number of 584 outcomes. To refine and narrow down the extensive pool of results, we implemented a rigorous selection process that prioritized articles and books with high citation counts, in addition to publications authored by recognized pioneers within their respective fields. Consequently, our efforts culminated in the identification of 90 distinct and noteworthy papers and books. Nevertheless, a subset of the retrieved articles failed to elucidate any factors associated with experiential learning methodologies. Subsequently, we employed a screening process to eliminate studies that, despite satisfying the search criteria, did not primarily focus on the identification of experiential methods for educational or learning purposes, and consequently lacked corresponding outcomes. Consequently, we excluded a total of 41 papers from further analysis, as they did not specifically investigate the subject matter at the core of our study. Following this rigorous procedure, we were left with a final selection of 49 papers and books that specifically examined or identified distinct methods capable of influencing the learning or educational procedures.
3. Theoretical Background in Experiential Learning in Other Fields
3.1. The concept of Behavior in Psychology
This section is a first reference to the basic theories that contributed to the under-standing of behavior as reflected by the field of psychology. More specifically, 4 basic theories are captured:
the neuropsychological theory,
the psychoanalytical theory and
the behavioral theory and
the cognitive theory.
The above theories were not the only ones formulated but the most basic ones studied by the specific field of psychology.
Neuropsychological Theory: This theory examines only pathological behaviors, which are seen through the cognitive effects of neurological disorders [
19,
43]. We will not delve into this theory as it relates to ailments of a medical nature.
Psychoanalytic Theory: According to Freud ([
17,
40]), human behavior is the result of a person’s defense against his instinctual impulses.
Behavioral Theory: A person’s behavior consists of the immediate reaction to an environmental stimulus. Stimulus
→ Reaction = Behavior or S
→ R = Behavior. Pavlov [
42] in his research describes that a person’s behavior is acquired through classical conditioning, while according to Skinner [
17,
40], through operant conditioning, and is modified only if the environmental stimuli are modified. The basic mechanisms of behavior control and modification are reward/reward, fear, and punishment.
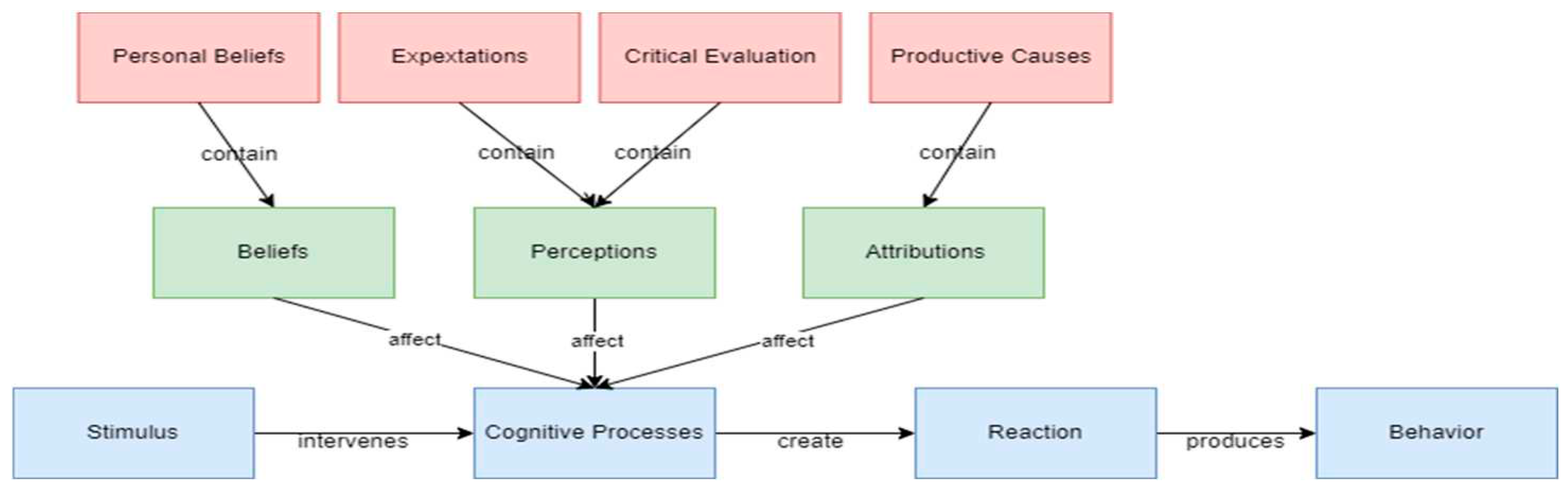
Cognitive Theory: It is the evolution of S R Behavioral Theory. This theory holds that the stimulus and the reaction mediate cognitive processes that influence behavior. According to Weinman [
55], cognitive processes include beliefs, perceptions, and attributions, or else called productive causes [
29]. According to Koulierakis et al., [
29] As attribution is defined as the cognitive process that a person construct trying to explain why an event happened to her. The above contributes together with the environment to making a decision or facing a challenge. Finally, according to Ambrason [
1], attributions can be generalized or specialized. Models that attempt to explain how cognitive factors lead to various social behaviors are referred to as socio-cognitive models. Conner [
10] and Conner and Norman [
11] distinguish two types of socio-cognitive models. The first type includes the attribution models which refer to people’s causal explanations for events related to their health. The second type includes models aimed at predicting people’s future behavior.
In the context of this research, we will not deal with the first two theories as the first concerns behaviors that are due to pathological factors, while the second captures more the explanation of behavior than how it can be modified. The schematic representation of the Behavioral Theory and Cognitive Theory can be seen in
Figure 1 and
Figure 2.
For example, John and Alice are looking at the photo uploaded on Instagram by their mutual acquaintances Tomas and Kathrin with public access to it. The photo shows the two of them sitting in a park in Karlovy Vary in the Czech Republic. John thinks what a beautiful photo (cognitive processes: belief and perception), while Alice, who is more privacy aware, realizes that Kathrin and Tomas are not in their residences and now several people will know about it and are exposed to the risk of robbery (cognitive process: attribution: awareness). In this example, the environmental conditions were the same but the cognitive background of Alice was different. Moreover, we observe that in this example multiple cognitive processes came into effect. From this point of view, John’s beliefs and perceptions made him observe only the romantic part of the photo. On the other hand, her privacy awareness levels of Alice activated her cognitive processes differently and made her understand the dangers of that post. The potential expositions in that photo do not stop at what Alice observed. For example, even If the date was not visible, an experienced ICT user could potentially find the date of the photograph from the meta-data of the photograph.
Cognitive psychologists describe two distinct types of cognitive processes. The first type of processes is the short-term processes which include expectations and critical evaluation as elements of perceptions and the productive causes as attributions. The second type is long-term processes that contain the personal beliefs of the person.
According to Bandura, expectancy is a process in which the individual discounts a future event. Bandura describes the Expectancy process as both a perception process and a belief depending on the point of view of the event. According to Beck [
5], critical evaluation is a perception process and can be used as a diagnostic process in which individuals evaluate what may be happening to them. According to Rotter [
48], productive causes are perceptions that people construct when trying to explain why something happened to them. It is also worth mentioning that according to the social psychologists, Stroebe & Stroebe [
53] cognitive processes are the essential causes of the manifestation of behavior. Also, cognitive processes are more amenable to modification when they involve cognitive factors such as beliefs than factors such as personality. Also, Sheeran and Abraham [
52] state that beliefs are stable individual characteristics that shape behavior and are acquired through early socialization without being strictly de-fined and can vary between individuals of the same social group. Finally, Lewin [
31] formulated the value-expectancy model which states that an individual’s behavior revolves around two axes: The value that the individual assigns to a specific goal and the individual’s assessment of the probability of a specific action to achieve this goal. From all that preceded, we believe that there is a scientific consensus that cognitive theory is the dominant method in the fields of psychology and philosophy answering research question 1. We have to mention that psychology and philosophy were treated as one field until the philosopher Gockel coined the term “psychology” [
30].
3.2. The Concept of Behavior in the Health Field
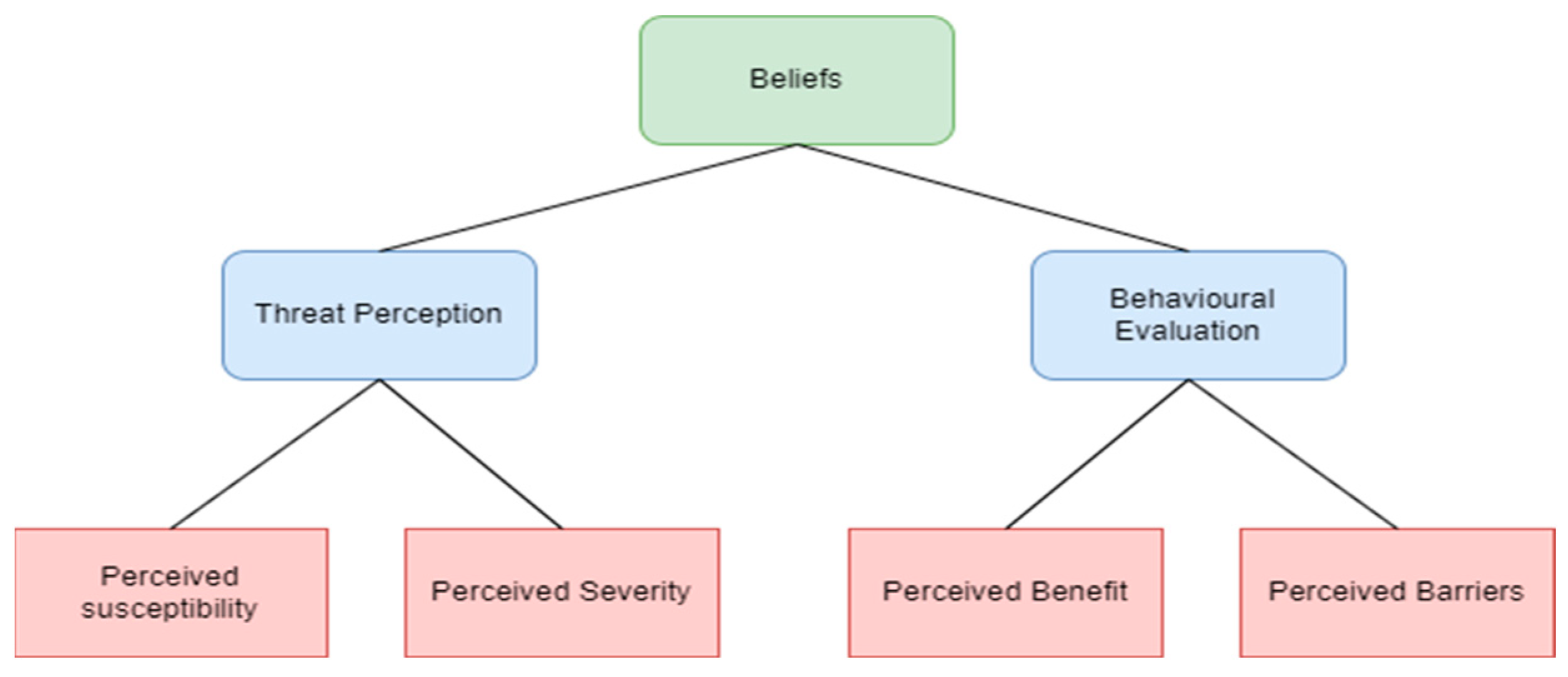
The health field played a significant role in the development of cognitive theory creating a new path of research mostly because of the close relationship between psychology and psychiatry. Many researchers from the health field tried to adjust the cognitive theory in their field of expertise most usually called the health belief model. The health model deals with the scientific area of psychology that deals with human behavior in the context of health and illness. Scientists use this model to intervene in problems arising from a chronic or life-threatening disease, but without engaging in a strictly therapeutic process [
22,
47,
52]. Becker et al., [
6] added another dimension to the model called “health motivation”, which is nothing more than the individual’s readiness to care about health issues. The model was formally established with the publication of the research by Becker et al., [
6] and was aimed at maintaining health and controlling frailty. The model has been used more than any other social-cognitive model in a range of health behaviors and different target populations [
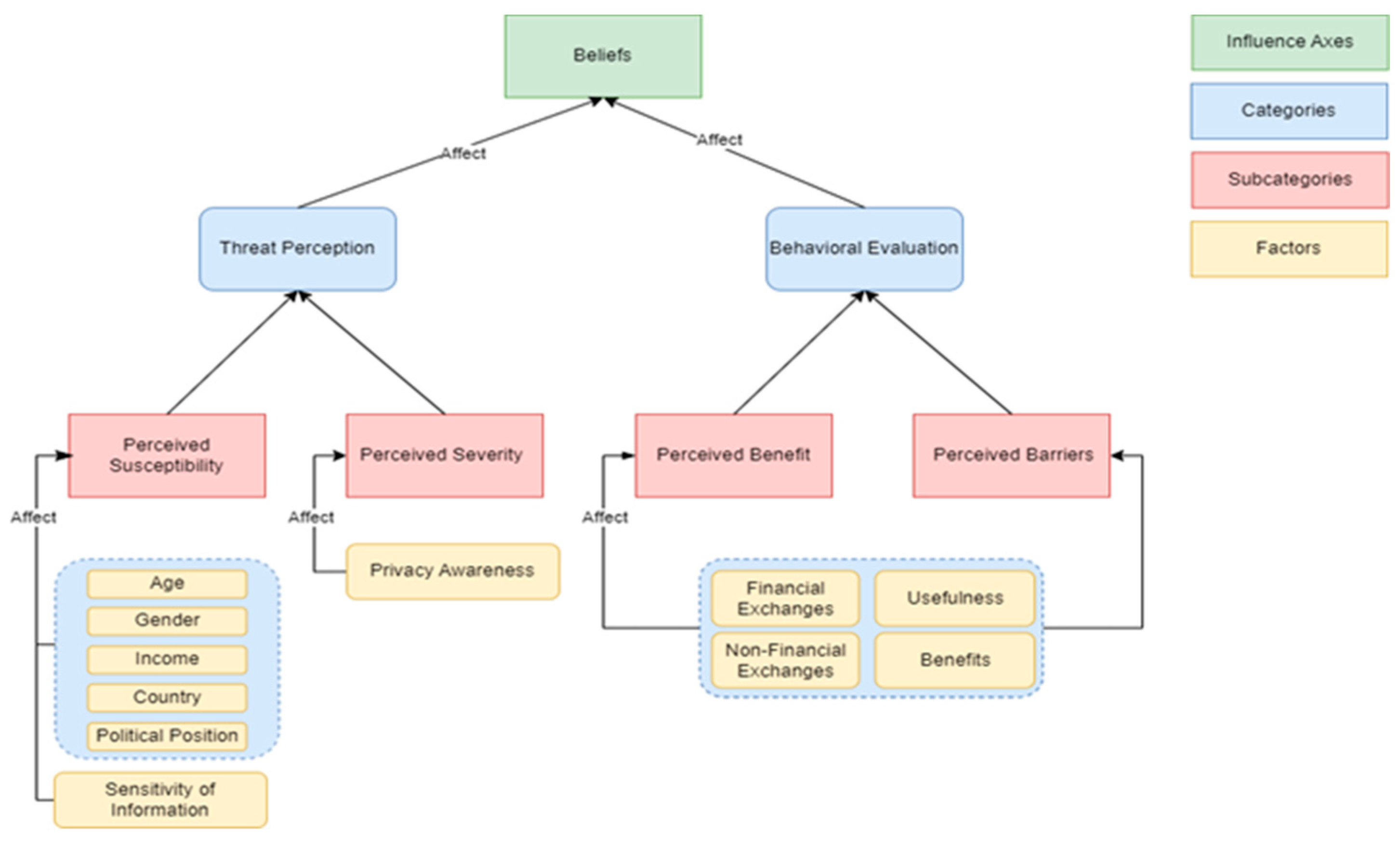
29]. The health belief model is based on two health-oriented axes. Threat perception and behavioral evaluation. The perception of a threat depends on two factors: the subjective sense of vulnerability (perceived susceptibility) and the subjective sense of severity (perceived severity) [
2,
6]. The evaluation of the behavior also consists of two sets of beliefs: the subjective feeling about the benefits (perceived benefits) from adopting a behavior targeting better health and the subjective feeling about the obstacles (perceived barriers) from adopting a behavior, i.e., the evaluation of the possible negative consequences associated with the prevention behavior (e.g., side effects.). The above is reflected in
Figure 3.
3.3. Behavior and Experiential Learning
In this section, we present the literature review on the definitions of experiential experience and learning, as they have been defined in the fields of psychology, philosophy, and sociology in the past.
Ross and Brown [
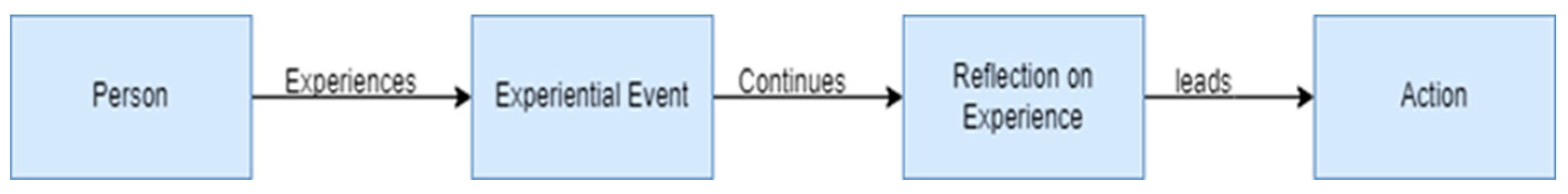
3] in their book about Aristotle called Aristotle in the Nicomachean Ethics state that according to Aristotle for the things we must learn before we do them, we learn them by doing them. The experiential experience differs from the didactic experience where the participant has a mostly passive role. Dewey [
13], one of the first scholars to deal with the importance of experiences in learning, states that a person learns from their experiences when they are active in them and the light of supporting evidence. In partial agreement with Aristotle, Freire [
16] states that the cycle of learning begins with an experiential event, continues with a reflection on experience, and leads to action. We argue that this last theory shows common elements with the cognitive theory model we described in
Section 3.1 (
Figure 2).
Figure 4.
Experiential learning process according to Frerie (1980).
Figure 4.
Experiential learning process according to Frerie (1980).
According to Kolbs [
28], personality and environmental and social factors play a large role in the acquisition of knowledge. He states that to acquire knowledge through experiential learning, the following factors must be present:
- -
The participants must have the will to learn through the experience they lived
- -
The participants should be able to reproduce the experience
- -
The participants must have analytical thinking and understand the experience
- -
The participants have the ability to make decisions and solve problems to create new ideas through the experiences they lived
Rogers [
45] extended Kolb’s view, including in the conditions of experiential learning both the assessment of an acquired experience of the subject himself and of a third party (the subject of experiential learning as an observer).
Boud et al. [
7] identify three stages of the reflective process in the context of experiential learning:
- -
The participant reviews the events and has the ability to study the experience again, calling this review a return to the experience
- -
The participant recognizes the importance of the experience to third parties, through emotions
- -
The participant discovers the new dimensions of the experience so that through it the change in his behavior occurs and creates a new way of thinking and abilities
Boud et al. [
7] recognize that this is a transformative process, and through experiences, the subject recognizes new tendencies and abilities.
Jarvis [
24] criticizing Kolb’s model, agrees that learning arises from experience but does not necessarily involve the activity of processing or conscious reflection, although he emphasizes that awareness allows the individual to change his reactions and beliefs. Therefore, according to Jarvis, experience consists of the integration of an external stimulus into one’s store of knowledge. According to Boud et. al, [
7] as cited in Kokko [
26], awareness can lead to an individual’s internal commitment to action/reaction as well as the modification of their knowledge. Mezirow [
36] states that adults in particular learn more efficiently through reflection on experience and thus experiential learning. By making use of mental habits, meaning-making perspectives, and meaning-sets, these become multifaceted, open, and emotionally ready to produce beliefs and opinions that prove capable of justifying the impulse to action. In agreement with the above, scientists in the fields of philosophy, sociology, and psychology are also the view of Taylor [
54]. According to his research, the adoption of opinions and patterns of behavior takes place gradually and mainly experientially and without the awareness of various social and cultural influences and limitations. Experiential learning has also occupied the field of school learning. Other researchers [
12,
34] have studied the learning processes of teachers and have concluded that teachers as adults are in a daily learning process focusing on improving teaching skills and their teaching methodologies. Such learning is part of the broader process of self-development and lifelong learning.
As we observe, various scientific fields have been involved with experiential learning for a long time. The first steps of experiential learning come from the ancient times of Aristotle probably around 335 B.C. when he said the famous phrase “the things we must learn before we do them, we learn them by doing them”. Afterward, at the start of the 20th century, we see the first tries at experiential learning and methods from psychologists and philosophers such as Freud [
16], Pavlov [
42], Dewey [
13], and, Kolbs [
28] and continues up to 21st century, especially from sociologists and philologists such as Kokko [
26], Mezirow [
36,
37,
38,
39], Jarvis [
24] and Dacou [
12].
4. Adaptation of Theoretical Background for the Domain of Privacy Behavior
In this section, we aim to adapt the aforementioned cognitive theory to our field of expertise. Our scope is to adapt the cognitive processes derived from the cognitive theory to the privacy behavior field. Our target is separated into two different axes. Firstly, we will connect, adapt and classify the cognitive processes elements of beliefs, perceptions, and attributions (productive causes) to privacy behavior factors. Secondly, to adapt the cognitive theory as a basic modifier of privacy behavior enhancement using the experiential methods as described in
Section 3.3.
With an aim to propose our model, we will create and appropriately define new experiential learning terms that respond to ICT. Moreover, we will try to adapt the terms derived from the behavior and the experiential learning section and transform them to be a match for our proposed model.
Taking into account existing literature, we propose the following terms, as shown in the Table below (
Table 1):
Figure 5.
Conceptual scheme.
Figure 5.
Conceptual scheme.
5. Cognitive Theory and Privacy Behavior Factors
If we focus on cognitive theory and the belief model, we examined in
Section 3, we can identify common elements with our previous work [
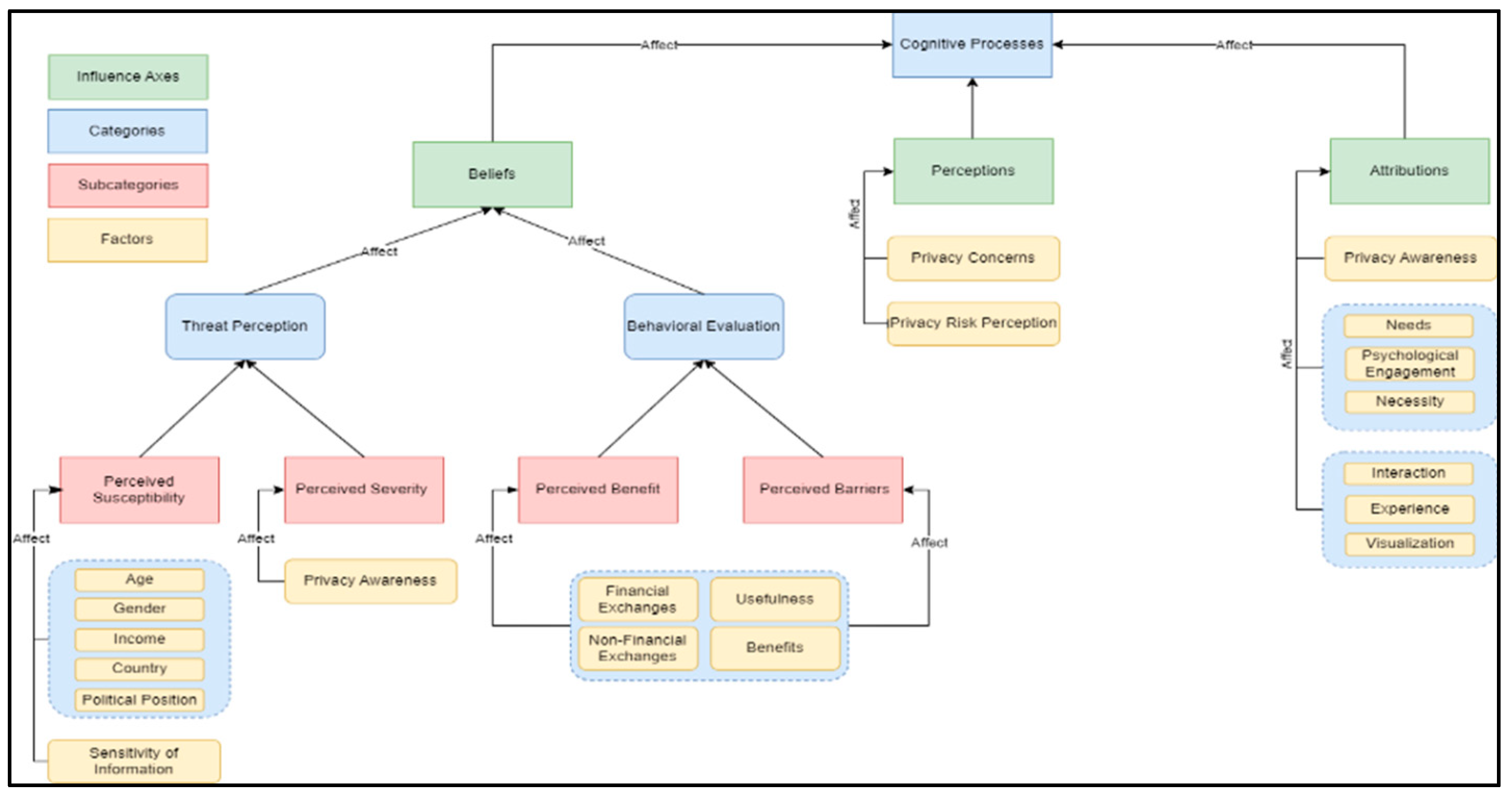
42] of what affects privacy behavior. More specifically, we observed that cognitive processes that affect behavior through experiential methods are affected by three influence axes (hereafter cognitive processes): beliefs, perceptions, and attributions. This offers fertile ground to try to conceptualize the factors that we analyzed in our previous work with the cognitive theory and the belief model. In the next subsection, we will show that every factor we found can be matched with the three elements of the cognitive theory. This match is not one way and each factor seems can be part of more than one influence axe.
5.1. Conceptualizing Cognitive Theory and Privacy Behavior Factors
5.1.1. Privacy Behavior Factors
In our recent research on how privacy behavior is formulated, we found evidence that privacy behavior is affected by a variety of factors, including individual ones (e.g., demographics) and contextual ones (e.g., financial exchanges). We synthesize a framework that aggregates the scattered factors that have been found to affect privacy behavior. More specifically, we found that there are eleven dominant factors that under the proper conditions can influence privacy behavior [
43]. The factors that we found are demonstrated in
Table 2.
In an aim to answer our second research question “How can we influence privacy behavior determinant factors to guide ICT users’ privacy behavior using experiential methods?” we have first to connect the cognitive theory we analyze above with our previous research results which privacy behavior factors can influence someone’s privacy behavior. To achieve our goal, we will try to show the connection between the privacy behavior modification factors with the cognitive theory’s cognitive processes influential axes.
Before we conceptualize the cognitive theory and privacy behavior factors, we set the matching criteria.
To set our matching criteria firstly we identify the variables we want to match from the fields we discussed and also be the most relevant to the research question 2: “How can we influence privacy behavior determinant factors to guide ICT users’ privacy behavior using experiential methods?”.
From the privacy behavior field, there is one variable the privacy behavior fac-tors. On behalf of the cognitive theory model, we recognize the 3 influential axes that influence the cognitive processes, perceptions, beliefs, and attributions (productive causes).
Secondly, we have to determine the method of matching. In academia, several methods have been proposed including propensity score matching [
49] as a means of reducing selection bias in observational studies.), covariate matching [
50,
51], and nearest neighbor matching [
23].
The propensity score matching method was first proposed by Rosenbaum & Rubin [
47] as a means of reducing selection bias in observational studies.
Covariate matching, also known as balance matching aims to balance the distribution of covariates between the treated and control groups in observational studies to reduce confounding bias.
The nearest neighbor matching method is particularly useful when the number of variables is small. The method can be used in a variety of fields, including epidemiology, economics, and psychology, to estimate the similarities of the observed variables, close relationships of the observed variables, or the outcome of a statistical or medical experiment.
We have excluded the first two methods because they do not apply to our study. The nature of this research is not to observe different groups or persons nor to reduce the confounding bias between groups. We believe that the nearest-neighbor method is close to the goals of this study. The dataset we have to match is relatively small while at the same time, this method is commonly used in psychology, philosophy, and sociology studies and experiments.
Based on the aforementioned considerations, we established the following criteria for our analysis:
Criterion 1: Etymological Similarity. This criterion pertains to the impact observed when an element of a cognitive theory exhibits congruence or similarity in meaning to a factor associated with privacy behavior.
Criterion 2: Similar Result or Definition. This criterion addresses the influence observed when an element of a cognitive theory and a factor related to privacy behavior yield comparable outcomes or share similar definitions.
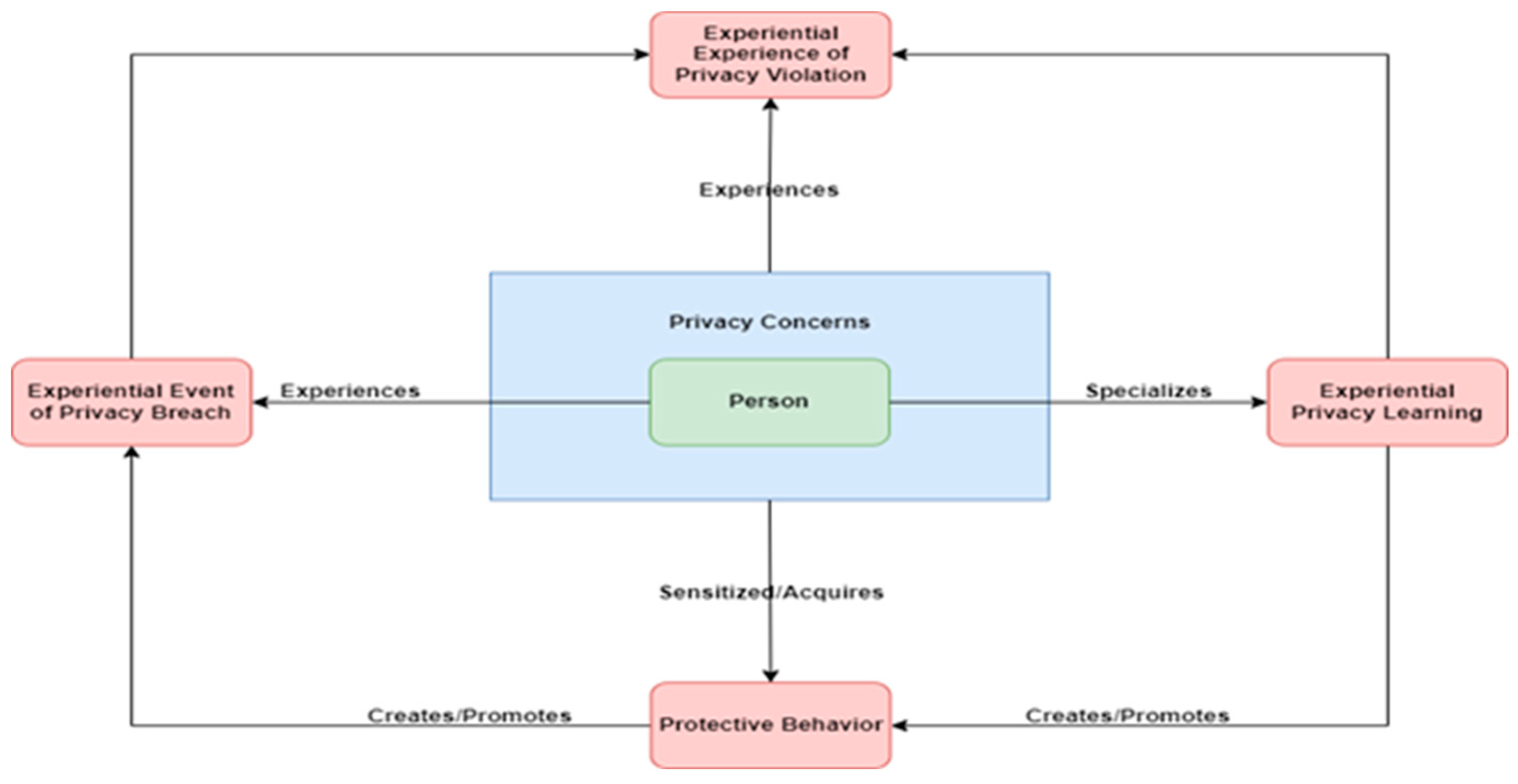
5.1.2. Beliefs
According to cognitive theory, beliefs affect the cognitive process and have two categories: Threat Perception and Behavioral Evaluation [
2,
6]. Each category has two subcategories. More specifically, the category Threat Perception includes the subcategories of Perceived and Perceived Susceptibility. The behavioral Evaluation includes the subcategories of Perceived Benefits and Perceived Barriers. Below we aim to align the identified privacy factors with the elements of the cognitive theory. According to Paspatis et. al., [
42], we argue that Financial/Non-financial Exchanges and Benefits are aligned with the subcategories Perceived Benefits and Perceived Barriers [
2,
6] because they correspond to both criteria 1 and 2. Both Financial/Non-financial Exchanges and Benefits have the same results on privacy behavior and the subcategories of behavioral evaluation element perceived benefit for the financial and non-financial benefits and perceived barriers as a similar result of the subfactor usefulness. At the same time perceive benefits are aligned etymologically with the subcategory financial/non-financial benefits. Respectively, the factor of Privacy Awareness matches the subcategory Perceived Severity. Privacy awareness as we presented in the photograph example in
Section 3.1 can play a significant role in the perceived severity of a person. We argue that privacy-aware persons can better understand a potential danger and minimize the severity of their actions. The cluster Demographics fits the sub-category Perceived Susceptibility looks which corresponds to criterion 2. This cluster contains elements such as age and gender. Reynolds et al., [
45] research showed that the susceptibility of a person is affected both by age and gender. More specifically, females tend to post more often and with fewer privacy re-strictions on OSNs than males while older users claimed to be more concerned with privacy and this is reflected in their posting practices. On the other hand, the Sensitivity of information we believe it fulfills only criterion 1 due to the etymological similarity. All of the above is reflected in
Figure 6.
Table 3 presents our adaptations of privacy behavior factors to the cognitive process Beliefs of the cognitive theory.
5.1.3. Perceptions
Respectively to the previous subsection, the Cognitive Processes contain two more categories’ Perceptions and Attributions or else productive causes. Following the same match criteria as the previous section we argue that cognitive processes’ element “perceptions can be a match with at least for the privacy behavior factors privacy risk perception and privacy concerns meeting criterion 2. As we mentioned in
Table 1 privacy concerns are the willingness of a person to share data, and how these relationships in turn are affected by inter-individual differences in individuals’ regulatory focus, thinking style, and institutional trust. The additional definition in psychology according to Cherry [
9] perception relies on the cognitive functions we use to process information, such as utilizing memory to recognize the face of a friend or detect a familiar scent. Through the percep-tion process, we can both identify and respond to environmental stimuli. We argue that concerns are philosophically in a close relationship with the cognitive processes’ perceptions. Respectively, privacy risk perception seems to meet both the match criteria 1 and 2. Privacy risk perception is a perception relevant to the risk a person may confront while at the same time cognitive processes’ perception definition is the process or result of becoming aware [
9]. As previously, we believe that privacy risk perceptions and cognitive processes element perception are good candidates for a match so we argue that etymologically is very similar to fulfilling criterion 1.
Table 4 presents our adaptations of privacy behavior factors to the cognitive process Perception of the cognitive theory.
5.1.4. Attributions
Following the same matching criteria as above we argue that cognitive processes element Attributions are a match for a variety of factors. As a definition, in social psychology, attribution is the process of inferring the causes of events or behaviors [
8]. At the same time, it may describe the characteristics of a person usually without any awareness of any underlying process. On behalf of privacy behavior, we argue that the cluster “needs, psychological engagement, and necessity” meet the matching criteria for both 1 and 2. Firstly, all of the factors of the cluster are from the field of psychology fulfilling criterion 2. Secondly, by etymology, the factor of psychological engagement fulfills criterion 2. Respectively, awareness is described by both cognitive process element attribution by definition as well as from the part of privacy behavior factor privacy awareness. From the above, we argue that privacy awareness and attribution element awareness are fulfilling both criteria. Continuing, we argue that from the side of privacy awareness, the factors of interaction and experience also meet our match criteria. As we mentioned, attribution is the process of inferring the causes of events or behaviors. We argue that both interactions can be the result of an event fulfilling criterion 2. Respectively, attributions may describe the characteristics of a person. We argue that the factor of experience is a characteristic of a person fulfilling criterion 2.
Figure 7 presents the cognitive theory with the adapted privacy behavior factors.
Table 5 presents our adaptations of privacy behavior factors to the cognitive process Attributions (Productive causes) of the cognitive theory.
6. Discussion
In our research, we have shown the use of cognitive theory in the field of information privacy behavior. We performed a literature review regarding relevant works and theories explaining behavior transformation in the domains of sociology, psychology, philosophy, and health. This analysis demonstrated that significant work related to behavioral transformation was conducted in the field of health. Taking into account the results of the literature analysis we put our perspective on the Cognitive Theory and Health Belief Model, by integrating them with Privacy Behavior Determinant Factors. Our proposed integrated framework aligns the factors that have been identified to influence privacy behavior with the Cognitive Theory and Health Belief Model.
Our literature review is in
Section 3.3. reveals that the experiential learning method is more beneficial for people than traditional learning. Aristotle set the starting line around 349 B.C. Since then, many philosophers, psychologists, and sociologists were engaged to prove that experiential learning has advantages over the traditional way of learning and education [
7,
13,
15,
28,
36,
46]. In addition, as we described in
Section 3.1 and 3.2 cognitive theory [
56] and the health belief model offer a proven approach to transforming someone’s behavior [
10,
11,
29]. With our work of conceptualizing the privacy behavior determined factors with the cognitive processes an element of cognitive theory creates a new optimistic frame of the research. With this model, we introduce not only experi-ential learning in the ICT environment but also which factors we should trigger to succeed in the privacy behavior modification of a person to a more protective one.
7. Conclusions and Future Work
Privacy behavior is a phenomenon that we observe for more than 20 years but it seems that there is more ground to cover to find new and more efficient ways to influence it. The traditional ways of teaching and educating are still present but it seems they may not be the optimal way for privacy behavior transforming. Many researchers observed in the past that ICT users’ privacy behavior needs improvement [
14,
21,
52] or else we may continue to confront phenomena such as “the privacy paradox” [
18,
20,
27,
32]. During our literature review in the fields of sociology, psychology, philosophy, and health we found that the cognitive theory and the health belief model may offer an alternative method to under-stand ICT users’ privacy behavior and influence it towards a more protective one. Building on our previous research on what factors affect privacy behavior we provided an integrated framework utilizing the cognitive theory and health belief model. We found connections between the majority of factors with the influential axes of the above theories proposing a fertile model for more research on experiential privacy learning.
The proposed integrated framework can be used by researchers to design empirical experiments and experiential methods toward finding novel ways to trigger ICT users’ protective behavior. Thus, our framework can have an impact of the AAA mechanism on privacy behavior. More specifically, this proposition is focused to enhance users’ privacy awareness and this will have effect to all three parameters of the AAA. To the best of our knowledge, this is the first research that offers a solid theoretical background for privacy behavioral trans-formation using the cognitive theory and the health belief model. Our research may be beneficial to the academic community for facilitating privacy learning; for example, for elementary schools, academic institutes, and private schools offering new models of teaching with an aim to improve students’ protective privacy behavior. In addition, it may shift the attention of privacy academics offering new paths of research.
Our findings related to the cognitive theory and the connection with our previous research on privacy behavior determinant factors are limited. Therefore, we aim to prove and improve our integrated model via empirical research which will allow us to refine and propose a solid model for improving ICT users’ privacy behavior. This research received no funding.
References
- Abramson, Seligman, Teasdale. Learned helplessness in humans: Critique and reformulation, Journal of Abnormal Psycology. Vol. 87, p. 49-74, 1978.
- Anagnostopoulou and Papadatou (1995). Psychology in the field of Health, Ellinika Grammata Publications, Athens, 1995.
- Aristotle, W. D. 1877-1971. Ross and Lesley Brown, The Nicomachean Ethics. Oxford; New York, Oxford University Press, 2009.
- Bandura (1977). “Self-efficacy: toward a unifying theory of behavioural change”, Psychological Review, 84, p.191-215, 1977.
- Beck (1976). Cognitive therapy and the emotional disorders, International Universities Press, New York, 1976.
- Becker, Haefner and, Mainman (1977). The health belief model in the prediction of dietary compliance: a field experiment, Journal of Health and Social behaviour.
- Boud, D, Keohg, R., Walker, D. (2002). Reflection: Turning experience into learning. New York: Kogan Press.
- Cherry (2022). What Is Attribution in Social Psychology? Available at: https://www.verywellmind.com/attribution-social-psychology-2795898.
- Cherry (2023). What Is Perception? Recognizing Environmental Stimuli Through the Five Senses. https://www.verywellmind.com/perception-and-the-perceptual-process-2795839.
- Conner (1993). Pros and cons of social cognition models in health behaviour, in Health Psychology. Update Volume 14, pages 24-31, 1993.
- Conner and Norman (1996). Predicting health behaviour. Research and practice with social cognition models, p. 1-22. Open University Press, Buckingham, 1996.
- Dacou (2018). H Εκπαιδευτική Βιογραφία επηρεάζει και καθορίζει την επαγγελματική διαδρομή των ενηλίκων. H περίπτωση των εκπαιδευτικών. Ελληνικό Aνοικτό Πανεπι-στήμιο. Available at: https://apothesis.eap.gr/handle/repo/39397 [Accessed 29/01/2020].
- Dewey (1938). Experience and Education. New York: Macmillan.
- Dhir A., Kaur P., Lonka K., Nieminen M. (2016). Why do adolescents untag photos on Facebook? Computers in Human Behavior.
- Freire (1980). Teachers as cultural workers – Letters to those who dare to teach, 1980.
- Freud. (1920), Massen Psychologie und Inch analyse, 1920.
- Gardner (1979). Behaviorism and dynamic psychology: Skinner and Freud. Psychoana-lytic Review, 66(2), 253–262.
- Gerber, N., Gerber, P. and Volkamer, M., (2018). Explaining the privacy paradox: A systematic review of literature investigating privacy attitude and behavior. Computers & Security, 77, pp.226-261.
- Gluck, Mercado, Myers (2016). Learning and Memory: From Brain to Behavior. New York/NY, USA: Worth Publishers. p. 57. ISBN 978-1-319-15405-9.
- Hallam, C. and Zanella, G., (2017). Online self-disclosure: The privacy paradox explained as a temporally discounted balance between concerns and rewards. Computers in Human Behavior, 68, pp.217-227.
- Hinds J., Williams E., Joinson A., (2020), “It wouldn’t happen to me”: Privacy concerns and perspectives following the Cambridge Analytica scandal, International Journal of Human-Computer Studies. [CrossRef]
- Hochbaum (1958). Public Participation in Medical Screening Programs: a Socio-Psychological Study, Public Health Service, United States Government Printing Office, Washington DC, 1958.
- Holmes, C. C., & Adams, N. M. (2003). Likelihood Inference in Nearest-Neighbour Classification Models. Biometrika, 90(1), 99-112. [CrossRef]
- Jarvis, P. (2004). Adult education & Lifelong Learning. London: RoutledgeFalmer.
- Koester, Cichy, Antons. et al. (2022). Perceived privacy risk in the Internet of Things: determinants, consequences, and contingencies in the case of connected cars. Electron Markets (2022). [CrossRef]
- Kokko (2005). Μεθοδολογία Εκπαίδευσης Ενηλίκων: Θεωρητικό Πλαίσιο και Προϋπο-θέσεις Μάθησης. Τόμ. A΄. Πάτρα: ΕAΠ.
- Kokolakis Spyros (2017), Privacy attitudes and privacy behaviour: A review of current research on the privacy paradox phenomenon, Computers & Security, Volume 64, 2017, Pages 122-134, ISSN 0167-4048. [CrossRef]
- Kolbs (1984). Experiential Learning: Experience as the Source of Learning and Development, 1984.
- Koulierakis, Metalinou, Pantzou (1995). Sociological and psychological approach to hospitals and health services. Hellenic Open University Publications, 1995.
- Krstic (1964). Acta Instituti Psychologici Universitatis Zagrabiensis, no. 36, pp. 7-13.
- Lewin (1951). Field theory in social science, Harper, New York, 1951.
- Li H., Luo X., Zhang J. and Xu H., (2017). Resolving the privacy paradox: Toward a cognitive appraisal and emotion approach to online privacy behaviors. Information & Management, 54(8), pp.1012-1022.
- Mathews-Hunt K., (2016). CookieConsumer: Tracking online behavioural advertising in Australia. computer law & security review 32 ( 2 0 1 6 ) 55–90.
- Mavrogiorgos (2009). Επιμόρφωση Εκπαιδευτικών: H «Άλλη»-αντί(-παλη) – Πρόταση. Λευκωσία.
- Menard P., Bott G., (2020). Analyzing IOT users’ mobile device privacy concerns: Extracting privacy permissions using a disclosure experiment. Computers & Security 95 (2020) 101856.
- Mezirow, Jack. (1991). Transformative dimensions of adult learning. San Fransisco: Jossey-Bass.
- Mezirow, Jack. (1998a). Transformative learning and social action: a response to Inglis. Adult education quarterly, 49, 70-72. American association for adult and continuing education: Sage publications.
- Mezirow, Jack. (1998b). On critical reflection. Adult education quarterly, vol 48, p. 185-198. American association for adult and continuing education: Sage publications.
- Mezirow, Jack., (2006). H μετασχηματίζουσα μάθηση. Εκδόσεις Μεταίχμιο.
- Overskeid, G. (2007). Looking for Skinner and finding Freud. American Psychologist, 62(6), 590–595. [CrossRef]
- Palos-Sancheza P., Jose Ramon Saurab, Felix Martin-Veliciaa (2019). A study of the effects of programmatic advertising on users’ concerns about privacy overtime. Journal of Business Research 96 (2019) 61–72.
- Paspatis (2023). HOW IS PRIVACY BEHAVIOR FORMULATED? A REVIEW OF CURRENT RESEARCH AND SYNTHESIS OF INFORMATION PRIVACY BEHAVIORAL FACTORS. Telematics and Informatics. [Submitted].
- Pavlov, I. P. (1927). Conditioned Reflexes: An Investigation of the Physiological Activity of the Cerebral Cortex. Translated and edited by Anrep, GV (Oxford University Press, London, 1927).
- Posner and DiGirolamo (2000). “Cognitive neuroscience: origins and promise”. Psycho-logical Bulletin. 126 (6): 873–889. [CrossRef] [PubMed]
- Reynolds, B., Venkatanathan, J., Goncalves, J. and, Kostakos, V., (2011b). Sharing Ephemeral Information in Online Social Networks: Privacy Perceptions and Behaviours. 204-215. [CrossRef]
- Rogers, A. (1999). H εκπαίδευση ενηλίκων. Εκδόσεις Μεταίχμιο.
- Rosenbaum & Rubin (1984). Reducing bias in observational studies using subclassifi-cation on the propensity score. Journal of the American Statistical Association. 1984;79:516–524.
- Rosenstock (1974). Historical origins of the health belief model, Health Education Monographs., Vol. 2, pages 1-8, 1974.
- Rotter (1966). Generalized expectancies for internal and external control of reinforcement, Psychological Monographs: General and Applied, Volume 80, p. 1-28, 1966.
- Rubin (1974). Estimating causal effects of treatments in randomized and nonrandomized studies. Journal of Educational Psychology. 1974;66:688–701.
- Rubin (1997). Estimating causal effects from large data sets using propensity scores. Annals of Internal Medicine. 1997;127:757–763.
- Shane-Simpson C, Manago A, Gaggi Naomi, Gillespie-Lynch Kristen, (2018). Why do college students prefer Facebook, Twitter, or Instagram? Site affordances, tensions be-tween privacy and self-expression, and implications for social capital, Computers in Human Behavior. [CrossRef]
- Sheeran and Abraham (1996). “The health belief model” in Conner and Norman, Predicting health behaviour. Research and practice with social cognition models. p.23-61. Open University Press, Buckingham, 1995.
- Stroebe and Stroebe (1995). Social Psychology and Health. Open University Press, Buckingham, 1995.
- Taylor W. E. (1998). The theory and practice of transformative learning: A critical re-view. ERIC Clearinghouse on adult, career, and vocational education. The Ohio State University.
- Weinman (1990). Health Psychology: Progress, perspectives, and prospects, Current developments in health Psychology, p. 9-33, Hardwood Academic Publishers, London, 1990.
- West and Michie (2020). West, Robert, and Susan Michie. Personal protective behaviour. Qeios, 2020.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).